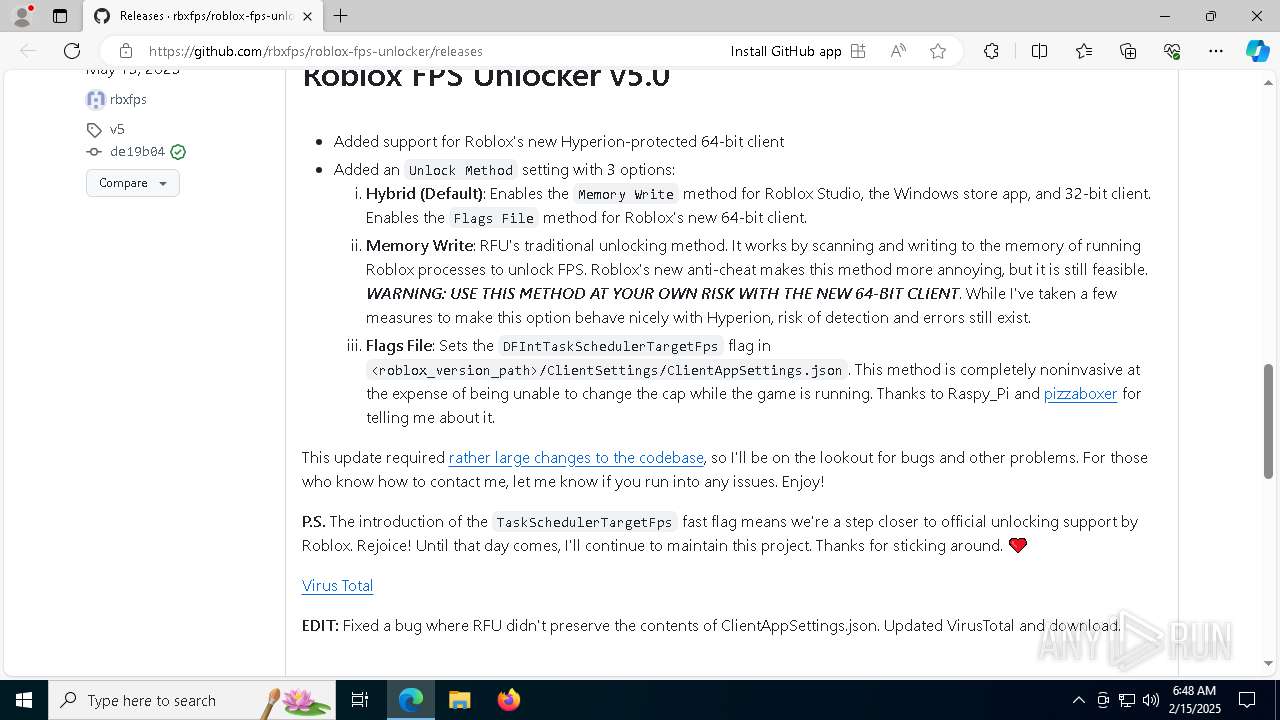
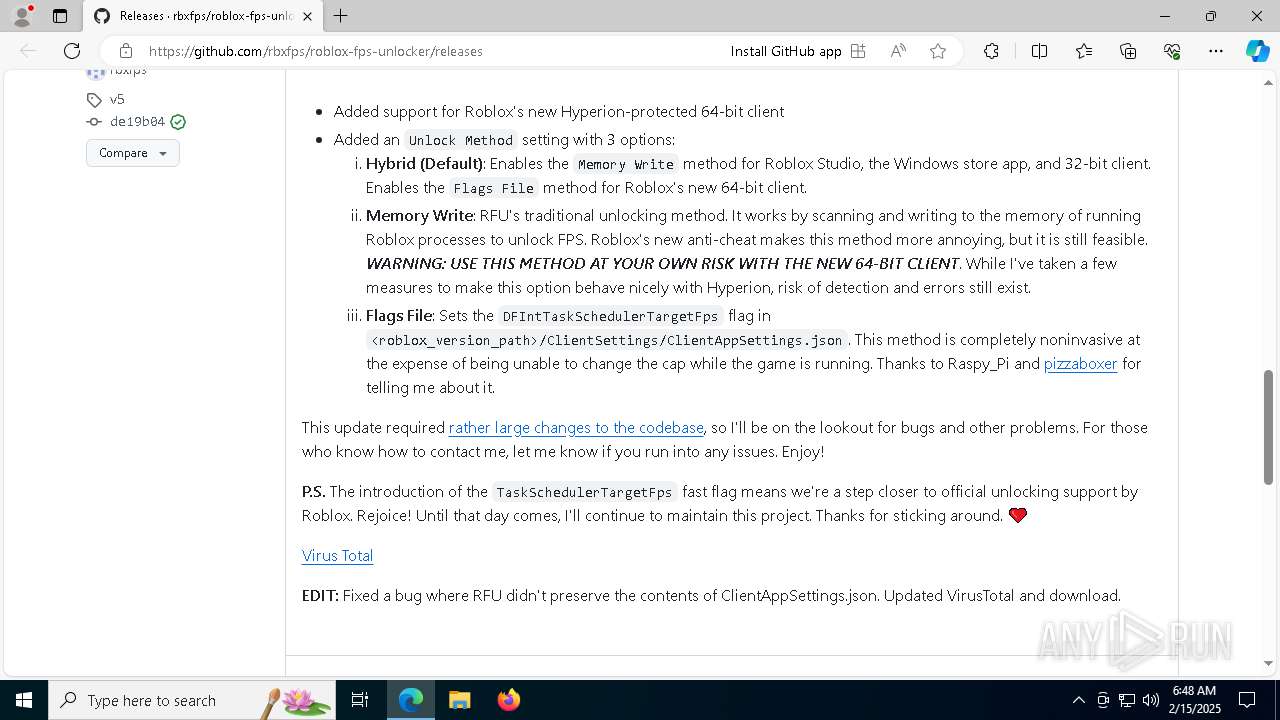
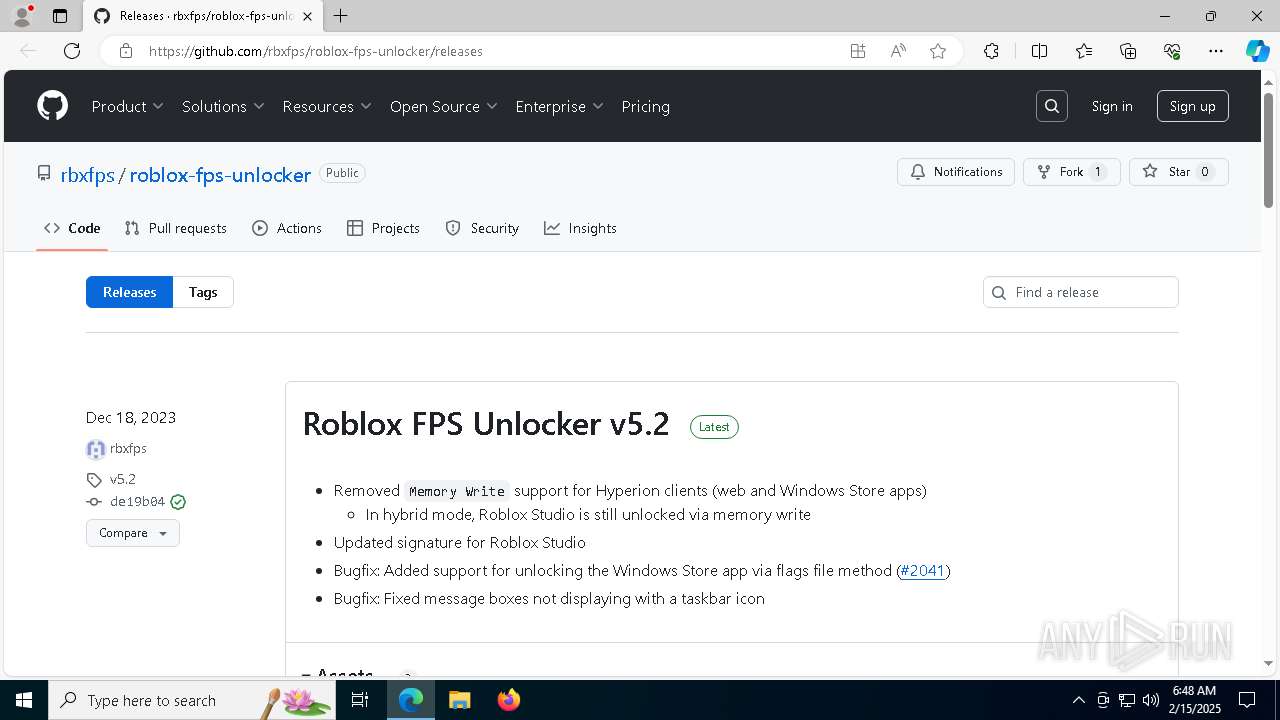
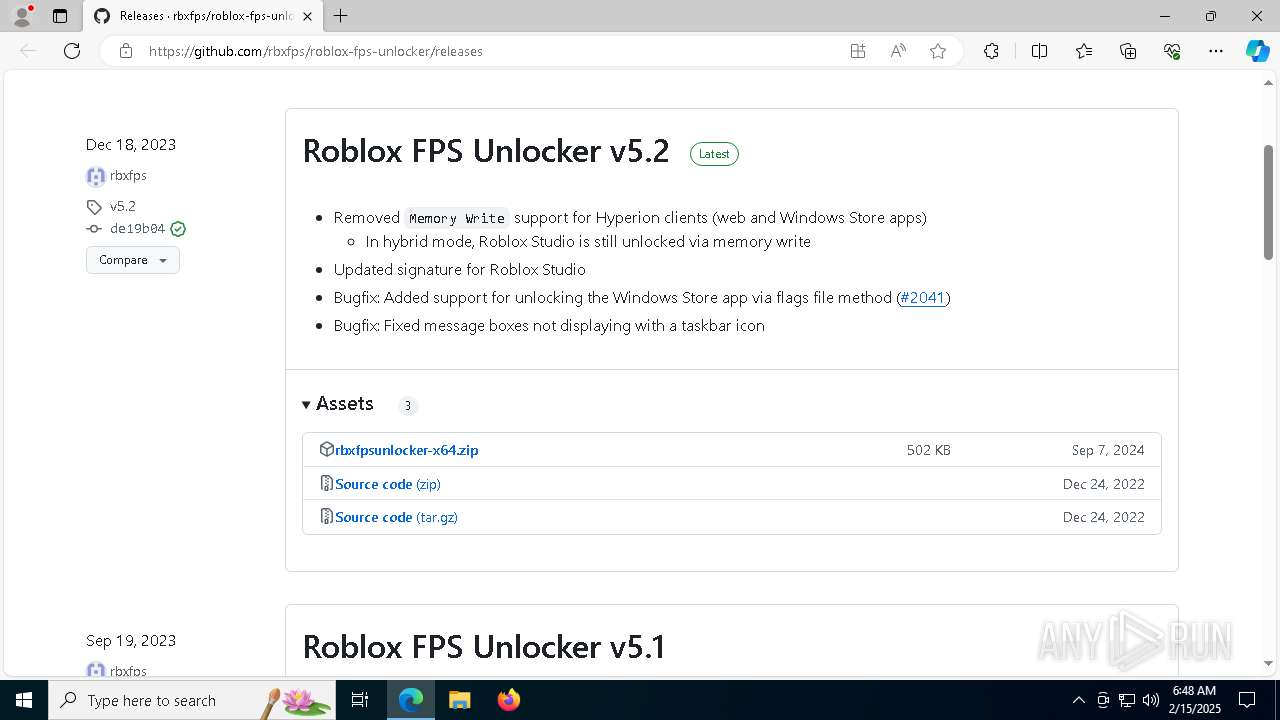
| URL: | https://github.com/rbxfps/roblox-fps-unlocker/releases |
| Full analysis: | https://app.any.run/tasks/64f30c3c-a329-42ac-a08f-1270ba7e48a0 |
| Verdict: | Malicious activity |
| Analysis date: | February 15, 2025, 06:48:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | EBF75787E58778185BE01CB0B89D67BE |
| SHA1: | 79CC29486AFE6CD89D0870358A261437C218833A |
| SHA256: | E1E990F7BF64409028EF021A6284C9A3489211C3593EF81352EE0A20D5D44A15 |
| SSDEEP: | 3:N8tEdn9Jr6e6XhE2n:2uFrSXhrn |
MALICIOUS
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7324)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7324)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7324)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7324)
Application was injected by another process
- svchost.exe (PID: 1176)
- explorer.exe (PID: 4488)
- svchost.exe (PID: 2944)
- svchost.exe (PID: 2500)
- svchost.exe (PID: 1128)
- svchost.exe (PID: 2748)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1768)
- svchost.exe (PID: 1564)
- svchost.exe (PID: 2360)
- svchost.exe (PID: 376)
- svchost.exe (PID: 2340)
- svchost.exe (PID: 4696)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 3160)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 2528)
- svchost.exe (PID: 3704)
- svchost.exe (PID: 1908)
- svchost.exe (PID: 3668)
- svchost.exe (PID: 2952)
- svchost.exe (PID: 1764)
- svchost.exe (PID: 2992)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 4456)
- svchost.exe (PID: 320)
- svchost.exe (PID: 2288)
- svchost.exe (PID: 2892)
- svchost.exe (PID: 4468)
- svchost.exe (PID: 1076)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 4436)
- svchost.exe (PID: 892)
- svchost.exe (PID: 2660)
- svchost.exe (PID: 2272)
- svchost.exe (PID: 2064)
- svchost.exe (PID: 1452)
- svchost.exe (PID: 1660)
- svchost.exe (PID: 1880)
- svchost.exe (PID: 1500)
- svchost.exe (PID: 1068)
- svchost.exe (PID: 3824)
- svchost.exe (PID: 3600)
- svchost.exe (PID: 1340)
- svchost.exe (PID: 1260)
- svchost.exe (PID: 1268)
- svchost.exe (PID: 4000)
- svchost.exe (PID: 4200)
- svchost.exe (PID: 3016)
- svchost.exe (PID: 2816)
- svchost.exe (PID: 2192)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 3592)
- svchost.exe (PID: 3976)
- svchost.exe (PID: 2364)
- svchost.exe (PID: 1424)
- svchost.exe (PID: 1612)
- svchost.exe (PID: 1972)
- svchost.exe (PID: 4168)
- svchost.exe (PID: 2852)
- svchost.exe (PID: 4176)
- svchost.exe (PID: 2372)
- svchost.exe (PID: 1276)
- svchost.exe (PID: 1776)
- svchost.exe (PID: 3164)
- svchost.exe (PID: 1784)
- svchost.exe (PID: 812)
- svchost.exe (PID: 1008)
Runs injected code in another process
- powershell.exe (PID: 7324)
Adds path to the Windows Defender exclusion list
- powershell.exe (PID: 7324)
SUSPICIOUS
Reads security settings of Internet Explorer
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Checks Windows Trust Settings
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Adds/modifies Windows certificates
- RbxFpsUnlocker.exe (PID: 7884)
Reads the date of Windows installation
- RbxFpsUnlocker.exe (PID: 7884)
Executing commands from a ".bat" file
- RbxFpsUnlocker.exe (PID: 7884)
- cmd.exe (PID: 8128)
Cryptography encrypted command line is found
- cmd.exe (PID: 7284)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 8128)
- RbxFpsUnlocker.exe (PID: 7884)
Application launched itself
- cmd.exe (PID: 8128)
- powershell.exe (PID: 7324)
Executable content was dropped or overwritten
- RbxFpsUnlocker.exe (PID: 7884)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7324)
Process checks specific path in scheduled tasks
- powershell.exe (PID: 5096)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 7324)
- cmd.exe (PID: 8128)
Probably obfuscated PowerShell command line is found
- powershell.exe (PID: 7324)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 7324)
INFO
Reads security settings of Internet Explorer
- svchost.exe (PID: 2364)
- explorer.exe (PID: 4488)
Application launched itself
- msedge.exe (PID: 4328)
