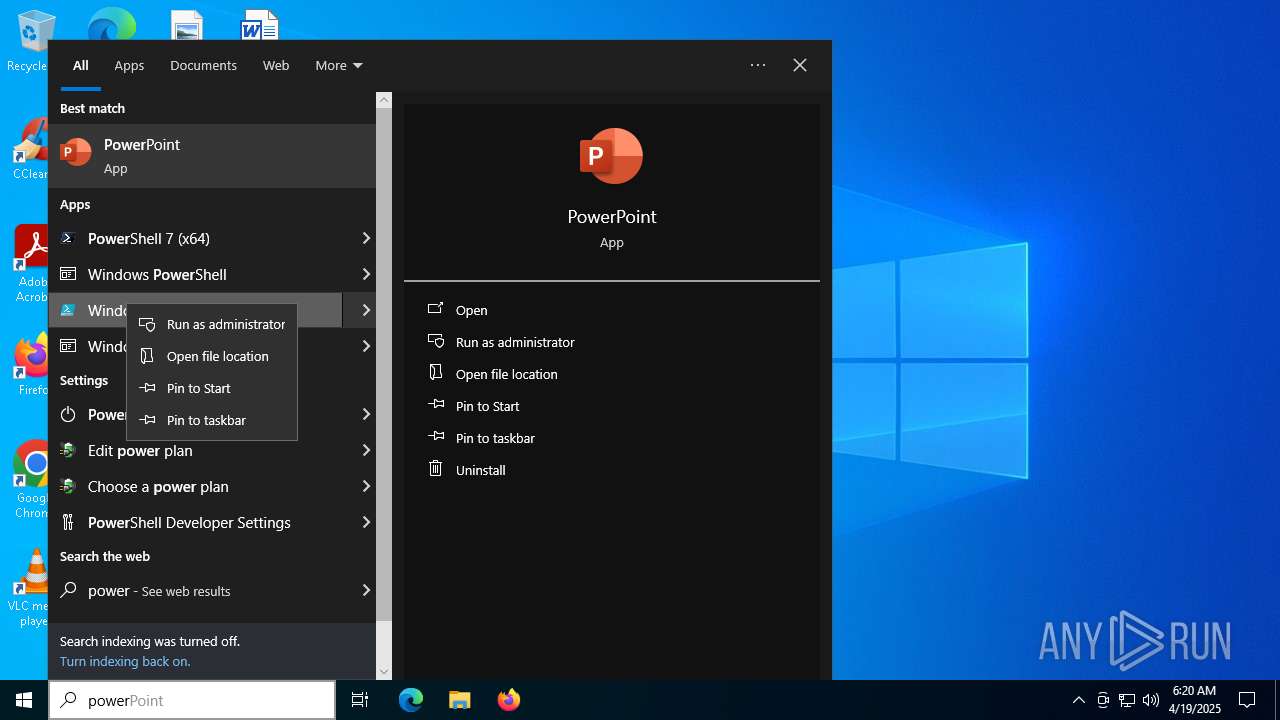
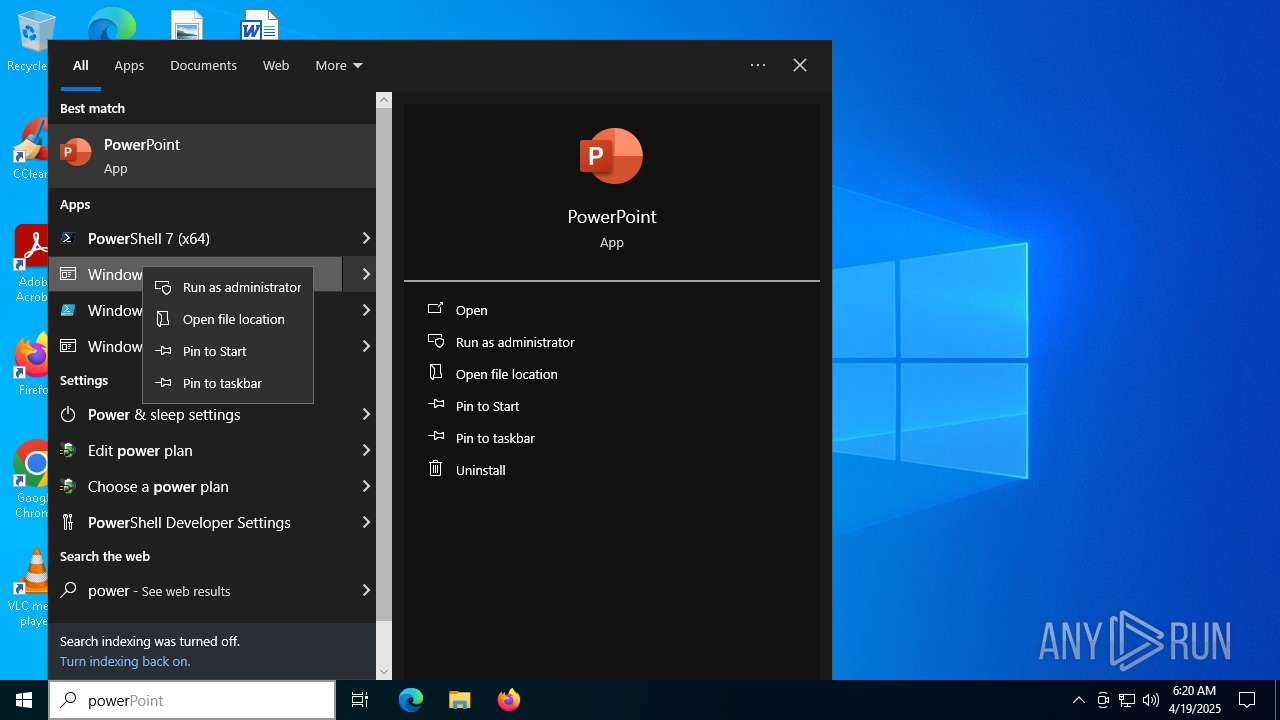
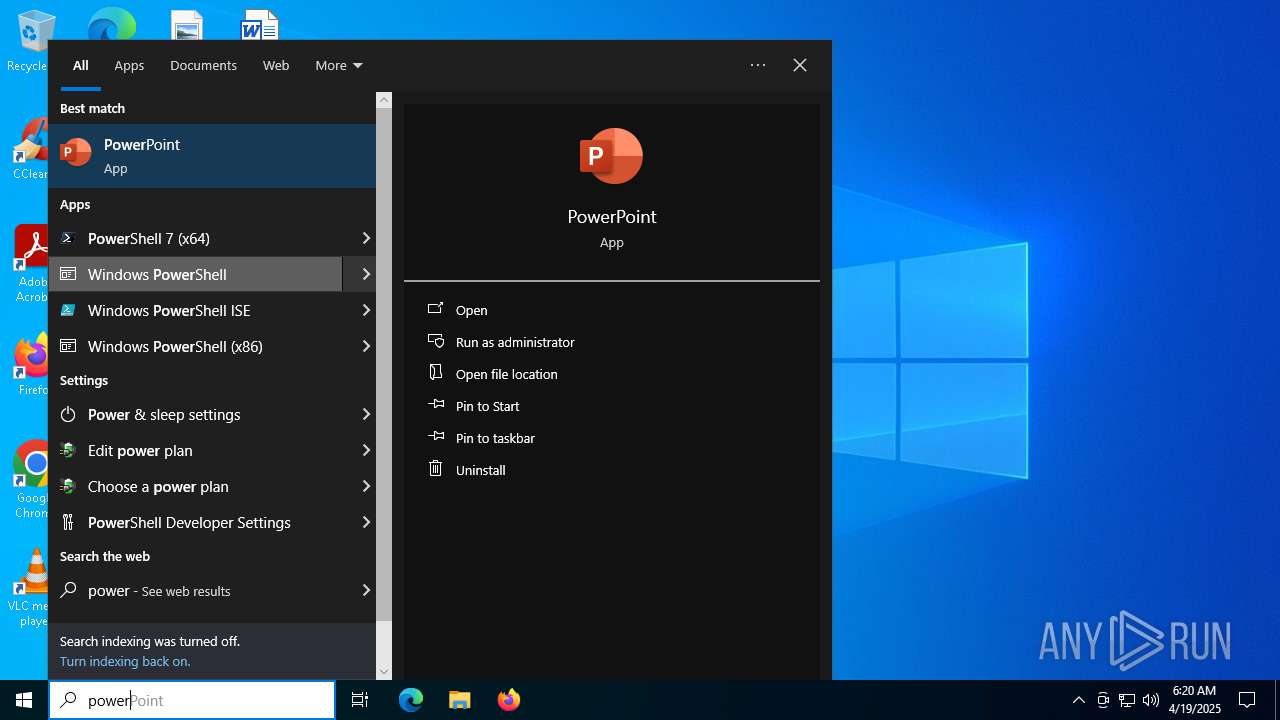
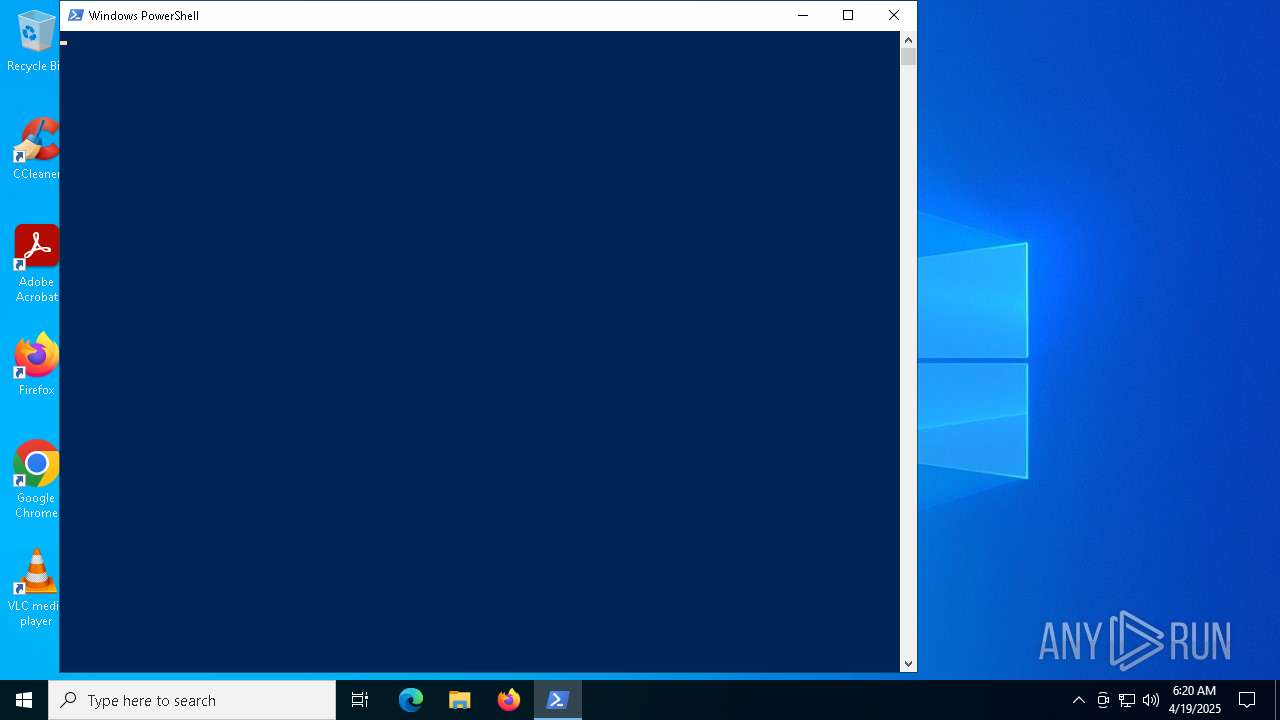
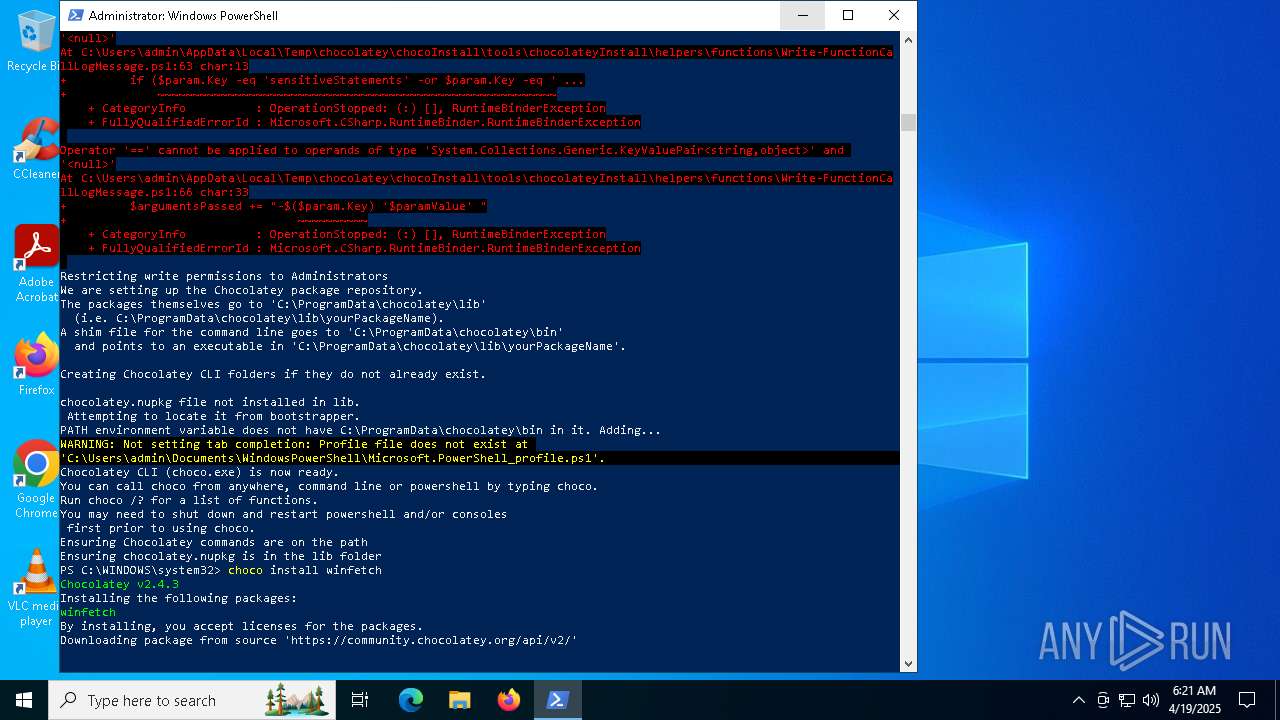
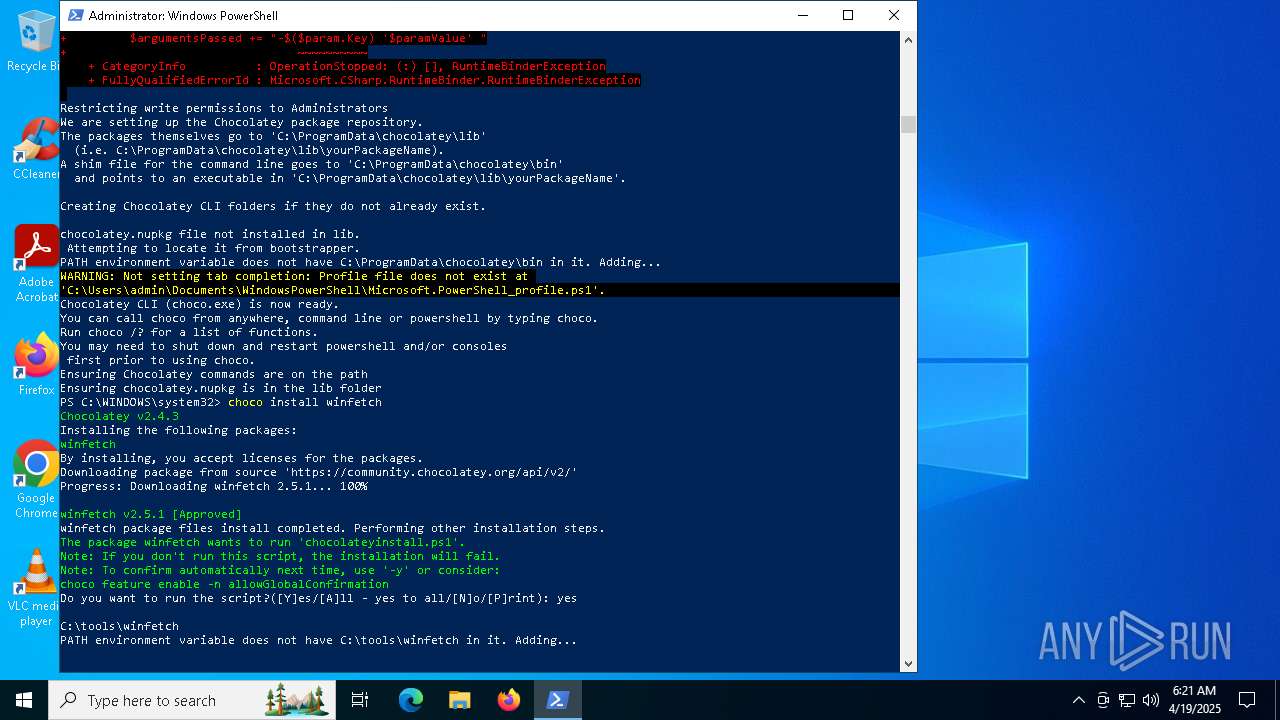
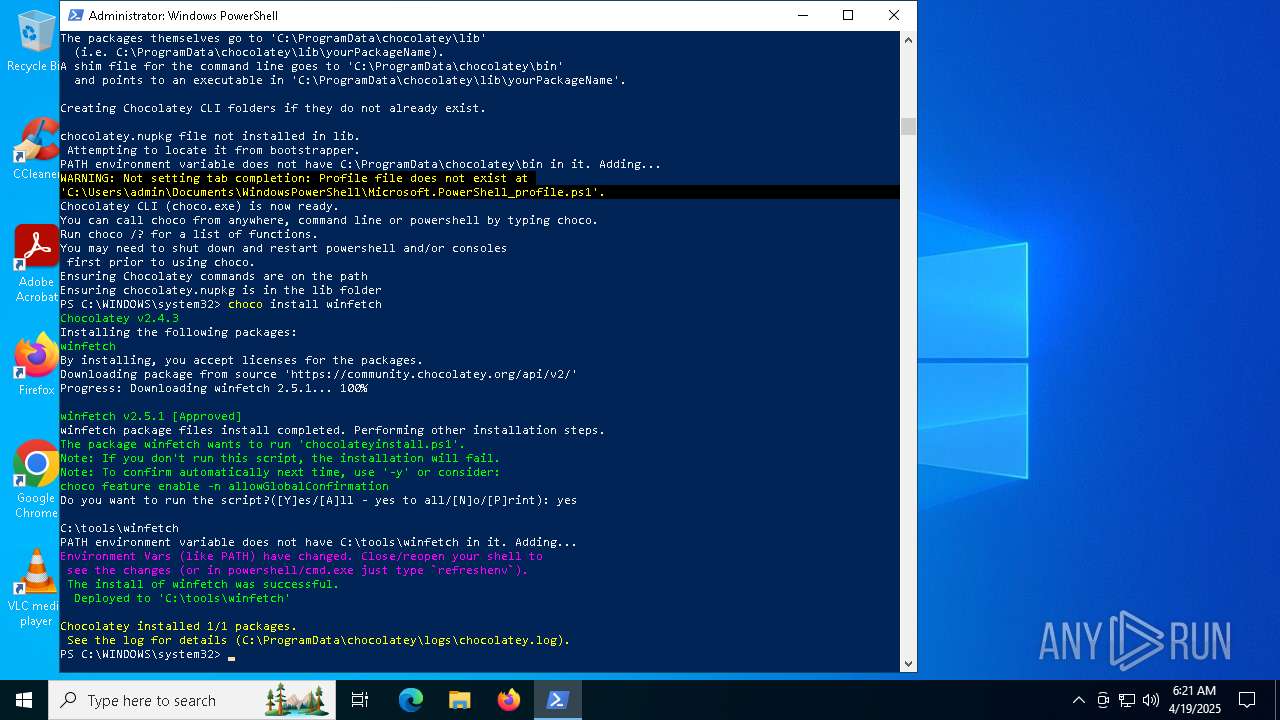
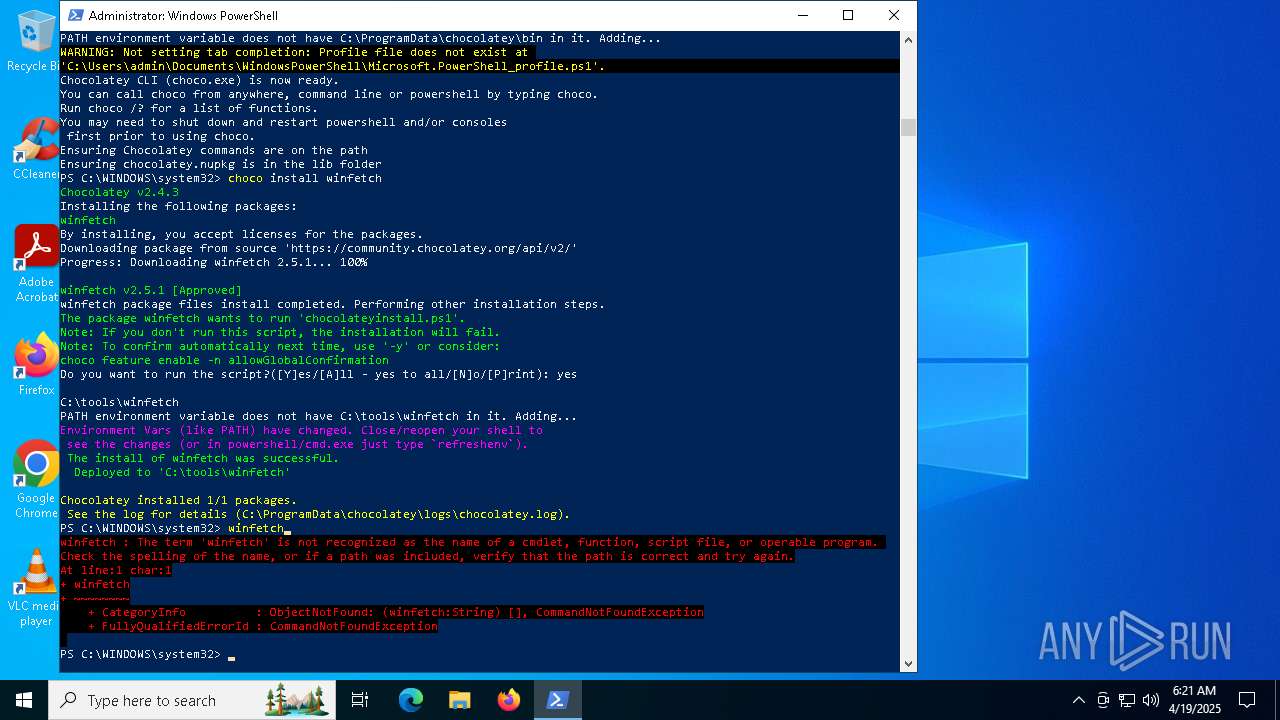
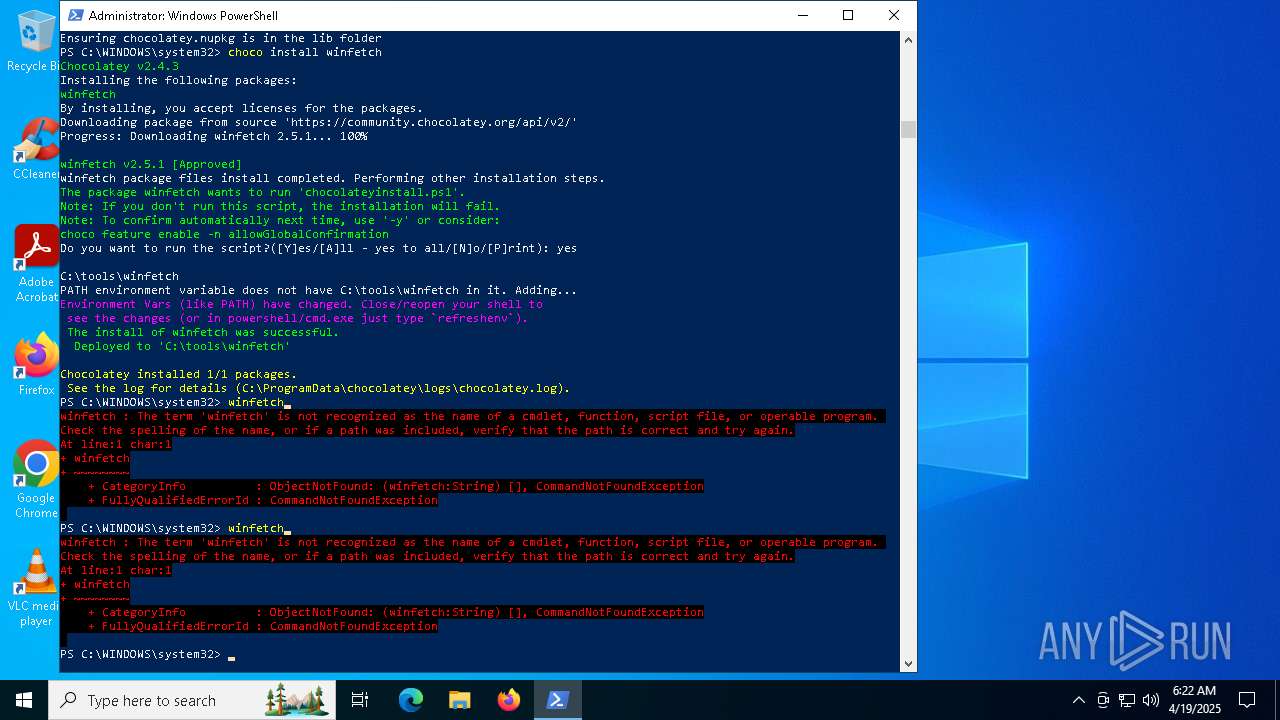
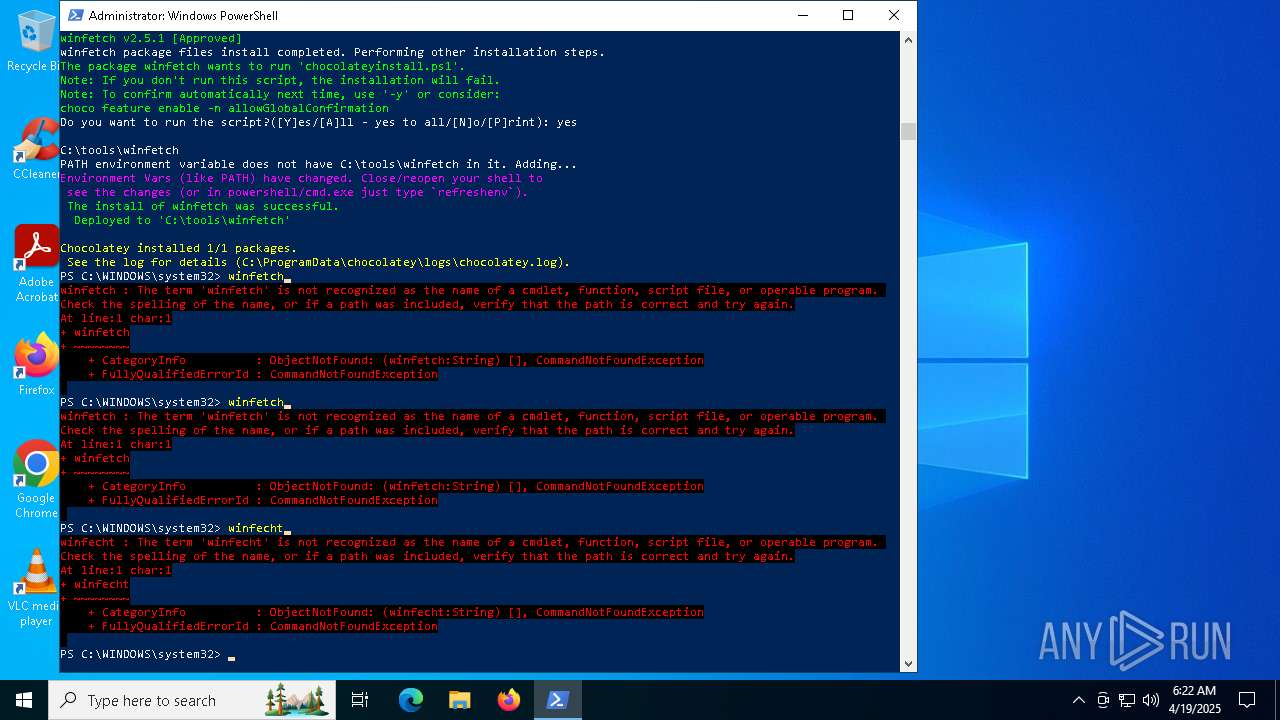
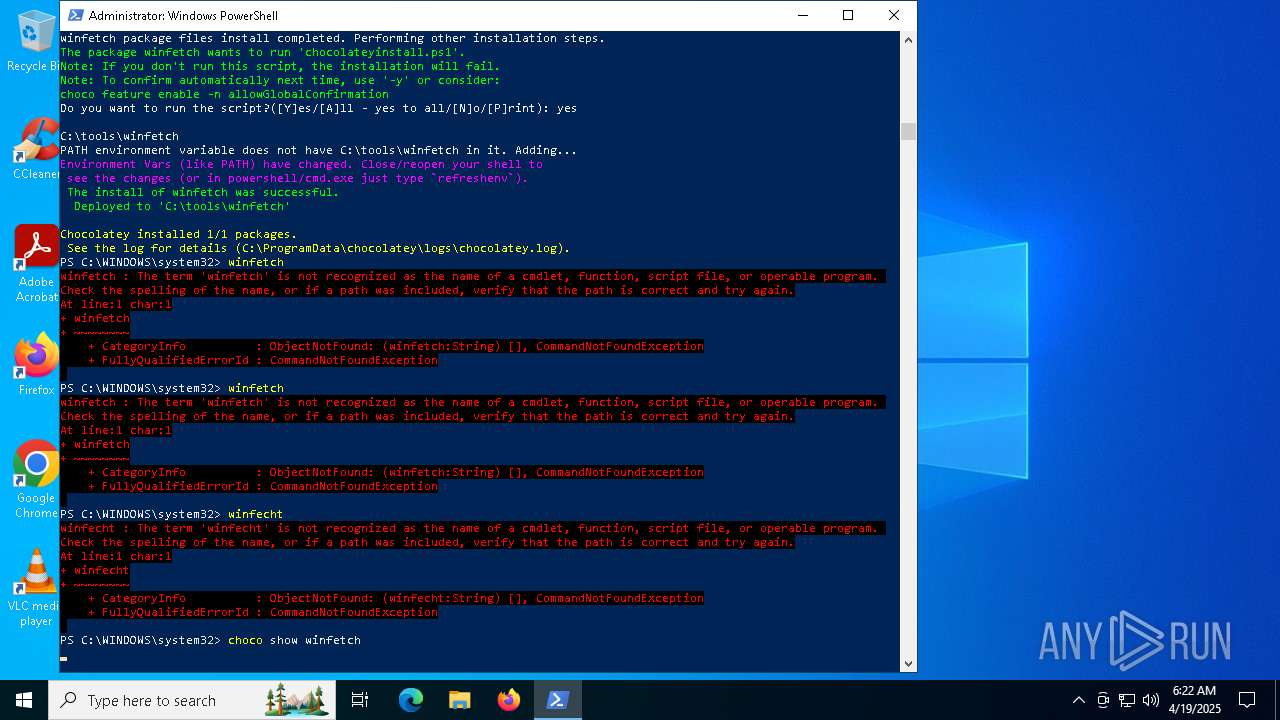
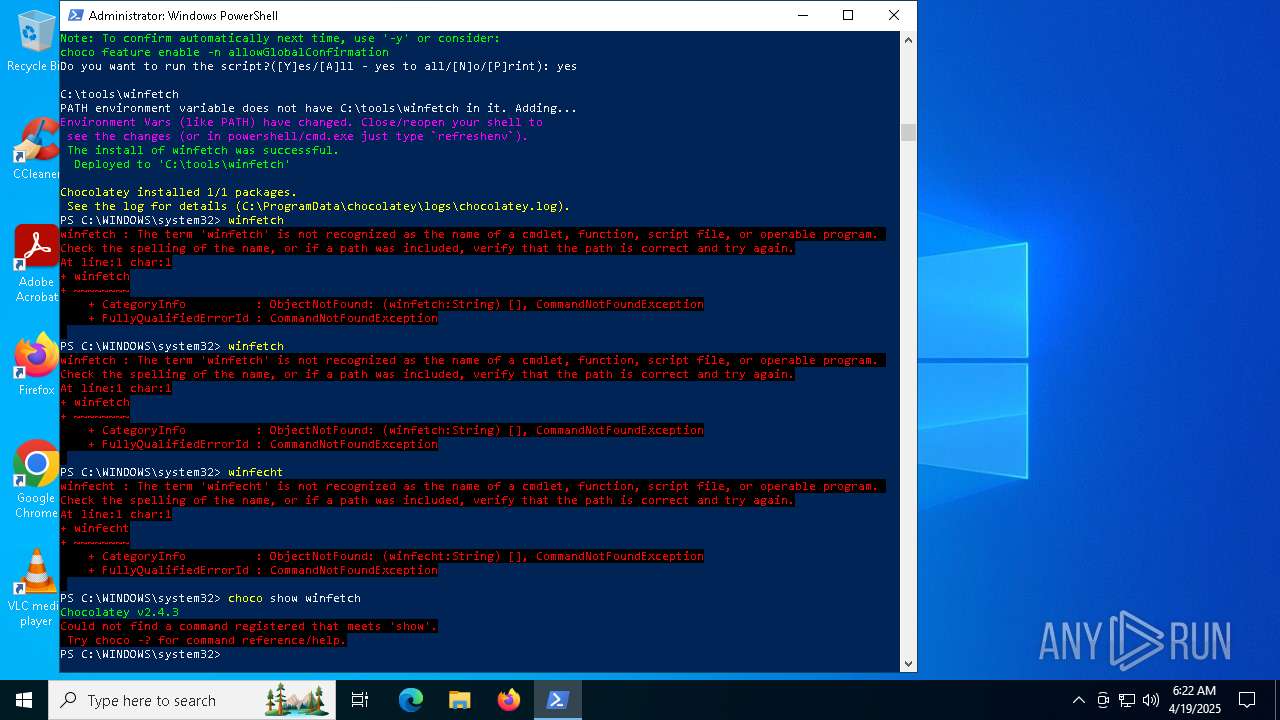
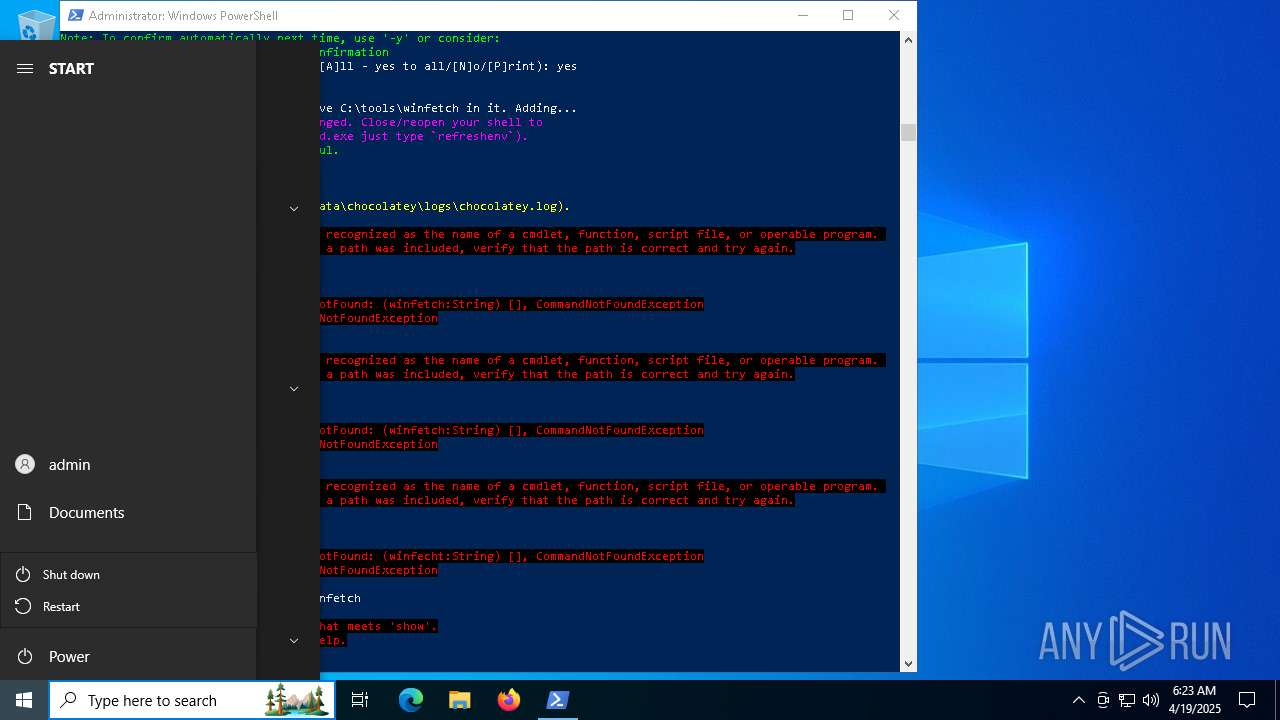
| File name: | MWFLAGIDK-ezgif.com-gif-maker.gif |
| Full analysis: | https://app.any.run/tasks/921e7f32-98f3-4e3e-a8c1-1a8a9716d530 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 06:19:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/gif |
| File info: | GIF image data, version 89a, 512 x 512 |
| MD5: | E83D22AE55D88D9F91837E654F8F30F3 |
| SHA1: | 98740061032B9B25B8BB87B96699259E2BA431AB |
| SHA256: | E172153E7BB84CB4BD5CDF364136F3EC98A5C46B734340D409C60BECC59F595A |
| SSDEEP: | 98304:/WqRMnBZR3riRwYevOci7zhk2mJlpFripjPFqwJUZ56Fio7BMhOTMHPVcoOEdM/7:3tuDn6 |
MALICIOUS
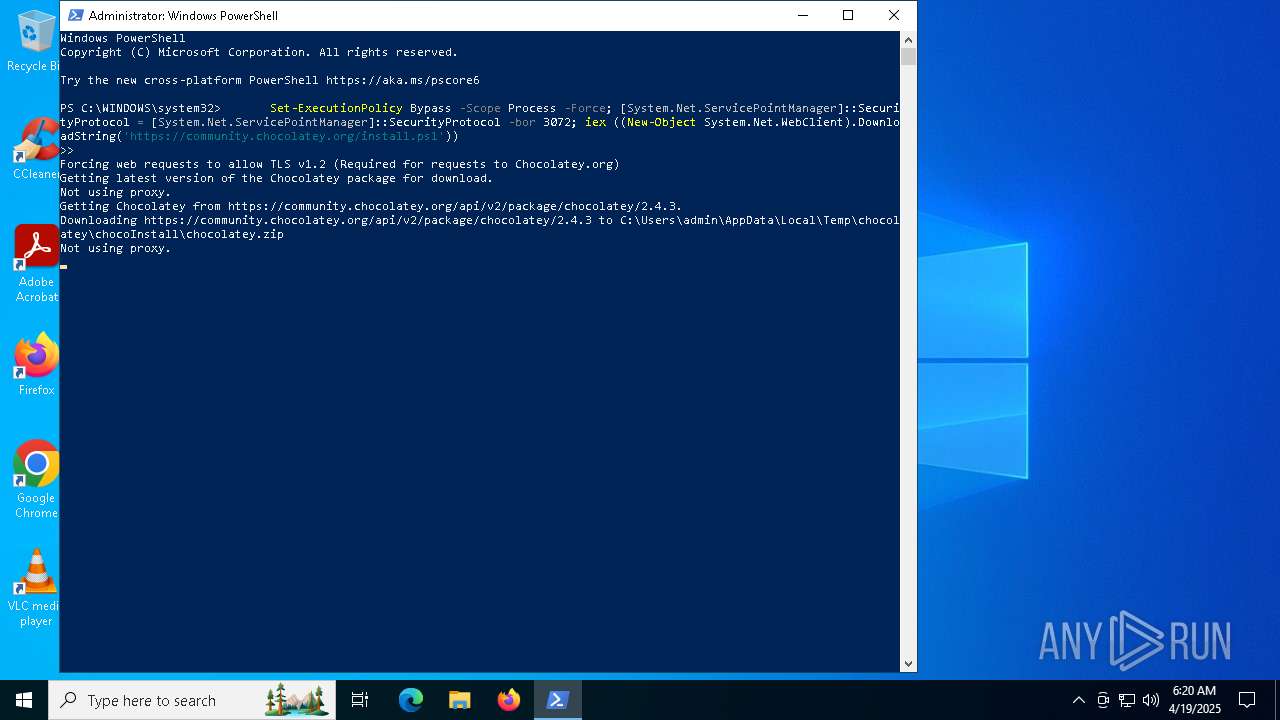
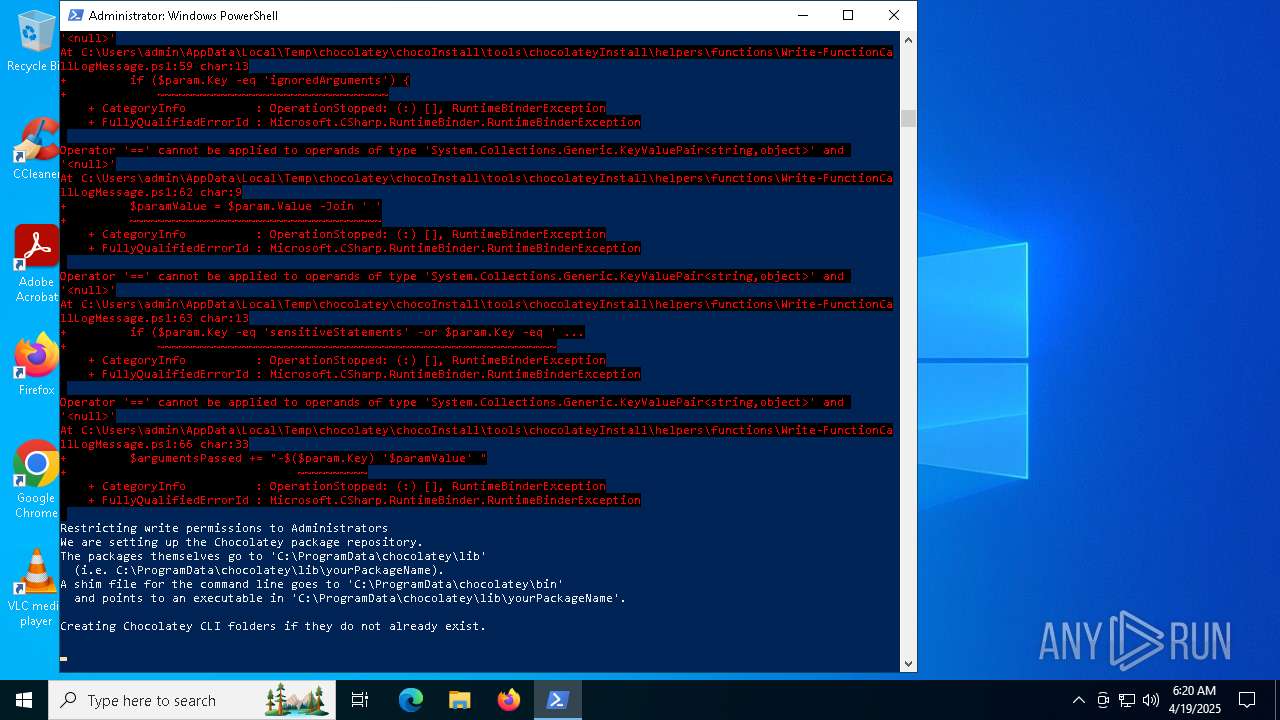
Script downloads file (POWERSHELL)
- powershell.exe (PID: 1672)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1672)
SUSPICIOUS
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1672)
- choco.exe (PID: 1328)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 1672)
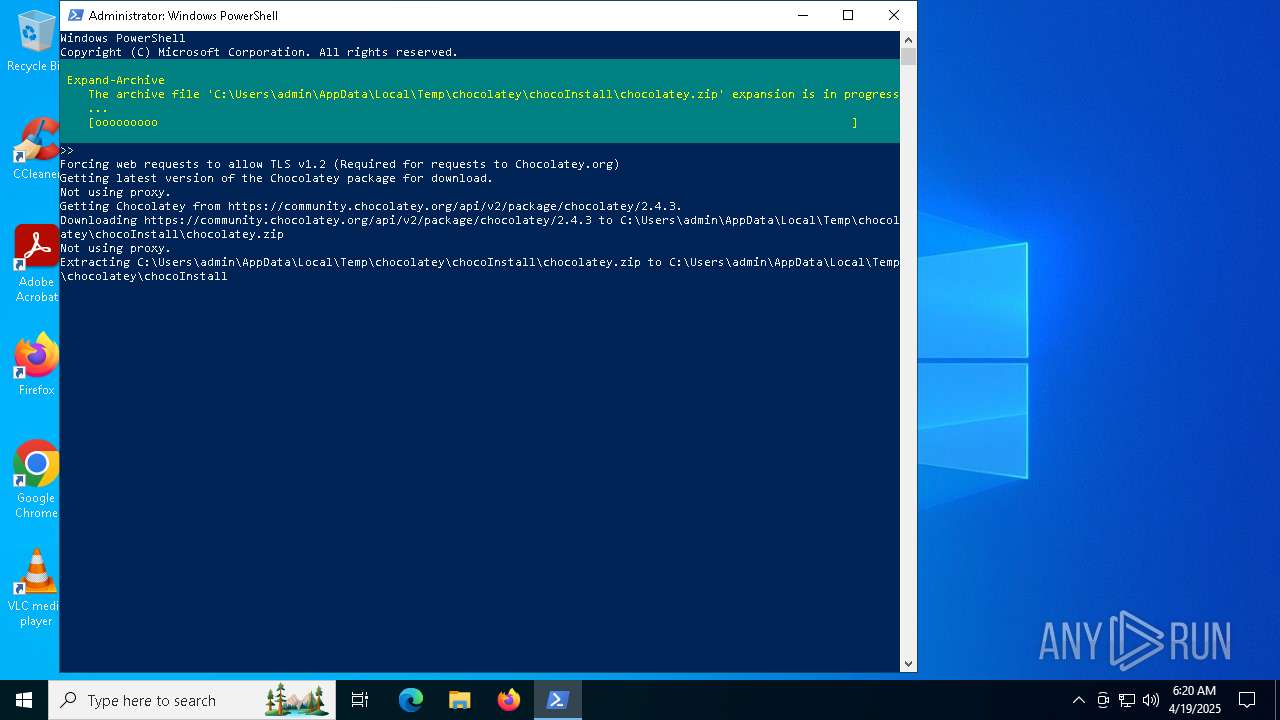
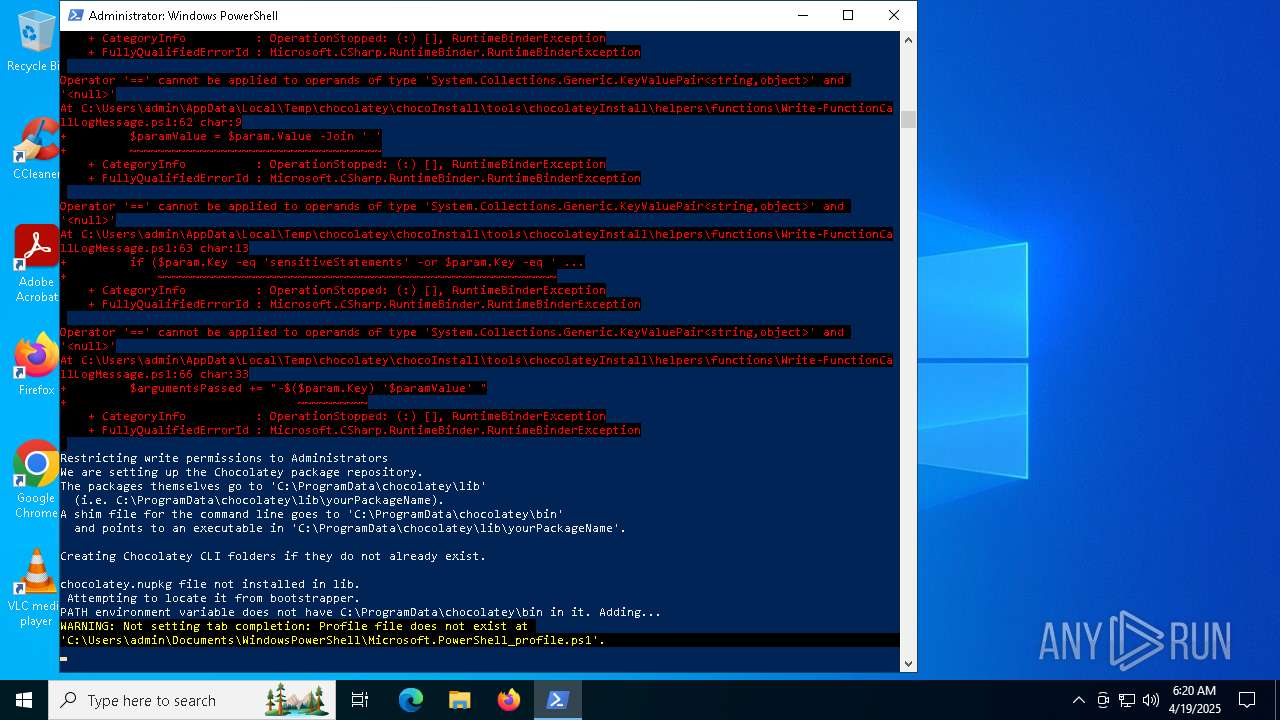
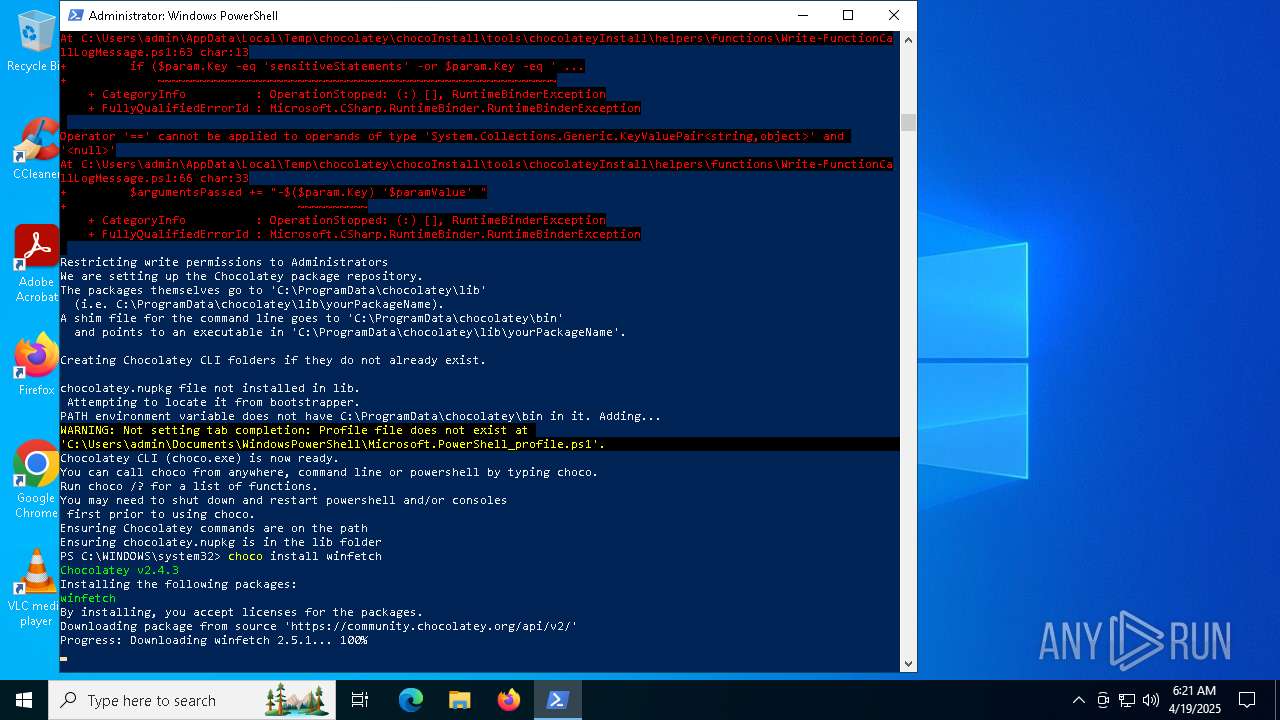
Drops 7-zip archiver for unpacking
- powershell.exe (PID: 1672)
Executable content was dropped or overwritten
- powershell.exe (PID: 1672)
The process creates files with name similar to system file names
- powershell.exe (PID: 1672)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 1672)
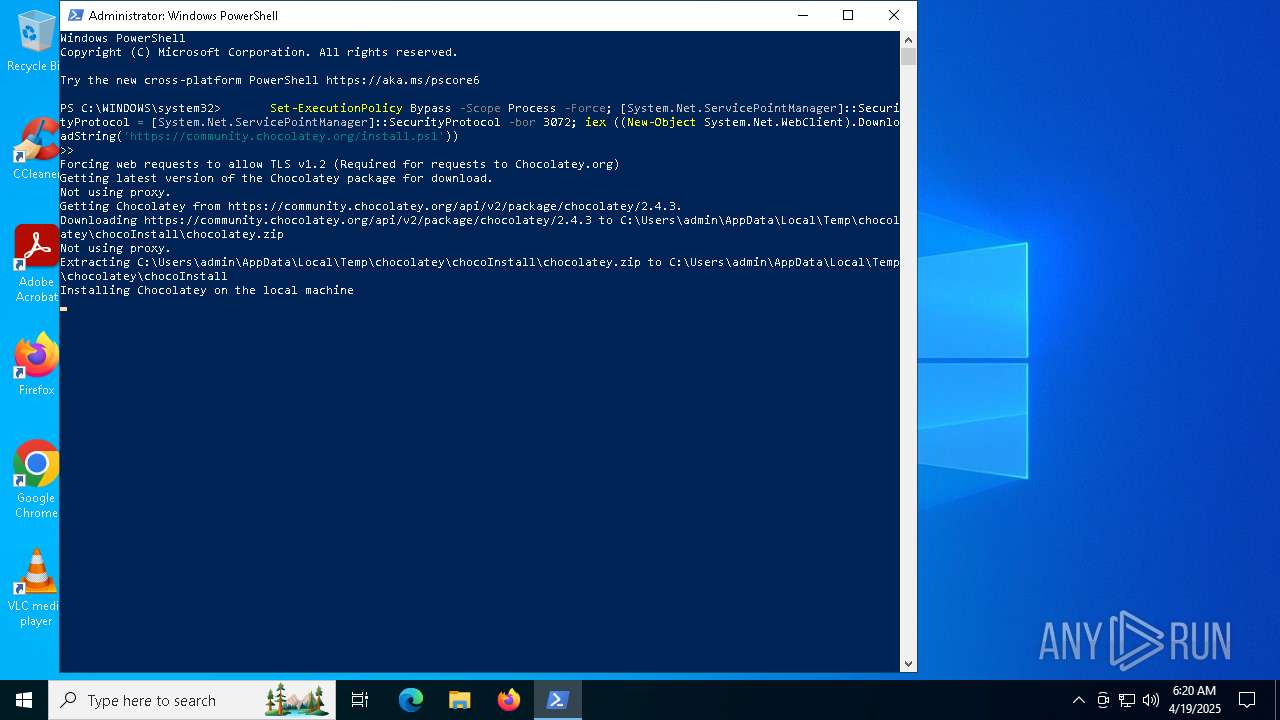
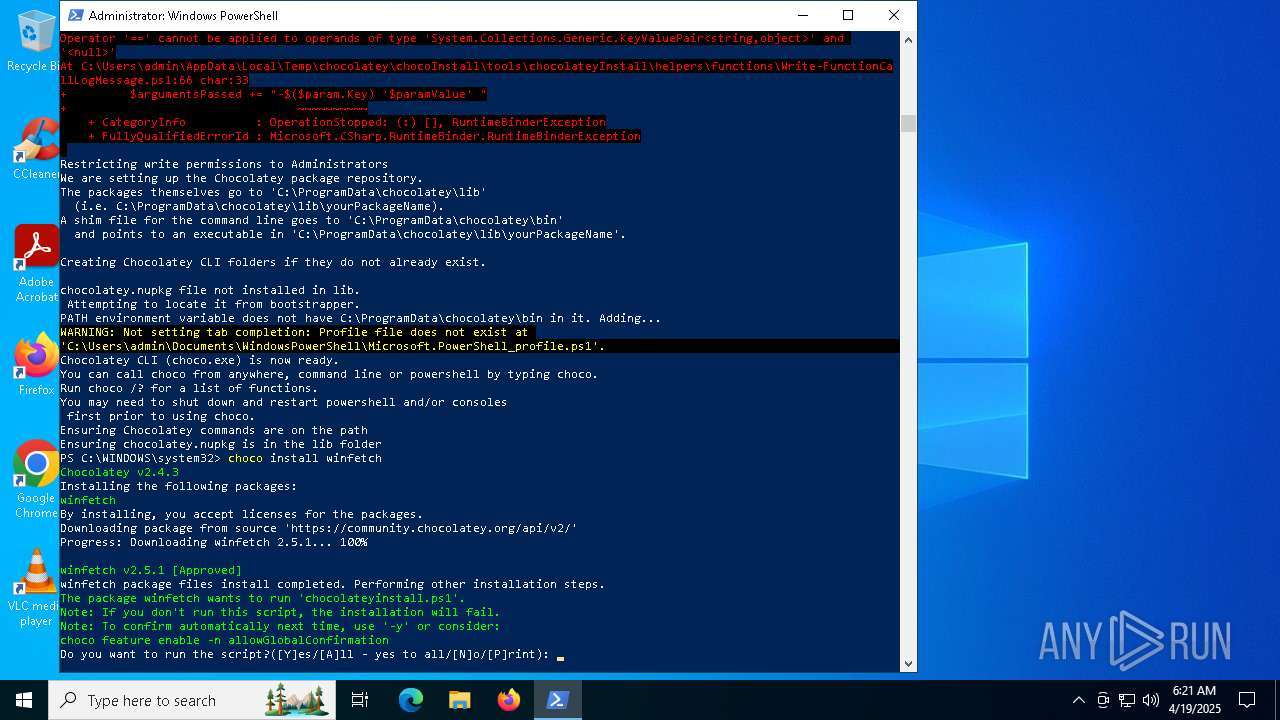
Creates a directory (POWERSHELL)
- powershell.exe (PID: 1672)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 1672)
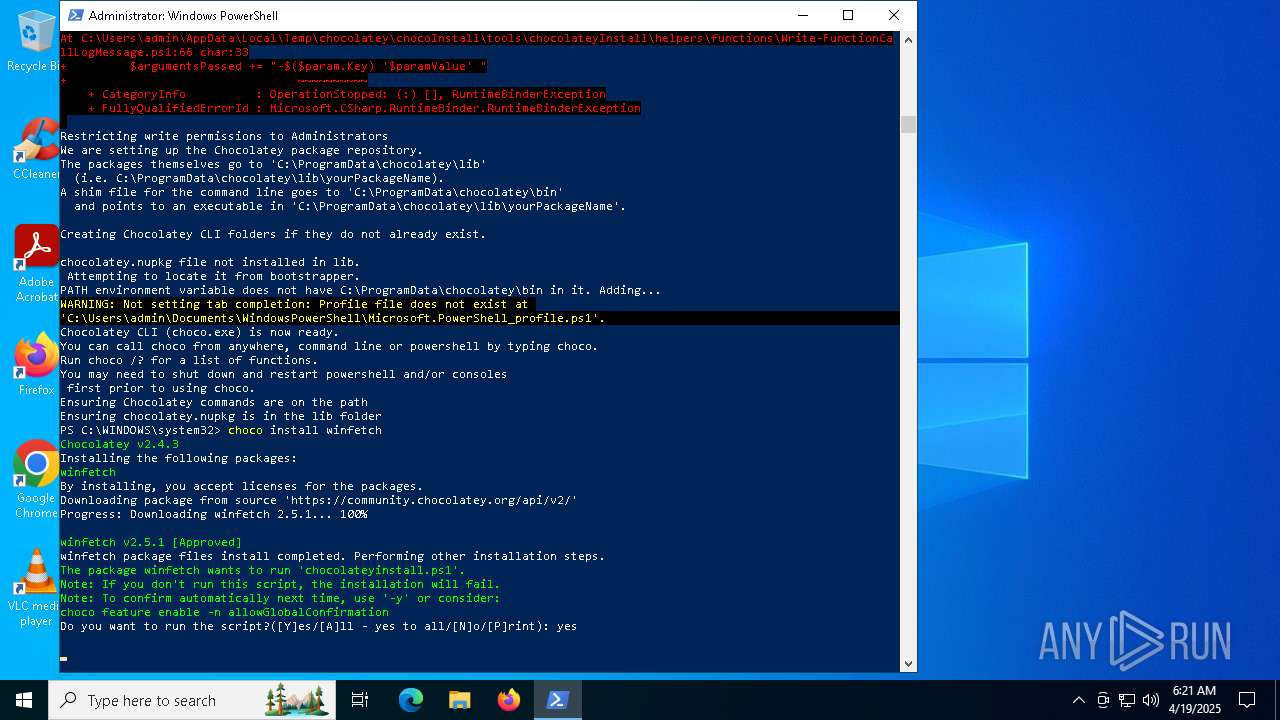
The system shut down or reboot
- choco.exe (PID: 1328)
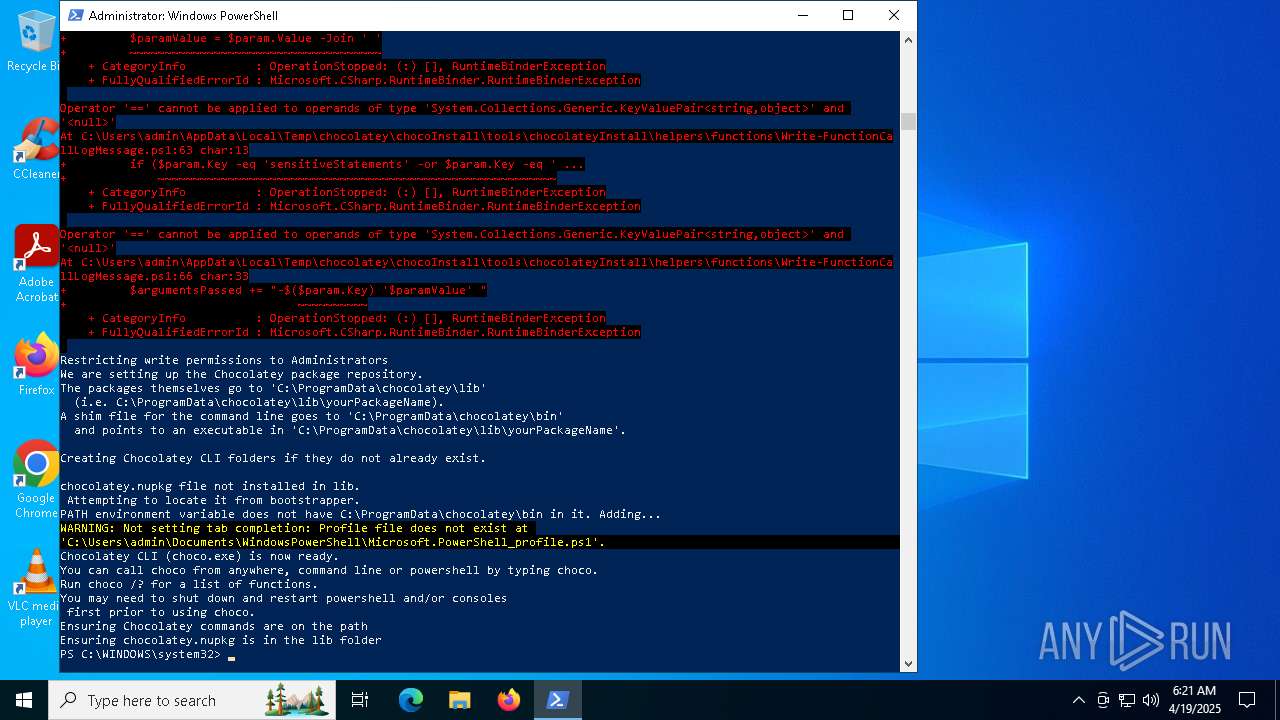
Searches for installed software
- choco.exe (PID: 1328)
Reads security settings of Internet Explorer
- choco.exe (PID: 1328)
INFO
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1672)
Manual execution by a user
- powershell.exe (PID: 1672)
Disables trace logs
- powershell.exe (PID: 1672)
- choco.exe (PID: 1328)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1672)
The sample compiled with english language support
- powershell.exe (PID: 1672)
Checks proxy server information
- powershell.exe (PID: 1672)
- choco.exe (PID: 1328)
- slui.exe (PID: 6576)
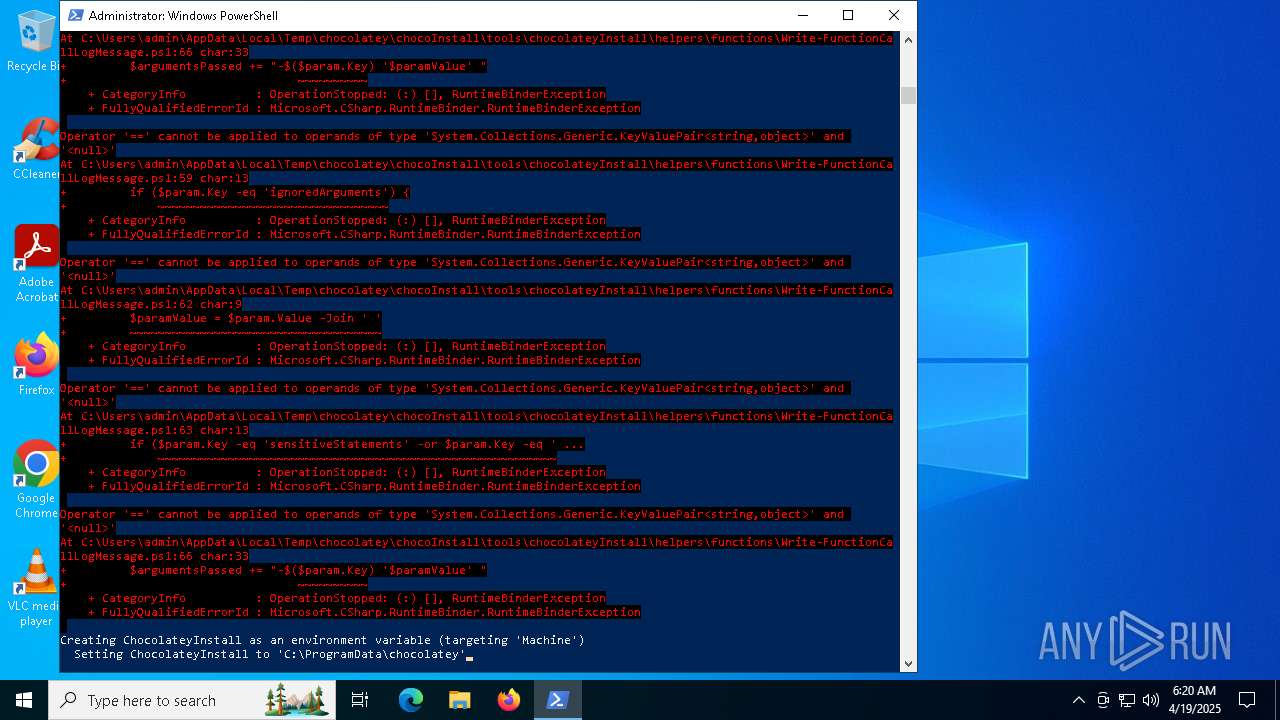
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1672)
Checks current location (POWERSHELL)
- powershell.exe (PID: 1672)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1672)
Creates files in the program directory
- powershell.exe (PID: 1672)
- choco.exe (PID: 1328)
- choco.exe (PID: 8068)
Reads the computer name
- choco.exe (PID: 8068)
- choco.exe (PID: 1328)
- choco.exe (PID: 5576)
- choco.exe (PID: 1228)
- choco.exe (PID: 7476)
Reads the machine GUID from the registry
- choco.exe (PID: 8068)
- choco.exe (PID: 1328)
- choco.exe (PID: 1228)
Reads Environment values
- choco.exe (PID: 1328)
- choco.exe (PID: 1228)
Checks supported languages
- choco.exe (PID: 5576)
- choco.exe (PID: 1328)
- choco.exe (PID: 8068)
- choco.exe (PID: 7476)
- choco.exe (PID: 1228)
Reads the software policy settings
- choco.exe (PID: 1328)
- slui.exe (PID: 7588)
- slui.exe (PID: 6576)
Create files in a temporary directory
- choco.exe (PID: 1328)
Process checks Powershell version
- choco.exe (PID: 1328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .gif | | | GIF animated bitmap (59.1) |
|---|---|---|
| .gif | | | GIF89a bitmap (24.4) |
| .gif | | | GIF bitmap (generic) (12.2) |
| .bs/bin | | | PrintFox (C64) bitmap (4) |
EXIF
GIF
| GIFVersion: | 89a |
|---|---|
| ImageWidth: | 512 |
| ImageHeight: | 512 |
| HasColorMap: | Yes |
| ColorResolutionDepth: | 1 |
| BitsPerPixel: | 1 |
| BackgroundColor: | - |
| AnimationIterations: | Infinite |
| TransparentColor: | - |
| FrameCount: | 181 |
| Duration: | 3.62 s |
Composite
| ImageSize: | 512x512 |
|---|---|
| Megapixels: | 0.262 |
Total processes
158
Monitored processes
19
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
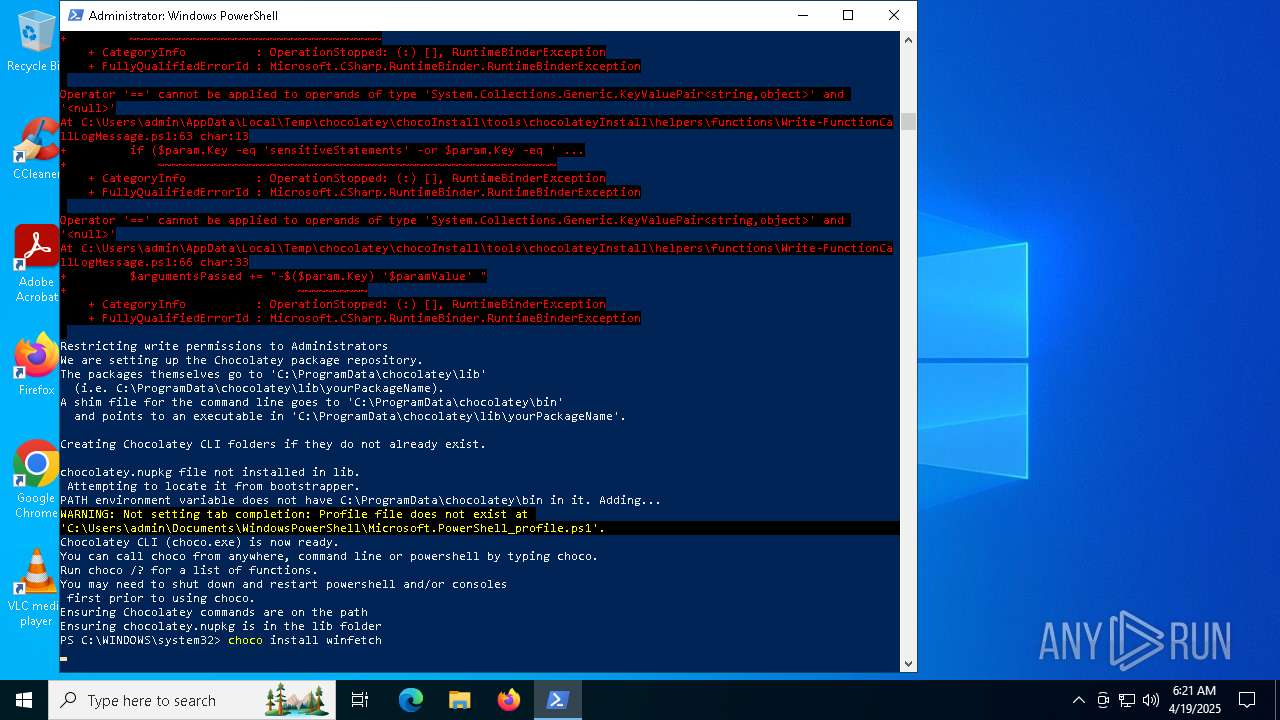
| 1228 | "C:\ProgramData\chocolatey\choco.exe" show winfetch | C:\ProgramData\chocolatey\choco.exe | — | choco.exe | |||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 1 Version: 2.4.3.0 Modules
| |||||||||||||||
| 1276 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\ProgramData\chocolatey\choco.exe" install winfetch | C:\ProgramData\chocolatey\choco.exe | choco.exe | ||||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: Exit code: 0 Version: 2.4.3.0 Modules
| |||||||||||||||
| 1672 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | "C:\WINDOWS\System32\setx.exe" ChocolateyLastPathUpdate 133895172902780322 | C:\Windows\System32\setx.exe | — | choco.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setx - Sets environment variables Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5084 | "C:\WINDOWS\System32\setx.exe" ChocolateyLastPathUpdate 133895172904967616 | C:\Windows\System32\setx.exe | — | choco.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setx - Sets environment variables Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | "C:\ProgramData\chocolatey\bin\choco.exe" install winfetch | C:\ProgramData\chocolatey\bin\choco.exe | — | powershell.exe | |||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: chocolatey - Chocolatey Shim Exit code: 0 Version: 0.12.1.0 Modules
| |||||||||||||||
| 6576 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7444 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\AppData\Local\Temp\MWFLAGIDK-ezgif.com-gif-maker.gif | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7476 | "C:\ProgramData\chocolatey\bin\choco.exe" show winfetch | C:\ProgramData\chocolatey\bin\choco.exe | — | powershell.exe | |||||||||||
User: admin Company: Chocolatey Software, Inc. Integrity Level: HIGH Description: chocolatey - Chocolatey Shim Exit code: 1 Version: 0.12.1.0 Modules
| |||||||||||||||
Total events
17 037
Read events
17 014
Write events
22
Delete events
1
Modification events
| (PID) Process: | (7444) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000033000000A00400007502000000000000 | |||
| (PID) Process: | (7744) setx.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | ChocolateyLastPathUpdate |
Value: 133895172584764320 | |||
| (PID) Process: | (1672) powershell.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | delete value | Name: | ChocolateyInstall |
Value: | |||
| (PID) Process: | (7980) setx.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | ChocolateyLastPathUpdate |
Value: 133895172579922137 | |||
| (PID) Process: | (7732) setx.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | ChocolateyLastPathUpdate |
Value: 133895172589298474 | |||
| (PID) Process: | (7696) setx.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | ChocolateyLastPathUpdate |
Value: 133895172598203153 | |||
| (PID) Process: | (1328) choco.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\choco_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1328) choco.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\choco_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1328) choco.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\choco_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1328) choco.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\choco_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
15
Suspicious files
10
Text files
148
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1672 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:17578B643AA4F26CBEF3D30558CC2B75 | SHA256:33CFDFF3112F6276F038AEEEABC1B71E99EBD9A20BF9F3B4332D572492254511 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\CREDITS.txt | text | |
MD5:2FDBAE8C0D612245A358336D15C76E70 | SHA256:CCA29EBA9D06E746B5ABECA46DD5864FE410A2D461F72820D093BEA792AF962A | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF110aab.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hpcx54dp.044.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5hw1lbm4.vhs.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4akexncq.lzq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\chocolatey.zip | compressed | |
MD5:BBC8DE02956827746E951C73BA6DABE5 | SHA256:D4998CA928A85A484507DCAA39C30948A6516DE0D1469B0511931D44A53456C3 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateysetup.psm1 | text | |
MD5:D082F6FA1357886CA99CFD9EB03FAA04 | SHA256:FB8E51208A641C5BEF628629BADAE9E3530A7D71495687BBA75EF88473C64026 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:9410E51238FAF1FC475B380A079D69EE | SHA256:6A36B5CD8E34D75FF08804326752DECFCED0F2158E9B537B84FBB89697E468B2 | |||
| 1672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\chocolatey.nuspec | xml | |
MD5:A4E0034972F8F29B70847FE6F04593DD | SHA256:B243F33B776F1E24492629350FBA09E0105A862B53CB5253852CF22A0023C4DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
38
DNS requests
20
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2924 | SearchApp.exe | 2.16.241.218:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2924 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1672 | powershell.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
1328 | choco.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |