| File name: | crackmes.txt |
| Full analysis: | https://app.any.run/tasks/a8fa0d10-2736-4160-b1f5-af2ab9e92d1a |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 12:10:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-c |
| File info: | C source, UTF-8 Unicode text |
| MD5: | AFA075CF26BA1B0A6E87D816E7D2CDC0 |
| SHA1: | 05D5579F7D44043C2A58098BD4986A8C6BFAF24B |
| SHA256: | E27F6BA4EA978D315831D02FD427C664077ABC09ECB6AF3765E4732AE44732B0 |
| SSDEEP: | 24:qXPpDuPY2BCrm4mOKSsGe89T9u+rxrc90qOUzRwsMZp4DyUHN+SwsWQ:qOY2BCrm4mOKl89TcgcRznJKQ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Creates files in the user directory
- opera.exe (PID: 748)
Reads settings of System Certificates
- chrome.exe (PID: 316)
Reads Internet Cache Settings
- chrome.exe (PID: 316)
Application launched itself
- chrome.exe (PID: 316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=888,16735710460205270002,7706291803063756010,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5799FE6FBF1487E59F874005B0FE8A15 --mojo-platform-channel-handle=4068 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=888,16735710460205270002,7706291803063756010,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=18EF663FFDB880F0423A6D01C08E6D7E --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18EF663FFDB880F0423A6D01C08E6D7E --renderer-client-id=7 --mojo-platform-channel-handle=3792 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=888,16735710460205270002,7706291803063756010,131072 --enable-features=PasswordImport --service-pipe-token=39ECD26C0C7CED01821DECA6334CB58C --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=39ECD26C0C7CED01821DECA6334CB58C --renderer-client-id=3 --mojo-platform-channel-handle=2120 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=888,16735710460205270002,7706291803063756010,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=C4354893C9750D9D350FBDF6F85D6225 --mojo-platform-channel-handle=4156 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=888,16735710460205270002,7706291803063756010,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=6E44BA82A94F37C4AA8D35FC209574A3 --mojo-platform-channel-handle=3828 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x70fe00b0,0x70fe00c0,0x70fe00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2948 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\crackmes.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=888,16735710460205270002,7706291803063756010,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=7774AF4CDCCDBC46A440F3818F2C1E90 --mojo-platform-channel-handle=912 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
1 443
Read events
1 201
Write events
237
Delete events
5
Modification events
| (PID) Process: | (2948) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 132 | |||
| (PID) Process: | (2948) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 132 | |||
| (PID) Process: | (2948) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (2948) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
| (PID) Process: | (748) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe | |||
| (PID) Process: | (748) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (316) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (316) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (316) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3928) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 316-13194360773394765 |
Value: 259 | |||
Executable files
0
Suspicious files
94
Text files
92
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr886A.tmp | — | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr88AA.tmp | — | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr0000V.tmp | — | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GO0ZFNXCJ7DW0KERAU0Q.temp | — | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprA088.tmp | — | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr4526.tmp | — | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr50EE.tmp | — | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\global_history.dat | text | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\dcache4.url | binary | |
MD5:— | SHA256:— | |||
| 748 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\08QMOF0DVT5O2U7EYENQ.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
29
DNS requests
21
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
748 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
748 | opera.exe | GET | 200 | 172.217.23.174:80 | http://clients1.google.com/complete/search?q=ipl&client=opera-suggest-omnibox&hl=de | US | text | 103 b | whitelisted |
748 | opera.exe | GET | 200 | 172.217.23.174:80 | http://clients1.google.com/complete/search?q=iplogger&client=opera-suggest-omnibox&hl=de | US | text | 110 b | whitelisted |
748 | opera.exe | GET | 200 | 104.16.92.188:80 | http://crl.comodoca.com/COMODORSACertificationAuthority.crl | US | der | 818 b | whitelisted |
748 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAOXQPQlVpLtFek%2BmcpabOk%3D | US | der | 471 b | whitelisted |
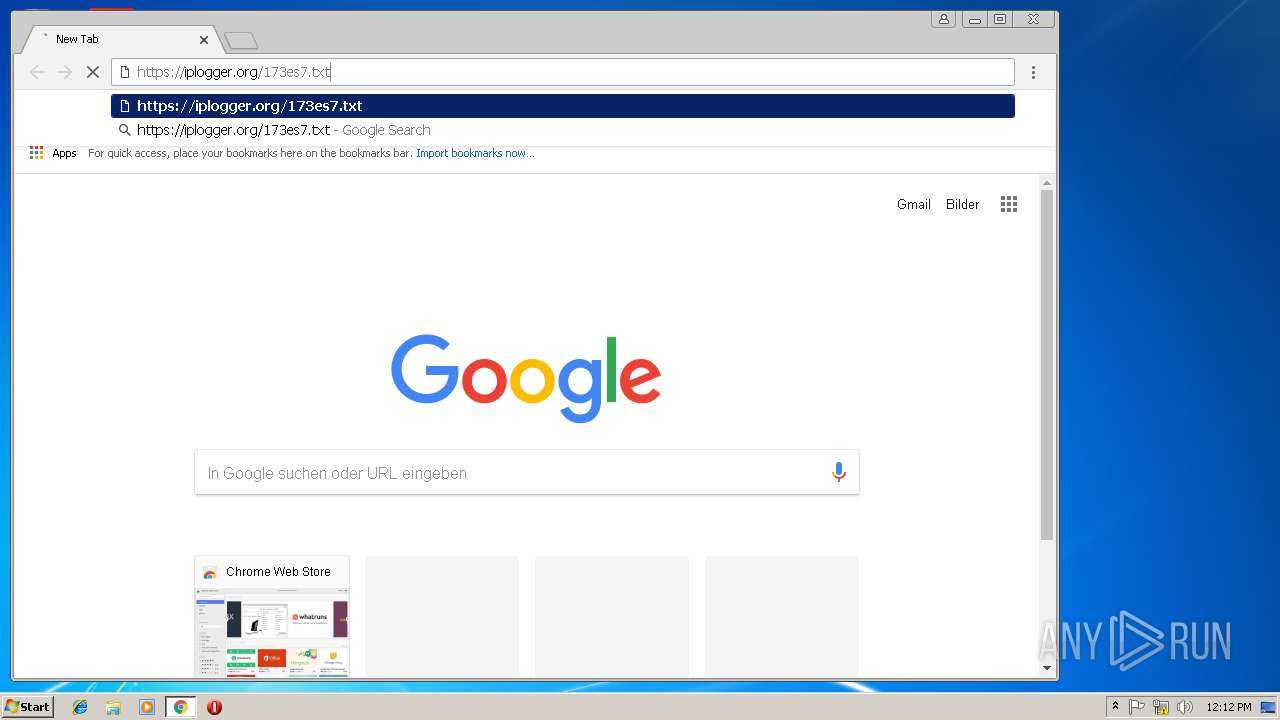
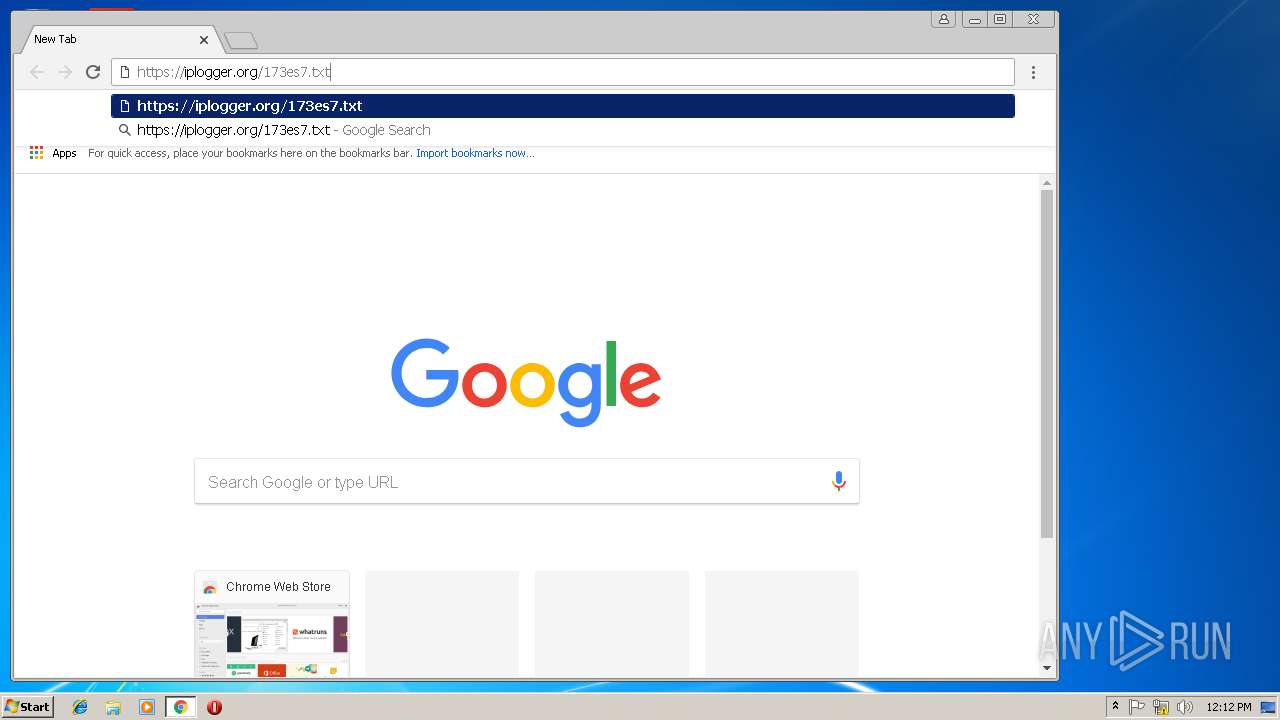
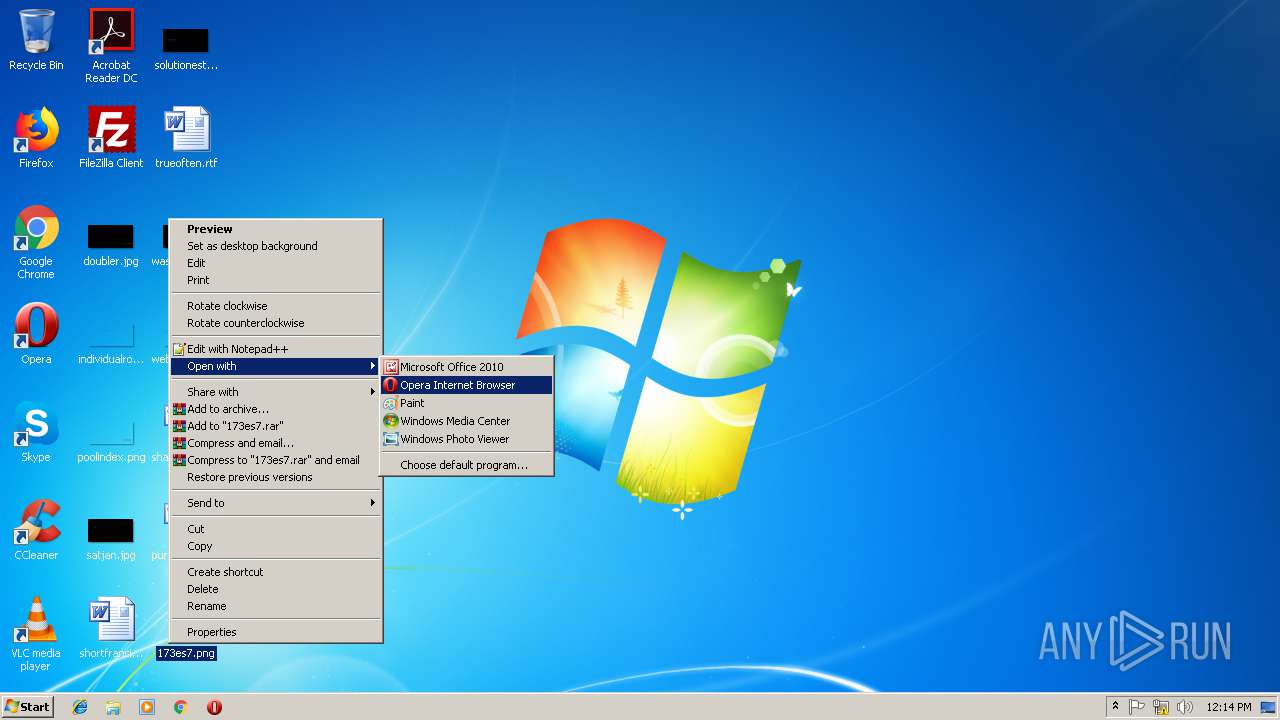
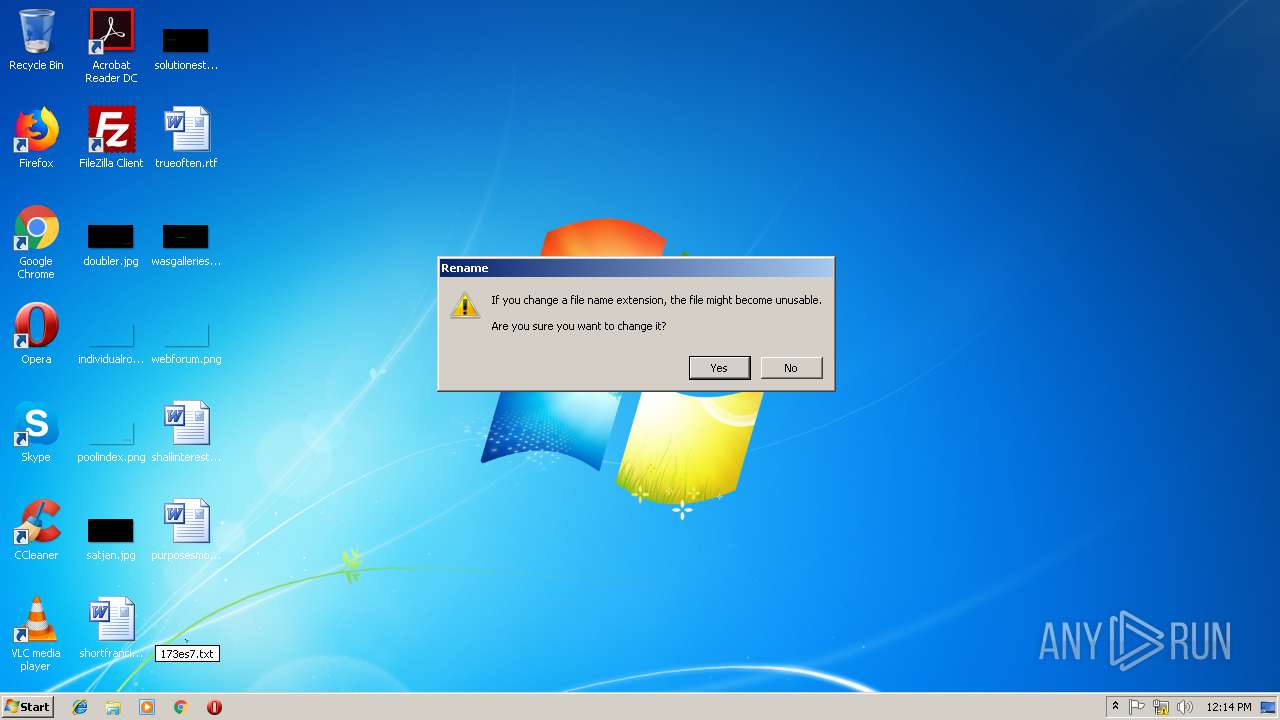
748 | opera.exe | GET | 301 | 88.99.66.31:80 | http://iplogger.org/173es7.txt | DE | html | 178 b | shared |
748 | opera.exe | GET | 400 | 185.26.182.112:80 | http://sitecheck2.opera.com/?host=iplogger.org&hdn=v2f3ETtwIf5etKJ2aHlvYg== | unknown | html | 166 b | whitelisted |
748 | opera.exe | GET | 200 | 104.17.104.175:80 | http://crl.usertrust.com/AddTrustExternalCARoot.crl | US | der | 612 b | whitelisted |
748 | opera.exe | GET | 200 | 2.16.106.50:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpRaC9iQ6hJWc99DtDoo2ucCEQD%2BofQtYJP0vg6JS%2B4x27Bg | unknown | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
748 | opera.exe | 82.145.215.40:443 | certs.opera.com | Opera Software AS | — | whitelisted |
748 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
748 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
748 | opera.exe | 172.217.23.174:80 | clients1.google.com | Google Inc. | US | whitelisted |
748 | opera.exe | 88.99.66.31:80 | iplogger.org | Hetzner Online GmbH | DE | malicious |
748 | opera.exe | 185.26.182.112:80 | sitecheck2.opera.com | Opera Software AS | — | malicious |
748 | opera.exe | 88.99.66.31:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
748 | opera.exe | 104.16.92.188:80 | crl.comodoca.com | Cloudflare Inc | US | shared |
748 | opera.exe | 104.17.104.175:80 | crl.usertrust.com | Cloudflare Inc | US | shared |
748 | opera.exe | 2.16.106.50:80 | ocsp.comodoca.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
clients1.google.com |
| whitelisted |
iplogger.org |
| shared |
sitecheck2.opera.com |
| whitelisted |
crl.usertrust.com |
| whitelisted |
crl.comodoca.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
5 ETPRO signatures available at the full report