| File name: | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe |
| Full analysis: | https://app.any.run/tasks/755c0f00-141b-4bf7-a9ee-49f1ba9d4d2e |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2024, 02:50:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | D39F2BB352876D16D8661FEDBF5F0252 |
| SHA1: | 851490097F175670E8579337FF26AEB24BA7837E |
| SHA256: | E1AF498F95432A4F2F666A8CBEC7BD6AB9DEB4D1695C6E7CDE7ACB9BD408E600 |
| SSDEEP: | 393216:lB+H8Mf4b1KoAUhH6sB0xyAWsx/iSR6o/DWdk:lB+cMfA1KoAUhH6sBcosY+6oV |
MALICIOUS
Drops the executable file immediately after the start
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
SUSPICIOUS
Executable content was dropped or overwritten
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
Malware-specific behavior (creating "System.dll" in Temp)
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
The process creates files with name similar to system file names
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
Creates a software uninstall entry
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
INFO
Reads the computer name
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
Checks supported languages
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
Create files in a temporary directory
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
Creates files in the program directory
- e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe (PID: 4548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:02 02:09:43+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3645 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.19.0 |
| ProductVersionNumber: | 2.0.19.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | ACLAP |
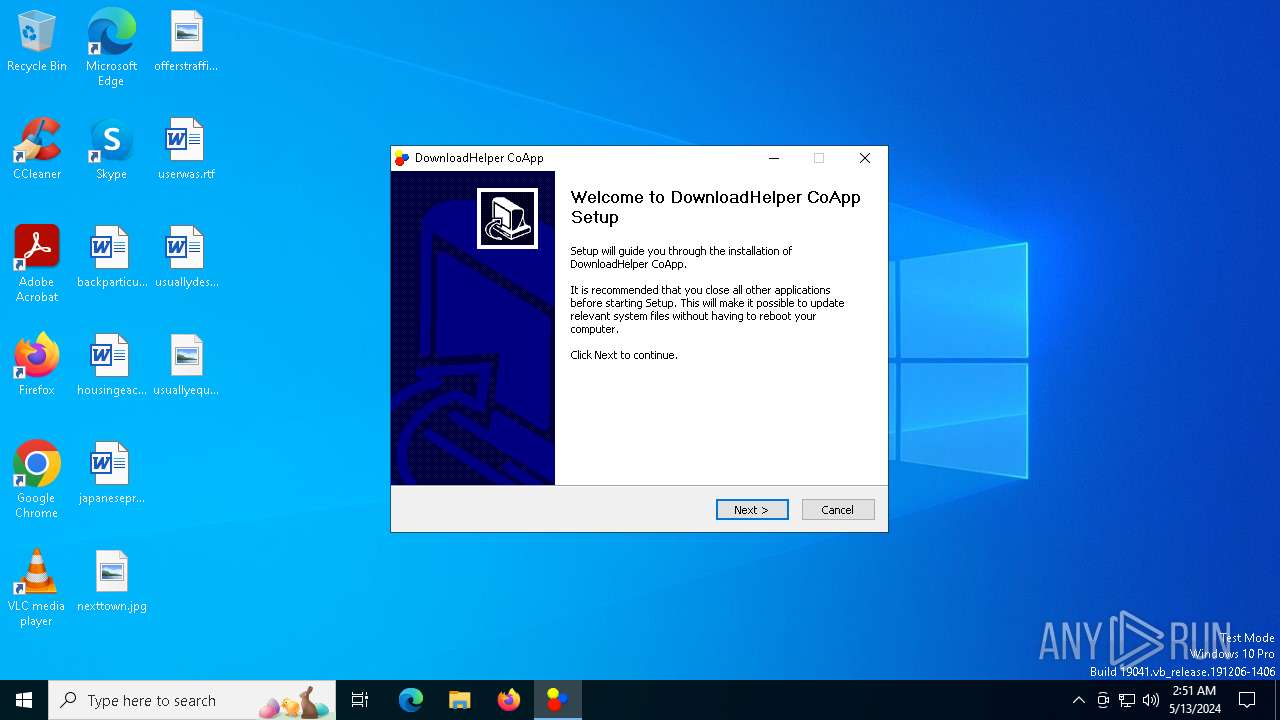
| FileDescription: | Video DownloadHelper companion app |
| FileVersion: | 2.0.19.0 |
| LegalCopyright: | ACLAP |
| ProductName: | DownloadHelper CoApp |
Total processes
125
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4548 | "C:\Users\admin\AppData\Local\Temp\e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe" | C:\Users\admin\AppData\Local\Temp\e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | explorer.exe | ||||||||||||
User: admin Company: ACLAP Integrity Level: HIGH Description: Video DownloadHelper companion app Exit code: 0 Version: 2.0.19.0 Modules
| |||||||||||||||
| 4720 | "C:\Users\admin\AppData\Local\Temp\e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe" | C:\Users\admin\AppData\Local\Temp\e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | — | explorer.exe | |||||||||||
User: admin Company: ACLAP Integrity Level: MEDIUM Description: Video DownloadHelper companion app Exit code: 3221226540 Version: 2.0.19.0 Modules
| |||||||||||||||
| 6016 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
Total events
3 362
Read events
3 357
Write events
5
Delete events
0
Modification events
| (PID) Process: | (4548) e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\DownloadHelper CoApp |
| Operation: | write | Name: | DisplayName |
Value: DownloadHelper CoApp | |||
| (PID) Process: | (4548) e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\DownloadHelper CoApp |
| Operation: | write | Name: | UninstallString |
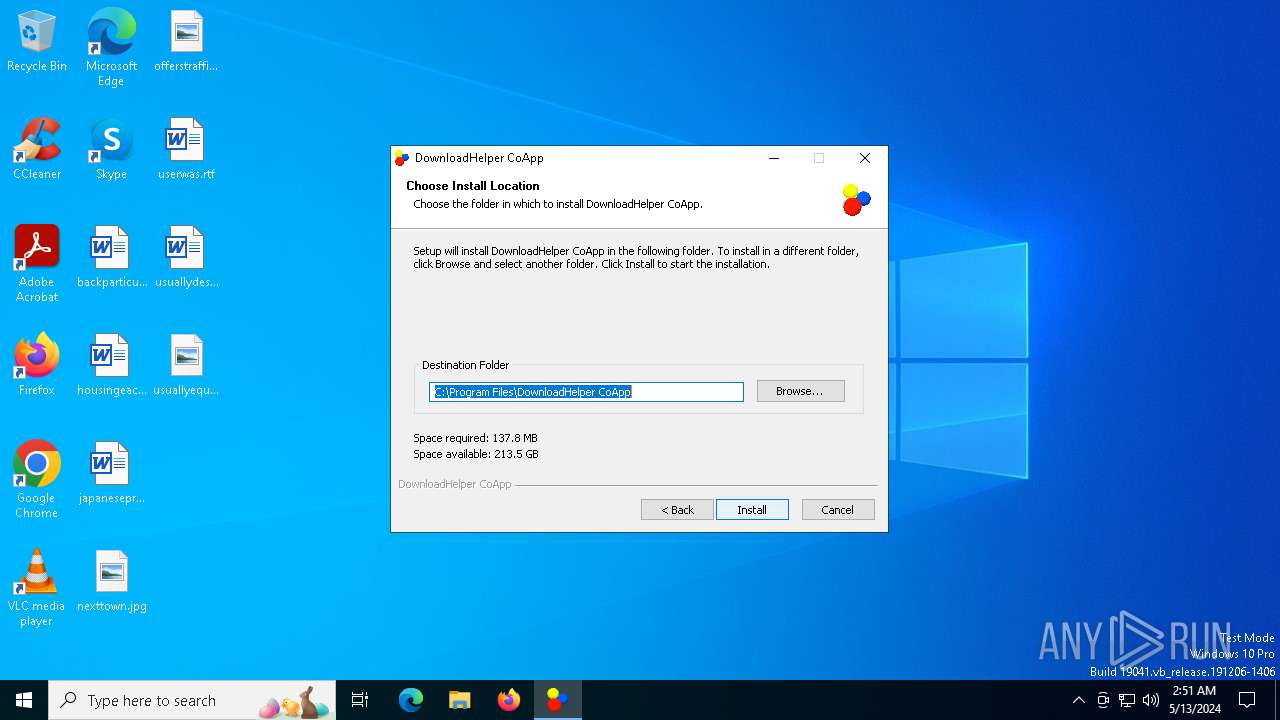
Value: C:\Program Files\DownloadHelper CoApp\uninstall.exe | |||
| (PID) Process: | (4548) e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\DownloadHelper CoApp |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\DownloadHelper CoApp\vdhcoapp.exe | |||
| (PID) Process: | (4548) e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\DownloadHelper CoApp |
| Operation: | write | Name: | DisplayVersion |
Value: 2.0.19.0 | |||
| (PID) Process: | (4548) e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\DownloadHelper CoApp |
| Operation: | write | Name: | Publisher |
Value: ACLAP | |||
Executable files
4
Suspicious files
5
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Program Files\DownloadHelper CoApp\ffmpeg.exe | — | |
MD5:— | SHA256:— | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Program Files\DownloadHelper CoApp\ffprobe.exe | — | |
MD5:— | SHA256:— | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Program Files\DownloadHelper CoApp\vdhcoapp.exe | — | |
MD5:— | SHA256:— | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Users\admin\AppData\Local\Temp\nsd62FE.tmp | — | |
MD5:— | SHA256:— | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Program Files\DownloadHelper CoApp\filepicker.exe | executable | |
MD5:83A9DCB2B5807B44DFE4D83923E3A05E | SHA256:B024918E2ABCDE65D8B615E7725B7CABD95270D7EF15AD223C7FA6AC1E82EB61 | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Users\admin\AppData\Local\Temp\nsd634D.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Program Files\DownloadHelper CoApp\mozilla.json | binary | |
MD5:6A07F200538DEE80656D53F3B082C49D | SHA256:5B5454BC699F81F7A1E92A4A03AD923F4A5039C586F84A8CE70A9EC53492C23C | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Users\admin\AppData\Local\Temp\nsd634D.tmp\System.dll | executable | |
MD5:4ADD245D4BA34B04F213409BFE504C07 | SHA256:9111099EFE9D5C9B391DC132B2FAF0A3851A760D4106D5368E30AC744EB42706 | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Program Files\DownloadHelper CoApp\microsoft.json | binary | |
MD5:DBCAD9E300E06F01046FE07EB1899929 | SHA256:1EA6D59DCC53BB1234CEB5936FEE20897F497E7EFCA16CC6090C5482E7660551 | |||
| 4548 | e1af498f95432a4f2f666a8cbec7bd6ab9deb4d1695c6e7cde7acb9bd408e600.exe | C:\Program Files\DownloadHelper CoApp\google.json | binary | |
MD5:DBCAD9E300E06F01046FE07EB1899929 | SHA256:1EA6D59DCC53BB1234CEB5936FEE20897F497E7EFCA16CC6090C5482E7660551 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
50
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
636 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
636 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1412 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3044 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3044 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
3724 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
2908 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
636 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
636 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4680 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4680 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1412 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |