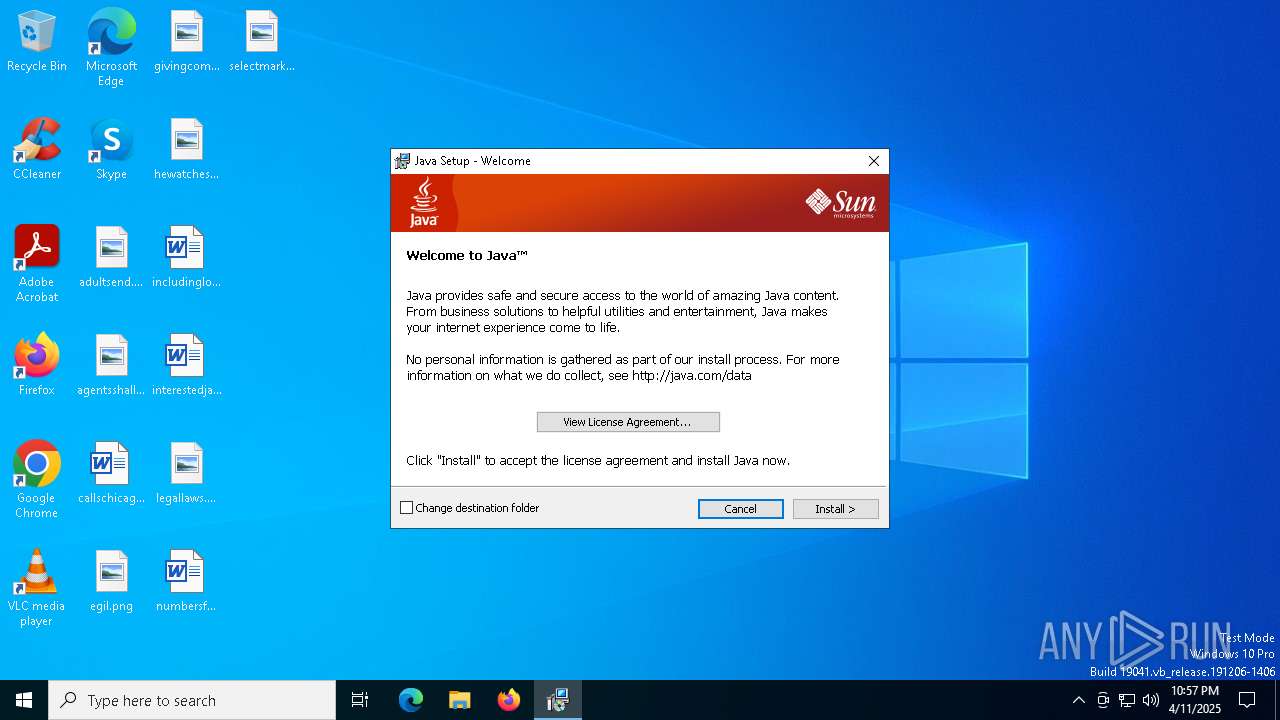
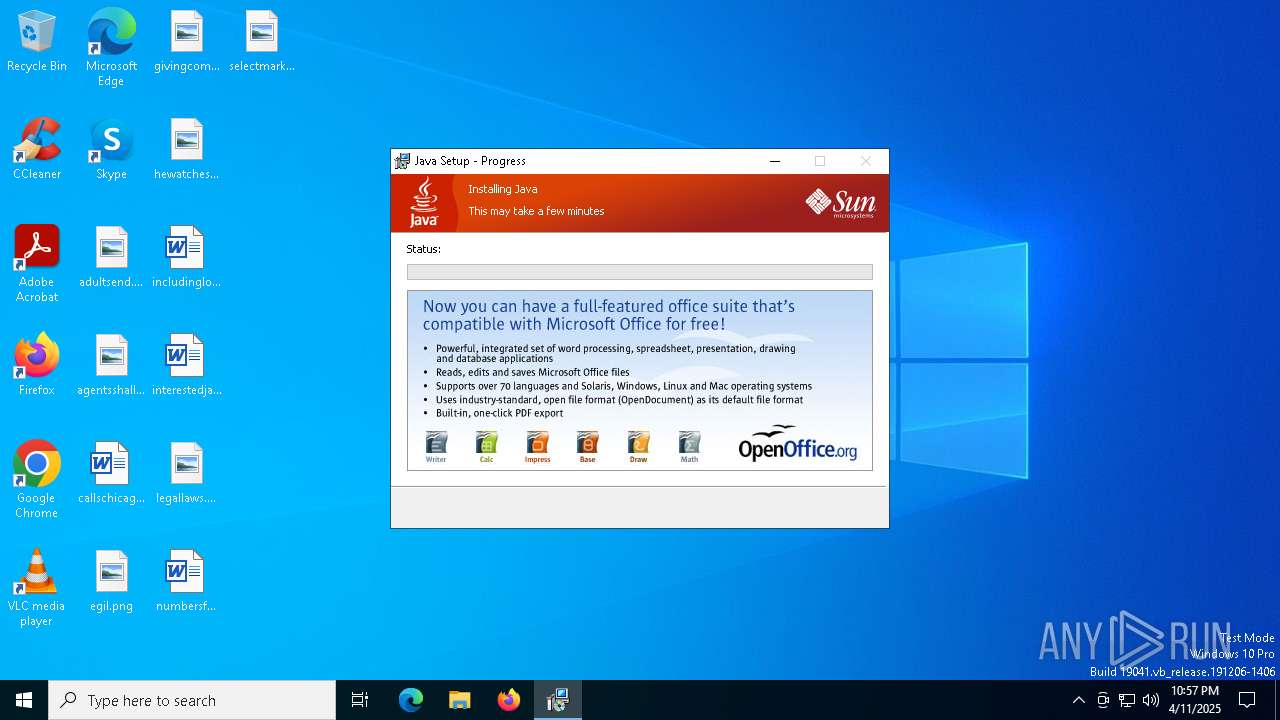
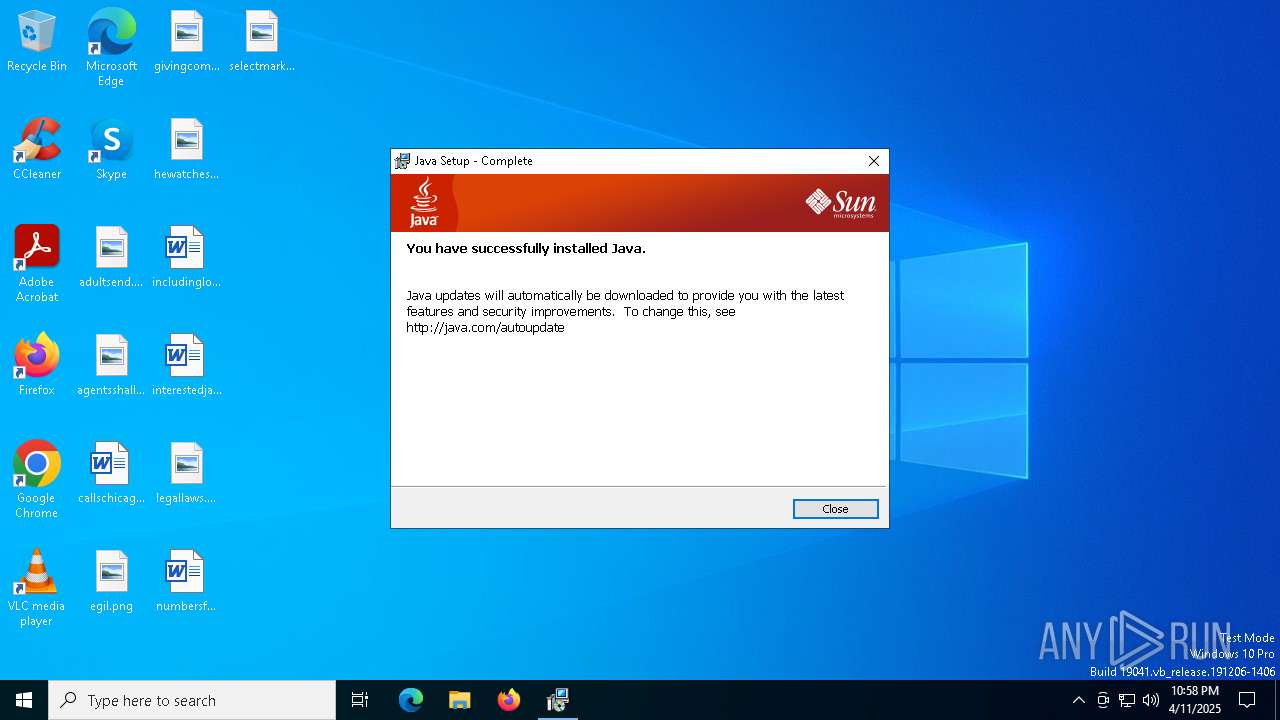
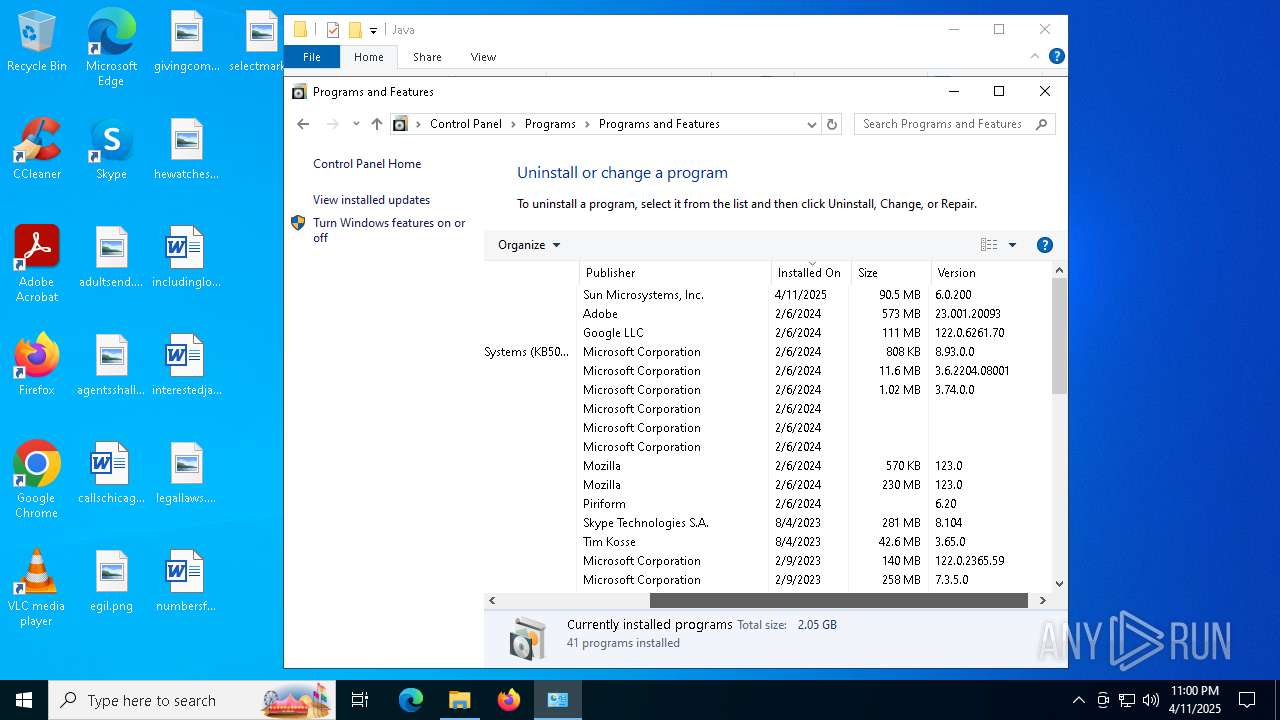
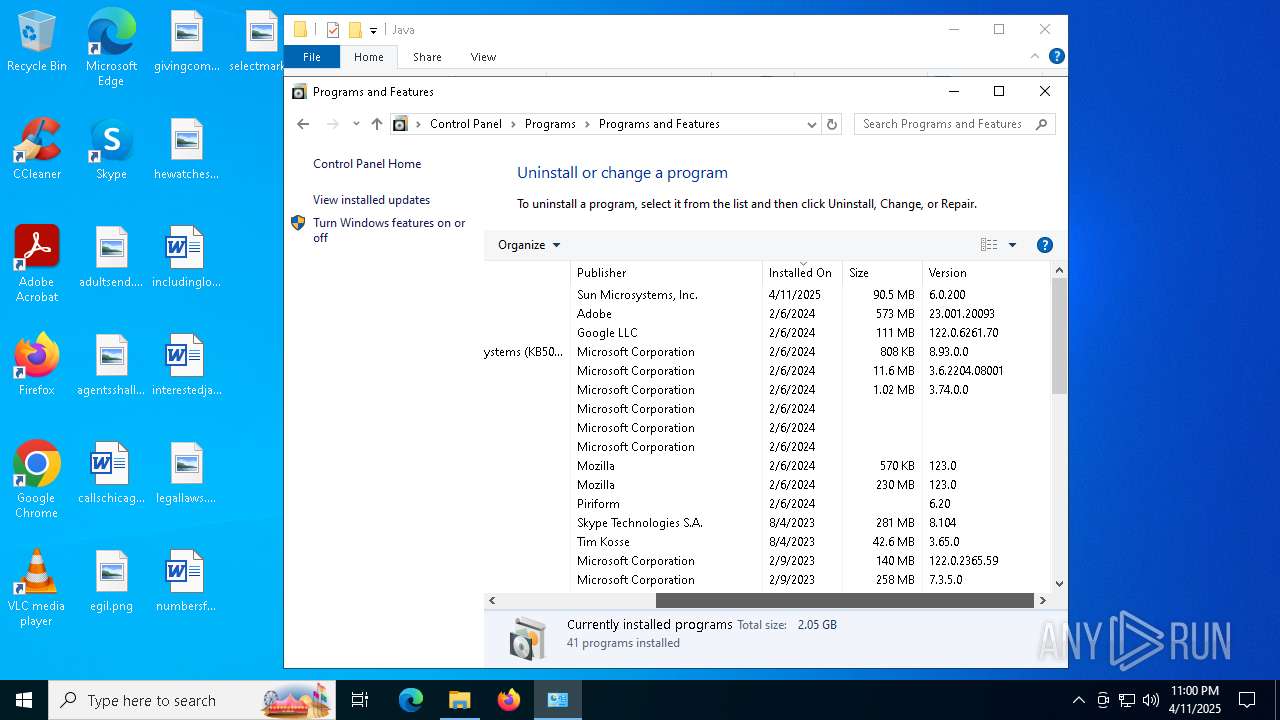
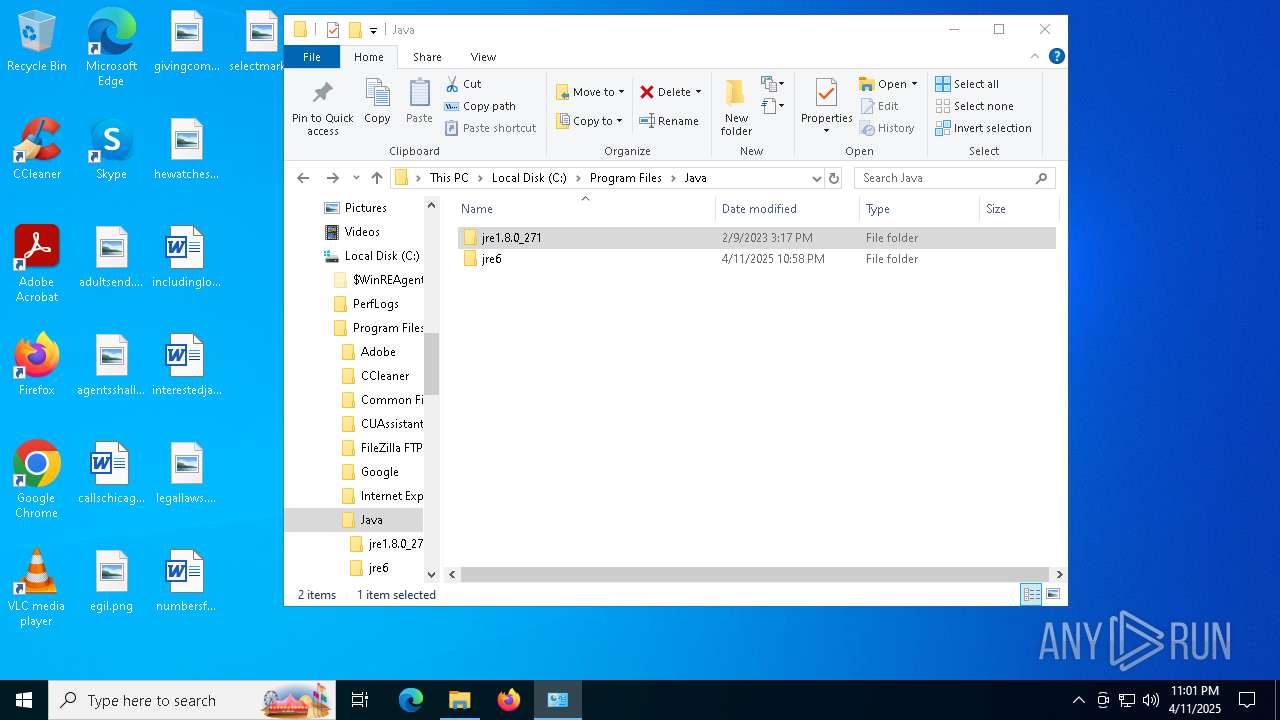
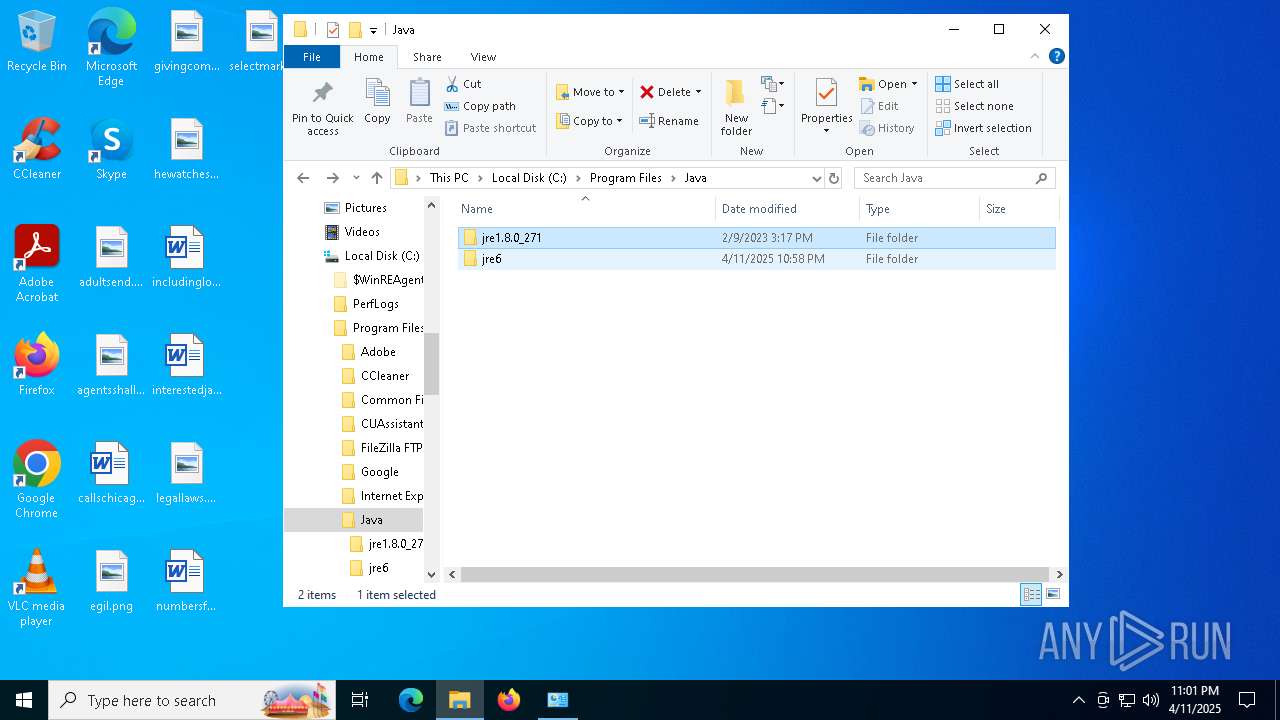
| File name: | jre-6u20-windows-x64.exe |
| Full analysis: | https://app.any.run/tasks/9b2054b6-2a63-43d0-958c-5947ad3b3e41 |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2025, 22:57:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 5 sections |
| MD5: | 343EEAD5222DA8F5BFFB298FB2683330 |
| SHA1: | 3E0C7BDD32AE22B1E3DA0D127AF06B6AD6742B46 |
| SHA256: | E191FE103FE341C2C900A6DF3D37D9C4D53A890D408F3DC8795851D37FB6E2AA |
| SSDEEP: | 98304:BbWx//8cT4GjimUc1K17zRlpnyBEvm8frkU6PMthGRlJF6JKwE7s6ySv+SyVXoz0:965r1K+5tG6dUlRqDuFbnD |
MALICIOUS
Executing a file with an untrusted certificate
- jre-6u20-windows-x64.exe (PID: 2320)
- jre-6u20-windows-x64.exe (PID: 3176)
Changes the autorun value in the registry
- msiexec.exe (PID: 672)
SUSPICIOUS
Executable content was dropped or overwritten
- jre-6u20-windows-x64.exe (PID: 3176)
- zipper.exe (PID: 928)
Checks for Java to be installed
- jre-6u20-windows-x64.exe (PID: 3176)
- msiexec.exe (PID: 2236)
- msiexec.exe (PID: 672)
- javaws.exe (PID: 4068)
- msiexec.exe (PID: 4400)
- javaw.exe (PID: 6820)
Reads security settings of Internet Explorer
- jre-6u20-windows-x64.exe (PID: 3176)
- msiexec.exe (PID: 672)
- msiexec.exe (PID: 4400)
- javaw.exe (PID: 6820)
Application launched itself
- msiexec.exe (PID: 2236)
Executes as Windows Service
- VSSVC.exe (PID: 1532)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2236)
Process drops legitimate windows executable
- zipper.exe (PID: 928)
The process drops C-runtime libraries
- zipper.exe (PID: 928)
Reads Mozilla Firefox installation path
- msiexec.exe (PID: 672)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6264)
- cmd.exe (PID: 5544)
- cmd.exe (PID: 3884)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 928)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 5036)
There is functionality for taking screenshot (YARA)
- jre-6u20-windows-x64.exe (PID: 3176)
Starts application with an unusual extension
- msiexec.exe (PID: 2600)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 6248)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 672)
Searches for installed software
- explorer.exe (PID: 6256)
INFO
The sample compiled with english language support
- jre-6u20-windows-x64.exe (PID: 3176)
- zipper.exe (PID: 928)
Checks supported languages
- jre-6u20-windows-x64.exe (PID: 3176)
- msiexec.exe (PID: 2236)
- msiexec.exe (PID: 4400)
- MSI6A7.tmp (PID: 1912)
- msiexec.exe (PID: 1132)
- zipper.exe (PID: 928)
- msiexec.exe (PID: 672)
- unpack200.exe (PID: 7000)
- unpack200.exe (PID: 7012)
- unpack200.exe (PID: 5508)
- unpack200.exe (PID: 6244)
- unpack200.exe (PID: 2332)
- unpack200.exe (PID: 6208)
- unpack200.exe (PID: 5988)
- javaw.exe (PID: 6416)
- javaw.exe (PID: 928)
- javaws.exe (PID: 4068)
- javaw.exe (PID: 4988)
- javaw.exe (PID: 6820)
Creates files or folders in the user directory
- jre-6u20-windows-x64.exe (PID: 3176)
- javaw.exe (PID: 928)
- msiexec.exe (PID: 4400)
- javaw.exe (PID: 6820)
Reads the computer name
- jre-6u20-windows-x64.exe (PID: 3176)
- msiexec.exe (PID: 2236)
- msiexec.exe (PID: 4400)
- msiexec.exe (PID: 1132)
- msiexec.exe (PID: 672)
- javaw.exe (PID: 928)
- javaw.exe (PID: 6820)
Checks proxy server information
- jre-6u20-windows-x64.exe (PID: 3176)
- msiexec.exe (PID: 4400)
- slui.exe (PID: 3020)
- javaw.exe (PID: 6820)
Create files in a temporary directory
- jre-6u20-windows-x64.exe (PID: 3176)
- msiexec.exe (PID: 672)
- javaw.exe (PID: 4988)
- javaw.exe (PID: 928)
- javaw.exe (PID: 6820)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2600)
- msiexec.exe (PID: 2236)
- msiexec.exe (PID: 672)
Manages system restore points
- SrTasks.exe (PID: 6828)
Creates files in the program directory
- zipper.exe (PID: 928)
- unpack200.exe (PID: 7000)
- unpack200.exe (PID: 5988)
- unpack200.exe (PID: 5508)
- unpack200.exe (PID: 7012)
- unpack200.exe (PID: 6244)
- unpack200.exe (PID: 2332)
- unpack200.exe (PID: 6208)
- javaw.exe (PID: 928)
- javaw.exe (PID: 6820)
Creates a software uninstall entry
- msiexec.exe (PID: 2236)
Reads the machine GUID from the registry
- javaw.exe (PID: 928)
- msiexec.exe (PID: 4400)
- javaw.exe (PID: 6820)
- jre-6u20-windows-x64.exe (PID: 3176)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4272)
- WMIC.exe (PID: 5036)
- WMIC.exe (PID: 976)
- WMIC.exe (PID: 6988)
- WMIC.exe (PID: 2416)
- explorer.exe (PID: 6256)
Reads the software policy settings
- msiexec.exe (PID: 4400)
- jre-6u20-windows-x64.exe (PID: 3176)
- javaw.exe (PID: 6820)
- slui.exe (PID: 3020)
Reads the time zone
- javaw.exe (PID: 928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (49) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.4) |
| .scr | | | Windows screen saver (14.9) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2010:04:12 23:48:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 8 |
| CodeSize: | 74752 |
| InitializedDataSize: | 16349696 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8b40 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.200.2 |
| ProductVersionNumber: | 6.0.200.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sun Microsystems, Inc. |
| FileDescription: | Java(TM) Platform SE binary |
| FileVersion: | 6.0.200.2 |
| FullVersion: | 1.6.0_20-b02 |
| InternalName: | Setup Launcher |
| LegalCopyright: | Copyright © 2004 |
| OriginalFileName: | jinstall.exe |
| ProductName: | Java(TM) Platform SE 6 U20 |
| ProductVersion: | 6.0.200.2 |
Total processes
185
Monitored processes
45
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | C:\Windows\System32\MsiExec.exe -Embedding 6CF16C6C96432977D574F12B3E45E176 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | "C:\Program Files\Java\jre6\zipper.exe" "C:\Program Files\Java\jre6\core.zip" "C:\Program Files\Java\jre6\" "C:\Users\admin\AppData\Local\Temp\java_install.log" | C:\Program Files\Java\jre6\zipper.exe | msiexec.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Java\jre6\bin\javaw.exe" com.sun.servicetag.Installer -source "Windows JRE installer" | C:\Program Files\Java\jre6\bin\javaw.exe | — | msiexec.exe | |||||||||||
User: admin Company: Sun Microsystems, Inc. Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 6.0.200.2 Modules
| |||||||||||||||
| 976 | WMIC computersystem get manufacturer | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\Windows\System32\MsiExec.exe -Embedding 75DF7D30A2F5557768828A51E0972B89 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | "C:\Users\admin\AppData\Local\Temp\MSI6A7.tmp" C:\Program Files\Java\jre6\;C | C:\Users\admin\AppData\Local\Temp\MSI6A7.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Sun Microsystems, Inc. Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 6.0.200.2 Modules
| |||||||||||||||
| 2084 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
41 963
Read events
29 159
Write events
6 576
Delete events
6 228
Modification events
| (PID) Process: | (3176) jre-6u20-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft |
| Operation: | delete value | Name: | InstallStatus |
Value: | |||
| (PID) Process: | (3176) jre-6u20-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3176) jre-6u20-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3176) jre-6u20-windows-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3176) jre-6u20-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Country |
Value: NL | |||
| (PID) Process: | (3176) jre-6u20-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | PostStatusUrl |
Value: https://sjremetrics.java.com/b/ss//6 | |||
| (PID) Process: | (3176) jre-6u20-windows-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Update\Policy |
| Operation: | write | Name: | Method |
Value: joff | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000CE23871D35ABDB01BC08000024190000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000CD9B3F1D35ABDB01BC08000024190000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000CD9B3F1D35ABDB01BC08000024190000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
105
Suspicious files
501
Text files
85
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3176 | jre-6u20-windows-x64.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\jre1.6.0_20_x64\Data1.cab | — | |
MD5:— | SHA256:— | |||
| 2236 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3176 | jre-6u20-windows-x64.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:5B5439FA8AD6E68BEFE8799B808E5952 | SHA256:9BDB98D9D3216FA4F6CCDD56805934392BB3B5119A03C886615EE7E8CCF7F22A | |||
| 3176 | jre-6u20-windows-x64.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\jre1.6.0_20_x64\jre1.6.0_20.msi | binary | |
MD5:B8100C23F7AF17BACBE811BE5B00D4CF | SHA256:B69FC19D586AC489E33309D80898955E2937B707BCA1E702087F5FAADBC22EBA | |||
| 2600 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI657.tmp | executable | |
MD5:154113531946747CD8B5341723772D39 | SHA256:BBBE2154737E7221FA1DC49A191D6DF74D3A737138B4941098FF0D346A60477E | |||
| 2600 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6A6.tmp | executable | |
MD5:154113531946747CD8B5341723772D39 | SHA256:BBBE2154737E7221FA1DC49A191D6DF74D3A737138B4941098FF0D346A60477E | |||
| 2600 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6E8.tmp | executable | |
MD5:154113531946747CD8B5341723772D39 | SHA256:BBBE2154737E7221FA1DC49A191D6DF74D3A737138B4941098FF0D346A60477E | |||
| 2236 | msiexec.exe | C:\Windows\Installer\114d42.msi | binary | |
MD5:B8100C23F7AF17BACBE811BE5B00D4CF | SHA256:B69FC19D586AC489E33309D80898955E2937B707BCA1E702087F5FAADBC22EBA | |||
| 2236 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:256443244037697A25FA45BD742C5D5A | SHA256:82D863BEAD511B2AC3AB0CA3B2992DAF9F3403DFA4F580D578A2D1A23523952C | |||
| 2236 | msiexec.exe | C:\Program Files\Java\jre6\core.zip | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
62
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3176 | jre-6u20-windows-x64.exe | GET | 200 | 2.18.121.5:80 | http://javadl-esd.sun.com/update/1.6.0/1.6.0_20-b02.xml | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.18.121.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3176 | jre-6u20-windows-x64.exe | HEAD | 200 | 2.18.121.81:80 | http://rps-svcs.sun.com/services/countrylookup | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
616 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4400 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4400 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAqs9WlmXhCsgGqdmiVHUBE%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.18.121.139:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3176 | jre-6u20-windows-x64.exe | 2.18.121.5:80 | javadl-esd.sun.com | AKAMAI-AS | FR | whitelisted |
3176 | jre-6u20-windows-x64.exe | 2.18.121.81:80 | rps-svcs.sun.com | AKAMAI-AS | FR | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
javadl-esd.sun.com |
| whitelisted |
rps-svcs.sun.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |