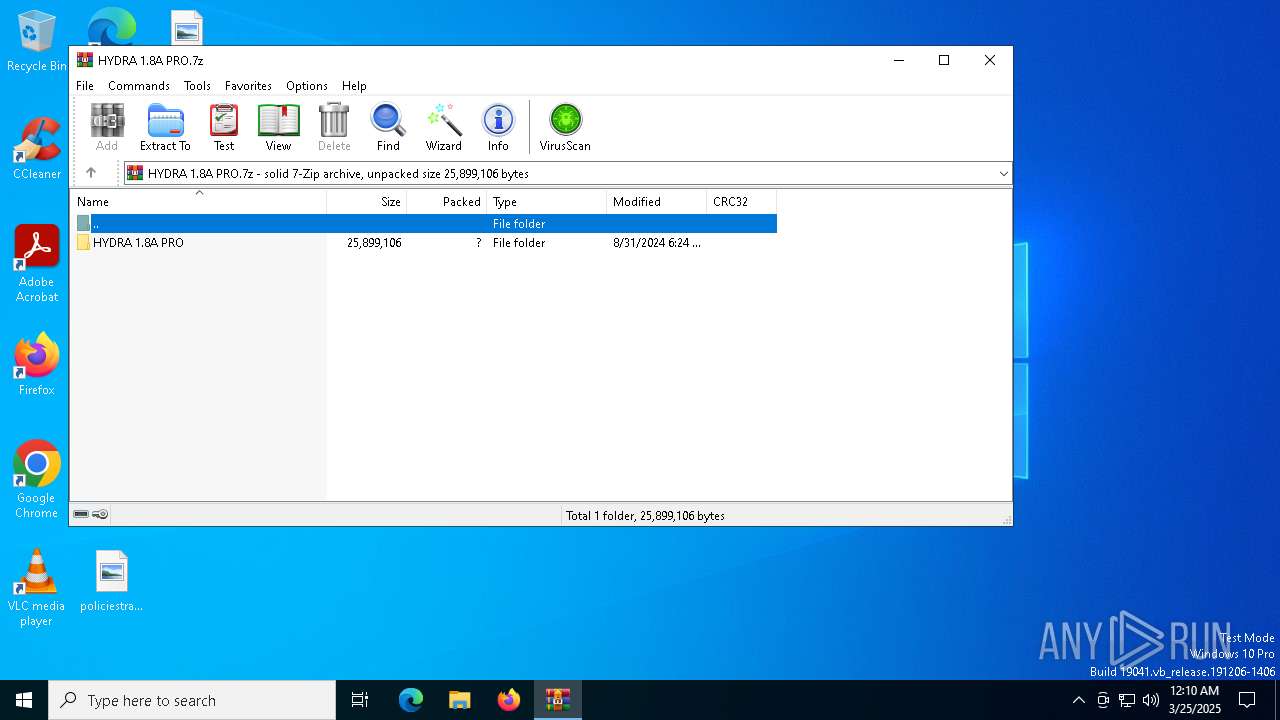
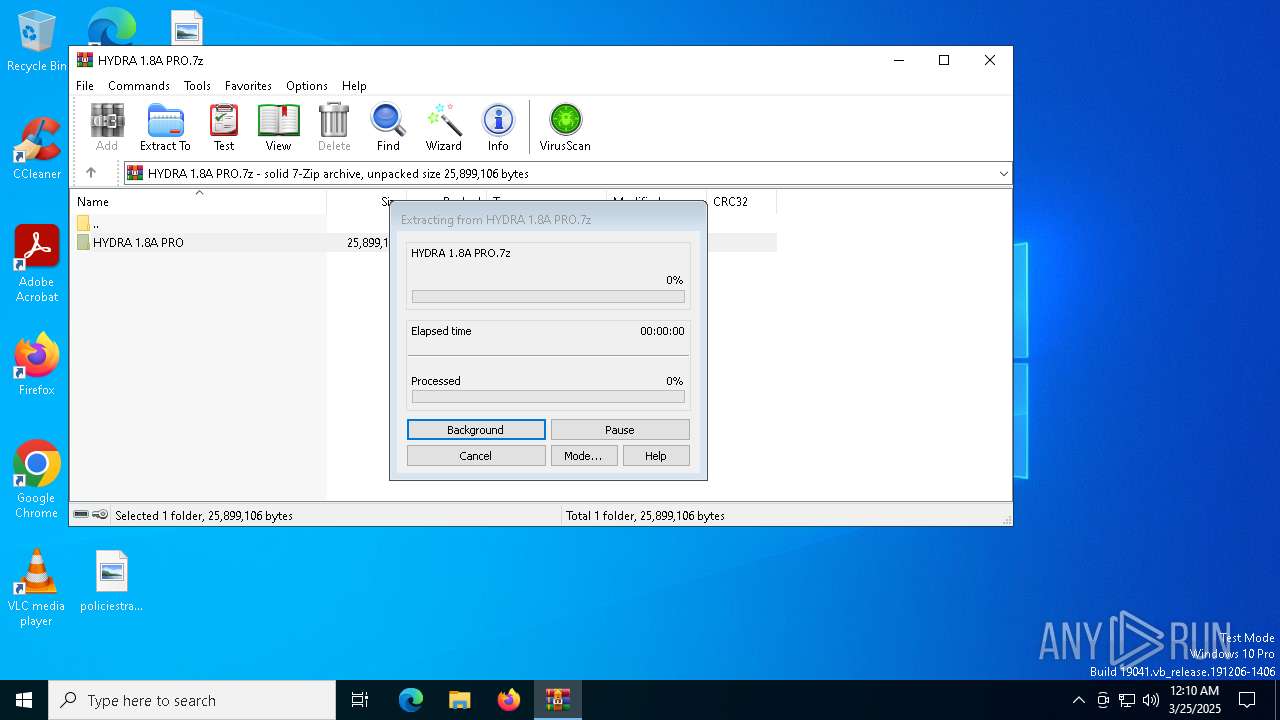
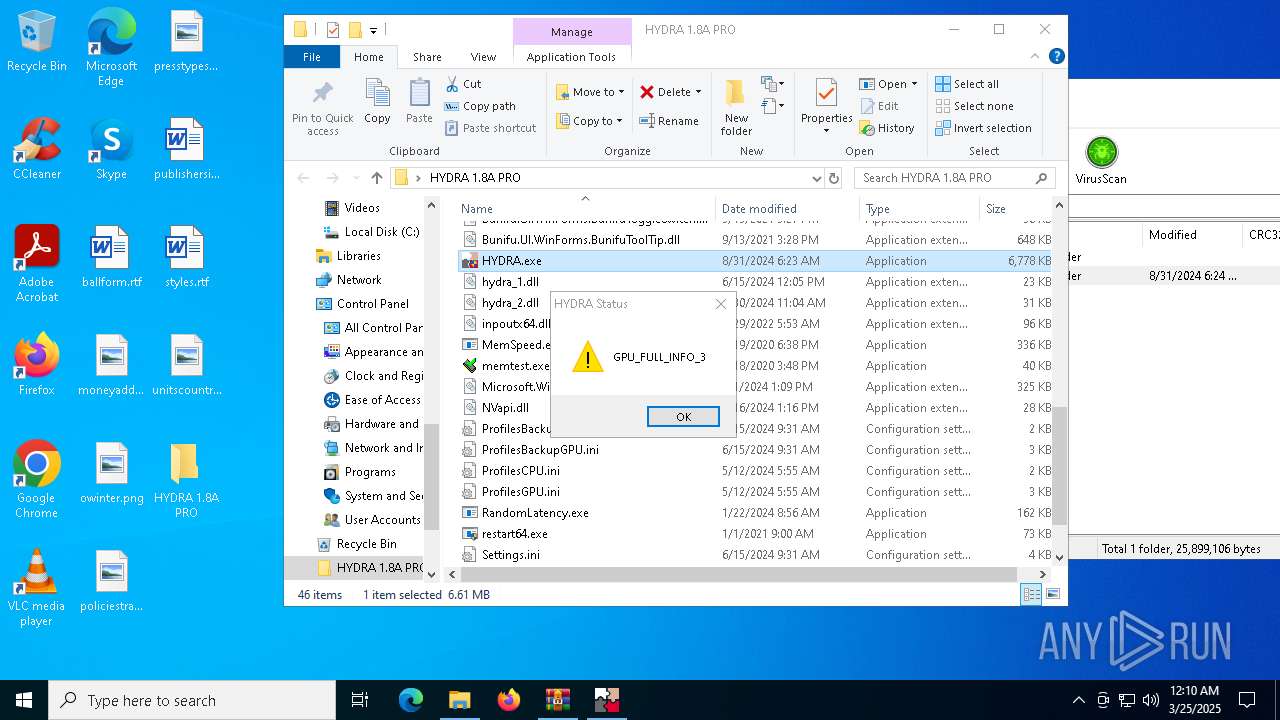
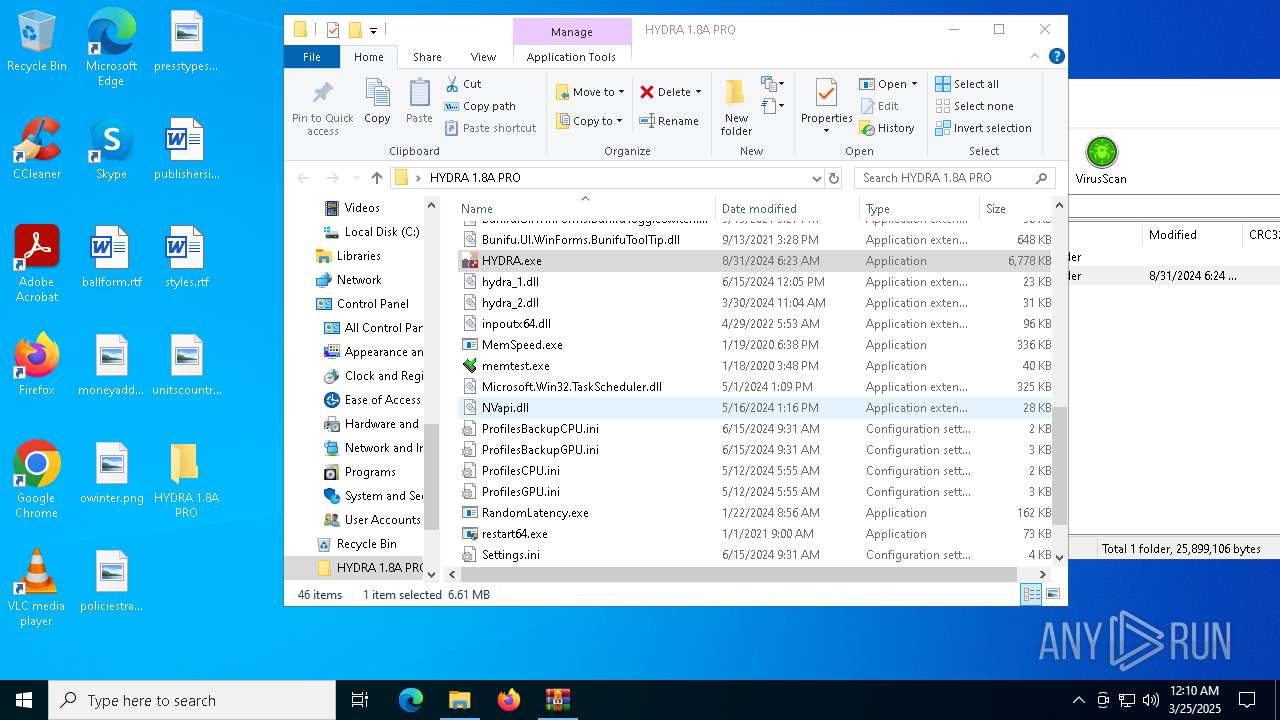
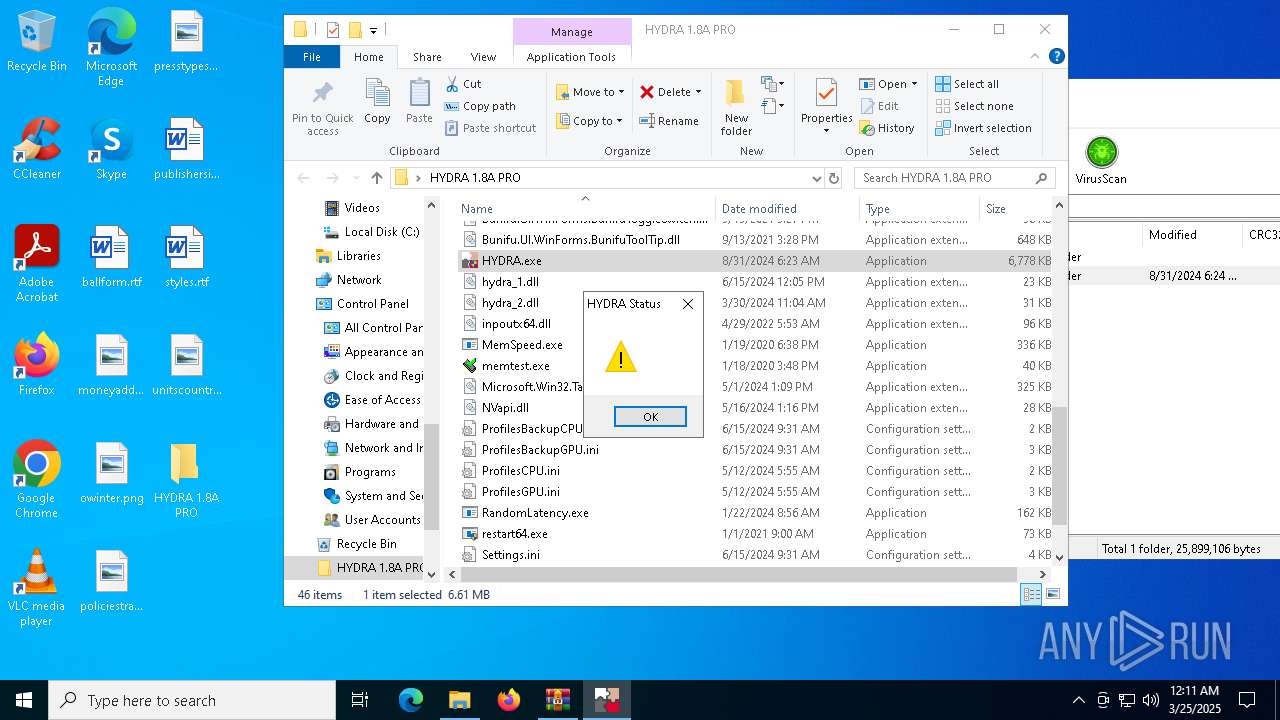
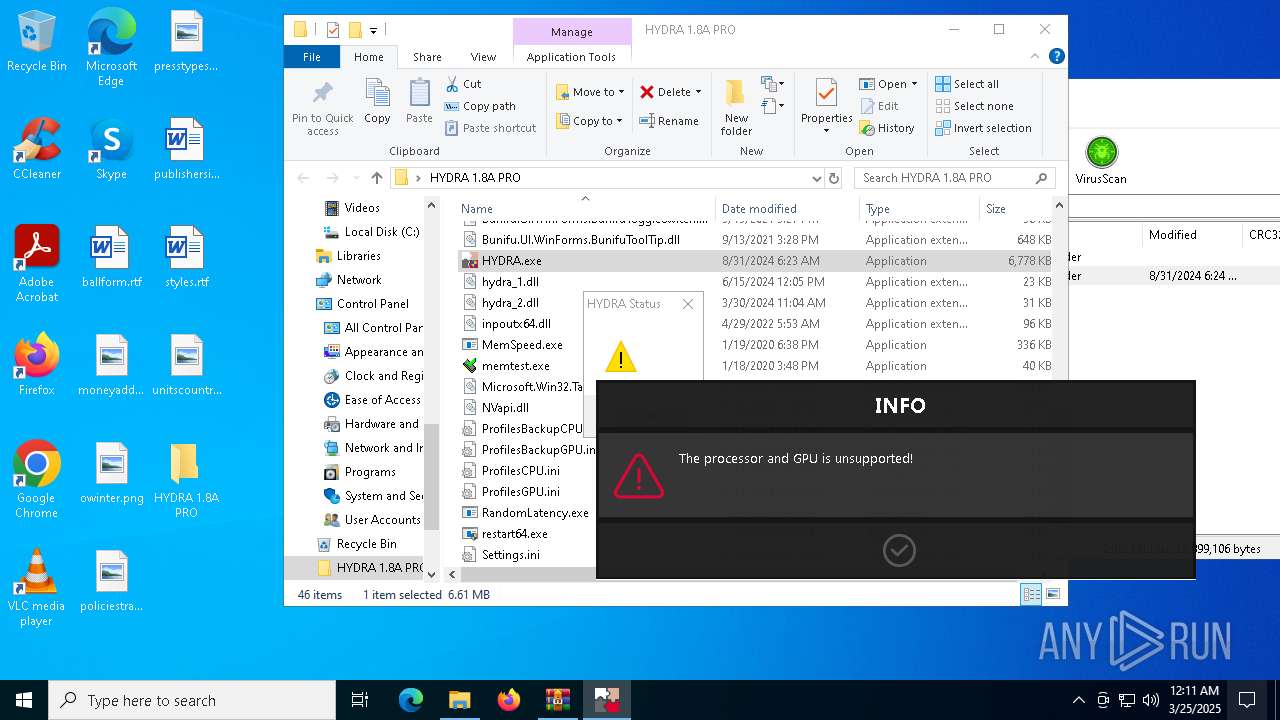
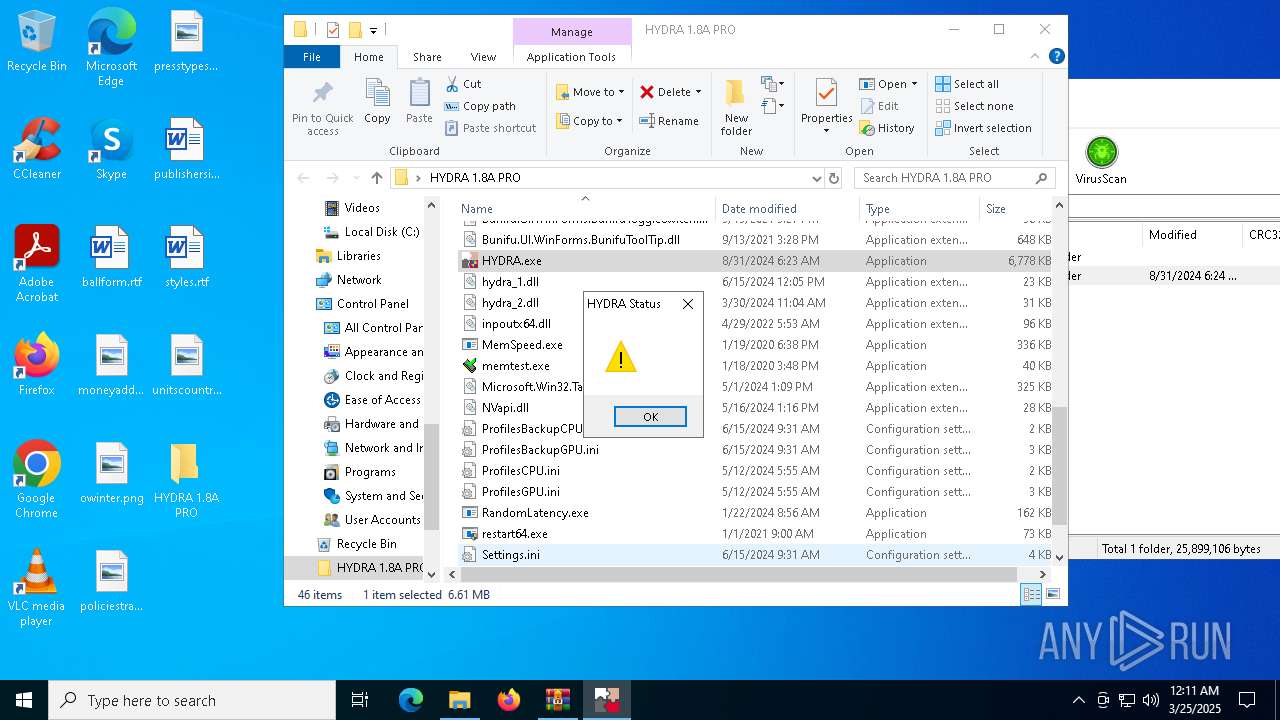
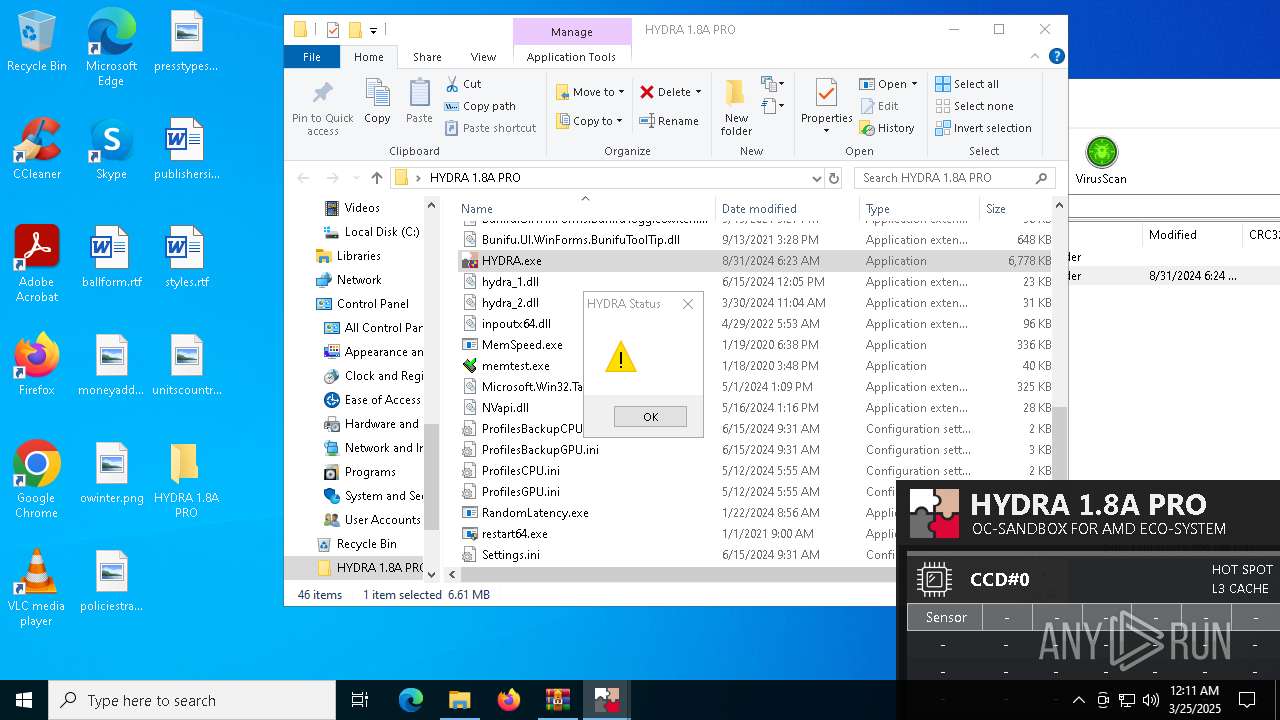
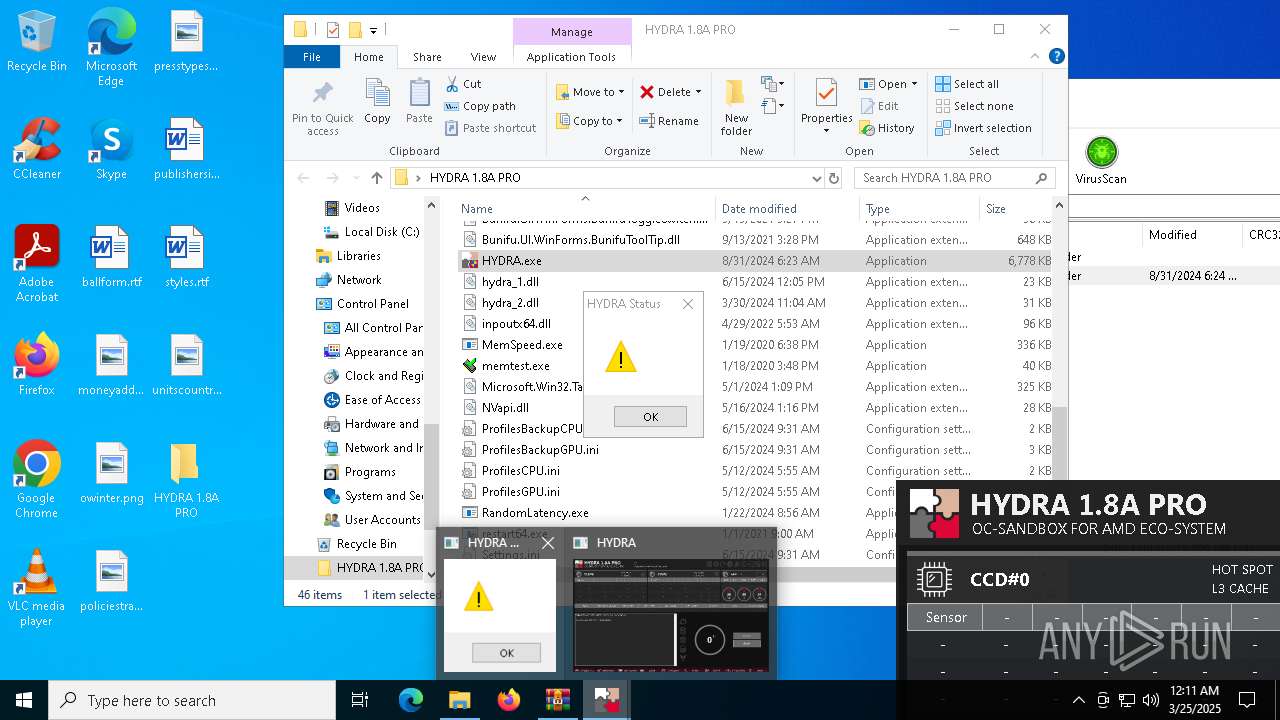
| File name: | HYDRA 1.8A PRO.7z |
| Full analysis: | https://app.any.run/tasks/be09e059-7290-4d72-9684-57e358dd84f3 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 00:10:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | AA96A11ABE1AE2735B92C2CA6EF954F9 |
| SHA1: | 99B6281B3624DDE990CD87A1DA7D8FC72BE0F46B |
| SHA256: | E26320635EE9A0E19F4019C29D6437784D4DE38564348BEDB49F992BA8EF6BDD |
| SSDEEP: | 98304:TL86LrScbzPLAjqgPc6fQFXB3NTopjETVxsU4kvoqYaXB6D7NNt0GSxfgJKjH8rH:e61vZ9+f5B |
MALICIOUS
Vulnerable driver has been detected
- WinRAR.exe (PID: 7412)
Changes powershell execution policy (Bypass)
- HYDRA.exe (PID: 7300)
Bypass execution policy to execute commands
- powershell.exe (PID: 6516)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 7412)
- HYDRA.exe (PID: 7300)
Creates files in the driver directory
- HYDRA.exe (PID: 7300)
Executable content was dropped or overwritten
- HYDRA.exe (PID: 7300)
Starts POWERSHELL.EXE for commands execution
- HYDRA.exe (PID: 7300)
The process bypasses the loading of PowerShell profile settings
- HYDRA.exe (PID: 7300)
Uses powercfg.exe to modify the power settings
- HYDRA.exe (PID: 7300)
Executes as Windows Service
- WmiApSrv.exe (PID: 7236)
The process checks if it is being run in the virtual environment
- HYDRA.exe (PID: 7300)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7412)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7412)
The sample compiled with japanese language support
- WinRAR.exe (PID: 7412)
Reads the computer name
- HYDRA.exe (PID: 7300)
Checks supported languages
- HYDRA.exe (PID: 7300)
Reads the machine GUID from the registry
- HYDRA.exe (PID: 7300)
Manual execution by a user
- HYDRA.exe (PID: 8176)
- HYDRA.exe (PID: 7300)
Reads the time zone
- HYDRA.exe (PID: 7300)
Reads CPU info
- HYDRA.exe (PID: 7300)
Reads the software policy settings
- slui.exe (PID: 7632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:08:31 06:24:12+00:00 |
| ArchivedFileName: | HYDRA 1.8A PRO |
Total processes
184
Monitored processes
48
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "powercfg.exe" /duplicatescheme 381b4222-f694-41f0-9685-ff5bb260df2e | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "powercfg.exe" /setacvalueindex be3e1c98-d25e-41e7-8169-c25c68351d83 54533251-82be-4824-96c1-47b60b740d00 bae08b81-2d5e-4688-ad6a-13243356654b 0x00000001 | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "powercfg.exe" /setacvalueindex be3e1c98-d25e-41e7-8169-c25c68351d83 54533251-82be-4824-96c1-47b60b740d00 3b04d4fd-1cc7-4f23-ab1c-d1337819c4bb 0x00000000 | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "powercfg.exe" /restoredefaultschemes | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | "powercfg.exe" /l | C:\Windows\System32\powercfg.exe | — | HYDRA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 172
Read events
10 804
Write events
199
Delete events
169
Modification events
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HYDRA 1.8A PRO.7z | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7412) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5508) lodctr.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET CLR Data\Performance |
| Operation: | delete value | Name: | First Counter |
Value: ᪸ | |||
| (PID) Process: | (5508) lodctr.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\.NET CLR Data\Performance |
| Operation: | delete value | Name: | Last Counter |
Value: ᫄ | |||
Executable files
45
Suspicious files
4
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\amdvbflash\AMDVBFLASH_User_Guide_NDA.pdf | ||
MD5:F4A483489567D6B10B6A2A884205DA5D | SHA256:A2463E61CE763447111A7EF97C6ED424E1921C5CA4F75F827E078238F23FAB93 | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\amdvbflash\readme.txt | text | |
MD5:B60613CA7DBE272CEC714088DC518682 | SHA256:30FFC0A7B1E00474B43EF84005B85A23329AD02977A4F20780372D061804186A | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\amdvbflash\Changelog.txt | text | |
MD5:E55A0130C287F8ACAAA432B787A4C8BB | SHA256:1CBE1AD43C3ABB2475FF9B237A3CB67827A268DDD6D37A854AD90BC80095FB0A | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\ProfilesBackupGPU.ini | text | |
MD5:2916E7A81DCA0BAB5F6EC47F9C2A7903 | SHA256:AB8DECE7C42A8359C0D8AB8235C711CD53AF11B727C628B2DC434B9C2A48EA13 | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\ProfilesGPU.ini | text | |
MD5:54B13710491C6BDAD9DC9E4111A1FF40 | SHA256:767AADCDF83F28C0A5BDC517B3452CAABAFE2000E220264EF58568A0F1AB69BF | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\Settings_Backup.ini | text | |
MD5:9B79B2E8441DF66AADCC7A0196DF71D3 | SHA256:44FC64C71C1ACACB59405C99ABE0E2D8B104D05D38E23EB1F91BB08F19EA92BA | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\Settings.ini | text | |
MD5:9B79B2E8441DF66AADCC7A0196DF71D3 | SHA256:44FC64C71C1ACACB59405C99ABE0E2D8B104D05D38E23EB1F91BB08F19EA92BA | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\ProfilesBackupCPU.ini | text | |
MD5:9CDE440C1351CAC670354CD26B506E9E | SHA256:DF4514C632059A703D85673AE23BCED5EECD68714893D3B1CE72428F46C9619A | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\amdvbflash\arguments.txt | text | |
MD5:696A0182C4867D2F6C6D7FB72674E7A2 | SHA256:8B463CABD48AB42E22870D8AE30F6CE88B2D1CFD519A5B53A863D63B42CA8838 | |||
| 7412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7412.24332\HYDRA 1.8A PRO\ProfilesCPU.ini | text | |
MD5:4CA18666617E02CAB5DE2CDAFFF7F9C3 | SHA256:6AAA613DD5E27C2E7ADE741044711803567B66626294E2DF11FC596022B76D2C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
22
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7720 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1852 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7720 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |