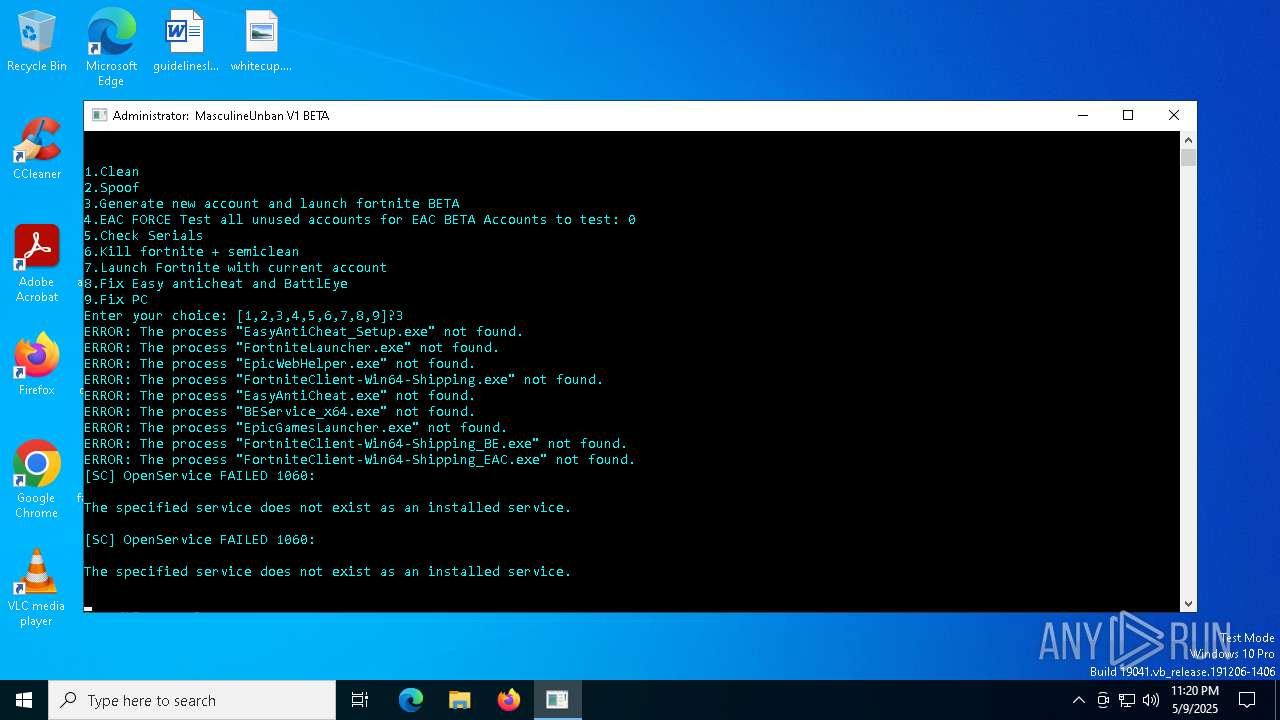
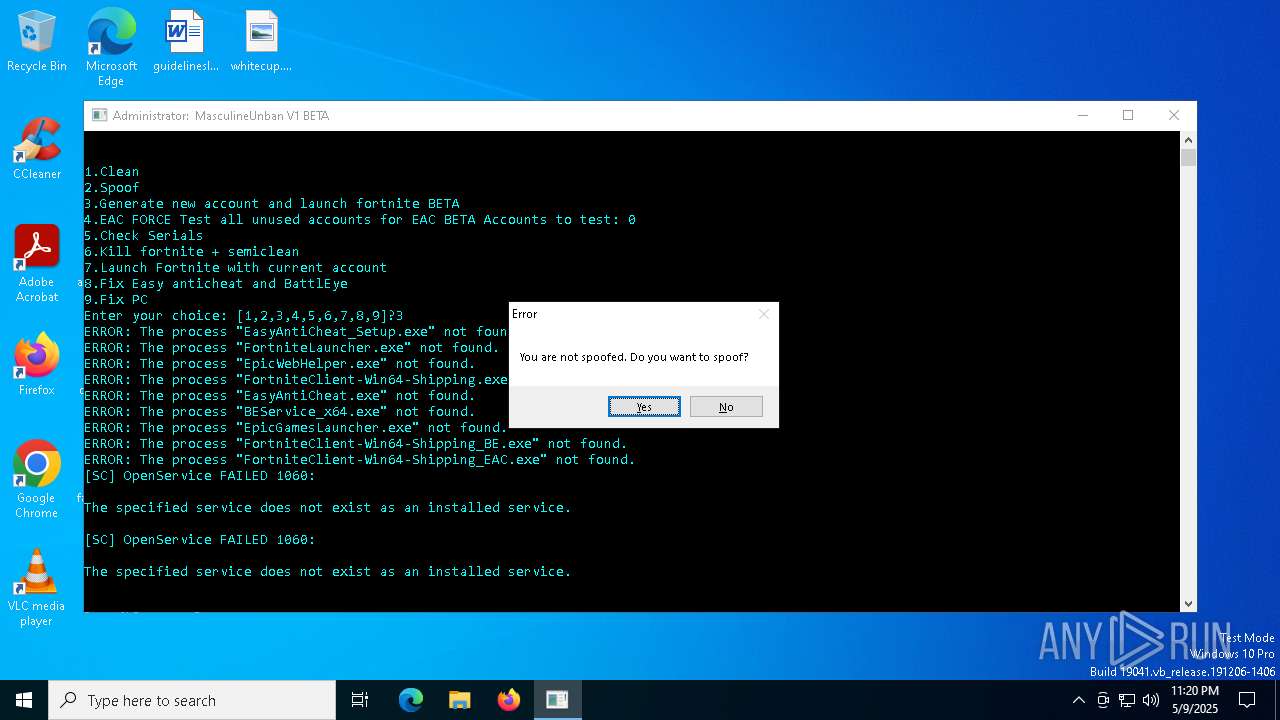
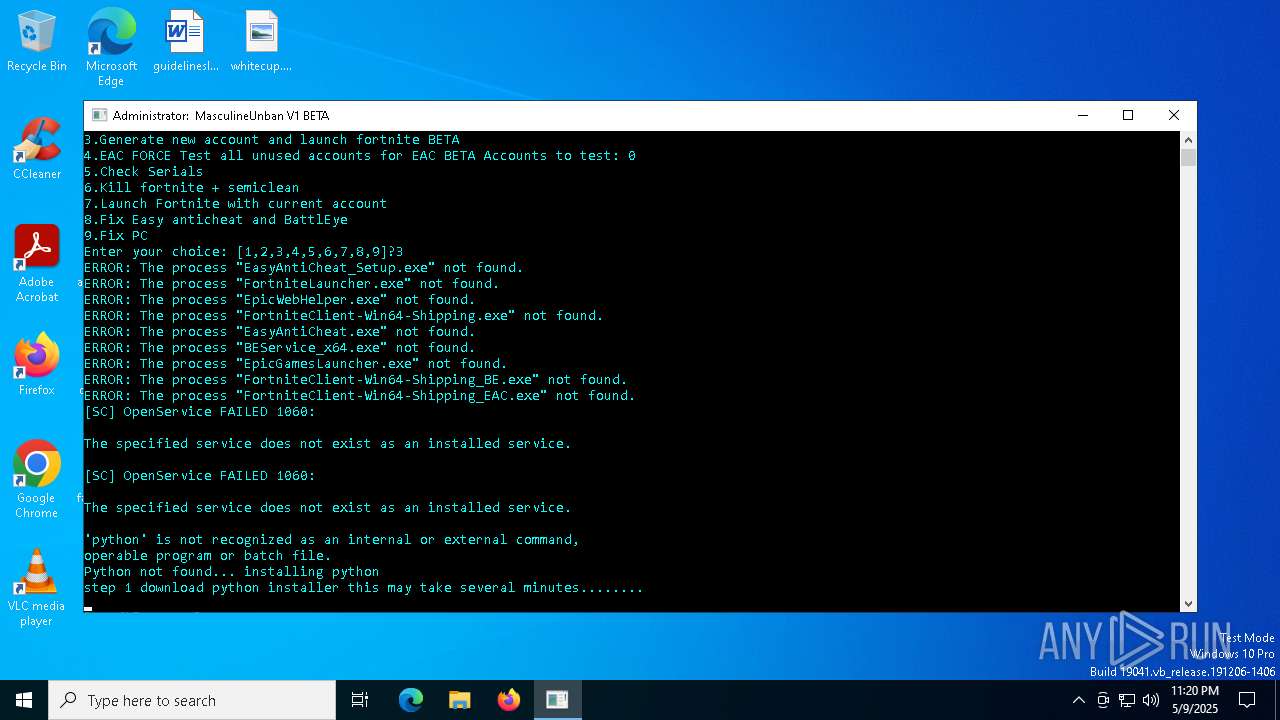
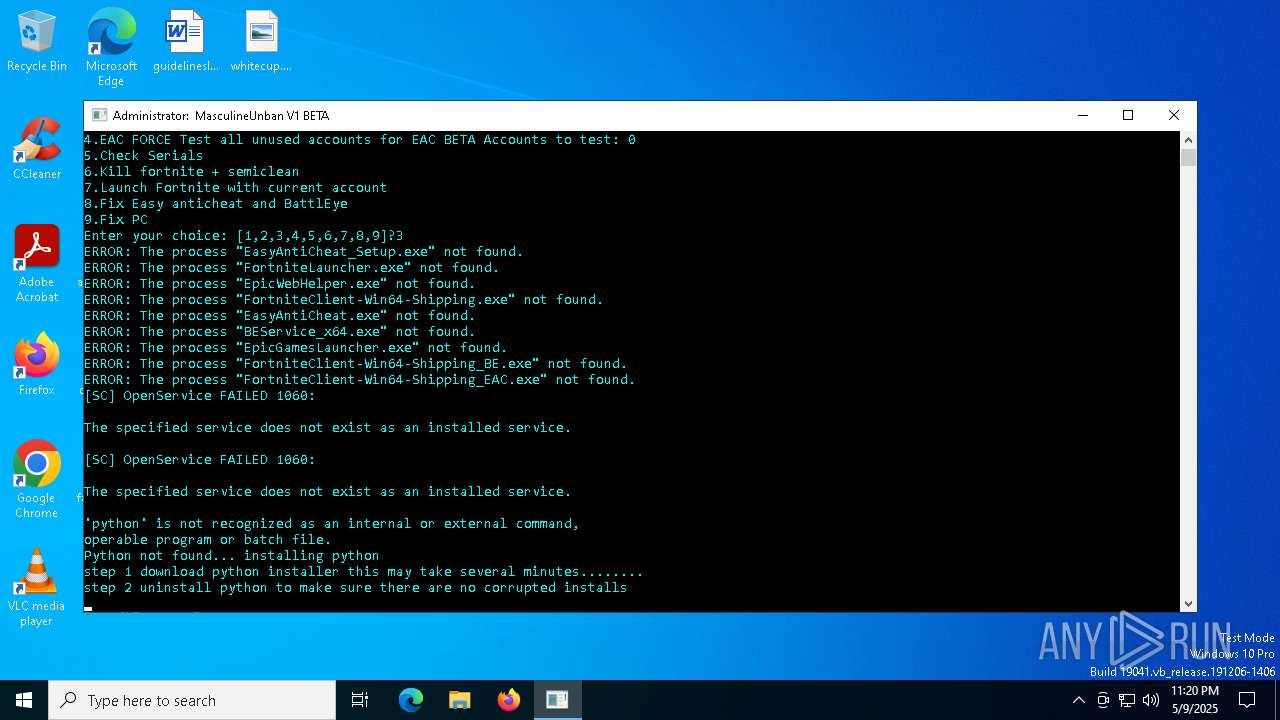
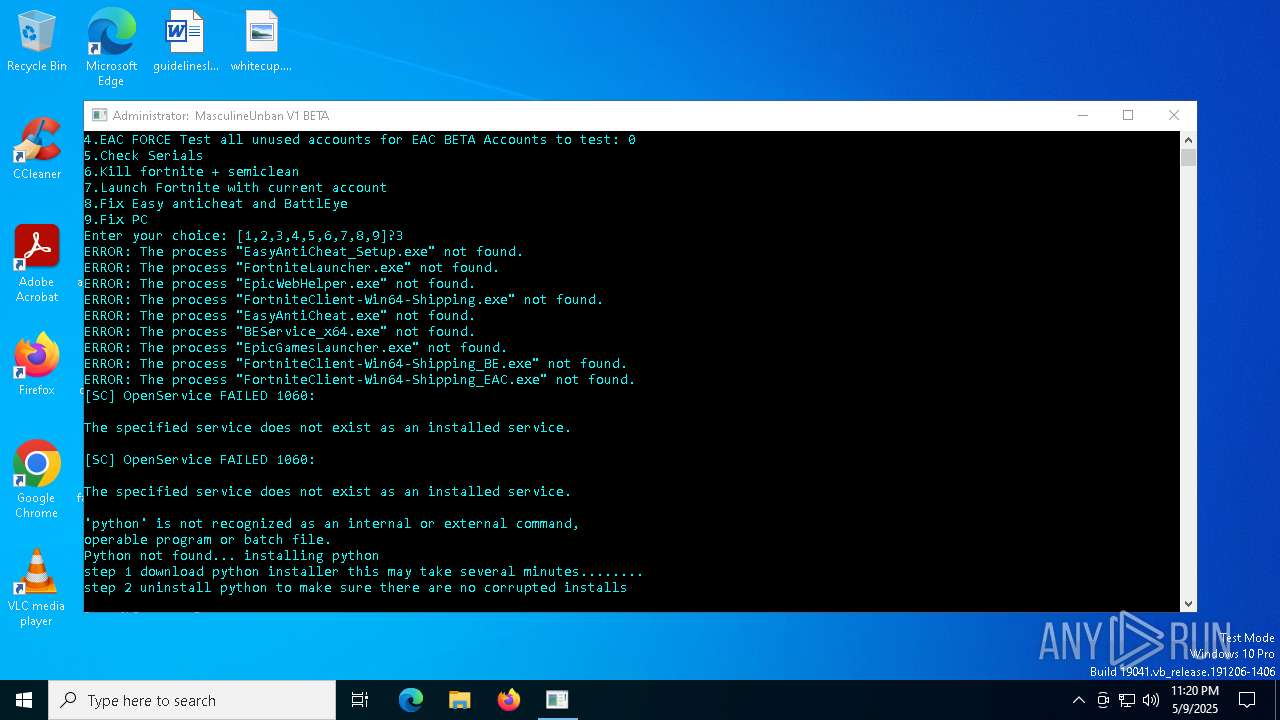
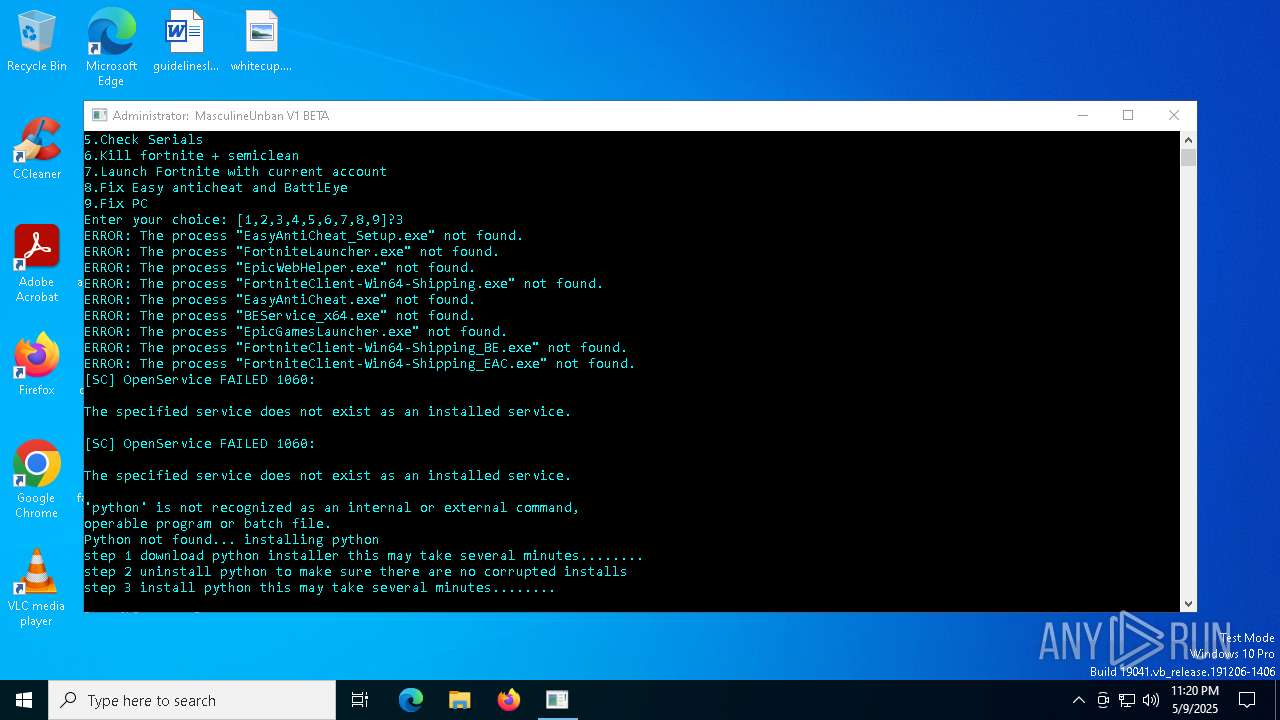
| File name: | MasculineUnban_EARLY_BETA.exe |
| Full analysis: | https://app.any.run/tasks/61fbde5b-9df4-4e10-96da-92286b74878b |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 23:19:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | ACAFC89FE5F6EFE9701AE037A7FF3690 |
| SHA1: | 7AC0C75C25129FCDA88AB4F3D3C8EB5BEB38D45F |
| SHA256: | E18FF240D3D8A5773515E6E61FA119D909530FD232DAD719A479CC44842BD1A4 |
| SSDEEP: | 98304:v0RzFU1J9HrOcFbOuSeORxedrjRFHOXonqpWvWc2QDtBH0a+U+WhNWg+hwyJQ0li:FCmDVzPNyS |
MALICIOUS
Vulnerable driver has been detected
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 7772)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 7624)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 5544)
Changes the autorun value in the registry
- pythin.exe (PID: 7264)
SUSPICIOUS
Process drops legitimate windows executable
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
- pythin.exe (PID: 7932)
- python-3.10.5-amd64.exe (PID: 7756)
- msiexec.exe (PID: 5596)
The process creates files with name similar to system file names
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
Executable content was dropped or overwritten
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
- powershell.exe (PID: 5544)
- pythin.exe (PID: 7264)
- pythin.exe (PID: 7784)
- pythin.exe (PID: 2852)
- pythin.exe (PID: 7932)
- python-3.10.5-amd64.exe (PID: 7756)
Drops a system driver (possible attempt to evade defenses)
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
Starts CMD.EXE for commands execution
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 7624)
- cmd.exe (PID: 7528)
Executing commands from a ".bat" file
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 7624)
The executable file from the user directory is run by the CMD process
- extd.exe (PID: 7548)
- extd.exe (PID: 7576)
- extd.exe (PID: 7600)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 7624)
- extd.exe (PID: 7684)
- pythin.exe (PID: 7784)
- pythin.exe (PID: 2852)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7748)
- cmd.exe (PID: 7528)
- cmd.exe (PID: 6032)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7528)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7528)
Stops a currently running service
- sc.exe (PID: 7724)
- sc.exe (PID: 7820)
Starts SC.EXE for service management
- cmd.exe (PID: 7528)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 7528)
Probably download files using WebClient
- cmd.exe (PID: 7528)
Application launched itself
- cmd.exe (PID: 7528)
Manipulates environment variables
- powershell.exe (PID: 4448)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7528)
Searches for installed software
- pythin.exe (PID: 7264)
- pythin.exe (PID: 7932)
- dllhost.exe (PID: 5200)
Creates a software uninstall entry
- pythin.exe (PID: 7264)
There is functionality for taking screenshot (YARA)
- pythin.exe (PID: 7264)
The process drops C-runtime libraries
- pythin.exe (PID: 7932)
- msiexec.exe (PID: 5596)
- python-3.10.5-amd64.exe (PID: 7756)
Reads security settings of Internet Explorer
- pythin.exe (PID: 7932)
Starts itself from another location
- pythin.exe (PID: 7932)
Executes as Windows Service
- VSSVC.exe (PID: 6392)
Process drops python dynamic module
- msiexec.exe (PID: 5596)
INFO
Checks supported languages
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
- extd.exe (PID: 7548)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 7624)
- devcon.exe (PID: 7804)
- extd.exe (PID: 7576)
- extd.exe (PID: 7600)
- extd.exe (PID: 7684)
- pythin.exe (PID: 2852)
- pythin.exe (PID: 7264)
- pythin.exe (PID: 7784)
- pythin.exe (PID: 7932)
- python-3.10.5-amd64.exe (PID: 7756)
Create files in a temporary directory
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 7624)
- pythin.exe (PID: 7264)
- pythin.exe (PID: 7932)
Creates files or folders in the user directory
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
The sample compiled with english language support
- MasculineUnban_EARLY_BETA.exe (PID: 7452)
- powershell.exe (PID: 5544)
- pythin.exe (PID: 2852)
- pythin.exe (PID: 7264)
- pythin.exe (PID: 7932)
- python-3.10.5-amd64.exe (PID: 7756)
- pythin.exe (PID: 7784)
- msiexec.exe (PID: 5596)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7764)
Reads the computer name
- extd.exe (PID: 7684)
- pythin.exe (PID: 7264)
- python-3.10.5-amd64.exe (PID: 7756)
- pythin.exe (PID: 7932)
Disables trace logs
- powershell.exe (PID: 5544)
Checks proxy server information
- powershell.exe (PID: 5544)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7800)
Process checks computer location settings
- pythin.exe (PID: 7932)
Manages system restore points
- SrTasks.exe (PID: 856)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 92672 |
| InitializedDataSize: | 6263296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
189
Monitored processes
53
Malicious processes
6
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
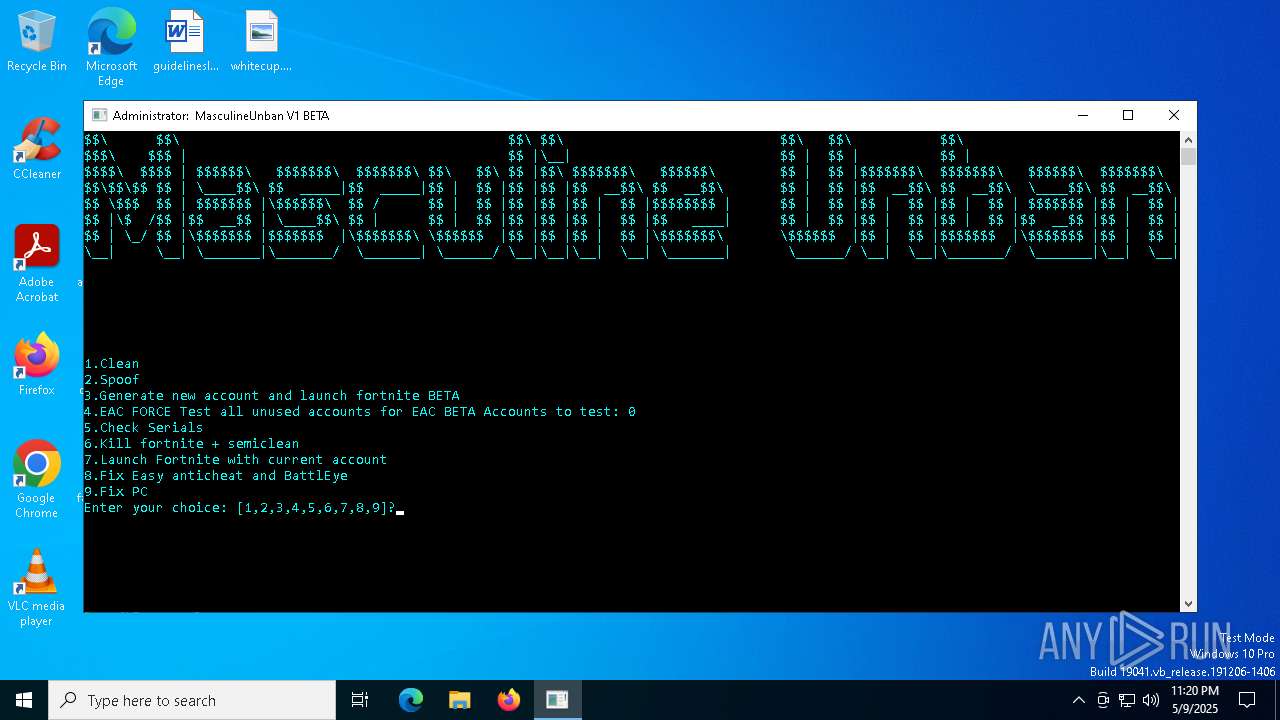
| 1020 | CHOICE /C 123456789 /M "Enter your choice:" | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | taskkill /f /im EasyAntiCheat_Setup.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2852 | pythin.exe /uninstall | C:\Users\admin\AppData\Roaming\pythin.exe | cmd.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python 3.10.5 (64-bit) Exit code: 0 Version: 3.10.5150.0 Modules
| |||||||||||||||
| 4448 | powershell $env:firmware_type | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4560 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo.UEFI" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | findstr /C:"Python 3.10" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | findstr /C:"Legacy" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5200 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
32 408
Read events
29 372
Write events
2 978
Delete events
58
Modification events
| (PID) Process: | (7648) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Power |
| Operation: | write | Name: | HiberbootEnabled |
Value: 0 | |||
| (PID) Process: | (7264) pythin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{e15803b8-d809-47f3-8818-73f0d155cf58} |
| Operation: | write | Name: | Resume |
Value: 1 | |||
| (PID) Process: | (7264) pythin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | {e15803b8-d809-47f3-8818-73f0d155cf58} |
Value: "C:\Users\admin\AppData\Local\Package Cache\{e15803b8-d809-47f3-8818-73f0d155cf58}\python-3.10.5-amd64.exe" /burn.runonce | |||
| (PID) Process: | (7264) pythin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{e15803b8-d809-47f3-8818-73f0d155cf58} |
| Operation: | write | Name: | BundleResumeCommandLine |
Value: /uninstall /burn.log.append "C:\Users\admin\AppData\Local\Temp\Python 3.10.5 (64-bit)_20250509232031.log" | |||
| (PID) Process: | (7264) pythin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{e15803b8-d809-47f3-8818-73f0d155cf58} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7264) pythin.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | {e15803b8-d809-47f3-8818-73f0d155cf58} |
Value: "C:\Users\admin\AppData\Local\Package Cache\{e15803b8-d809-47f3-8818-73f0d155cf58}\python-3.10.5-amd64.exe" /burn.runonce | |||
| (PID) Process: | (7756) python-3.10.5-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000097646E0039C1DB014C1E0000541E0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5200) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000D39CB90039C1DB015014000004180000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5200) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000003BC4B90039C1DB015014000004180000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5200) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000009C036F0039C1DB015014000004180000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
94
Suspicious files
156
Text files
1 706
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Local\Temp\B344.tmp\B345.tmp\B346.bat | text | |
MD5:E98BD549CD2795AE7D7B4533A3C5BC78 | SHA256:67E4D9DB30B2AC0502D11EDAB4BACD13138B1BFDC4F768114DDA44DCB3AE6AD4 | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\ddc.exe | executable | |
MD5:97B963FD85FF4CC2A3B0DA8164593CFC | SHA256:AF219747072341760396D686F2FE7350EC2DCE713F1EC1977C21F8BE7B9197D5 | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\cleanerOLD1.exe | executable | |
MD5:59A7CE7A4D30E28E6BC356263693EB98 | SHA256:390257A0360C025E42F0DB4C4826C3EA192E99A68C7AFCC548A8956F828F6379 | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\dd.dll | executable | |
MD5:CBE4163CAAB5AE09FA1E03B87B491380 | SHA256:E982CB681DD366D5F83FA3C17C2E1929611479507C9247D063E47ACE0C971ACA | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\1-cleaner.bat | text | |
MD5:94380E226AFD2EF08D4847986EFFA082 | SHA256:F5C0FE7711A2AF390FEB6D8CEE4E2C7D52FEFB5047DE05EF905AF887698CDD1D | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\AppleCleaner.exe | executable | |
MD5:DA2176757B2FEAD6539243B42057CB3C | SHA256:1A62ED192FF4A7BD746FA24C8D7CD96578A4C7E9F0D4A6651A2A3D0BAFF9C433 | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\1-spoofer.bat | text | |
MD5:6BAAF74862BD68849ADC91B8160E5DF3 | SHA256:AD5A2EF7ED4ED98186AE7E6F32FD58D5E7321989A6427D73002A474ED9968DA6 | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\AMIDEWINx64.EXE | executable | |
MD5:F17ECF761E70FEB98C7F628857EEDFE7 | SHA256:311F5C844746D4270B5B971CCEF8D74DDEDCA873EB45F34A1A55F1EA4A3BAFCF | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\1-RUNFIRST.exe | executable | |
MD5:6FBE881F1D6480E2E15D3EBE0F493D2D | SHA256:49B84540D5B4B8D2344C25EDB042E216592DD1DC78A5C00F2AD9457442C4581C | |||
| 7452 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Local\Temp\B344.tmp\B345.tmp\extd.exe | executable | |
MD5:C14CE13AB09B4829F67A879D735A10A1 | SHA256:EF2699BA677FCDB8A3B70A711A59A5892D8439E108E3AC4D27A7F946C4D01A4A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7184 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7184 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5596 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
5596 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAcfFBuLMA0l8xTrIwzQ0d0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5544 | powershell.exe | 151.101.192.223:443 | www.python.org | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.python.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |