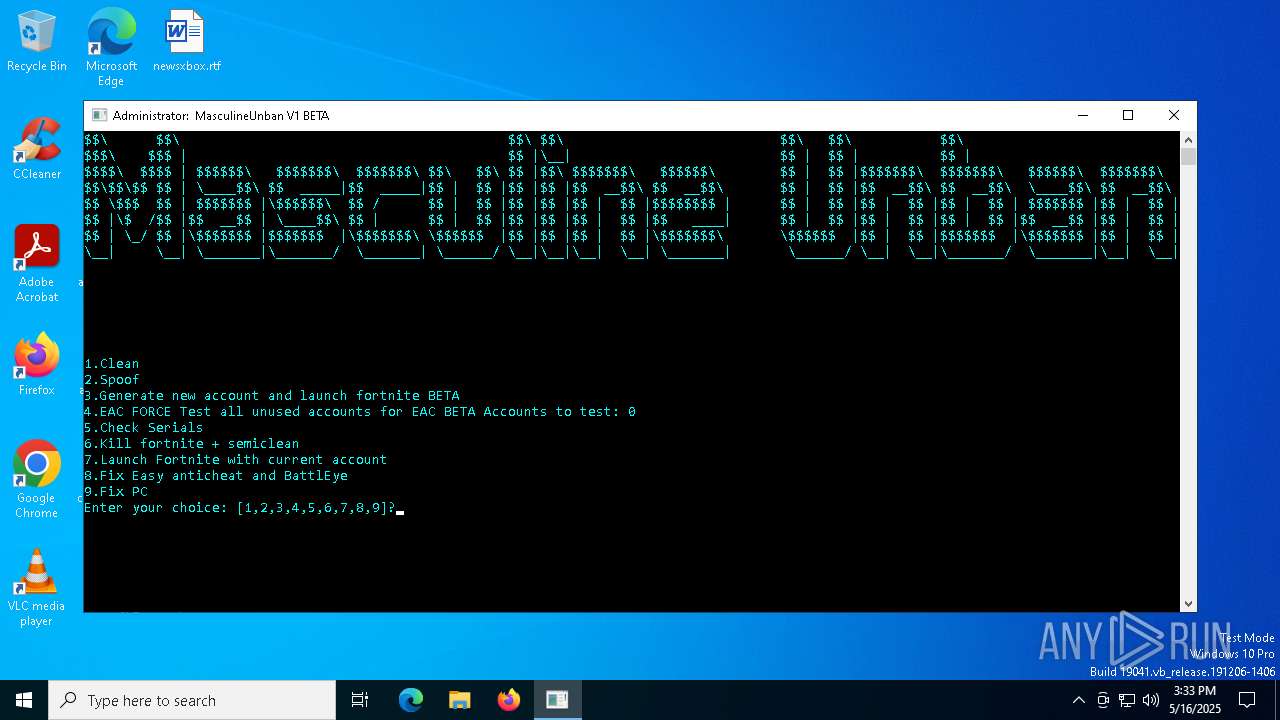
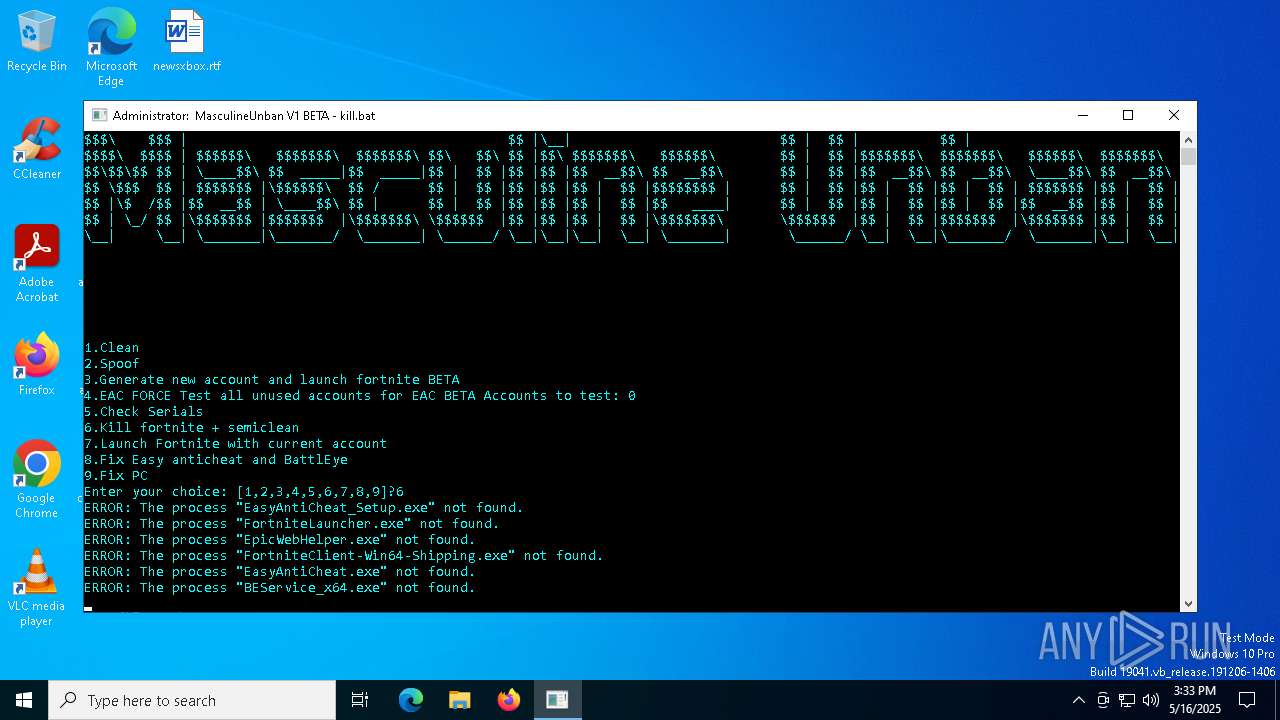
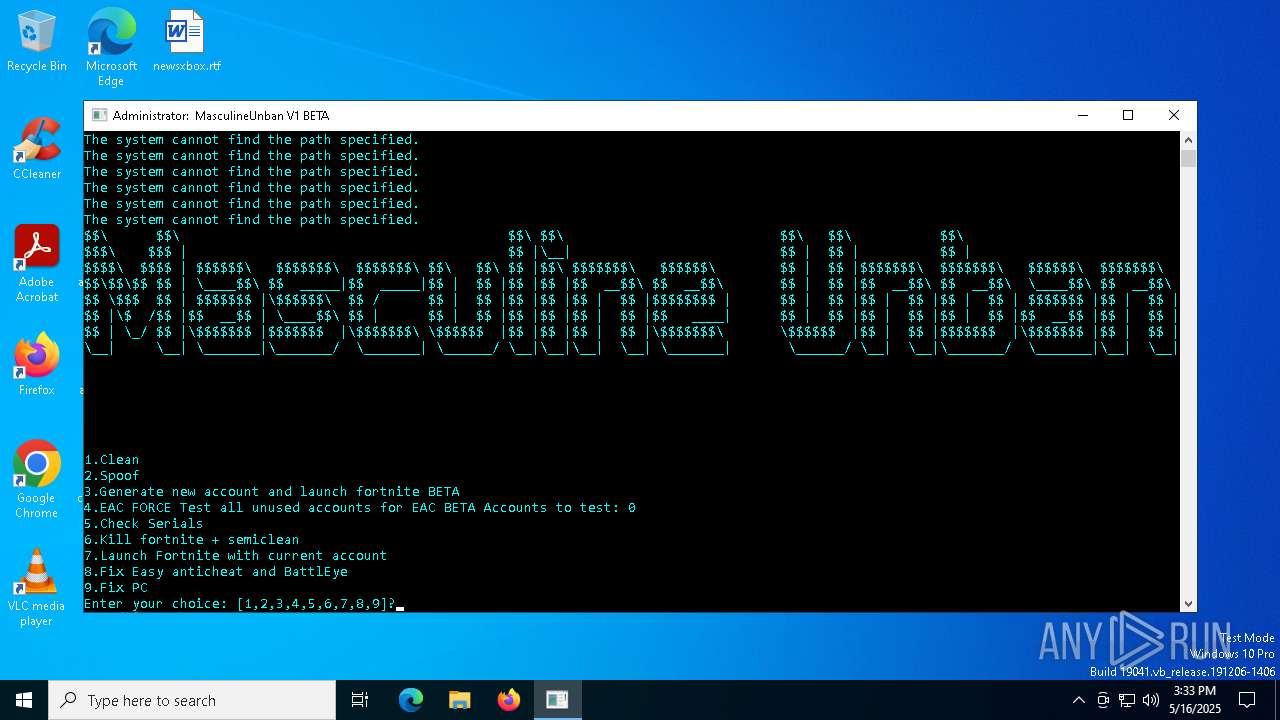
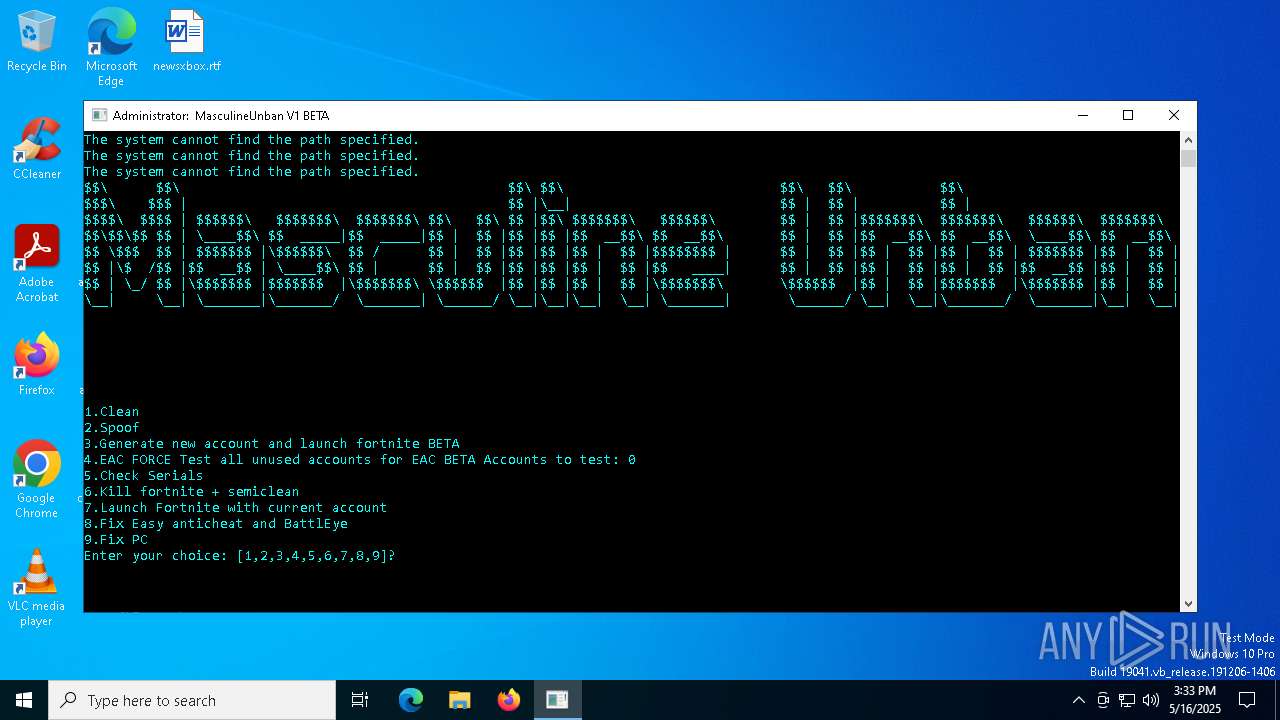
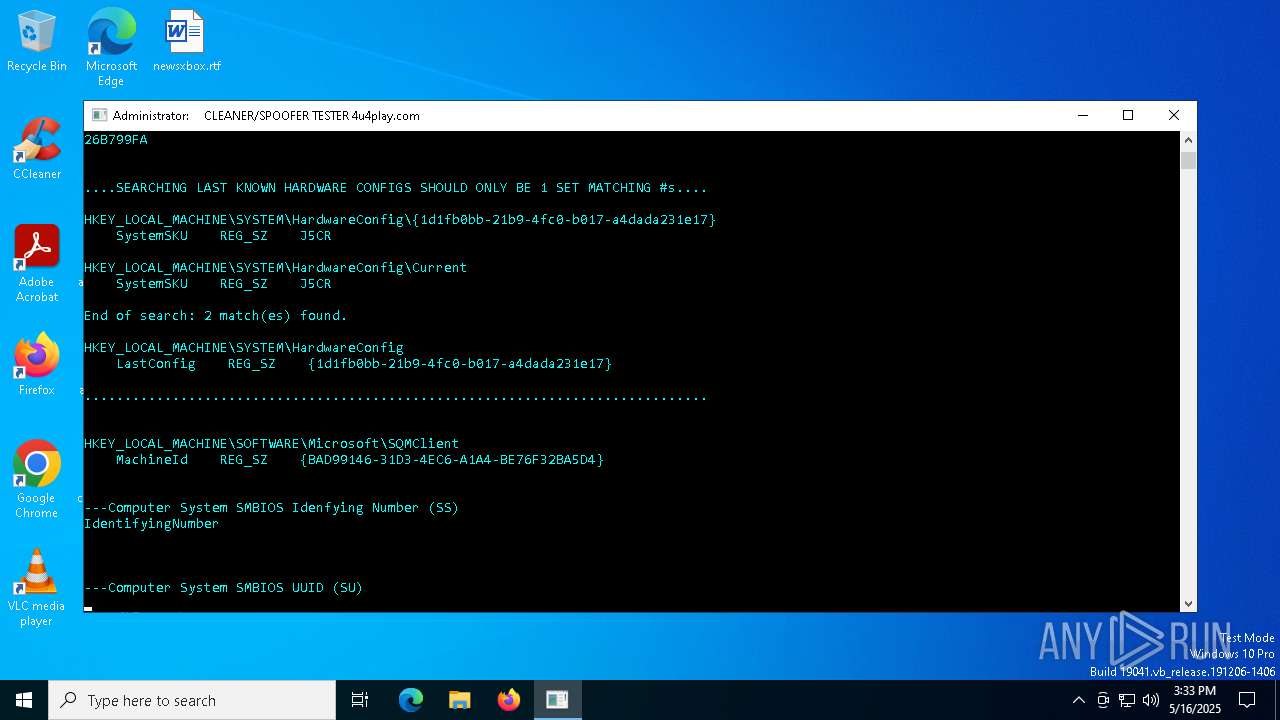
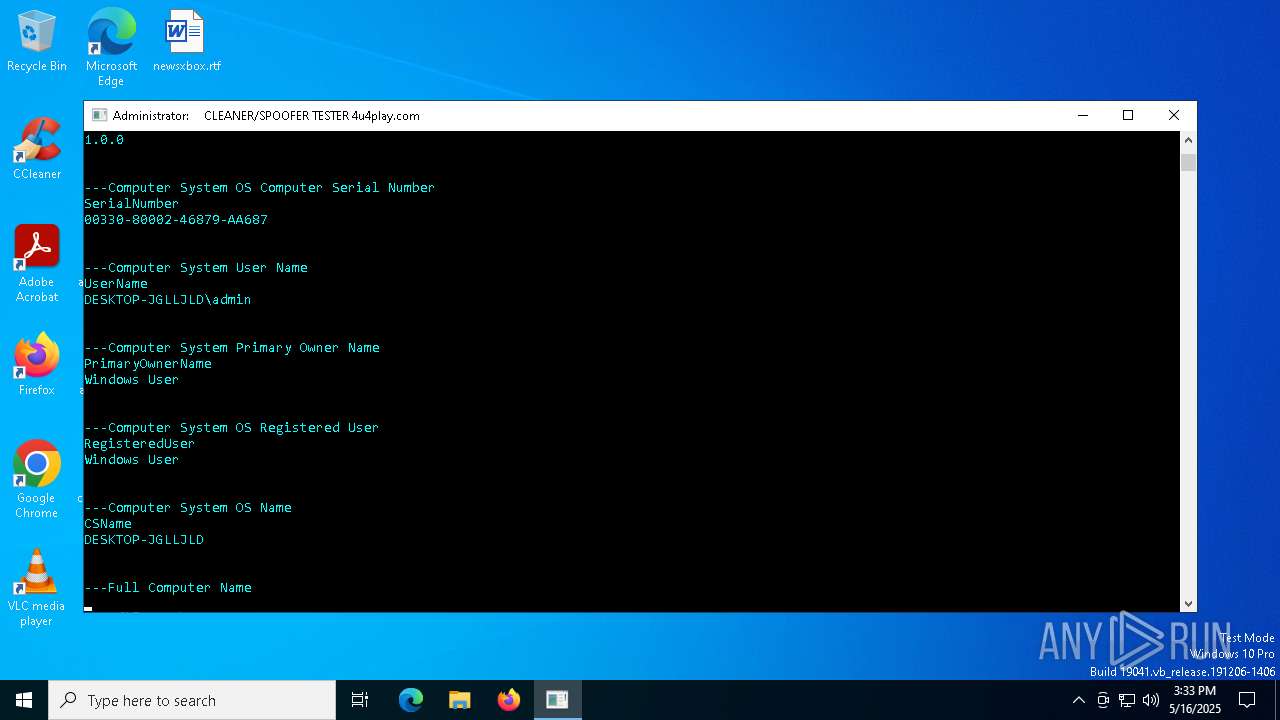
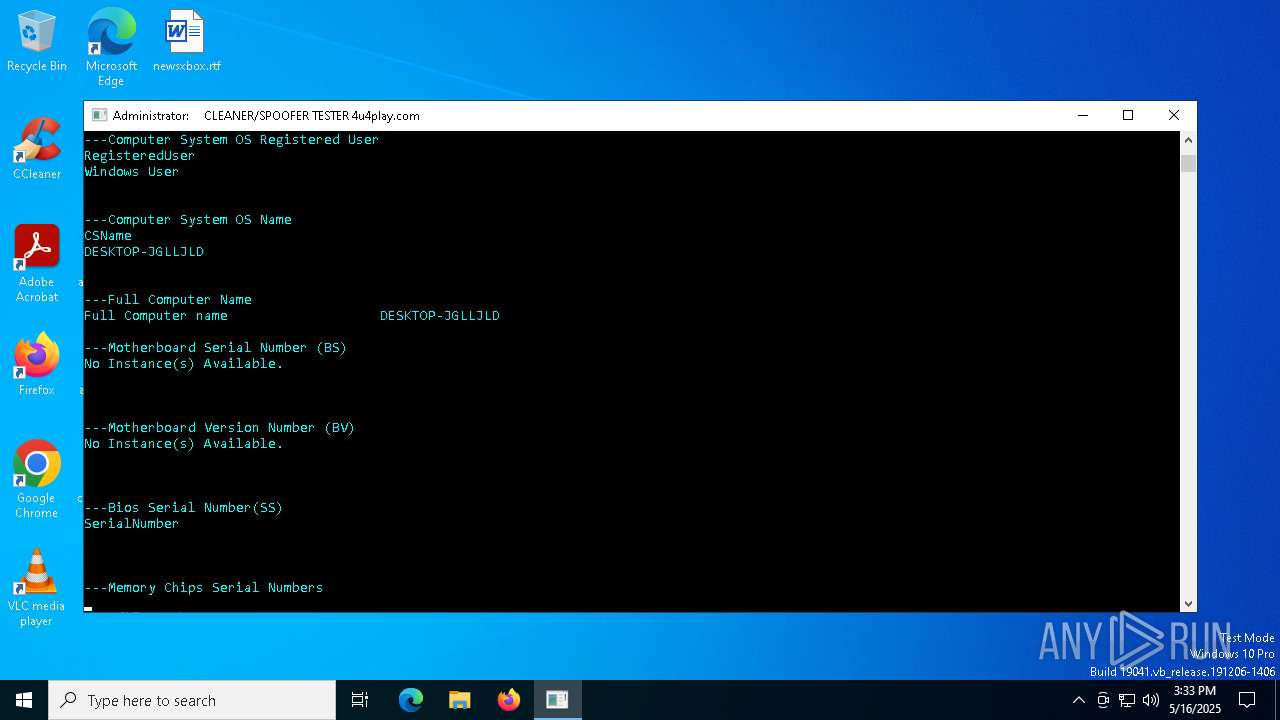
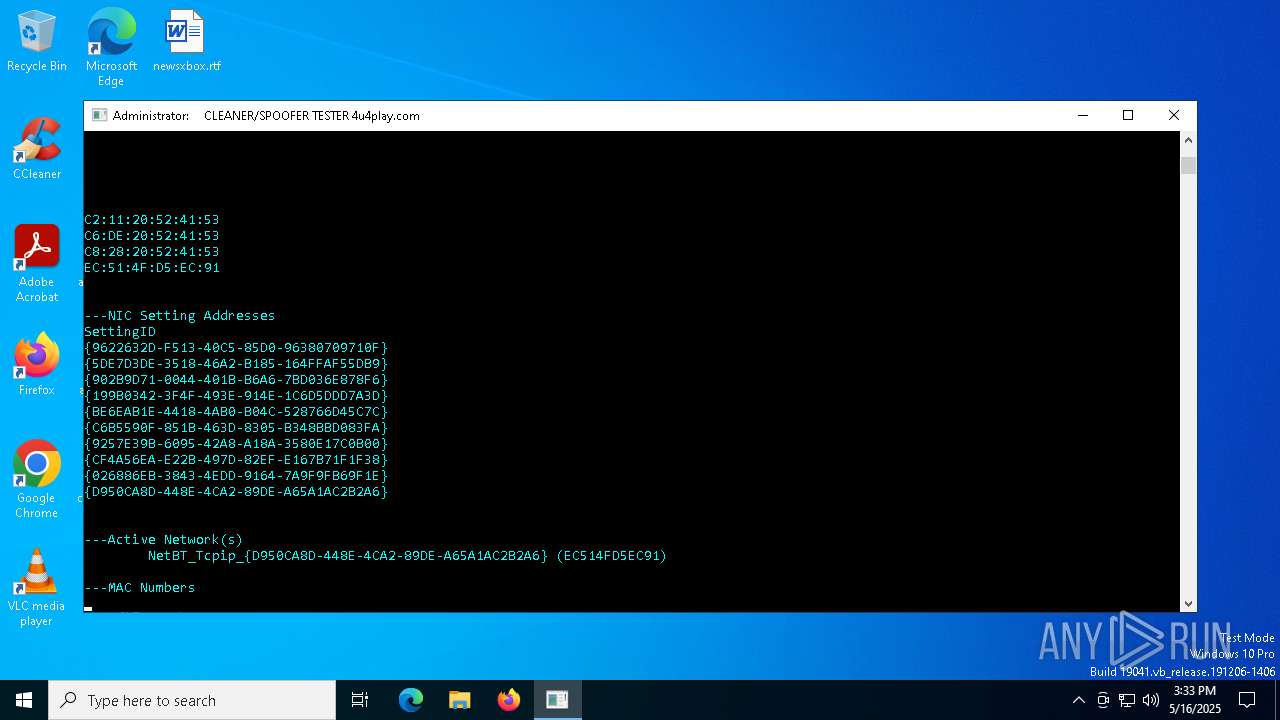
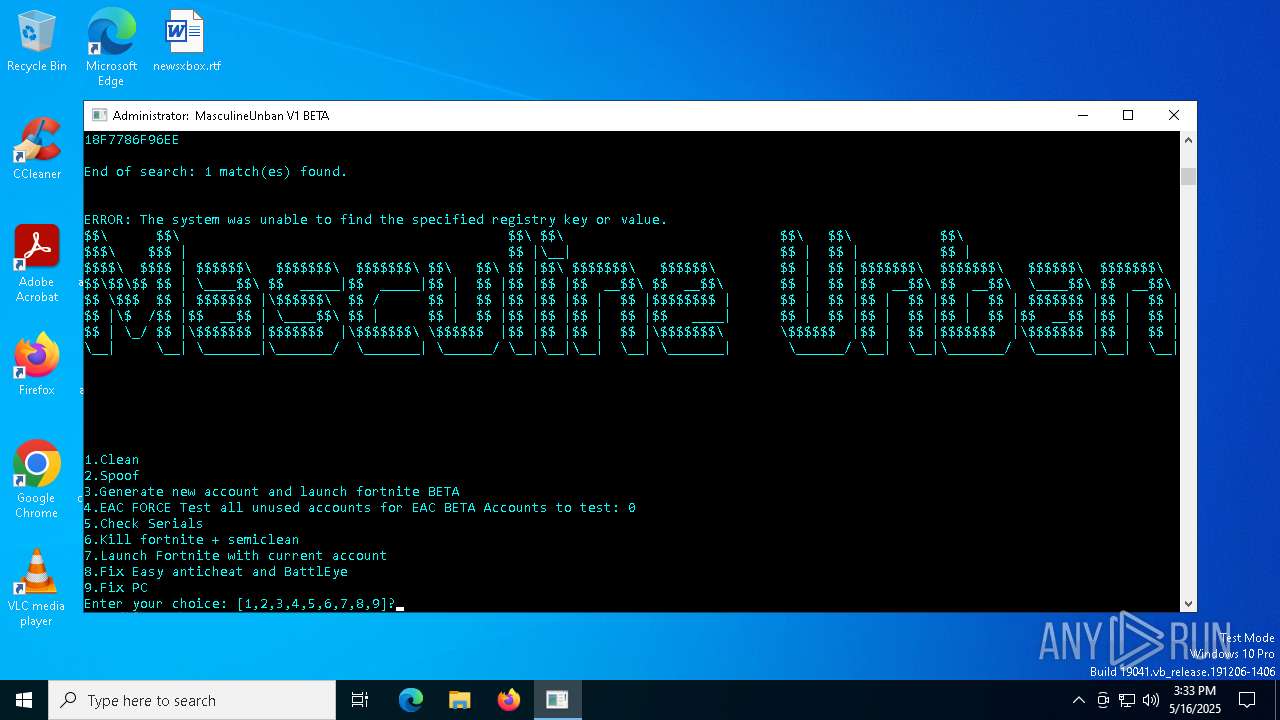
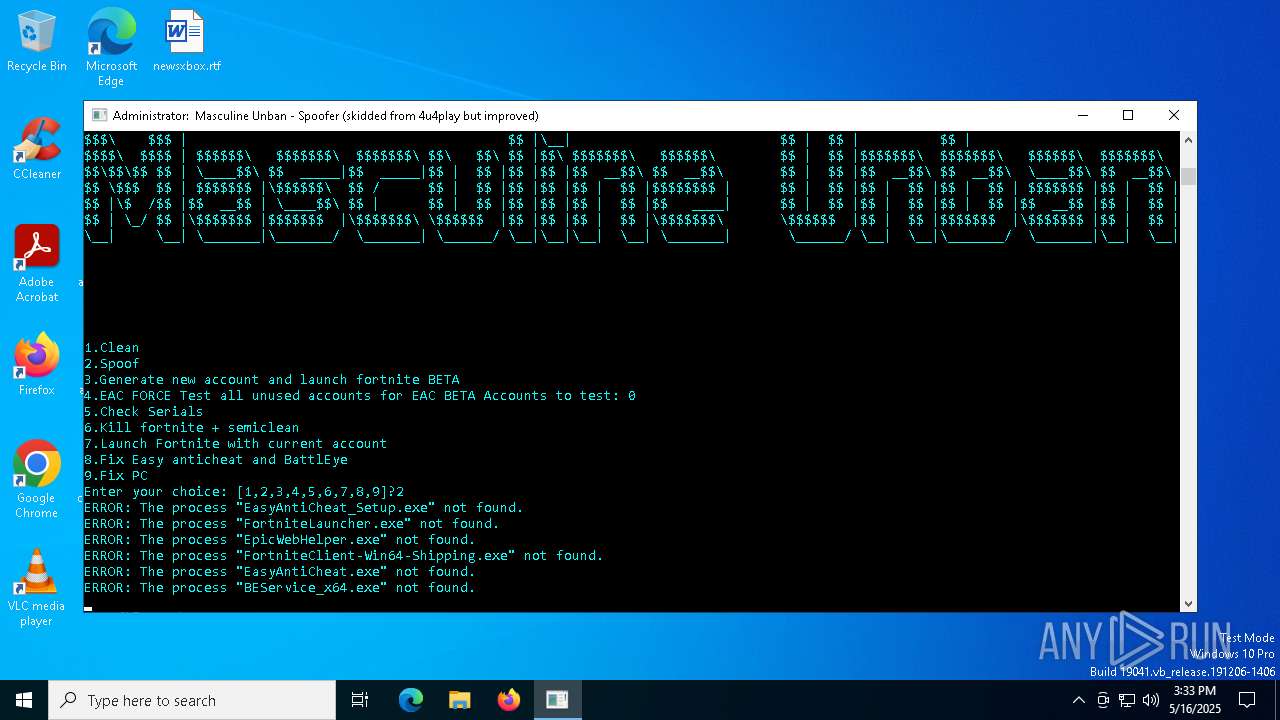
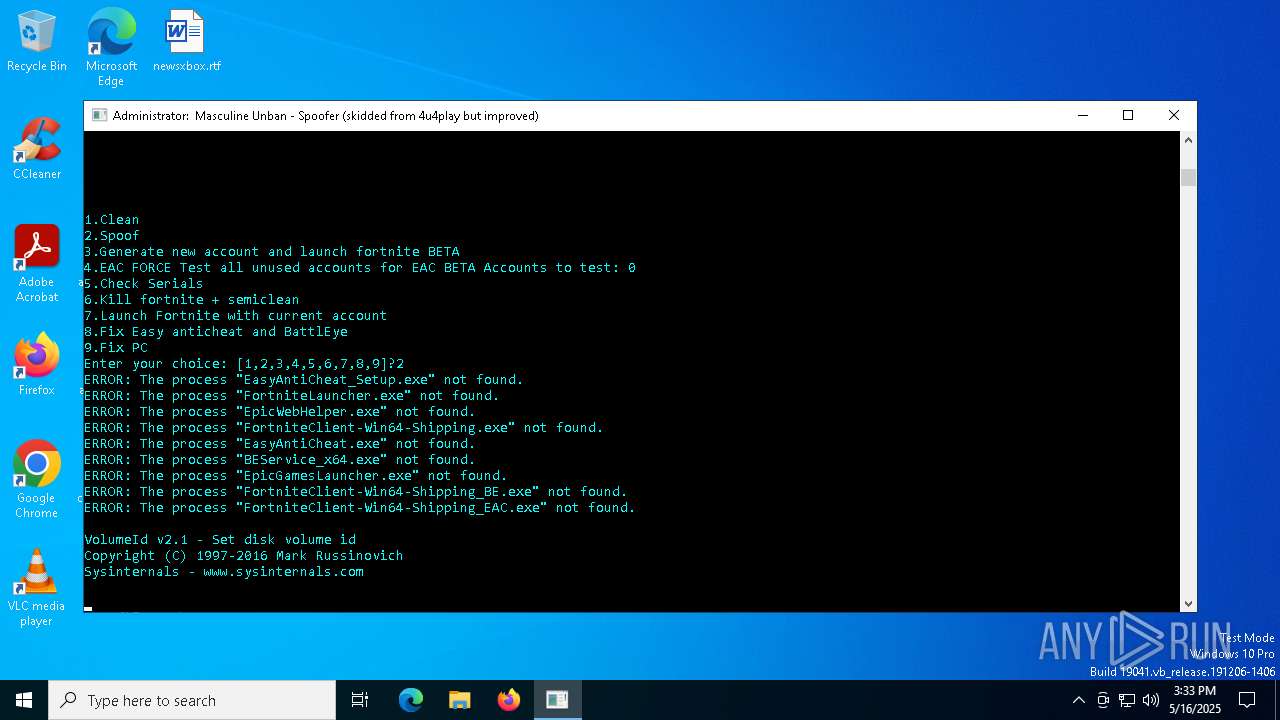
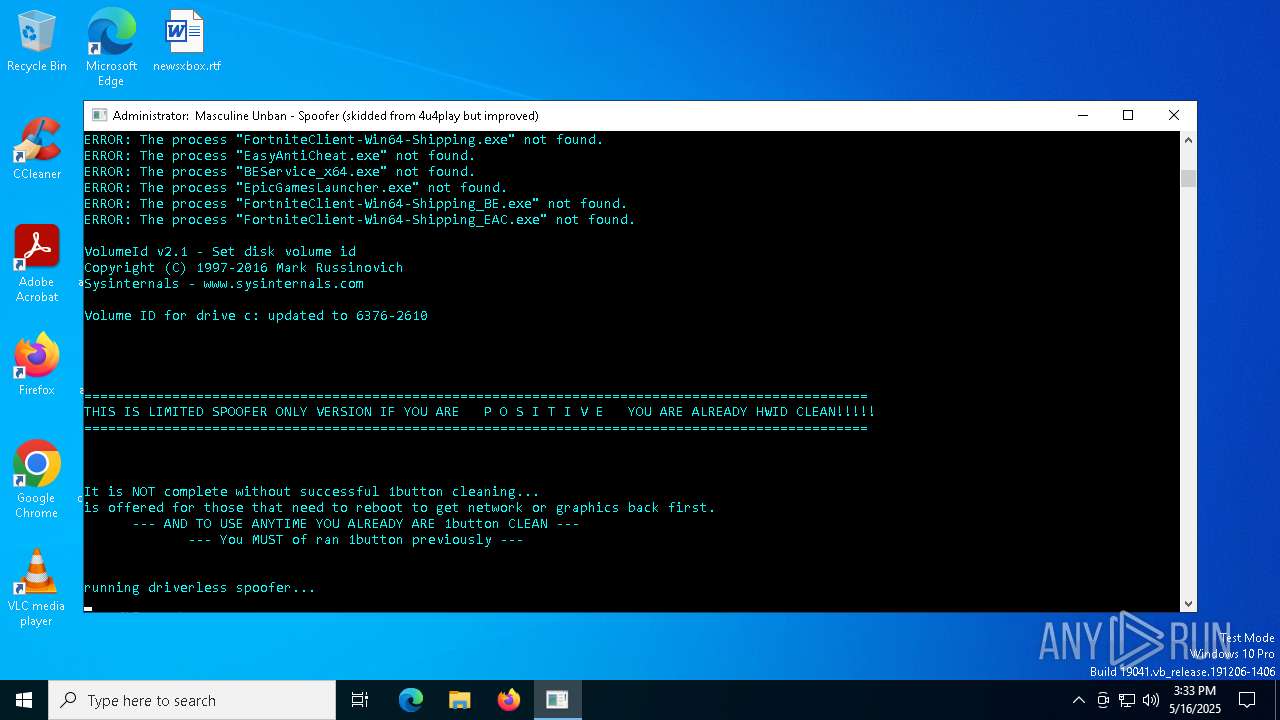
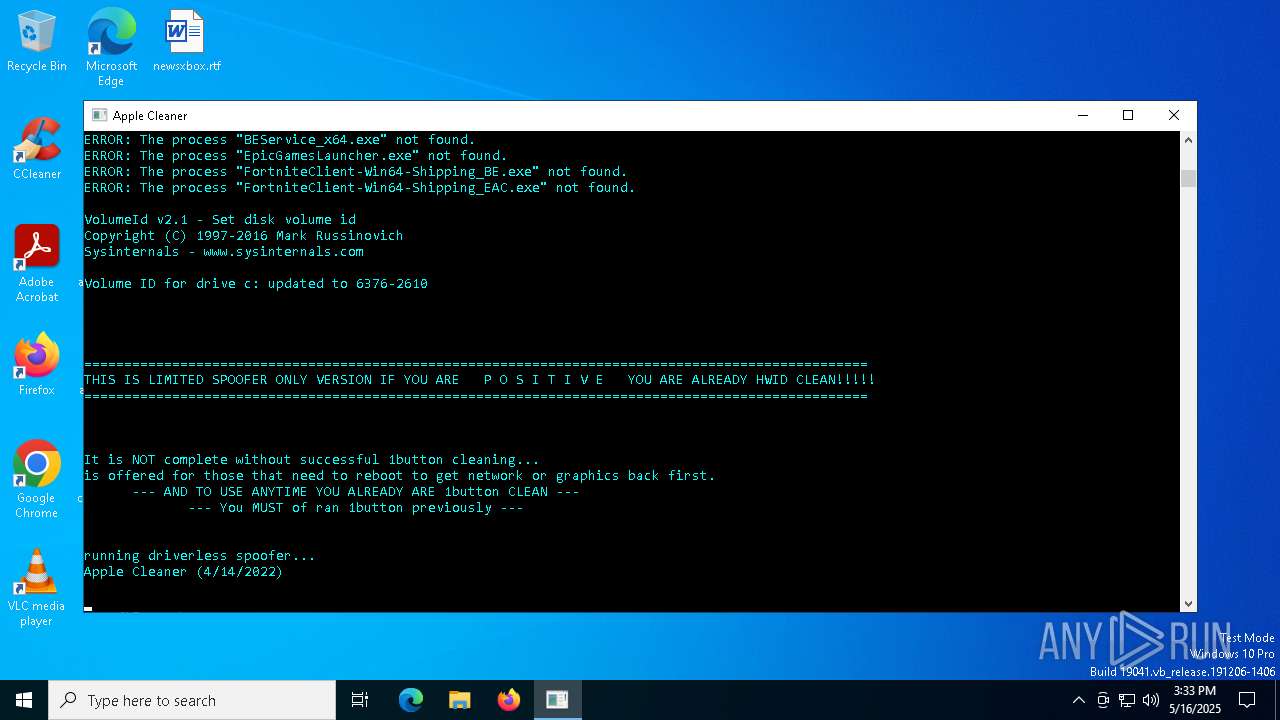
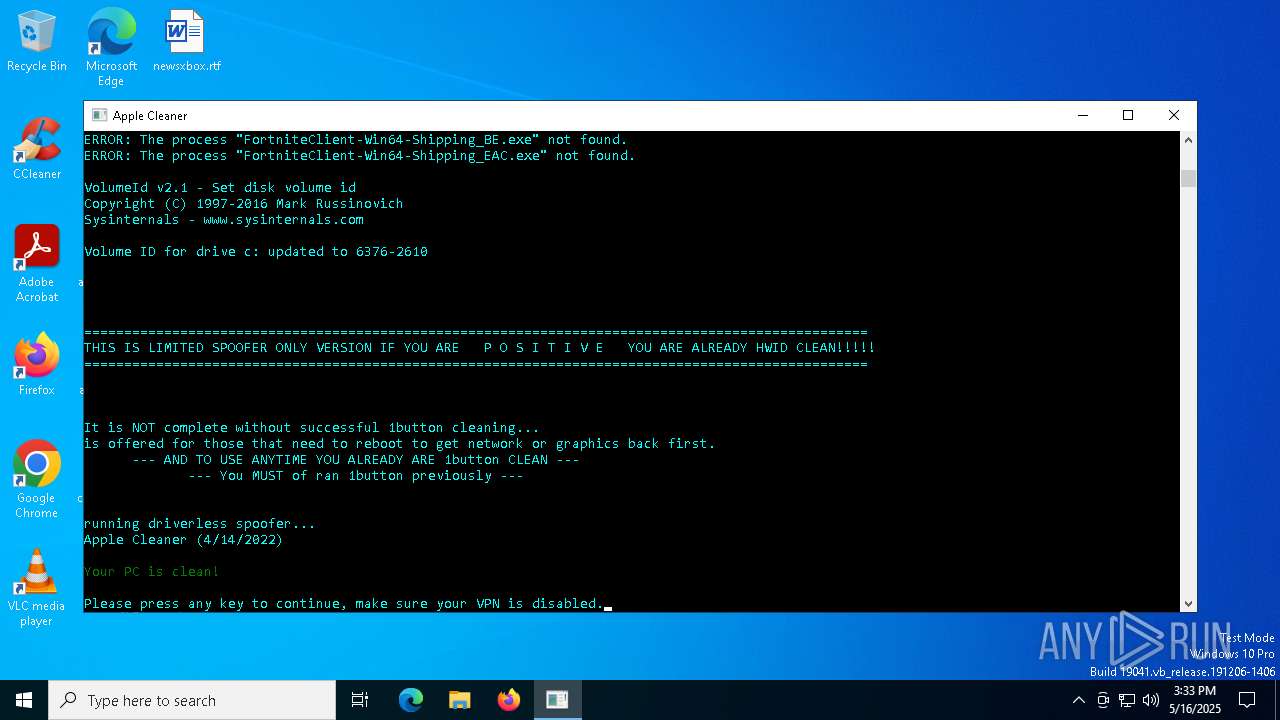
| File name: | MasculineUnban_EARLY_BETA.exe |
| Full analysis: | https://app.any.run/tasks/3935c949-abb2-4222-a7de-f0bee3b55d47 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 15:33:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | ACAFC89FE5F6EFE9701AE037A7FF3690 |
| SHA1: | 7AC0C75C25129FCDA88AB4F3D3C8EB5BEB38D45F |
| SHA256: | E18FF240D3D8A5773515E6E61FA119D909530FD232DAD719A479CC44842BD1A4 |
| SSDEEP: | 98304:v0RzFU1J9HrOcFbOuSeORxedrjRFHOXonqpWvWc2QDtBH0a+U+WhNWg+hwyJQ0li:FCmDVzPNyS |
MALICIOUS
Vulnerable driver has been detected
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
Antivirus name has been found in the command line (generic signature)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 6148)
- cmd.exe (PID: 6244)
Executing a file with an untrusted certificate
- Volumeid64.exe (PID: 1912)
Changes the autorun value in the registry
- AppleCleaner.exe (PID: 4336)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
Process drops legitimate windows executable
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
The process creates files with name similar to system file names
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
Executable content was dropped or overwritten
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
Starts CMD.EXE for commands execution
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
- cmd.exe (PID: 5720)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 6148)
- AppleCleaner.exe (PID: 4336)
Executing commands from a ".bat" file
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 6148)
- cmd.exe (PID: 5720)
The executable file from the user directory is run by the CMD process
- extd.exe (PID: 5960)
- extd.exe (PID: 5596)
- extd.exe (PID: 516)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 6148)
- Volumeid64.exe (PID: 1912)
- AppleCleaner.exe (PID: 4336)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5720)
- cmd.exe (PID: 5384)
- cmd.exe (PID: 4172)
Application launched itself
- cmd.exe (PID: 5720)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5720)
- cmd.exe (PID: 4172)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6488)
- cmd.exe (PID: 4336)
Manipulates environment variables
- powershell.exe (PID: 5008)
Stops a currently running service
- sc.exe (PID: 6108)
- sc.exe (PID: 7052)
- sc.exe (PID: 2092)
- sc.exe (PID: 4728)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5384)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 744)
Starts SC.EXE for service management
- cmd.exe (PID: 5384)
- cmd.exe (PID: 2644)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 4172)
Uses WMIC.EXE to obtain volume information
- cmd.exe (PID: 4172)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 4172)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4172)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 960)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 4172)
Accesses system license id via WMI (SCRIPT)
- WMIC.exe (PID: 4200)
Accesses current user name via WMI (SCRIPT)
- WMIC.exe (PID: 1132)
Uses WMIC.EXE
- cmd.exe (PID: 4172)
Accesses computer name via WMI (SCRIPT)
- WMIC.exe (PID: 4620)
Starts NET.EXE to manage network resources
- cmd.exe (PID: 4172)
- net.exe (PID: 2904)
- net.exe (PID: 6808)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 4172)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 4172)
Uses WMIC.EXE to obtain memory chip information
- cmd.exe (PID: 4172)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 4172)
Uses WMIC.EXE to obtain information about the network interface controller
- cmd.exe (PID: 4172)
Hides command output
- cmd.exe (PID: 744)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 4464)
Reads the BIOS version
- AppleCleaner.exe (PID: 4336)
Reads the Windows owner or organization settings
- AppleCleaner.exe (PID: 4336)
Detected use of alternative data streams (AltDS)
- AppleCleaner.exe (PID: 4336)
INFO
The sample compiled with english language support
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
Checks supported languages
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
- extd.exe (PID: 5960)
- extd.exe (PID: 5596)
- extd.exe (PID: 516)
- devcon.exe (PID: 2564)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 6148)
- Volumeid64.exe (PID: 1912)
- AppleCleaner.exe (PID: 4336)
- identity_helper.exe (PID: 7840)
Creates files or folders in the user directory
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
Create files in a temporary directory
- MasculineUnban_EARLY_BETA.exe (PID: 5056)
- reset2-Hardware Rescan after Adapter reset.exe (PID: 6148)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5988)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2800)
- WMIC.exe (PID: 4112)
- WMIC.exe (PID: 4300)
- WMIC.exe (PID: 736)
- WMIC.exe (PID: 960)
- WMIC.exe (PID: 1228)
- WMIC.exe (PID: 4200)
- WMIC.exe (PID: 1132)
- WMIC.exe (PID: 4728)
- WMIC.exe (PID: 4336)
- WMIC.exe (PID: 4724)
- WMIC.exe (PID: 4620)
- WMIC.exe (PID: 2772)
- WMIC.exe (PID: 1240)
- WMIC.exe (PID: 1056)
- WMIC.exe (PID: 1040)
- WMIC.exe (PID: 5228)
- WMIC.exe (PID: 6272)
- WMIC.exe (PID: 1388)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 2140)
Reads Windows Product ID
- reg.exe (PID: 4272)
- AppleCleaner.exe (PID: 4336)
Process checks whether UAC notifications are on
- AppleCleaner.exe (PID: 4336)
Reads the time zone
- AppleCleaner.exe (PID: 4336)
Manual execution by a user
- msedge.exe (PID: 7052)
Reads the machine GUID from the registry
- AppleCleaner.exe (PID: 4336)
Reads Environment values
- AppleCleaner.exe (PID: 4336)
- identity_helper.exe (PID: 7840)
Reads the computer name
- AppleCleaner.exe (PID: 4336)
- identity_helper.exe (PID: 7840)
Application launched itself
- msedge.exe (PID: 2984)
- msedge.exe (PID: 7052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 92672 |
| InitializedDataSize: | 6263296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
316
Monitored processes
182
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\Users\admin\AppData\Local\Temp\B9EB.tmp\B9EC.tmp\extd.exe "/center" "" "" "" "" "" "" "" "" | C:\Users\admin\AppData\Local\Temp\B9EB.tmp\B9EC.tmp\extd.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 672 | reg delete "HKEY_CURRENT_USER\Software\Epic Games" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | REG QUERY HKLM\SOFTWARE\Microsoft\SQMClient /v MachineId | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | reg query "HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\StillImage\Events\Disconnected" /v GUID /t REG_SZ | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | reg delete "HKLM\SYSTEM\CurrentControlSet\Services\BEService" /va /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | reg query "HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\StillImage\Events\Connected" /v GUID /t REG_SZ | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | wmic logicaldisk get volumeserialnumber | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | reg query "HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.microsoftedge_8wekyb3d8bbwe\MicrosoftEdge\ExtensionsStore\datastore\usage\dscc_inventory\ExtensionInventoryVersionGUID_DONOTUSEINSTORE" /v value /t REG_SZ | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
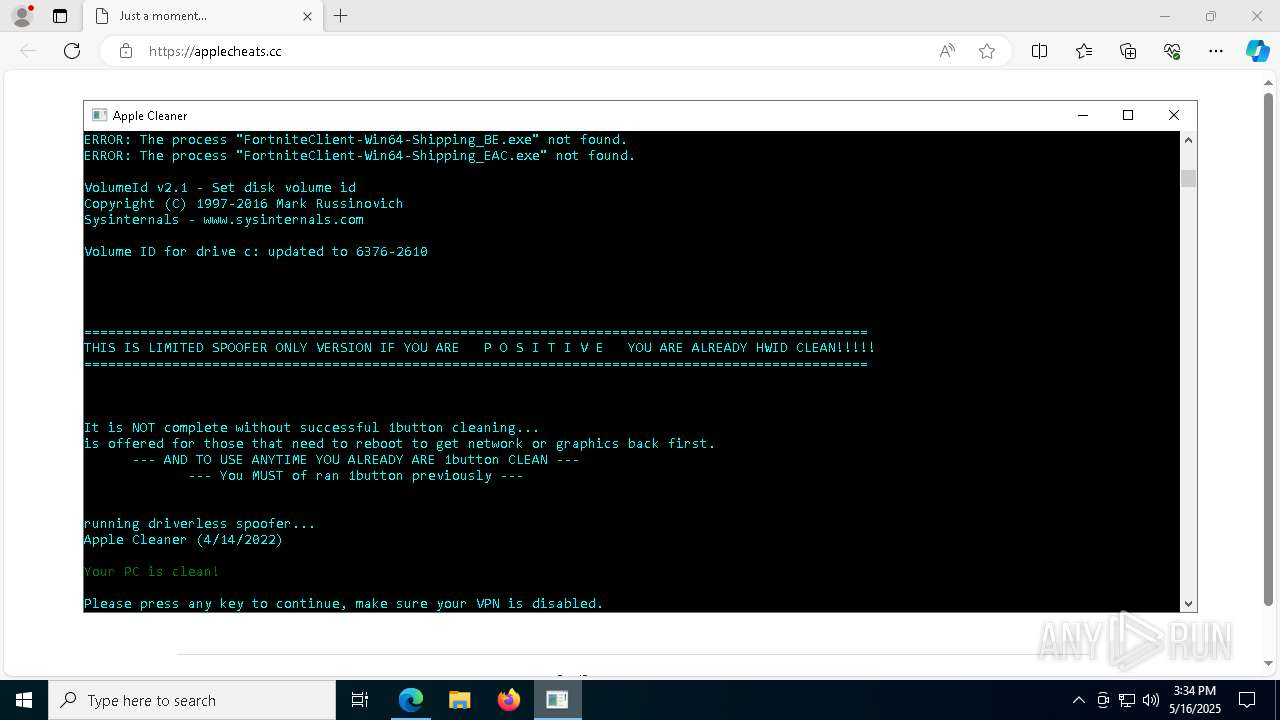
| 744 | C:\WINDOWS\system32\cmd.exe /c taskkill /f /im FortniteClient-Win64-Shipping.exe >nul 2>&1 | C:\Windows\System32\cmd.exe | — | AppleCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | findstr /C:"Full Computer name" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 980
Read events
21 825
Write events
150
Delete events
5
Modification events
| (PID) Process: | (5556) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\Power |
| Operation: | write | Name: | HiberbootEnabled |
Value: 0 | |||
| (PID) Process: | (2800) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | EpicGamesLauncher |
Value: | |||
| (PID) Process: | (2564) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ComputerName\ComputerName |
| Operation: | write | Name: | ComputerName |
Value: 19529 | |||
| (PID) Process: | (6488) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ComputerName\ActiveComputerName |
| Operation: | write | Name: | ComputerName |
Value: 30499 | |||
| (PID) Process: | (1912) Volumeid64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\VolumeID |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (2040) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2040) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2040) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2984) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
25
Suspicious files
212
Text files
53
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\1-spoofer.bat | text | |
MD5:6BAAF74862BD68849ADC91B8160E5DF3 | SHA256:AD5A2EF7ED4ED98186AE7E6F32FD58D5E7321989A6427D73002A474ED9968DA6 | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\1-cleaner.bat | text | |
MD5:94380E226AFD2EF08D4847986EFFA082 | SHA256:F5C0FE7711A2AF390FEB6D8CEE4E2C7D52FEFB5047DE05EF905AF887698CDD1D | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\DeviceCleanupCmd.exe | executable | |
MD5:030180CC1C3299E061D1B6F5B1754297 | SHA256:878AAF3A5283F1403552909E42558FC24C90D8EEEB66527EAEDD8555F9E117C9 | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\AMIDEWINx64.EXE | executable | |
MD5:F17ECF761E70FEB98C7F628857EEDFE7 | SHA256:311F5C844746D4270B5B971CCEF8D74DDEDCA873EB45F34A1A55F1EA4A3BAFCF | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Local\Temp\B9EB.tmp\B9EC.tmp\B9ED.bat | text | |
MD5:E1B05D54655CB15573784BB2B4C6B691 | SHA256:8F4058ADA426F29710437D2BB78A68C989FA9A506769C694BC945CE57EEF75AC | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\1-RUNFIRST.exe | executable | |
MD5:6FBE881F1D6480E2E15D3EBE0F493D2D | SHA256:49B84540D5B4B8D2344C25EDB042E216592DD1DC78A5C00F2AD9457442C4581C | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\ddc.exe | executable | |
MD5:97B963FD85FF4CC2A3B0DA8164593CFC | SHA256:AF219747072341760396D686F2FE7350EC2DCE713F1EC1977C21F8BE7B9197D5 | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\AMIFLDRV64.SYS | executable | |
MD5:F22740BA54A400FD2BE7690BB204AA08 | SHA256:65C26276CADDA7A36F8977D1D01120EDB5C3418BE2317D501761092D5F9916C9 | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\dd.dll | executable | |
MD5:CBE4163CAAB5AE09FA1E03B87B491380 | SHA256:E982CB681DD366D5F83FA3C17C2E1929611479507C9247D063E47ACE0C971ACA | |||
| 5056 | MasculineUnban_EARLY_BETA.exe | C:\Users\admin\AppData\Roaming\cleanerOLD1.exe | executable | |
MD5:59A7CE7A4D30E28E6BC356263693EB98 | SHA256:390257A0360C025E42F0DB4C4826C3EA192E99A68C7AFCC548A8956F828F6379 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
41
DNS requests
42
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5552 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5552 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5552 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5552 | SIHClient.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5552 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
applecheats.cc |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6436 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6436 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6436 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6436 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6436 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |