| File name: | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe |
| Full analysis: | https://app.any.run/tasks/6c1e07e6-b30b-4da5-926b-c4ba987323c4 |
| Verdict: | Malicious activity |
| Analysis date: | August 14, 2025, 19:19:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | F1E7F7CE851CDAE4AA96270FF14F18E3 |
| SHA1: | CEF0D9E16347C3A67580EA8AACC40DCC318FE5D0 |
| SHA256: | E2454D8F0BD913AA3C1126525F97F0D2D34BB70D92B994D6B51C2B88CA7099E4 |
| SSDEEP: | 98304:EuBftSXNj+NM2bm5JcxboHf2ZCDdLc3LVd4Z/c5GdgCB2hgvRzpg5fVBIqtsNBM7:hWIyx0pwi |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
Detected use of alternative data streams (AltDS)
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
Drops 7-zip archiver for unpacking
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
There is functionality for taking screenshot (YARA)
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
INFO
The sample compiled with english language support
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
Checks supported languages
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
- 7z.exe (PID: 7040)
Reads the computer name
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
Reads mouse settings
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
The sample compiled with chinese language support
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
Checks proxy server information
- slui.exe (PID: 7052)
Reads the software policy settings
- slui.exe (PID: 7052)
The process uses AutoIt
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
Create files in a temporary directory
- e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe (PID: 6808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:10:26 02:29:38+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 570880 |
| InitializedDataSize: | 2369024 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25f74 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.21.328 |
| ProductVersionNumber: | 7.0.21.315 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 7.0.21.0328 |
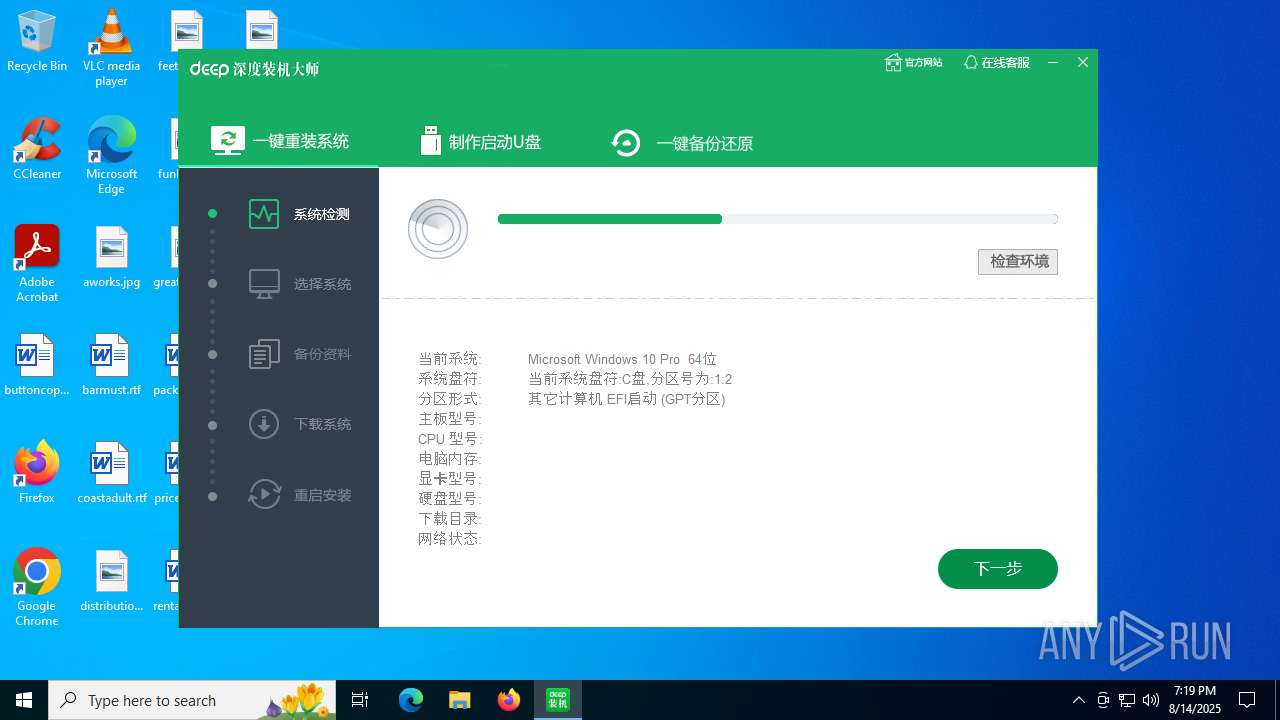
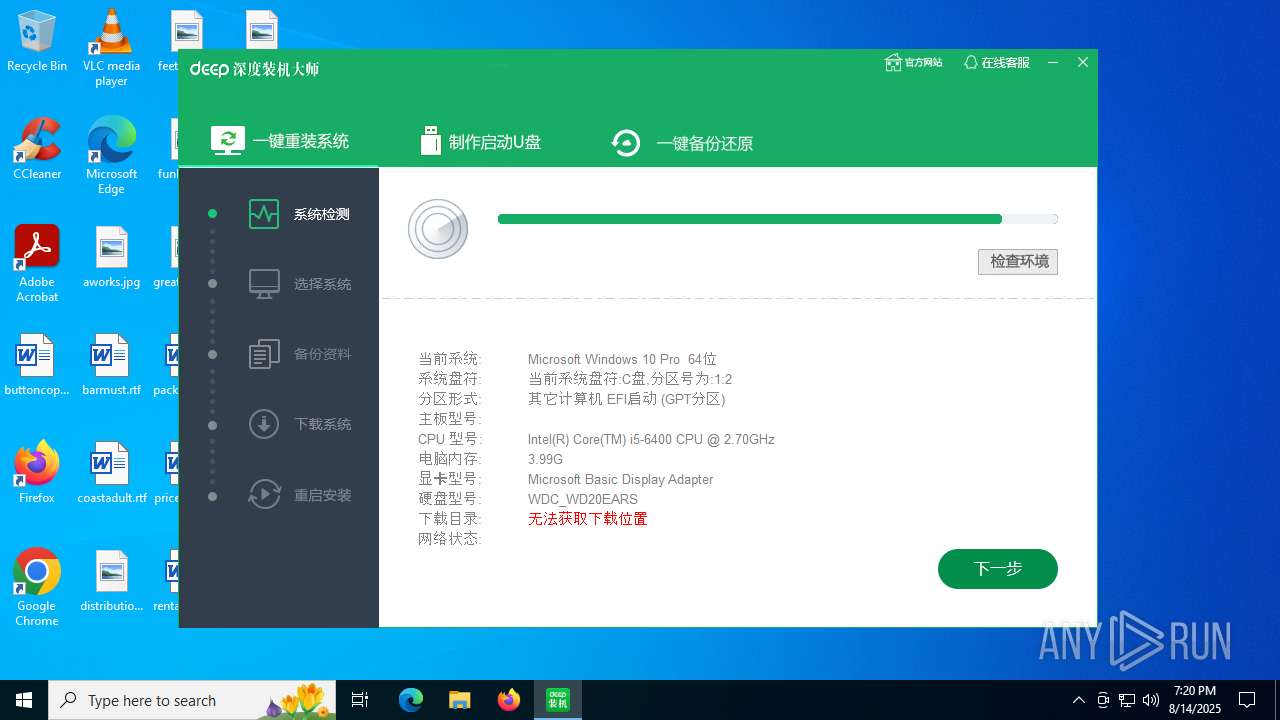
| Comments: | 深度技术-装机大师 |
| FileDescription: | 深度技术_网络维护系统,方便安全快捷高效! |
| ProductVersion: | 7.0.21.0315 |
| LegalCopyright: | Copyright 2018-2021 PEoss, All Rights Reserved. |
| ProductName: | 深度技术装机大师 |
| LegalTrademarks: | 深度技术装机大师 |
| OriginalFileName: | sdxitong.exe |
Total processes
140
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\Desktop\e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe" | C:\Users\admin\Desktop\e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 深度技术_网络维护系统,方便安全快捷高效! Exit code: 3221226540 Version: 7.0.21.0328 Modules
| |||||||||||||||
| 6808 | "C:\Users\admin\Desktop\e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe" | C:\Users\admin\Desktop\e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 深度技术_网络维护系统,方便安全快捷高效! Version: 7.0.21.0328 Modules
| |||||||||||||||
| 7040 | C:\Users\admin\AppData\Local\Temp\xh_rztzgek.\7z.exe x "C:\Users\admin\Desktop\e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe" -y -o"C:\Users\admin\AppData\Local\Temp\xh_rztzgek." | C:\Users\admin\AppData\Local\Temp\xh_rztzgek\7z.exe | — | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 2 Version: 9.20 Modules
| |||||||||||||||
| 7052 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 866
Read events
3 866
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
36
Text files
63
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\xh_rztzgek\images\bg.jpg | image | |
MD5:16264DE8792D0F674EA0E81574BD0C1E | SHA256:16F39D0E75DF77B08CE2A8D5BB104AC3E7D9EDD9FC8B88AC188D6C001A5C7C22 | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\autDC62.tmp | binary | |
MD5:3BB3F5324B757E8CAE7C06B7998D49AD | SHA256:2367FFD71171EE34C535E843BAC01CCE93AA788184C7DF51BE0B2391095136E6 | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\autDCA1.tmp | binary | |
MD5:5C84E0523B807E578E9745C0111904A7 | SHA256:065C767CCAAFF68602F6D393DBA35FBB2194DF346E1822138FC0984898E1C260 | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\autDC42.tmp | binary | |
MD5:9EC1AE050F4E62379645DEB9505DADF7 | SHA256:C5BE51C3EF712A697FCFA6DD6D8993B07E30BB324C7626D88B847F3883641D30 | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\xh_rztzgek\7z.exe | executable | |
MD5:FF7A6F30A05959C05CA54D47BEBB28B8 | SHA256:29717709356C1C1C28339D80C97F202AB00D2D42B7E16296E5E7456056B7BB84 | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\autDCD1.tmp | binary | |
