| URL: | https://mega.nz/file/Y8IxRTiB#3KLJbP6amzNPoVppqed57cquDETmzCqjqyHRGMMbwzg |
| Full analysis: | https://app.any.run/tasks/19ce6f2b-db9f-4cb7-a9ee-3335a84def26 |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2025, 19:17:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | DA28B8B644340A66CEEEEE80F6D5825D |
| SHA1: | D09253B2807517C7245387A864F0EF25AF96EEC2 |
| SHA256: | E16E8192FB62833C19677A0A5640E2600857D16AF1C33ED6A8204C4496382F12 |
| SSDEEP: | 3:N8X/iU3xxWOBjnZOU9t3cHsC:2f3XWOBjnwQSMC |
MALICIOUS
Adds path to the Windows Defender exclusion list
- Mail Checker.exe (PID: 1812)
- QBFRMDZ.exe (PID: 7888)
- QBFRMDZ.exe (PID: 7816)
Changes Windows Defender settings
- Mail Checker.exe (PID: 1812)
- QBFRMDZ.exe (PID: 7888)
- QBFRMDZ.exe (PID: 7816)
Uses Task Scheduler to run other applications
- QBFRMDZ.exe (PID: 7888)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- Mail Checker.exe (PID: 1812)
- QBFRMDZ.exe (PID: 7888)
- QBFRMDZ.exe (PID: 7816)
Reads security settings of Internet Explorer
- Mail Checker.exe (PID: 8132)
- Mail Checker.exe (PID: 1812)
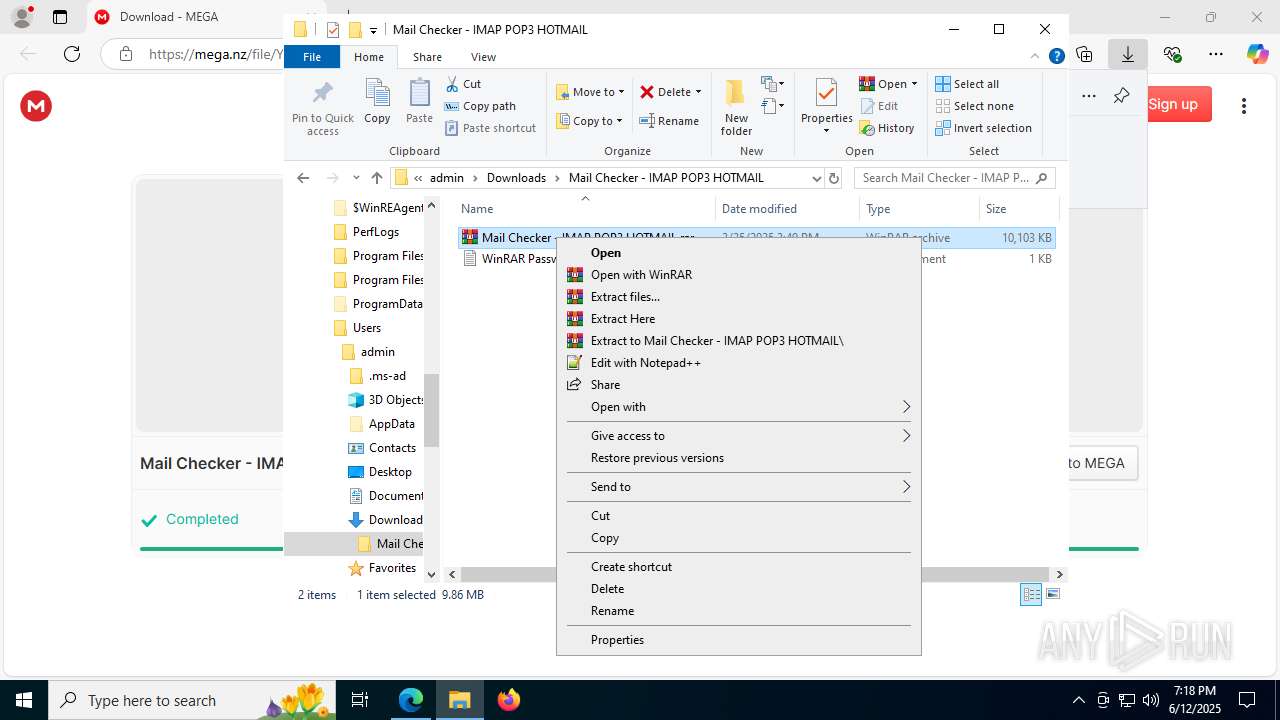
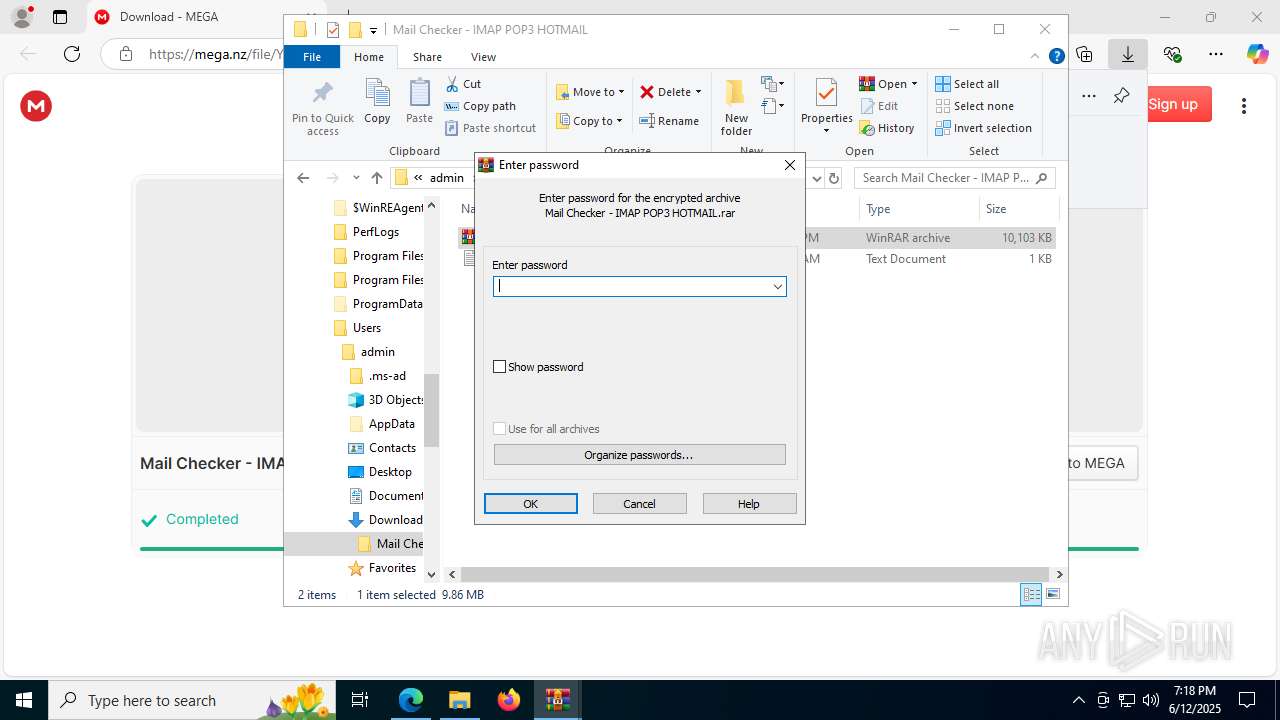
Process drops legitimate windows executable
- WinRAR.exe (PID: 8072)
Application launched itself
- Mail Checker.exe (PID: 8132)
Starts CMD.EXE for commands execution
- Mail Checker.exe (PID: 1812)
Found regular expressions for crypto-addresses (YARA)
- Mail Checker.exe (PID: 1812)
Executing commands from a ".bat" file
- Mail Checker.exe (PID: 1812)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7556)
Script adds exclusion path to Windows Defender
- QBFRMDZ.exe (PID: 7888)
- QBFRMDZ.exe (PID: 7816)
- Mail Checker.exe (PID: 1812)
The process executes via Task Scheduler
- QBFRMDZ.exe (PID: 7816)
INFO
Checks supported languages
- identity_helper.exe (PID: 7824)
- Mail Checker.exe (PID: 8132)
- Mail Checker.exe (PID: 1812)
Reads Environment values
- identity_helper.exe (PID: 7824)
Manual execution by a user
- WinRAR.exe (PID: 6492)
- WinRAR.exe (PID: 8072)
- Mail Checker.exe (PID: 8132)
Reads the computer name
- identity_helper.exe (PID: 7824)
- Mail Checker.exe (PID: 8132)
- Mail Checker.exe (PID: 1812)
Application launched itself
- msedge.exe (PID: 6936)
The sample compiled with english language support
- WinRAR.exe (PID: 8072)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8072)
Process checks computer location settings
- Mail Checker.exe (PID: 8132)
- Mail Checker.exe (PID: 1812)
UPX packer has been detected
- Mail Checker.exe (PID: 1812)
Creates files in the program directory
- Mail Checker.exe (PID: 1812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
193
Monitored processes
53
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6208,i,10859976601688358768,1477419228303681494,262144 --variations-seed-version --mojo-platform-channel-handle=6036 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
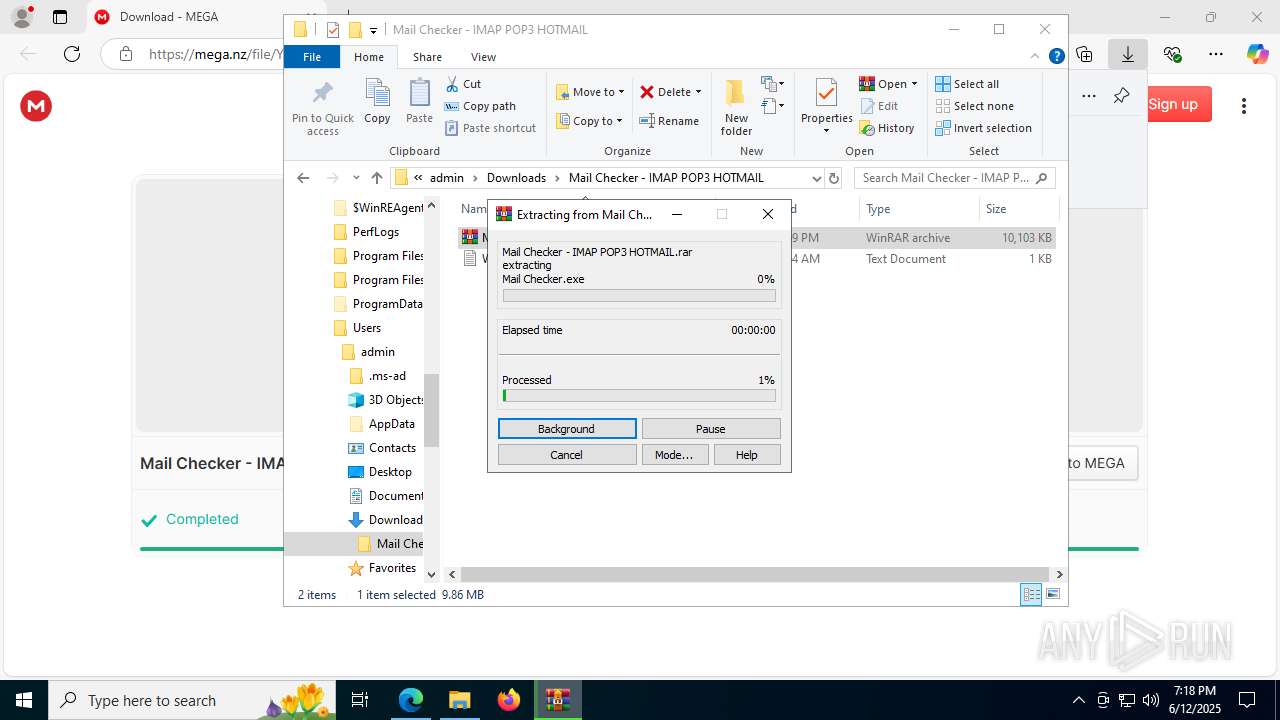
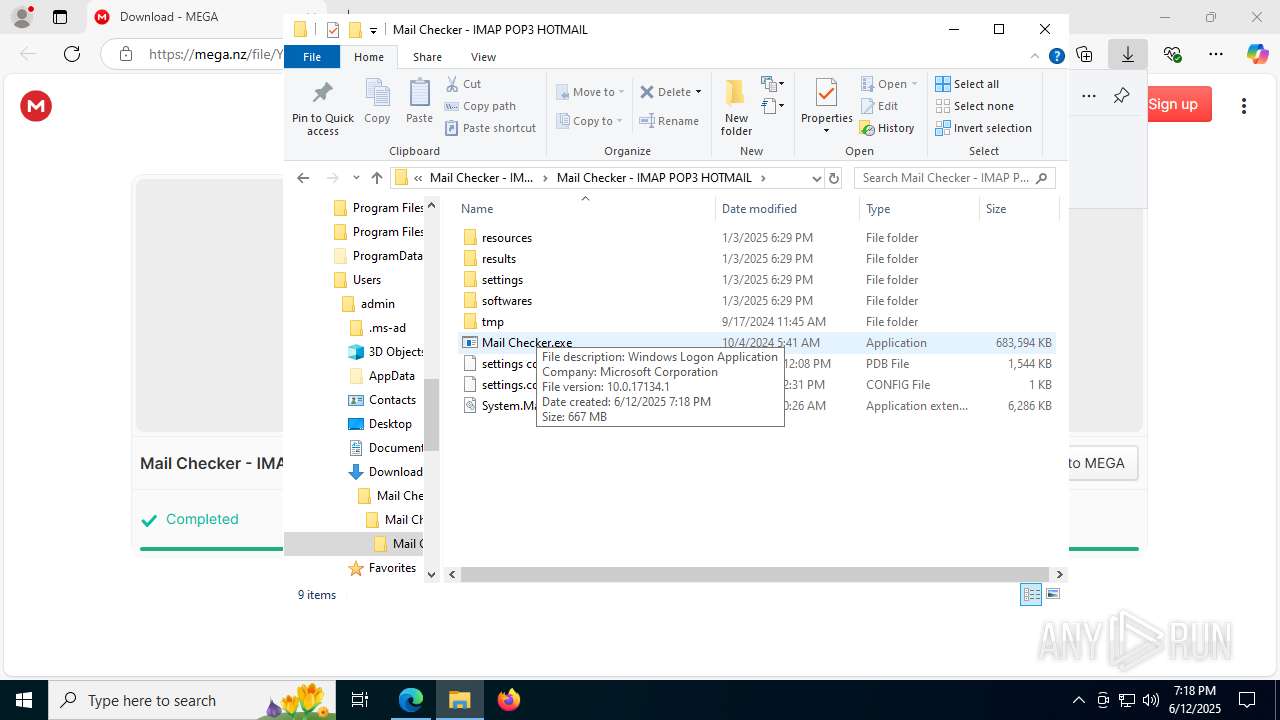
| 1812 | "C:\Users\admin\Downloads\Mail Checker - IMAP POP3 HOTMAIL\Mail Checker - IMAP POP3 HOTMAIL\Mail Checker - IMAP POP3 HOTMAIL\Mail Checker.exe" | C:\Users\admin\Downloads\Mail Checker - IMAP POP3 HOTMAIL\Mail Checker - IMAP POP3 HOTMAIL\Mail Checker - IMAP POP3 HOTMAIL\Mail Checker.exe | Mail Checker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 10.0.17134.1 Modules
| |||||||||||||||
| 1948 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x294,0x298,0x29c,0x28c,0x2a4,0x7ffc439ef208,0x7ffc439ef214,0x7ffc439ef220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5768,i,10859976601688358768,1477419228303681494,262144 --variations-seed-version --mojo-platform-channel-handle=5792 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2760 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3612,i,10859976601688358768,1477419228303681494,262144 --variations-seed-version --mojo-platform-channel-handle=3684 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3108 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=6636,i,10859976601688358768,1477419228303681494,262144 --variations-seed-version --mojo-platform-channel-handle=7548 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3724 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3668,i,10859976601688358768,1477419228303681494,262144 --variations-seed-version --mojo-platform-channel-handle=3792 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
40 441
Read events
40 380
Write events
57
Delete events
4
Modification events
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31185870 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
8
Suspicious files
267
Text files
174
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1764c5.TMP | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1764d4.TMP | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF176503.TMP | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF176503.TMP | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF176503.TMP | — | |
MD5:— | SHA256:— | |||
| 6936 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
113
DNS requests
77
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6532 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:aKwIlz4RZgh7655rtkqG_2B8t7JRNHDEhN1-8Bb8Bv8&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4476 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8052 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8052 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7156 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750016057&P2=404&P3=2&P4=iDE0m9zP81IlC49H0KAcblEioNzAVs4wzI1x3mvAzP8Hd95wtrsUeAJFC4oGu6TKzw%2fjvBib2H9sYniZ17uL7A%3d%3d | unknown | — | — | whitelisted |
7156 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750016057&P2=404&P3=2&P4=iDE0m9zP81IlC49H0KAcblEioNzAVs4wzI1x3mvAzP8Hd95wtrsUeAJFC4oGu6TKzw%2fjvBib2H9sYniZ17uL7A%3d%3d | unknown | — | — | whitelisted |
7156 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1750016058&P2=404&P3=2&P4=W873rbNIX4aje7aPgS0SDugJT4meDm4jhjV4eeusbuAMcl10KY6aK94UuI2BmKdm8DlqKlbG8Ntfg5OxXc2Blw%3d%3d | unknown | — | — | whitelisted |
7156 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750016057&P2=404&P3=2&P4=iDE0m9zP81IlC49H0KAcblEioNzAVs4wzI1x3mvAzP8Hd95wtrsUeAJFC4oGu6TKzw%2fjvBib2H9sYniZ17uL7A%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7052 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6532 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6532 | msedge.exe | 31.216.144.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | whitelisted |
6532 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6532 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6532 | msedge.exe | 2.16.204.153:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
mega.nz |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
eu.static.mega.co.nz |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
g.api.mega.co.nz |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6532 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |