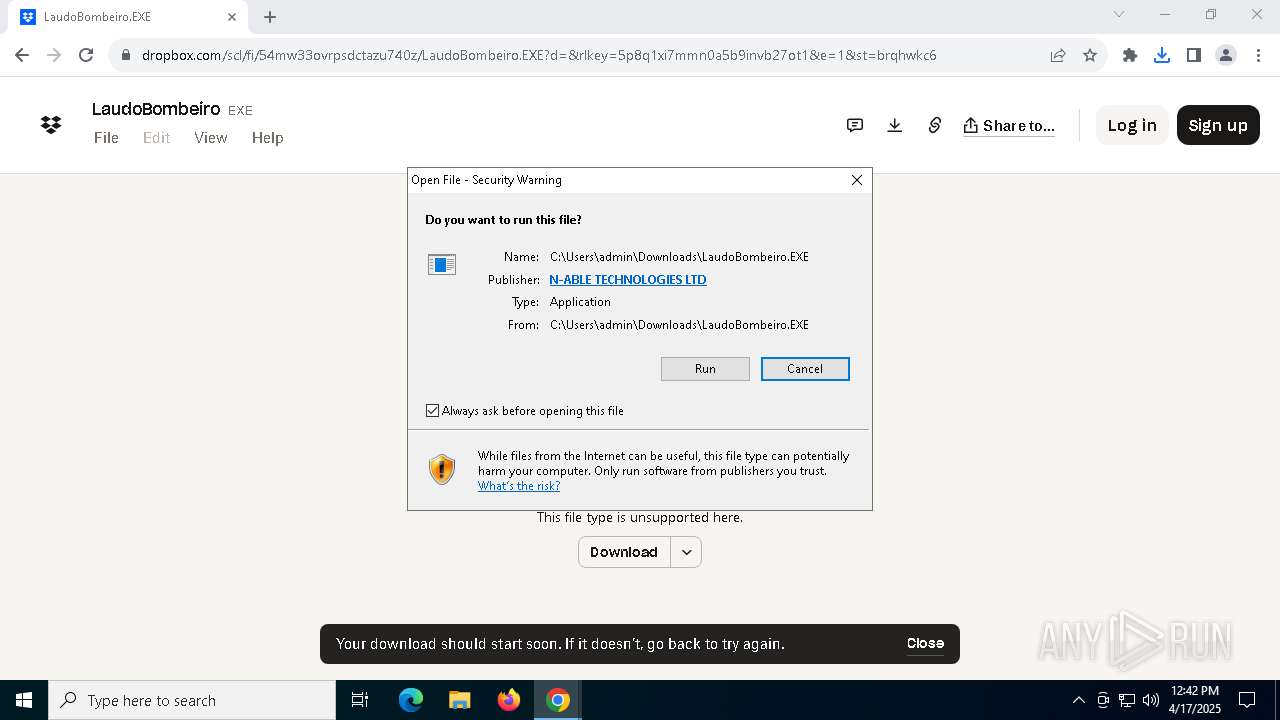
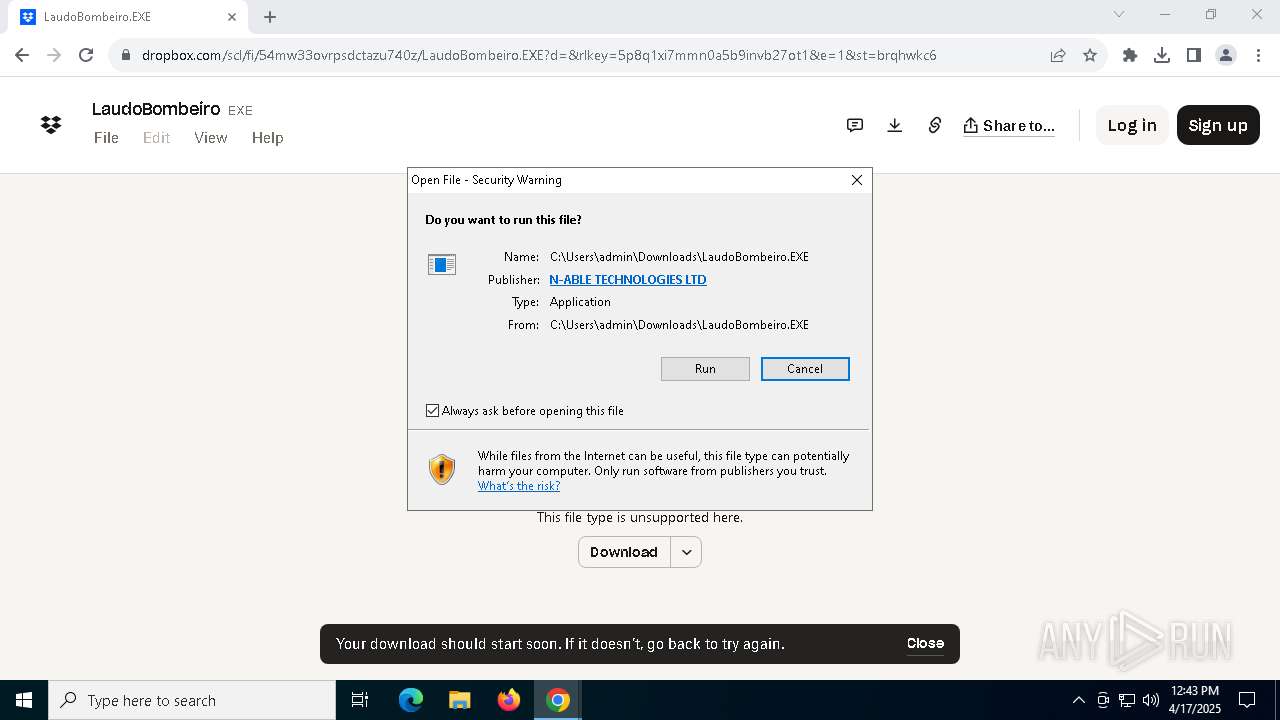
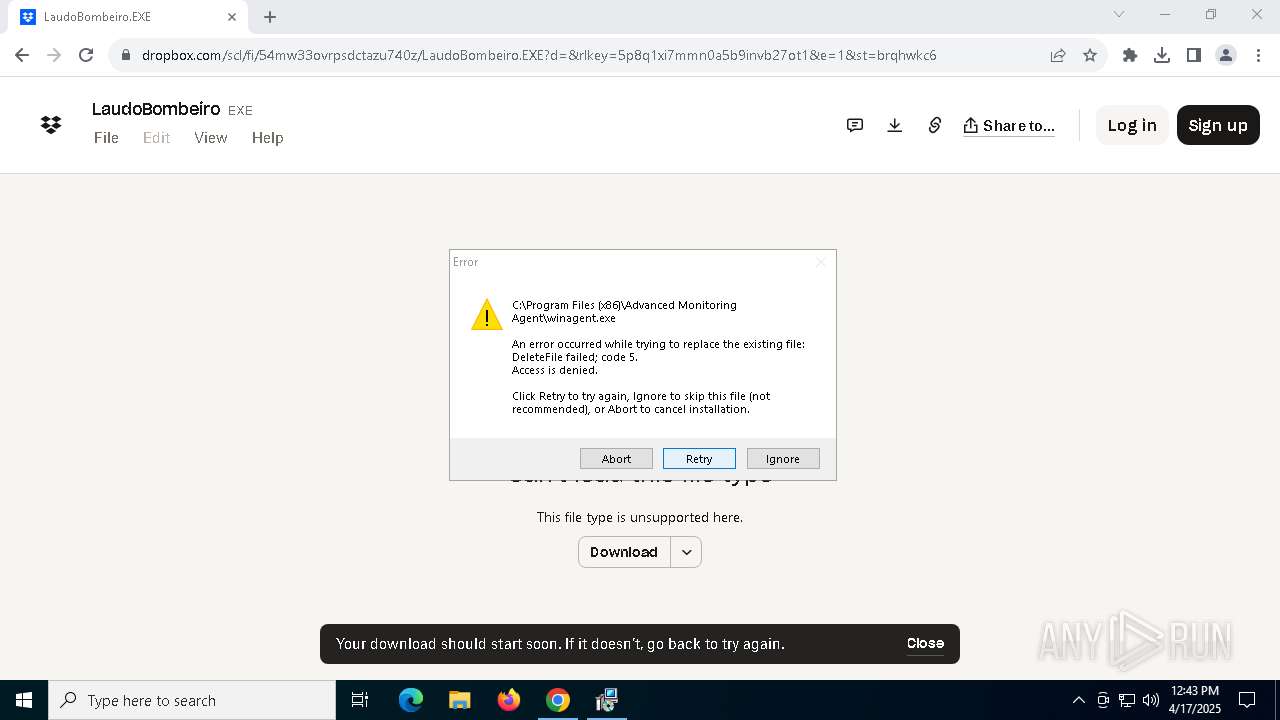
| URL: | https://www.dropbox.com/scl/fi/54mw33ovrpsdctazu740z/LaudoBombeiro.EXE?rlkey=5p8q1xi7mmn0a5b9invb27ot1&st=brqhwkc6&dl=1__;!!MupN1mo!T4NPbpHKCgq1eYCczpqmCwdMOO8w_sO4oL7VKqzSg75gEiWkMcTTchSkasF13S6d1xxDaBuNSJprKEk9JBv2rwL0xyoTaQ$ |
| Full analysis: | https://app.any.run/tasks/912d2de9-0d58-405b-a99d-11f61a7e8f8c |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2025, 12:40:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5F99D920C43AFAAE979399E183DDC71F |
| SHA1: | 2051DEFD0D4D1273320E8C4FBA3AF933C30C30D3 |
| SHA256: | E28F8CE89C320364CAE400095D3329FC27CB43EB1CBB490011B9875ECC47678C |
| SSDEEP: | 6:2OLHkOXT0YcYPEMKED6tKExuLL3x2SqMY/iv9SplD:2ikoTPZPRDlEIvXeM9Sr |
MALICIOUS
Starts NET.EXE for service management
- agent.tmp (PID: 2108)
- net.exe (PID: 5280)
- net.exe (PID: 2332)
Changes the autorun value in the registry
- vcredist_x86.exe (PID: 7556)
- ScriptRunner.Installer.exe (PID: 2908)
- MSP_Connect.exe (PID: 3800)
SUSPICIOUS
Executable content was dropped or overwritten
- LaudoBombeiro.EXE (PID: 4988)
- agent.exe (PID: 7288)
- agent.exe (PID: 684)
- agent.tmp (PID: 6760)
- winagent.exe (PID: 6208)
- vcredist_x86.exe (PID: 8044)
- LaudoBombeiro.EXE (PID: 6324)
- agent.exe (PID: 3784)
- agent.exe (PID: 7308)
- agent.tmp (PID: 2108)
- vcredist_x86.exe (PID: 7556)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7368)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
- ScriptRunner.Installer.exe (PID: 2908)
- msp-agent-core-upgrade.exe (PID: 2332)
- winagent.exe (PID: 7876)
- MSP_Connect.exe (PID: 3800)
- msp-agent-core.exe (PID: 776)
Reads security settings of Internet Explorer
- LaudoBombeiro.EXE (PID: 4988)
- agent.tmp (PID: 5376)
- agent.tmp (PID: 6740)
- LaudoBombeiro.EXE (PID: 6324)
- vcredist_x86.exe (PID: 7556)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
Process drops legitimate windows executable
- agent.tmp (PID: 6760)
- winagent.exe (PID: 6208)
- vcredist_x86.exe (PID: 8044)
- agent.tmp (PID: 2108)
- vcredist_x86.exe (PID: 7556)
- msiexec.exe (PID: 5812)
- MSP_Connect.exe (PID: 3800)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2196)
Searches for installed software
- winagent.exe (PID: 6208)
- vcredist_x86.exe (PID: 8044)
- vcredist_x86.exe (PID: 7556)
- dllhost.exe (PID: 4376)
- agent.tmp (PID: 2108)
- ScriptRunner.Installer.exe (PID: 2908)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
- winagent.exe (PID: 7876)
- assetscan.exe (PID: 5952)
- winagent.exe (PID: 2240)
- winagent.exe (PID: 2908)
- msp-agent-core.exe (PID: 472)
Reads the Windows owner or organization settings
- agent.tmp (PID: 6760)
- agent.tmp (PID: 2108)
- msiexec.exe (PID: 5812)
The process checks if it is being run in the virtual environment
- winagent.exe (PID: 6208)
- winagent.exe (PID: 7876)
Creates/Modifies COM task schedule object
- winagent.exe (PID: 6208)
- MSP_Connect.exe (PID: 3800)
Application launched itself
- vcredist_x86.exe (PID: 7556)
Executes as Windows Service
- VSSVC.exe (PID: 904)
- winagent.exe (PID: 7876)
- msp-agent-core.exe (PID: 776)
- msp-agent-core.exe (PID: 472)
There is functionality for taking screenshot (YARA)
- winagent.exe (PID: 6208)
Creates a software uninstall entry
- vcredist_x86.exe (PID: 7556)
- ScriptRunner.Installer.exe (PID: 2908)
- msp-agent-core.exe (PID: 472)
The process drops C-runtime libraries
- msiexec.exe (PID: 5812)
- MSP_Connect.exe (PID: 3800)
Starts itself from another location
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 7176)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 5812)
Executes application which crashes
- winagent.exe (PID: 6208)
- winagent.exe (PID: 2240)
Starts CMD.EXE for commands execution
- msp-agent-core.exe (PID: 8080)
- msp-agent-core.exe (PID: 776)
- msp-agent-core.exe (PID: 684)
- msp-agent-core.exe (PID: 4200)
- msp-agent-core.exe (PID: 472)
Creates or modifies Windows services
- BASupSrvc.exe (PID: 6044)
The process creates files with name similar to system file names
- MSP_Connect.exe (PID: 3800)
INFO
Connects to unusual port
- chrome.exe (PID: 7764)
Application launched itself
- chrome.exe (PID: 7580)
Reads the software policy settings
- slui.exe (PID: 7420)
- winagent.exe (PID: 6208)
- slui.exe (PID: 6456)
- vcredist_x86.exe (PID: 7556)
- msiexec.exe (PID: 5812)
- winagent.exe (PID: 7876)
- winagent.exe (PID: 2908)
- winagent.exe (PID: 2240)
- msp-agent-core.exe (PID: 776)
- msp-agent-core.exe (PID: 472)
Executable content was dropped or overwritten
- chrome.exe (PID: 6068)
- chrome.exe (PID: 7580)
- msiexec.exe (PID: 5812)
The sample compiled with english language support
- chrome.exe (PID: 6068)
- agent.tmp (PID: 6760)
- vcredist_x86.exe (PID: 8044)
- winagent.exe (PID: 6208)
- agent.tmp (PID: 2108)
- vcredist_x86.exe (PID: 7556)
- msiexec.exe (PID: 5812)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
- msp-agent-core.exe (PID: 776)
- msp-agent-core-upgrade.exe (PID: 2332)
- MSP_Connect.exe (PID: 3800)
Reads the computer name
- LaudoBombeiro.EXE (PID: 4988)
- agent.tmp (PID: 5376)
- agent.tmp (PID: 6760)
- winagent.exe (PID: 6208)
- vcredist_x86.exe (PID: 8044)
- vcredist_x86.exe (PID: 7556)
- agent.tmp (PID: 6740)
- LaudoBombeiro.EXE (PID: 6324)
- agent.tmp (PID: 2108)
- msiexec.exe (PID: 5812)
- ScriptRunner.Installer.exe (PID: 2908)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
- msiexec.exe (PID: 7176)
- winagent.exe (PID: 7876)
- assetscan.exe (PID: 5952)
- msp-agent-core.exe (PID: 8080)
- winagent.exe (PID: 2240)
- msp-agent-core.exe (PID: 776)
- msp-agent-core.exe (PID: 4200)
- msp-agent-core-upgrade.exe (PID: 2332)
- msp-agent-core.exe (PID: 472)
- BASupSrvc.exe (PID: 6044)
- TCLauncherHelper.exe (PID: 7428)
Create files in a temporary directory
- LaudoBombeiro.EXE (PID: 4988)
- agent.exe (PID: 7288)
- agent.tmp (PID: 6760)
- agent.exe (PID: 684)
- vcredist_x86.exe (PID: 8044)
- agent.exe (PID: 3784)
- agent.exe (PID: 7308)
- agent.tmp (PID: 2108)
- LaudoBombeiro.EXE (PID: 6324)
Checks supported languages
- LaudoBombeiro.EXE (PID: 4988)
- agent.exe (PID: 7288)
- agent.tmp (PID: 5376)
- agent.exe (PID: 684)
- agent.tmp (PID: 6760)
- unzip.exe (PID: 7260)
- unzip.exe (PID: 7500)
- winagent.exe (PID: 6208)
- vcredist_x86.exe (PID: 8044)
- vcredist_x86.exe (PID: 7556)
- LaudoBombeiro.EXE (PID: 6324)
- agent.tmp (PID: 6740)
- agent.exe (PID: 7308)
- agent.exe (PID: 3784)
- agent.tmp (PID: 2108)
- msiexec.exe (PID: 5812)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7368)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
- winagent.exe (PID: 7876)
- msiexec.exe (PID: 7176)
- assetscan.exe (PID: 5952)
- winagent.exe (PID: 2240)
- winagent.exe (PID: 2908)
- msp-agent-core.exe (PID: 776)
- msp-agent-core.exe (PID: 684)
- msp-agent-core-upgrade.exe (PID: 6268)
- msp-agent-core-upgrade.exe (PID: 2332)
- msp-agent-core-upgrade.exe (PID: 5280)
- msp-agent-core.exe (PID: 472)
- BASupSrvc.exe (PID: 6044)
- ScriptRunner.Installer.exe (PID: 2908)
- TCLauncherHelper.exe (PID: 7428)
Process checks computer location settings
- LaudoBombeiro.EXE (PID: 4988)
- agent.tmp (PID: 5376)
- LaudoBombeiro.EXE (PID: 6324)
- agent.tmp (PID: 6740)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
Creates files in the program directory
- agent.tmp (PID: 6760)
- unzip.exe (PID: 7260)
- winagent.exe (PID: 6208)
- vcredist_x86.exe (PID: 8044)
- agent.tmp (PID: 2108)
- vcredist_x86.exe (PID: 7556)
- ScriptRunner.Installer.exe (PID: 2908)
- assetscan.exe (PID: 5952)
- unzip.exe (PID: 5008)
- winagent.exe (PID: 7876)
- msp-agent-core.exe (PID: 776)
- msp-agent-core-upgrade.exe (PID: 2332)
- msp-agent-core.exe (PID: 472)
- MSP_Connect.exe (PID: 3800)
- TCLauncherHelper.exe (PID: 7428)
Reads product name
- winagent.exe (PID: 6208)
- winagent.exe (PID: 7876)
- assetscan.exe (PID: 5952)
- winagent.exe (PID: 2240)
- winagent.exe (PID: 2908)
Reads Environment values
- winagent.exe (PID: 6208)
- winagent.exe (PID: 7876)
- assetscan.exe (PID: 5952)
- winagent.exe (PID: 2240)
- winagent.exe (PID: 2908)
Creates a software uninstall entry
- agent.tmp (PID: 6760)
- msiexec.exe (PID: 5812)
- agent.tmp (PID: 2108)
Checks proxy server information
- slui.exe (PID: 6456)
- vcredist_x86.exe (PID: 7556)
Manages system restore points
- SrTasks.exe (PID: 8108)
Reads the machine GUID from the registry
- vcredist_x86.exe (PID: 7556)
- msiexec.exe (PID: 5812)
- ScriptRunner.Installer.exe (PID: 2908)
- winagent.exe (PID: 7876)
- msp-agent-core.exe (PID: 776)
- msp-agent-core.exe (PID: 472)
- BASupSrvc.exe (PID: 6044)
- ScriptRunnerInstaller-2.98.1.1.exe (PID: 7500)
- TCLauncherHelper.exe (PID: 7428)
Creates files or folders in the user directory
- vcredist_x86.exe (PID: 7556)
- WerFault.exe (PID: 3016)
- WerFault.exe (PID: 8056)
The sample compiled with spanish language support
- msiexec.exe (PID: 5812)
The sample compiled with Italian language support
- msiexec.exe (PID: 5812)
The sample compiled with japanese language support
- msiexec.exe (PID: 5812)
The sample compiled with russian language support
- msiexec.exe (PID: 5812)
The sample compiled with french language support
- msiexec.exe (PID: 5812)
The sample compiled with korean language support
- msiexec.exe (PID: 5812)
Manual execution by a user
- Taskmgr.exe (PID: 780)
- Taskmgr.exe (PID: 668)
Reads Windows Product ID
- assetscan.exe (PID: 5952)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 668)
Drops encrypted JS script (Microsoft Script Encoder)
- msp-agent-core.exe (PID: 8080)
Checks operating system version
- msp-agent-core.exe (PID: 8080)
- msp-agent-core.exe (PID: 684)
- msp-agent-core.exe (PID: 4200)
- msp-agent-core.exe (PID: 776)
- msp-agent-core.exe (PID: 472)
The sample compiled with german language support
- msiexec.exe (PID: 5812)
The sample compiled with chinese language support
- msiexec.exe (PID: 5812)
Process checks whether UAC notifications are on
- TCLauncherHelper.exe (PID: 7428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
247
Monitored processes
100
Malicious processes
17
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | msp-agent-core-upgrade.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\Msp Agent\msp-agent-core.exe" | C:\Program Files (x86)\Msp Agent\msp-agent-core.exe | services.exe | ||||||||||||
User: SYSTEM Company: N-able Technologies, Ltd. Integrity Level: SYSTEM Description: N-able MSP Agent Core Modules
| |||||||||||||||
| 516 | cmd ver | C:\Windows\SysWOW64\cmd.exe | — | msp-agent-core.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\agent.exe" /SPAWNWND=$50242 /NOTIFYWND=$50238 /VERYSILENT /norestart | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\agent.exe | agent.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Advanced Monitoring Agent Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\MSP Agent\msp-agent-core.exe" --provisioning_state | C:\Program Files (x86)\Msp Agent\msp-agent-core.exe | — | winagent.exe | |||||||||||
User: SYSTEM Company: N-able Technologies, Ltd. Integrity Level: SYSTEM Description: N-able MSP Agent Core Exit code: 1 Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Msp Agent\msp-agent-core.exe" | C:\Program Files (x86)\Msp Agent\msp-agent-core.exe | services.exe | ||||||||||||
User: SYSTEM Company: N-able Technologies, Ltd. Integrity Level: SYSTEM Description: N-able MSP Agent Core Exit code: 0 Modules
| |||||||||||||||
| 780 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
93 156
Read events
91 259
Write events
1 817
Delete events
80
Modification events
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000CF50DF3196AFDB01 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (7580) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
Executable files
354
Suspicious files
618
Text files
194
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c45b.TMP | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c46b.TMP | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c46b.TMP | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c46b.TMP | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c46b.TMP | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7580 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
111
DNS requests
96
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5772 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5772 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7176 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5772 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5772 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
5772 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5772 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5772 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7580 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 162.125.66.18:443 | www.dropbox.com | DROPBOX | DE | whitelisted |
— | — | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.dropbox.com |
| whitelisted |
accounts.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
cfl.dropboxstatic.com |
| whitelisted |
assets.dropbox.com |
| whitelisted |
www.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |
2196 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |
2196 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |
2196 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query for Suspicious TLD (.management) |