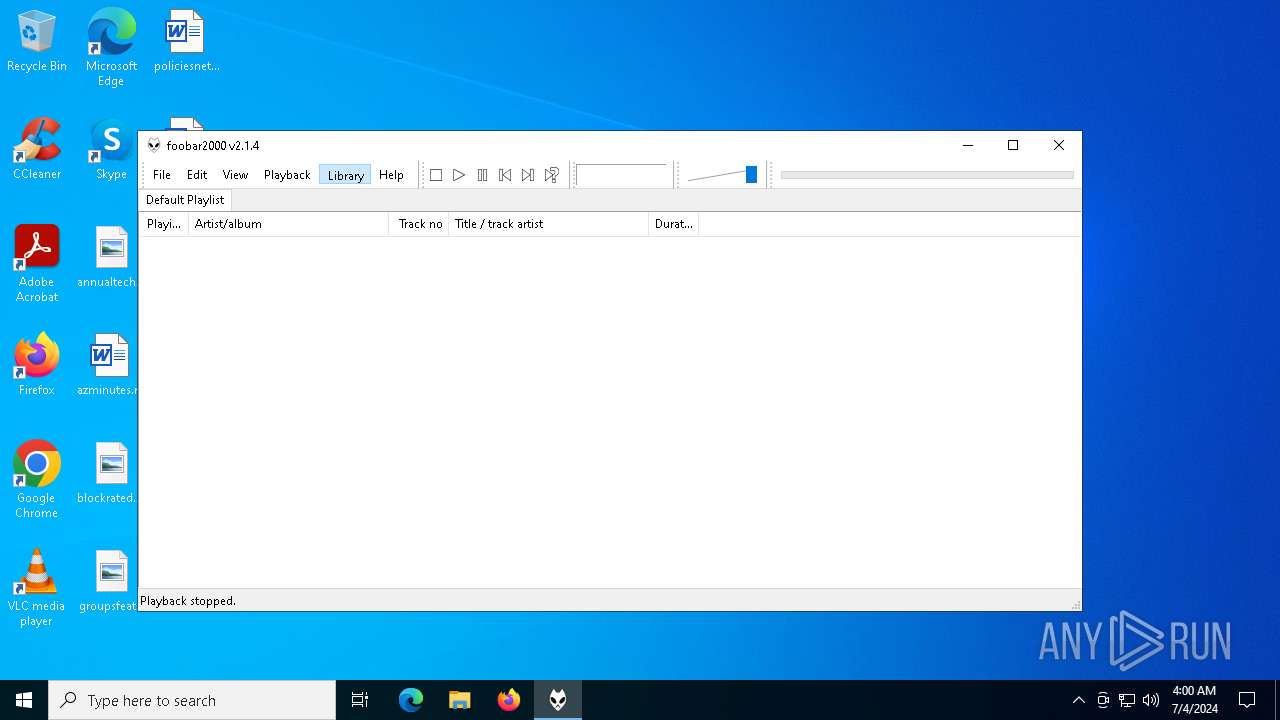
| File name: | Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe |
| Full analysis: | https://app.any.run/tasks/7b599664-dfd4-4816-bd92-eab9e1e6f06b |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2024, 03:59:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4C793953CFC69E13AB9490E786BB9920 |
| SHA1: | DBA02A794CDAB7C307409151D4060CEC655C7884 |
| SHA256: | E1459D69B38764A1EC3497127B44108541AC446C166B2F2A3475C87585BFB5D2 |
| SSDEEP: | 98304:hosbzrcEnyoBDJ2ogp9hn5yshbz2FnBs/9S4dv/oC7UCtZ9ONOHX6meCRo7cF6lP:1XezwSaJiy6CWel |
MALICIOUS
Drops the executable file immediately after the start
- Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe (PID: 2104)
- setup.exe (PID: 6400)
- setup.exe (PID: 5324)
SUSPICIOUS
Executable content was dropped or overwritten
- Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe (PID: 2104)
- setup.exe (PID: 6400)
- setup.exe (PID: 5324)
The process creates files with name similar to system file names
- setup.exe (PID: 6400)
- setup.exe (PID: 5324)
Process drops legitimate windows executable
- setup.exe (PID: 6400)
The process drops C-runtime libraries
- setup.exe (PID: 6400)
Reads security settings of Internet Explorer
- setup.exe (PID: 5324)
- foobar2000.exe (PID: 6772)
Application launched itself
- setup.exe (PID: 5324)
Malware-specific behavior (creating "System.dll" in Temp)
- setup.exe (PID: 6400)
- setup.exe (PID: 5324)
Creates a software uninstall entry
- setup.exe (PID: 6400)
Creates/Modifies COM task schedule object
- setup.exe (PID: 6400)
Changes default file association
- foobar2000 Shell Associations Updater.exe (PID: 6720)
Reads the date of Windows installation
- setup.exe (PID: 5324)
INFO
Checks supported languages
- Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe (PID: 2104)
- setup.exe (PID: 5324)
- setup.exe (PID: 6400)
- foobar2000.exe (PID: 6692)
- foobar2000.exe (PID: 6772)
- foobar2000 Shell Associations Updater.exe (PID: 6720)
Reads the computer name
- Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe (PID: 2104)
- setup.exe (PID: 6400)
- foobar2000.exe (PID: 6772)
- setup.exe (PID: 5324)
Create files in a temporary directory
- Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe (PID: 2104)
- setup.exe (PID: 5324)
- setup.exe (PID: 6400)
- foobar2000.exe (PID: 6692)
Creates files in the program directory
- setup.exe (PID: 6400)
Process checks computer location settings
- setup.exe (PID: 5324)
Creates files or folders in the user directory
- foobar2000.exe (PID: 6772)
- foobar2000.exe (PID: 6692)
Reads the software policy settings
- slui.exe (PID: 3152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:06:20 12:17:24+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 1229824 |
| InitializedDataSize: | 691712 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11de8c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.5.0 |
| ProductVersionNumber: | 2.1.5.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Efficacious Approval Applications |
| FileDescription: | Efficacious Approval Applications |
| FileVersion: | 2.1.5.0 |
| LegalCopyright: | Copyright 2003-2023 Efficacious Approval Applications |
| ProductName: | Efficacious Approval Applications |
| ProductVersion: | 2.1.5.0 |
Total processes
147
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2104 | "C:\Users\admin\AppData\Local\Temp\Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe" | C:\Users\admin\AppData\Local\Temp\Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe | explorer.exe | ||||||||||||
User: admin Company: Efficacious Approval Applications Integrity Level: MEDIUM Description: Efficacious Approval Applications Exit code: 0 Version: 2.1.5.0 Modules
| |||||||||||||||
| 3152 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
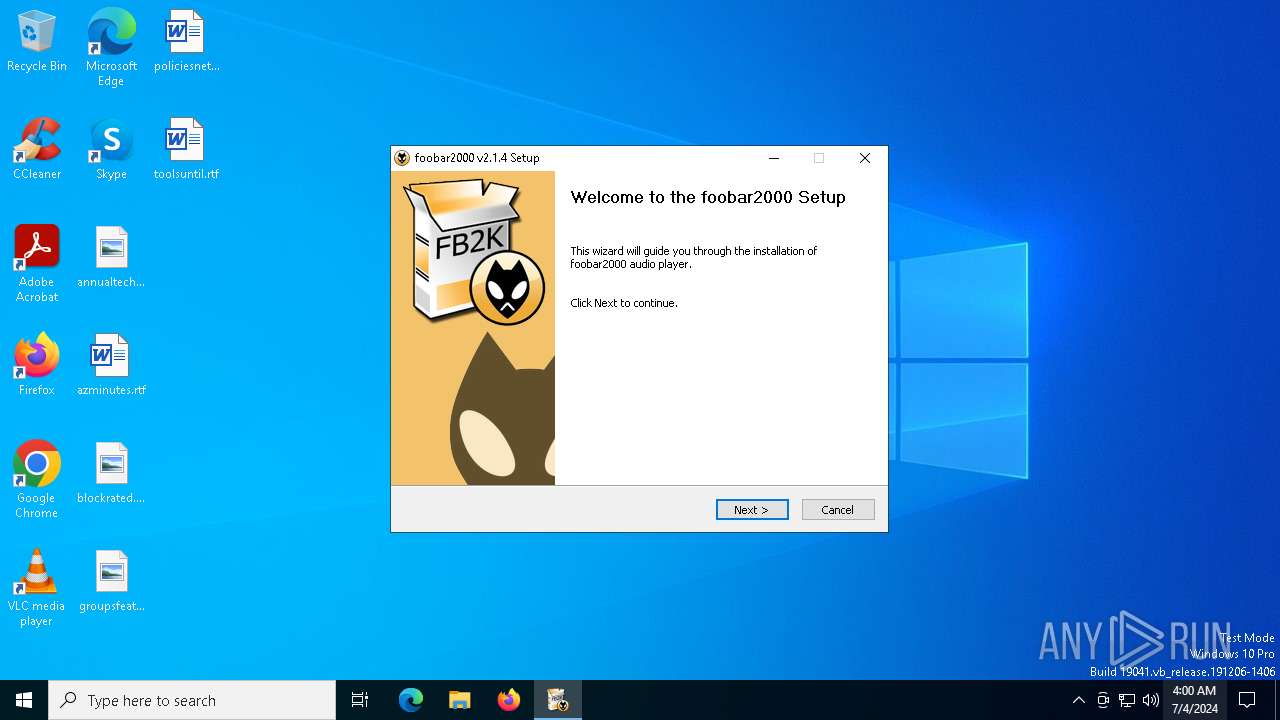
| 5324 | .\setup.exe | C:\Users\admin\AppData\Local\Temp\7zS838CE8FC\setup.exe | Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe | ||||||||||||
User: admin Company: foobar2000.org Integrity Level: MEDIUM Description: foobar2000 Installer Exit code: 0 Version: 2.1.4 Modules
| |||||||||||||||
| 5624 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6400 | "C:\Users\admin\AppData\Local\Temp\7zS838CE8FC\setup.exe" /UAC:602C4 /NCRC | C:\Users\admin\AppData\Local\Temp\7zS838CE8FC\setup.exe | setup.exe | ||||||||||||
User: admin Company: foobar2000.org Integrity Level: HIGH Description: foobar2000 Installer Exit code: 0 Version: 2.1.4 Modules
| |||||||||||||||
| 6456 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6692 | "C:\Program Files (x86)\foobar2000\foobar2000.exe" /install /quiet /exportshelldata "C:\Users\admin\AppData\Local\Temp\fb2kshelldata.tmp" | C:\Program Files (x86)\foobar2000\foobar2000.exe | — | setup.exe | |||||||||||
User: admin Company: Piotr Pawlowski Integrity Level: MEDIUM Description: foobar2000 Exit code: 0 Version: 2.1.4.0 Modules
| |||||||||||||||
| 6720 | "C:\Program Files (x86)\foobar2000\foobar2000 Shell Associations Updater.exe" "C:\Users\admin\AppData\Local\Temp\fb2kshelldata.tmp" | C:\Program Files (x86)\foobar2000\foobar2000 Shell Associations Updater.exe | — | setup.exe | |||||||||||
User: admin Company: Peter Pawlowski Integrity Level: HIGH Description: foobar2000 Shell Associations Updater Exit code: 0 Version: 1, 0, 0, 0 Modules
| |||||||||||||||
| 6772 | "C:\Program Files (x86)\foobar2000\foobar2000.exe" | C:\Program Files (x86)\foobar2000\foobar2000.exe | — | setup.exe | |||||||||||
User: admin Company: Piotr Pawlowski Integrity Level: MEDIUM Description: foobar2000 Exit code: 0 Version: 2.1.4.0 Modules
| |||||||||||||||
Total events
9 522
Read events
9 226
Write events
296
Delete events
0
Modification events
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\Fb2kShellExt.DLL |
| Operation: | write | Name: | AppID |
Value: {3B3052C5-E430-4A00-84C9-BFD43336940B} | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{0A35F9F4-F4BE-471A-890D-E09FFA6B38AD} |
| Operation: | write | Name: | AppID |
Value: {0A35F9F4-F4BE-471A-890D-E09FFA6B38AD} | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{0A35F9F4-F4BE-471A-890D-E09FFA6B38AD}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{0A35F9F4-F4BE-471A-890D-E09FFA6B38AD} |
| Operation: | write | Name: | DllSurrogate |
Value: | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\foobar2000 |
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files (x86)\foobar2000 | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\foobar2000.exe |
| Operation: | write | Name: | UseUrl |
Value: 1 | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\AutoplayHandlers\Handlers\foobar2000 |
| Operation: | write | Name: | DefaultIcon |
Value: C:\Program Files (x86)\foobar2000\foobar2000.exe | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\AutoplayHandlers\Handlers\foobar2000 |
| Operation: | write | Name: | Action |
Value: Play | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\AutoplayHandlers\Handlers\foobar2000 |
| Operation: | write | Name: | InvokeVerb |
Value: open | |||
| (PID) Process: | (6400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\AutoplayHandlers\Handlers\foobar2000 |
| Operation: | write | Name: | Provider |
Value: foobar2000 | |||
Executable files
93
Suspicious files
50
Text files
46
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6400 | setup.exe | C:\Users\admin\AppData\Local\Temp\nsj19F5.tmp\nsDialogs.dll | executable | |
MD5:B7D61F3F56ABF7B7FF0D4E7DA3AD783D | SHA256:89A82C4849C21DFE765052681E1FAD02D2D7B13C8B5075880C52423DCA72A912 | |||
| 6400 | setup.exe | C:\Users\admin\AppData\Local\Temp\nsj19F5.tmp\modern-header.bmp | image | |
MD5:D0A335B55AEA042DBA383CB9EB91C093 | SHA256:60F9E6030D4C75E5ED7E9300FB13FD46346D581E2039AE5E9A66DA72984C78F5 | |||
| 5324 | setup.exe | C:\Users\admin\AppData\Local\Temp\nsoFFC6.tmp\UAC.dll | executable | |
MD5:3FA5491C158C30082B42569CF4F54381 | SHA256:560BA0A768687A5B8643062B6183991E4D8E172B870E3C0A8A8847043CE32C86 | |||
| 2104 | Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe | C:\Users\admin\AppData\Local\Temp\7zS838CE8FC\setup.exe | executable | |
MD5:98B7FF04D271A6456FF75695569D0131 | SHA256:9BE23DA2B8505180A1F94520DAB6E6A741DBE961520BF4AE1EB6A0E68D1F811D | |||
| 6400 | setup.exe | C:\Program Files (x86)\foobar2000\avutil-fb2k-58.dll | executable | |
MD5:7B5A19D59E16243EE5FA626D2C85F591 | SHA256:6989E896E11FFB32599BA3171C1BA621760B8B3A17C528D49C249CA6A6829375 | |||
| 6400 | setup.exe | C:\Program Files (x86)\foobar2000\foobar2000.exe | executable | |
MD5:A6D44952C28AFBEB29DBB6CA489356F7 | SHA256:2CDE955CC262006E314BFEB14151AB81C6ABA33CFC4A2536F03BF6966B8CD7B9 | |||
| 6400 | setup.exe | C:\Program Files (x86)\foobar2000\avformat-fb2k-60.dll | executable | |
MD5:3FBE2CA8E9F16CBC664139C9EBD6EC15 | SHA256:7E273F00B5DA2CC7608EAA000DF4038BFAA0266A0C0BB3A6CDFEC8018E8EF1F8 | |||
| 6400 | setup.exe | C:\Program Files (x86)\foobar2000\avcodec-fb2k-60.dll | executable | |
MD5:92E12DA2EB765AB11FBBE5B7CEDAAE38 | SHA256:050A92A54F3258FC31F97CFE462DBF307C55DFBBBF3862AA1549117777BF3F03 | |||
| 6400 | setup.exe | C:\Program Files (x86)\foobar2000\PP-UWP-Interop.dll | executable | |
MD5:48A7C1F9E5E9B7556FFE21881D1C14C6 | SHA256:F41D7B5EDEBBFAAA062E41112EBEC85210A2877F0E0338F05237BC817AB17D94 | |||
| 5324 | setup.exe | C:\Users\admin\AppData\Local\Temp\nsoFFC6.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
76
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3716 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
900 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
900 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5228 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2268 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2088 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
2088 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1856 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2476 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
900 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | Resident-Evil-4-Ultimate-HD-Edition-v1.1.0_923224.exe | 104.26.8.6:443 | codeonicinc.com | CLOUDFLARENET | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3716 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3716 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
codeonicinc.com |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |