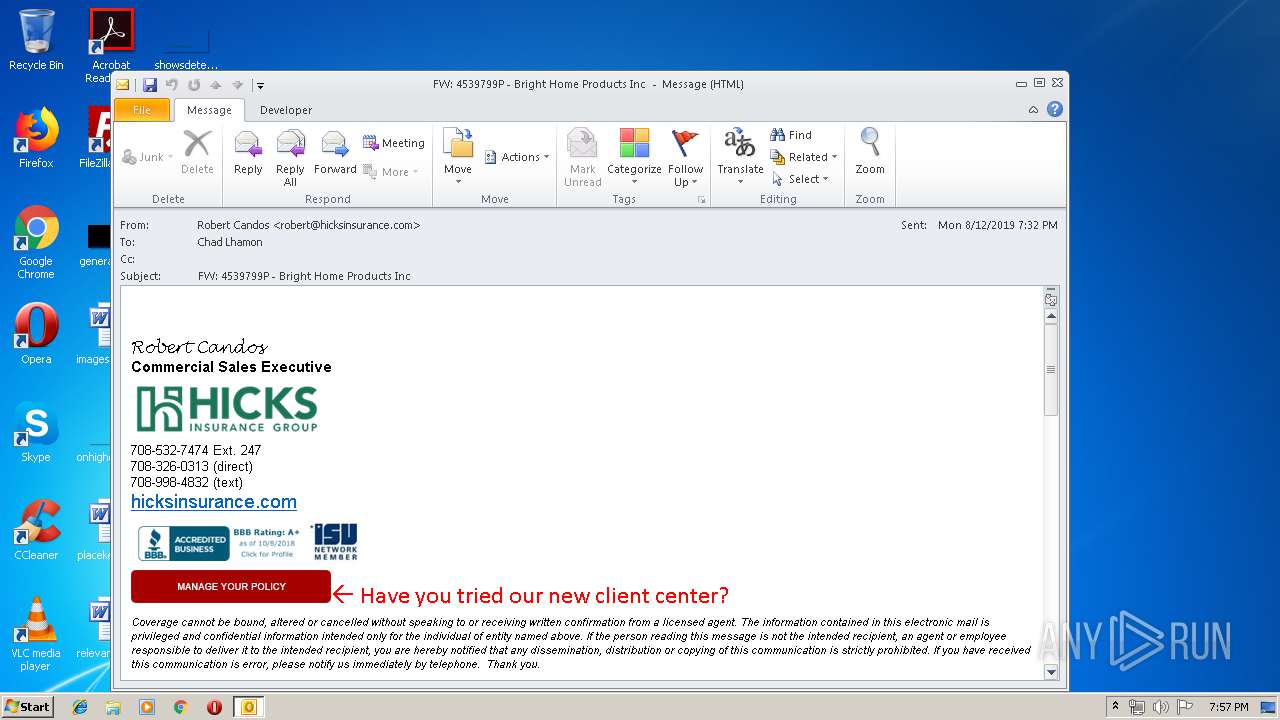
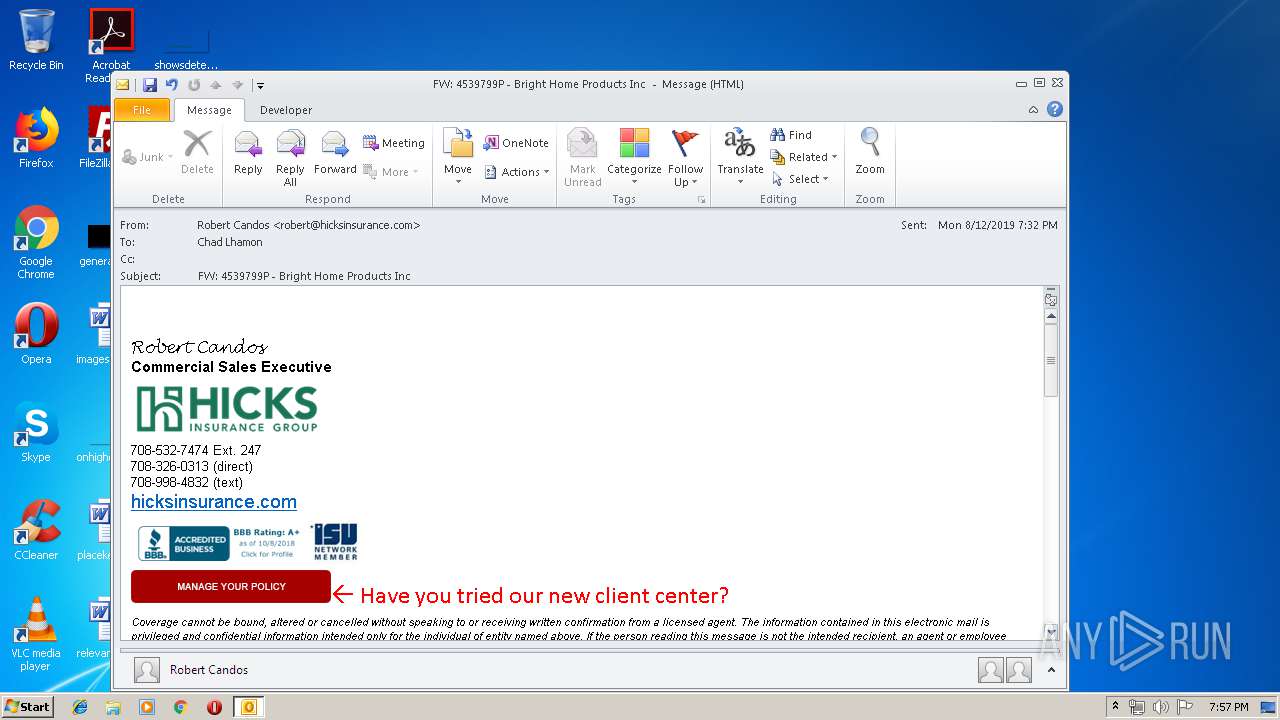
| File name: | FW 4539799P - Bright Home Products Inc .msg |
| Full analysis: | https://app.any.run/tasks/12c083e0-e5f0-4211-b89a-a7d3a671505b |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2019, 18:57:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | DBECBF359DAA171765ACE72838593665 |
| SHA1: | 53DDFB4A42AAFE87AD3A90F5651E00B12FF5109E |
| SHA256: | E1BB8613E82D12E6EE1F5197DFB03632BE2604BDDC34D097CD961C59455CE634 |
| SSDEEP: | 3072:FlyohhTpM7/pM75/B9j5pM7NUL27L2iKB3DKBwuc9Ein4qVNJKvYs47b3yqqPRv2:DcYE6Pb3ZqPNE |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 1404)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 1404)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 1404)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1404)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2596)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1404)
Changes internet zones settings
- iexplore.exe (PID: 1484)
Application launched itself
- chrome.exe (PID: 2596)
Reads internet explorer settings
- iexplore.exe (PID: 3580)
Reads Internet Cache Settings
- iexplore.exe (PID: 3580)
Manual execution by user
- chrome.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
69
Monitored processes
32
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2988 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,9043229541271812362,8987602219823049495,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2346087568710176501 --mojo-platform-channel-handle=3656 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,9043229541271812362,8987602219823049495,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8214871344872558664 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2392 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,9043229541271812362,8987602219823049495,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16273123124395224802 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2588 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\FW 4539799P - Bright Home Products Inc .msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
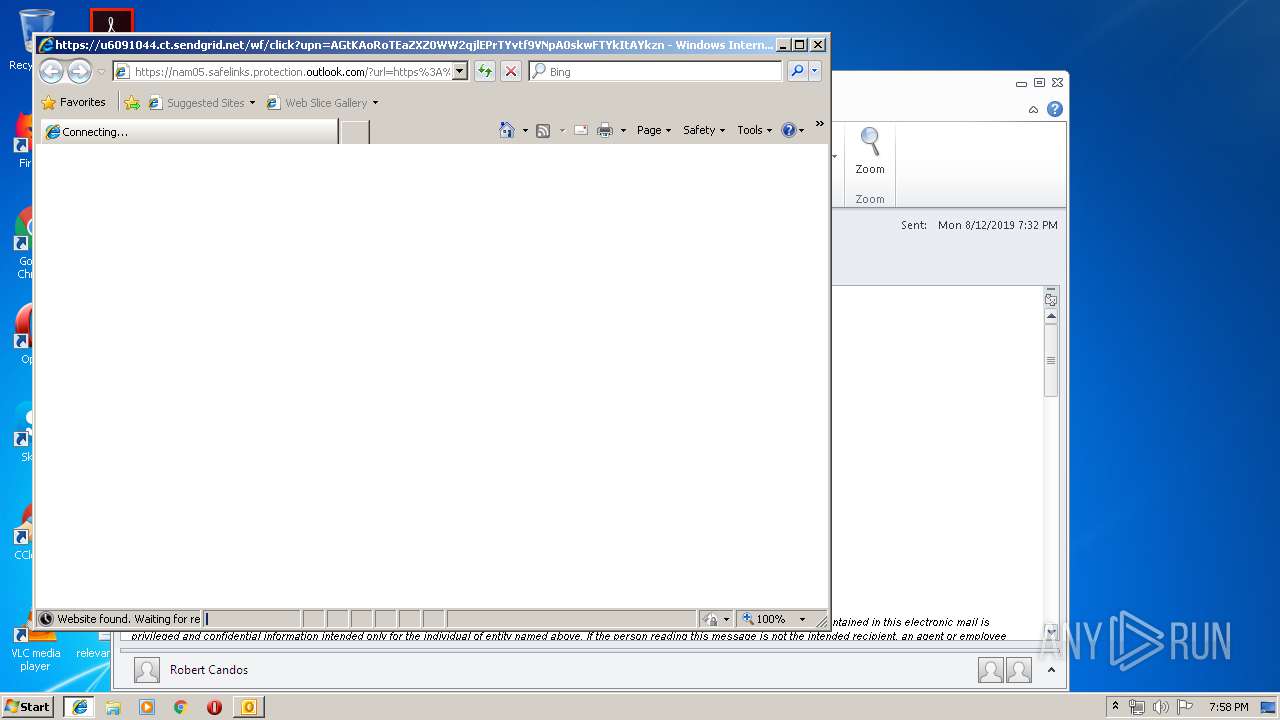
| 1484 | "C:\Program Files\Internet Explorer\iexplore.exe" https://nam05.safelinks.protection.outlook.com/?url=https%3A%2F%2Fu6091044.ct.sendgrid.net%2Fwf%2Fclick%3Fupn%3DAGtKAoRoTEaZXZ0WW2qjlEPrTYvtf9VNpA0skwFTYkItAYkznbVyNgXghnV6RTo7g7xAAGI68GnuB6hzfmgbnQ-3D-3D_P-2FJ7xsVHH-2FqU6SiJFx1gFmff1IZwJh2NTGFjZwAVuFtYRG03MiGySBst91jlCRqsuJLtNrBDMb9pitEuiyp28Wg-2BfXHodYjgh347L6UcROZ0lr-2BrwkrcJVPSrgf4MMaHhrANlzW14kjYmPoJcB-2BFveTGNhIqig2Gyy79gOr30nCR-2Bhh0Q1nN9TfMvPzQ-2FGKNasUv1t3KnOQDkcx-2BgEs0w7iT-2FlkN-2Bw-2Fq5tm5fy58Bf5QAV4kG3Ut3Pp9yWFPQSv5jISSWGv7cSPhcZFWXwzgQmKqsLBBEWDVaAhjTgpWoNe1EW2QMi6F0icMnIkPbAdTR-2Bw7pfynR-2FL9A4O-2BKhx6cja9xktgU7C39TcSsiqbxf8FUlOI0vl6pM6ZAGdZGBxnezv0ylF6O5k5o8Uxr5edxp8VrZVFLXlRebOIF85tRk3FzHBz9XpwysMJWjWtoQIaeLDvlA1E3eTvVyvSd03O2NRmGgb6hsCgltb9Ap8-2FIfZkeydFtCo-2Fe9B8O4a5-2FPil2HBYVl7tlvCZx8H18yjpx-2FCBsZZA6c59yaCiGAXpxIK-2FiPfJphOsMWT2u7hkQeM1&data=02%7C01%7Cclhamon%40pekininsurance.com%7C4810a06f551b47588c7708d71f536e82%7Caab19002fe2d4488ae543316324c96c2%7C0%7C0%7C637012315515422315&sdata=Dsb772rVgcoSL8yReKmL4iNsUL%2BjcW9bKo5KgWGrXXM%3D&reserved=0 | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1040,9043229541271812362,8987602219823049495,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=11296957495867333757 --mojo-platform-channel-handle=4000 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,9043229541271812362,8987602219823049495,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15732258483861146487 --mojo-platform-channel-handle=3236 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,9043229541271812362,8987602219823049495,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4651223337970710995 --mojo-platform-channel-handle=4160 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1040,9043229541271812362,8987602219823049495,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=17583709071354253491 --mojo-platform-channel-handle=1048 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 204
Read events
1 656
Write events
524
Delete events
24
Modification events
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | -/a |
Value: 2D2F61007C050000010000000000000000000000 | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 7C0500002062C4040952D50100000000 | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220168800 | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (1404) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1326252053 | |||
Executable files
0
Suspicious files
59
Text files
212
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1404 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE71D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1404 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\msoEB73.tmp | — | |
MD5:— | SHA256:— | |||
| 1404 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1404 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\FB8C9BAD.dat | image | |
MD5:— | SHA256:— | |||
| 1484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1404 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\30B65743.dat | image | |
MD5:— | SHA256:— | |||
| 1484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1404 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\FD5CA.dat | image | |
MD5:— | SHA256:— | |||
| 1404 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A5922068.dat | image | |
MD5:— | SHA256:— | |||
| 3580 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
45
DNS requests
41
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2760 | chrome.exe | GET | 302 | 172.217.22.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 516 b | whitelisted |
2760 | chrome.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.6 Kb | whitelisted |
2760 | chrome.exe | GET | 200 | 74.125.4.216:80 | http://r2---sn-aigzrney.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.183.105.212&mm=28&mn=sn-aigzrney&ms=nvh&mt=1565722644&mv=m&mvi=1&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
2760 | chrome.exe | GET | 200 | 54.230.93.170:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
1484 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1404 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3580 | iexplore.exe | 104.47.49.28:443 | nam05.safelinks.protection.outlook.com | Microsoft Corporation | US | whitelisted |
1484 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3580 | iexplore.exe | 167.89.118.35:443 | u6091044.ct.sendgrid.net | SendGrid, Inc. | US | suspicious |
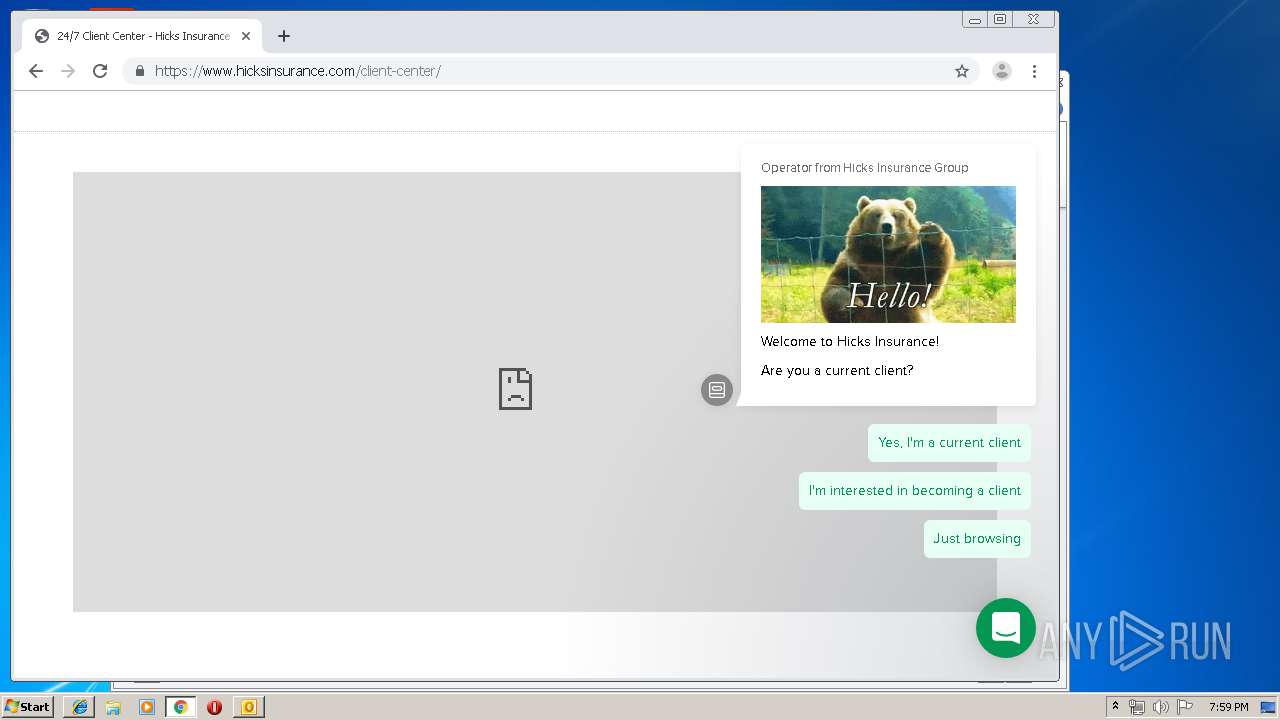
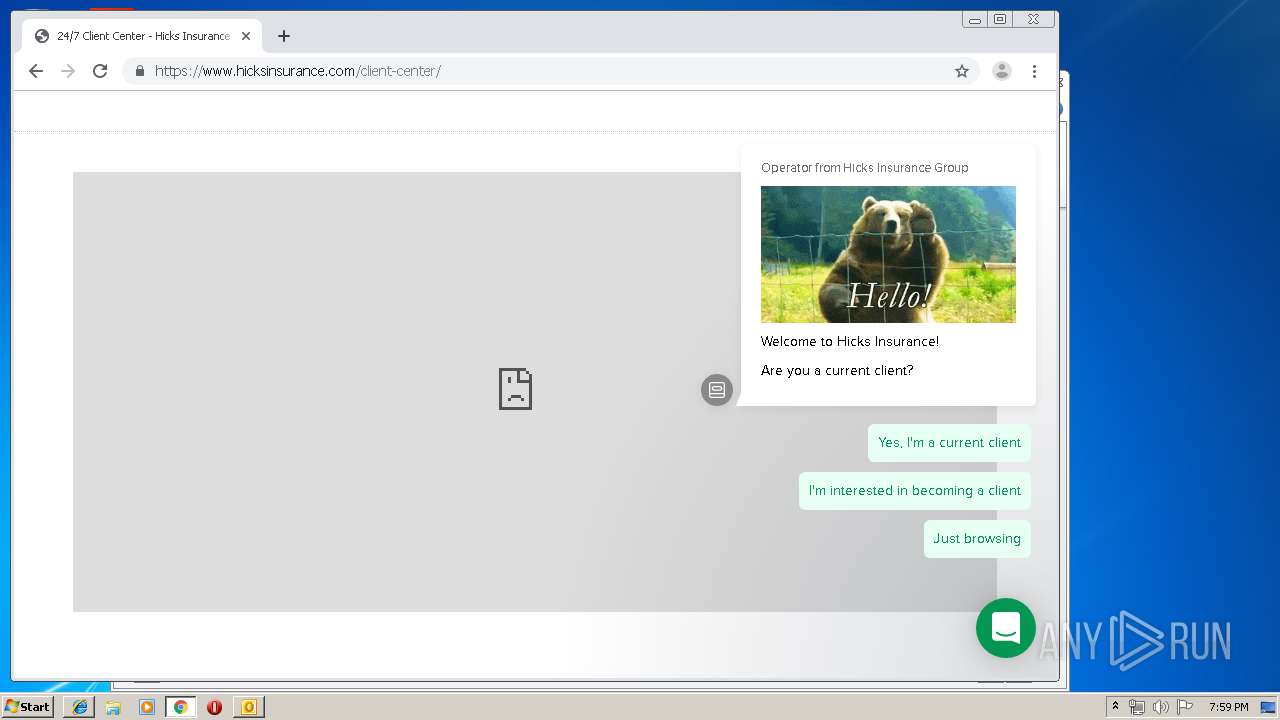
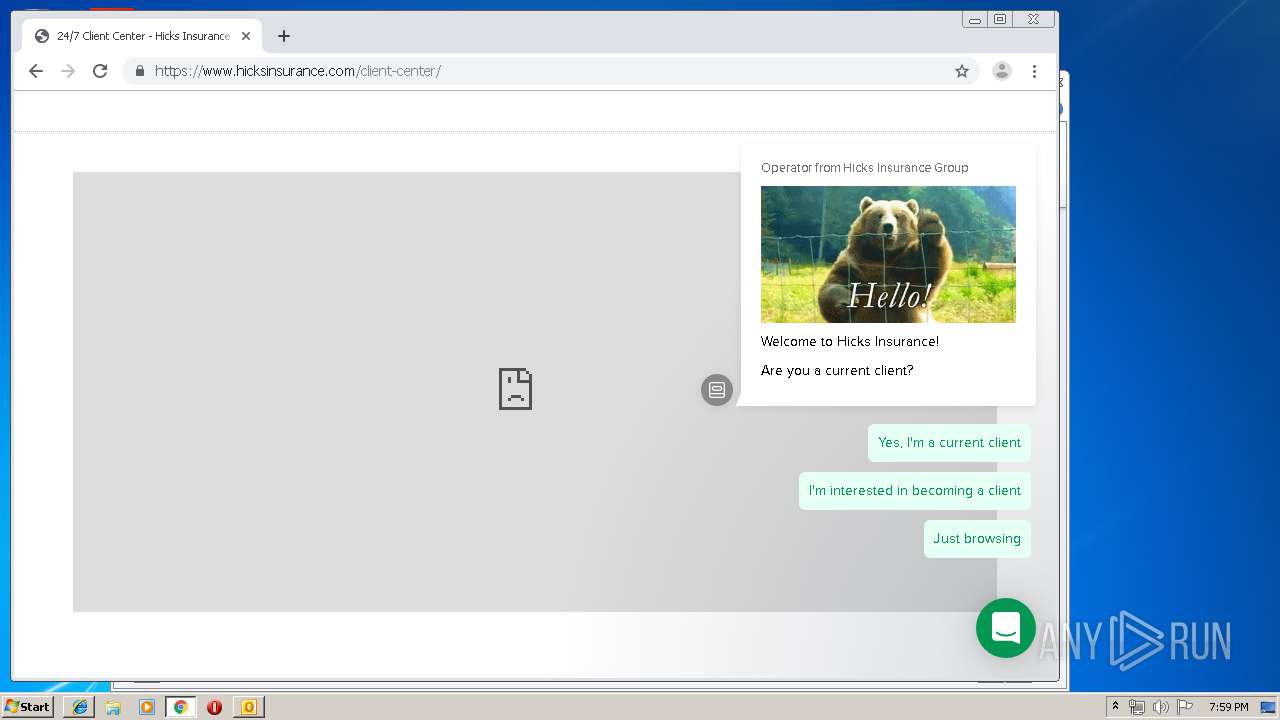
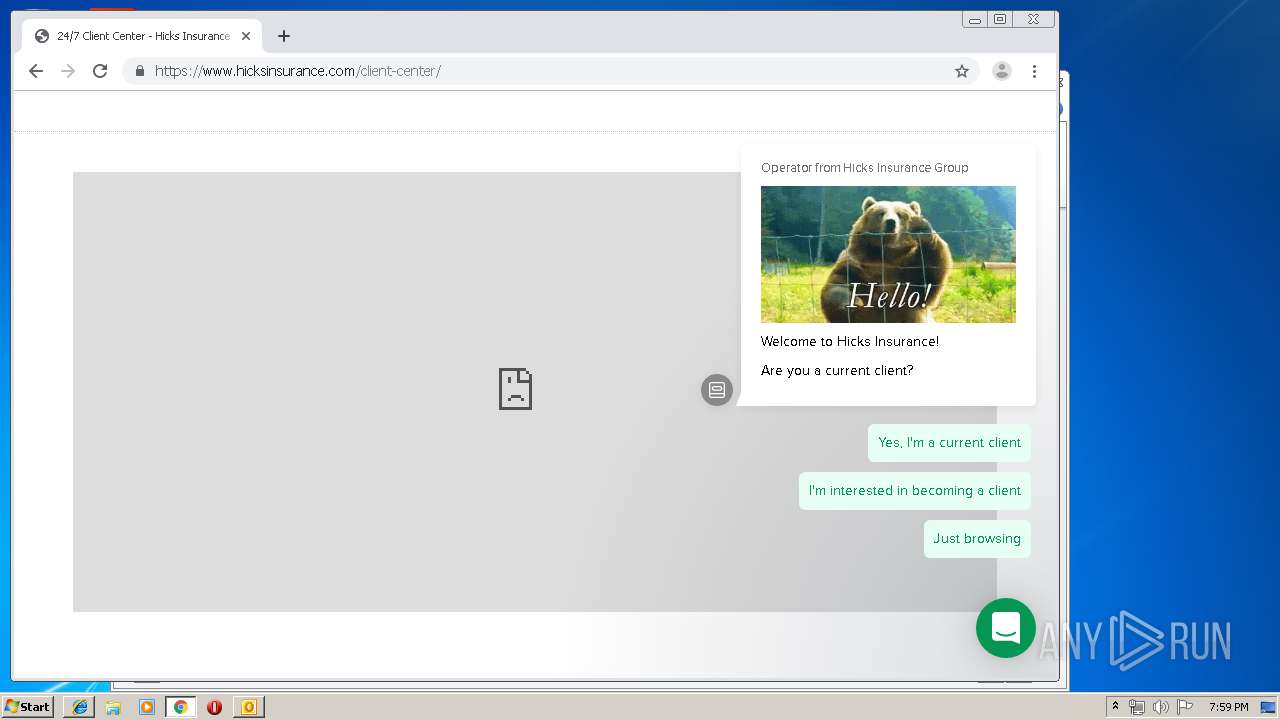
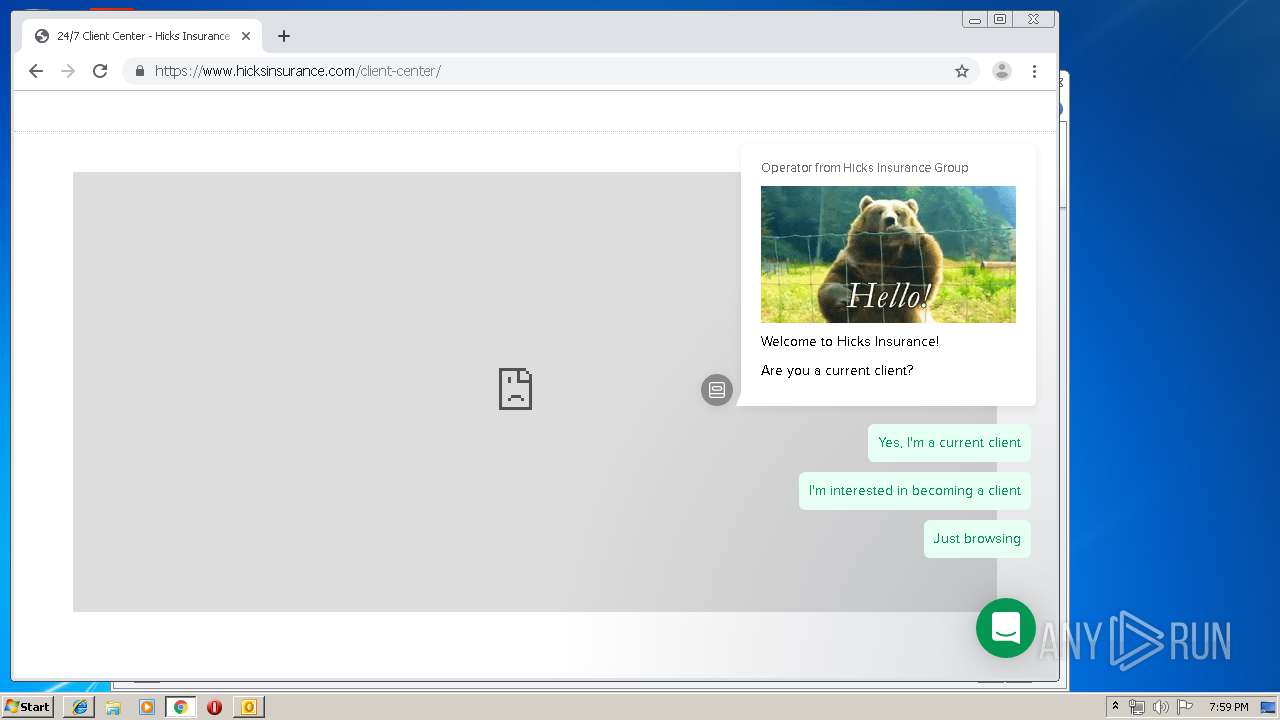
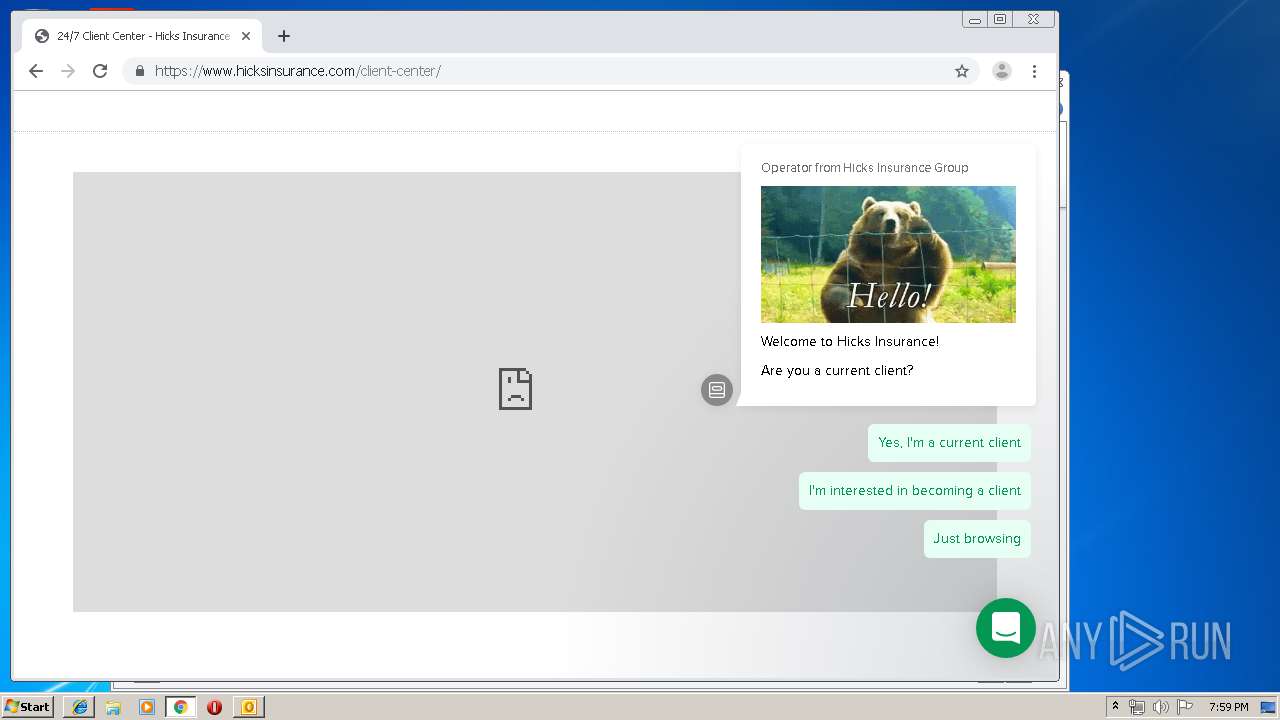
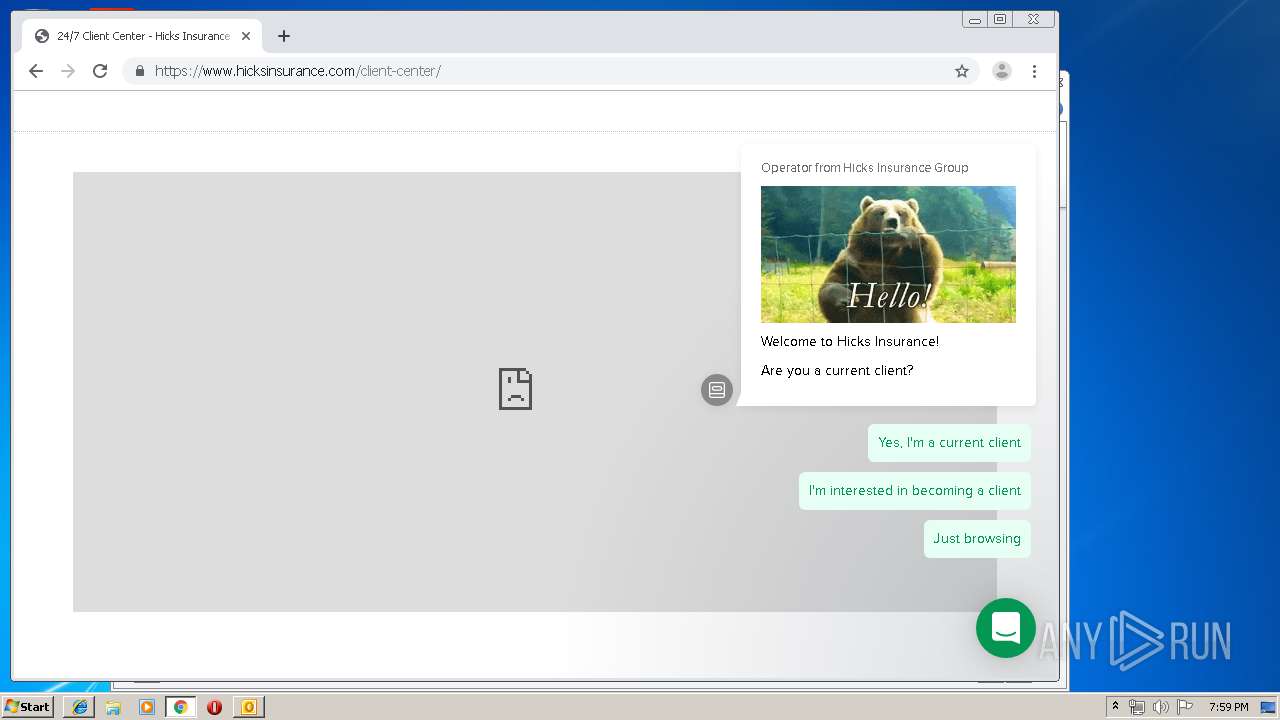
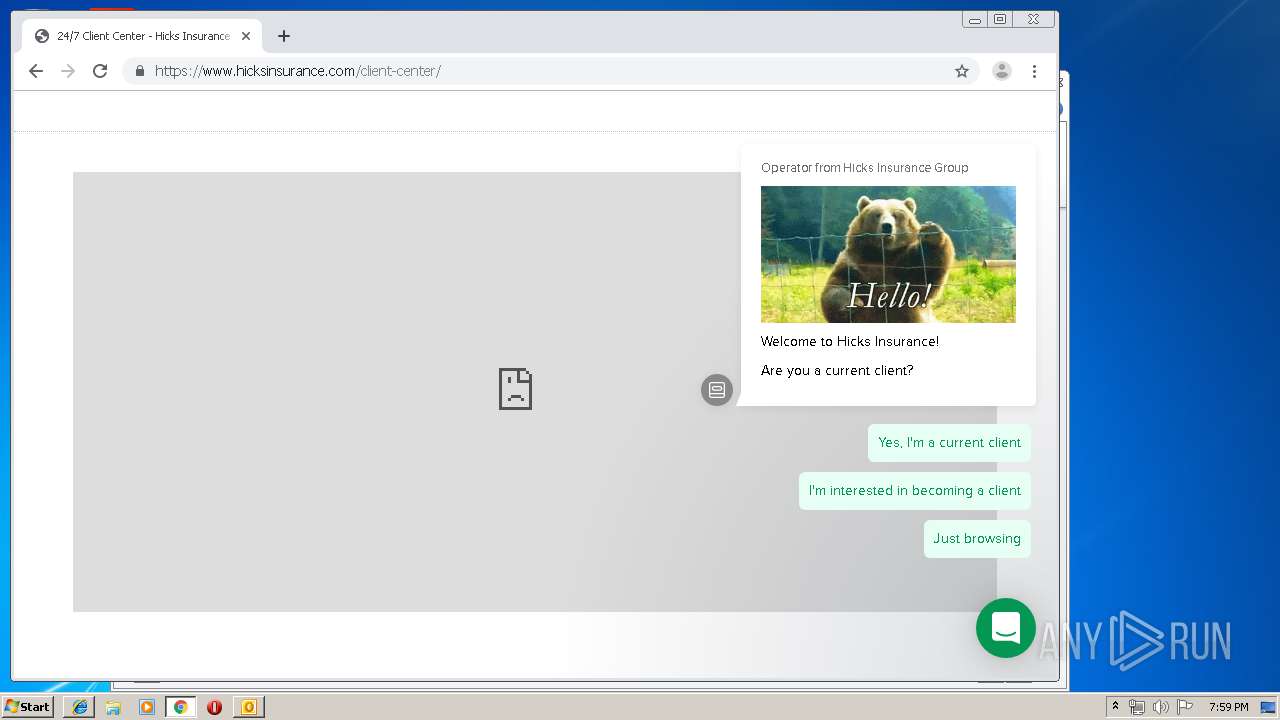
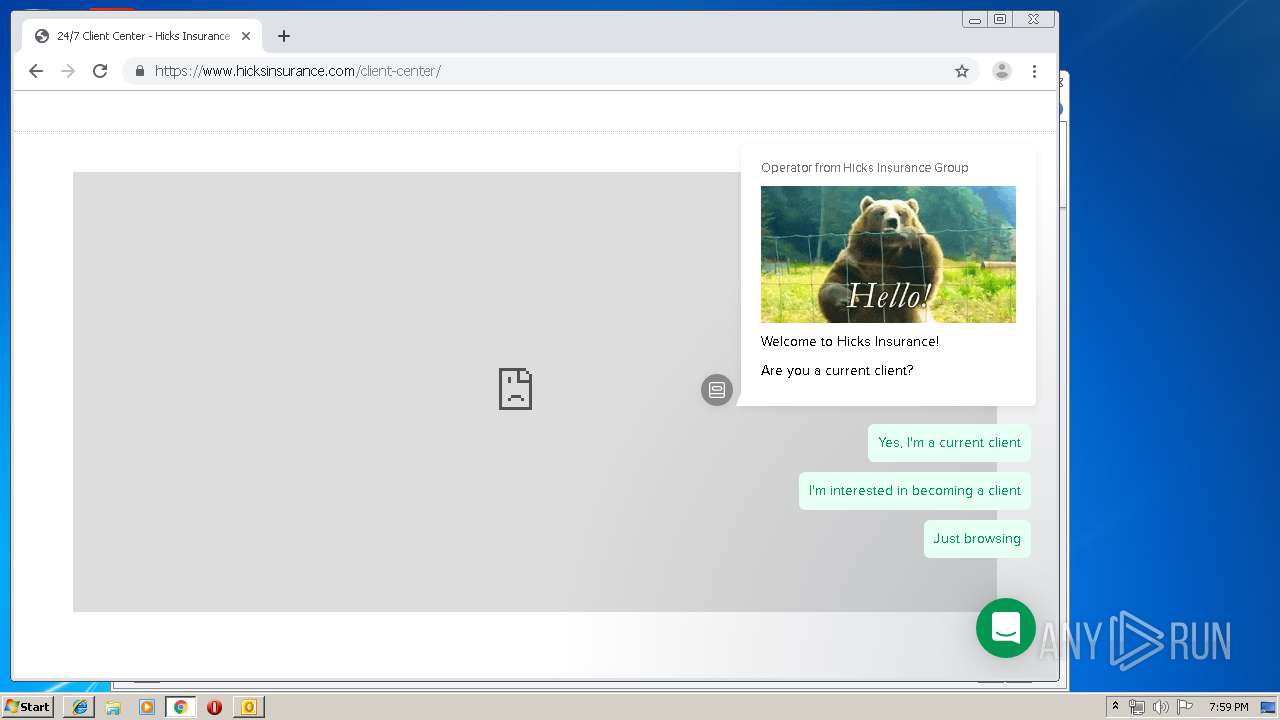
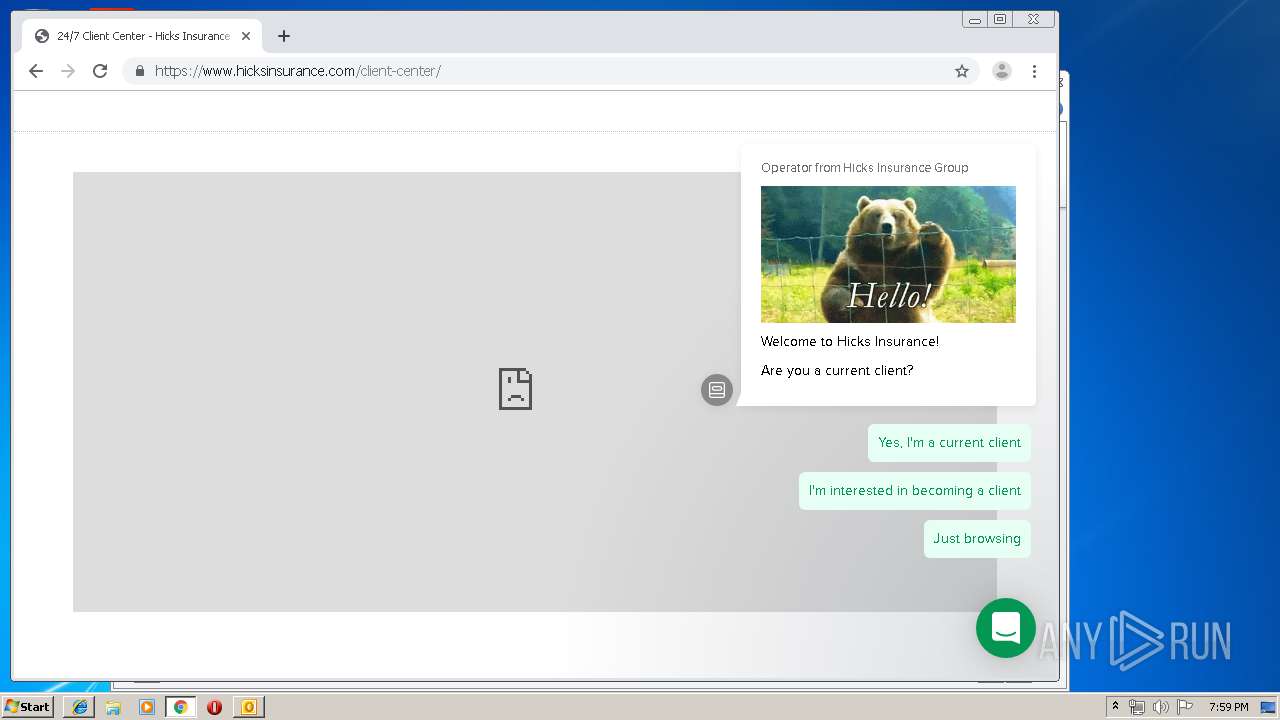
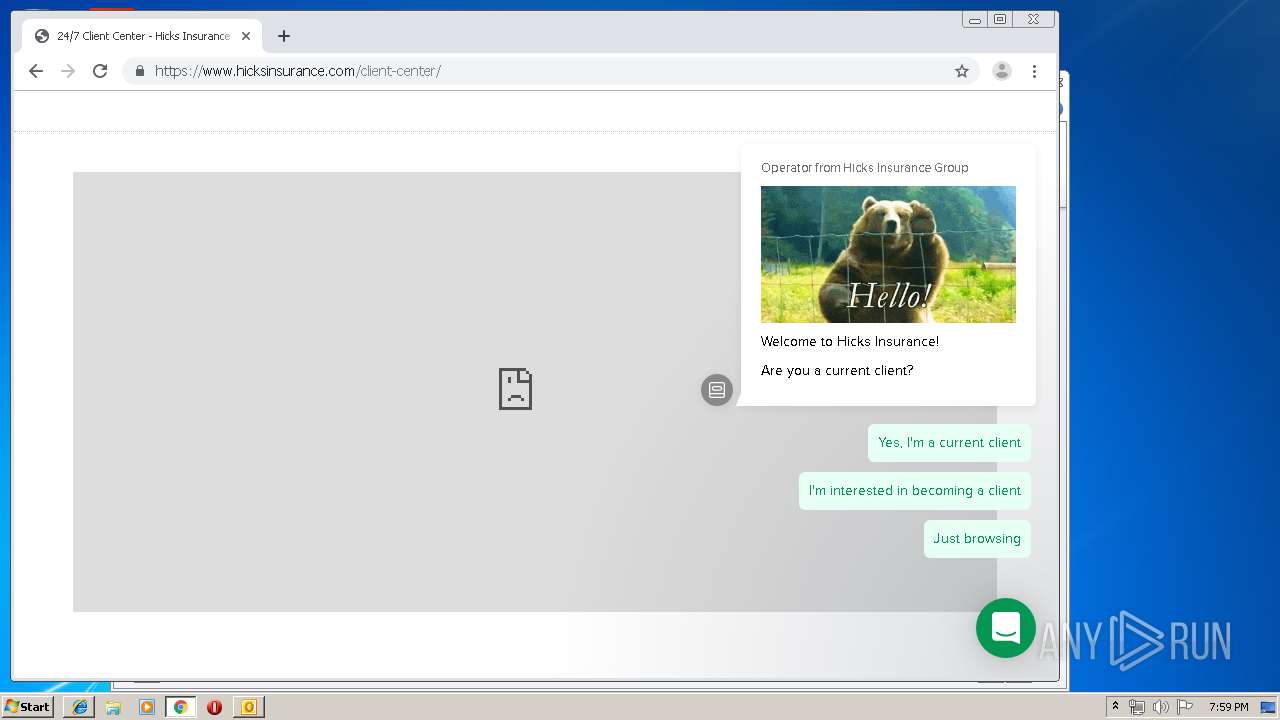
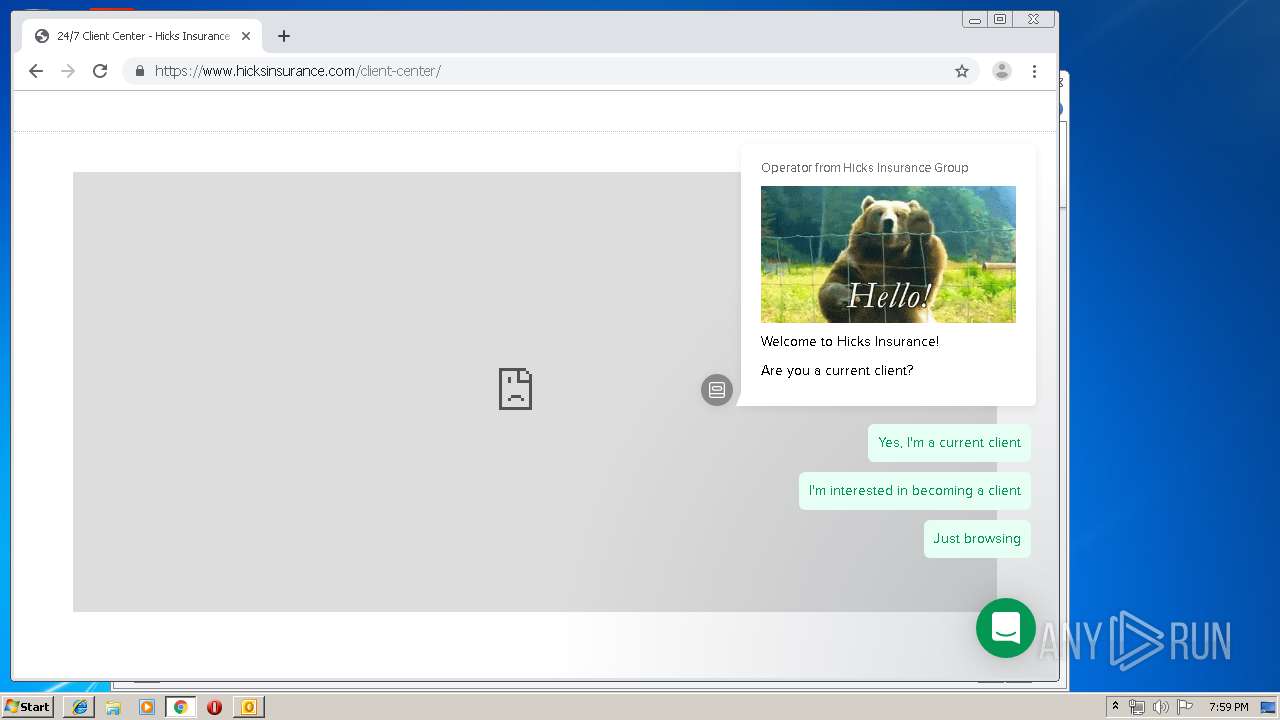
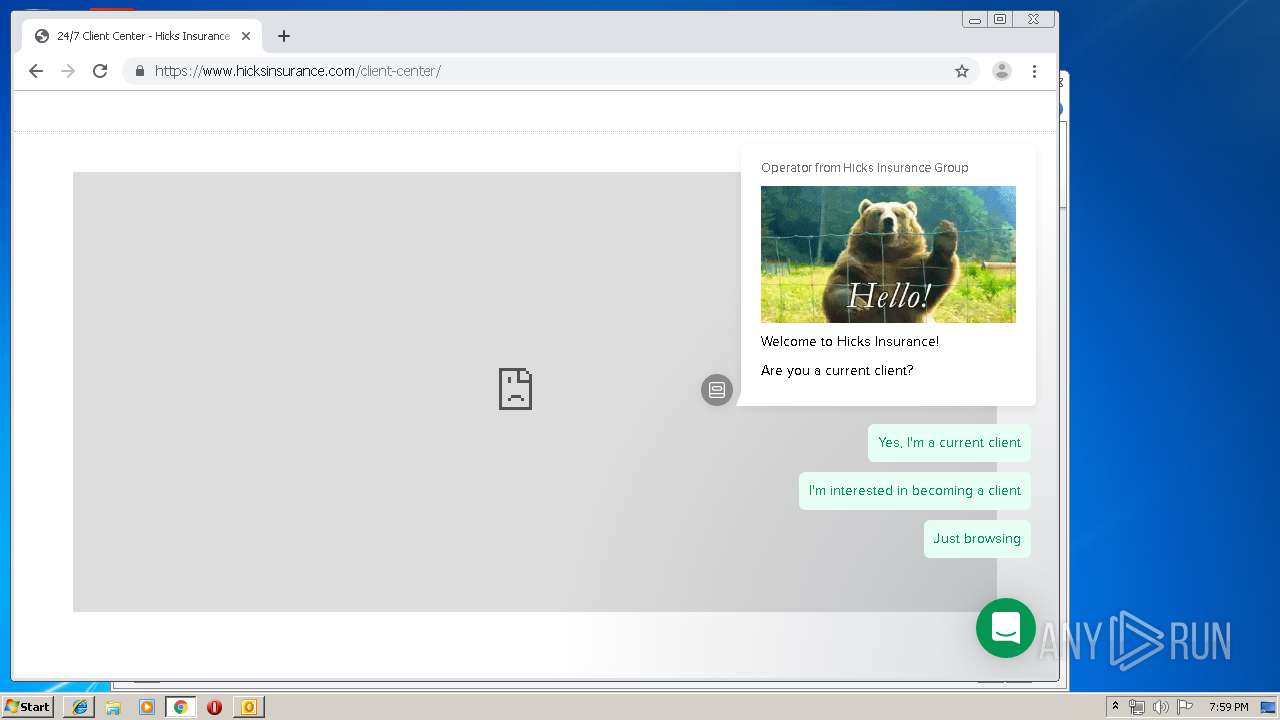
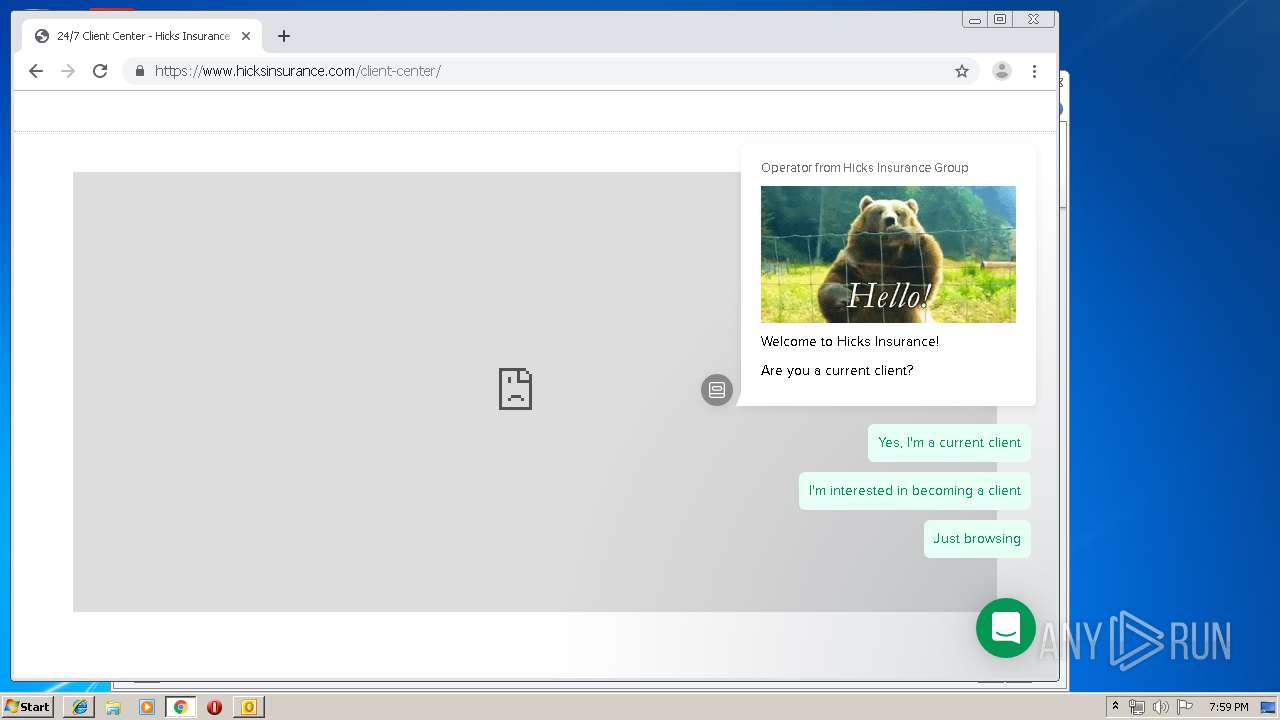
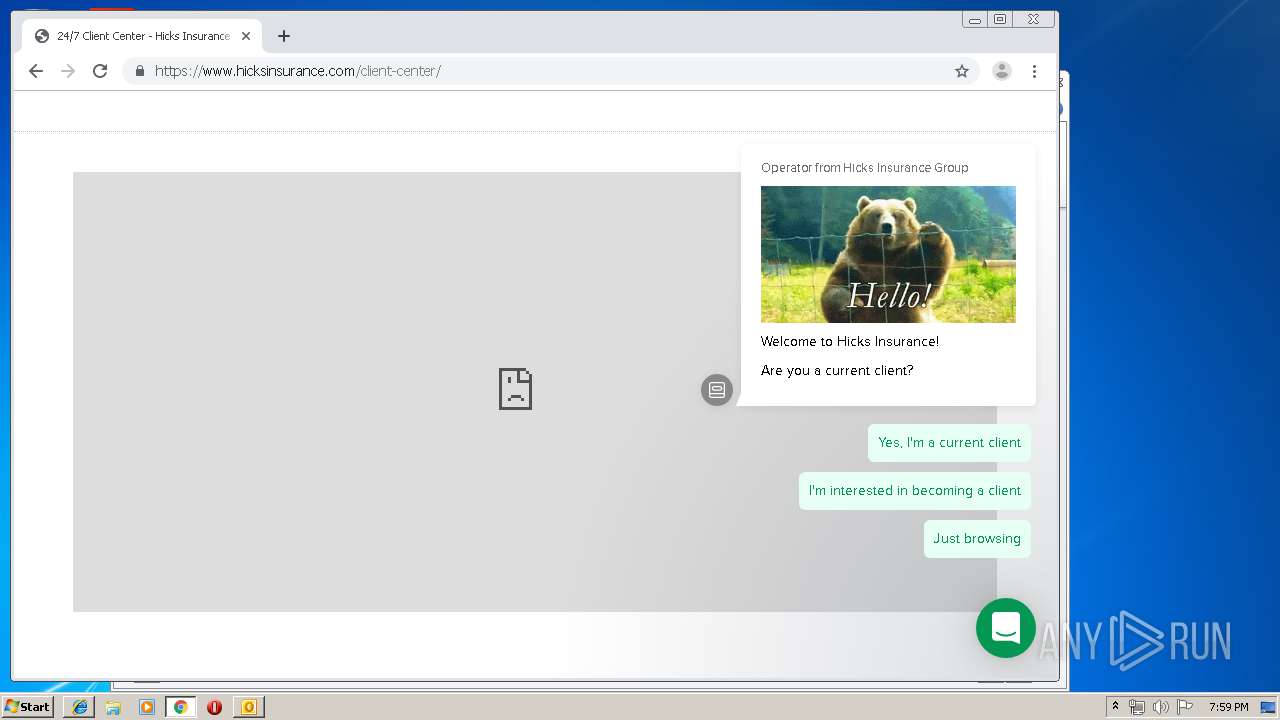
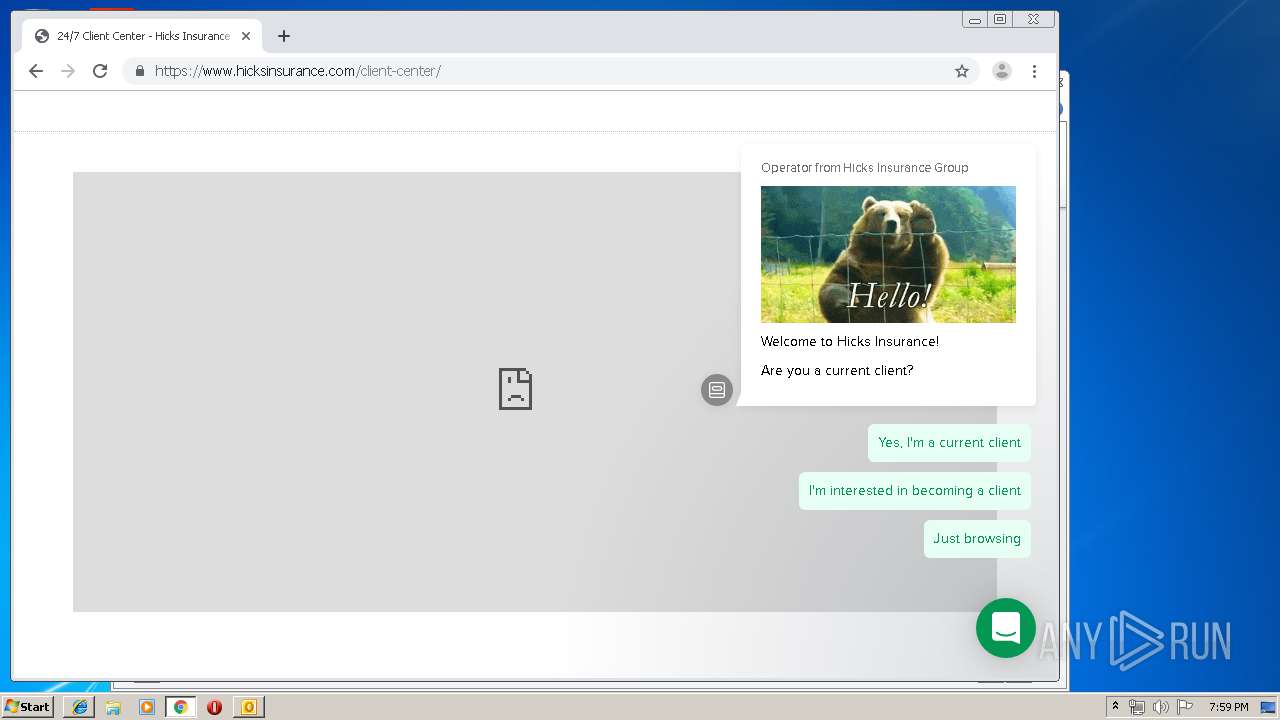
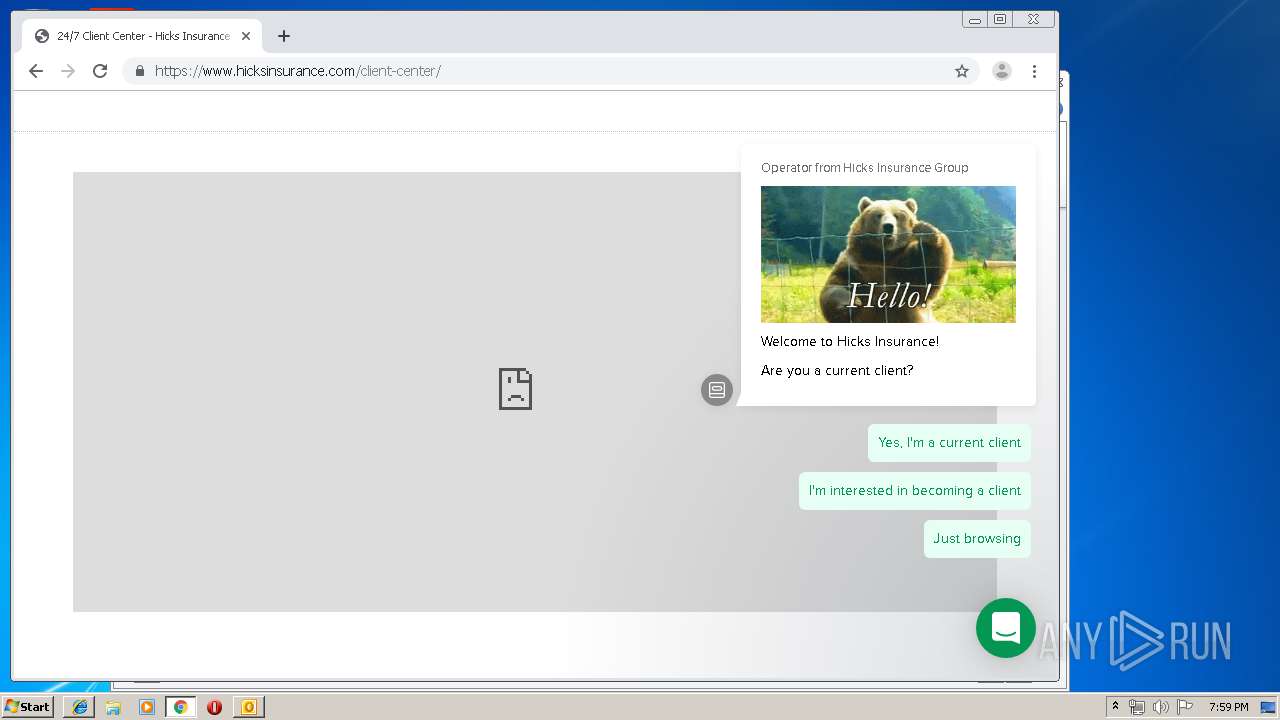
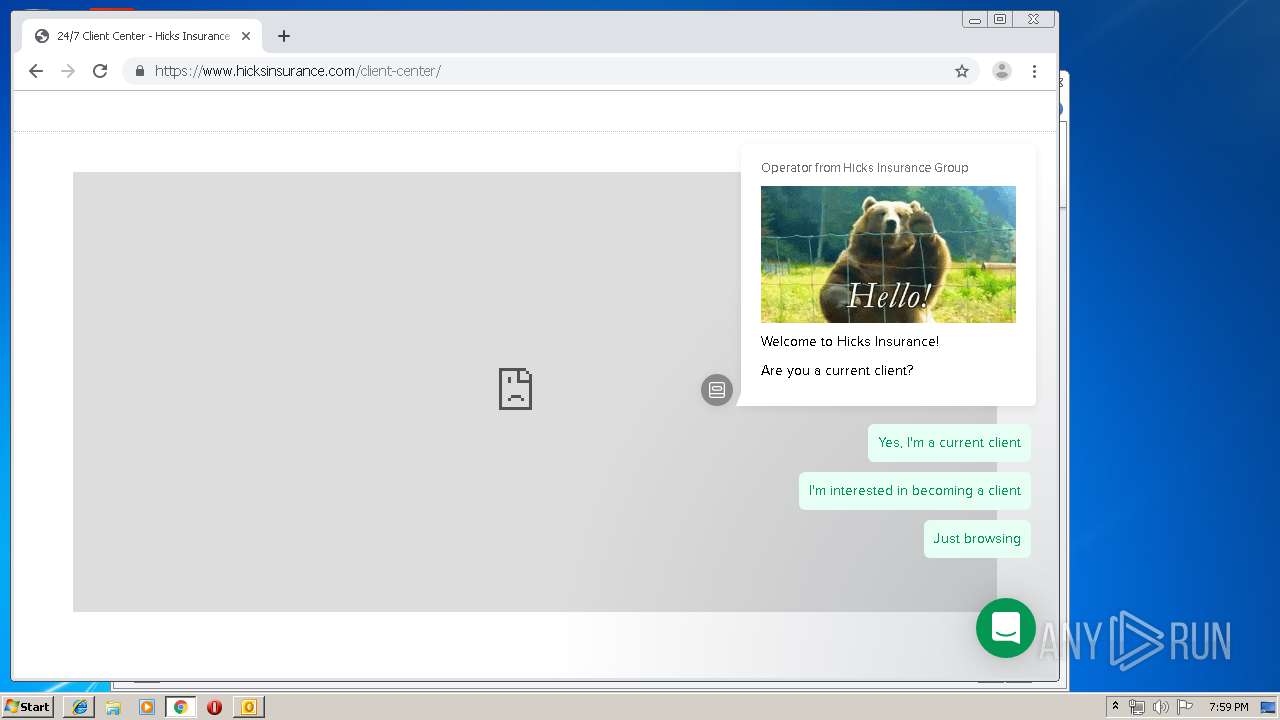
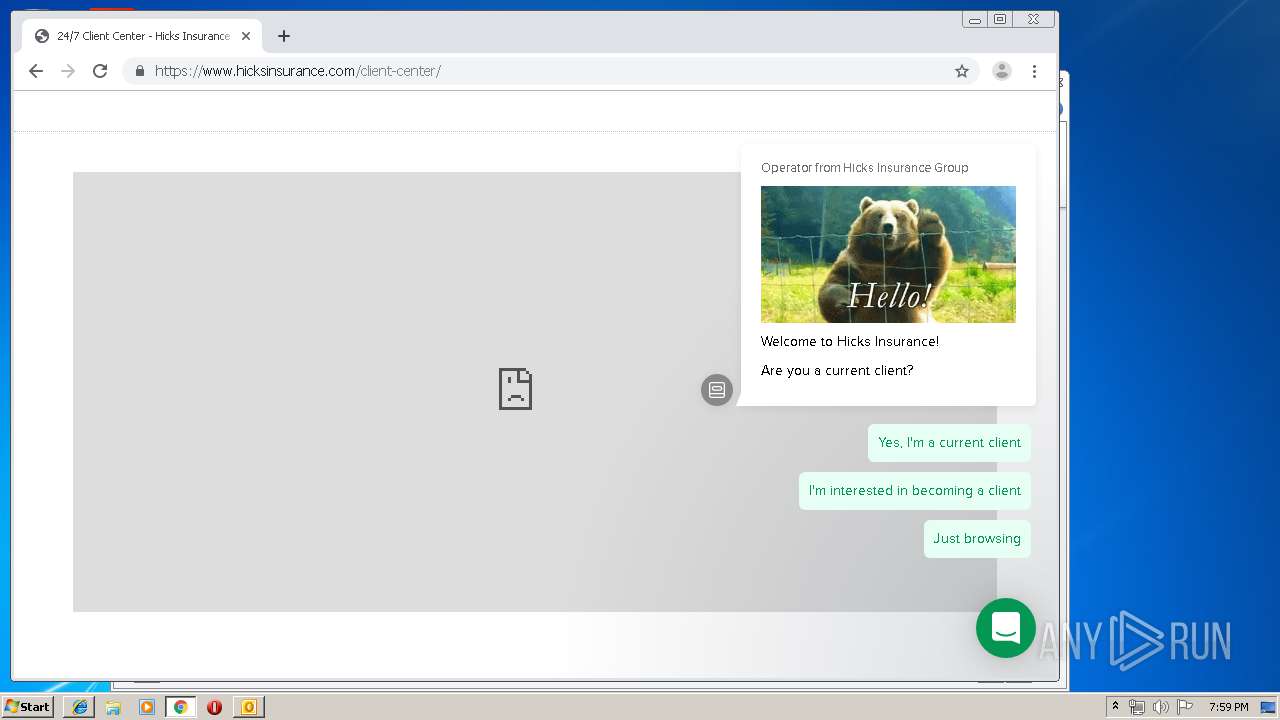
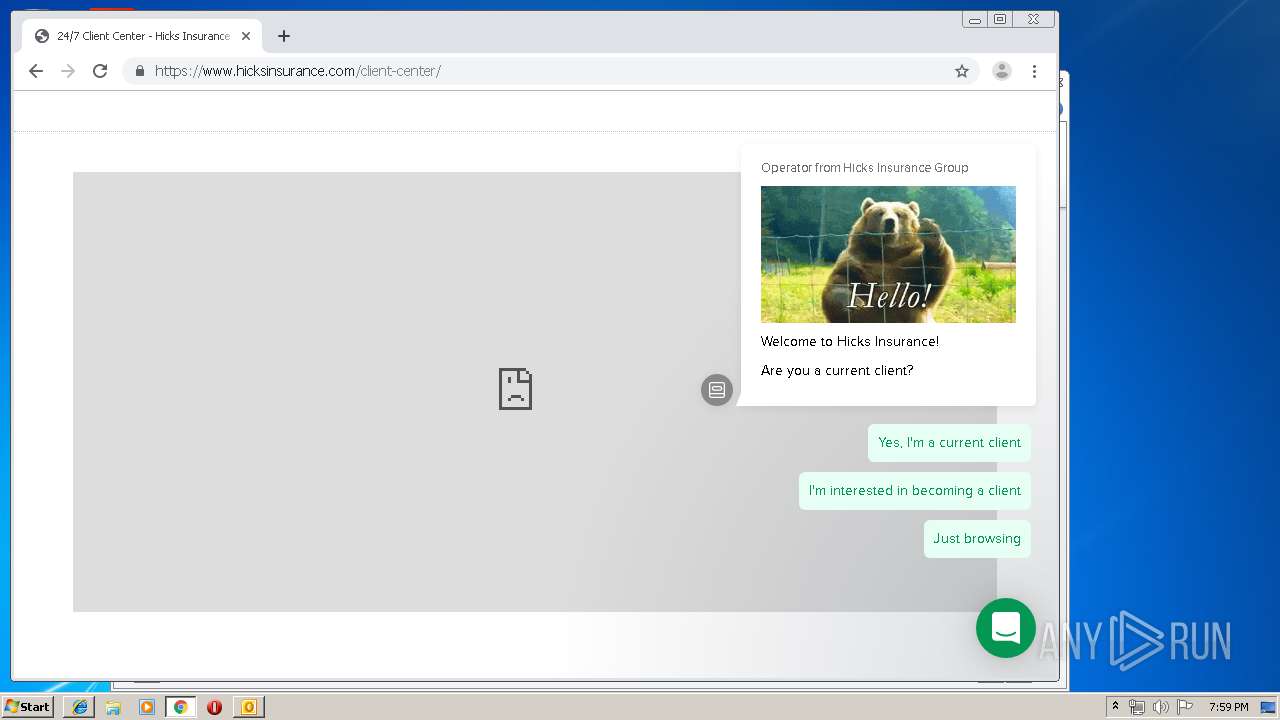
3580 | iexplore.exe | 184.168.47.225:443 | www.hicksinsurance.com | GoDaddy.com, LLC | US | malicious |
2760 | chrome.exe | 172.217.21.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2760 | chrome.exe | 172.217.22.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
— | — | 172.217.21.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2760 | chrome.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2760 | chrome.exe | 172.217.23.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
nam05.safelinks.protection.outlook.com |
| whitelisted |
www.bing.com |
| whitelisted |
u6091044.ct.sendgrid.net |
| malicious |
www.hicksinsurance.com |
| malicious |
dns.msftncsi.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |