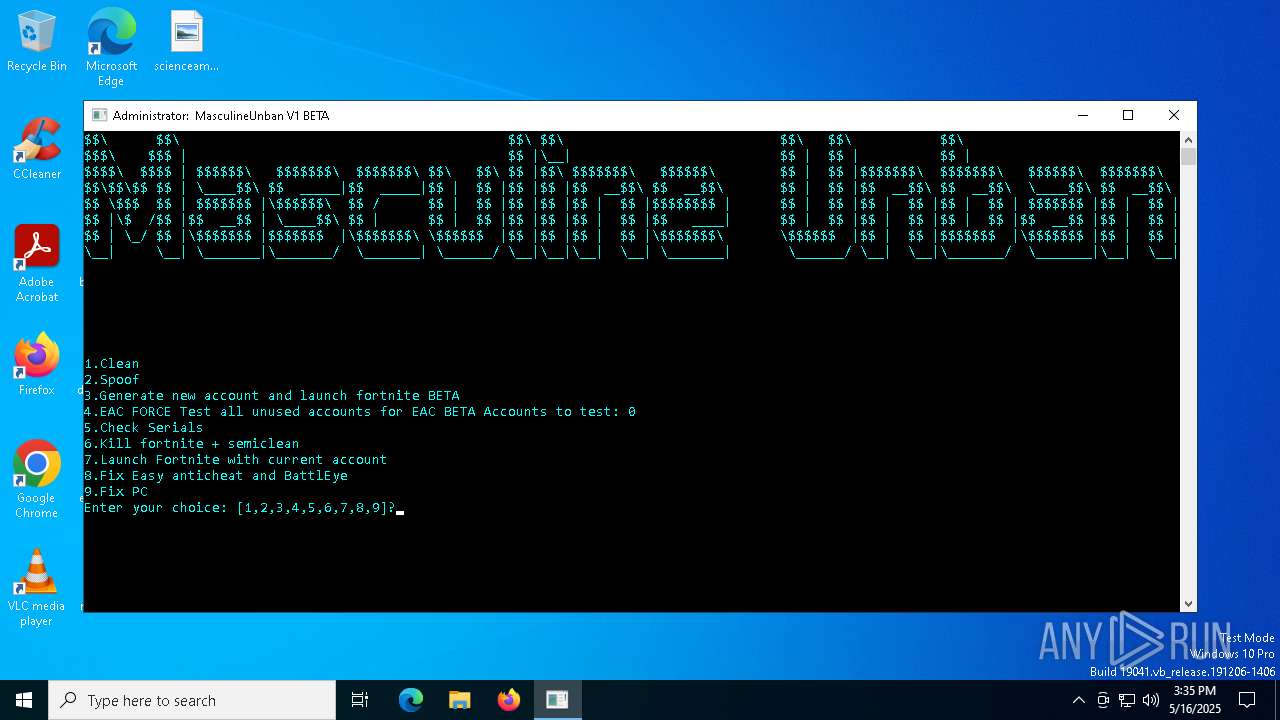
| File name: | MasculineUnban_EARLY_BETA.exe |
| Full analysis: | https://app.any.run/tasks/b90d8a13-478b-4391-9479-c88badcdab26 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 15:35:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | ACAFC89FE5F6EFE9701AE037A7FF3690 |
| SHA1: | 7AC0C75C25129FCDA88AB4F3D3C8EB5BEB38D45F |
| SHA256: | E18FF240D3D8A5773515E6E61FA119D909530FD232DAD719A479CC44842BD1A4 |
| SSDEEP: | 98304:v0RzFU1J9HrOcFbOuSeORxedrjRFHOXonqpWvWc2QDtBH0a+U+WhNWg+hwyJQ0li:FCmDVzPNyS |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 4696)
- cmd.exe (PID: 864)
Vulnerable driver has been detected
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
SUSPICIOUS
Executable content was dropped or overwritten
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
The executable file from the user directory is run by the CMD process
- reset2-Hardware Rescan after Adapter reset.exe (PID: 4696)
- extd.exe (PID: 6728)
- extd.exe (PID: 6040)
- extd.exe (PID: 7148)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5304)
Drops a system driver (possible attempt to evade defenses)
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
The process creates files with name similar to system file names
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
Process drops legitimate windows executable
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5304)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 4696)
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
Application launched itself
- cmd.exe (PID: 5304)
Executing commands from a ".bat" file
- reset2-Hardware Rescan after Adapter reset.exe (PID: 4696)
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5304)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1812)
- cmd.exe (PID: 1164)
Manipulates environment variables
- powershell.exe (PID: 6132)
INFO
Checks supported languages
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
- extd.exe (PID: 7148)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 4696)
- devcon.exe (PID: 4608)
- extd.exe (PID: 6040)
- extd.exe (PID: 6728)
Creates files or folders in the user directory
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
The sample compiled with english language support
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
Create files in a temporary directory
- MasculineUnban_EARLY_BETA.exe (PID: 6480)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 4696)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 92672 |
| InitializedDataSize: | 6263296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
153
Monitored processes
25
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\WINDOWS\sysnative\cmd" /c "C:\Users\admin\AppData\Local\Temp\C1FA.tmp\C1FB.tmp\C1FC.bat "C:\Users\admin\AppData\Roaming\reset2-Hardware Rescan after Adapter reset.exe"" | C:\Windows\System32\cmd.exe | — | reset2-Hardware Rescan after Adapter reset.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\Temp\MasculineUnban_EARLY_BETA.exe" | C:\Users\admin\AppData\Local\Temp\MasculineUnban_EARLY_BETA.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | MasculineUnban_EARLY_BETA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | C:\WINDOWS\system32\cmd.exe /c powershell $env:firmware_type | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo." | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | C:\WINDOWS\system32\cmd.exe /c powershell Confirm-SecureBootUEFI | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reset2-Hardware Rescan after Adapter reset.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | powershell Confirm-SecureBootUEFI | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | findstr /C:"True" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 302
Read events
9 301
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6712) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Power |
| Operation: | write | Name: | HiberbootEnabled |
Value: 0 | |||
Executable files
16
Suspicious files
1
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Local\Temp\BCBA.tmp\BCBB.tmp\BCBC.bat | text | |
MD5:1FF9320EF924E1E92D09F88E35E949DC | SHA256:4E5A6C2219E513FD707259C63B50B0A469EFF2E211951F5536B54CA715C17F9E | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\1-RUNFIRST.exe | executable | |
MD5:6FBE881F1D6480E2E15D3EBE0F493D2D | SHA256:49B84540D5B4B8D2344C25EDB042E216592DD1DC78A5C00F2AD9457442C4581C | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\AMIDEWINx64.EXE | executable | |
MD5:F17ECF761E70FEB98C7F628857EEDFE7 | SHA256:311F5C844746D4270B5B971CCEF8D74DDEDCA873EB45F34A1A55F1EA4A3BAFCF | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\ddc.exe | executable | |
MD5:97B963FD85FF4CC2A3B0DA8164593CFC | SHA256:AF219747072341760396D686F2FE7350EC2DCE713F1EC1977C21F8BE7B9197D5 | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\AppleCleaner.exe | executable | |
MD5:DA2176757B2FEAD6539243B42057CB3C | SHA256:1A62ED192FF4A7BD746FA24C8D7CD96578A4C7E9F0D4A6651A2A3D0BAFF9C433 | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\Cleaner8.exe | executable | |
MD5:3546548BE0B0940C52EC881D48404818 | SHA256:DEC2A16531A09D05F1AE64A21C35D53CEC5998BE22C16A88B2E8B4A36878DB9A | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\dd.dll | executable | |
MD5:CBE4163CAAB5AE09FA1E03B87B491380 | SHA256:E982CB681DD366D5F83FA3C17C2E1929611479507C9247D063E47ACE0C971ACA | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\e.bat | text | |
MD5:C457CC5B041B15C50C57A2C6244DE7CF | SHA256:B665E651CC2D02AE376A69EF648300D1C26863D30876C9CBA7EE387CDBB1561A | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\AMIFLDRV64.SYS | executable | |
MD5:F22740BA54A400FD2BE7690BB204AA08 | SHA256:65C26276CADDA7A36F8977D1D01120EDB5C3418BE2317D501761092D5F9916C9 | |||
| 6480 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\devcon.exe | executable | |
MD5:D153A0BC6F0476457B56FC38795DEA01 | SHA256:DF048DF347A738B6ADDEC6F3FD65C73E371D0E11E2DC02F88F8EF307B964E1B7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5376 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5376 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |