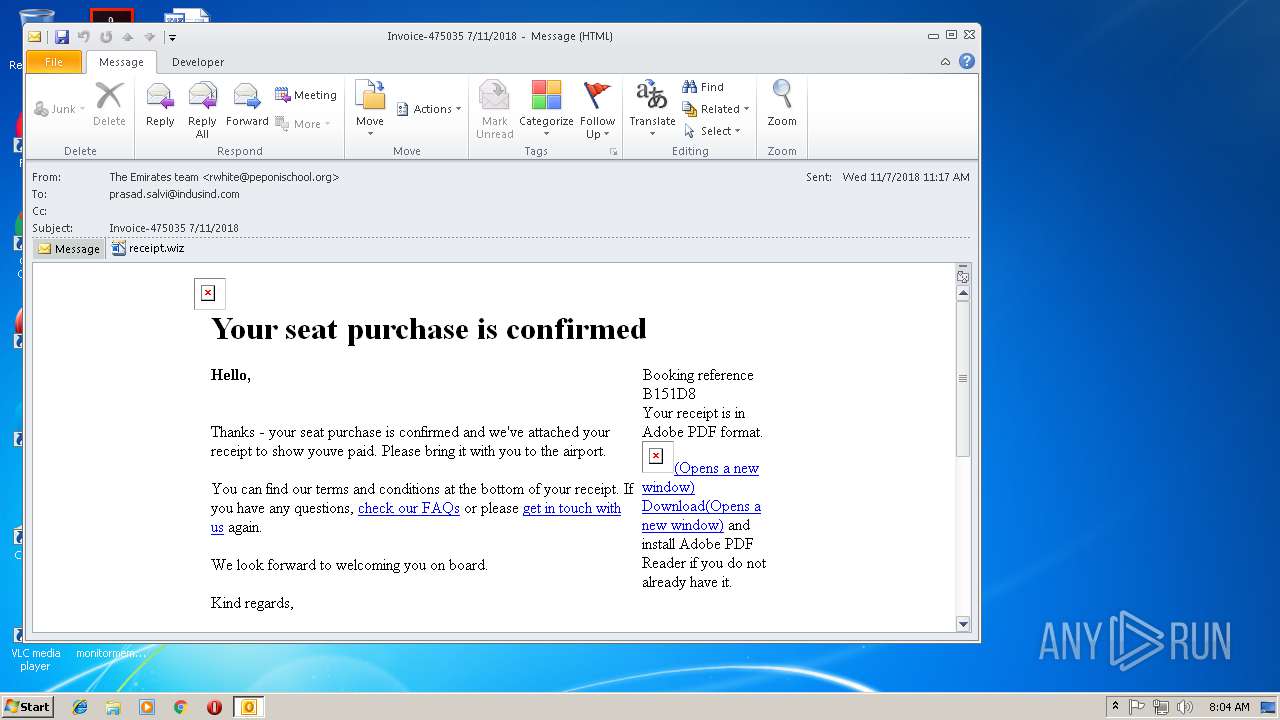
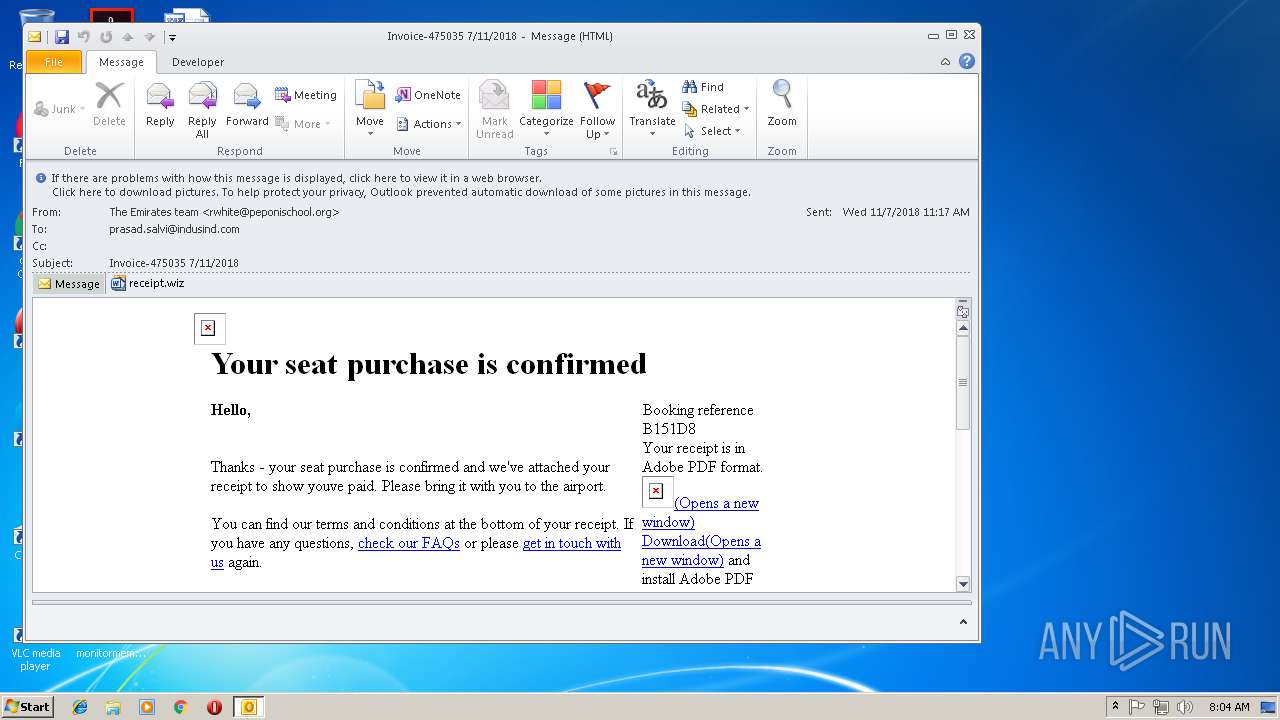
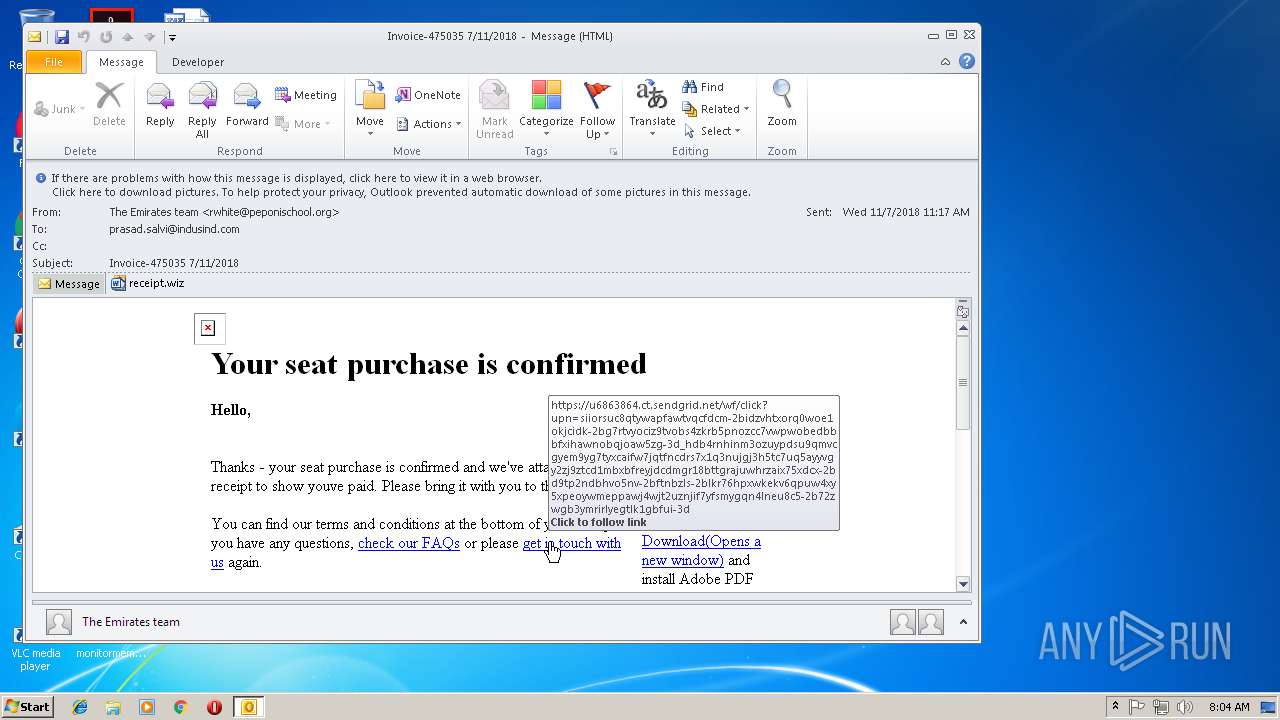
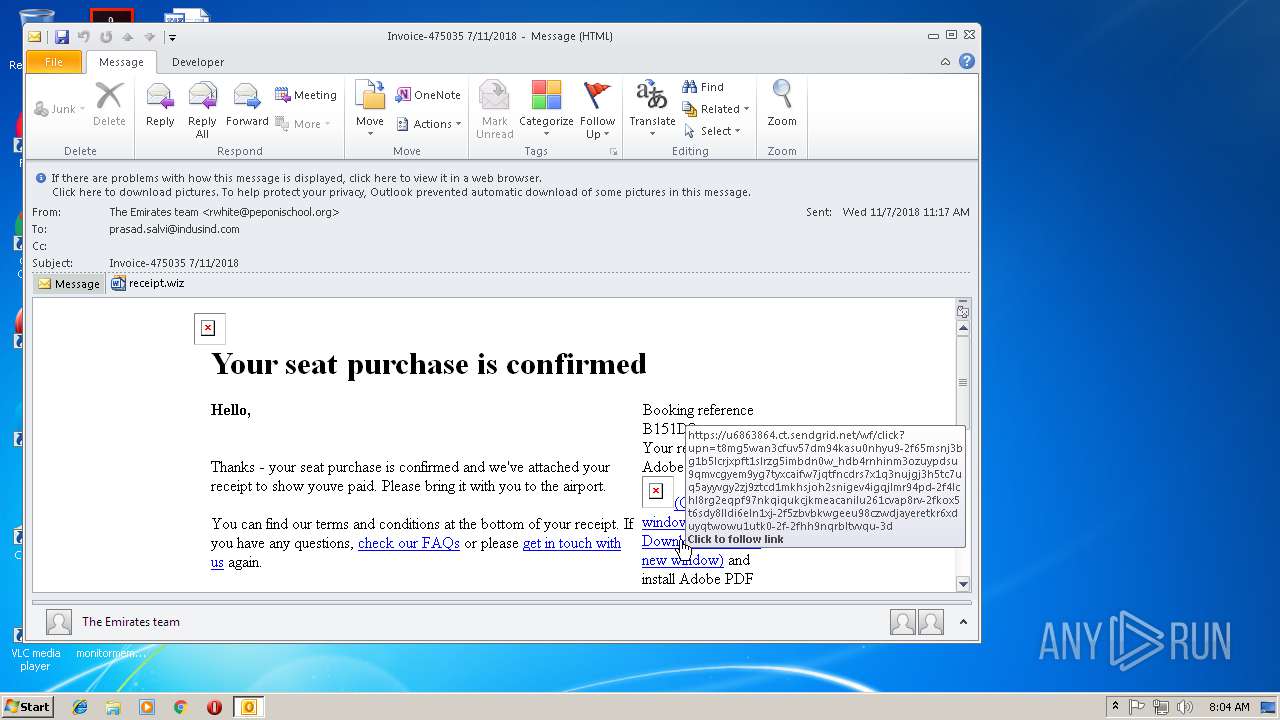
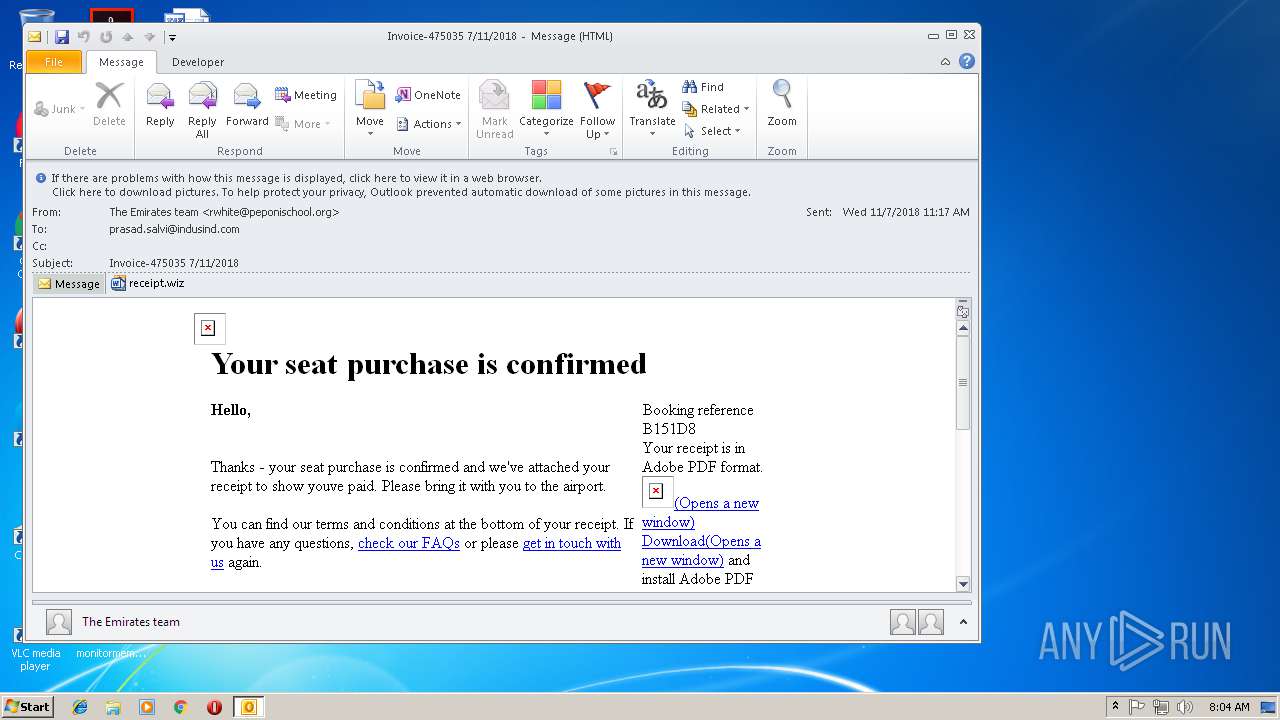
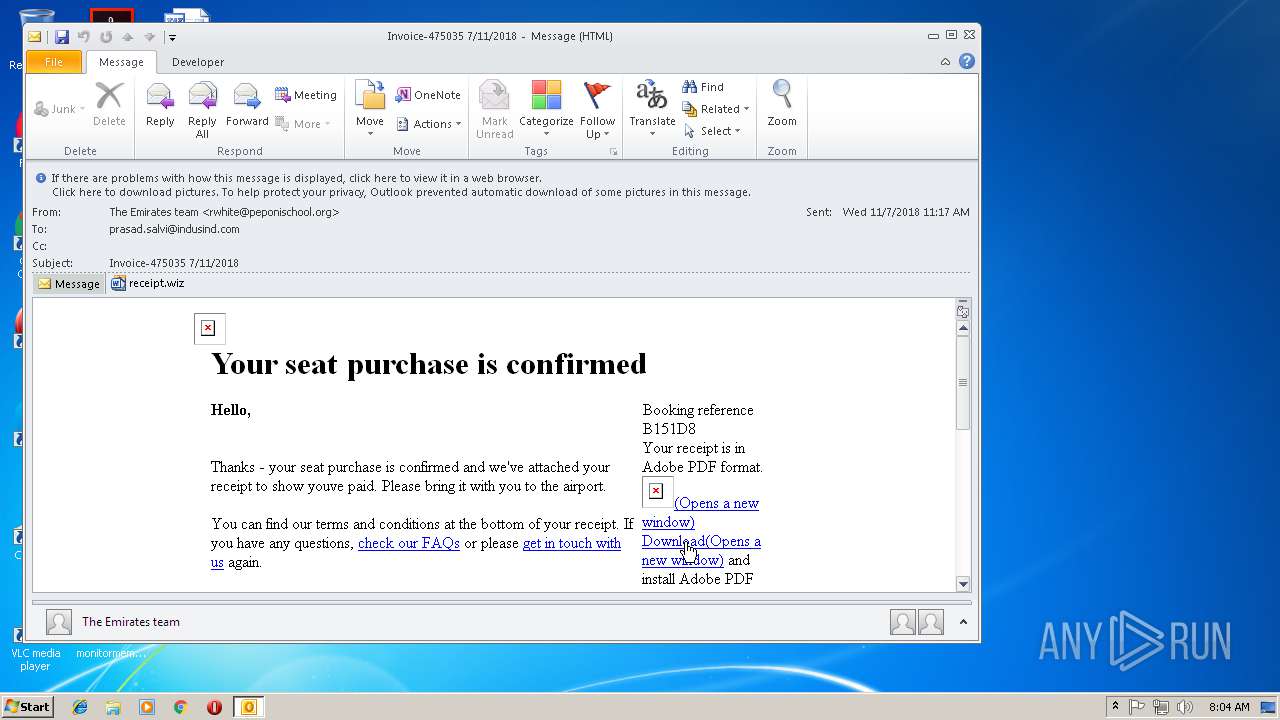
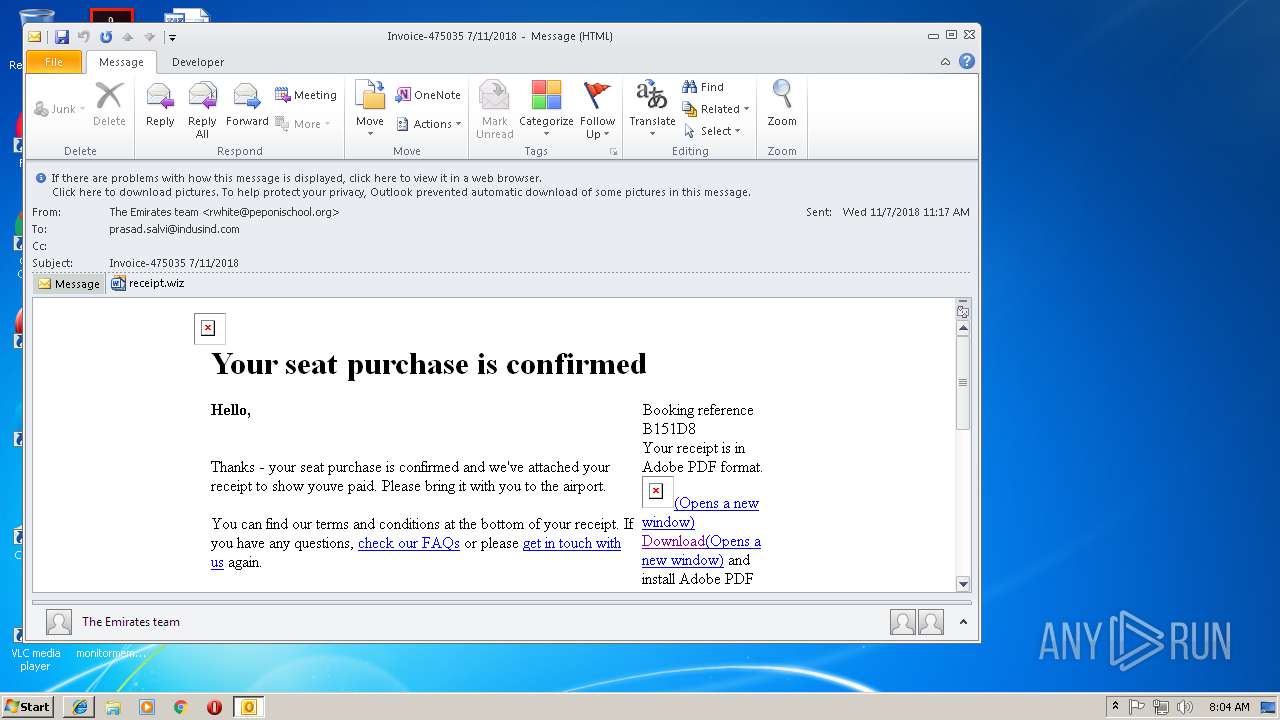
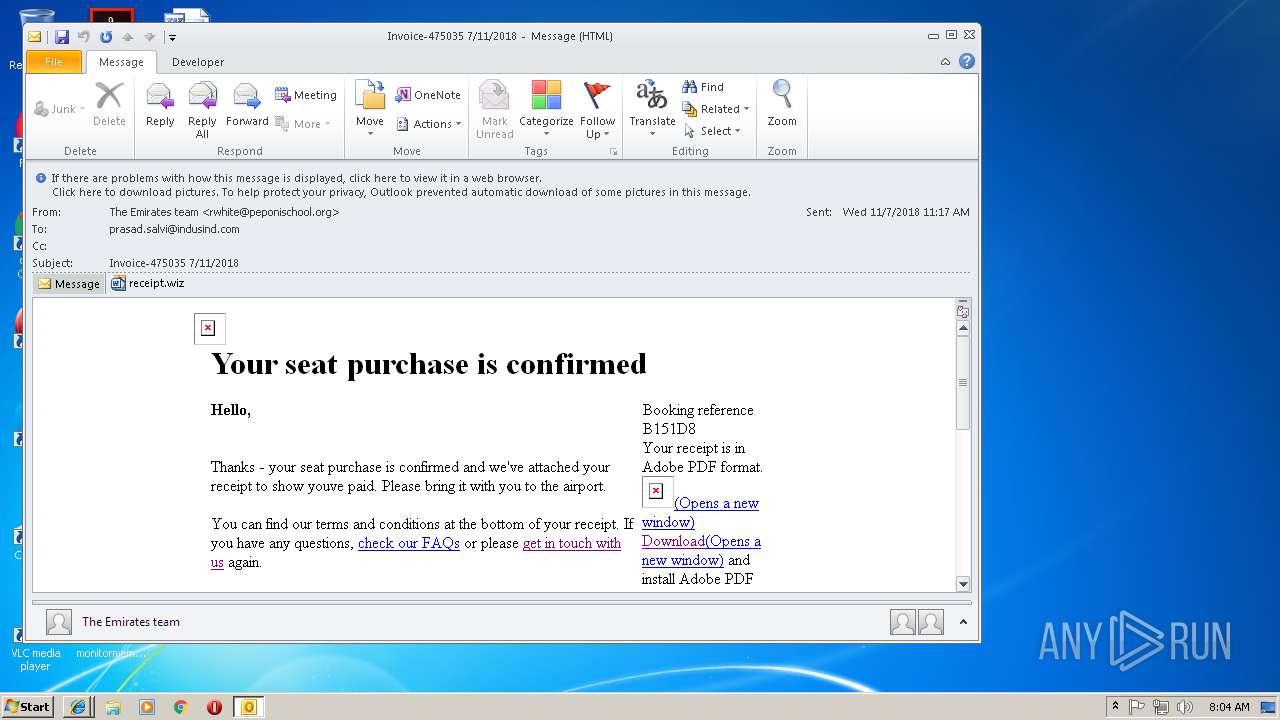
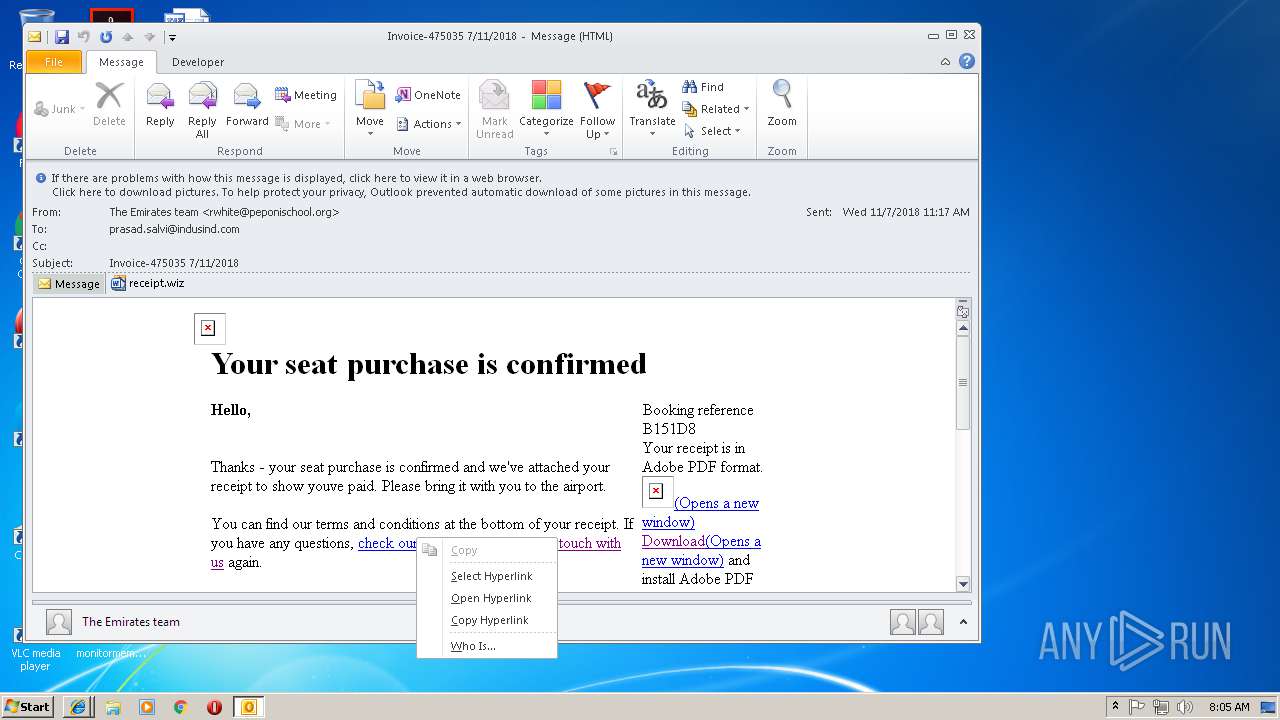
| File name: | 0aa4_12e4_241de41b_52ff_45bb_96d5_83c60ff98b85.eml (73.1 KB).msg |
| Full analysis: | https://app.any.run/tasks/78baeea5-d735-479f-bc5d-6cce208d9de7 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 08:03:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | F7E94BD7C8580D8EBD3F1009C11F4D02 |
| SHA1: | 7889B0922827E1528A2B74680684B3B1F147F288 |
| SHA256: | E203A4D568036AFB2171A26C719A5B6827587FBF9359201B1D41E519AF08FD0B |
| SSDEEP: | 1536:c97YBd0pwlTa9oDhD2wr9rkIepWgo28S5GxvSt3y83D2hjNxqb8Ni:c978nWDw5r8pWgKKt3R4jXS8N |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3032)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3032)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3032)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3032)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1904)
Application launched itself
- iexplore.exe (PID: 1904)
Reads Internet Cache Settings
- iexplore.exe (PID: 2072)
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 2296)
Creates files in the user directory
- iexplore.exe (PID: 2072)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1672)
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 1904)
- iexplore.exe (PID: 2296)
Reads internet explorer settings
- iexplore.exe (PID: 2072)
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 2296)
Reads settings of System Certificates
- iexplore.exe (PID: 1904)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3032)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1904)
Changes settings of System certificates
- iexplore.exe (PID: 1904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (38.9) |
|---|---|---|
| .oft | | | Outlook Form Template (22.7) |
| .doc | | | Microsoft Word document (17.5) |
| .xls | | | Microsoft Excel sheet (16.4) |
Total processes
38
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
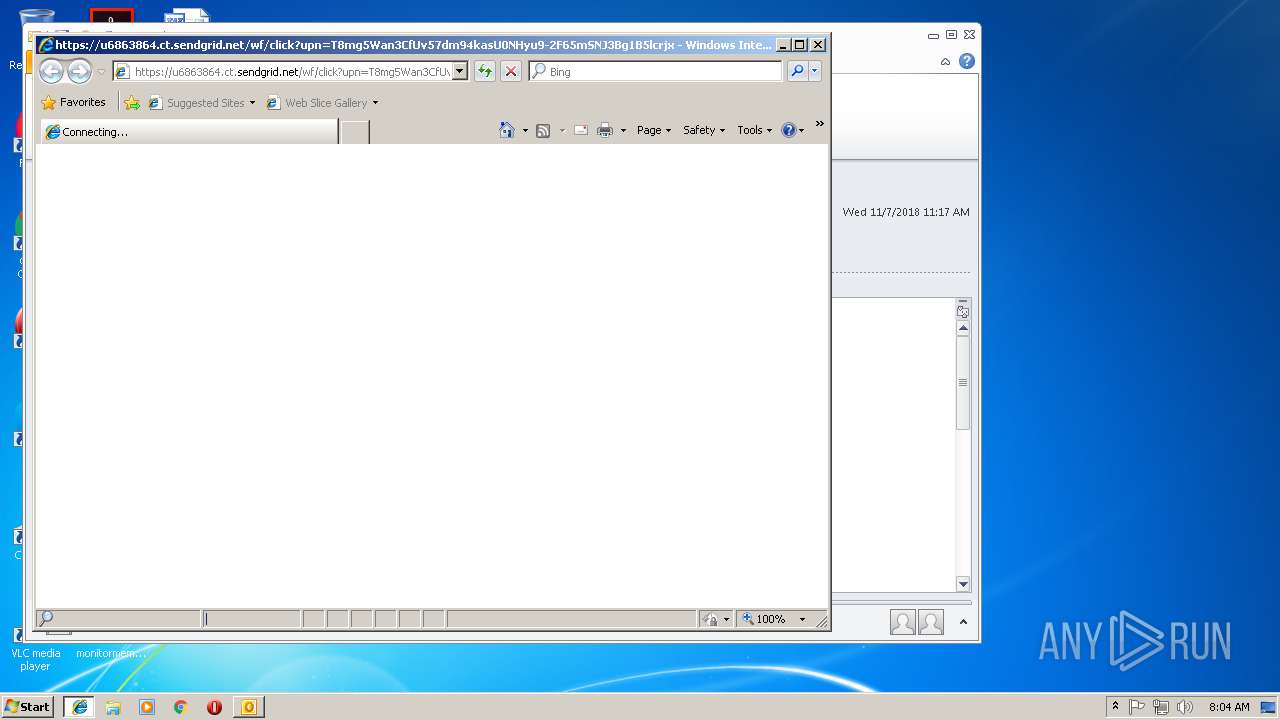
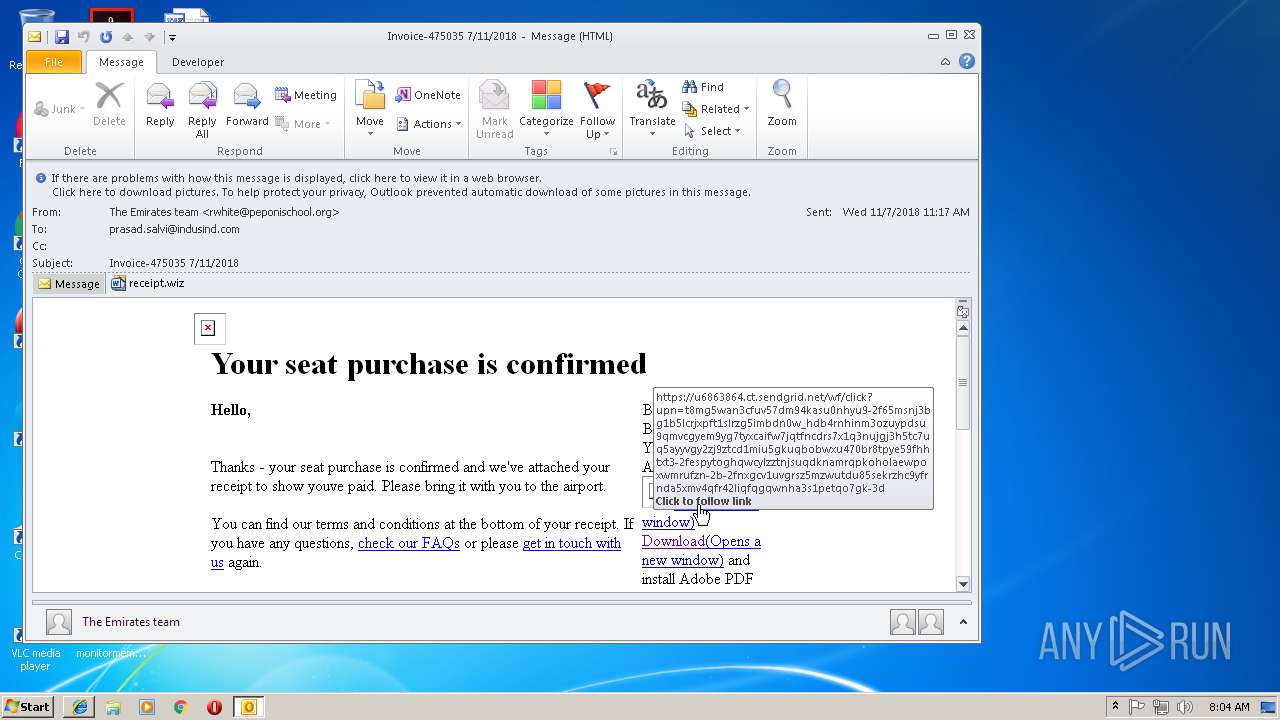
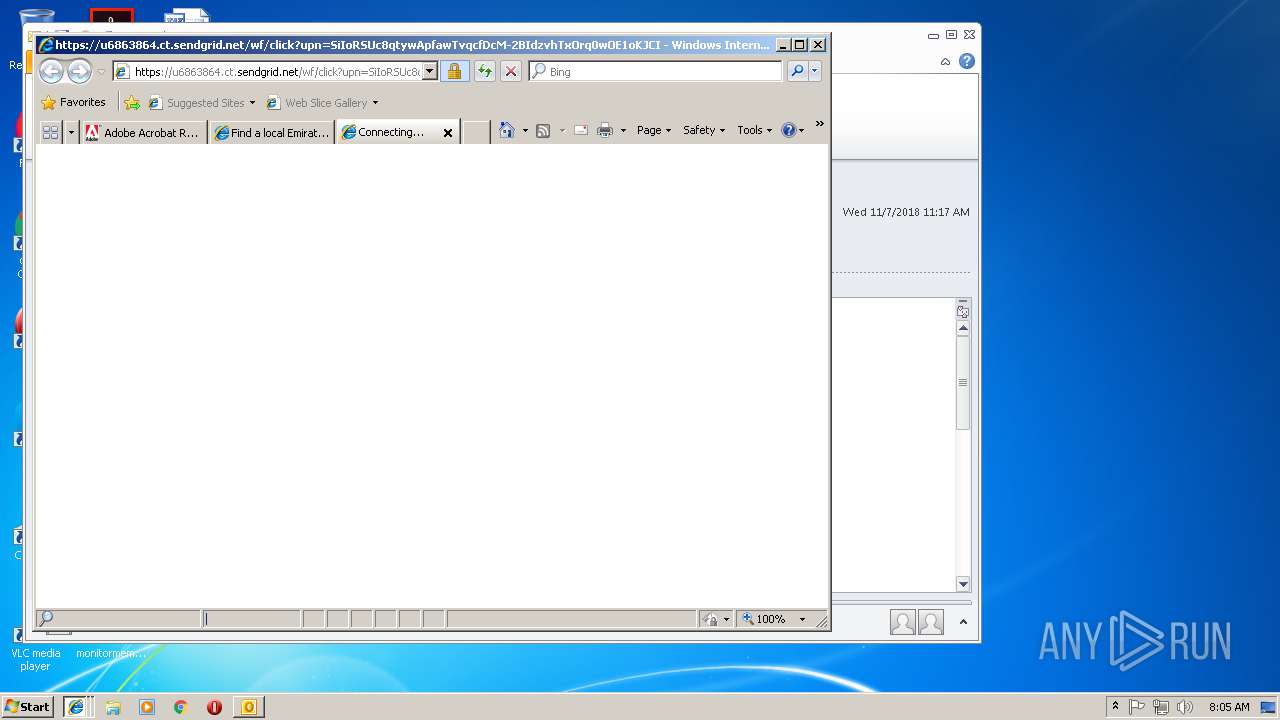
| 1904 | "C:\Program Files\Internet Explorer\iexplore.exe" https://u6863864.ct.sendgrid.net/wf/click?upn=T8mg5Wan3CfUv57dm94kasU0NHyu9-2F65mSNJ3Bg1B5lcrjxPfT1SLrZg5imBDn0w_Hdb4rnHInm3Ozuypdsu9QmVcGyEM9YG7TYxcaIfW7JqTfNcDRs7X1q3nujGj3h5Tc7uQ5ayYvgY2Zj9ZtcD1MKhsjoh2SniGEV4iGqjLmR94pd-2F4LchL8Rg2eqPF97nKQIQUKcjkmEACANILu261cvAp8Rv-2FkoX5t6SdY8LlDI6elN1xJ-2F5zBVBKWgeeu98CZWdjAYeRetkr6XduyQtWoWU1uTk0-2F-2Fhh9nqRBltvVqU-3D | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1904 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1904 CREDAT:6406 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3032 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\0aa4_12e4_241de41b_52ff_45bb_96d5_83c60ff98b85.eml (73.1 KB).msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3496 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1904 CREDAT:6403 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 253
Read events
1 670
Write events
562
Delete events
21
Modification events
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | j>i |
Value: 6A3E6900D80B0000010000000000000000000000 | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: D80B000068BC519E3977D40100000000 | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219768480 | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3032) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1298661397 | |||
Executable files
0
Suspicious files
7
Text files
186
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3032 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA6CA.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\reader[1].txt | — | |
MD5:— | SHA256:— | |||
| 3032 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@adobe[1].txt | text | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\core[1].css | text | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\reset[1].css | text | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\reader[1].htm | html | |
MD5:— | SHA256:— | |||
| 2072 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\ie_fix[1].css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
91
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3032 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2296 | iexplore.exe | GET | 304 | 23.0.35.131:80 | http://cdn.ek.aero/qubit/opentag-93989-1321710.js | NL | — | — | whitelisted |
2072 | iexplore.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 54.4 Kb | whitelisted |
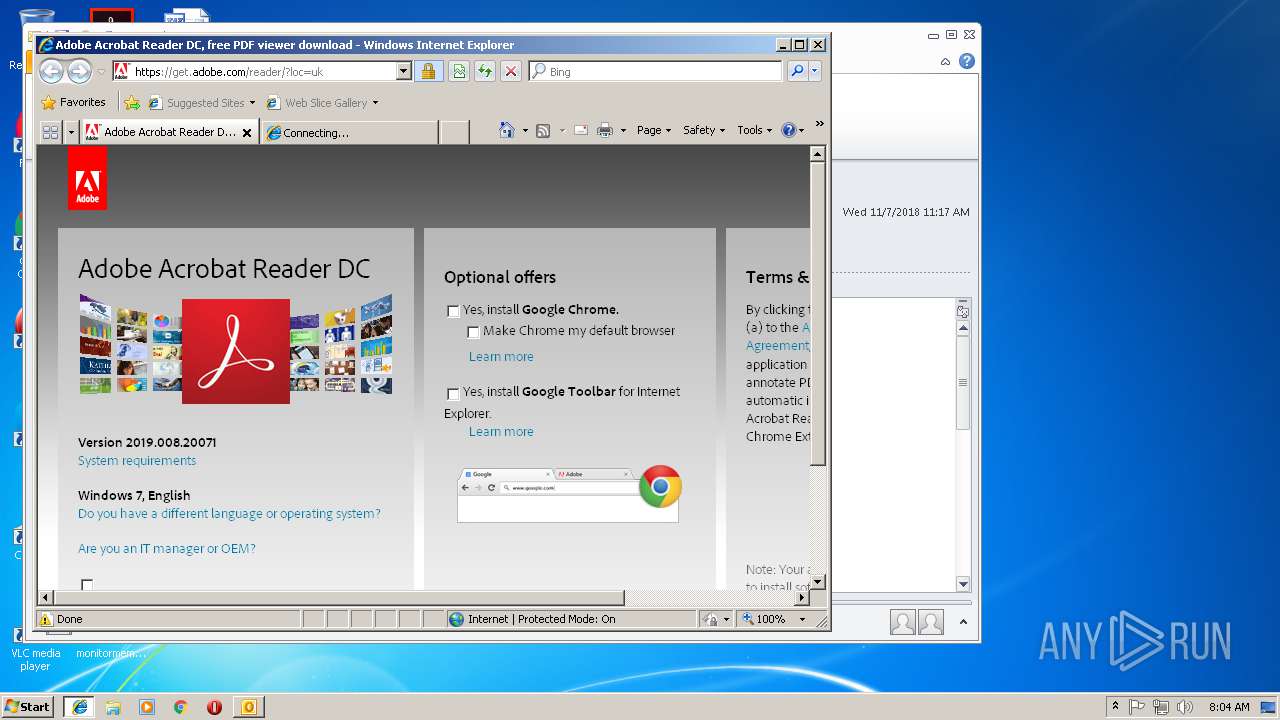
2072 | iexplore.exe | GET | 301 | 193.104.215.66:80 | http://get.adobe.com/uk/reader/ | unknown | html | 244 b | whitelisted |
3496 | iexplore.exe | GET | 200 | 23.0.35.131:80 | http://cdn.ek.aero/qubit/opentag-93989-1321710.js | NL | text | 36.3 Kb | whitelisted |
2072 | iexplore.exe | GET | 200 | 52.222.163.162:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
3496 | iexplore.exe | GET | 200 | 52.222.161.196:80 | http://cdn.appdynamics.com/adrum/adrum-4.5.0.773.js?r=cib-767a | US | text | 23.3 Kb | whitelisted |
1904 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2072 | iexplore.exe | 193.104.215.66:443 | get.adobe.com | Level 3 Communications, Inc. | — | malicious |
2072 | iexplore.exe | 54.164.20.167:443 | fonts.adobe.com | Amazon.com, Inc. | US | unknown |
2072 | iexplore.exe | 104.111.237.111:443 | wwwimages2.adobe.com | Akamai International B.V. | NL | whitelisted |
2072 | iexplore.exe | 172.227.13.196:443 | static-fonts.adobe.com | Akamai Technologies, Inc. | US | whitelisted |
2072 | iexplore.exe | 2.18.232.23:443 | assets.adobedtm.com | Akamai International B.V. | — | whitelisted |
2072 | iexplore.exe | 54.194.108.5:443 | adobe.demdex.net | Amazon.com, Inc. | IE | unknown |
3032 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2072 | iexplore.exe | 167.89.115.54:443 | u6863864.ct.sendgrid.net | SendGrid, Inc. | US | suspicious |
1904 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2072 | iexplore.exe | 193.104.215.66:80 | get.adobe.com | Level 3 Communications, Inc. | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
u6863864.ct.sendgrid.net |
| suspicious |
www.bing.com |
| whitelisted |
get.adobe.com |
| whitelisted |
wwwimages2.adobe.com |
| whitelisted |
fonts.adobe.com |
| whitelisted |
assets.adobedtm.com |
| whitelisted |
static-fonts.adobe.com |
| whitelisted |
dpm.demdex.net |
| whitelisted |
p.typekit.net |
| shared |