Checks supported languages
- identity_helper.exe (PID: 2928)
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Reads Environment values
- identity_helper.exe (PID: 2928)
- RbxFpsUnlocker.exe (PID: 7884)
Reads the computer name
- identity_helper.exe (PID: 2928)
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7228)
Manual execution by a user
- RbxFpsUnlocker.exe (PID: 7836)
- RbxFpsUnlocker.exe (PID: 7884)
Reads the machine GUID from the registry
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Create files in a temporary directory
- RbxFpsUnlocker.exe (PID: 7884)
Creates files or folders in the user directory
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Checks proxy server information
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Reads the software policy settings
- RbxFpsUnlocker.exe (PID: 7884)
- rbx.exe (PID: 8172)
Checks if a key exists in the options dictionary (POWERSHELL)
- RbxFpsUnlocker.exe (PID: 7884)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 7576)
- powershell.exe (PID: 7832)
Process checks computer location settings
- RbxFpsUnlocker.exe (PID: 7884)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7324)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7324)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7324)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7324)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7832)
Creates files in the program directory
- svchost.exe (PID: 1076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
174
Monitored processes
111
Malicious processes
4
Suspicious processes
67
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | C:\WINDOWS\system32\svchost.exe -k RPCSS -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s gpsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s DsmSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNoNetwork -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1176 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wlidsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1260 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s TimeBrokerSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
85 138
Read events
84 430
Write events
451
Delete events
257
Modification events
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000B022A |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000005030E |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E0A617F5BE8C2F00 | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: ACAF29F5BE8C2F00 | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721450 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {1C83C3EC-8DA8-4456-8EB1-48A553368A74} | |||
| (PID) Process: | (4328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721450 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {49BD66B9-9435-4F87-896A-6BA6D542B6C5} | |||
Executable files
10
Suspicious files
345
Text files
57
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1364a9.TMP | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1364b8.TMP | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1364b8.TMP | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1364c8.TMP | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1364c8.TMP | — | |
MD5:— | SHA256:— | |||
| 4328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
78
DNS requests
72
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7448 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7448 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1224 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8172 | rbx.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
7884 | RbxFpsUnlocker.exe | GET | 200 | 3.160.39.124:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSoEwb5tith0jIBy9frSyNGB1lsAAQUNr1J%2FzEs669qQP6ZwBbtuvxI3V8CEC5PS6JcFeO7CIfoudHuK%2F8%3D | unknown | — | — | whitelisted |
8172 | rbx.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
6372 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4328 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6372 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
github.com |
| whitelisted |