| URL: | https://cdn.discordapp.com/attachments/972462409266655305/977438551669108766/File.7z?file=181.zip |
| Full analysis: | https://app.any.run/tasks/924f3efa-ef3e-446c-ae55-b65ec57d6e7c |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | May 21, 2022, 11:21:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 46821FD3FF1E4E87DBA6BEC314D2F029 |
| SHA1: | 2615BB8D62A375881BDE41AA4999D6B4D874B1CE |
| SHA256: | E1C605EBC3E29A930CFC9504C0FCC6B705BE9983A893A8B5C0077FBC0705F930 |
| SSDEEP: | 3:N8cCWdy6//jB1VcrFWVfjiblB3gGjIAjIADn:2cry6XjD2lhB3x9jIADn |
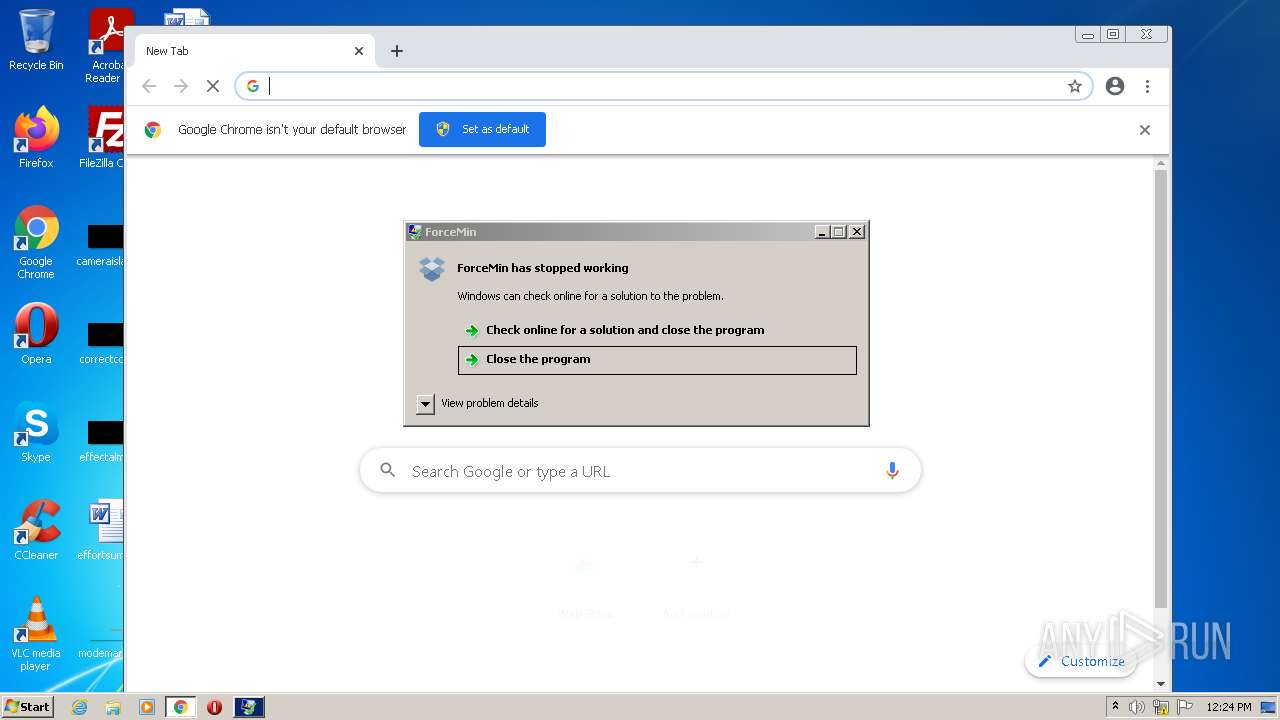
MALICIOUS
Application was dropped or rewritten from another process
- File.exe (PID: 2808)
- File.exe (PID: 3396)
Drops executable file immediately after starts
- WinRAR.exe (PID: 2552)
Changes settings of System certificates
- File.exe (PID: 2808)
SOCELARS was detected
- File.exe (PID: 2808)
Disables Windows Defender
- File.exe (PID: 2808)
Modifies files in Chrome extension folder
- File.exe (PID: 2808)
Connects to CnC server
- File.exe (PID: 2808)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2552)
- File.exe (PID: 2808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2552)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 916)
Checks supported languages
- WinRAR.exe (PID: 2552)
- File.exe (PID: 2808)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2552)
Checks for external IP
- File.exe (PID: 2808)
Adds / modifies Windows certificates
- File.exe (PID: 2808)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1760)
INFO
Reads the computer name
- iexplore.exe (PID: 1876)
- iexplore.exe (PID: 916)
- chrome.exe (PID: 1760)
- chrome.exe (PID: 1604)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 960)
- chrome.exe (PID: 1900)
Application launched itself
- iexplore.exe (PID: 1876)
- chrome.exe (PID: 1760)
Checks Windows Trust Settings
- iexplore.exe (PID: 916)
- iexplore.exe (PID: 1876)
- File.exe (PID: 2808)
Checks supported languages
- iexplore.exe (PID: 1876)
- iexplore.exe (PID: 916)
- chrome.exe (PID: 1760)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 1604)
- chrome.exe (PID: 1388)
- chrome.exe (PID: 1856)
- chrome.exe (PID: 2032)
- chrome.exe (PID: 960)
- chrome.exe (PID: 4088)
- chrome.exe (PID: 2148)
- chrome.exe (PID: 3500)
- chrome.exe (PID: 1900)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 3948)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1876)
Changes internet zones settings
- iexplore.exe (PID: 1876)
Reads the date of Windows installation
- iexplore.exe (PID: 1876)
Reads settings of System Certificates
- iexplore.exe (PID: 916)
- File.exe (PID: 2808)
- chrome.exe (PID: 1604)
Manual execution by user
- chrome.exe (PID: 1760)
Reads the hosts file
- chrome.exe (PID: 1760)
- chrome.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
18
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1876 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1056,1320749889870422059,11835566977879249052,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2860 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6eb5d988,0x6eb5d998,0x6eb5d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1056,1320749889870422059,11835566977879249052,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1240 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,1320749889870422059,11835566977879249052,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cdn.discordapp.com/attachments/972462409266655305/977438551669108766/File.7z?file=181.zip" | C:\Program Files\Internet Explorer\iexplore.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1056,1320749889870422059,11835566977879249052,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,1320749889870422059,11835566977879249052,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1972 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1056,1320749889870422059,11835566977879249052,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3608 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
22 575
Read events
22 362
Write events
210
Delete events
3
Modification events
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960900 | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 19998804 | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960901 | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
128
Text files
115
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2CF0256F-D8F8-11EC-8C9F-1203334A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\File.7z.6hl2w22.partial | compressed | |
MD5:— | SHA256:— | |||
| 916 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\File[1].7z | compressed | |
MD5:— | SHA256:— | |||
| 1876 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA09FBCCE210D3171.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{2CF0256D-D8F8-11EC-8C9F-1203334A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 2808 | File.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extensions\glmhhkoaglkboooplngidahblhiadpab\1.0.3_0\assets\icons\128x128.png | image | |
MD5:— | SHA256:— | |||
| 2808 | File.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extensions\glmhhkoaglkboooplngidahblhiadpab\1.0.3_0\assets\background.html | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
26
DNS requests
13
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2808 | File.exe | HEAD | 200 | 212.193.30.45:80 | http://212.193.30.45/EXT/smartsearch.jpeg | RU | — | — | malicious |
2808 | File.exe | GET | 200 | 212.193.30.21:80 | http://212.193.30.21/base/api/statistics.php | RU | binary | 94 b | malicious |
2808 | File.exe | GET | 400 | 45.144.225.57:80 | http://45.144.225.57/server.txt | unknown | html | 301 b | malicious |
2808 | File.exe | GET | 400 | 212.193.30.45:80 | http://212.193.30.45/proxies.txt | RU | html | 301 b | malicious |
2808 | File.exe | POST | 200 | 212.193.30.21:80 | http://212.193.30.21/base/api/getData.php | RU | text | 108 b | malicious |
2808 | File.exe | POST | 200 | 212.193.30.21:80 | http://212.193.30.21/base/api/getData.php | RU | text | 280 b | malicious |
2808 | File.exe | GET | 200 | 212.193.30.45:80 | http://212.193.30.45/EXT/smartsearch.png | RU | text | 5.96 Kb | malicious |
2808 | File.exe | GET | 200 | 212.193.30.45:80 | http://212.193.30.45/EXT/smartsearch.jpeg | RU | crx | 203 Kb | malicious |
916 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
1604 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
916 | iexplore.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
916 | iexplore.exe | 8.250.177.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | unknown |
916 | iexplore.exe | 8.252.188.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
916 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2808 | File.exe | 212.193.30.45:80 | — | — | RU | malicious |
2808 | File.exe | 45.144.225.57:80 | — | — | — | malicious |
2808 | File.exe | 212.193.30.21:80 | — | — | RU | malicious |
2808 | File.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
1604 | chrome.exe | 142.250.186.163:443 | update.googleapis.com | Google Inc. | US | whitelisted |
1604 | chrome.exe | 142.250.186.97:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
pastebin.com |
| malicious |
ipinfo.io |
| shared |
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.googleusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
916 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
916 | iexplore.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2808 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2808 | File.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2808 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2808 | File.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2808 | File.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
2808 | File.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2808 | File.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2808 | File.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |