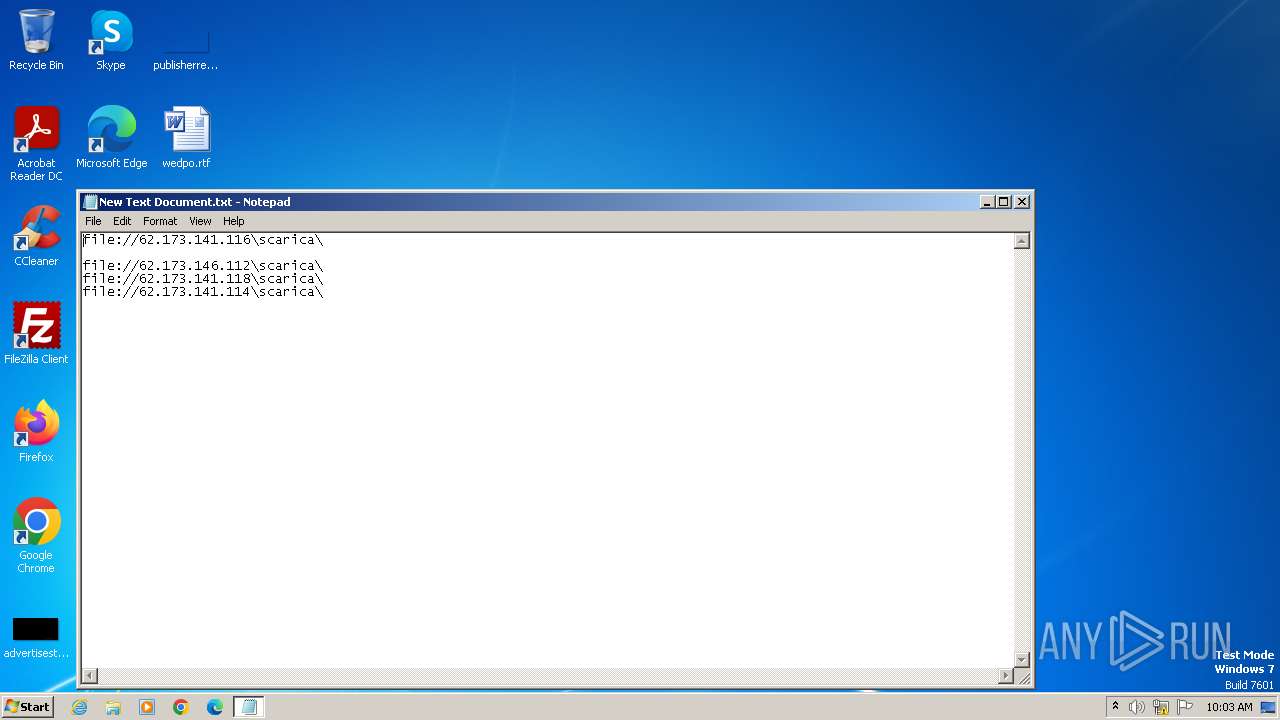
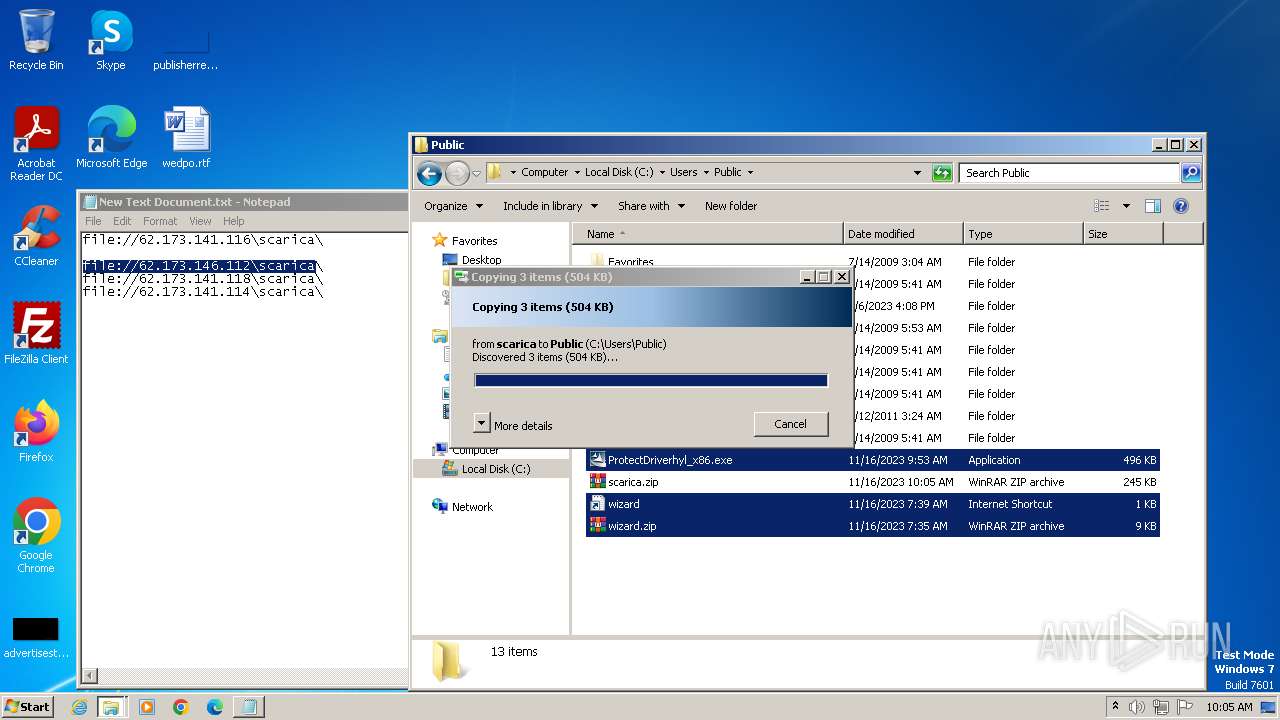
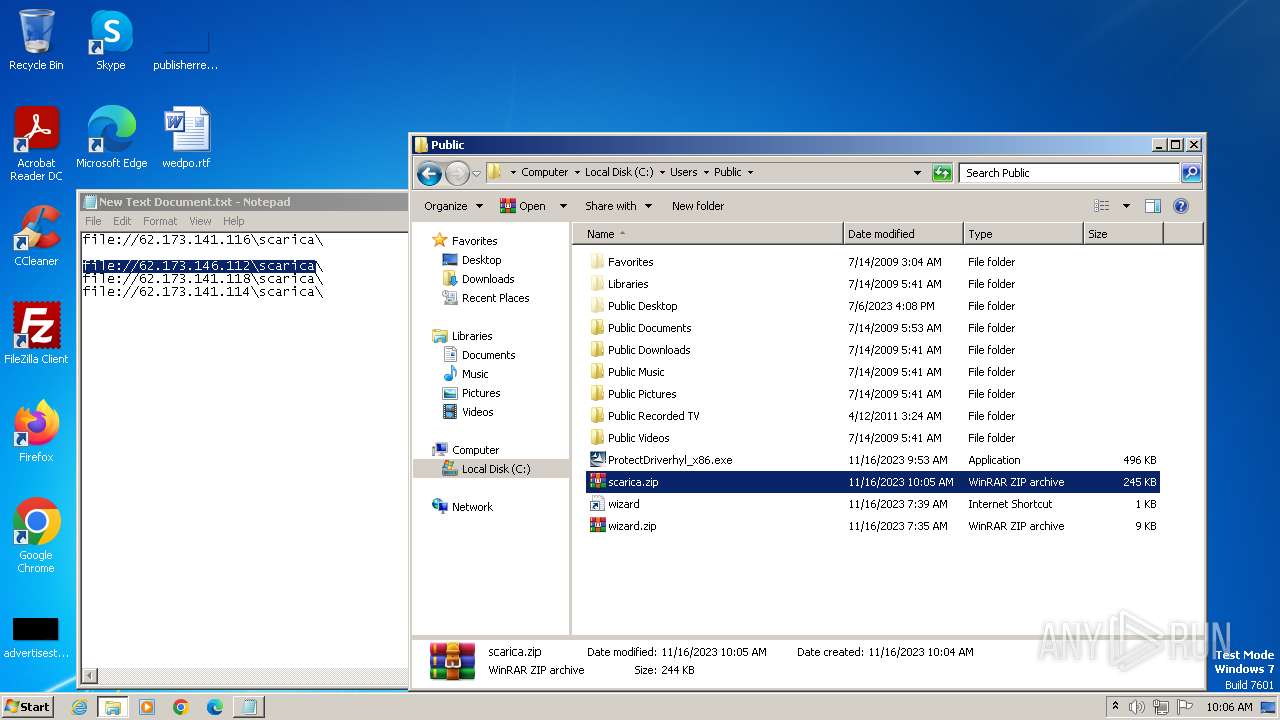
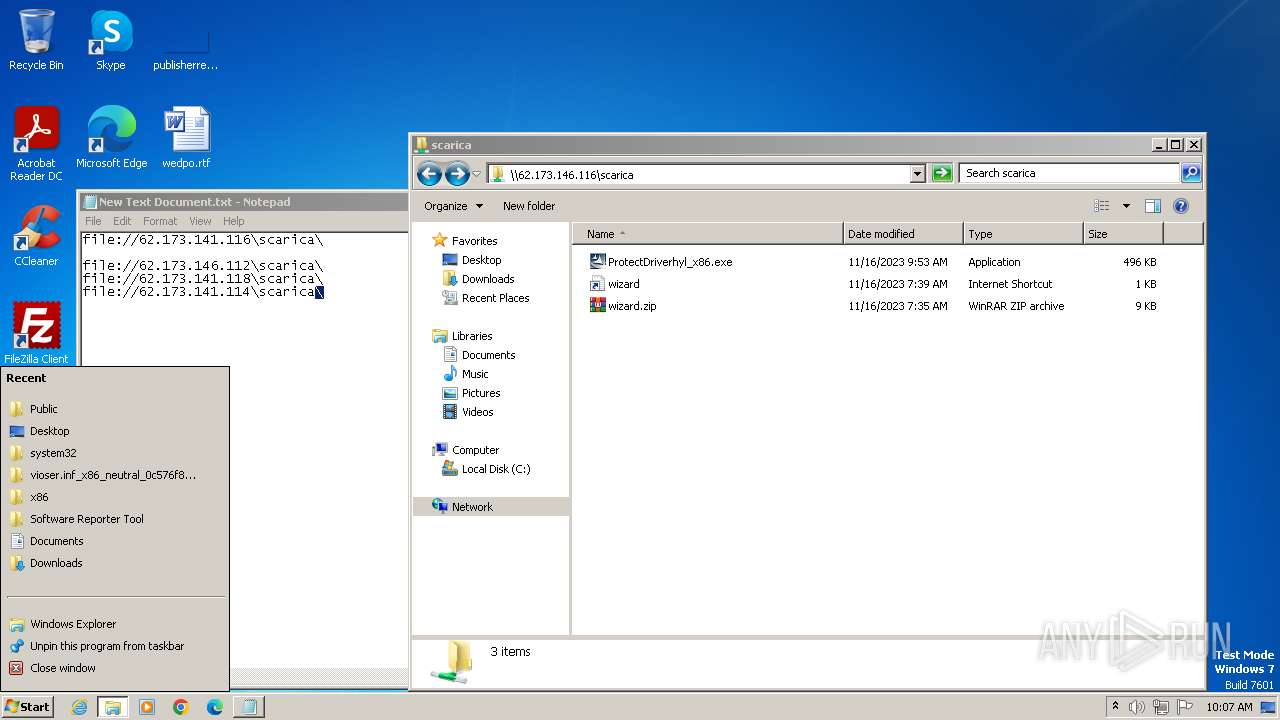
| File name: | New Text Document.txt |
| Full analysis: | https://app.any.run/tasks/d34107b8-ce64-480b-acc0-662e4a036d93 |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2023, 10:03:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | A5F0ECB757E162E61AD44F8873195277 |
| SHA1: | B11C2B97F16DD82A4C2184D2EC26AA5217BD5F2A |
| SHA256: | E154ABC6729964524C8C54FB0A4B6E9F4546F7FF20CEC05304335C0AD38F0989 |
| SSDEEP: | 3:xiwUlL5WGxr0wUlQFITc1QM/wUlFI8QM/wUlJ7z1n:xiwC7xr0wdAAQM/wMNQM/wA7xn |
MALICIOUS
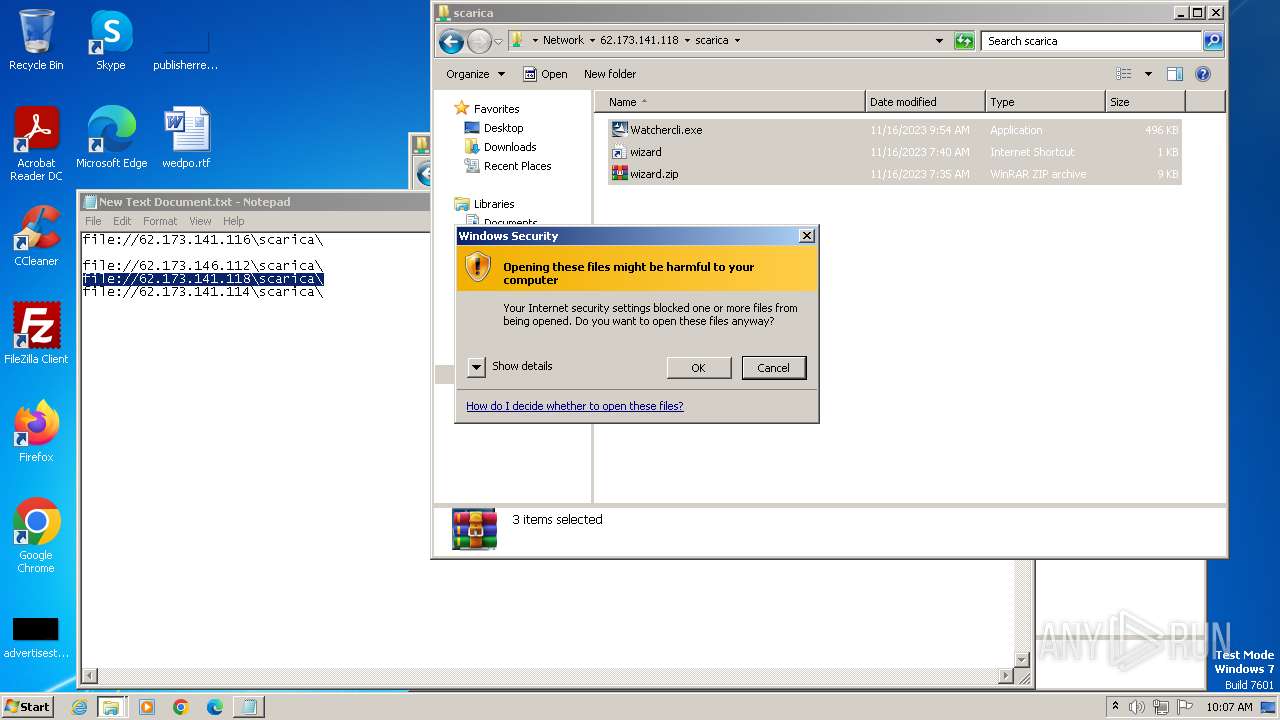
No malicious indicators.SUSPICIOUS
SMB connection has been detected (probably for file transfer)
- explorer.exe (PID: 1388)
Uses pipe srvsvc via SMB (transferring data)
- WinRAR.exe (PID: 4016)
- explorer.exe (PID: 1388)
Application launched itself
- explorer.exe (PID: 1388)
INFO
Manual execution by a user
- explorer.exe (PID: 3432)
- WinRAR.exe (PID: 4016)
- wmpnscfg.exe (PID: 3472)
- WinRAR.exe (PID: 1008)
Checks supported languages
- wmpnscfg.exe (PID: 3472)
Reads the computer name
- wmpnscfg.exe (PID: 3472)
Reads the Internet Settings
- explorer.exe (PID: 1388)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3472)
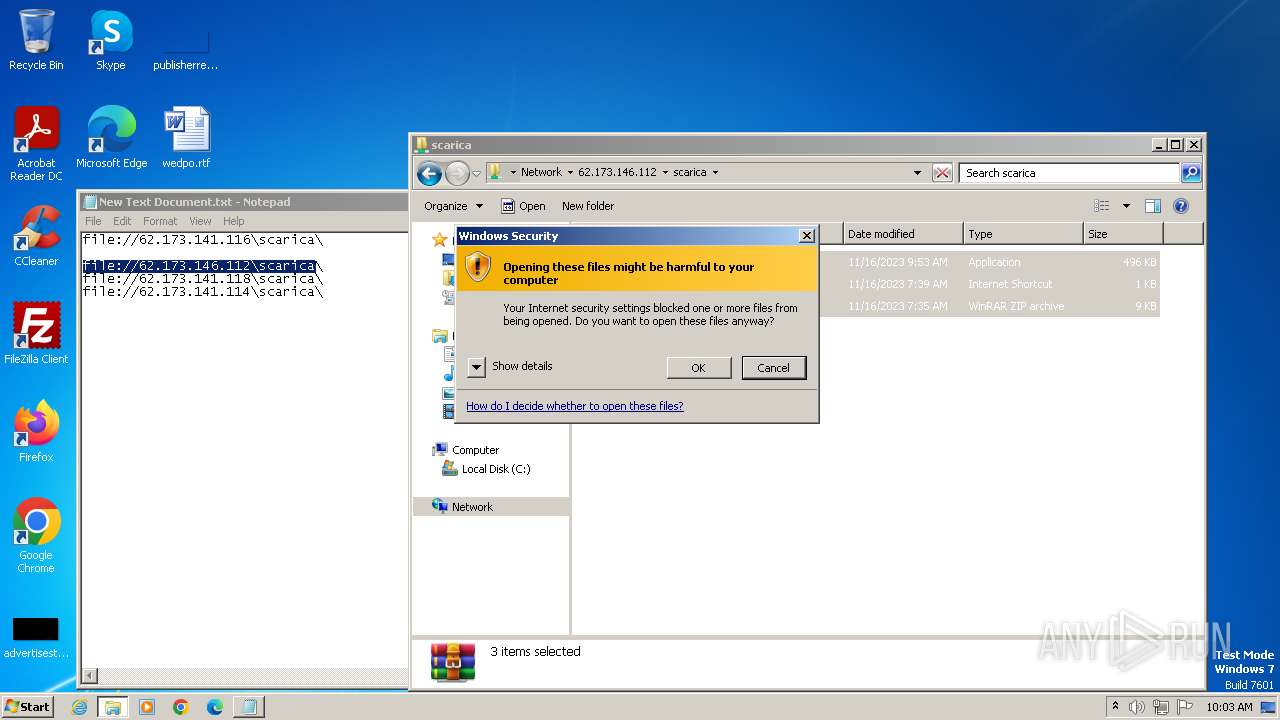
Drops the executable file immediately after the start
- explorer.exe (PID: 1388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1008 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\Public\scarica.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1388 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3252 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3428 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\New Text Document.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3432 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3472 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
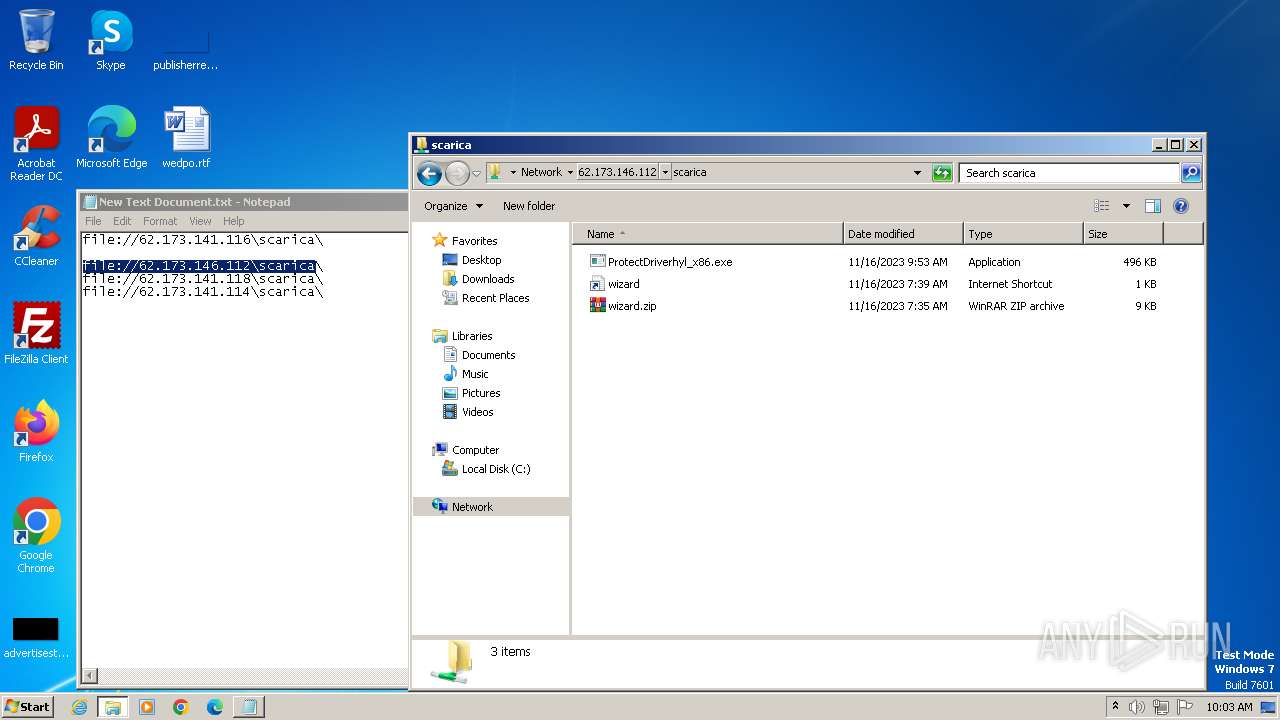
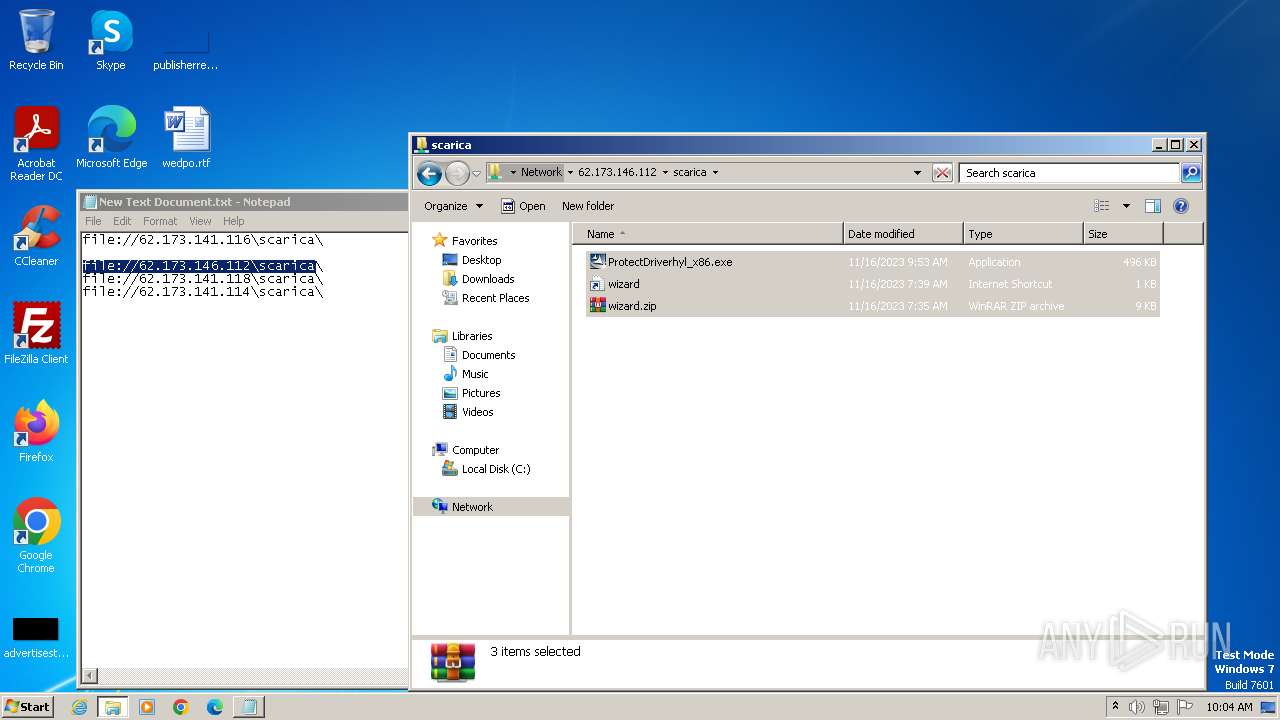
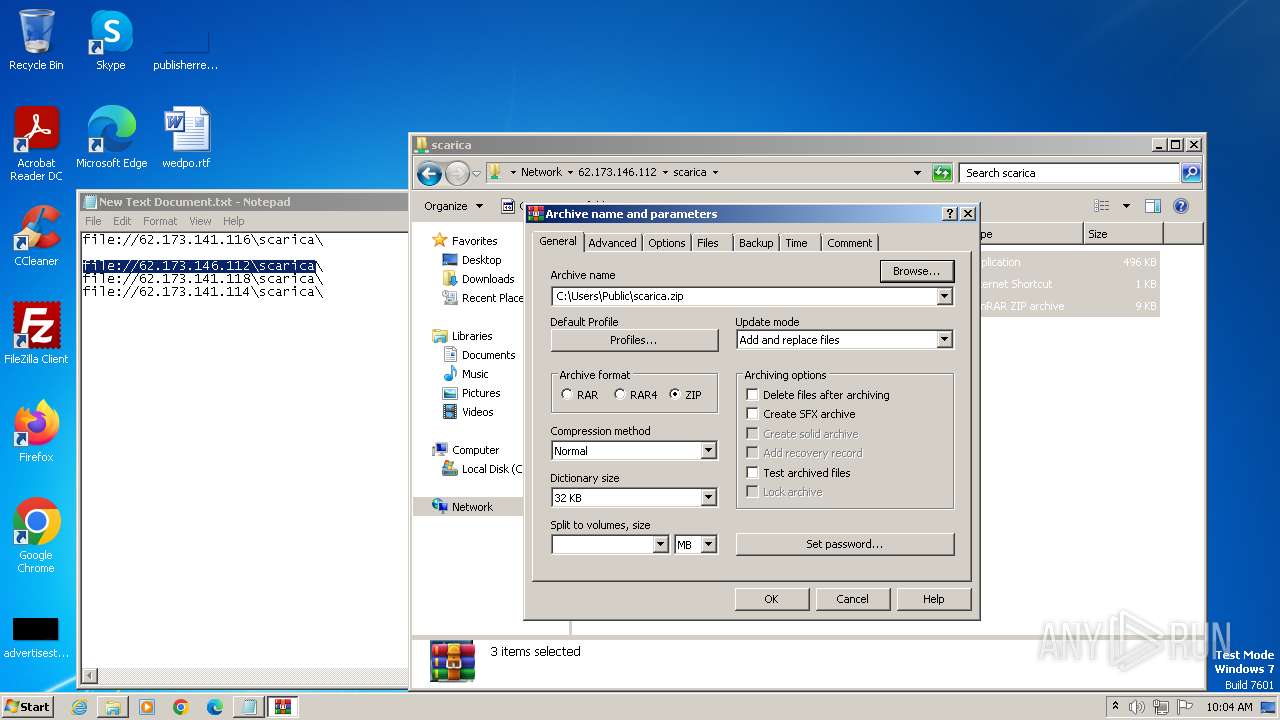
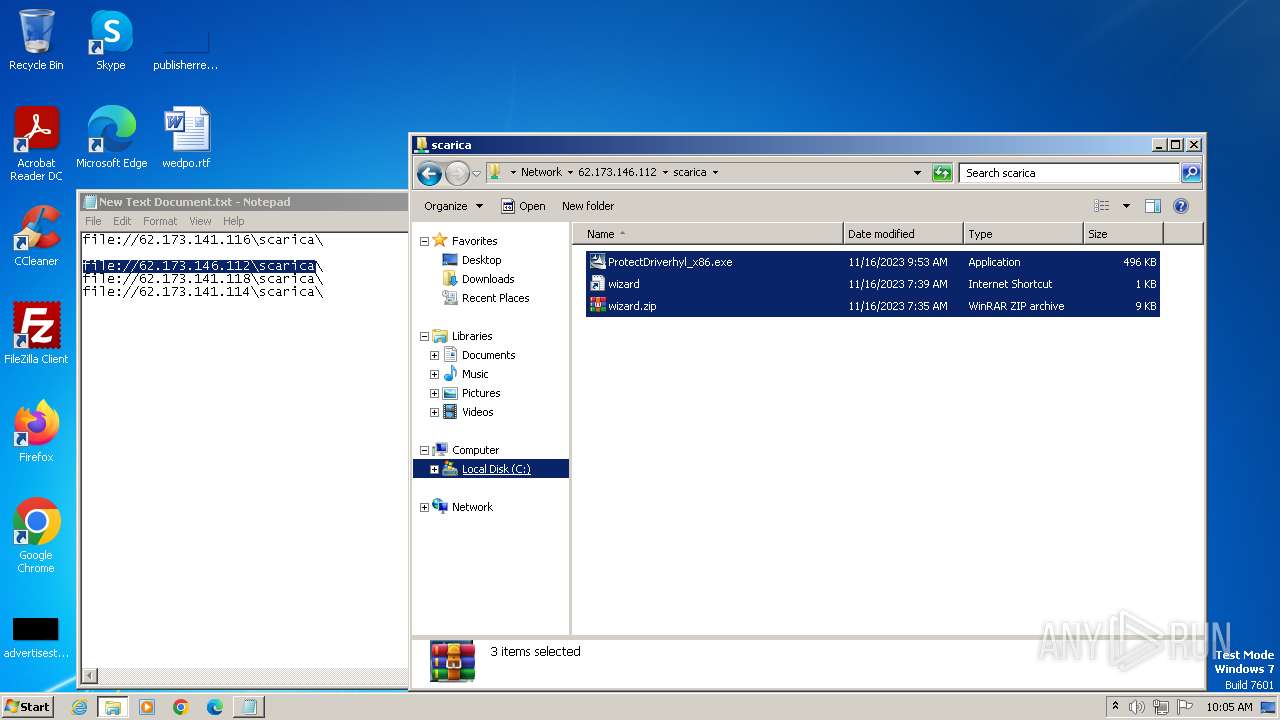
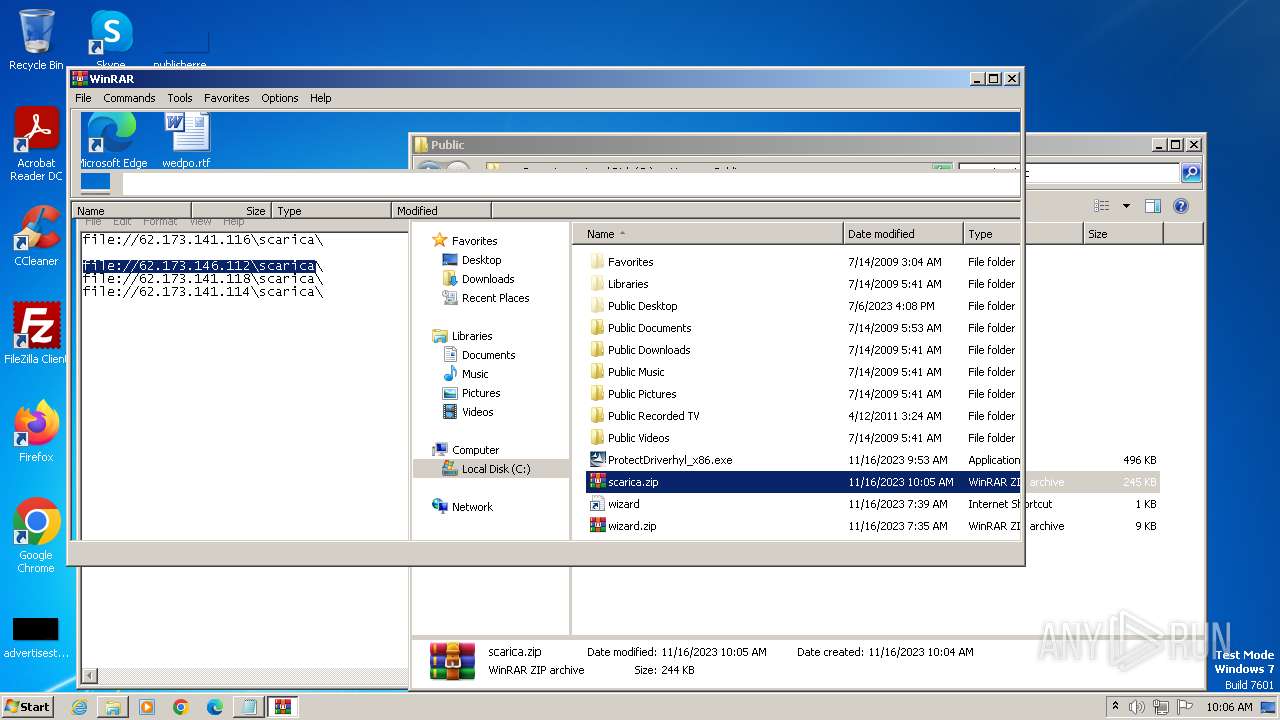
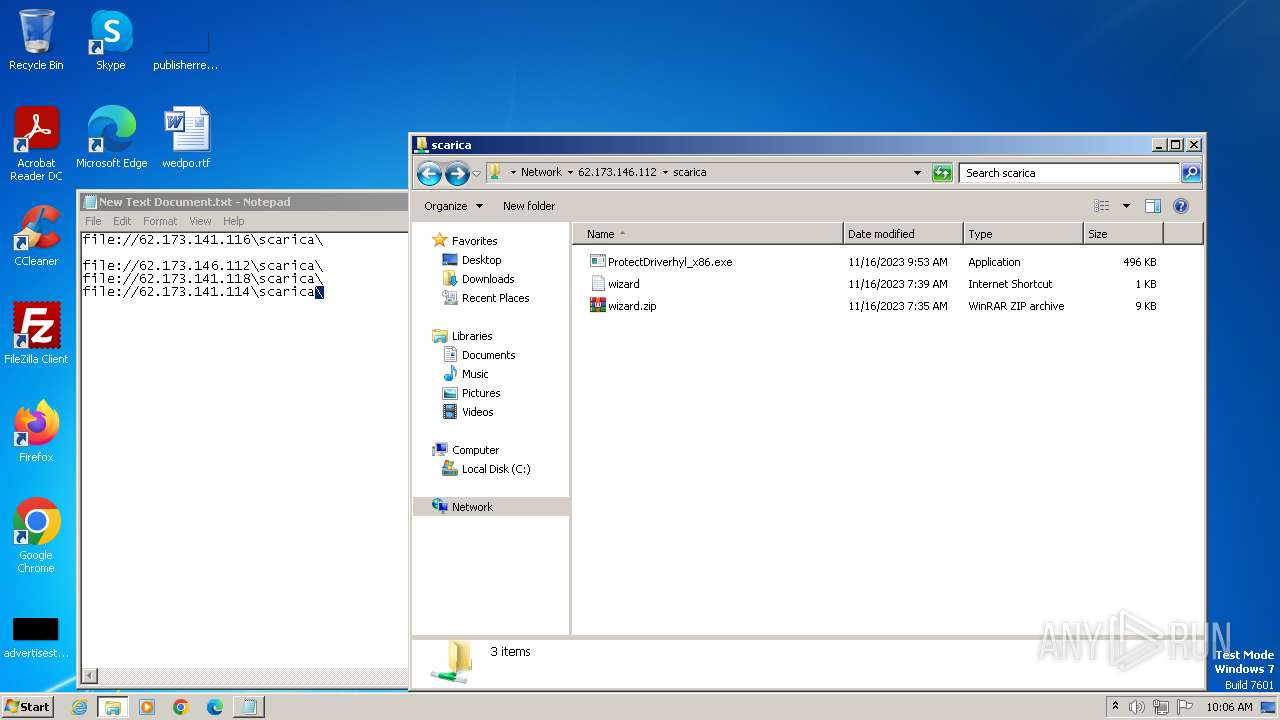
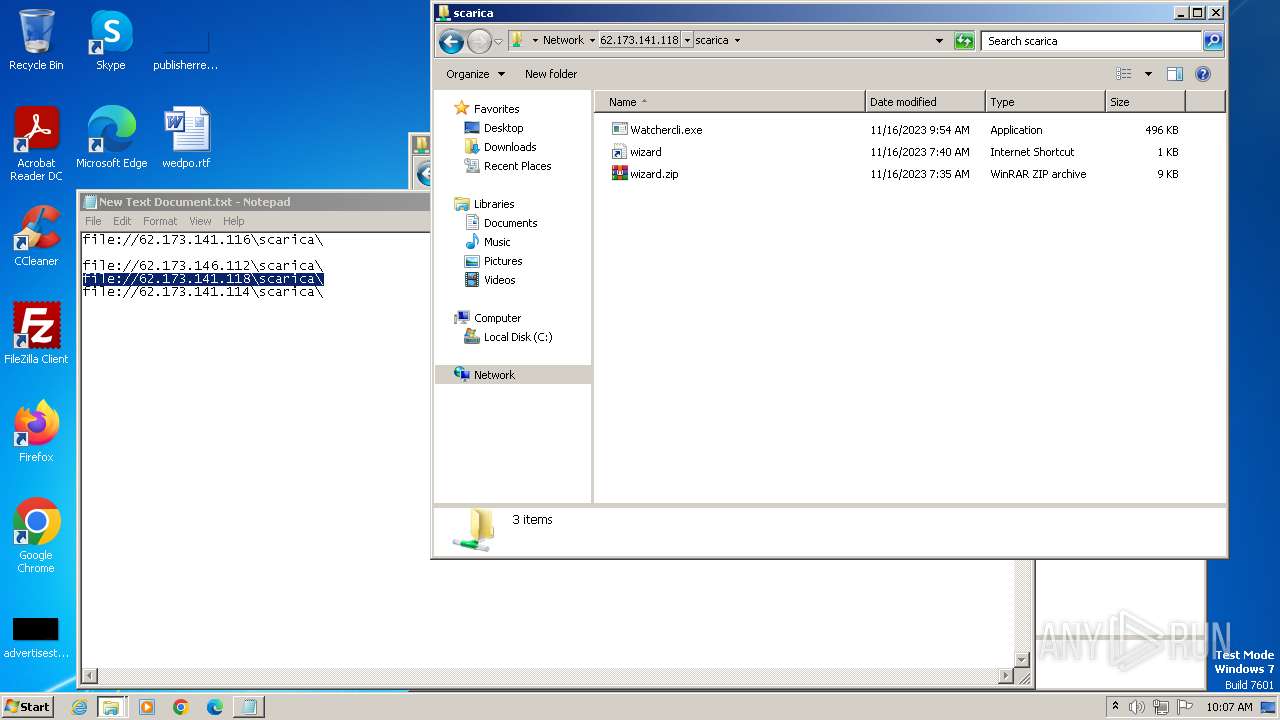
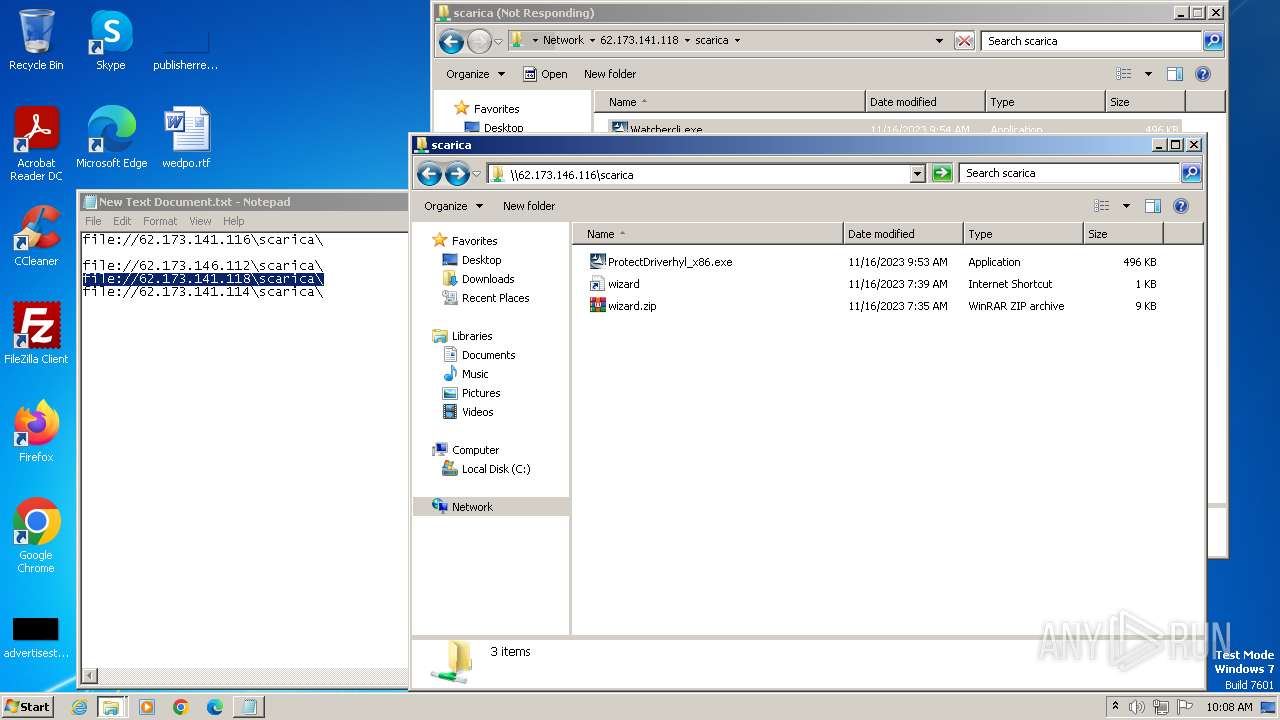
| 4016 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- . \\62.173.146.112\scarica\ProtectDriverhyl_x86.exe \\62.173.146.112\scarica\wizard.url \\62.173.146.112\scarica\wizard.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
12 950
Read events
12 428
Write events
512
Delete events
10
Modification events
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {Q65231O0-O2S1-4857-N4PR-N8R7P6RN7Q27}\abgrcnq.rkr |
Value: 0000000004000000040000005BFC0100000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF8023783622B0D90100000000 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000B001000012030000FFFD76013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E4510202000000840000003D3567004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000059004C61EF75A022590063003A005C00770069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C000000570069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C00000032020000000007000000E4E332021400000000000000000056007896210845D397750C12000000000000FA279C777896210814E432025F389C7764389C772279967578962108FA279C770000000000000000FFFFFFFF0000000000000000A21000004CE432023B600D77087C7C000000000047600D773F09C3B300000000A21000000000000024E432026C006C0050E4320200000000E8E43202A2100000081C09086CE43202B0FE5F74081C0908E8E43202A2100000000000000000004098E4320237C30D77C4000300A210000000000000F0E93202A2100000CDABBADC11000000485159004051590010E53202C4E4320270FE5F7414E500008809C3B3C4E432025E90EF7514E53202C8E432020394EF750000000044454402F0E43202A993EF75444544029CE53202B8404402BD93EF7500000000B84044029CE53202F8E4320202000000840000003D3567004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000059004C61EF75A022590063003A005C00770069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C000000570069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C00000032020000000007000000E4E332021400000000000000000056007896210845D397750C12000000000000FA279C777896210814E432025F389C7764389C772279967578962108FA279C770000000000000000FFFFFFFF0000000000000000A21000004CE432023B600D77087C7C000000000047600D773F09C3B300000000A21000000000000024E432026C006C0050E4320200000000E8E43202A2100000081C09086CE43202B0FE5F74081C0908E8E43202A2100000000000000000004098E4320237C30D77C4000300A210000000000000F0E93202A2100000CDABBADC11000000485159004051590010E53202C4E4320270FE5F7414E500008809C3B3C4E432025E90EF7514E53202C8E432020394EF750000000044454402F0E43202A993EF75444544029CE53202B8404402BD93EF7500000000B84044029CE53202F8E43202 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000F6D6788197A75D498472ACE88906AC8D000000000200000000001066000000010000200000007F0C5AFCF1AE7F71286A81A9B86E67A7BE47980777E154AD953E683E2064784E000000000E8000000002000020000000C547D0854BEA52CCDED7859B79990A863903B335001ED826D40C3D8E323F237F30000000DF0FBC24E15CFF4FE438F74D8486DFB808CBF3EC9160BD0CF16731298F2800053F0DC9D2737FB85ABF81EDB882A089A94000000011BAC043EAAF96F8497DEE93A36C7829C97427DA018BC7750377DAC2CC3CE4D64139784732F789D57202D54D80C3AAC2B4B5EE990B65AEF23416199647916AD4 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {S38OS404-1Q43-42S2-9305-67QR0O28SP23}\rkcybere.rkr |
Value: 000000003D0000007E00000010FC2C00000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFD0BBB0A82AB0D90100000000 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000B001000013030000FFFD76013F0000004A0000008E0F0D004D006900630072006F0073006F00660074002E0049006E007400650072006E00650074004500780070006C006F007200650072002E00440065006600610075006C007400000028003E004000A4E75102B8E651020000000000000000000000000000080274E45102000008026CE25102000000000000D26CFFFFFFFF705911750000000000000000A4E251027C900D75000400000000000008E35102FFFFFFFF38EA7000FFFFFFFF080A7400D80E740030EA7000D4E25102F7AF3D7680D0707614F05102081D3E76E4613E766820700008E351020000000071000000BBF2CB00E8E25102A1693E766820700008E351020000000014E551023F613E766820700008E3510200000400000000800400000026E4510298E351025DA5147726E45102D26E147779A51477D6794D7526E4510210E65102000100006400610072E3510226E451026F0061006D0069006E0067005C006D006900630072006F0073006F0066007400CCE351023400000080E35102DE70310033003300350033003800310030003000F8E551025A000000A0E351021DA71477D6610E02D4E351025A00000010E651025C00000011000000104F7000084F7000F8E55102C4E3510220E40000D7F3CB00D0E351025E903E7620E45102D4E3510203943E760000000064561802FCE35102A9933E7664561802A8E45102D8511802BD933E7600000000D8511802A8E4510204E4510202000000840000003D3567004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000059004C61EF75A022590063003A005C00770069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C000000570069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C00000032020000000007000000E4E332021400000000000000000056007896210845D397750C12000000000000FA279C777896210814E432025F389C7764389C772279967578962108FA279C770000000000000000FFFFFFFF0000000000000000A21000004CE432023B600D77087C7C000000000047600D773F09C3B300000000A21000000000000024E432026C006C0050E4320200000000E8E43202A2100000081C09086CE43202B0FE5F74081C0908E8E43202A2100000000000000000004098E4320237C30D77C4000300A210000000000000F0E93202A2100000CDABBADC11000000485159004051590010E53202C4E4320270FE5F7414E500008809C3B3C4E432025E90EF7514E53202C8E432020394EF750000000044454402F0E43202A993EF75444544029CE53202B8404402BD93EF7500000000B84044029CE53202F8E4320202000000840000003D3567004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000059004C61EF75A022590063003A005C00770069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C000000570069006E0064006F00770073005C00730079007300740065006D00330032005C0069006D006100670065007200650073002E0064006C006C00000032020000000007000000E4E332021400000000000000000056007896210845D397750C12000000000000FA279C777896210814E432025F389C7764389C772279967578962108FA279C770000000000000000FFFFFFFF0000000000000000A21000004CE432023B600D77087C7C000000000047600D773F09C3B300000000A21000000000000024E432026C006C0050E4320200000000E8E43202A2100000081C09086CE43202B0FE5F74081C0908E8E43202A2100000000000000000004098E4320237C30D77C4000300A210000000000000F0E93202A2100000CDABBADC11000000485159004051590010E53202C4E4320270FE5F7414E500008809C3B3C4E432025E90EF7514E53202C8E432020394EF750000000044454402F0E43202A993EF75444544029CE53202B8404402BD93EF7500000000B84044029CE53202F8E43202 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 000000003B000000000000003B000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFD0BBB0A82AB0D90100000000 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000E900000000000000E90000003E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D6033E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D6033E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D603 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | {9R3995NO-1S9P-4S13-O827-48O24O6P7174}\GnfxOne\Jvaqbjf Rkcybere.yax |
Value: 000000003C000000000000003B000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFFB0FD2A287418DA0100000000 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000EA00000000000000E90000003E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D6033E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D6033E000000000000003E0000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000006D000000000078AB287598117500084B7600981175000000000000000000DE1C0000E0791401C8D4D60313A91477E01D32BD0C0C00001027000002000000FF560200FCD4D603D8A81477FF560200E07914011CD5D603C05C18029CD5D60300000000A40100005CD500009BC44C010CD5D6035E903E765CD5D60310D5D60303943E76000000004C61180238D5D603A9933E764C611802E4D5D603C05C1802BD933E7600000000C05C1802E4D5D60340D5D603 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
1
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1388 | explorer.exe | \Device\Mup:\62.173.146.112\PIPE\wkssvc | — | |
MD5:— | SHA256:— | |||
| 1388 | explorer.exe | \Device\Mup:\62.173.146.112\PIPE\srvsvc | — | |
MD5:— | SHA256:— | |||
| 4016 | WinRAR.exe | \Device\Mup:\62.173.146.112\PIPE\srvsvc | — | |
MD5:— | SHA256:— | |||
| 1388 | explorer.exe | \Device\Mup:\62.173.141.118\PIPE\srvsvc | — | |
MD5:— | SHA256:— | |||
| 1388 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | binary | |
MD5:70F6947DA4C1B2EE593C5EE6EB3244A6 | SHA256:A6B323D111C090356FF3997A62603838D38FB51A82D136D22F621CD293EC027E | |||
| 1388 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\scarica.zip.lnk | binary | |
MD5:307CD06986EFDBD93D2DBE6E6E6C7B25 | SHA256:C3871EF37345E3F4CB34FDFD3C41241E0A443DD4E0886E534E29967FC80B76C7 | |||
| 1388 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | binary | |
MD5:DD5A836F9725909192622472F53B3C5C | SHA256:924DAF6AA1E79C326260F7D8633B9DB5306DFF2C178AD2C363687B17182FAB35 | |||
| 1388 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Public.lnk | binary | |
MD5:DC46F6CA1DC06333A8337ECDD4D56595 | SHA256:34E10FFA2255DD3B1ECFD4E5F556343E314B29B716A494112AE1BED6E46CF212 | |||
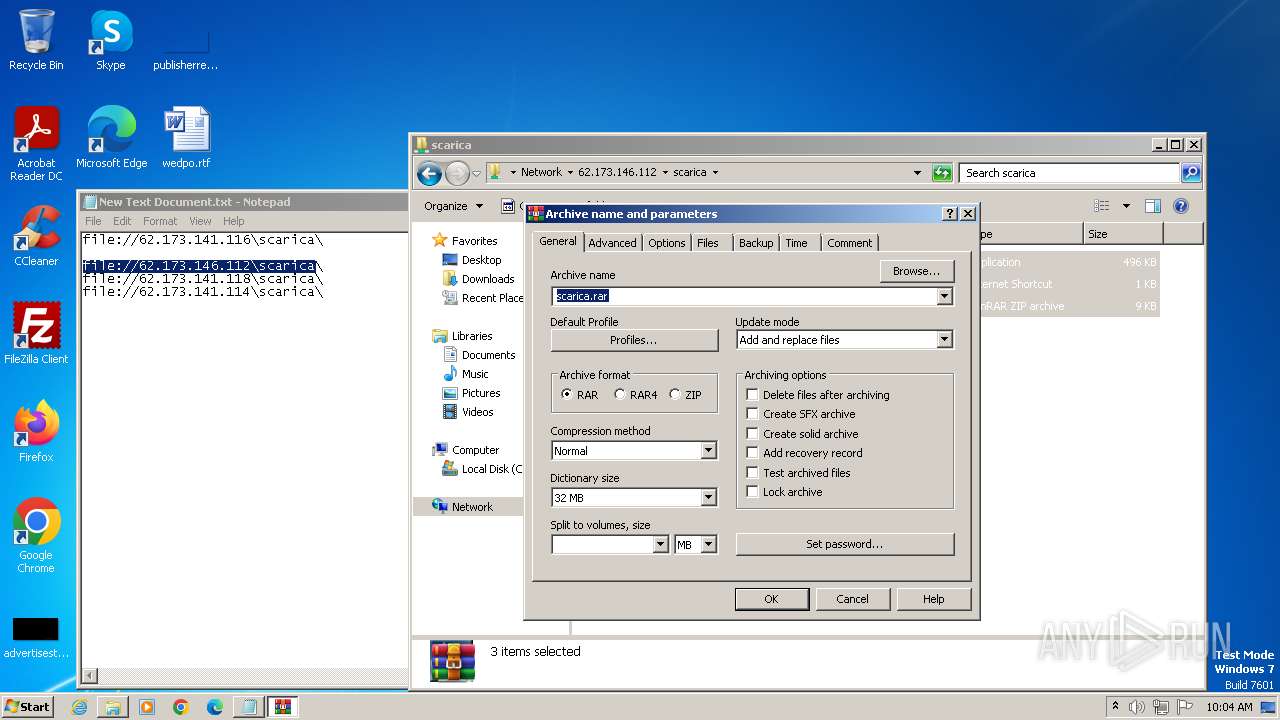
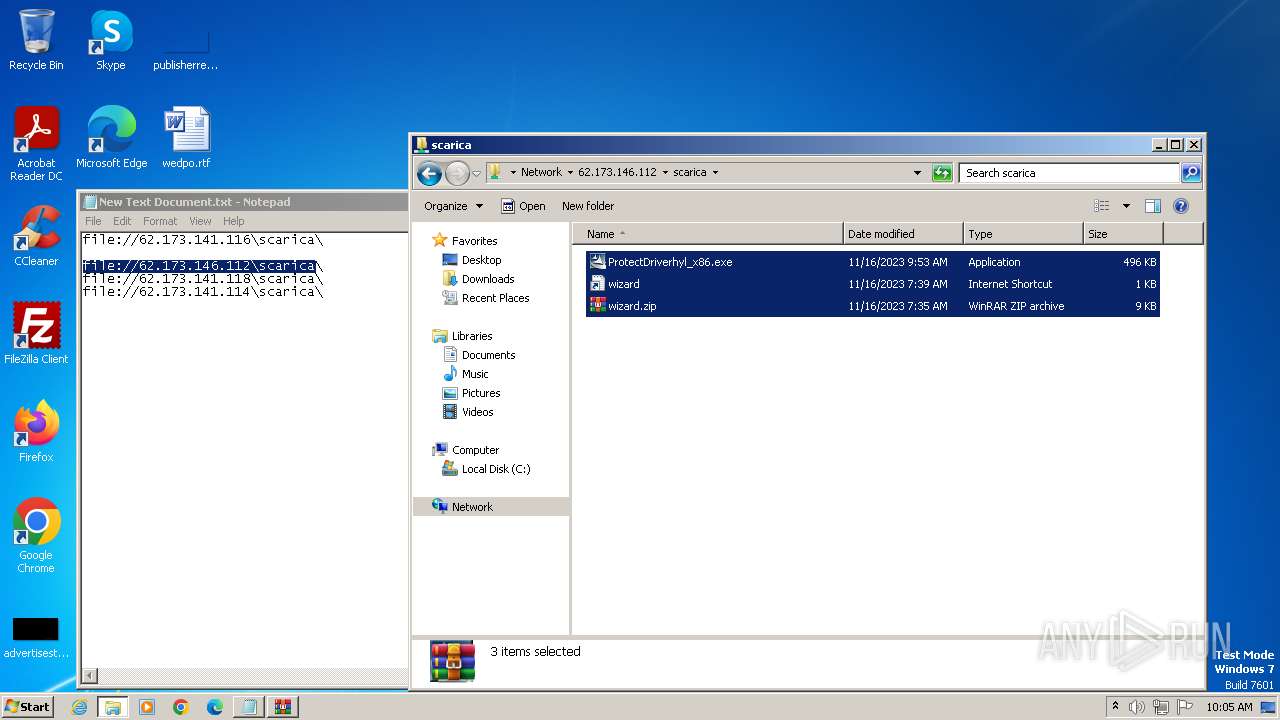
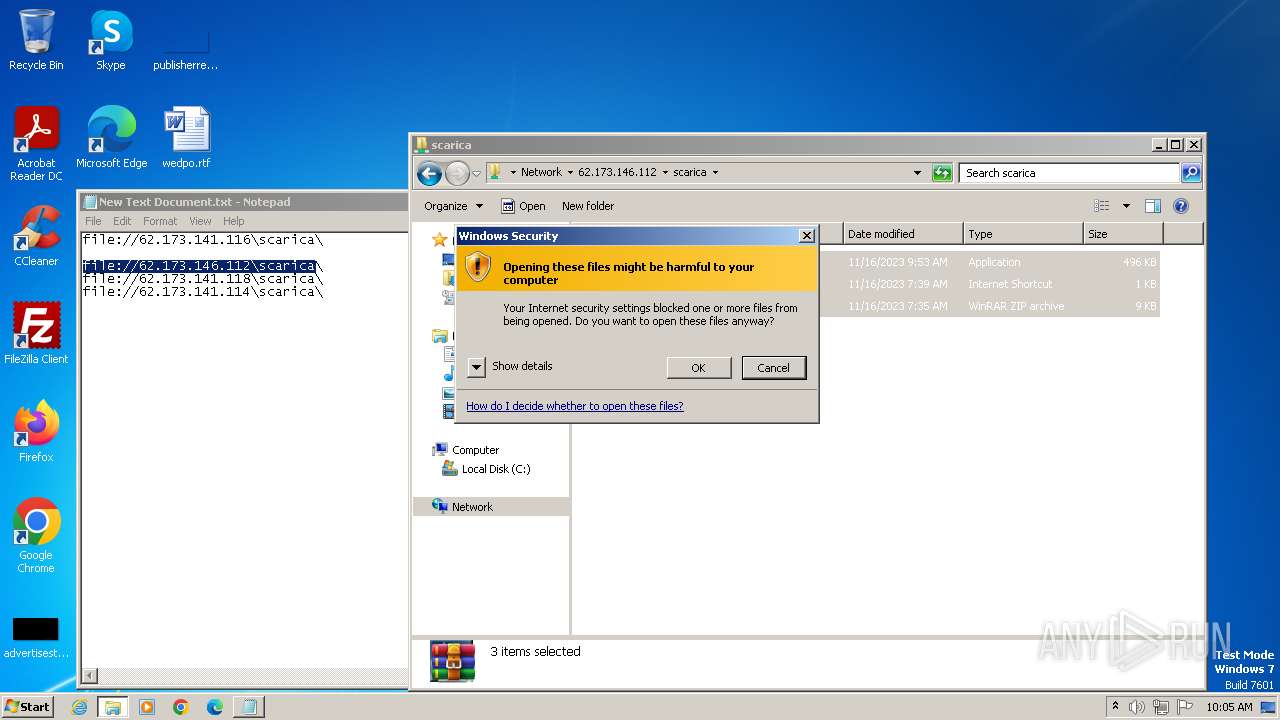
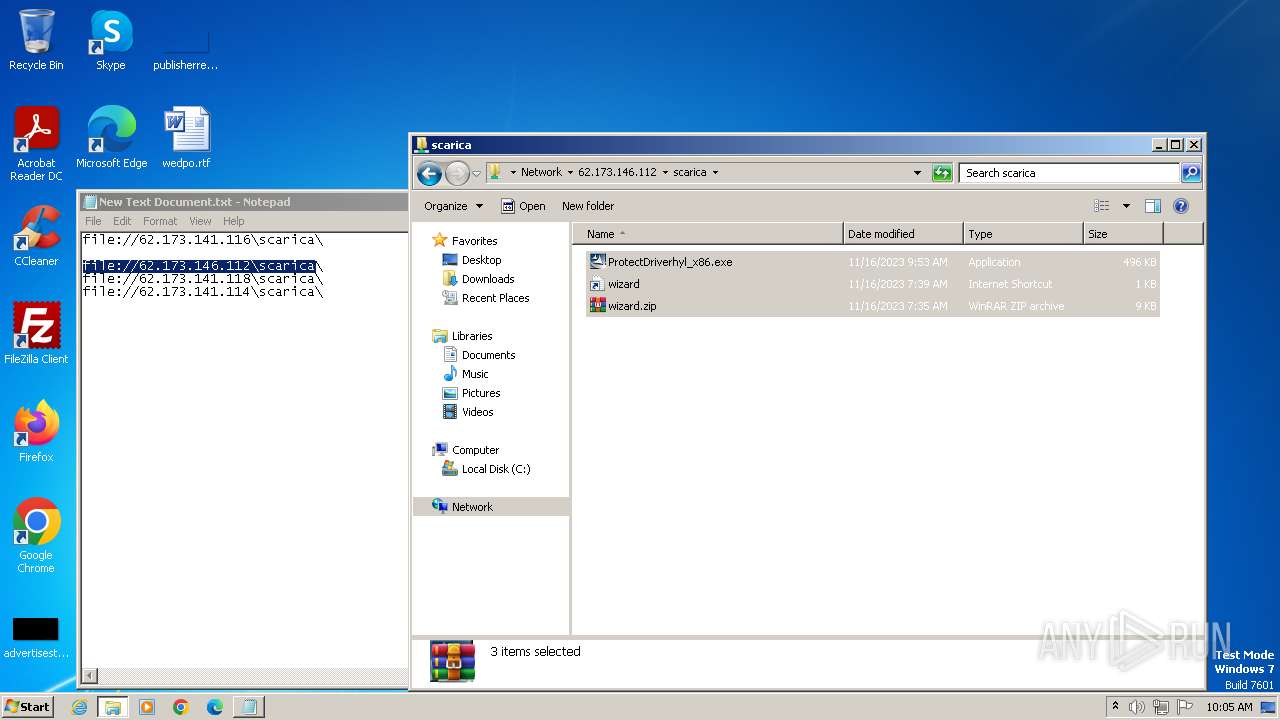
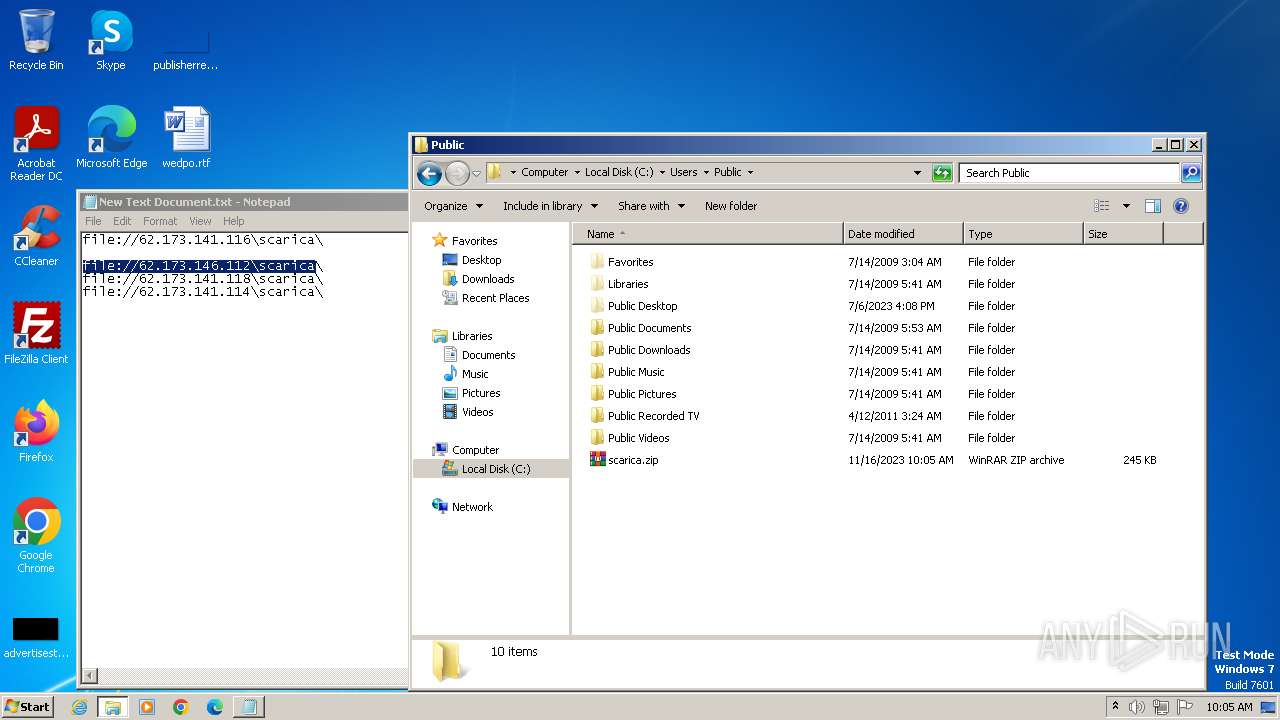
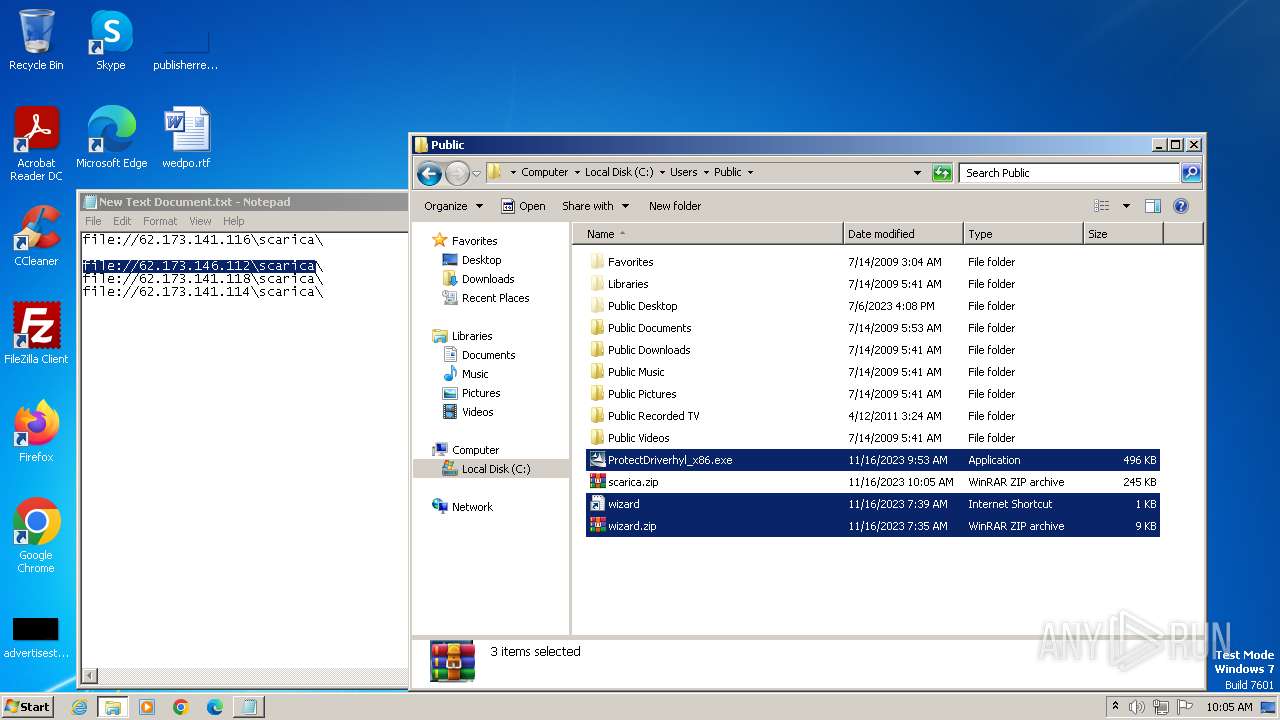
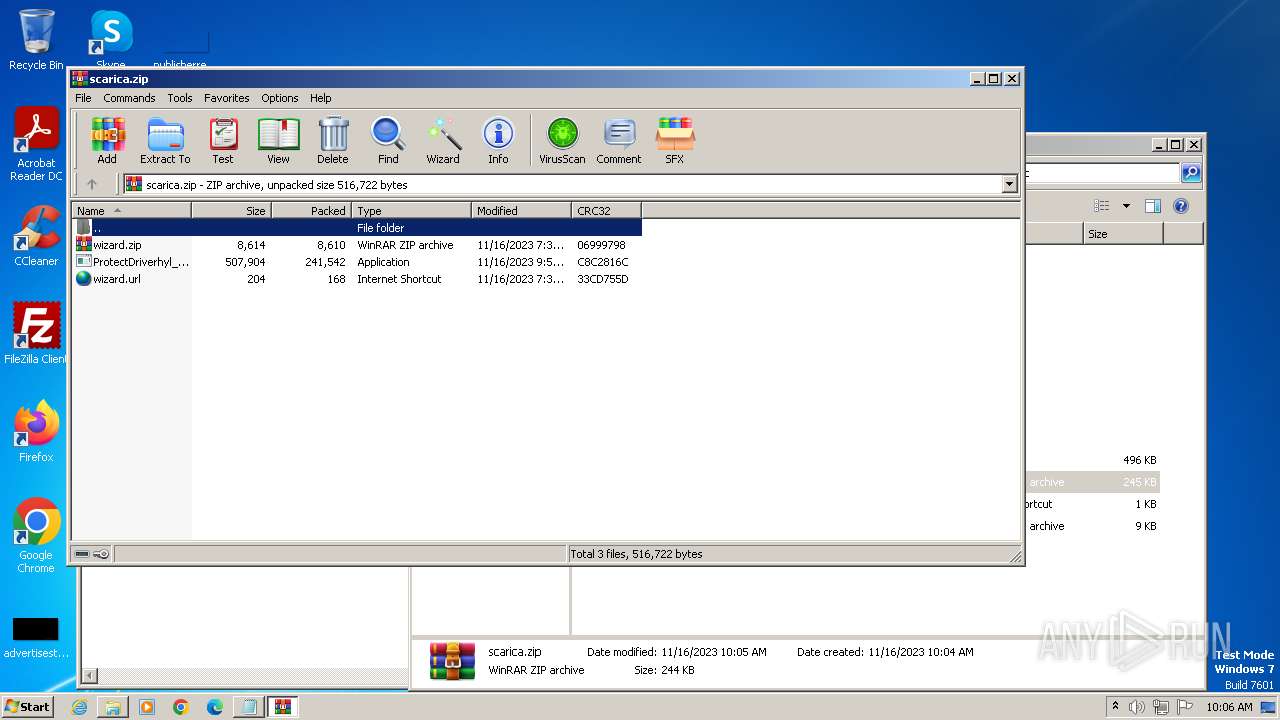
| 4016 | WinRAR.exe | C:\Users\Public\scarica.zip | compressed | |
MD5:C7D0AF6BE17E09BF16228284FB2205C1 | SHA256:0E1A2182B71E2B574A7B9BF8F5E9DEBAA9BCA522BB7A94D0BB9C4FC0DDC1A4E8 | |||
| 1388 | explorer.exe | C:\Users\Public\wizard.zip | compressed | |
MD5:4839CF7CF6B828CD5F2F920510B2356E | SHA256:9124FF5F4B0866441BCB1D0BDC93C80E7D5EB09700ECB05DAA68C38A12AB54BB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
31
DNS requests
0
Threats
10
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 62.173.146.112:445 | — | Internet-Cosmos LLC | RU | unknown |
4 | System | 62.173.146.11:445 | — | Internet-Cosmos LLC | RU | unknown |
4 | System | 62.173.146.11:139 | — | Internet-Cosmos LLC | RU | unknown |
4 | System | 62.173.146.116:445 | — | Internet-Cosmos LLC | RU | unknown |
4 | System | 62.173.146.116:139 | — | Internet-Cosmos LLC | RU | unknown |
1388 | explorer.exe | 62.173.146.11:80 | — | Internet-Cosmos LLC | RU | unknown |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Query an Executable file via SMB2 from an external server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Reading an Executable file via SMB2 from an external server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Reading an Executable file via SMB2 from an external server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Reading an Executable file via SMB2 from an external server |
4 | System | Generic Protocol Command Decode | SURICATA SMB file overlap |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Reading an Executable file via SMB2 from an external server |