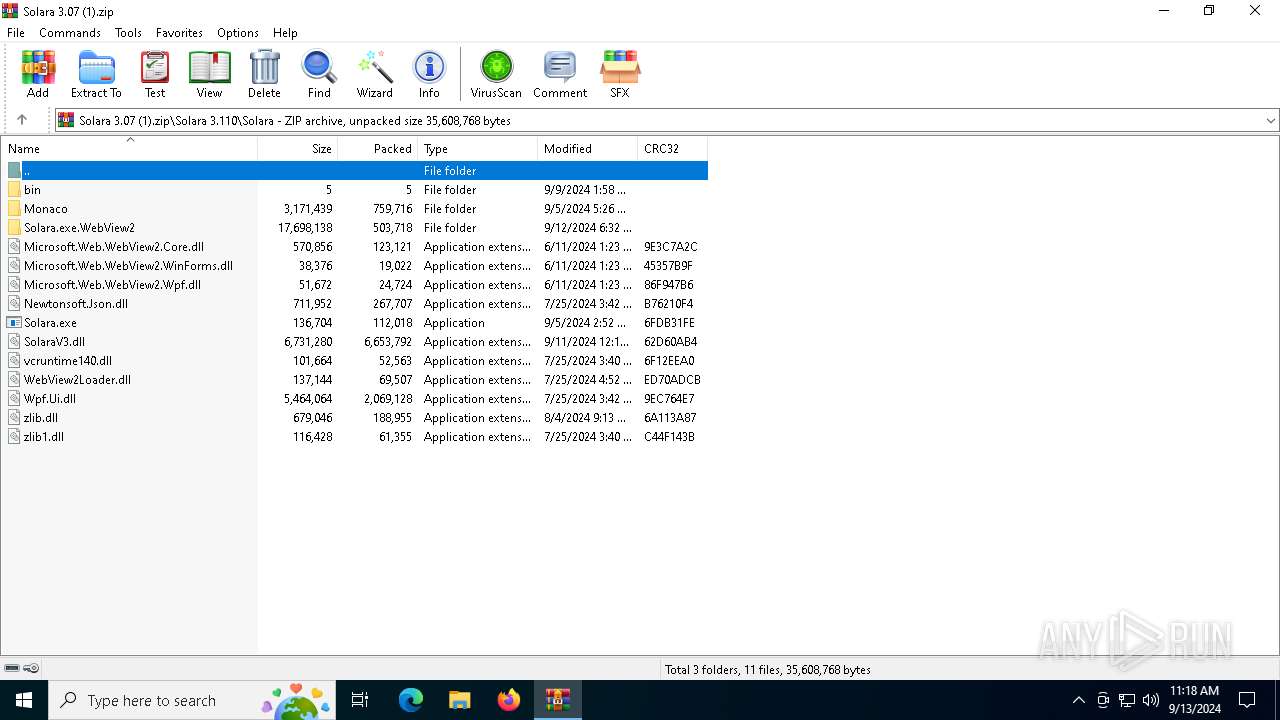
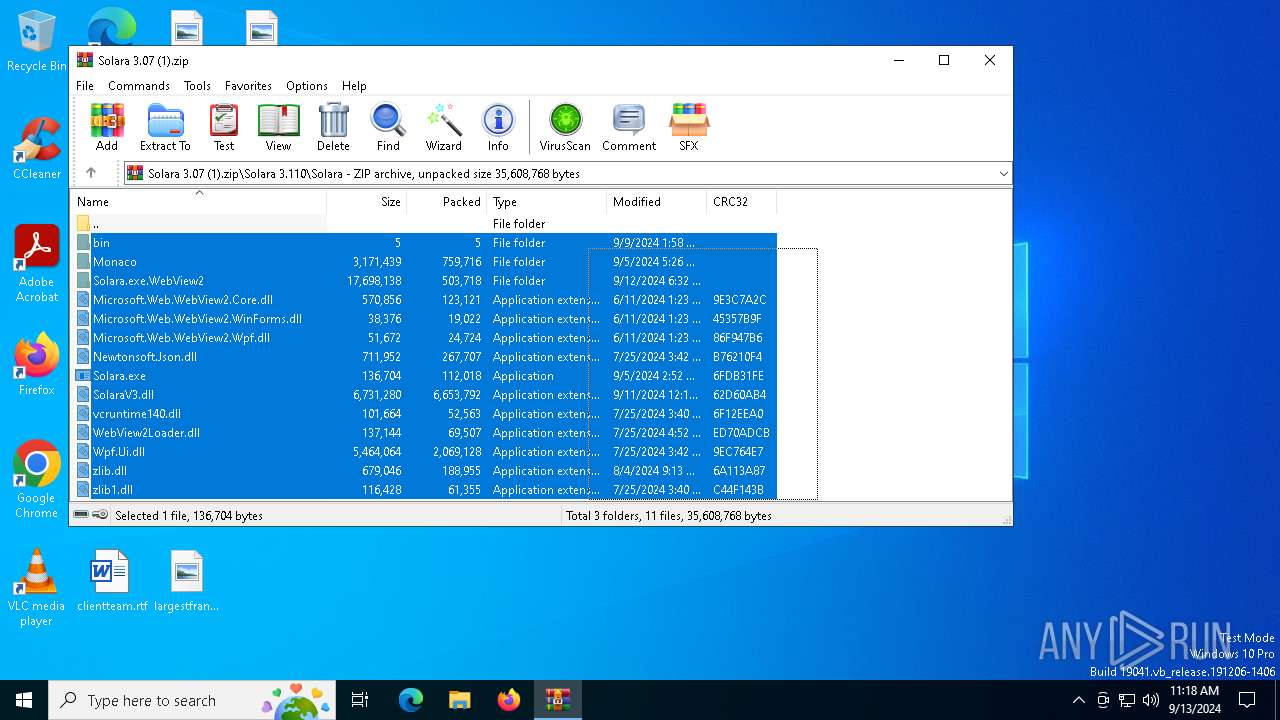
| File name: | Solara 3.07 (1).zip |
| Full analysis: | https://app.any.run/tasks/4c20e970-28a3-4a6c-afa8-91e62a8f6572 |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 11:18:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 9354A65DBFB6953AD01BE6CFFE5740F4 |
| SHA1: | EF73FD4D4BD511449FB2DB15F255FB92C1D25E3F |
| SHA256: | E28AC1C19529E863C0F1647B9C684EAAD0E9F809DFBD4E4199B7E275EA5B52EF |
| SSDEEP: | 98304:lKo9hvbuXScA3JpmGQ8HnFHWtJXIapOUlqcERLodC63smXYl06MV0cAOOi1xm3kW:UlHlNjB+THQx5+1laW5 |
MALICIOUS
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 5492)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6844)
- MicrosoftEdgeUpdate.exe (PID: 5492)
Executes application which crashes
- Solara.exe (PID: 3236)
Executable content was dropped or overwritten
- RobloxPlayerInstaller.exe (PID: 5344)
- MicrosoftEdgeWebview2Setup.exe (PID: 4252)
- MicrosoftEdgeUpdate.exe (PID: 5492)
Changes default file association
- RobloxPlayerInstaller.exe (PID: 5344)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 5492)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7188)
- MicrosoftEdgeUpdate.exe (PID: 7184)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 876)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7624)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 5492)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2056)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6844)
- msedge.exe (PID: 3880)
- msedge.exe (PID: 2992)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6844)
- msedge.exe (PID: 2992)
- msedge.exe (PID: 7676)
Reads the computer name
- Solara.exe (PID: 3236)
- identity_helper.exe (PID: 7472)
- RobloxPlayerInstaller.exe (PID: 5344)
- MicrosoftEdgeUpdate.exe (PID: 5492)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7188)
- MicrosoftEdgeUpdate.exe (PID: 7184)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 876)
- MicrosoftEdgeUpdate.exe (PID: 4668)
- MicrosoftEdgeUpdate.exe (PID: 7636)
- MicrosoftEdgeUpdate.exe (PID: 3876)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7624)
Reads the software policy settings
- Solara.exe (PID: 3236)
- WerFault.exe (PID: 360)
- MicrosoftEdgeUpdate.exe (PID: 4668)
- MicrosoftEdgeUpdate.exe (PID: 3876)
Checks proxy server information
- Solara.exe (PID: 3236)
- WerFault.exe (PID: 360)
- MicrosoftEdgeUpdate.exe (PID: 4668)
- MicrosoftEdgeUpdate.exe (PID: 3876)
Disables trace logs
- Solara.exe (PID: 3236)
Checks supported languages
- Solara.exe (PID: 3236)
- identity_helper.exe (PID: 7472)
- RobloxPlayerInstaller.exe (PID: 5344)
- MicrosoftEdgeWebview2Setup.exe (PID: 4252)
- MicrosoftEdgeUpdate.exe (PID: 5492)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7188)
- MicrosoftEdgeUpdate.exe (PID: 4668)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 876)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7624)
- MicrosoftEdgeUpdate.exe (PID: 7184)
- MicrosoftEdgeUpdate.exe (PID: 7636)
- MicrosoftEdgeUpdate.exe (PID: 3876)
Creates files or folders in the user directory
- WerFault.exe (PID: 360)
- RobloxPlayerInstaller.exe (PID: 5344)
- MicrosoftEdgeUpdate.exe (PID: 5492)
Reads the machine GUID from the registry
- Solara.exe (PID: 3236)
- RobloxPlayerInstaller.exe (PID: 5344)
Manual execution by a user
- msedge.exe (PID: 2992)
Reads Environment values
- Solara.exe (PID: 3236)
- identity_helper.exe (PID: 7472)
- MicrosoftEdgeUpdate.exe (PID: 4668)
Sends debugging messages
- msedge.exe (PID: 320)
- RobloxPlayerInstaller.exe (PID: 5344)
Application launched itself
- msedge.exe (PID: 2992)
Create files in a temporary directory
- svchost.exe (PID: 2056)
- RobloxPlayerInstaller.exe (PID: 5344)
- MicrosoftEdgeWebview2Setup.exe (PID: 4252)
- MicrosoftEdgeUpdate.exe (PID: 5492)
Process checks whether UAC notifications are on
- RobloxPlayerInstaller.exe (PID: 5344)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 5492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:12 21:32:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Solara 3.110/ |
Total processes
218
Monitored processes
88
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5640 --field-trial-handle=2460,i,16832268484742517519,15523285669590367051,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --no-appcompat-clear --mojo-platform-channel-handle=6440 --field-trial-handle=2460,i,16832268484742517519,15523285669590367051,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 320 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x2f8,0x310,0x7fffd36b5fd8,0x7fffd36b5fe4,0x7fffd36b5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 360 | C:\WINDOWS\system32\WerFault.exe -u -p 3236 -s 1800 | C:\Windows\System32\WerFault.exe | Solara.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.171.39\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.171.39\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.171.39 Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2788 --field-trial-handle=2460,i,16832268484742517519,15523285669590367051,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1172 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6312 --field-trial-handle=2460,i,16832268484742517519,15523285669590367051,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1992 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=57 --mojo-platform-channel-handle=7764 --field-trial-handle=2460,i,16832268484742517519,15523285669590367051,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2056 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s BITS | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2452 --field-trial-handle=2460,i,16832268484742517519,15523285669590367051,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
22 270
Read events
21 267
Write events
951
Delete events
52
Modification events
| (PID) Process: | (6844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Solara 3.07 (1).zip | |||
| (PID) Process: | (6844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6844) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3236) Solara.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Solara_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3236) Solara.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Solara_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3236) Solara.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Solara_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3236) Solara.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Solara_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
220
Suspicious files
1 439
Text files
568
Unknown types
45
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Microsoft.Web.WebView2.Core.dll | executable | |
MD5:B037CA44FD19B8EEDB6D5B9DE3E48469 | SHA256:11E88B2CA921E5C88F64567F11BD83CBC396C10365D40972F3359FCC7965D197 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\bin\version.txt | text | |
MD5:1087F46B6FE067D6674D8B7787EB8EF6 | SHA256:7C8BC82D3AFEAF6167DB5B64BA2006C99617200C4DA73657D0EF81705C6E7E29 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Microsoft.Web.WebView2.Wpf.dll | executable | |
MD5:E107C88A6FC54CC3CEB4D85768374074 | SHA256:8F821F0C818F8D817B82F76C25F90FDE9FB73FF1AE99C3DF3EAF2B955653C9C8 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Monaco\fileaccess\node_modules\accepts\package.json | binary | |
MD5:32A15D6909FCAE63E52D8664593D32D5 | SHA256:E5716D5D939DB08C5C28EC6AE86ED67BE5320F91089E2673FCA1C5B876E57AA3 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Monaco\fileaccess\node_modules\array-flatten\package.json | binary | |
MD5:CB1AA7F817100A03395DD0163BF6EBE9 | SHA256:5C5E0E10CFA23F163D1FE68AA57A881D09CAC39D720E1361C697B86C4D33E0F5 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Monaco\fileaccess\node_modules\body-parser\lib\read.js | text | |
MD5:C148BB38C59CE266E271C96AB1F2D192 | SHA256:1E9E274755366C39AE70E8B9A7A42FC12219566E67EFAF9B7EBC2A8B337F5B6B | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Monaco\fileaccess\node_modules\body-parser\index.js | text | |
MD5:B9E991C0E57C4D5ADDE68A2F4F063BC7 | SHA256:9C6C900E7E85FB599C62D9B9E4DFD2EA2F61D119DCE5ED69AC3A8DA828819241 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Monaco\fileaccess\node_modules\accepts\index.js | binary | |
MD5:4FE4D2C90A2FD19D6E97443A7D24F815 | SHA256:BE2DECBD50610E8F995C1E312EE4DD6D7C1244CFDF03EE4C4A3DA68E572DADA1 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Monaco\fileaccess\node_modules\body-parser\lib\types\raw.js | text | |
MD5:ACB38E4FE575AFAF8D1A257E47C6E362 | SHA256:4E9CC80A7EE8BD667C68C264B4C374B28E731246DDB6EC22C3968DAF837E30A2 | |||
| 6844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6844.11532\Solara 3.110\Solara\Monaco\fileaccess\index.js | text | |
MD5:0E709BFB5675FF0531C925B909B58008 | SHA256:ED94FD8980C043BAD99599102291E3285323B99CE0EB5D424C00E3DEA1A34E67 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
241
DNS requests
344
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6056 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1764 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
360 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2612 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2612 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2056 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1726551324&P2=404&P3=2&P4=EeAltj09IVbfh56mshsxn7BcIT4%2b7d1t83rgtbTsFPblJo2qFzhn2CYiJfuu4plHw7N2wLcU1ojpI19T0OjGDw%3d%3d | unknown | — | — | whitelisted |
2056 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1726551324&P2=404&P3=2&P4=EeAltj09IVbfh56mshsxn7BcIT4%2b7d1t83rgtbTsFPblJo2qFzhn2CYiJfuu4plHw7N2wLcU1ojpI19T0OjGDw%3d%3d | unknown | — | — | whitelisted |
2056 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1726551324&P2=404&P3=2&P4=EeAltj09IVbfh56mshsxn7BcIT4%2b7d1t83rgtbTsFPblJo2qFzhn2CYiJfuu4plHw7N2wLcU1ojpI19T0OjGDw%3d%3d | unknown | — | — | whitelisted |
2056 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1726551324&P2=404&P3=2&P4=EeAltj09IVbfh56mshsxn7BcIT4%2b7d1t83rgtbTsFPblJo2qFzhn2CYiJfuu4plHw7N2wLcU1ojpI19T0OjGDw%3d%3d | unknown | — | — | whitelisted |
2056 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1726551324&P2=404&P3=2&P4=EeAltj09IVbfh56mshsxn7BcIT4%2b7d1t83rgtbTsFPblJo2qFzhn2CYiJfuu4plHw7N2wLcU1ojpI19T0OjGDw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6056 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
736 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6056 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6056 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3236 | Solara.exe | 172.67.19.24:443 | pastebin.com | CLOUDFLARENET | US | shared |
3236 | Solara.exe | 128.116.123.3:443 | clientsettings.roblox.com | ROBLOX-PRODUCTION | US | whitelisted |
1764 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
pastebin.com |
| shared |
clientsettings.roblox.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
6168 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
Process | Message |
|---|---|
msedge.exe | [0913/111919.431:WARNING:device_ticket.cc(151)] Timed out waiting for device ticket. Canceling async operation.
|
msedge.exe | [0913/111919.431:ERROR:device_ticket.cc(187)] The identity is null.
|
msedge.exe | [0913/111920.525:ERROR:process_memory_win.cc(74)] ReadMemory at 0x7ff6278d0000 of 64 bytes failed: Only part of a ReadProcessMemory or WriteProcessMemory request was completed. (0x12B)
|
msedge.exe | [0913/111920.526:WARNING:pe_image_reader.cc(340)] could not read dos header from C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe
|
msedge.exe | [0913/111920.526:ERROR:process_memory_win.cc(74)] ReadMemory at 0x7ffff85f0000 of 64 bytes failed: Only part of a ReadProcessMemory or WriteProcessMemory request was completed. (0x12B)
|
msedge.exe | [0913/111920.526:WARNING:pe_image_reader.cc(340)] could not read dos header from C:\WINDOWS\SYSTEM32\ntdll.dll
|
msedge.exe | [0913/111920.526:ERROR:process_memory_win.cc(74)] ReadMemory at 0x7ffff6f10000 of 64 bytes failed: Only part of a ReadProcessMemory or WriteProcessMemory request was completed. (0x12B)
|
msedge.exe | [0913/111920.526:WARNING:pe_image_reader.cc(340)] could not read dos header from C:\WINDOWS\System32\KERNEL32.DLL
|
msedge.exe | [0913/111920.526:ERROR:process_memory_win.cc(74)] ReadMemory at 0x7ffff5da0000 of 64 bytes failed: Only part of a ReadProcessMemory or WriteProcessMemory request was completed. (0x12B)
|
msedge.exe | [0913/111920.526:WARNING:pe_image_reader.cc(340)] could not read dos header from C:\WINDOWS\System32\KERNELBASE.dll
|