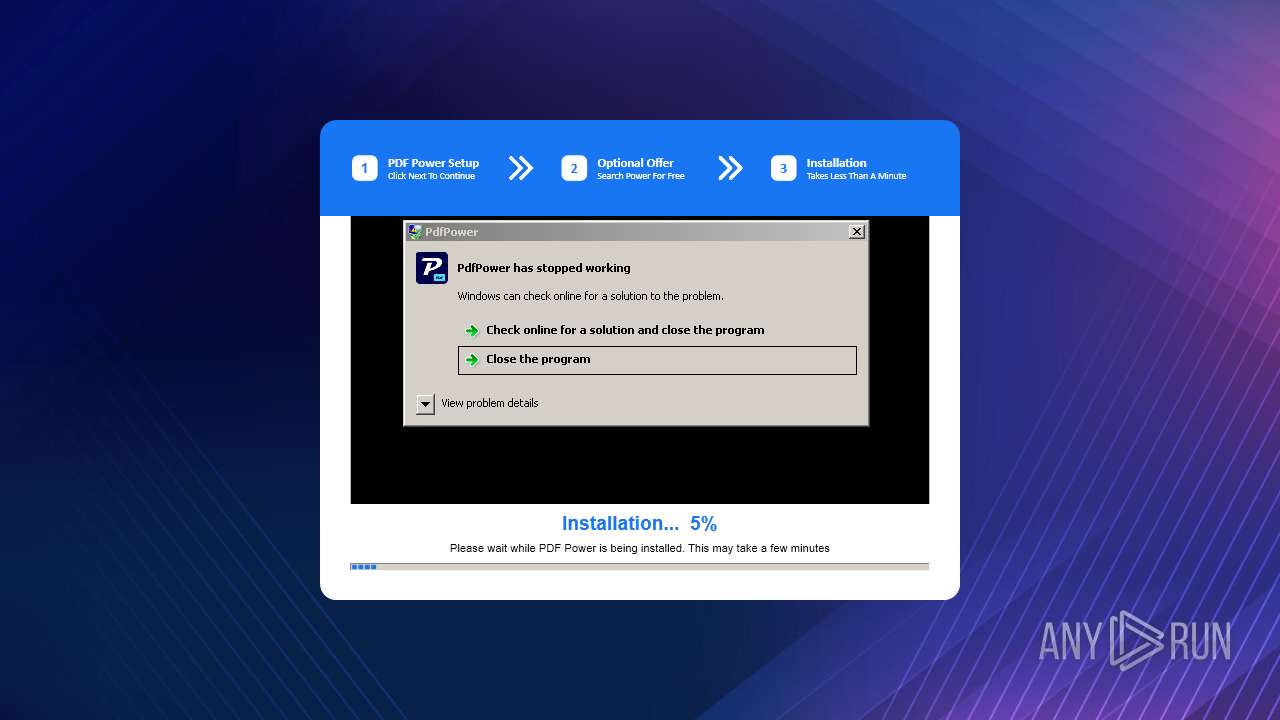
| File name: | PDFpower.exe |
| Full analysis: | https://app.any.run/tasks/f88136d8-1c8f-4191-8a5f-bd6d99aac643 |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2023, 12:33:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 1E2A99AE43D6365148D412B5DFEE0E1C |
| SHA1: | 33C02D70ABB2F1F12A79CFD780D875A94E7FE877 |
| SHA256: | E248B01E3CCDE76B4D8E8077D4FCB4D0B70E5200BF4E738B45A0BD28FBC2CAE6 |
| SSDEEP: | 24576:sWjYtbXSRxqO8m657w6ZBLmkitKqBCjC0PDgM5A6:sW8tbiJVV1BCjB |
MALICIOUS
Actions looks like stealing of personal data
- PDFpower.exe (PID: 2368)
SUSPICIOUS
Reads the Internet Settings
- PDFpower.exe (PID: 2368)
Reads settings of System Certificates
- PDFpower.exe (PID: 2368)
INFO
The process checks LSA protection
- PDFpower.exe (PID: 2368)
- wisptis.exe (PID: 4076)
Reads the computer name
- PDFpower.exe (PID: 2368)
Reads the machine GUID from the registry
- PDFpower.exe (PID: 2368)
Checks supported languages
- PDFpower.exe (PID: 2368)
Reads Environment values
- PDFpower.exe (PID: 2368)
Checks proxy server information
- PDFpower.exe (PID: 2368)
Create files in a temporary directory
- PDFpower.exe (PID: 2368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (49.4) |
|---|---|---|
| .scr | | | Windows screen saver (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.7) |
| .exe | | | Win32 Executable (generic) (8) |
| .exe | | | Generic Win/DOS Executable (3.5) |
EXIF
EXE
| AssemblyVersion: | 4.0.1.0 |
|---|---|
| ProductVersion: | 4.0.1.0 |
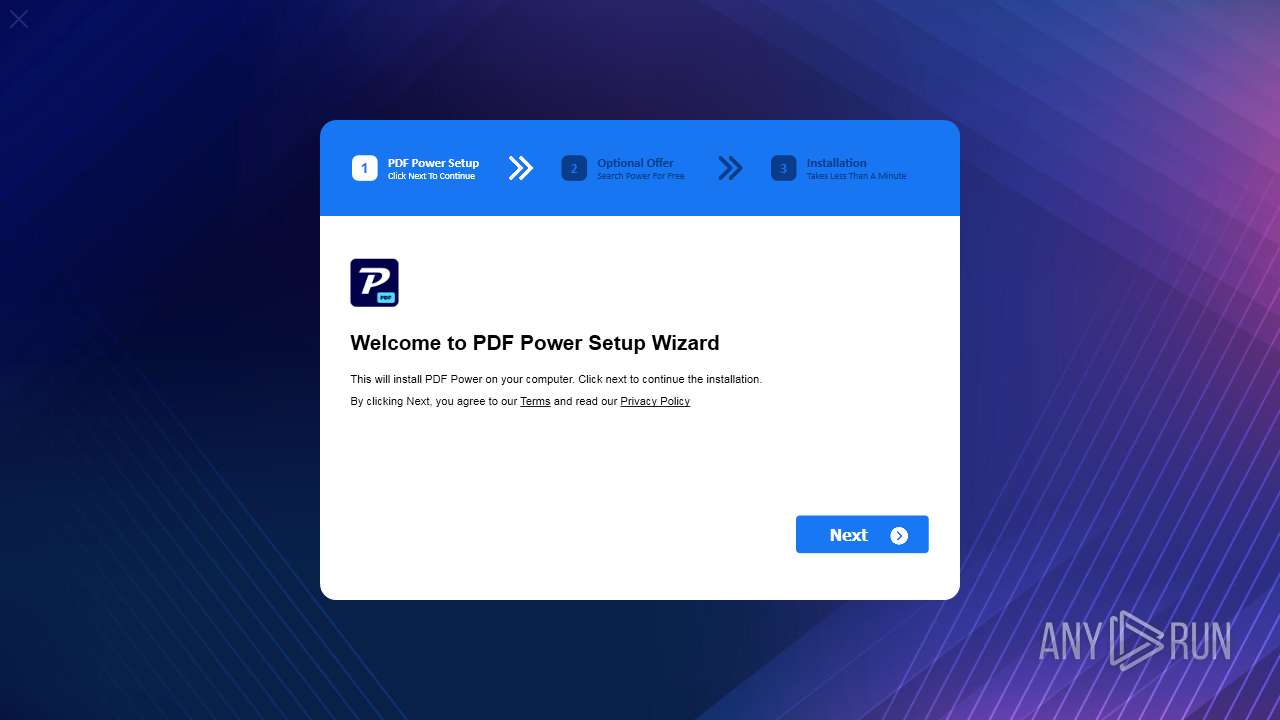
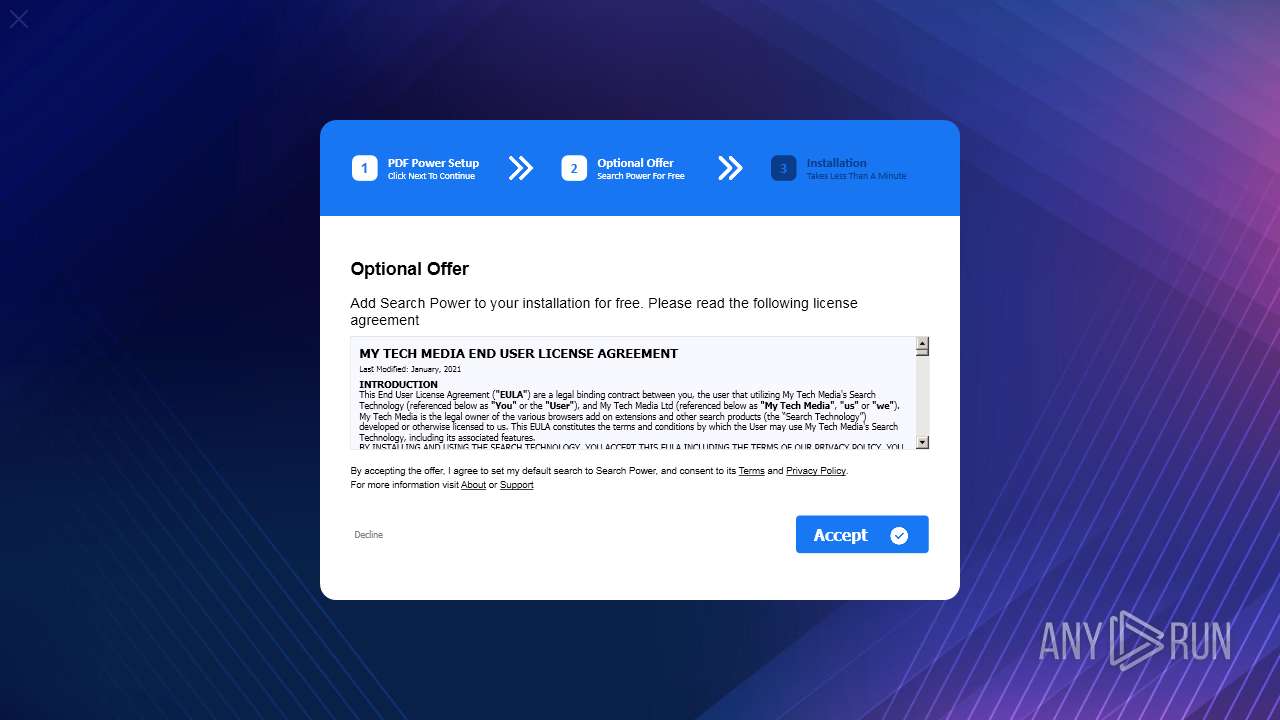
| ProductName: | PdfPower |
| OriginalFileName: | PdfPowerB2C.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © 2022 |
| InternalName: | PdfPowerB2C.exe |
| FileVersion: | 4.0.1.0 |
| FileDescription: | PdfPower |
| CompanyName: | - |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 4.0.1.0 |
| FileVersionNumber: | 4.0.1.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x103c5e |
| UninitializedDataSize: | - |
| InitializedDataSize: | 19456 |
| CodeSize: | 1056256 |
| LinkerVersion: | 48 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, Large address aware |
| TimeStamp: | 2042:10:01 03:36:44+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Oct-2042 03:36:44 |
| Debug artifacts: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | PdfPower |
| FileVersion: | 4.0.1.0 |
| InternalName: | PdfPowerB2C.exe |
| LegalCopyright: | Copyright © 2022 |
| LegalTrademarks: | - |
| OriginalFilename: | PdfPowerB2C.exe |
| ProductName: | PdfPower |
| ProductVersion: | 4.0.1.0 |
| Assembly Version: | 4.0.1.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 01-Oct-2042 03:36:44 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00101CAC | 0x00101E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.37083 |
.rsrc | 0x00104000 | 0x00004880 | 0x00004A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.67245 |
.reloc | 0x0010A000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
32512 | 1.91924 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
42
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2368 | "C:\Users\admin\AppData\Local\Temp\PDFpower.exe" | C:\Users\admin\AppData\Local\Temp\PDFpower.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: PdfPower Exit code: 0 Version: 4.0.1.0 Modules
| |||||||||||||||
| 3292 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | — | PDFpower.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Pen and Touch Input Component Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4076 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\System32\wisptis.exe | PDFpower.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 24 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 142
Read events
10 066
Write events
76
Delete events
0
Modification events
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4076) wisptis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: PDFpower.exe | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates\C7C20953EB5AC83C81CA388170EEC982E577F810 |
| Operation: | write | Name: | Blob |
Value: 0200000001000000CC0000001C0000006C00000001000000000000000000000000000000010000007B00410032003900380043003100300039002D0036004300440030002D0034004600410044002D0042003300370046002D004600430039003500360045003100340046004200440036007D00000000004D006900630072006F0073006F0066007400200045006E00680061006E006300650064002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072002000760031002E00300000000000140000000100000014000000396A962A0D9CA2D65CF53FD9D5915A728280AB80030000000100000014000000C7C20953EB5AC83C81CA388170EEC982E577F8100F00000001000000200000003940FA3A00F54D92B7F88E2D48C2772C8ABB2A13E49A0D26CD13424C4B5518321900000001000000100000000FED148DCA9288CFE9E8CFEDE332D41E20000000010000004C0300003082034830820230A0030201020209009BC2D79761F68C84300D06092A864886F70D01010B05003039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E79301E170D3230303932383036333030355A170D3330303932363036333030355A3039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E7930820122300D06092A864886F70D01010105000382010F003082010A0282010100A20B189EC9265492B7621FFE83B82E05923AB02D2DEE3E20C24BB7D8923FA45D5D62E0925DAF5EABBDD7C870E4D1229FF08A2D78D685E81450475802410F692FBBD1DFA12CE5E60EE26583458D949D7C0EDC212A1DCADB4426B6F6C2BE40B90B95BED978CC99FCBE9C00035C8FEE07200B20EA4B86FD3E9FFE42AAD926D2D381CC4C95AF963C3A19A7C90BC1C084F7434A83B0626E41A8E4EB3AC624E5DBB3D3214D535FC45294D746609F6E69B44DA48305DE63BA6FEF283E2778254E8579ABB0295629954E228B18AB5355FEF0F664D9DCD2C4A5047D4879BE8587687E37DE690C4E0D45927B2384E1BF09BE1F2744B50D54D5CD0B1223F5D31A446401D1A90203010001A3533051301D0603551D0E04160414396A962A0D9CA2D65CF53FD9D5915A728280AB80301F0603551D23041830168014396A962A0D9CA2D65CF53FD9D5915A728280AB80300F0603551D130101FF040530030101FF300D06092A864886F70D01010B0500038201010089391C5F3A6B3AA5CCD58C62CE4DC5E71A59F014066678C1ECB7959D4F5F5ACDF23E1EAD032ECC41C459B54A991C40E23F546C64C424BF954035D94C0F30EA7172E98E40F5D8A9B389A56360D837BDF5149754095403EE1AC7BE6415DEA18C10E98113868D6BD01C1FCA8A7704AAB167D9BA70D4FBCCC8E1836CC11AF03E8A62E13DB2EBF7038E469ED65D1D46B3074D92BB304F8FF41068DEC4BB499974635A8C524E4DA418B524529C641DBA82918A55FFBC82B8688B0838C3CEB24647B6142CDB17837E3978D7C551803638DE839DC9B2F9B368773E9148364ABEACF9ABB4A20A3D72122F22E3E17F0969B4C8C2CAF88C5B5D74EC82C19FA533D01ADD79A3 | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\Root\Certificates\C7C20953EB5AC83C81CA388170EEC982E577F810 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000F7998935234BC4DE2CB672C84BD550341900000001000000100000000FED148DCA9288CFE9E8CFEDE332D41E0F00000001000000200000003940FA3A00F54D92B7F88E2D48C2772C8ABB2A13E49A0D26CD13424C4B551832030000000100000014000000C7C20953EB5AC83C81CA388170EEC982E577F810140000000100000014000000396A962A0D9CA2D65CF53FD9D5915A728280AB800200000001000000CC0000001C0000006C00000001000000000000000000000000000000010000007B00410032003900380043003100300039002D0036004300440030002D0034004600410044002D0042003300370046002D004600430039003500360045003100340046004200440036007D00000000004D006900630072006F0073006F0066007400200045006E00680061006E006300650064002000430072007900700074006F0067007200610070006800690063002000500072006F00760069006400650072002000760031002E0030000000000020000000010000004C0300003082034830820230A0030201020209009BC2D79761F68C84300D06092A864886F70D01010B05003039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E79301E170D3230303932383036333030355A170D3330303932363036333030355A3039310B30090603550406130241553113301106035504080C0A536F6D652D537461746531153013060355040A0C0C536F6D652D436F6D70616E7930820122300D06092A864886F70D01010105000382010F003082010A0282010100A20B189EC9265492B7621FFE83B82E05923AB02D2DEE3E20C24BB7D8923FA45D5D62E0925DAF5EABBDD7C870E4D1229FF08A2D78D685E81450475802410F692FBBD1DFA12CE5E60EE26583458D949D7C0EDC212A1DCADB4426B6F6C2BE40B90B95BED978CC99FCBE9C00035C8FEE07200B20EA4B86FD3E9FFE42AAD926D2D381CC4C95AF963C3A19A7C90BC1C084F7434A83B0626E41A8E4EB3AC624E5DBB3D3214D535FC45294D746609F6E69B44DA48305DE63BA6FEF283E2778254E8579ABB0295629954E228B18AB5355FEF0F664D9DCD2C4A5047D4879BE8587687E37DE690C4E0D45927B2384E1BF09BE1F2744B50D54D5CD0B1223F5D31A446401D1A90203010001A3533051301D0603551D0E04160414396A962A0D9CA2D65CF53FD9D5915A728280AB80301F0603551D23041830168014396A962A0D9CA2D65CF53FD9D5915A728280AB80300F0603551D130101FF040530030101FF300D06092A864886F70D01010B0500038201010089391C5F3A6B3AA5CCD58C62CE4DC5E71A59F014066678C1ECB7959D4F5F5ACDF23E1EAD032ECC41C459B54A991C40E23F546C64C424BF954035D94C0F30EA7172E98E40F5D8A9B389A56360D837BDF5149754095403EE1AC7BE6415DEA18C10E98113868D6BD01C1FCA8A7704AAB167D9BA70D4FBCCC8E1836CC11AF03E8A62E13DB2EBF7038E469ED65D1D46B3074D92BB304F8FF41068DEC4BB499974635A8C524E4DA418B524529C641DBA82918A55FFBC82B8688B0838C3CEB24647B6142CDB17837E3978D7C551803638DE839DC9B2F9B368773E9148364ABEACF9ABB4A20A3D72122F22E3E17F0969B4C8C2CAF88C5B5D74EC82C19FA533D01ADD79A3 | |||
| (PID) Process: | (2368) PDFpower.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2368 | PDFpower.exe | C:\Users\admin\AppData\Local\Temp\PdfPowerB2C\favicon.ico | image | |
MD5:68814A062FD60A524FFC92E3132B924C | SHA256:49CFC761F6EF30F7FF6276AF7A7093026D8985090200362858E1E77336ED2448 | |||
| 2368 | PDFpower.exe | C:\Users\admin\AppData\Local\Temp\PdfPowerB2C\installing.gif | image | |
MD5:375DA4DEA8747071B487386DA14B1264 | SHA256:B891A5DFE676B829D5A1B68063765EFE3B7CA842D69315EB25DD97F47A02080A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2368 | PDFpower.exe | GET | 200 | 167.99.105.92:443 | https://bl.searchpoweronline.com/v4/install/first_time?BwQYBwYBGj4CEFJcEAQIRlgNQExTQAtYWVVSFl5DTQJTFUIPEAQITF9XFlZdTF9IFREbKwYKSVBdR1leRVlTQV9WTFBaTF1IEQwCEFJfQ1kpMi0oMlFbRFpeQiRYQAtbRVJbR19dRFJbRl9dRVNbRl9cRFNbRl9cRFNbRl9cRFNbRl9cRFBZNVZWQlcoQ1gqMUcCGhwaFQ0HKxkLBhICGwFTRUcCEAoAAAgfDVIdEQAZFwceGxYOBgAAGAgFEUkdHQZWJC4gPSMqODA+MCc7OzgrJj44PSggNTU+JipIEA4cGgMBFQU0Fh0BAxIOBlILEAYOKwwGBg4GEUkBBz4dER0dHQ4FSVlARU9cQl9fUhNWR1pZQ1haQ11a | US | — | — | suspicious |
2368 | PDFpower.exe | GET | 200 | 167.99.105.92:443 | https://bl.searchpoweronline.com/v4/install?BwQYBwYBGj4CEFJcEAQIRlgNQExTQAtYWVVSFl5DTQJTFUIPEAQITF9XFlZdTF9IFREbKwYKSVBdR1leRVlTQV9WTFBaTF1IEQwCEFJfQ1kpMi0oMlFbRFpeQiRYQAtbRVJbR19dRFJbRl9dRVNbRl9cRFNbRl9cRFNbRl9cRFNbRl9cRFBZNVZWQlcoQ1gqMUcCGhwaFQ0HKxkLBhICGwFTRUcCEAoAAAgfDVIdEQAZFwceGxYOBgAAGAgFEUkHGgcEKw1TMwocMS0JPSs6RT0qJSMMUVwKUgUEAwECGwAPKw0cGxYYER1TEQUMETANHBMEGQpIGxI0AgocBwgEGlJYWlBFQ1leRUcZSV5aQ1NdRF9YRVE= | US | — | — | suspicious |
2368 | PDFpower.exe | GET | 200 | 167.99.105.92:443 | https://info.searchpoweronline.com/report?event_name=repc&infoJson=D0MKBAMxHQVJTk1fQlJdRF5WTFRbTFdfRVlZVkNMFREHKwEPGQRJTk0%2bMCc7GxgLBkNHVhwbHQVJTk1fQ1kpMi0oMlFbRFpeQiRYQAtbRVJbR19dRFJbRl9dRVNbRl9cRFNbRl9cRFNbRl9cRFNbRl9cRFBZNVZWQlcoQ1gqMUNHVgAeERMKAAYAEz4YDRwxAgQZBwYBGkNRVllARU9cQl9fVk1JGx8LBgAfHQEJKxISBzAFHQ8PVlVMOQgIBgAdGwcfVDgHGgUEAxxOQ0NHVhkLBhICGwExHQ8YAE1UVlBJWE0MBg4cBwocVltJEQsJET4IHB0BGQRJWE0HEAQFAE1UVhIOFR0NHBEEAwocGw8HHQELVk1JBwYJGgQPVlVMJCAlPS0vOD47MCk%2bOzYuJjA9PSYlNTs7JiRJWE0MBg4cBwocKxcOBhwHGw9JTk1MWEMGGx0LKwgFEgBMTkMvEQkPAQ0fVC0cGxYYER1OHRJRVCYAAAQZGgoaVCQTBAMBBgQZVkNMFQIfHQAAVltJJwoPBgIDVAAIEgQZVA4NFwQbAE0T | US | — | — | suspicious |
2368 | PDFpower.exe | GET | 200 | 167.99.105.92:443 | https://bl.searchpoweronline.com/interpolate?emid=178BFBFF000506E34d5130303030203120202020202020202020202012A9866C77DE&appId=1636018850881182&string_interpolation=GET_BRAND_NAME | US | binary | 39 b | suspicious |
2368 | PDFpower.exe | GET | 200 | 167.99.105.92:443 | https://bl.searchpoweronline.com/interpolate?emid=178BFBFF000506E34d5130303030203120202020202020202020202012A9866C77DE&appId=1636018850881182&string_interpolation=GET_SIGNATURE | US | binary | 47 b | suspicious |
2368 | PDFpower.exe | GET | 200 | 167.99.105.92:443 | https://info.searchpoweronline.com/report?event_name=repc&infoJson=D0MKBAMxHQVJTk1fQlJdRF5WTFRbTFdfRVlZVkNMFREHKwEPGQRJTk0%2bMCc7GxgLBkNHVhwbHQVJTk1fQ1kpMi0oMlFbRFpeQiRYQAtbRVJbR19dRFJbRl9dRVNbRl9cRFNbRl9cRFNbRl9cRFNbRl9cRFBZNVZWQlcoQ1gqMUNHVgAeERMKAAYAEz4YDRwxAgQZBwYBGkNRVllARU9cQl9fVk1JGx8LBgAfHQEJKxISBzAFHQ8PVlVMOQgIBgAdGwcfVDgHGgUEAxxOQ0NHVhkLBhICGwExHQ8YAE1UVlBJWE0MBg4cBwocVltJEQsJET4IHB0BGQRJWE0HEAQFAE1UVhIOFR0NHBEEAwocGw8HHQELVk1JBwYJGgQPVlVMJCAlPS0vOD47MCk%2bOzYuJjA9PSYlNTs7JiRJWE0MBg4cBwocKxcOBhwHGw9JTk1MWEMGGx0LKwgFEgBMTkMvEQkPAQ0fVC0cGxYYER1OHRJRVCYAAAQZGgoaVCQTBAMBBgQZVkNMFQIfHQAAVltJJwoPBgIDVAAIEgQZVBwGGxZJCQ%3d%3d | US | — | — | suspicious |
2368 | PDFpower.exe | GET | 200 | 167.99.105.92:443 | https://bl.searchpoweronline.com/interpolate?emid=178BFBFF000506E34d5130303030203120202020202020202020202012A9866C77DE&appId=1636018850881182&string_interpolation=GET_OSOU | US | binary | 259 b | suspicious |
2368 | PDFpower.exe | POST | 200 | 142.250.185.206:443 | https://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
2368 | PDFpower.exe | POST | 200 | 142.250.185.206:443 | https://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
2368 | PDFpower.exe | POST | 200 | 142.250.185.206:443 | https://www.google-analytics.com/collect | US | image | 35 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2368 | PDFpower.exe | 142.250.185.206:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
2368 | PDFpower.exe | 167.99.105.92:443 | bl.searchpoweronline.com | DIGITALOCEAN-ASN | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google-analytics.com |
| whitelisted |
bl.searchpoweronline.com |
| suspicious |
info.searchpoweronline.com |
| suspicious |
Threats
Process | Message |
|---|---|
PDFpower.exe | MainWindow Started
|
PDFpower.exe | MainWindow Started
|
PDFpower.exe | FirstScreen Started
|
PDFpower.exe | FirstScreen Started
|
PDFpower.exe | GA TRACK START - IMP_FTA_PPW
|
PDFpower.exe | GA TRACK START - IMP_FTA_PPW
|
PDFpower.exe | Mac Adress after adjusting = 12A9866C77DE
|
PDFpower.exe | GetMacAddress :: uuid = 1343eda4-d3ae-11ed-94df-12a9866c77de
|
PDFpower.exe | Is succeed to execute machine code? True; CPUId = 178BFBFF000506E3
|
PDFpower.exe | Mac Adress before adjusting = 12A9866C77DE
|