MD5:9E10B25B7F8D4B571176A79B67E05DAD | SHA256:A1AF7522E4B71F5EFF96B0199D1E2860A5FEE89F4D3108297D73C10F027E837F | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\xh_rztzgek\images\Min_1.jpg | image | |
MD5:705CEFCD90E95AB5DB12E9C26BC15BF2 | SHA256:39E5F28BE2EFDF027B07E6E9DD35E32D7794FC239DC3A7571E7B8CAED4997BF8 | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\autDCE3.tmp | binary | |
MD5:C2249A6F7D03D20AA8BB82086759AFEE | SHA256:338F1C165DA200D3200B15D8A0A18F926C58CC4E96B05B98F961F237D8AA1D8C | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\xh_rztzgek\images\1_Mode1_3.jpg | image | |
MD5:8088423B4258D2FD19DA275DB2D26007 | SHA256:2C48D3D3394E262433E28204BADC3EF0D8E319320AD2352C2363BE41056B9BD3 | |||
| 6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | C:\Users\admin\AppData\Local\Temp\xh_rztzgek\images\Close_1.jpg | image | |
MD5:E86A04267D947C1A0D0F157B5787A232 | SHA256:DCF4C99DAB3142414890DE4A570EFCBB3F4757121AFD1509F8F0FC95DF601B00 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
49
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 193.108.153.160:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 193.108.153.160:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2992 | RUXIMICS.exe | GET | 200 | 193.108.153.160:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6808 | e2454d8f0bd913aa3c1126525f97f0d2d34bb70d92b994d6b51c2b88ca7099e4.exe | GET | 200 | 185.106.177.142:80 | http://xiaohei.xiuchufang.com/config.txt | unknown | — | — | unknown |
2992 | RUXIMICS.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.32.74:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 200 | 20.190.160.130:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 40.126.32.74:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2992 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 193.108.153.160:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 193.108.153.160:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2992 | RUXIMICS.exe | 193.108.153.160:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.32.97.216:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
1268 | svchost.exe | 23.32.97.216:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
xiaohei.xiuchufang.com |
| unknown |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |