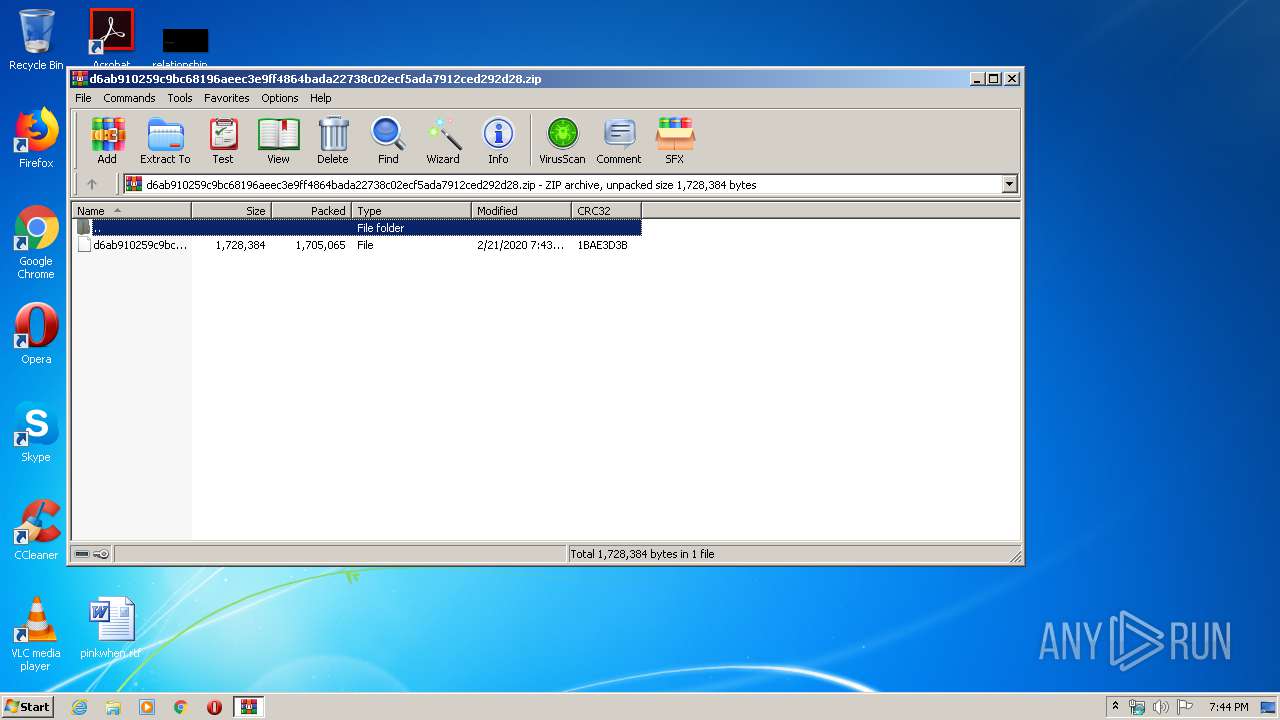
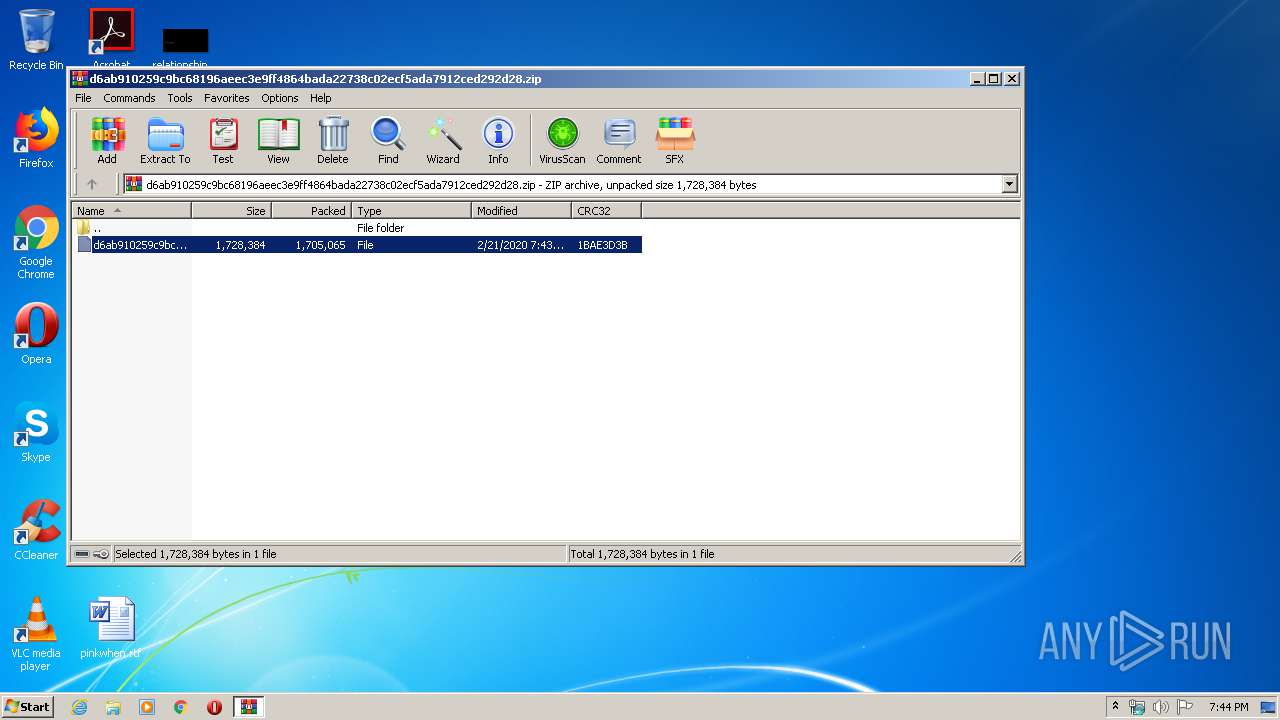
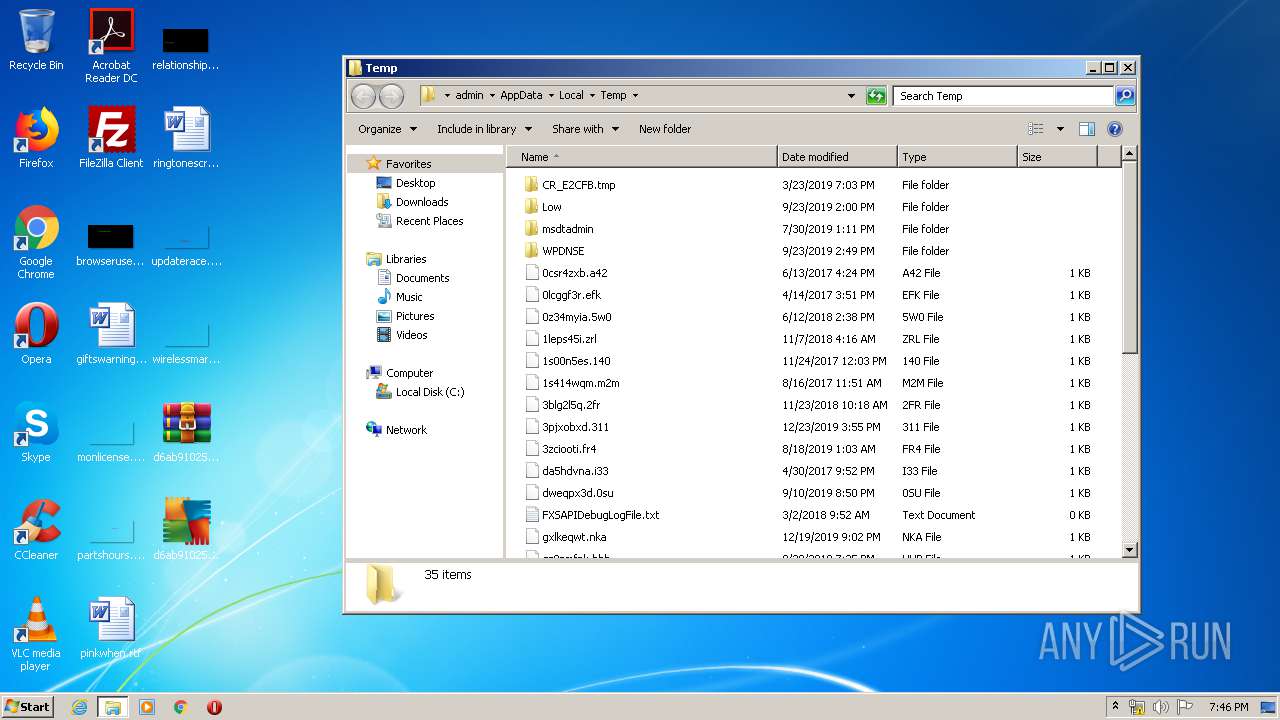
| File name: | d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.zip |
| Full analysis: | https://app.any.run/tasks/c24faea0-e041-45be-969a-3b18a1dc6e9b |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2020, 19:43:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FED0312E3BB72E4D2527022B74923FA9 |
| SHA1: | A0A5457D7C67112CC242B3089BBA5209657299F0 |
| SHA256: | E1B4FD20F4ACA16193BF3E559AE28571360C4A978396BF7D18BF0BC560A4D409 |
| SSDEEP: | 24576:FYI87DBIIctRt8HdqzuPeqH6OV3bafC2goIdZprw7LipyB+awp/508:2I8DyIcN8HubmHVLaq2gomUEyVwp/5d |
MALICIOUS
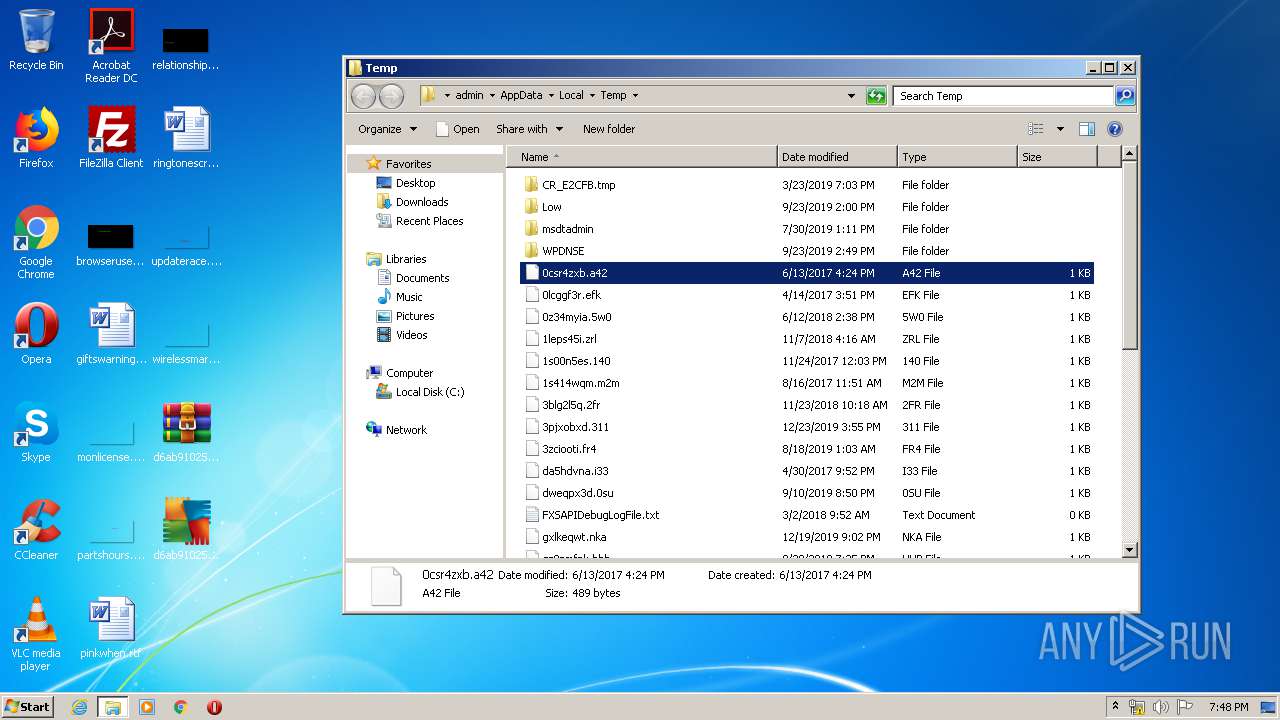
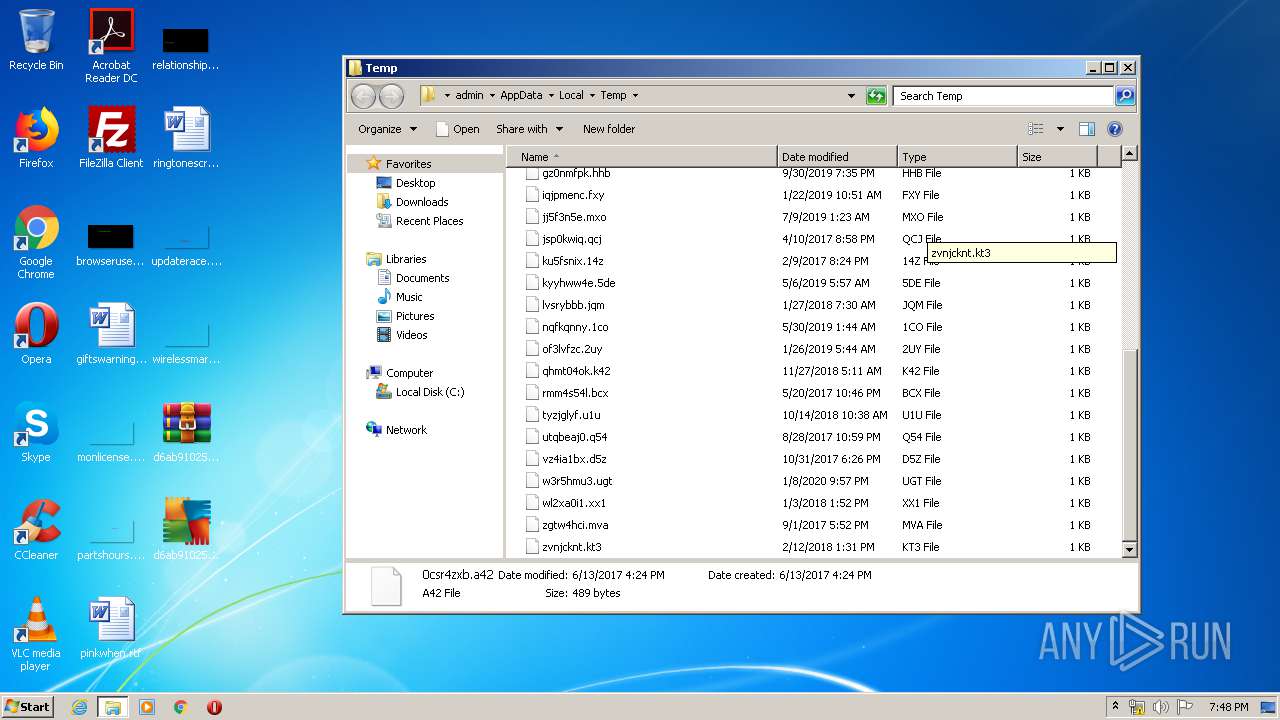
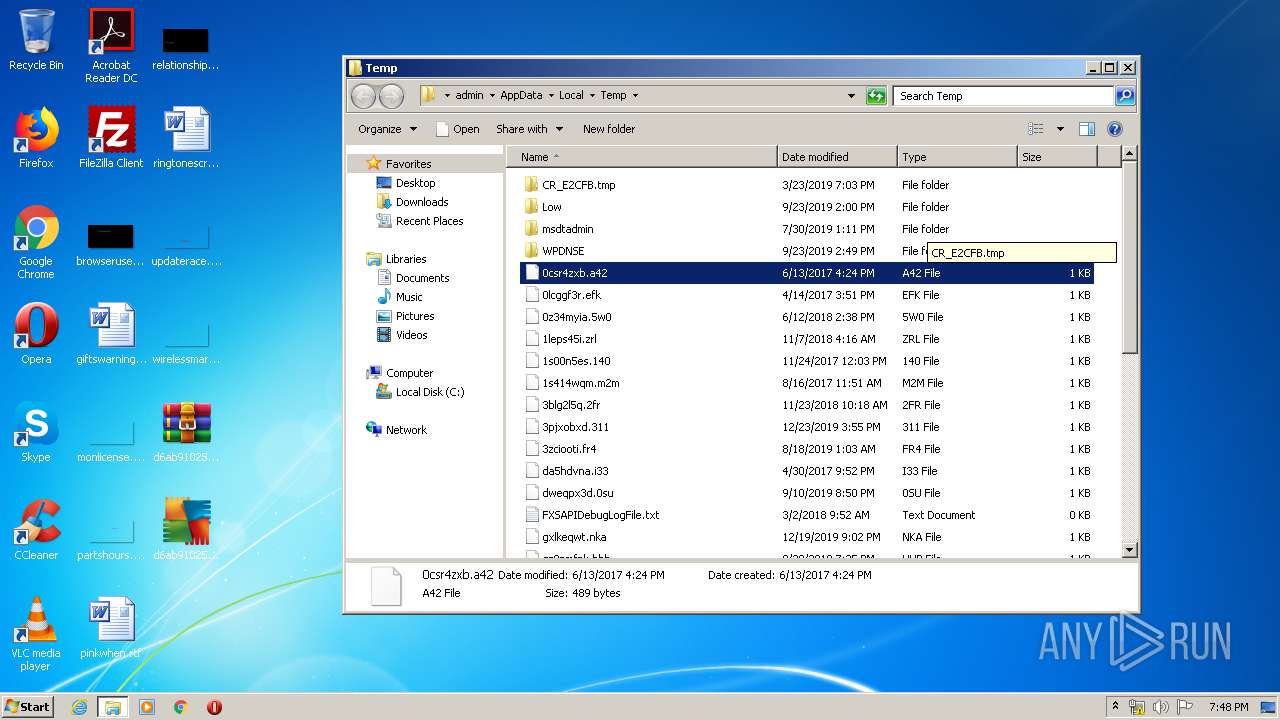
Renames files like Ransomware
- explorer.exe (PID: 372)
Application was dropped or rewritten from another process
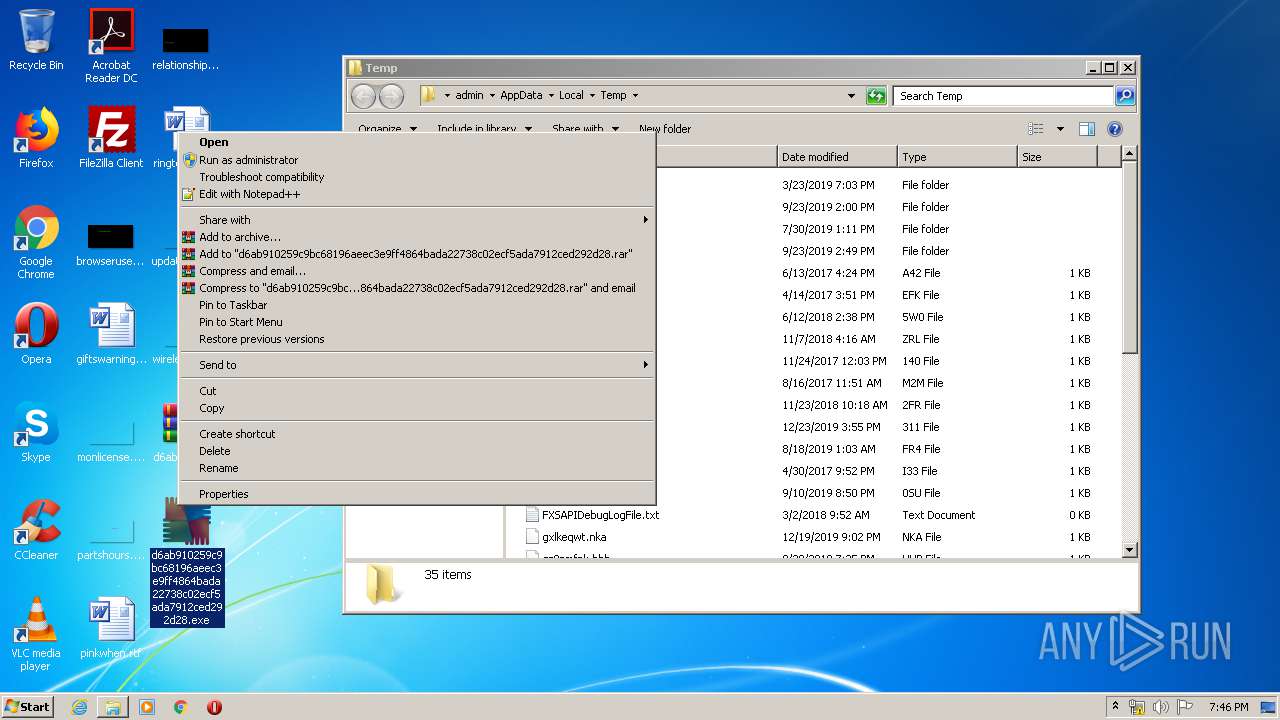
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 2932)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 1520)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 3292)
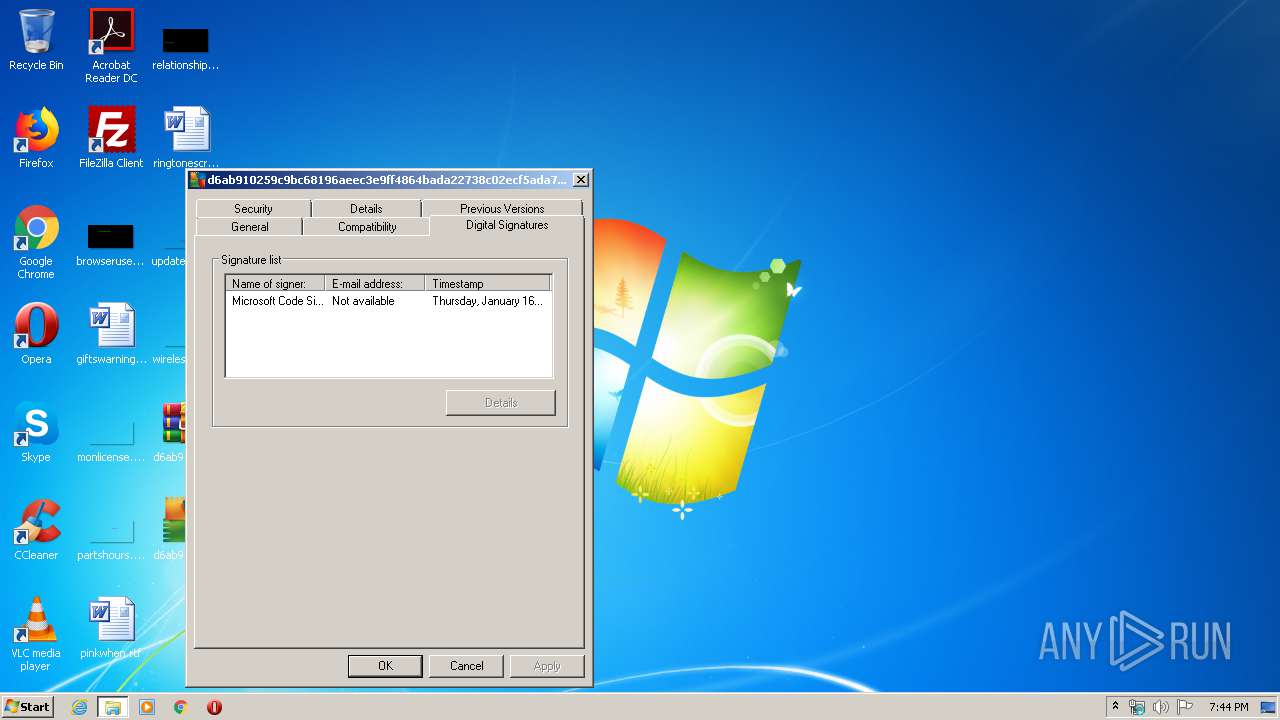
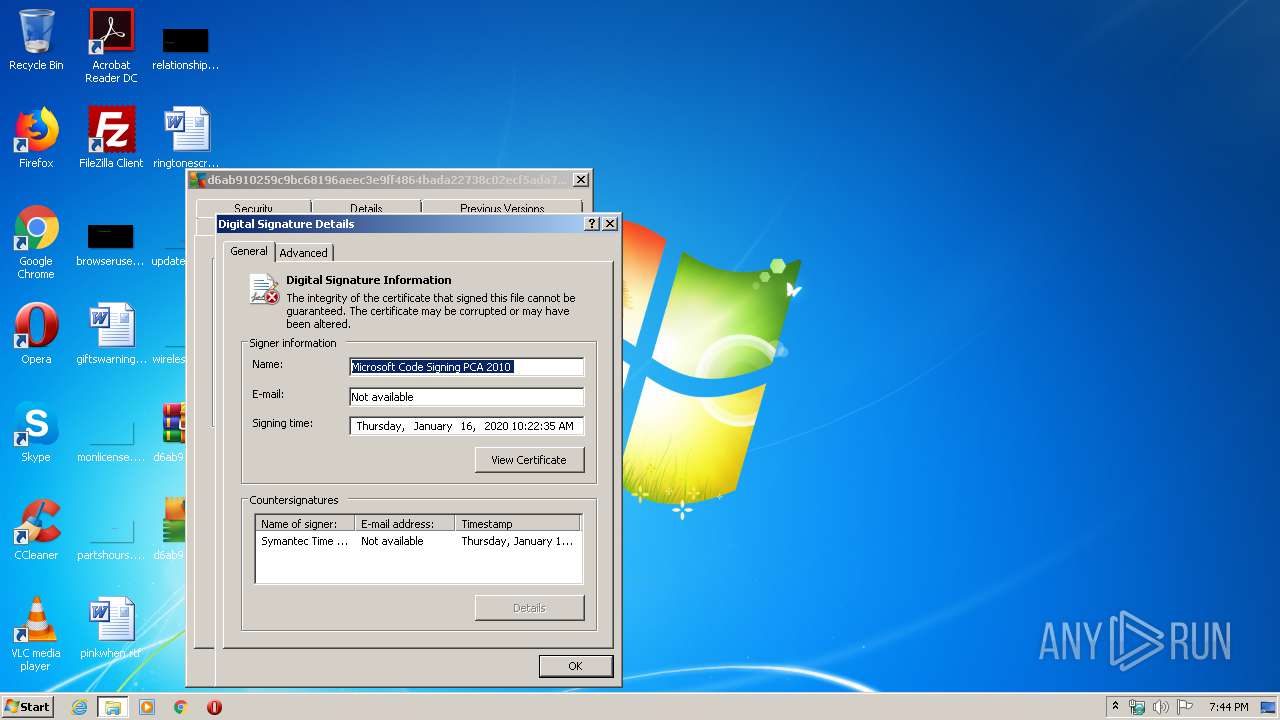
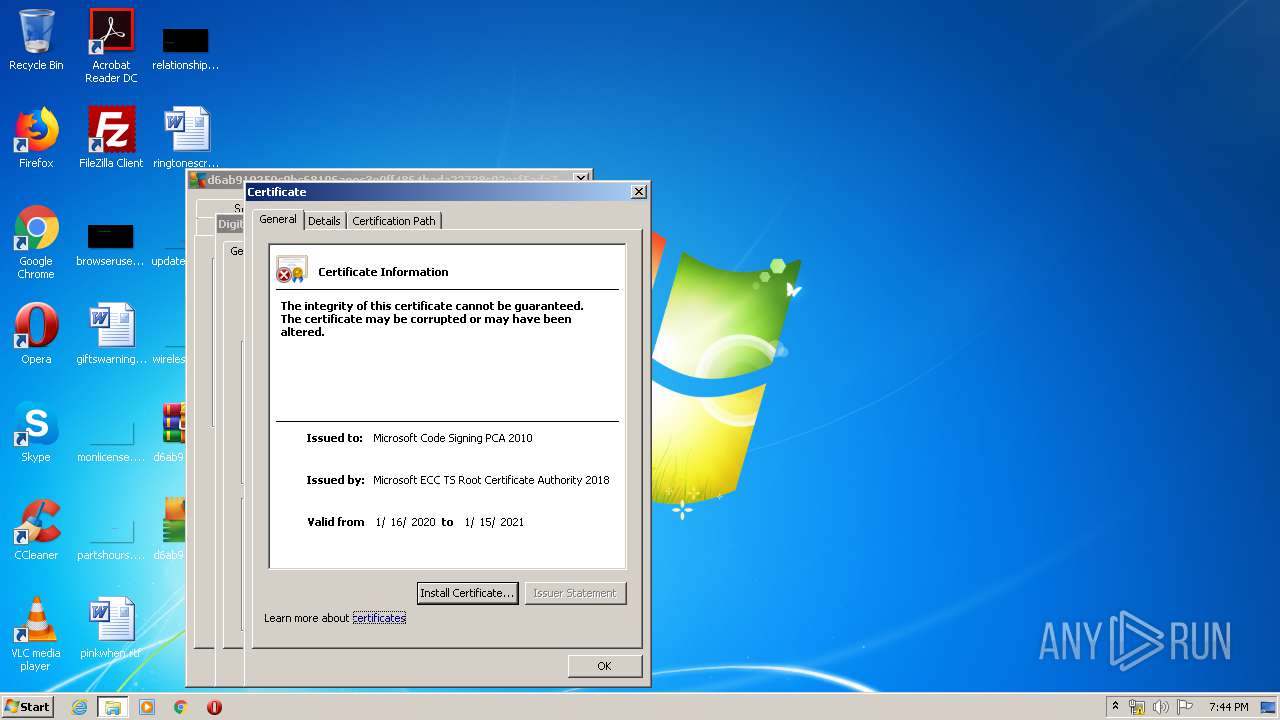
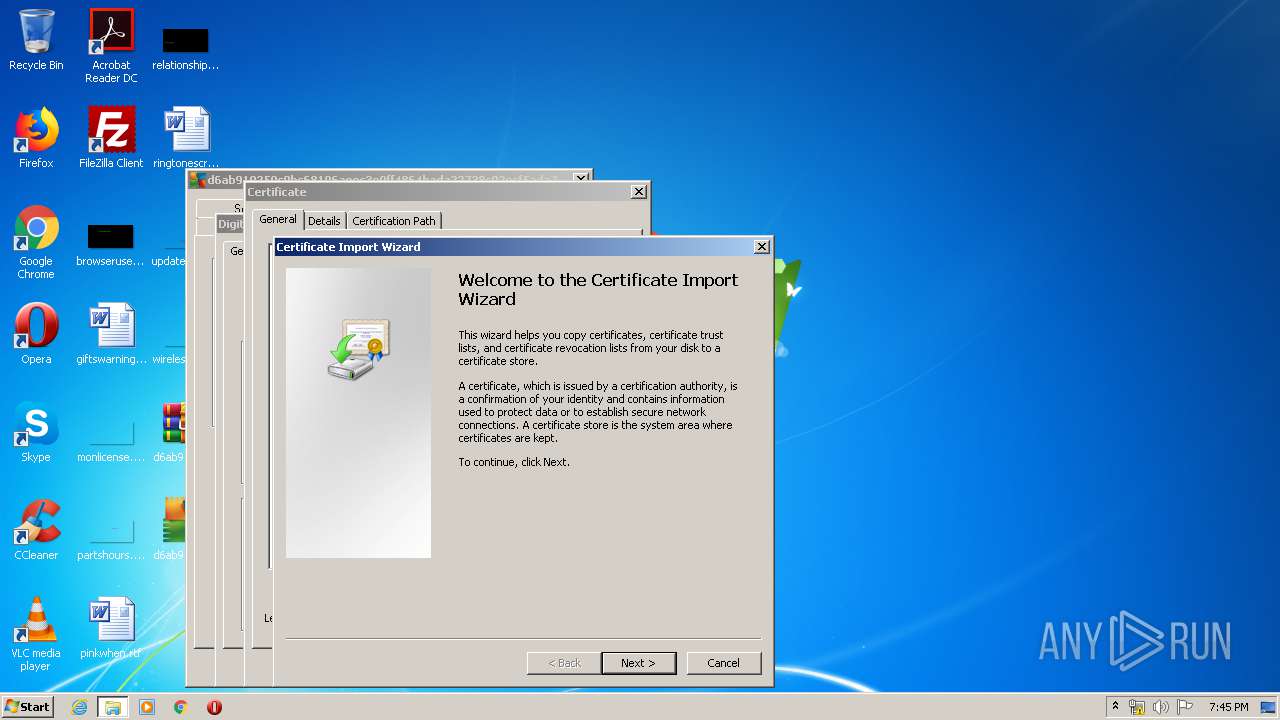
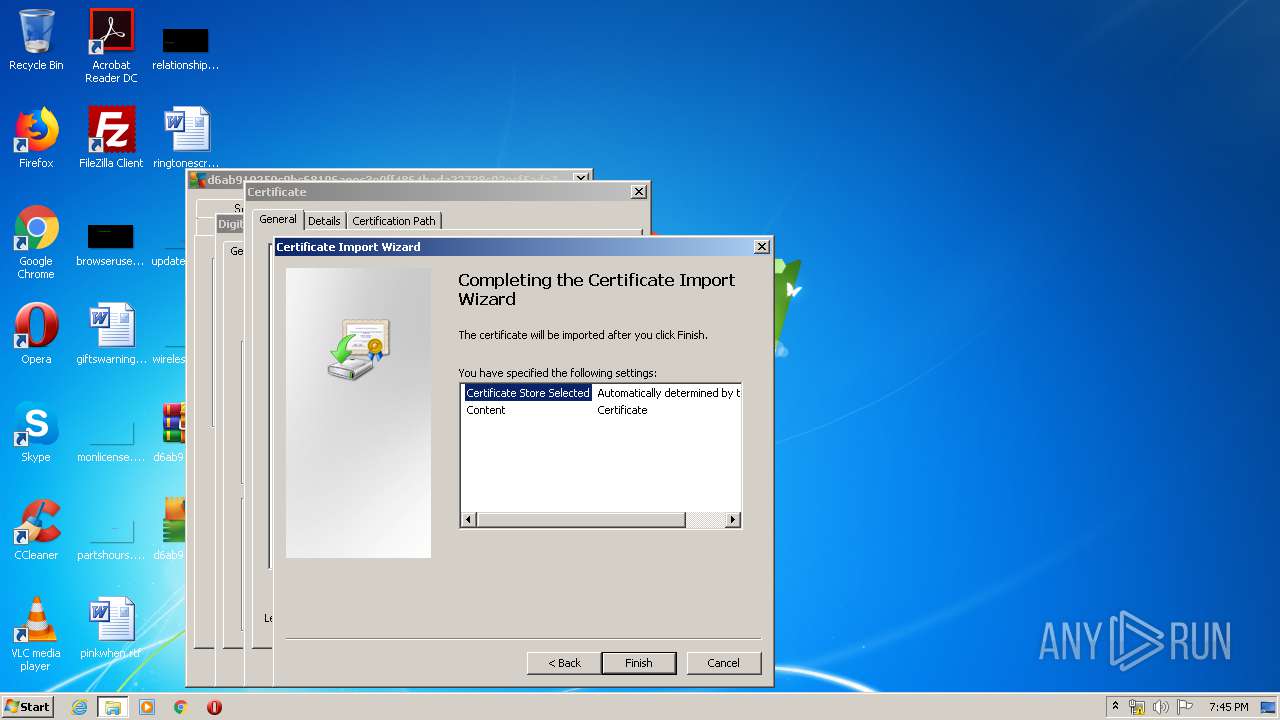
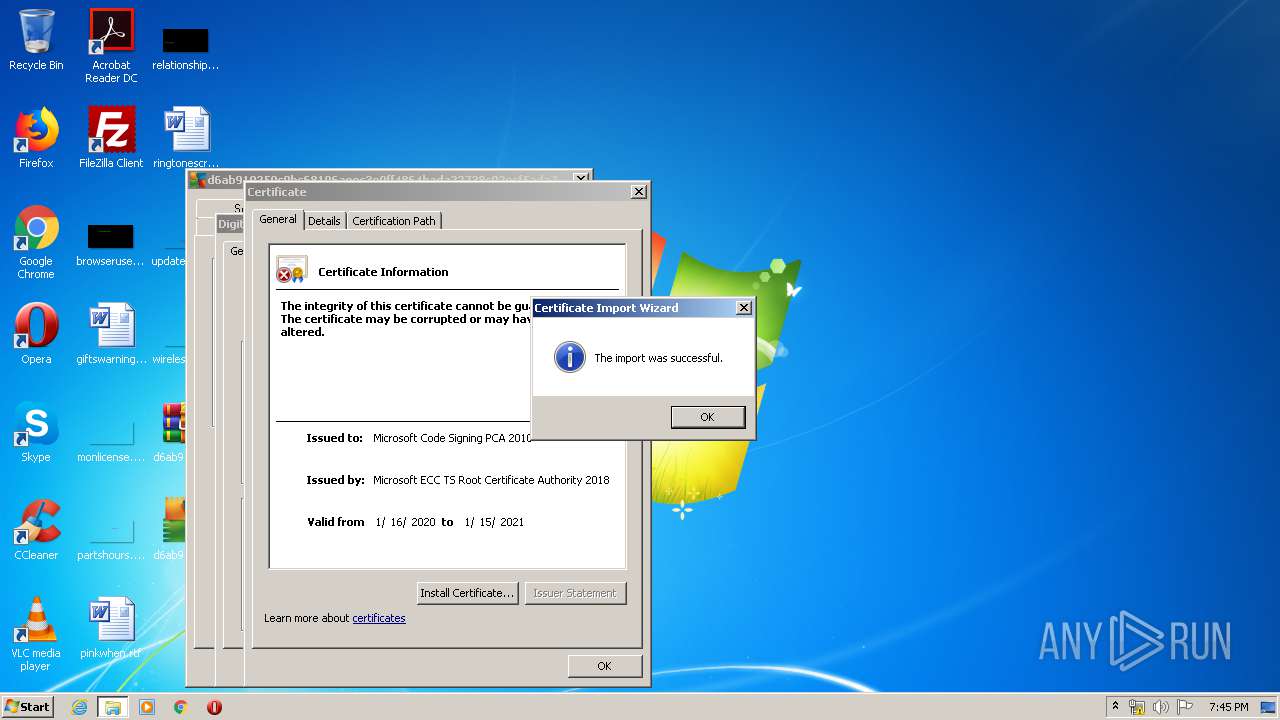
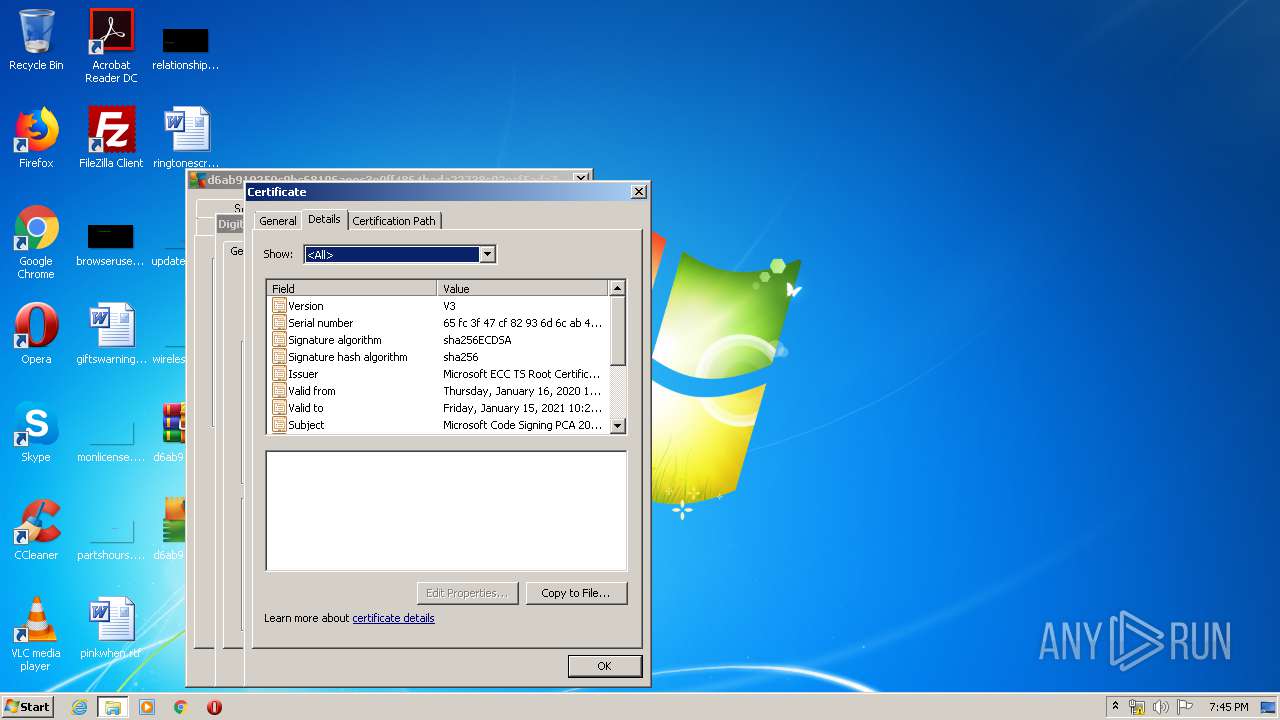
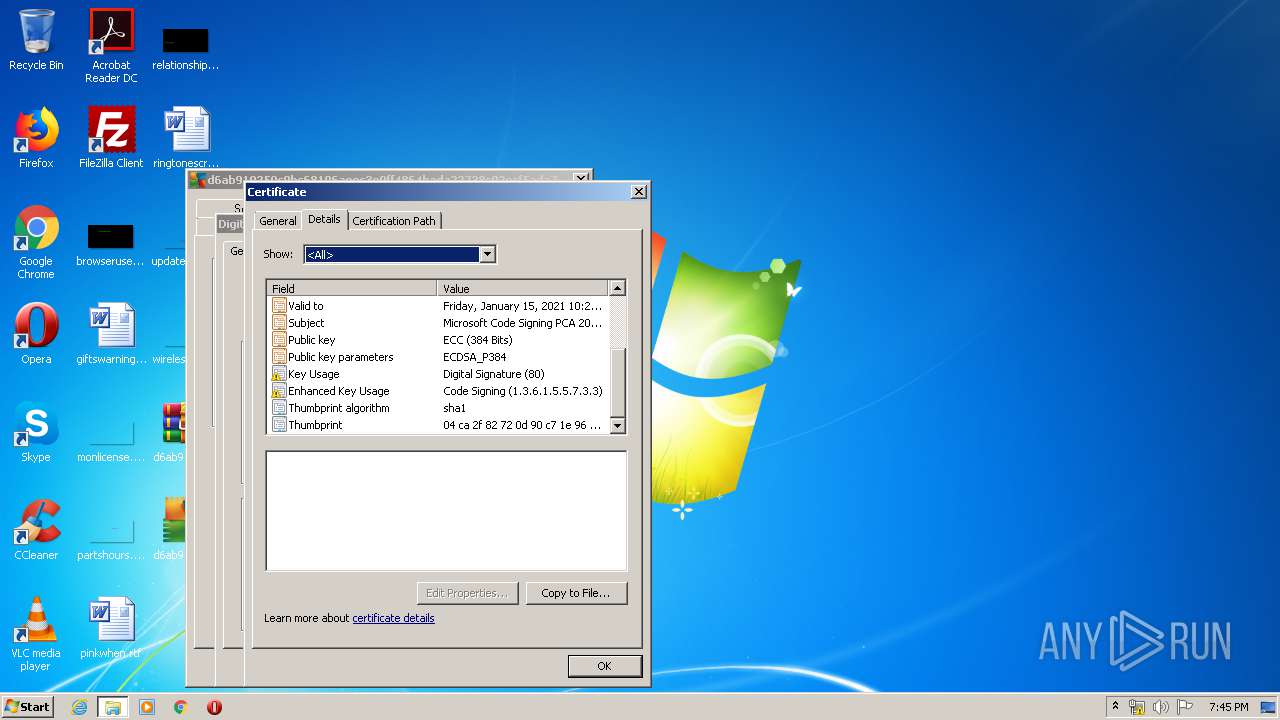
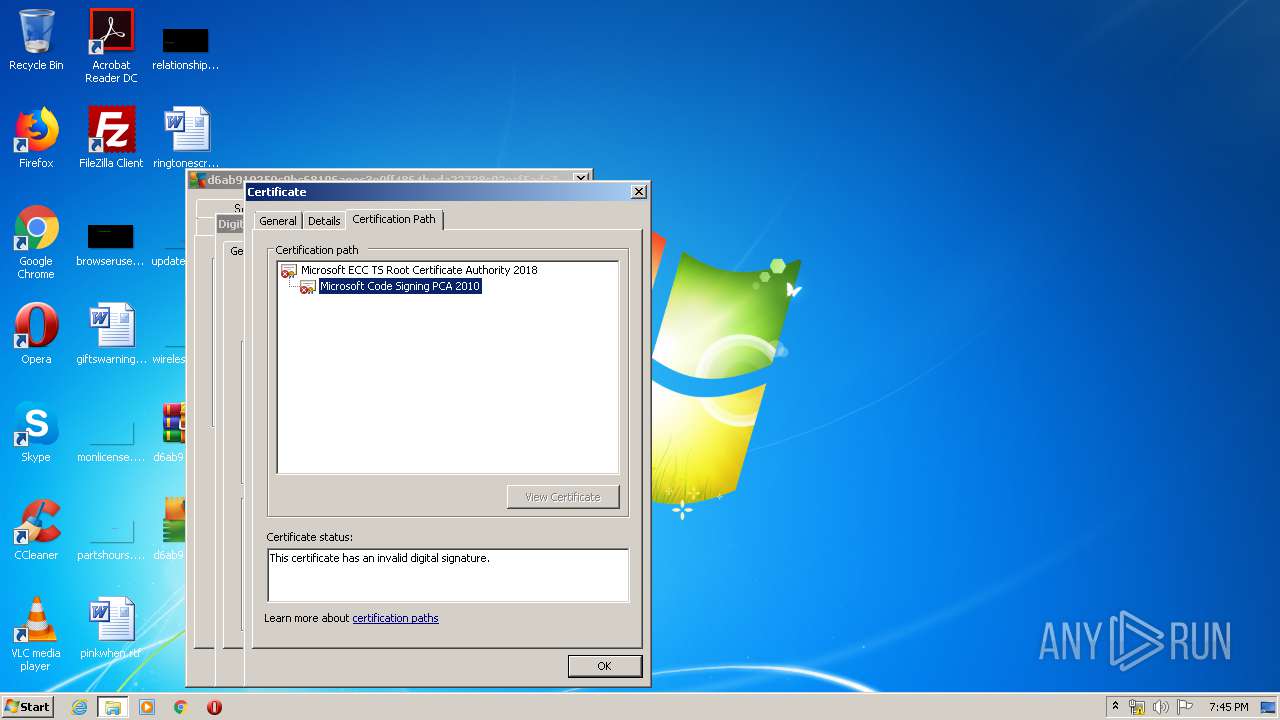
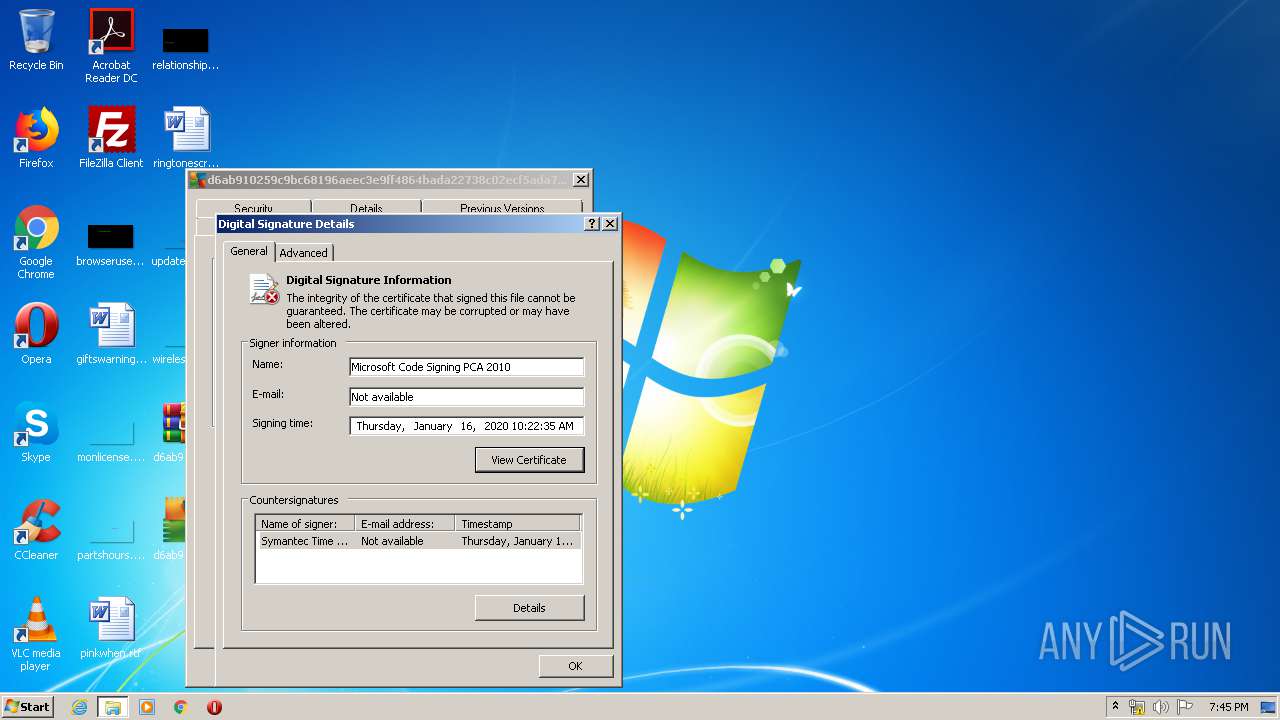
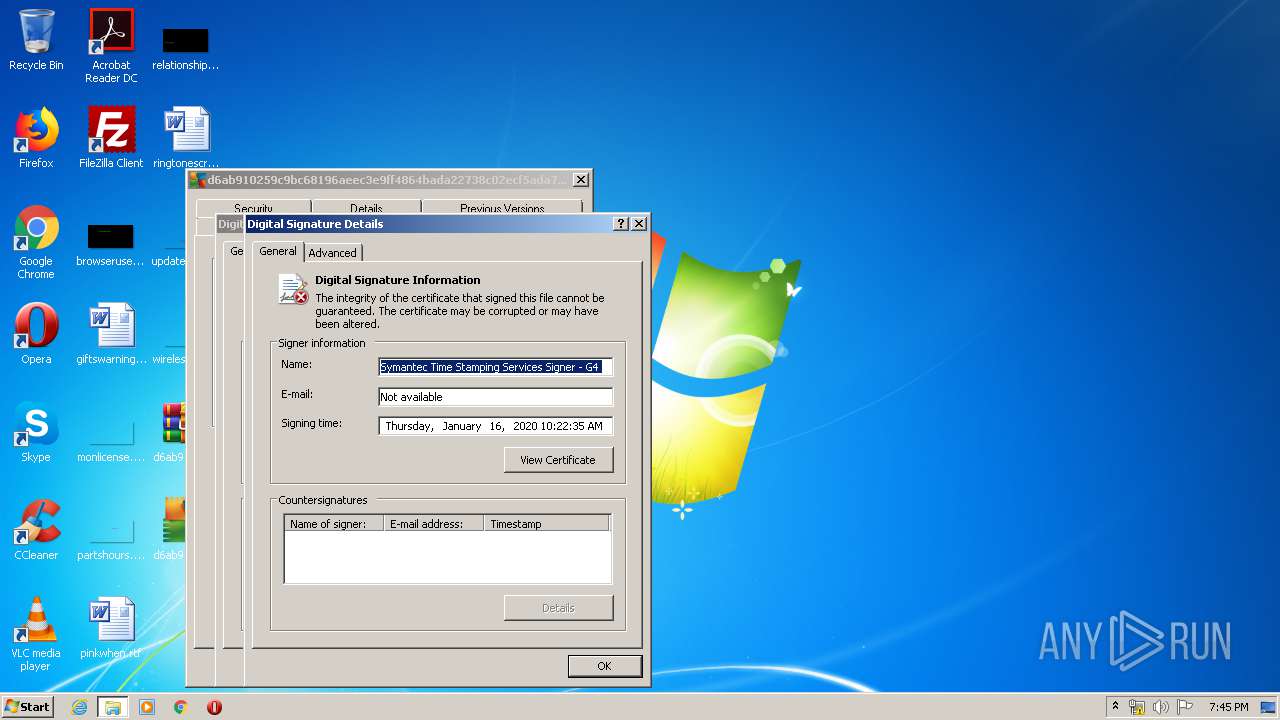
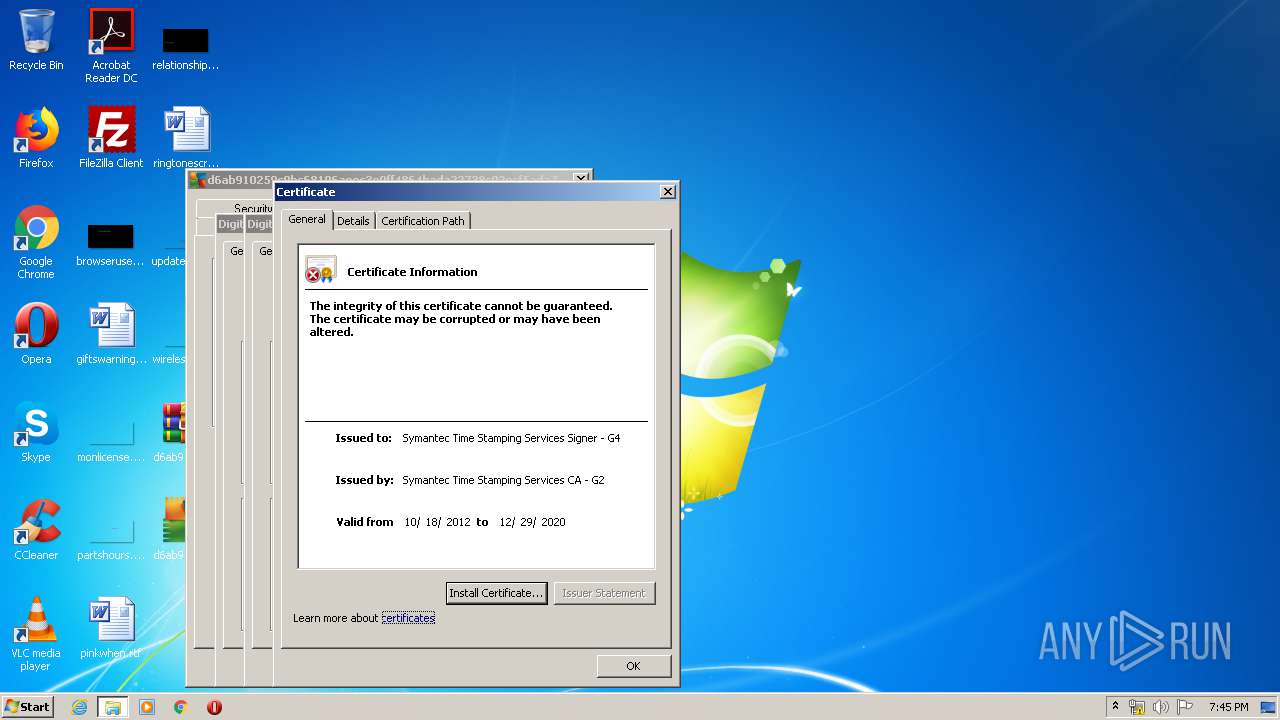
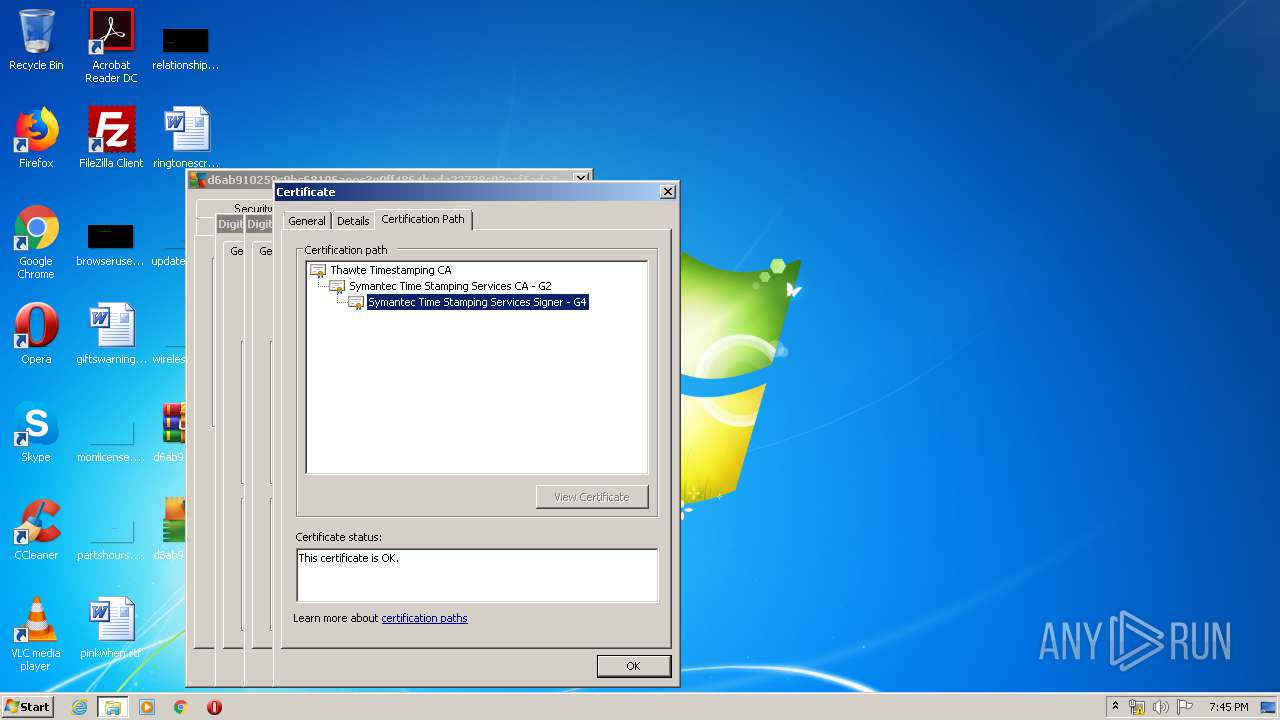
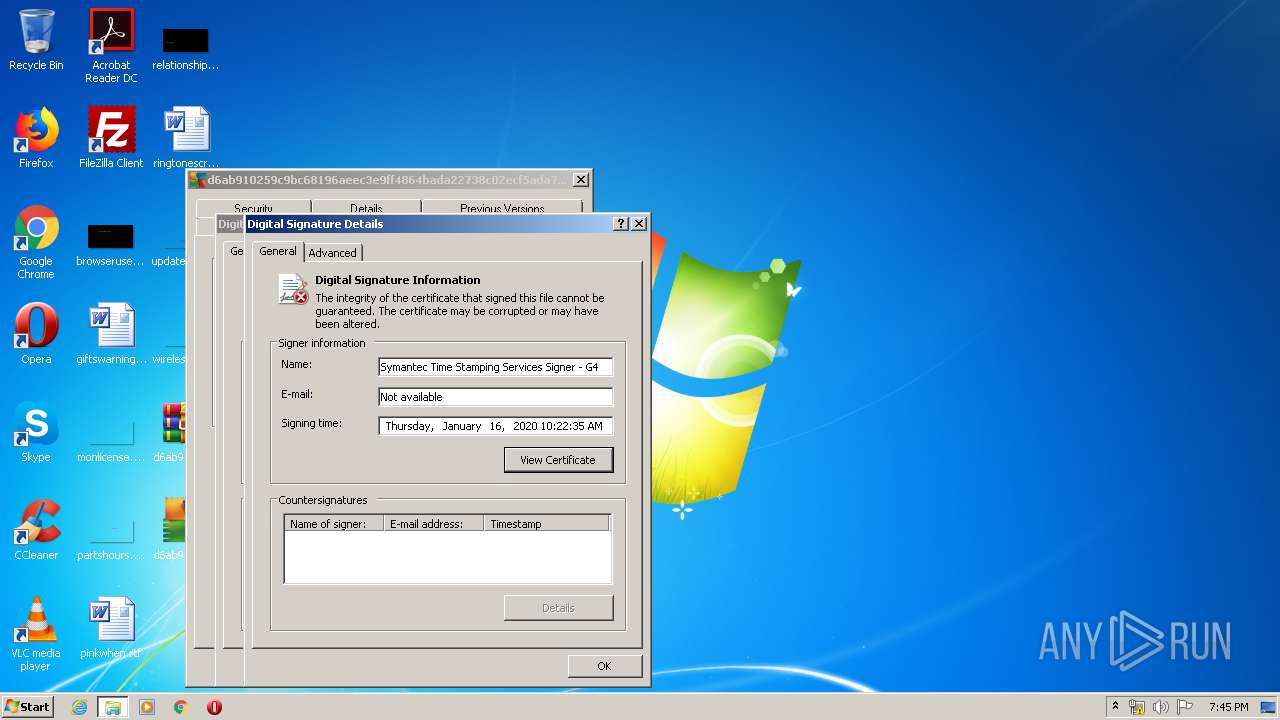
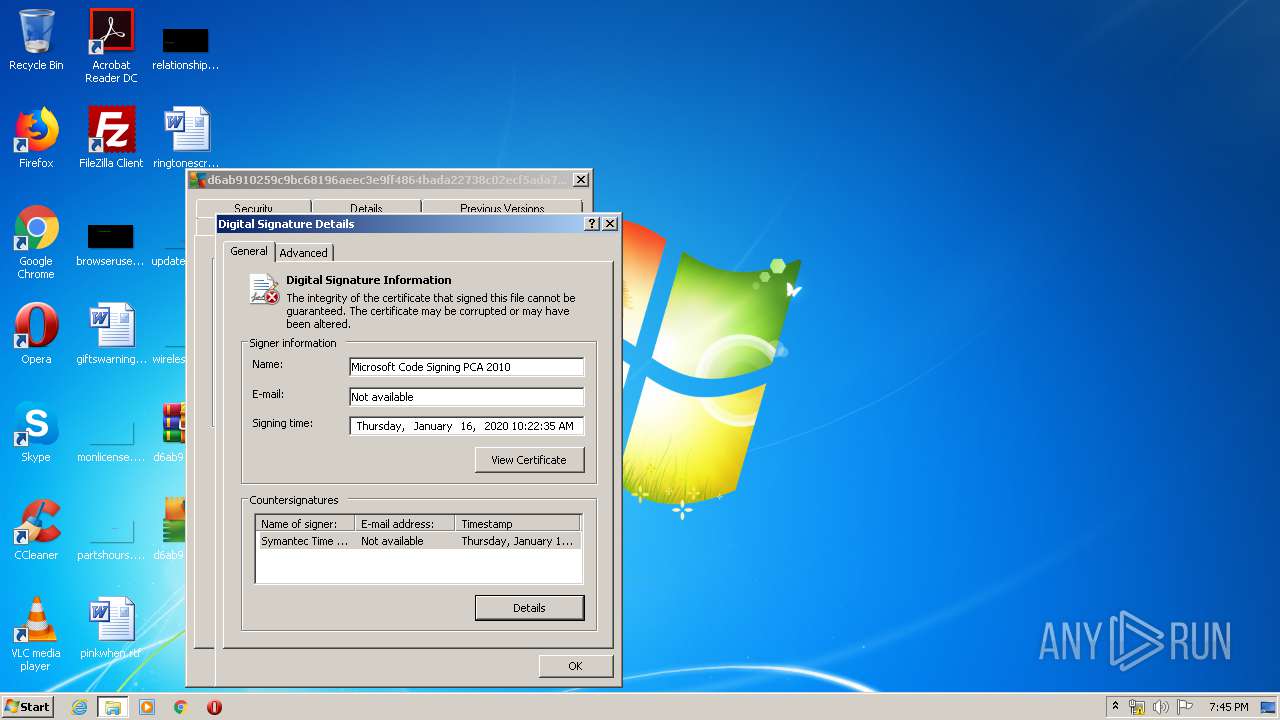
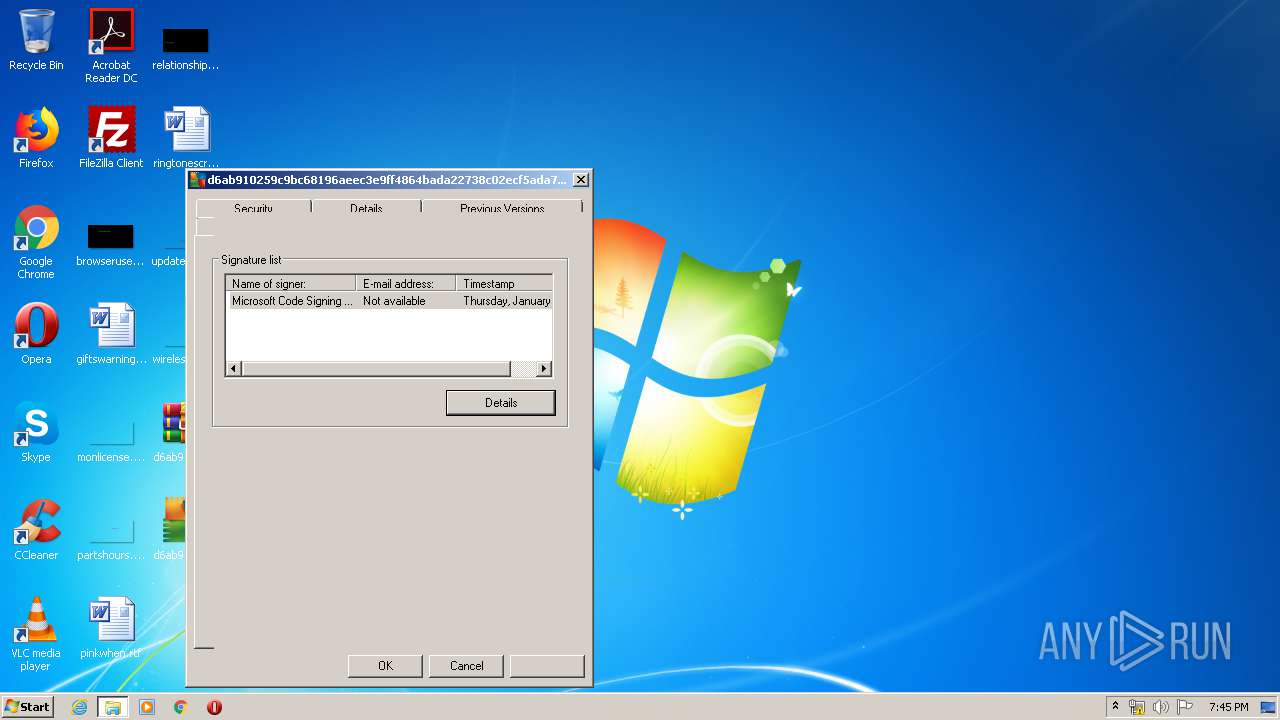
Changes settings of System certificates
- explorer.exe (PID: 372)
Runs app for hidden code execution
- explorer.exe (PID: 372)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 372)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 2932)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3328)
Starts CMD.EXE for commands execution
- explorer.exe (PID: 372)
Writes to a desktop.ini file (may be used to cloak folders)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 1520)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 3292)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 2932)
Creates files in the program directory
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 3292)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 1520)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 2932)
INFO
Dropped object may contain Bitcoin addresses
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 3292)
- d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe (PID: 1520)
Reads settings of System Certificates
- explorer.exe (PID: 372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:02:21 20:43:10 |
| ZipCRC: | 0x1bae3d3b |
| ZipCompressedSize: | 1705065 |
| ZipUncompressedSize: | 1728384 |
| ZipFileName: | d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28 |
Total processes
46
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
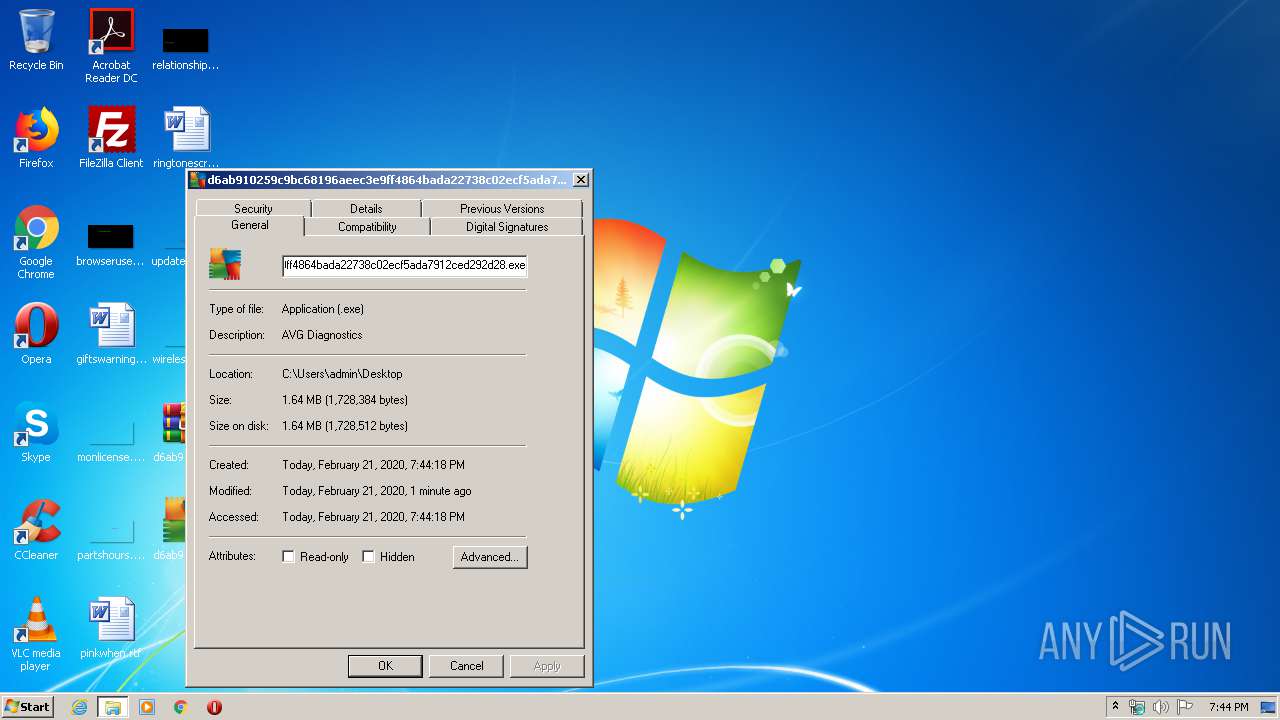
| 1520 | "C:\Users\admin\Desktop\d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe" | C:\Users\admin\Desktop\d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe | explorer.exe | ||||||||||||
User: admin Company: AVG Technologies, sro Integrity Level: HIGH Description: AVG Diagnostics Exit code: 0 Version: 14.0.1001.380 Modules
| |||||||||||||||
| 2932 | "C:\Users\admin\Desktop\d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe" | C:\Users\admin\Desktop\d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe | — | explorer.exe | |||||||||||
User: admin Company: AVG Technologies, sro Integrity Level: MEDIUM Description: AVG Diagnostics Exit code: 0 Version: 14.0.1001.380 Modules
| |||||||||||||||
| 3180 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3292 | d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe --AutoStart | C:\Users\admin\Desktop\d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.exe | — | cmd.exe | |||||||||||
User: admin Company: AVG Technologies, sro Integrity Level: MEDIUM Description: AVG Diagnostics Exit code: 0 Version: 14.0.1001.380 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3820 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 660
Read events
3 308
Write events
352
Delete events
0
Modification events
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\d6ab910259c9bc68196aeec3e9ff4864bada22738c02ecf5ada7912ced292d28.zip | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3328) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
2
Suspicious files
1 628
Text files
1 851
Unknown types
50
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\CabD81.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\TarD82.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\CabD93.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\TarD94.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\CabDF3.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\TarDF4.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\Cab1C0E.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\Tar1C0F.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\Cab1C2F.tmp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Local\Temp\Tar1C30.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
372 | explorer.exe | GET | 200 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.4 Kb | whitelisted |
372 | explorer.exe | GET | 304 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.4 Kb | whitelisted |
372 | explorer.exe | GET | 304 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.4 Kb | whitelisted |
372 | explorer.exe | GET | 304 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.4 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
372 | explorer.exe | 205.185.216.42:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |