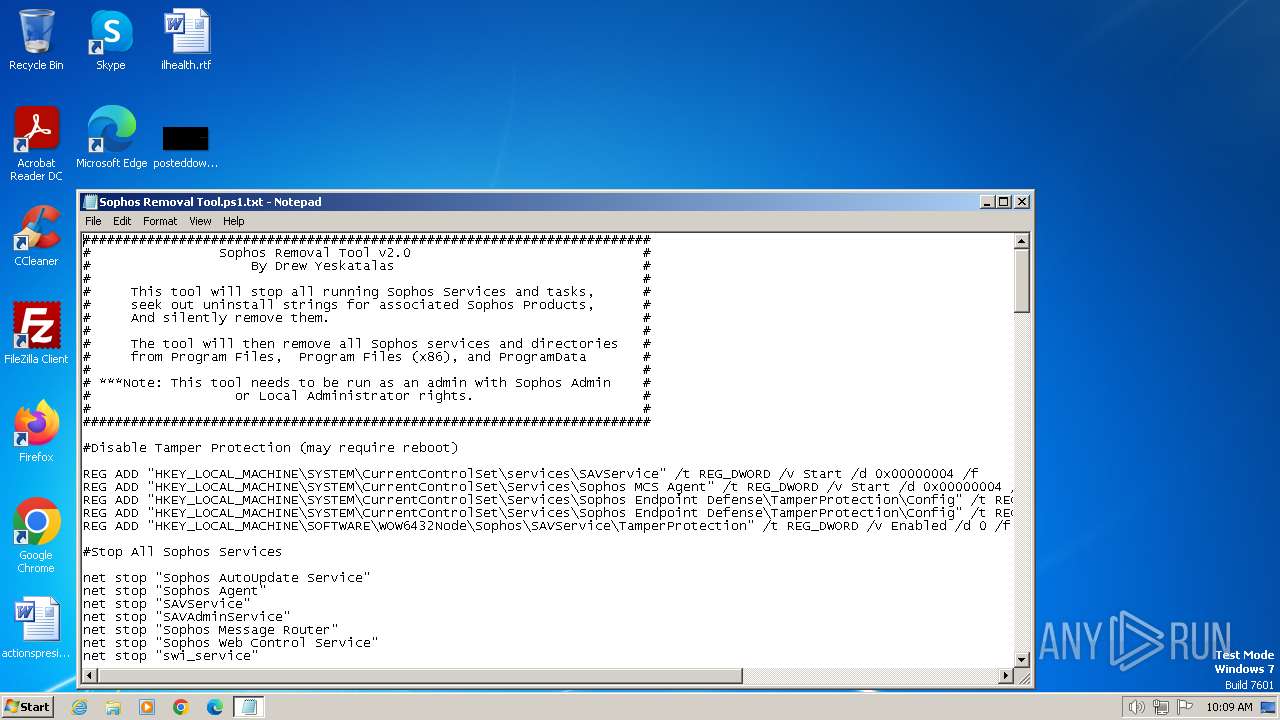
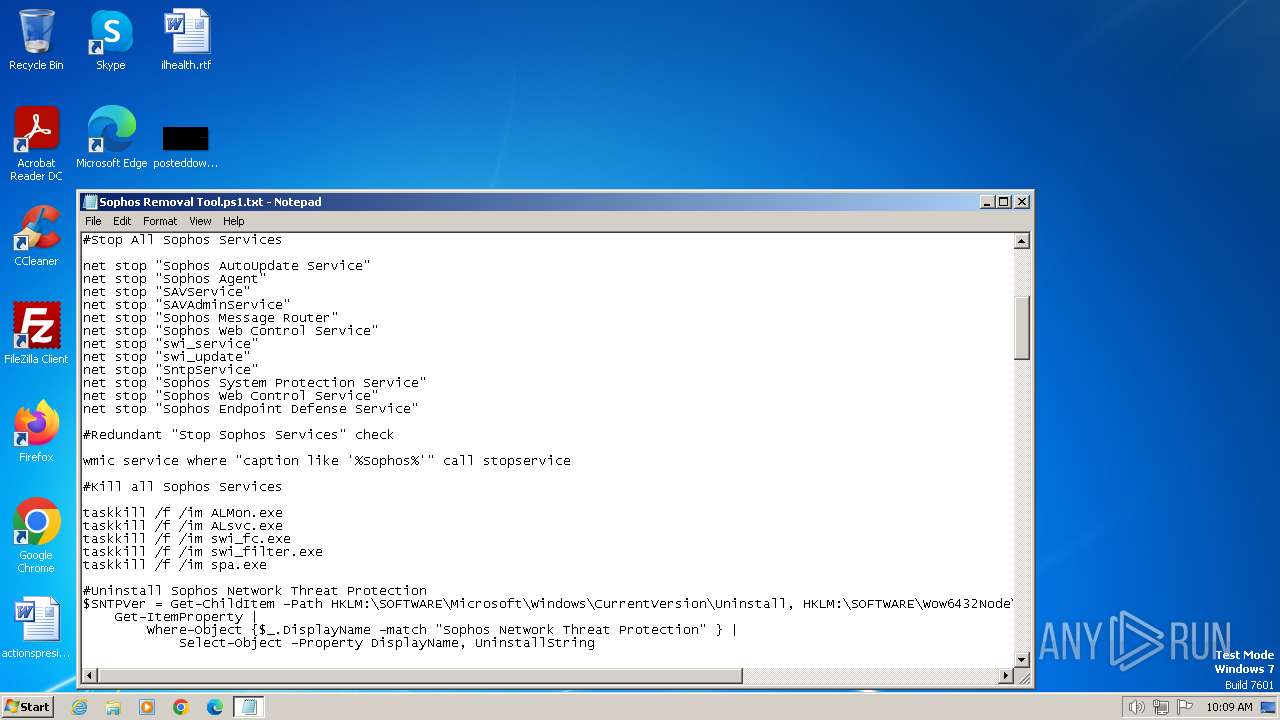
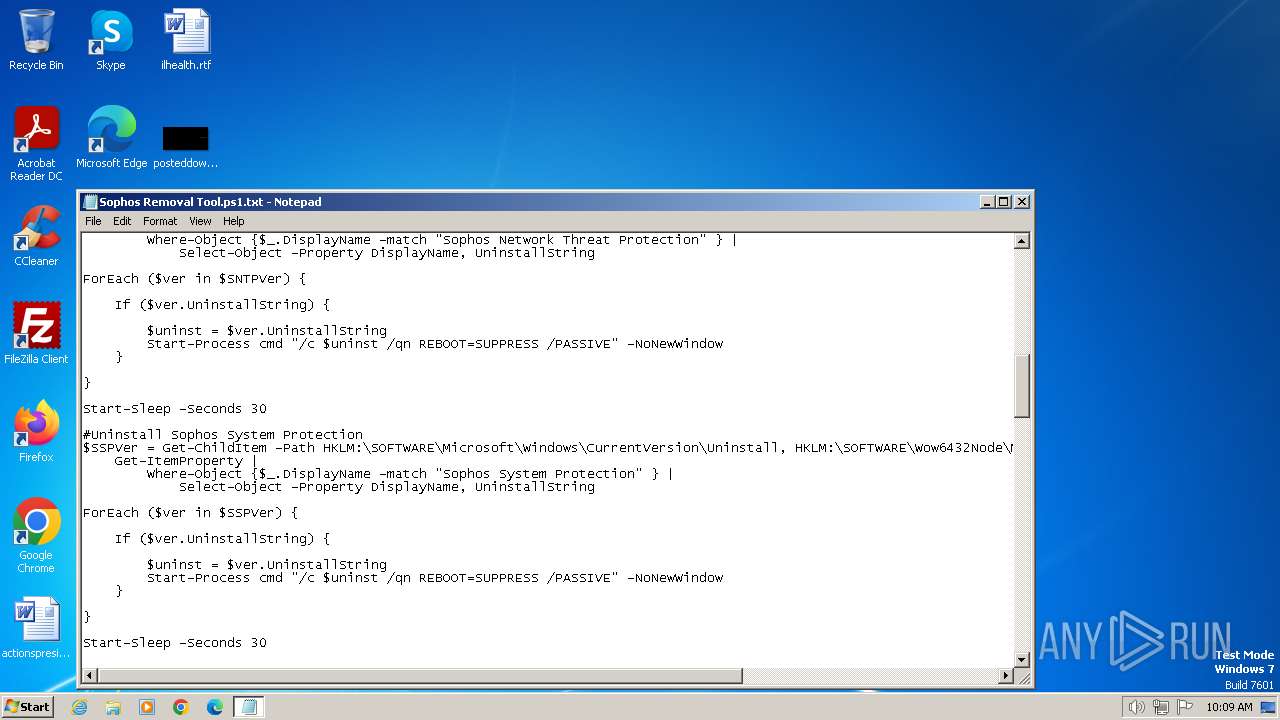
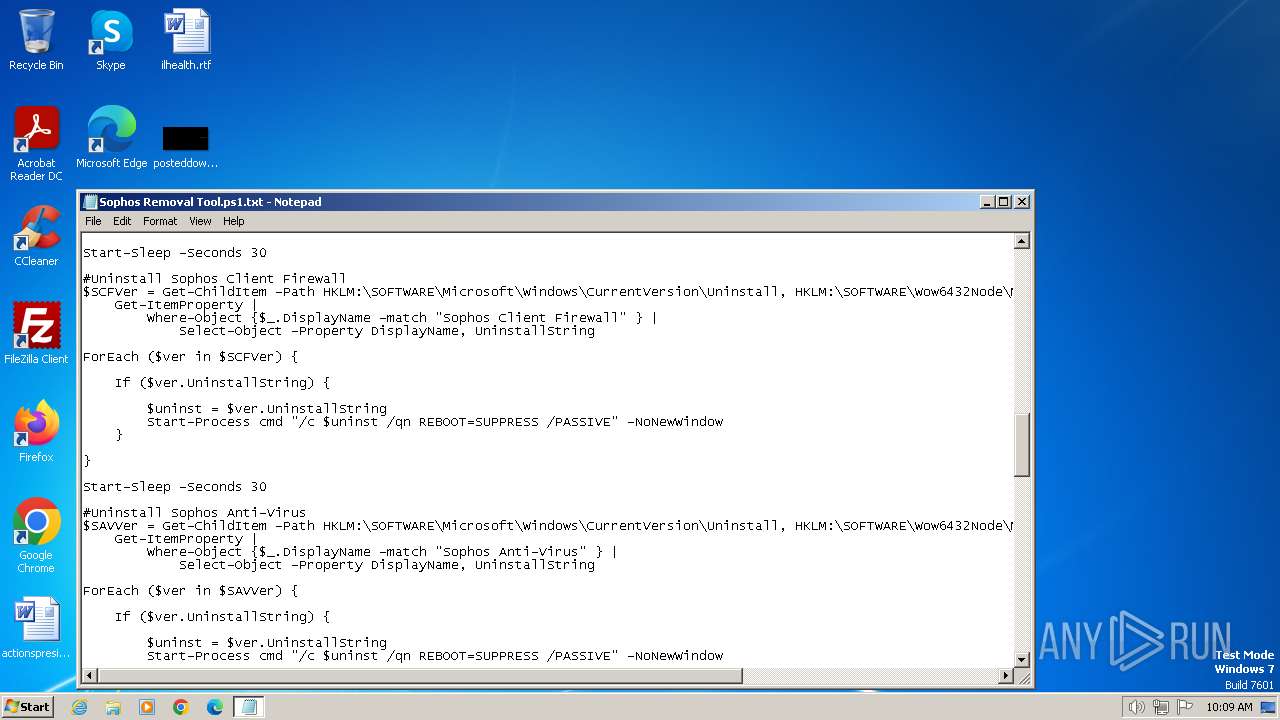
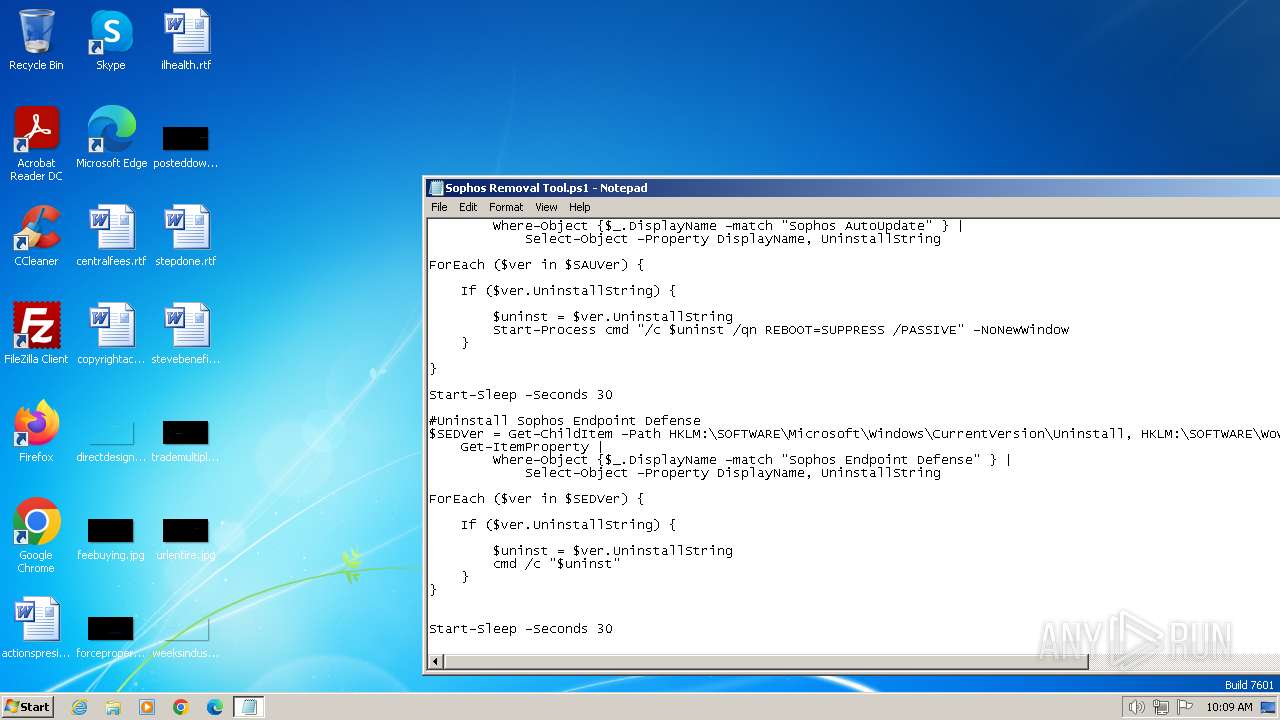
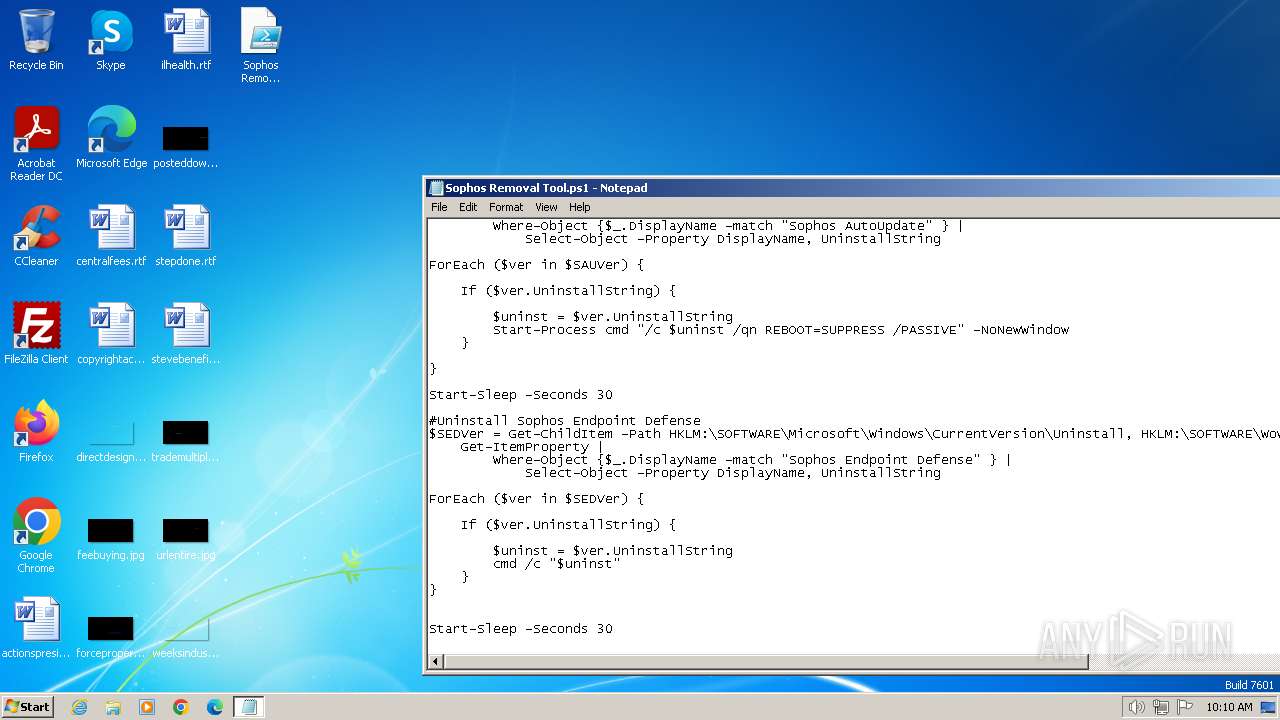
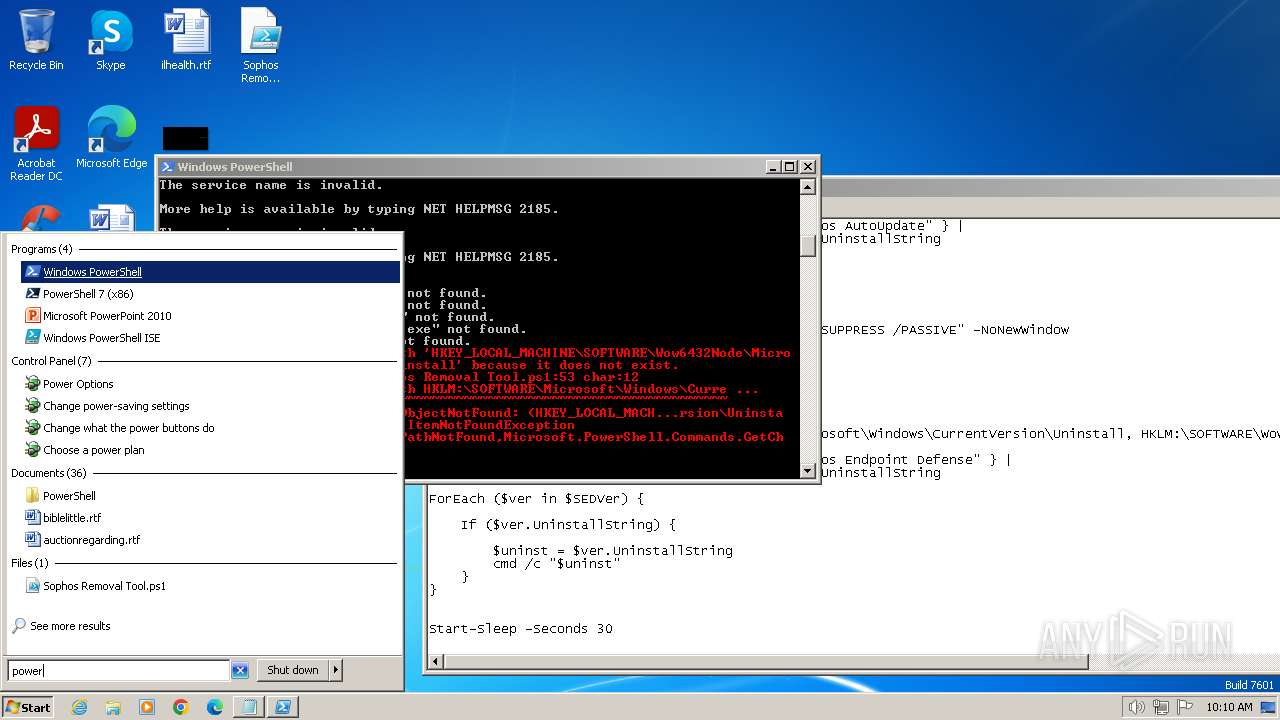
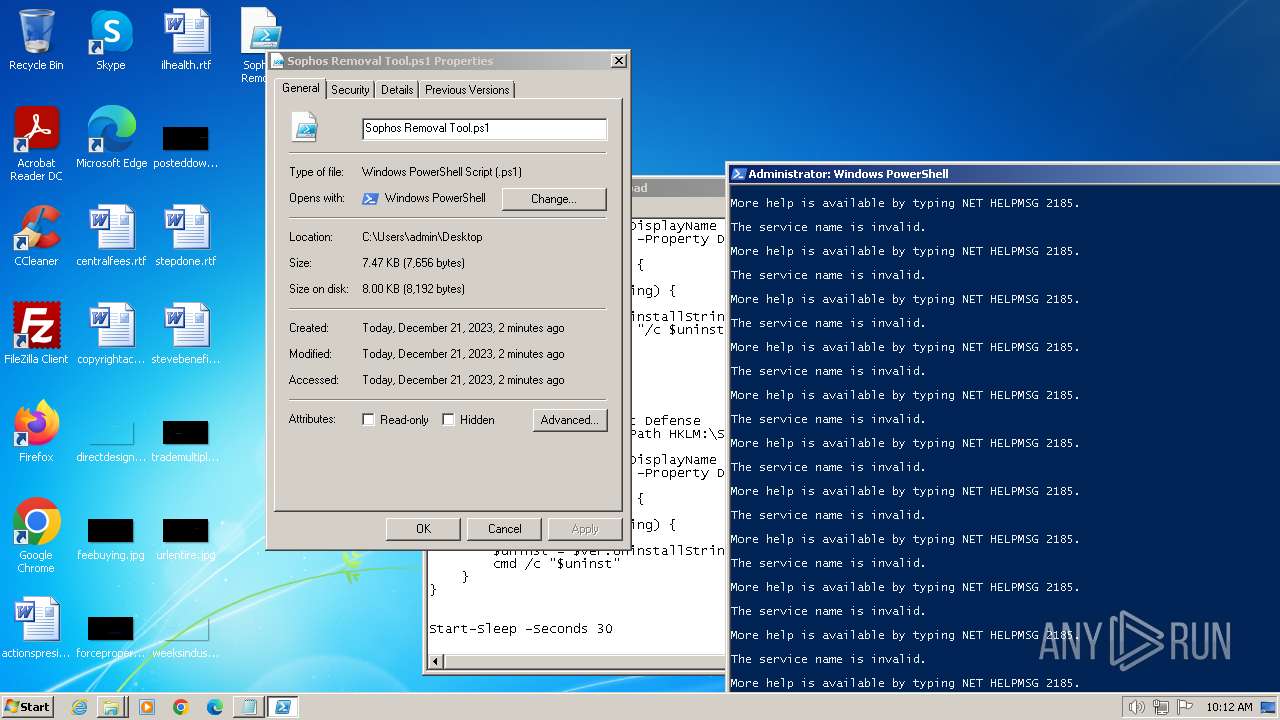
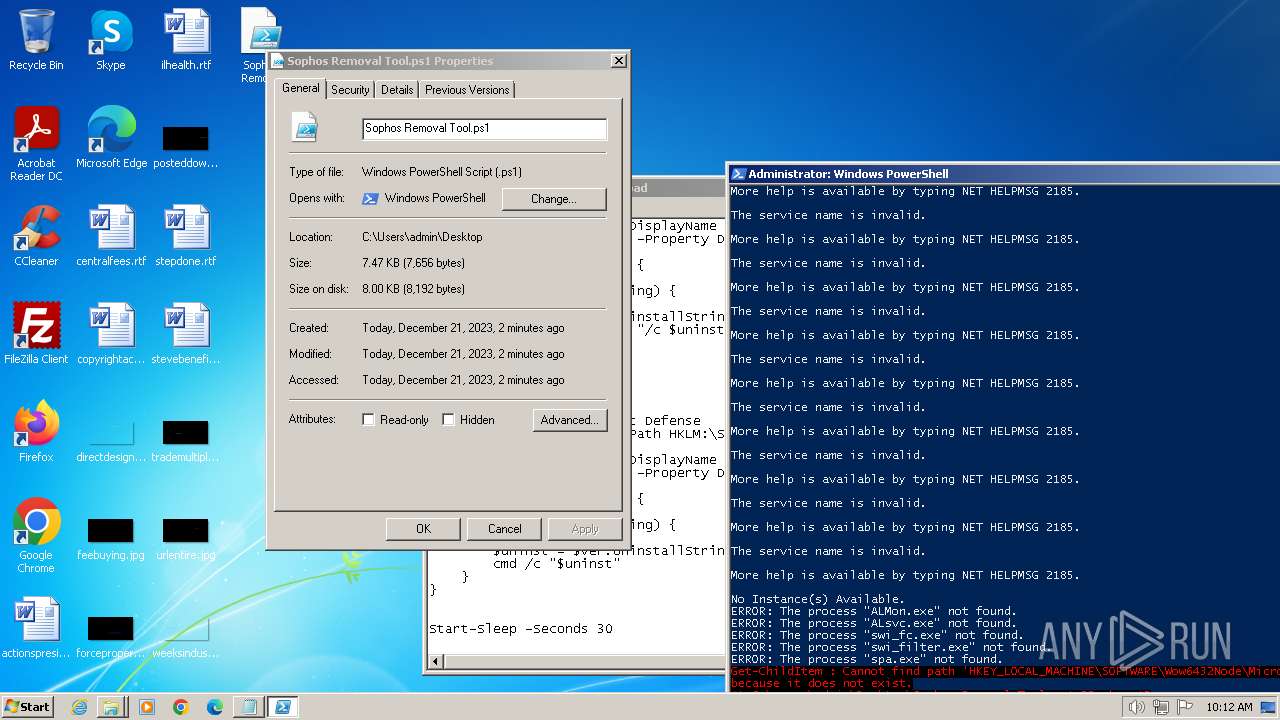
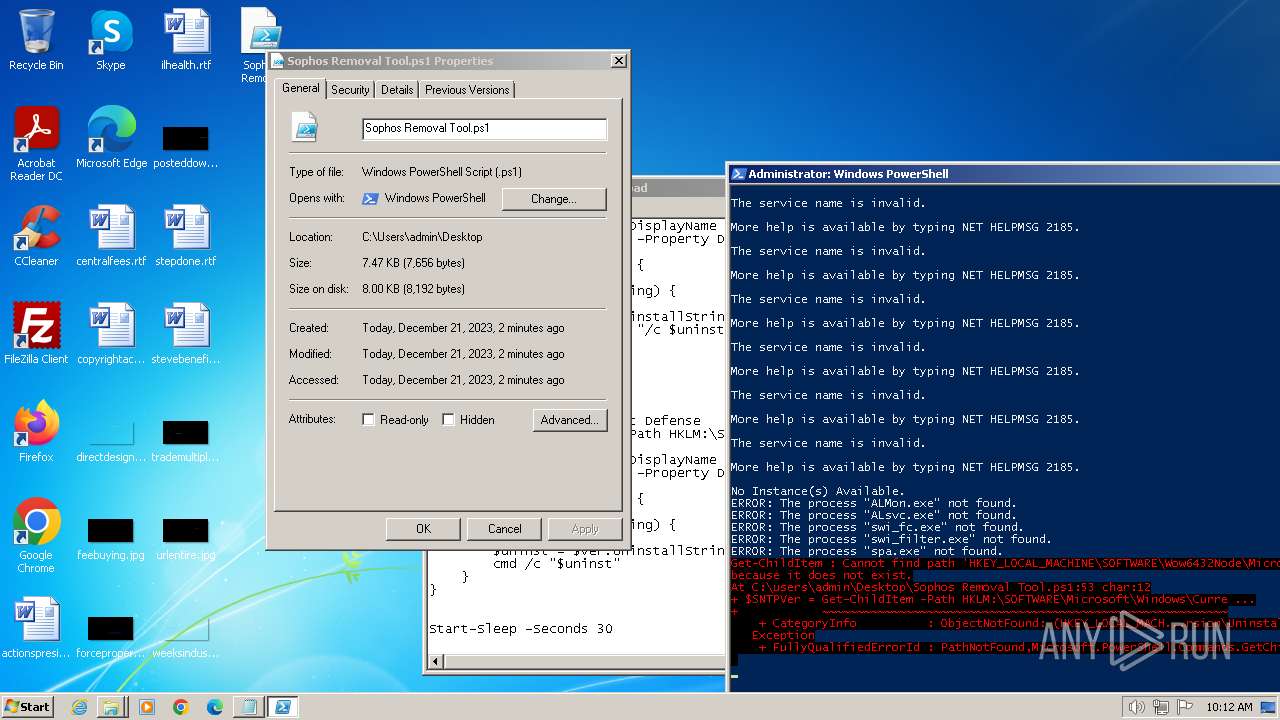
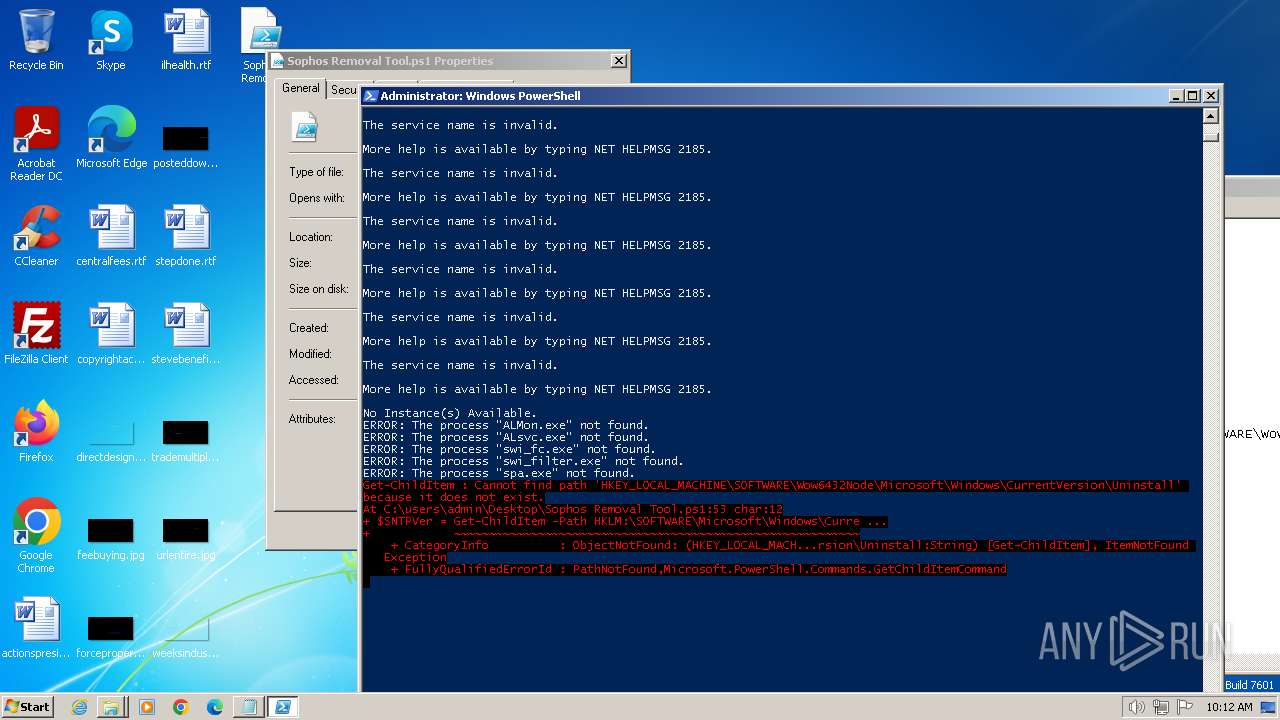
| File name: | Sophos Removal Tool.ps1 |
| Full analysis: | https://app.any.run/tasks/b074bc27-1ddb-4bcc-a77e-8b195718b36f |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2023, 10:09:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | UTF-8 Unicode (with BOM) text, with CRLF line terminators |
| MD5: | AC87D3612F7AF8E17105CF9E7580272A |
| SHA1: | 9ECE8431F6D86242DA1B32D99700C9D44949D00B |
| SHA256: | E1D459E568068BAE8DB668A9478E7D373AFDA5A174F2EA54A329056F5D6B681B |
| SSDEEP: | 96:ySMbc1wilDi+0+z+D+D+a+Ax+fqGlDugI:ySMbc1wsDDmlDugI |
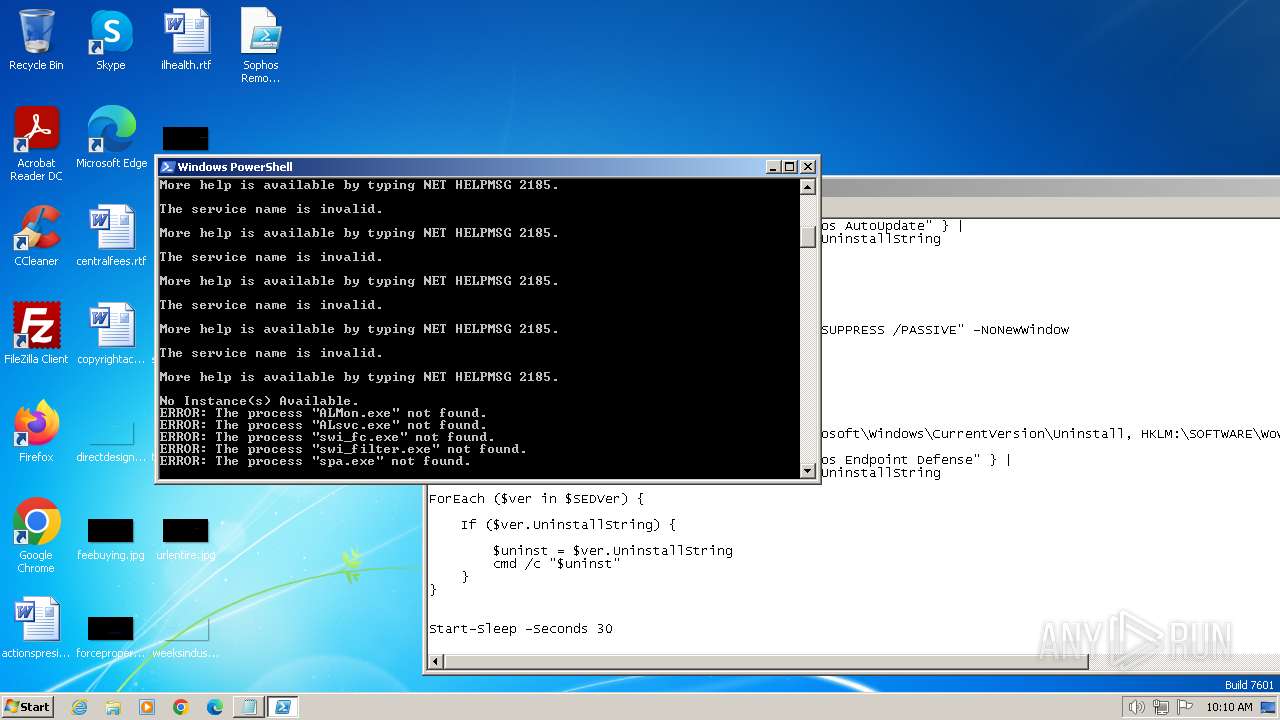
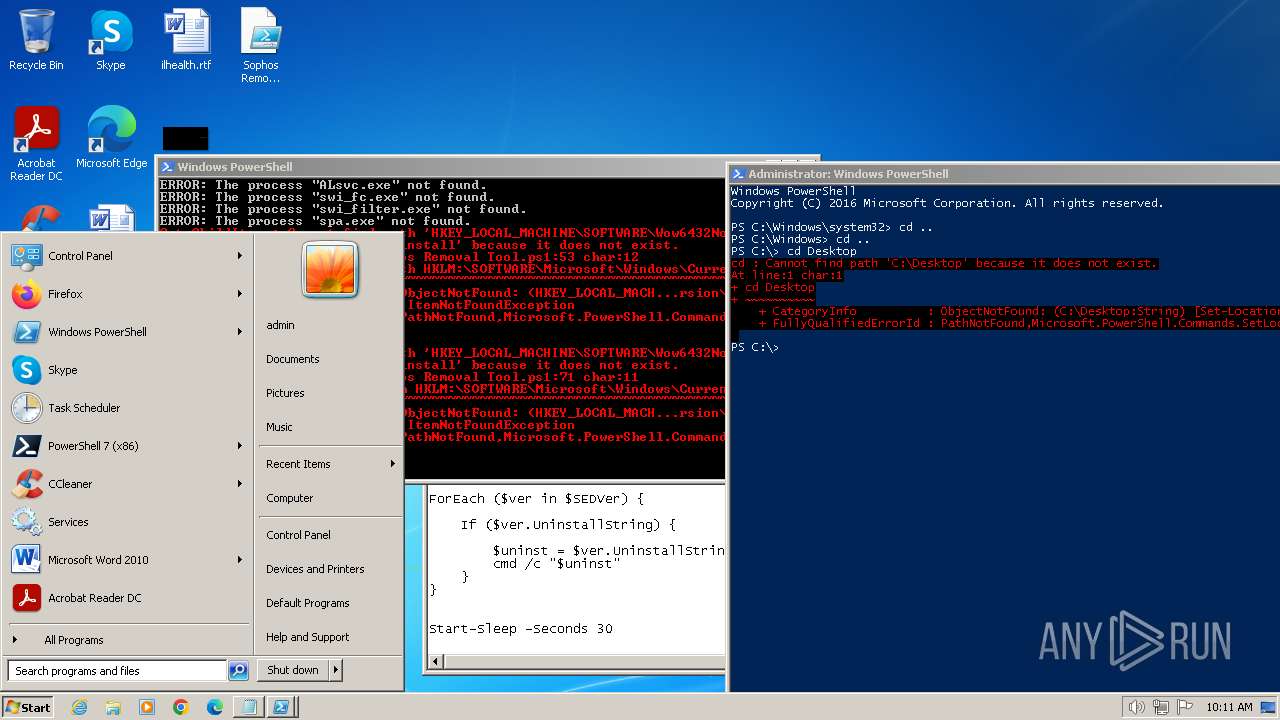
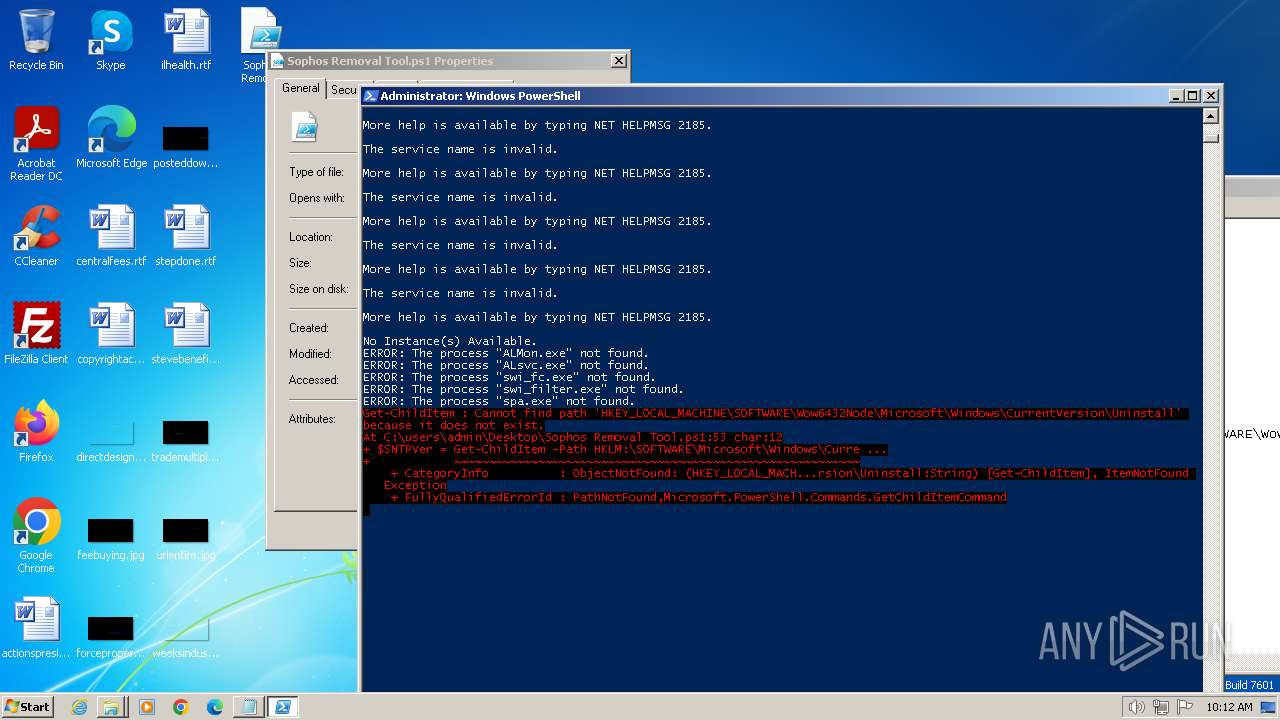
MALICIOUS
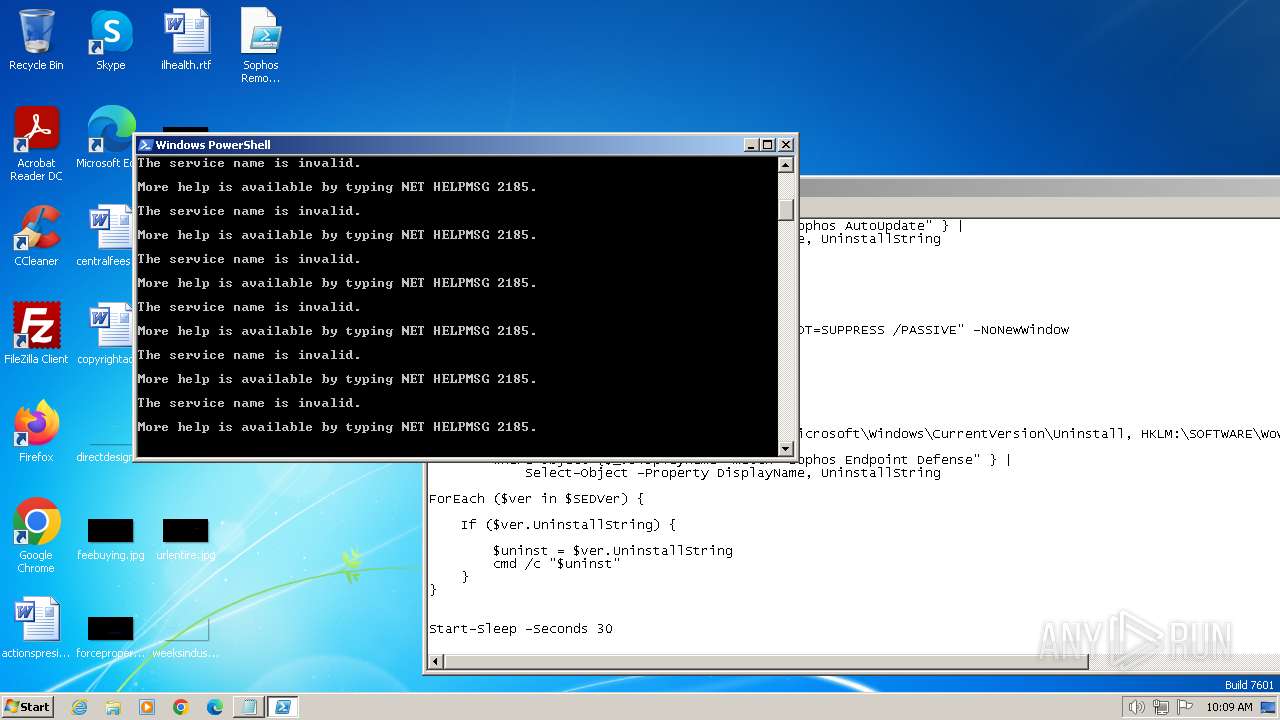
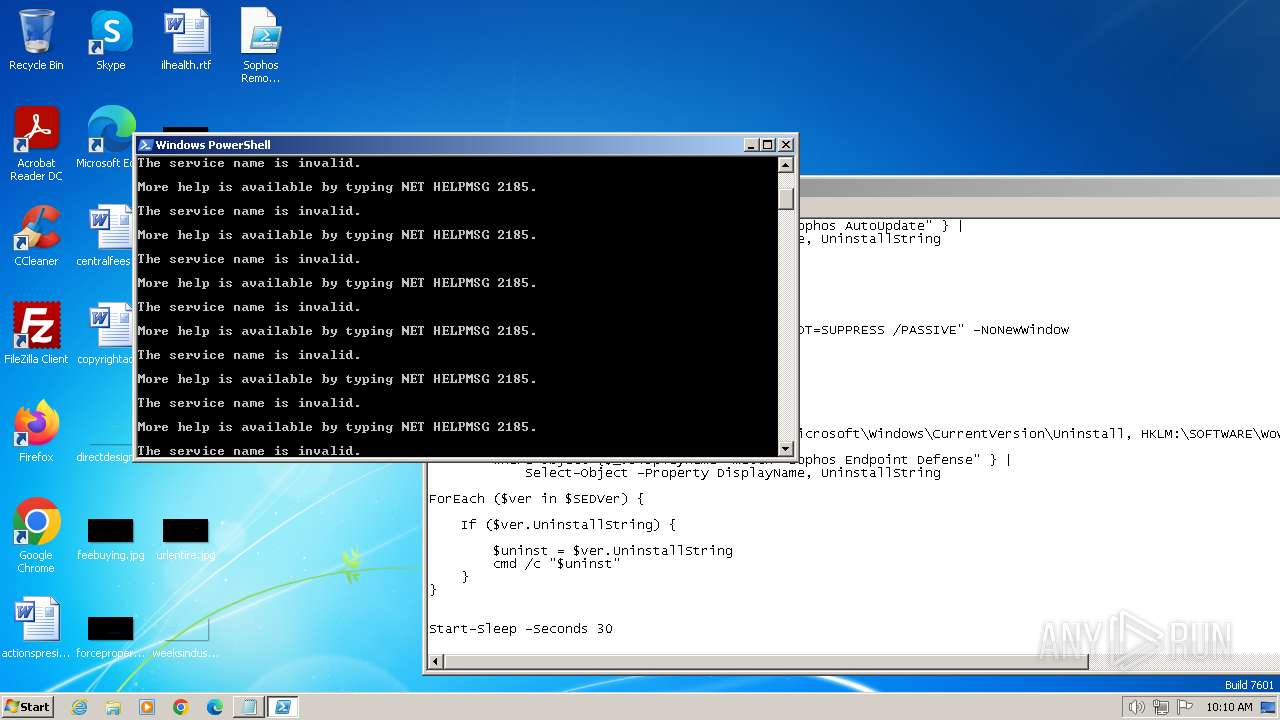
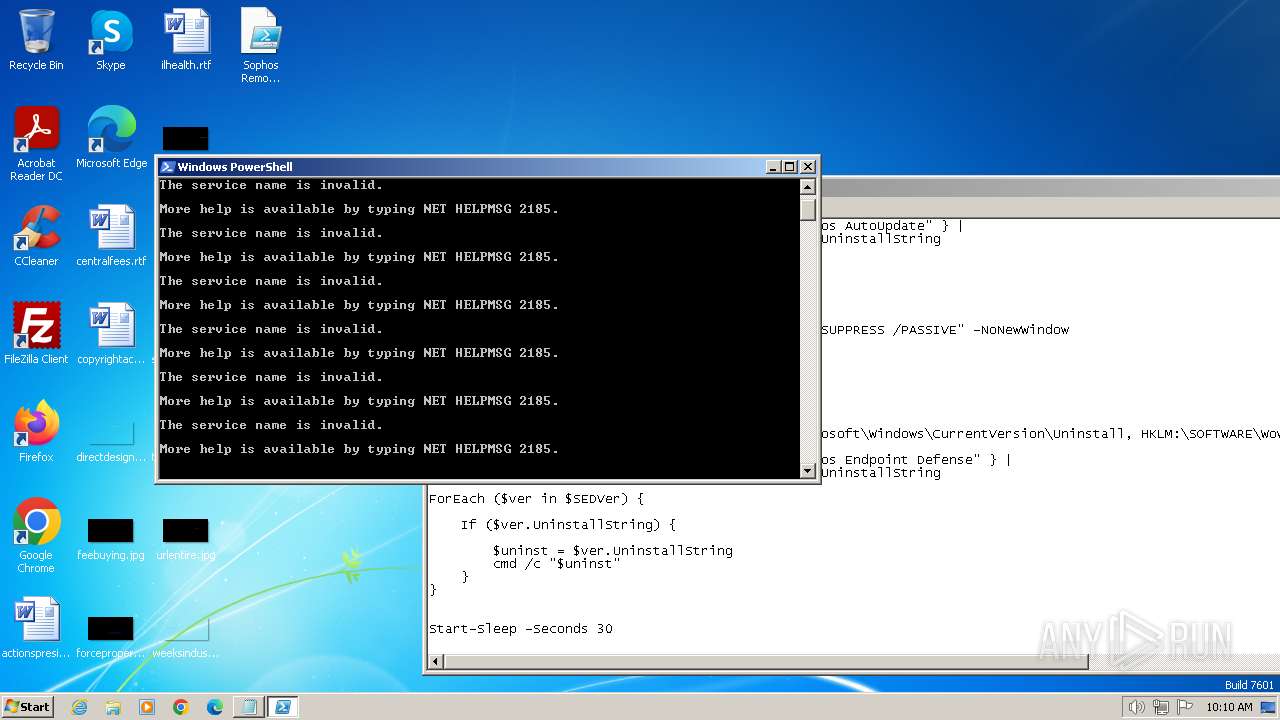
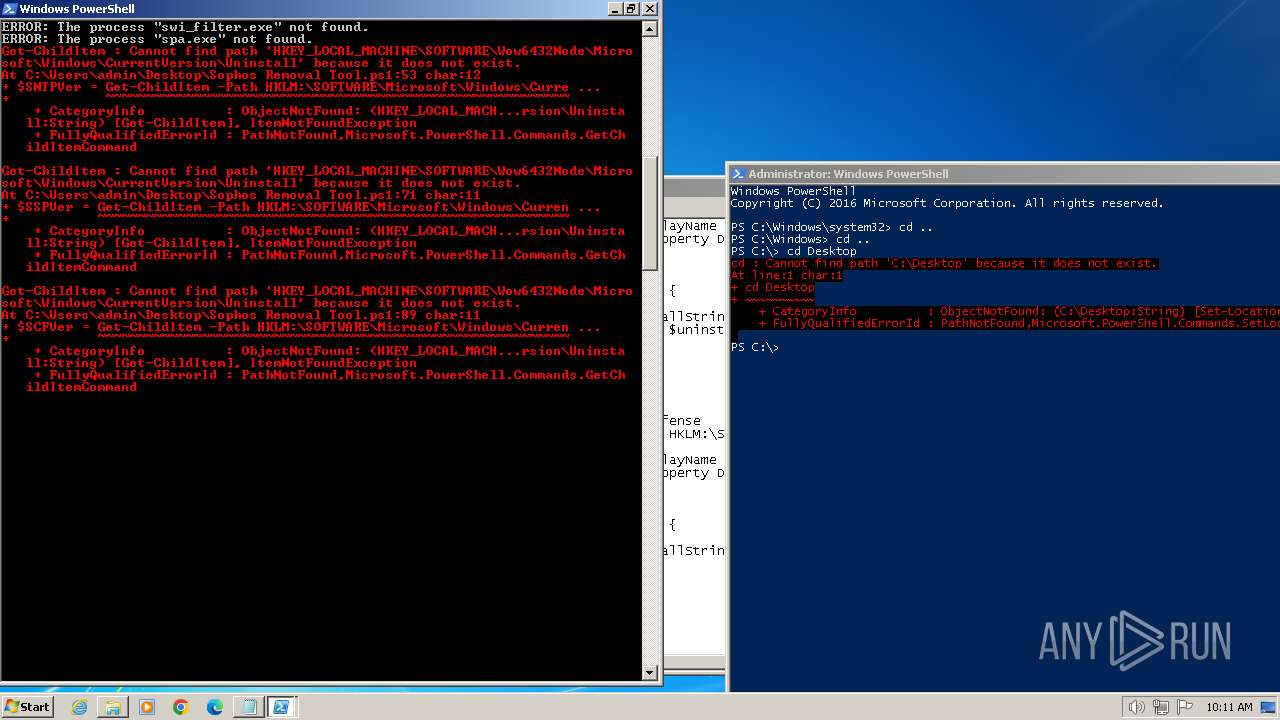
Starts NET.EXE for service management
- net.exe (PID: 1792)
- net.exe (PID: 1928)
- net.exe (PID: 1544)
- net.exe (PID: 2480)
- powershell.exe (PID: 1632)
- net.exe (PID: 2384)
- net.exe (PID: 1844)
- net.exe (PID: 2300)
- net.exe (PID: 2440)
- net.exe (PID: 2624)
- net.exe (PID: 2028)
- net.exe (PID: 2740)
- net.exe (PID: 996)
- net.exe (PID: 3068)
- powershell.exe (PID: 1196)
- net.exe (PID: 2968)
- net.exe (PID: 2880)
- net.exe (PID: 3020)
- net.exe (PID: 3048)
- net.exe (PID: 2460)
- net.exe (PID: 1028)
- net.exe (PID: 2676)
- net.exe (PID: 2664)
- net.exe (PID: 3236)
- net.exe (PID: 3104)
- net.exe (PID: 3136)
- net.exe (PID: 3404)
- powershell.exe (PID: 3848)
- net.exe (PID: 3560)
- net.exe (PID: 3608)
- net.exe (PID: 3880)
- net.exe (PID: 2744)
- net.exe (PID: 1996)
- net.exe (PID: 2856)
- net.exe (PID: 2844)
- net.exe (PID: 2968)
- net.exe (PID: 900)
- net.exe (PID: 3068)
- net.exe (PID: 2880)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 1632)
- notepad.exe (PID: 120)
- WMIC.exe (PID: 2464)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3848)
- WMIC.exe (PID: 3008)
- WMIC.exe (PID: 3048)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 1632)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3848)
Uses WMIC.EXE to obtain service application data
- powershell.exe (PID: 1632)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3848)
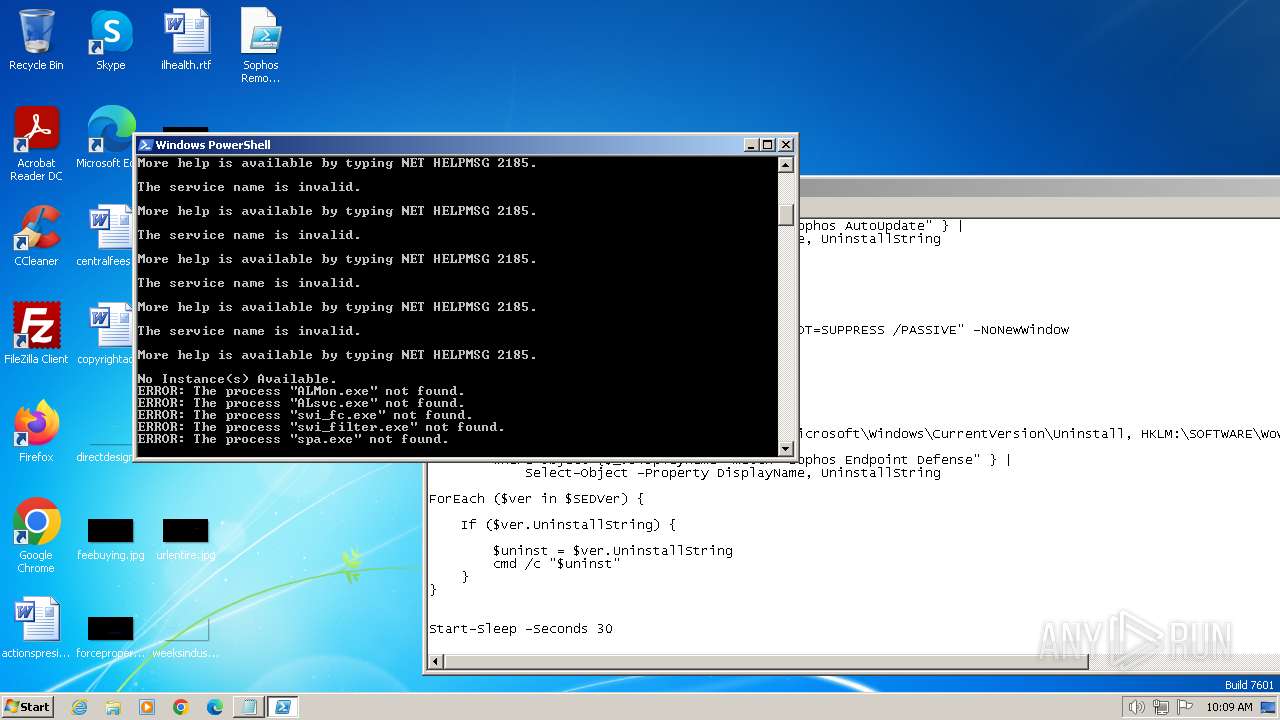
Uses TASKKILL.EXE to kill process
- powershell.exe (PID: 1632)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3848)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3848)
INFO
Manual execution by a user
- powershell.exe (PID: 1632)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3848)
Bypass execution policy to execute commands
- powershell.exe (PID: 1196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
160
Monitored processes
110
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
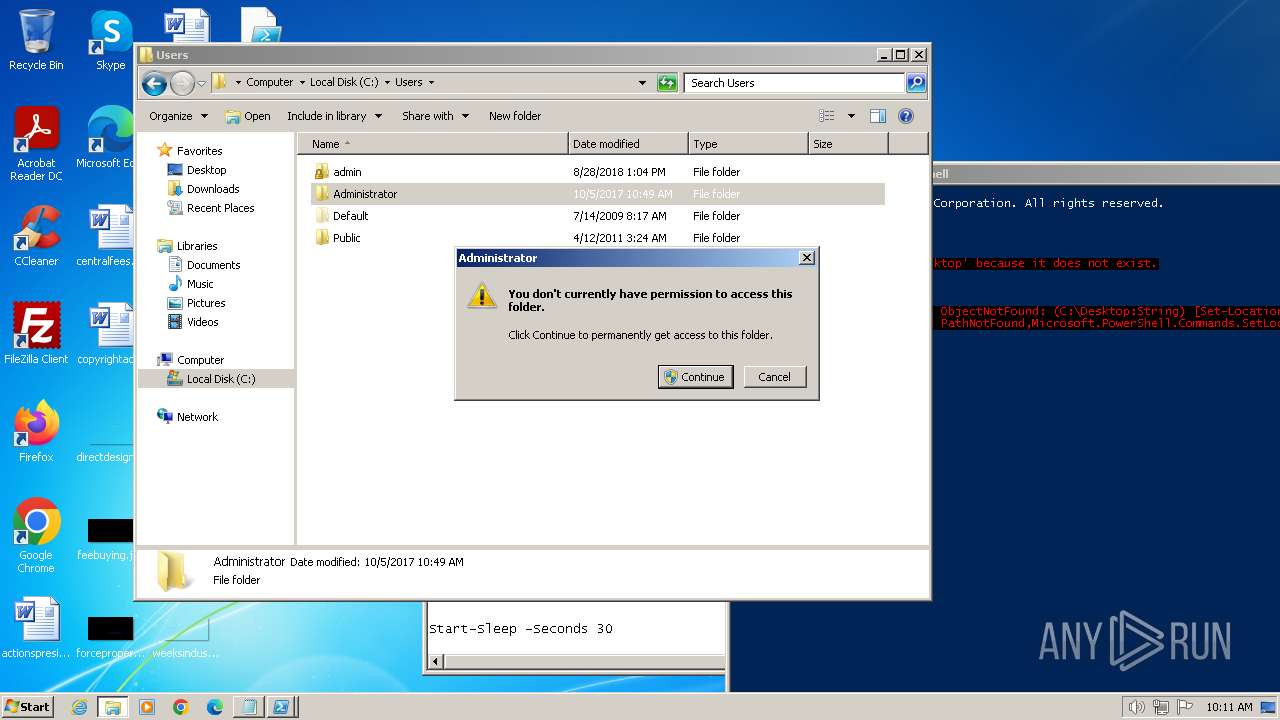
| 120 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\Sophos Removal Tool.ps1.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 632 | C:\Windows\system32\net1 stop swi_service | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
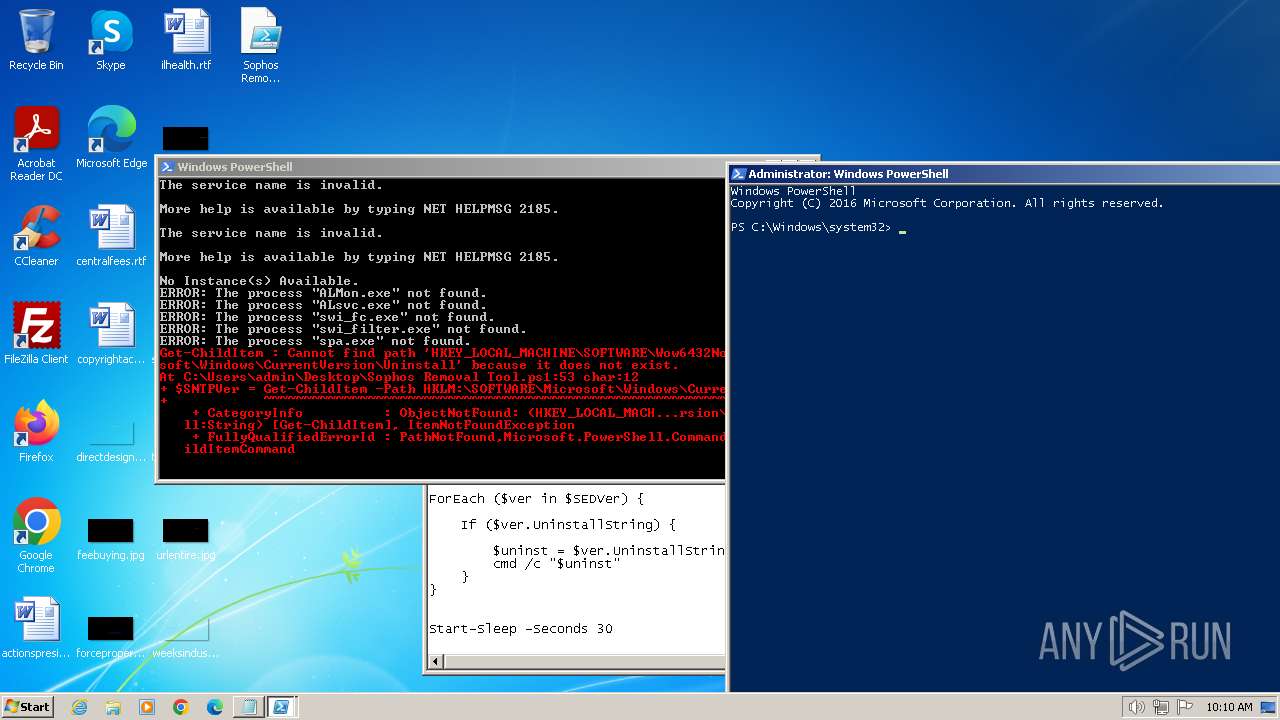
| 680 | "C:\Windows\system32\taskkill.exe" /f /im ALsvc.exe | C:\Windows\System32\taskkill.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
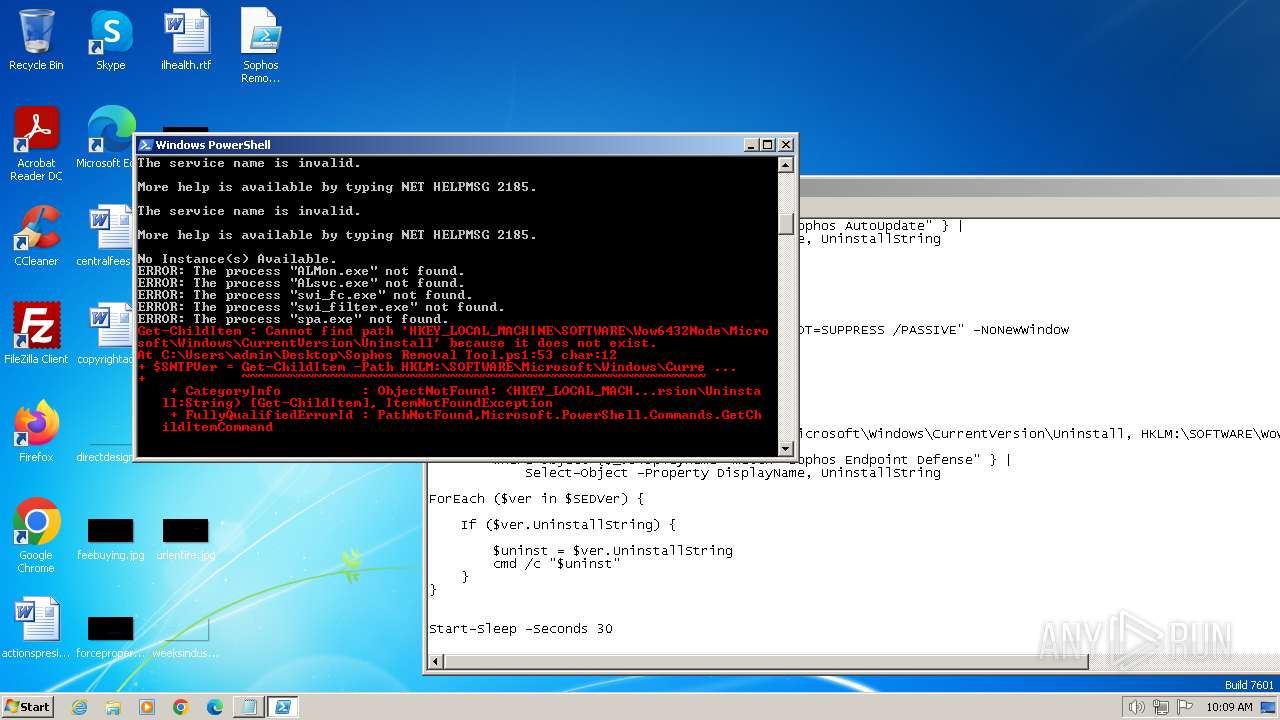
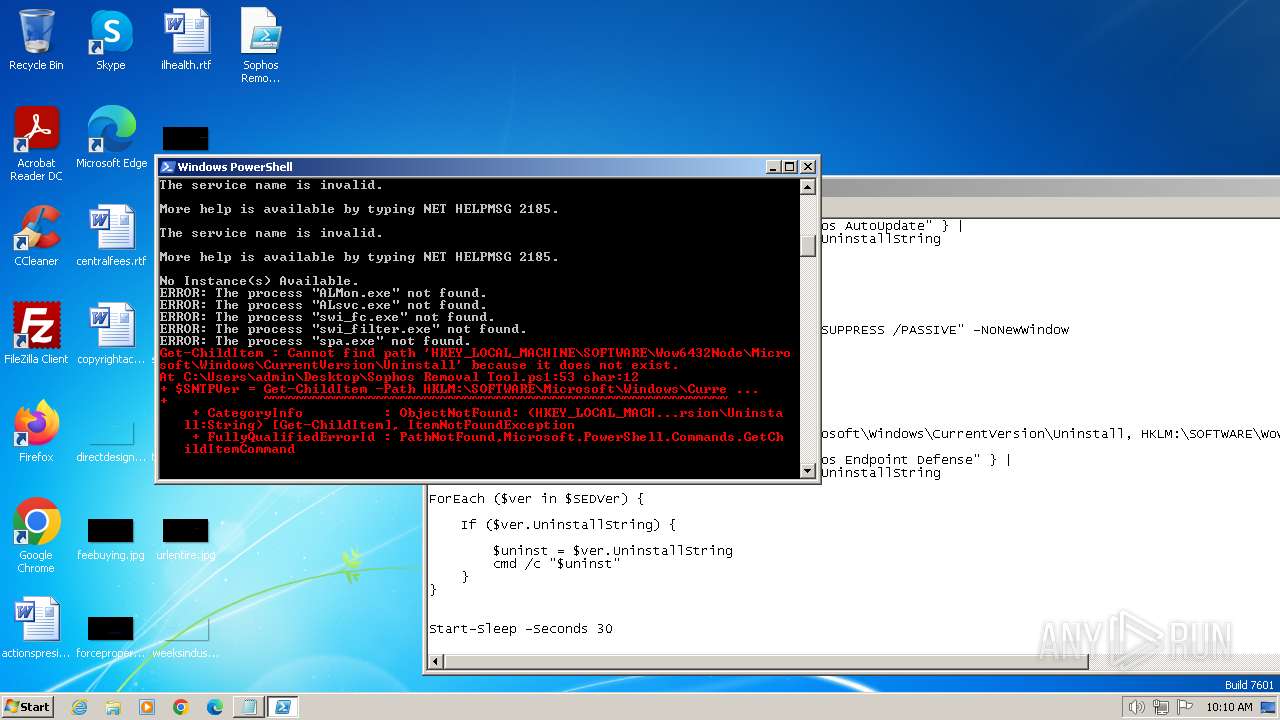
| 712 | "C:\Windows\system32\reg.exe" ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Sophos Endpoint Defense\TamperProtection\Config" /t REG_DWORD /v SEDEnabled /d 0 /f | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Windows\system32\reg.exe" ADD HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Sophos\SAVService\TamperProtection /t REG_DWORD /v Enabled /d 0 /f | C:\Windows\System32\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Windows\system32\net.exe" stop SntpService | C:\Windows\System32\net.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | C:\Windows\system32\net1 stop SntpService | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 968 | C:\Windows\system32\net1 stop "Sophos AutoUpdate Service" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 996 | "C:\Windows\system32\net.exe" stop "Sophos Endpoint Defense Service" | C:\Windows\System32\net.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | "C:\Windows\system32\net.exe" stop "Sophos Web Control Service" | C:\Windows\System32\net.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
62 200
Read events
61 960
Write events
238
Delete events
2
Modification events
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 06000000000000000B0000000100000002000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000006000000000000000B00000001000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (120) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
Executable files
0
Suspicious files
17
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1632 | powershell.exe | C:\Users\admin\AppData\Local\Temp\gfoypae0.4ro.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
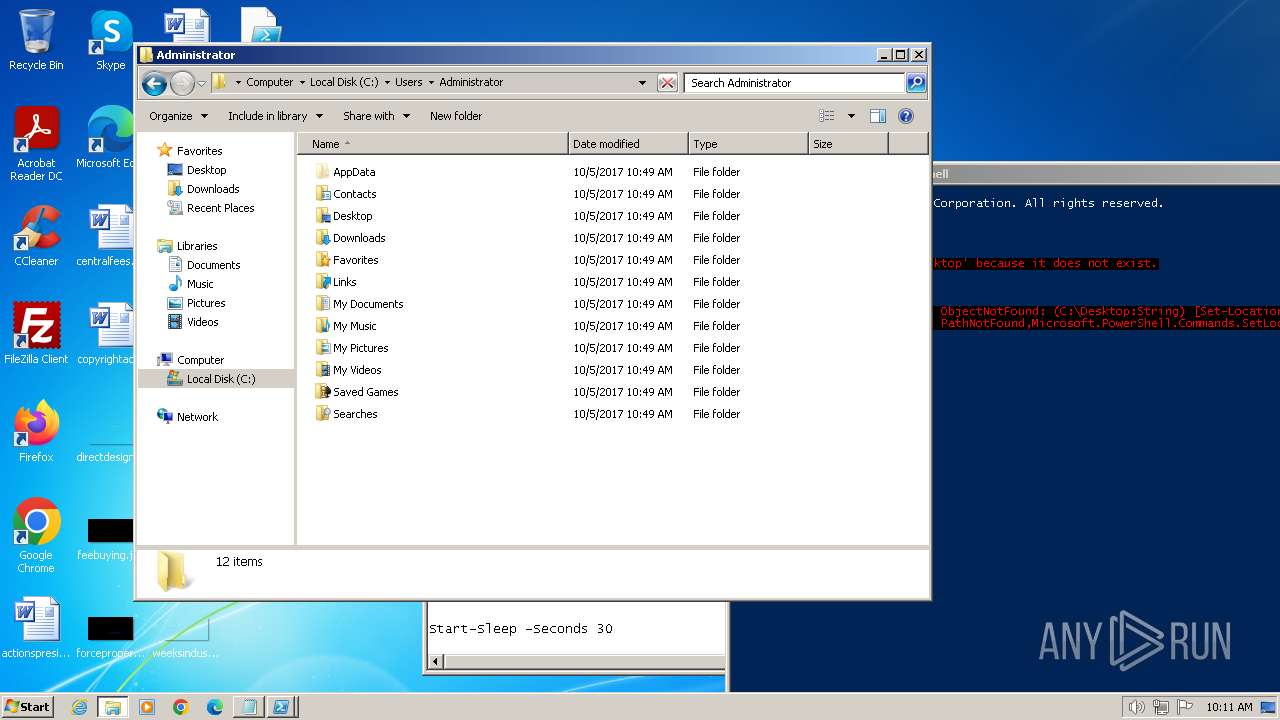
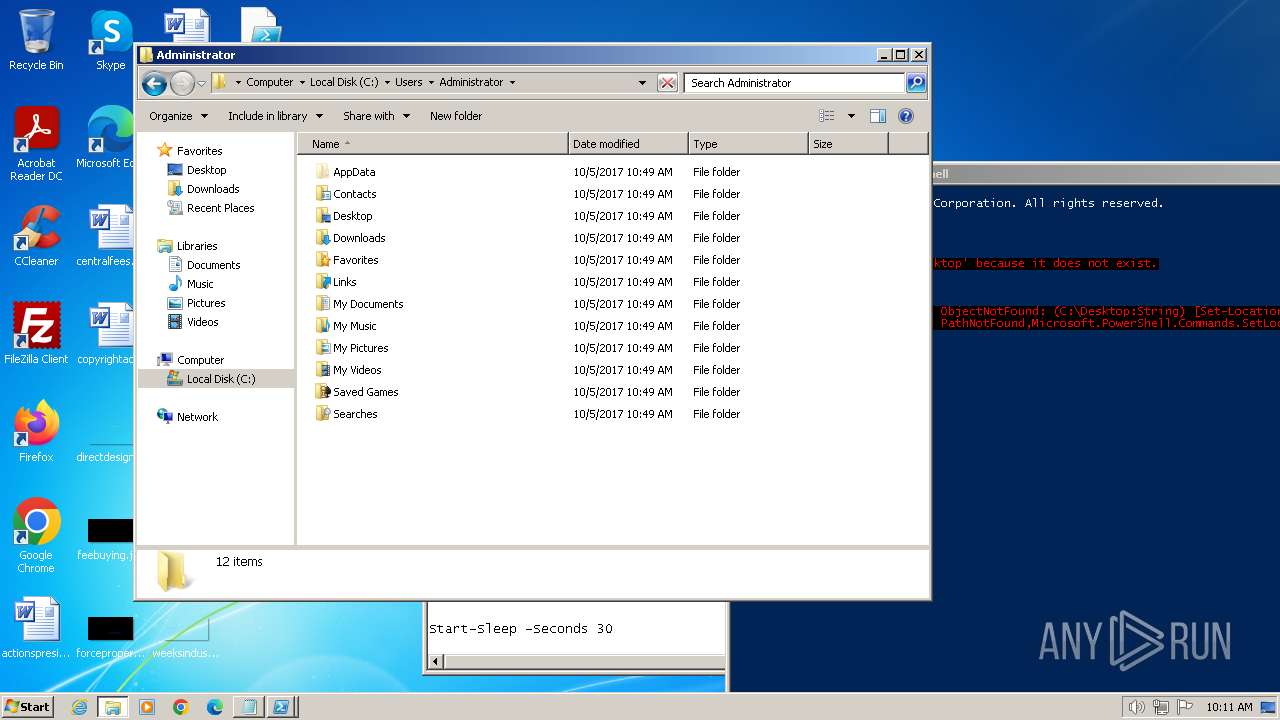
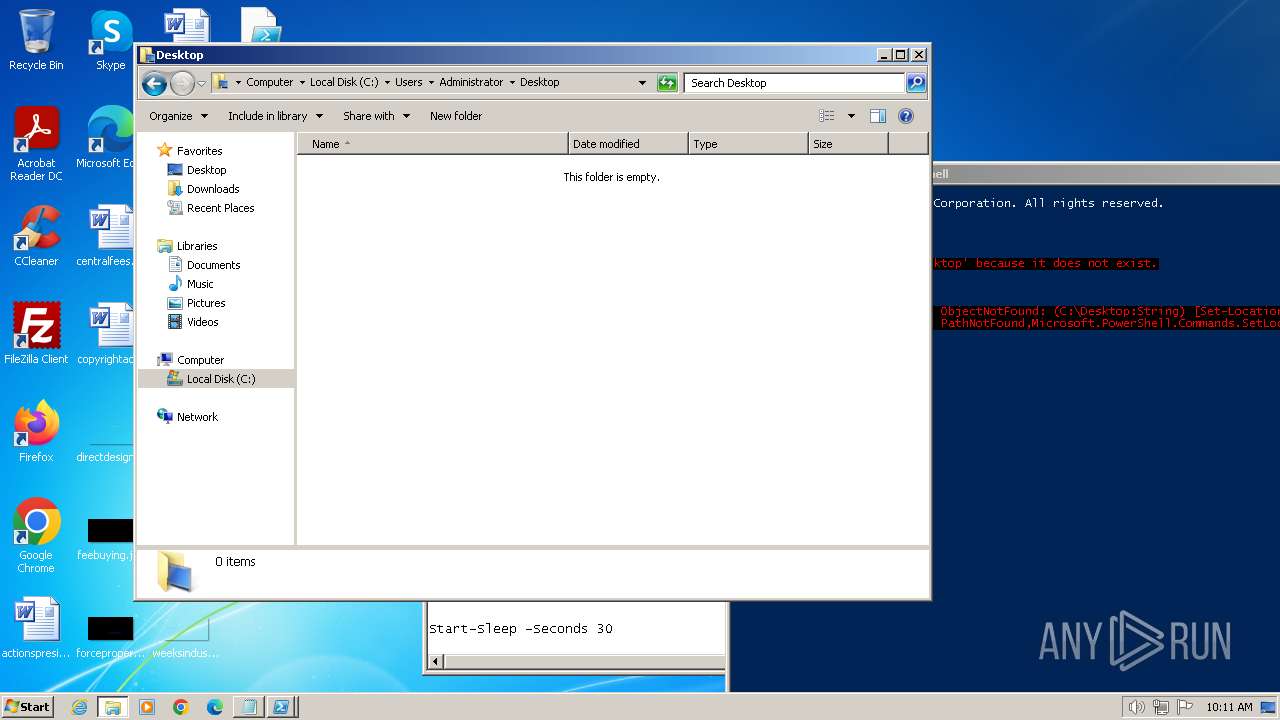
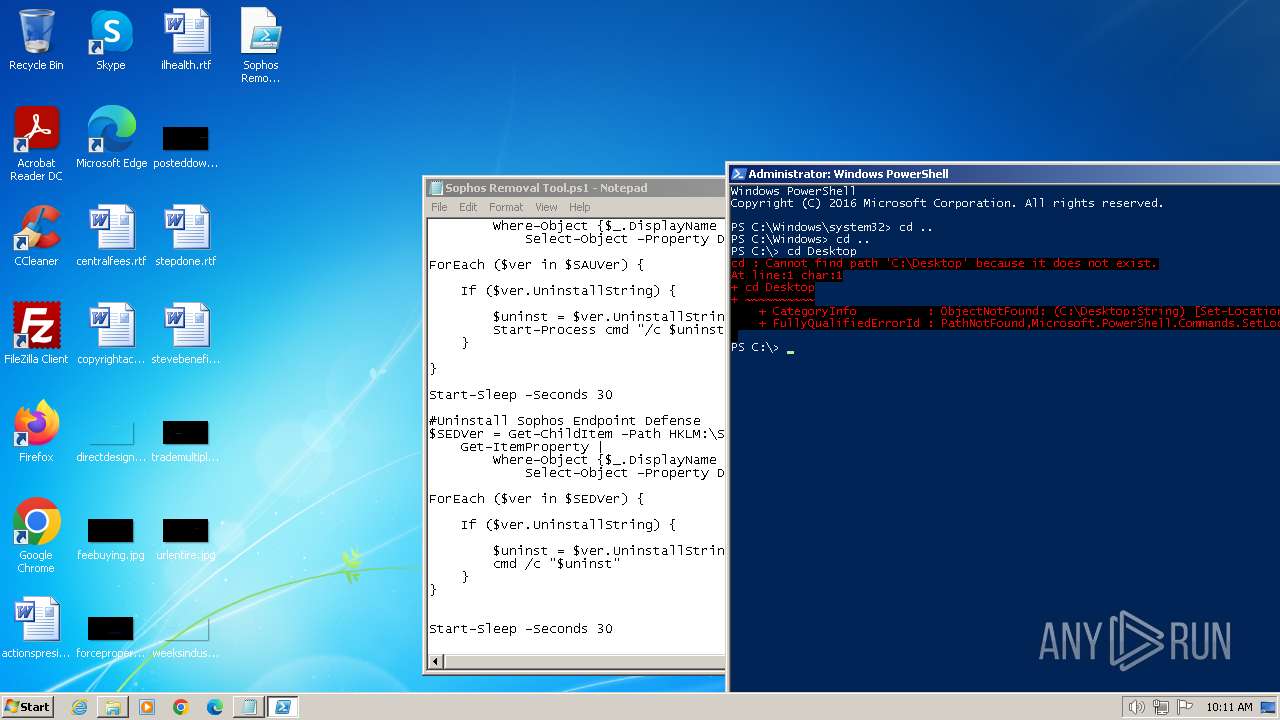
| 120 | notepad.exe | C:\Users\admin\Desktop\Sophos Removal Tool.ps1 | text | |
MD5:AC87D3612F7AF8E17105CF9E7580272A | SHA256:E1D459E568068BAE8DB668A9478E7D373AFDA5A174F2EA54A329056F5D6B681B | |||
| 1632 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Y6J1KLK566BFZGB4QY23.temp | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 3848 | powershell.exe | C:\Users\admin\AppData\Local\Temp\vkpqxrnu.ud1.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1632 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 1632 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFe7c40.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 1632 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ssuzdnc3.lcr.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kxofdhhp.0fh.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\LLI422N1DWZBBW5G7ZBV.temp | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 1632 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |