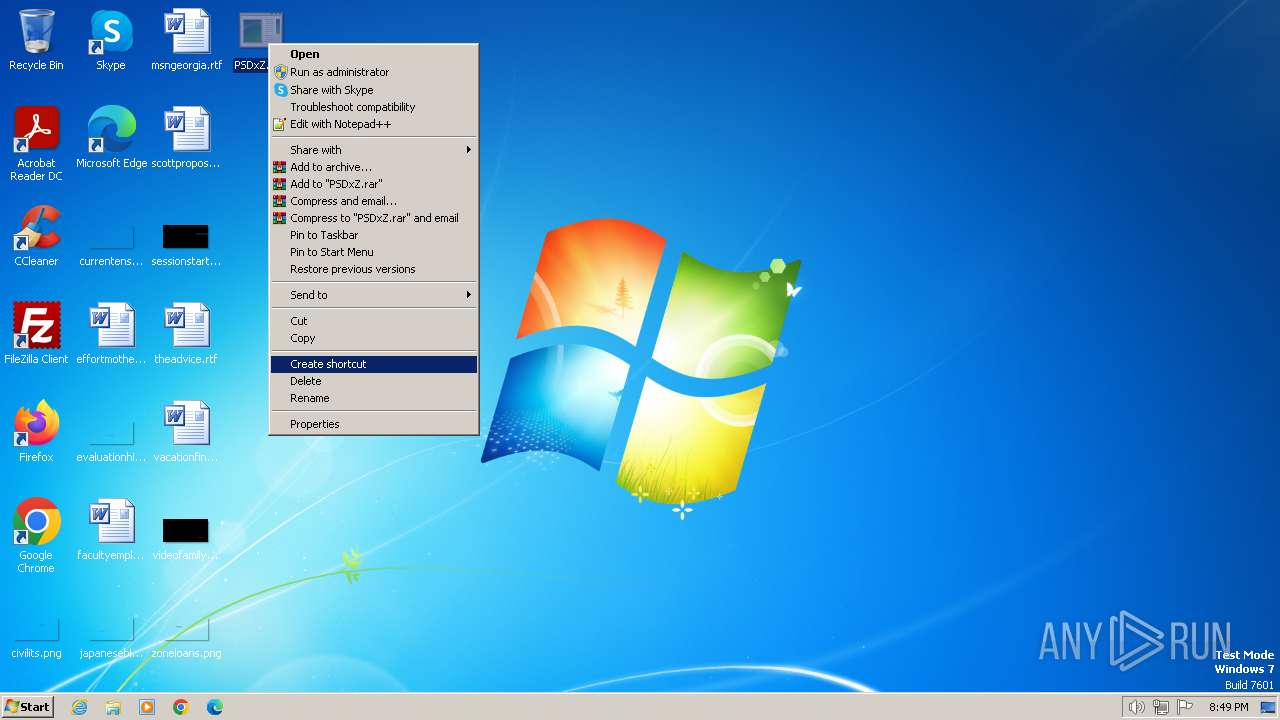
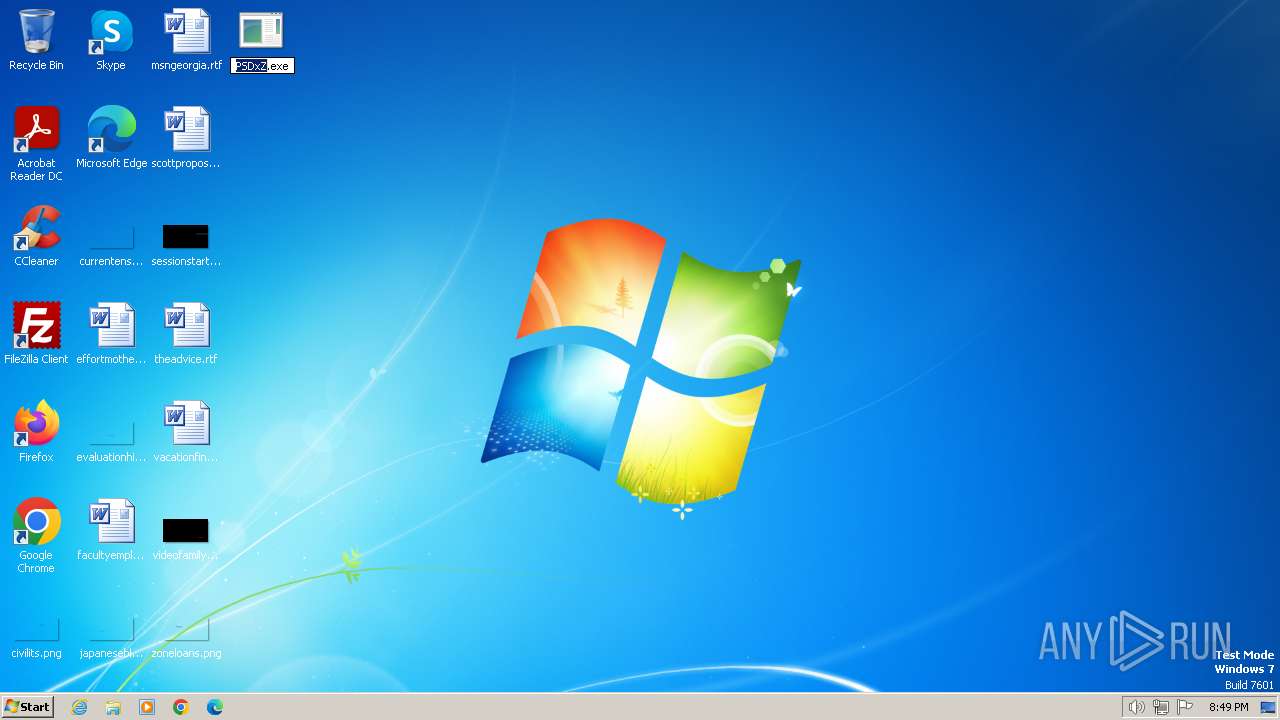
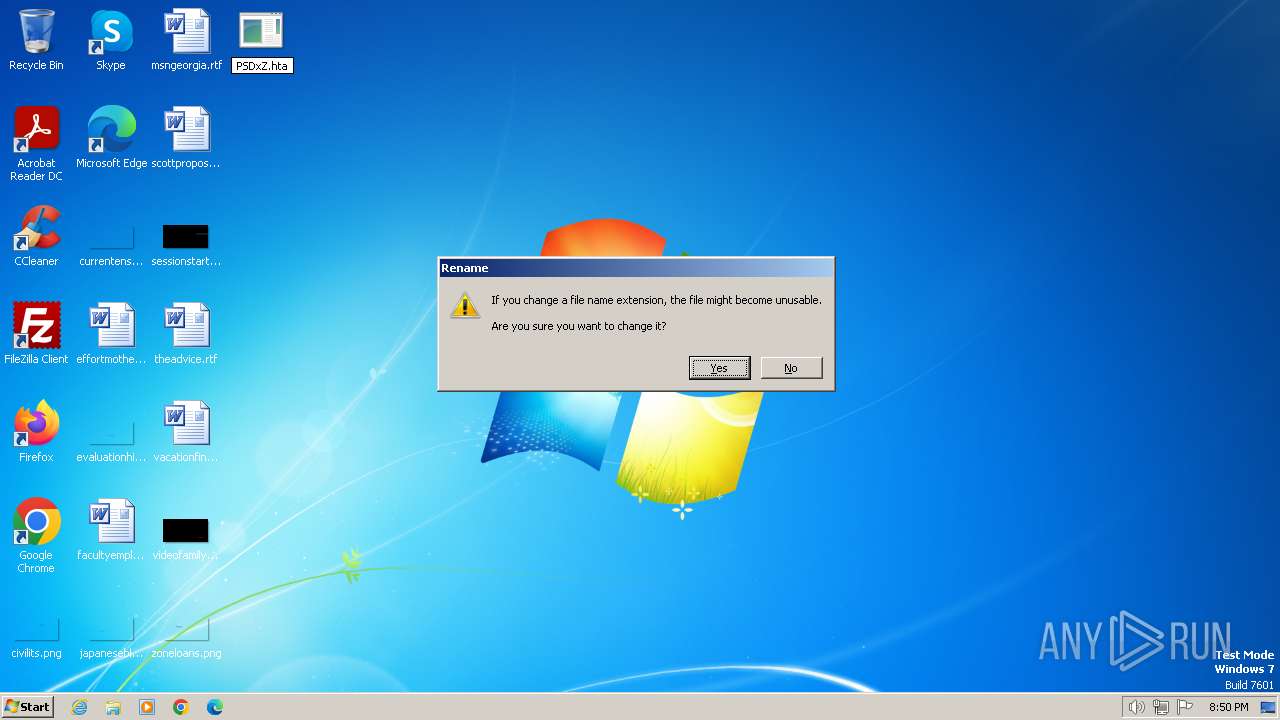
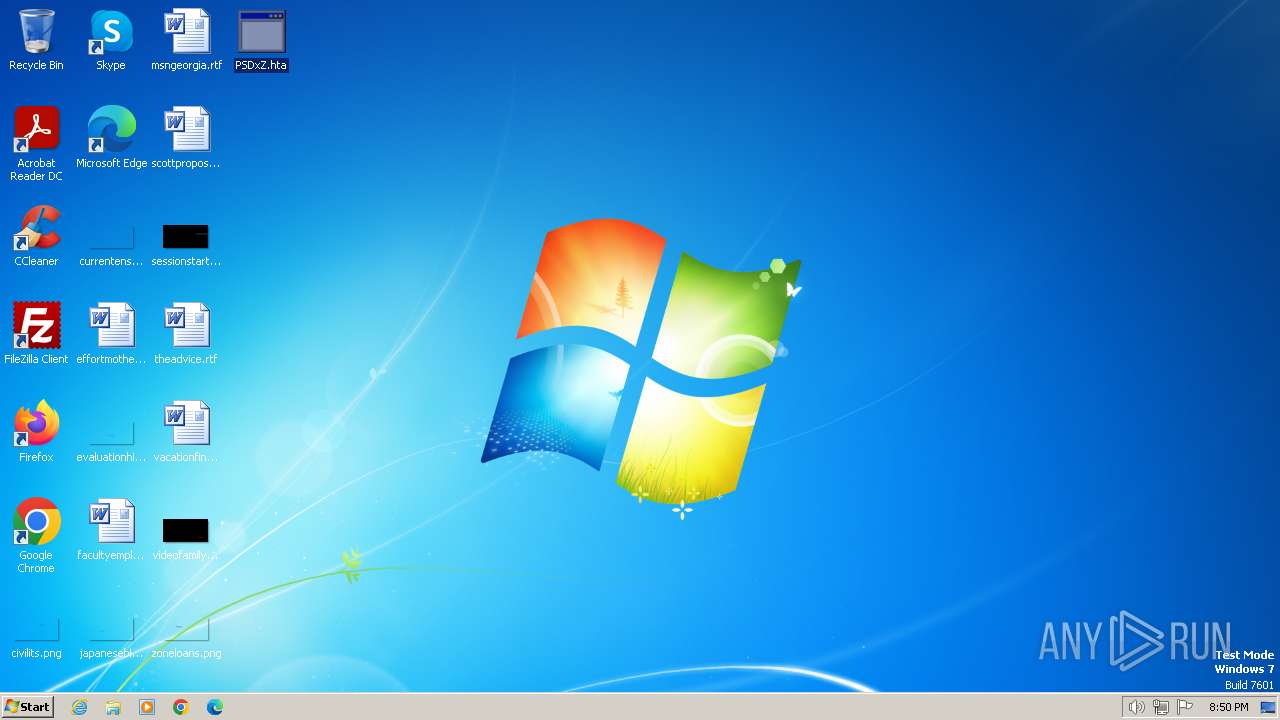
| download: | /PSDxZ |
| Full analysis: | https://app.any.run/tasks/644055d0-1ddc-457b-be1d-303a2f635092 |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2024, 20:47:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 5992424DDFCC2709B91FA8F9E025A807 |
| SHA1: | 0427D21B367DCA9BCFD0A20BC6EB495DC6BE2303 |
| SHA256: | E1D7A95E95C96E339A85A1445B6AAE04464CE8DCE359A0CA1FDAF7F939A3B245 |
| SSDEEP: | 768:ovb25dCMB6hI1sSRRMTCDGzdUkHgSN9SS8j9L3eeIHg0CEjuKWDUUN8/92DdNswn:ovkdptp0CEKjO9AR5ShN3F |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 2060)
Run PowerShell with an invisible window
- powershell.exe (PID: 2320)
Drops the executable file immediately after the start
- powershell.exe (PID: 1864)
SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 2472)
- mshta.exe (PID: 2060)
- powershell.exe (PID: 1864)
Suspicious use of symmetric encryption in PowerShell
- mshta.exe (PID: 2060)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 2060)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 2060)
- powershell.exe (PID: 2320)
Base64-obfuscated command line is found
- mshta.exe (PID: 2060)
Application launched itself
- powershell.exe (PID: 2320)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1864)
Executing commands from a ".bat" file
- powershell.exe (PID: 1864)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2668)
- cmd.exe (PID: 1540)
- cmd.exe (PID: 3556)
- cmd.exe (PID: 128)
- cmd.exe (PID: 1936)
- cmd.exe (PID: 1636)
The Powershell connects to the Internet
- powershell.exe (PID: 1864)
Unusual connection from system programs
- powershell.exe (PID: 1864)
Executable content was dropped or overwritten
- powershell.exe (PID: 1864)
INFO
Manual execution by a user
- mshta.exe (PID: 2060)
- csrstub.exe (PID: 4004)
- notepad++.exe (PID: 2364)
- ntvdm.exe (PID: 2964)
Reads Internet Explorer settings
- mshta.exe (PID: 2060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
73
Monitored processes
26
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Windows\system32\cmd.exe" /c "REG DELETE HKEY_CURRENT_USER\Software\Classes\MS-Settings /F && REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | REG ADD HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT\Shell\Open\Command /VE /T REG_SZ /D "C:\Users\admin\AppData\Local\Temp\r.bat" /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | REG ADD HKEY_CURRENT_USER\Software\Classes\MS-Settings\CurVer /VE /T REG_SZ /D "ServiceHostXGRT" /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | REG DELETE HKEY_CURRENT_USER\Software\Classes\MS-Settings /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1484 | REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1540 | "C:\Windows\system32\cmd.exe" /c "REG DELETE HKEY_CURRENT_USER\Software\Classes\MS-Settings /F && REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1636 | "C:\Windows\system32\cmd.exe" /c "REG DELETE HKEY_CURRENT_USER\Software\Classes\MS-Settings /F && REG DELETE HKEY_CURRENT_USER\Software\Classes\ServiceHostXGRT /F" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1792 | REG ADD HKEY_CURRENT_USER\Software\Classes\MS-Settings\CurVer /VE /T REG_SZ /D "ServiceHostXGRT" /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1864 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
9 455
Read events
9 384
Write events
53
Delete events
18
Modification events
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: Firefox | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (2472) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
Executable files
1
Suspicious files
4
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsFE42.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 3996 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsFE41.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2364 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:75DAF0C838CA0F9DAA89D4074A504E1B | SHA256:97901B6DEF410AA997B0E91A0FD0947EB3A26B7D5C83FD7228FDE04F981AC53C | |||
| 2320 | powershell.exe | C:\Users\admin\AppData\Local\Temp\fvh1uhyu.yhx.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kmniyvsx.pvz.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\fpetg2mv.kbc.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2320 | powershell.exe | C:\Users\admin\AppData\Local\Temp\zouxmsui.zpg.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2364 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:CB05223E6043E54EE9967CE904F8237B | SHA256:BDDCD4B42B2F268FF498CC39EB0A22AAA8C06422D6BEA64CE8D156C38A68DF95 | |||
| 1864 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\psdxz.exe | executable | |
MD5:38960D94FE970430CA9120F8539C1891 | SHA256:238D33F22277016B0F7078B2C643D3961B7EE4A021E8E22C1320C067B335845E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1864 | powershell.exe | 169.150.247.37:443 | transparency.b-cdn.net | — | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
transparency.b-cdn.net |
| unknown |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|