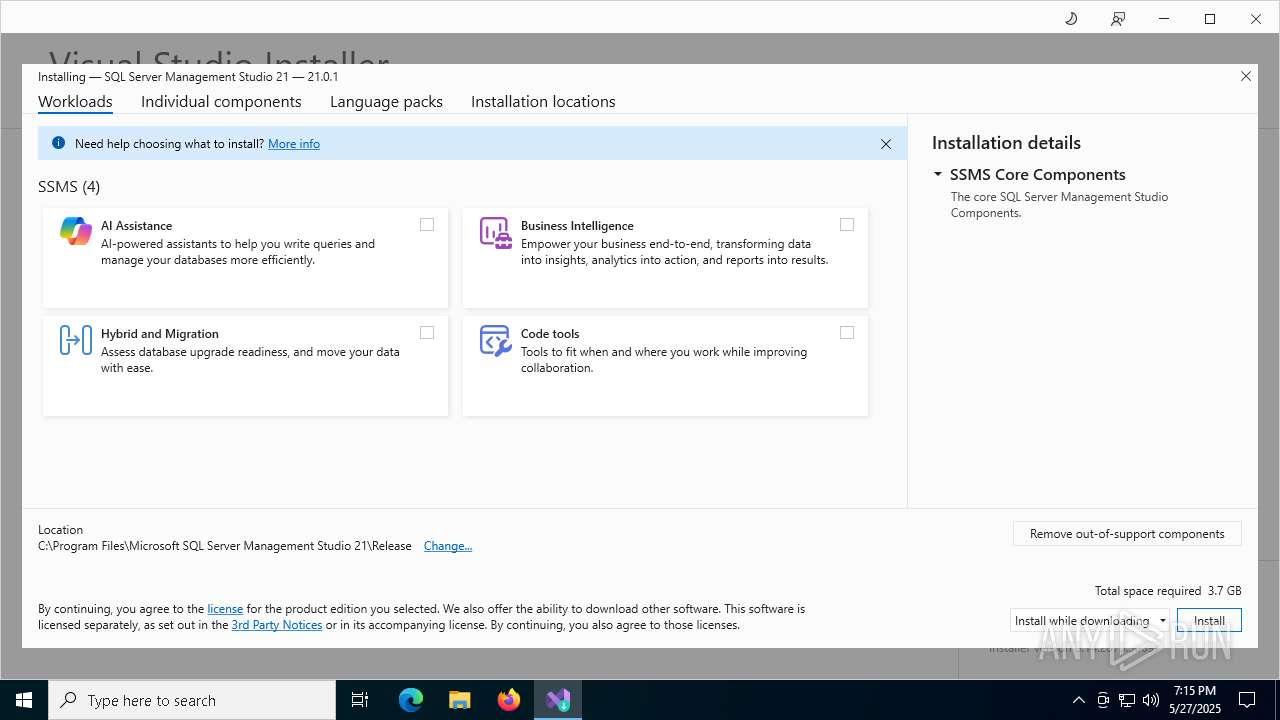
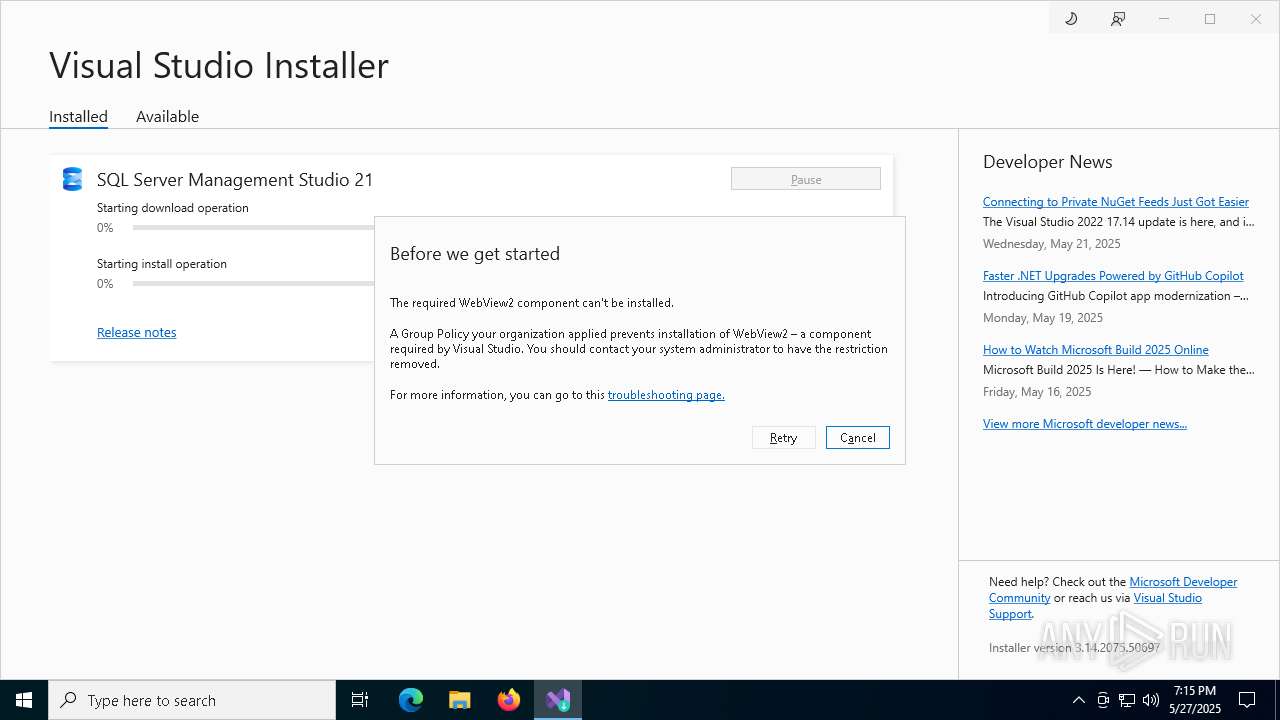
| File name: | vs_SSMS.exe |
| Full analysis: | https://app.any.run/tasks/1448c343-884b-437b-872f-984887fc6399 |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 19:14:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 88E46645EA2E0E6CBE58E1B9AF572679 |
| SHA1: | 520241C1D7D55E082A69F426158176E49C820A13 |
| SHA256: | E16B5EDA7E6EECAD858FAA89CABB3FD5F6B108B70F2FA18EB38FBBE3D679DD3D |
| SSDEEP: | 98304:pL263DSd27jP7ms0DBtXqlxNEBL/piSL23g/GHhRJO3QMIQ5r2SN7Sc4/AVBMEsZ:Hprt |
MALICIOUS
Changes powershell execution policy (Bypass)
- setup.exe (PID: 7212)
Bypass execution policy to execute commands
- powershell.exe (PID: 4188)
- powershell.exe (PID: 3956)
- powershell.exe (PID: 7656)
SUSPICIOUS
Starts a Microsoft application from unusual location
- vs_SSMS.exe (PID: 976)
Process drops legitimate windows executable
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
Executable content was dropped or overwritten
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7212)
Reads security settings of Internet Explorer
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
Found regular expressions for crypto-addresses (YARA)
- vs_setup_bootstrapper.exe (PID: 4776)
The process drops C-runtime libraries
- vs_setup_bootstrapper.exe (PID: 4776)
The process creates files with name similar to system file names
- vs_setup_bootstrapper.exe (PID: 4776)
Application launched itself
- setup.exe (PID: 7752)
Creates a software uninstall entry
- vs_installer.windows.exe (PID: 7948)
Searches for installed software
- vs_installer.windows.exe (PID: 7948)
Reads the date of Windows installation
- setup.exe (PID: 7752)
The process hide an interactive prompt from the user
- setup.exe (PID: 7212)
The process hides Powershell's copyright startup banner
- setup.exe (PID: 7212)
The process bypasses the loading of PowerShell profile settings
- setup.exe (PID: 7212)
The process executes Powershell scripts
- setup.exe (PID: 7212)
Starts POWERSHELL.EXE for commands execution
- setup.exe (PID: 7212)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2772)
INFO
Checks supported languages
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- vs_installer.windows.exe (PID: 7948)
- setup.exe (PID: 7212)
- msiexec.exe (PID: 2772)
The sample compiled with english language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with Italian language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
Reads the machine GUID from the registry
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
- msiexec.exe (PID: 2772)
Reads the computer name
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- vs_installer.windows.exe (PID: 7948)
- setup.exe (PID: 7212)
- msiexec.exe (PID: 2772)
The sample compiled with chinese language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with portuguese language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with spanish language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with czech language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with german language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with french language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with korean language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with polish language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
Create files in a temporary directory
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 7656)
- powershell.exe (PID: 3956)
The sample compiled with russian language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with turkish language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
The sample compiled with japanese language support
- vs_SSMS.exe (PID: 976)
- vs_setup_bootstrapper.exe (PID: 4776)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 1324)
Checks proxy server information
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
Reads CPU info
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
Process checks computer location settings
- vs_SSMS.exe (PID: 976)
- setup.exe (PID: 7752)
Creates files in the program directory
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
Reads the software policy settings
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
- msiexec.exe (PID: 2772)
- powershell.exe (PID: 4188)
- slui.exe (PID: 4696)
- powershell.exe (PID: 3956)
- powershell.exe (PID: 7656)
Creates files or folders in the user directory
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
Disables trace logs
- vs_setup_bootstrapper.exe (PID: 4776)
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
Reads Environment values
- setup.exe (PID: 7752)
- setup.exe (PID: 7212)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2772)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4188)
- powershell.exe (PID: 3956)
- powershell.exe (PID: 7656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:25 17:46:24+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 229376 |
| InitializedDataSize: | 199680 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e090 |
| OSVersion: | 5.1 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.14.36119.2 |
| ProductVersionNumber: | 17.14.36119.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | SSMS Installer |
| FileVersion: | 17.14.36119.2 |
| InternalName: | vs_ssms.exe |
| OriginalFileName: | vs_ssms.exe |
| ProductName: | Microsoft SQL Server Management Studio |
| ProductVersion: | 21.0.1 |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
Total processes
149
Monitored processes
18
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 976 | "C:\Users\admin\AppData\Local\Temp\vs_SSMS.exe" | C:\Users\admin\AppData\Local\Temp\vs_SSMS.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: SSMS Installer Exit code: 0 Version: 17.14.36119.2 Modules
| |||||||||||||||
| 1324 | "getmac" | C:\Windows\SysWOW64\getmac.exe | — | vs_setup_bootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Displays NIC MAC information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3956 | "C:\WINDOWS\SysWOW64\\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -NoLogo -NoProfile -Noninteractive -File "C:\Program Files (x86)\Microsoft Visual Studio\Installer\PrecheckTools\Microsoft.VisualStudio.Setup.TestPowerShell.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4188 | "C:\WINDOWS\SysWOW64\\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -NoLogo -NoProfile -Noninteractive -File "C:\Program Files (x86)\Microsoft Visual Studio\Installer\PrecheckTools\Microsoft.VisualStudio.Setup.TestPowerShell.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4696 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
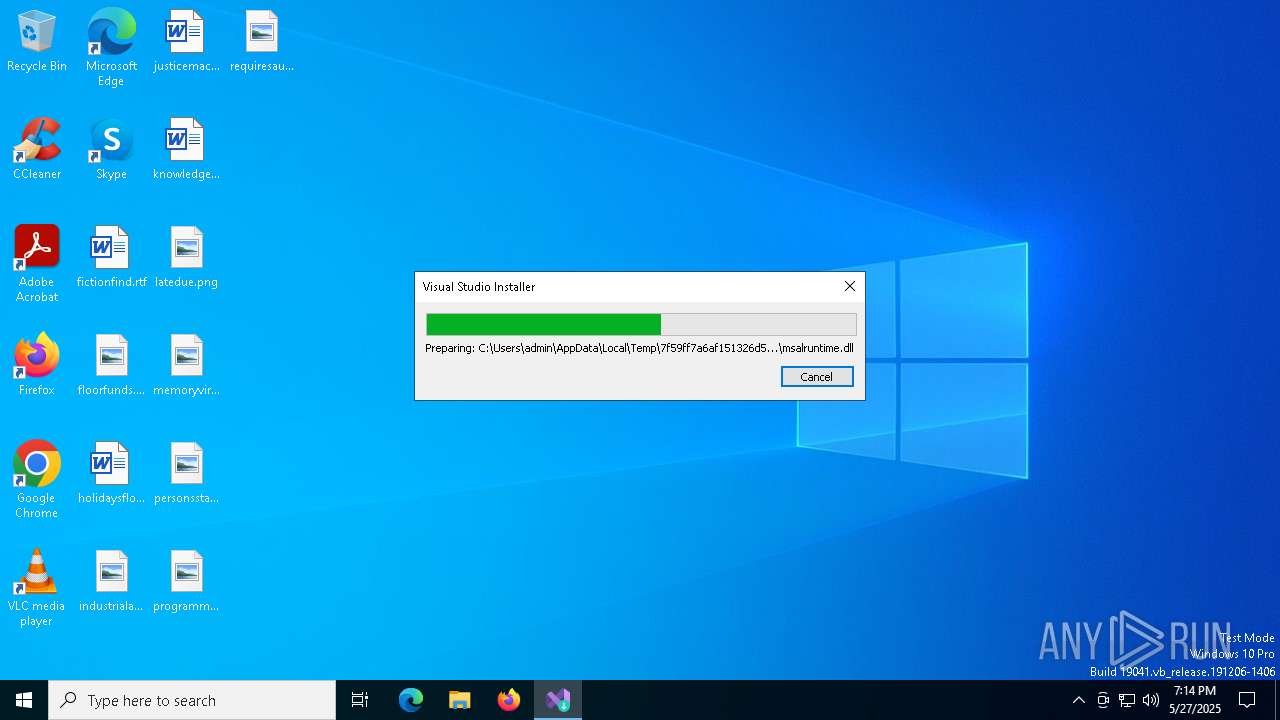
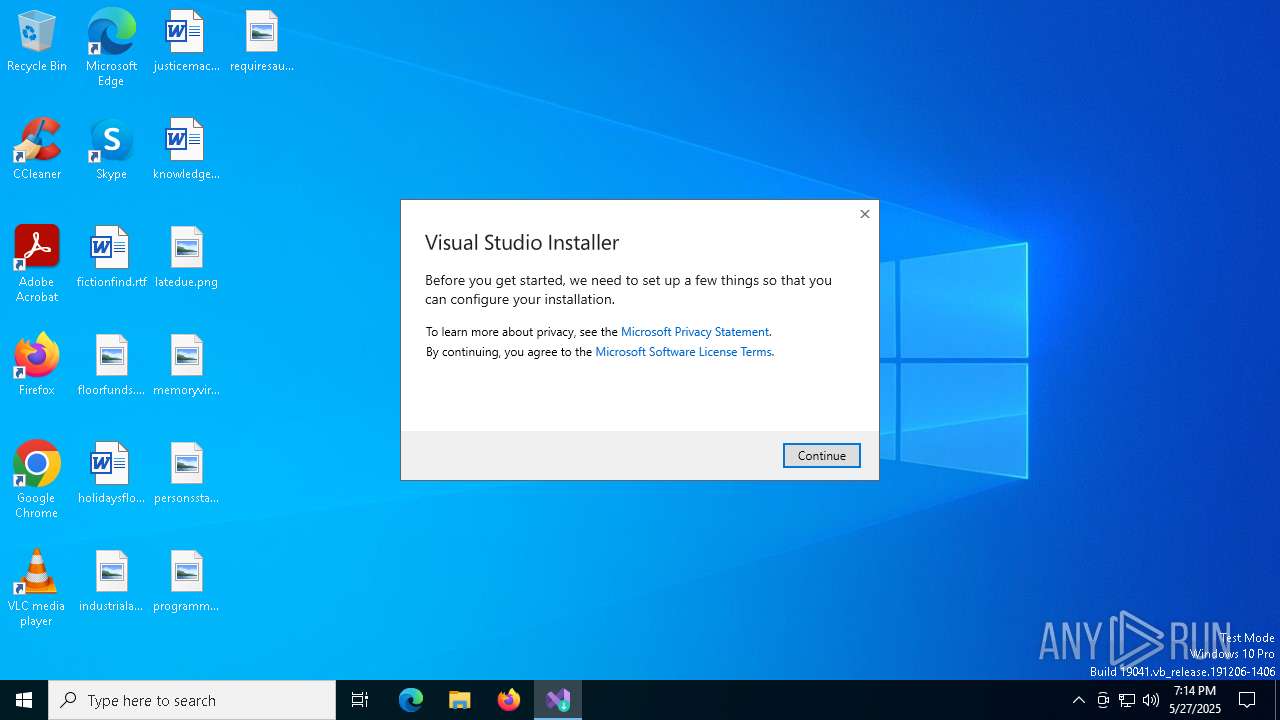
| 4776 | "C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\vs_setup_bootstrapper.exe" --env "_SFX_CAB_EXE_PACKAGE:C:\Users\admin\AppData\Local\Temp\vs_SSMS.exe _SFX_CAB_EXE_ORIGINALWORKINGDIR:C:\Users\admin\AppData\Local\Temp" | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\vs_setup_bootstrapper.exe | vs_SSMS.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Visual Studio Installer Exit code: 0 Version: 3.14.2075.50697 Modules
| |||||||||||||||
| 5332 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | getmac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 347
Read events
36 077
Write events
197
Delete events
73
Modification events
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DeveloperTools\HardwareCache |
| Operation: | write | Name: | Uuid |
Value: 1d1fb0bb-21b9-4fc0-b017-a4dada231e17 | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DeveloperTools\HardwareCache |
| Operation: | write | Name: | MachineGuid |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DeveloperTools\HardwareCache |
| Operation: | write | Name: | HardDriveSerialNumber |
Value: qm00001 | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\vs_setup_bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\vs_setup_bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\vs_setup_bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\vs_setup_bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\vs_setup_bootstrapper_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\vs_setup_bootstrapper_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4776) vs_setup_bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\vs_setup_bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
447
Suspicious files
67
Text files
106
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\HelpFile\1055\help.html | html | |
MD5:C7B60E697671394781260D5B2CD21810 | SHA256:CCF766B55CB0CC623F2705206A2AF04F2C83801580BC40A5AC20F644B814AB8F | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\HelpFile\2052\help.html | html | |
MD5:1BD86FBD65D005648103E050D9BEB9F1 | SHA256:740117157B31BD5C634A232A0BA98A692B28ED2B4829EF52372200EB547D07CF | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\HelpFile\1029\help.html | html | |
MD5:432E50F4764D69625E5143571F823B6A | SHA256:C877FE7CD9544369A42A61B5C51264D74BFCA5B4BC5D4DD1FA703428261D6ABC | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\HelpFile\1028\help.html | html | |
MD5:EEAF8CBF54B4E891FF6BE38CF44E3814 | SHA256:AAD5B2ACF30EB9C2DD35FF3B5C6C1A76CC4F1AE0AB6F382A635F5C329439F3AF | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\HelpFile\1046\help.html | html | |
MD5:C2BDEAA46B13E3CDE01E3DCAA734C0F2 | SHA256:5A0802D6CA8D63D8476EEC79BDBD6079A17DC149D5D8C7DF13059D47BBB09F3A | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\Microsoft.C2RSignatureReader.Interop.dll | executable | |
MD5:CF7B7683ED3882C249894EA21AB97809 | SHA256:8ADD7C3474243F310828B7BA15D7498BDE97B66F51BC000B804D3A0142800F5E | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\Microsoft.Identity.Client.Broker.dll | executable | |
MD5:0616C47711CD8E496DE1CDF7A37DCED9 | SHA256:2F8F83D478736EDDF80D531B5772AF61D4F70FBFADA671C9EC3D16E1CEBD7EF3 | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\vs_setup_bootstrapper.exe | executable | |
MD5:74DD072F6E323C91AAFDD0F48F0D09A4 | SHA256:09DE373135CF94E0773517BEC0E6E48002034E55E381567EBE362AAAB4A281F8 | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\HelpFile\1033\help.html | html | |
MD5:4F7415E811ACBDDED478B40C3E7B287E | SHA256:55846D86DBE60B1B663018D72BEFA0F53A61D34A4EB093563B93A41B2FAA34A5 | |||
| 976 | vs_SSMS.exe | C:\Users\admin\AppData\Local\Temp\7f59ff7a6af151326d5ffc5822da6578\vs_bootstrapper_d15\HelpFile\1031\help.html | html | |
MD5:6F489A55562732D253AD828581176A9A | SHA256:9502AC0910BCEE0EB3123F7B68A605D71C8DF72FE7B33F4173AFB4A01390581A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
56
DNS requests
37
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4776 | vs_setup_bootstrapper.exe | GET | 200 | 23.48.23.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4776 | vs_setup_bootstrapper.exe | GET | 200 | 23.48.23.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4776 | vs_setup_bootstrapper.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
4776 | vs_setup_bootstrapper.exe | GET | 200 | 23.48.23.172:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7648 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4776 | vs_setup_bootstrapper.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
7648 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.162:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4776 | vs_setup_bootstrapper.exe | 23.50.131.198:443 | telemetry.visualstudio.microsoft.com | Akamai International B.V. | DE | whitelisted |
4776 | vs_setup_bootstrapper.exe | 95.100.186.9:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
4776 | vs_setup_bootstrapper.exe | 20.42.128.98:443 | targetednotifications-tm.trafficmanager.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
telemetry.visualstudio.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings.visualstudio.microsoft.com |
| whitelisted |
targetednotifications-tm.trafficmanager.net |
| whitelisted |
login.live.com |
| whitelisted |