| File name: | install-interception.exe |
| Full analysis: | https://app.any.run/tasks/1789e46f-dae3-425a-bf9a-52dc7465d7ba |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2024, 15:39:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 0F0B50D92E030B8965CE669C8058FA6E |
| SHA1: | 257B3F0402285A29F4618B32958C208B3E9D4C4D |
| SHA256: | E137863A79DA797F08E7A137280FF2A123809044A888FD75CE9C973198915ABE |
| SSDEEP: | 6144:+sglhAWORQG8O1dMDmJPjQy4xZWLUKc2y:+s4LjGvMk74+B4 |
MALICIOUS
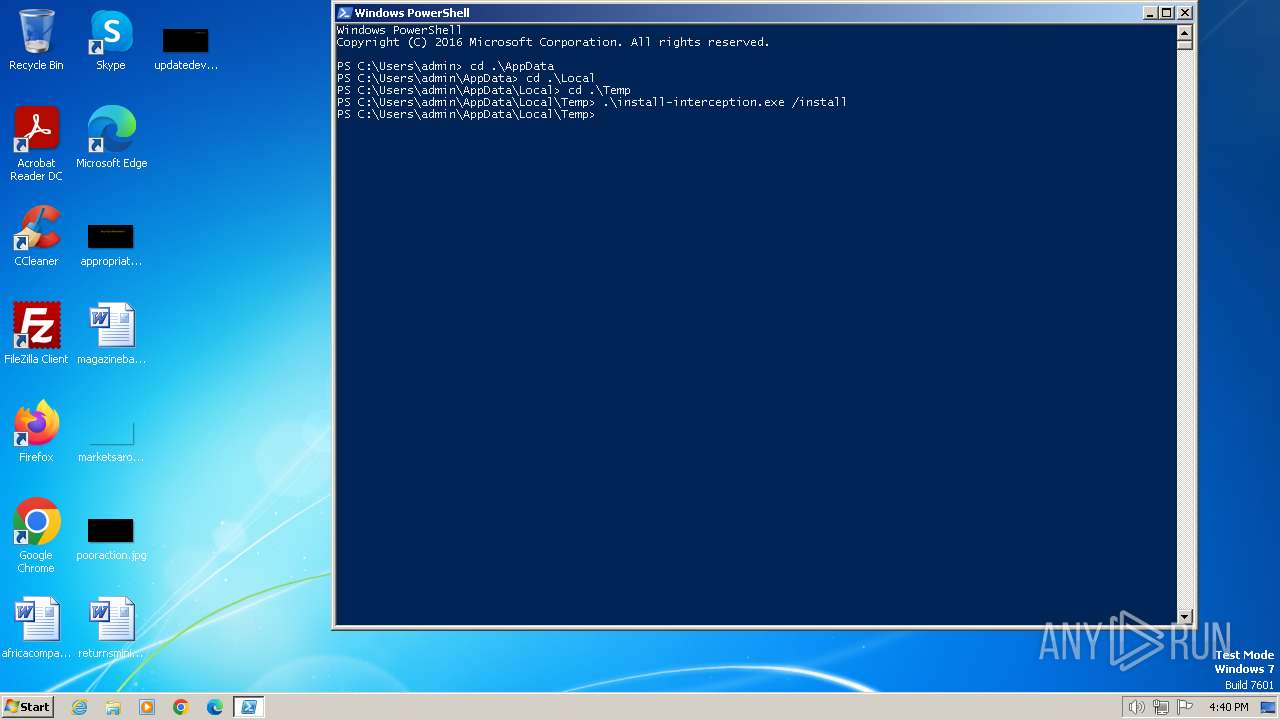
Drops the executable file immediately after the start
- install-interception.exe (PID: 3192)
- install-interception.exe (PID: 1788)
Creates a writable file in the system directory
- install-interception.exe (PID: 1788)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 740)
Drops a system driver (possible attempt to evade defenses)
- install-interception.exe (PID: 1788)
Creates files in the driver directory
- install-interception.exe (PID: 1788)
Executable content was dropped or overwritten
- install-interception.exe (PID: 1788)
Creates or modifies Windows services
- install-interception.exe (PID: 1788)
INFO
Checks supported languages
- install-interception.exe (PID: 3192)
- wmpnscfg.exe (PID: 2980)
- install-interception.exe (PID: 1788)
Reads the computer name
- wmpnscfg.exe (PID: 2980)
Manual execution by a user
- explorer.exe (PID: 3096)
- wmpnscfg.exe (PID: 2980)
- powershell.exe (PID: 740)
Checks current location (POWERSHELL)
- powershell.exe (PID: 740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:03:24 23:52:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 29696 |
| InitializedDataSize: | 441344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x614c |
| OSVersion: | 6.1 |
| ImageVersion: | 6.1 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Francisco Lopes |
| FileDescription: | Interception command line installation tool |
| FileVersion: | 1.00 built by: WinDDK |
| InternalName: | install-interception.exe |
| LegalCopyright: | Copyright (C) 2008-2018 Francisco Lopes da Silva |
| OriginalFileName: | install-interception.exe |
| ProductName: | Interception |
| ProductVersion: | 1 |
Total processes
54
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 740 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1788 | "C:\Users\admin\AppData\Local\Temp\install-interception.exe" /install | C:\Users\admin\AppData\Local\Temp\install-interception.exe | powershell.exe | ||||||||||||
User: admin Company: Francisco Lopes Integrity Level: HIGH Description: Interception command line installation tool Exit code: 0 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\AppData\Local\Temp\install-interception.exe" /install | C:\Users\admin\AppData\Local\Temp\install-interception.exe | — | powershell.exe | |||||||||||
User: admin Company: Francisco Lopes Integrity Level: MEDIUM Description: Interception command line installation tool Exit code: 3221226540 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 2980 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3084 | "C:\Users\admin\AppData\Local\Temp\INSTAL~1.EXE" "C:\Users\admin\AppData\Local\Temp\install-interception.exe" /install | C:\Users\admin\AppData\Local\Temp\install-interception.exe | — | powershell.exe | |||||||||||
User: admin Company: Francisco Lopes Integrity Level: MEDIUM Description: Interception command line installation tool Exit code: 3221226540 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 3088 | "C:\Users\admin\AppData\Local\Temp\install-interception.exe" /install | C:\Users\admin\AppData\Local\Temp\install-interception.exe | — | powershell.exe | |||||||||||
User: admin Company: Francisco Lopes Integrity Level: MEDIUM Description: Interception command line installation tool Exit code: 3221226540 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 3096 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3192 | "C:\Users\admin\AppData\Local\Temp\install-interception.exe" | C:\Users\admin\AppData\Local\Temp\install-interception.exe | explorer.exe | ||||||||||||
User: admin Company: Francisco Lopes Integrity Level: HIGH Description: Interception command line installation tool Exit code: 1 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
| 3700 | "C:\Users\admin\AppData\Local\Temp\install-interception.exe" | C:\Users\admin\AppData\Local\Temp\install-interception.exe | — | explorer.exe | |||||||||||
User: admin Company: Francisco Lopes Integrity Level: MEDIUM Description: Interception command line installation tool Exit code: 3221226540 Version: 1.00 built by: WinDDK Modules
| |||||||||||||||
Total events
4 654
Read events
4 584
Write events
70
Delete events
0
Modification events
| (PID) Process: | (740) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (740) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (740) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (740) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (740) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1788) install-interception.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\keyboard |
| Operation: | write | Name: | DisplayName |
Value: Keyboard Upper Filter Driver | |||
| (PID) Process: | (1788) install-interception.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\keyboard |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (1788) install-interception.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\keyboard |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (1788) install-interception.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\keyboard |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (1788) install-interception.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\mouse |
| Operation: | write | Name: | DisplayName |
Value: Mouse Upper Filter Driver | |||
Executable files
2
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 740 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\95KO9CQM1L2BTGLYRR1T.temp | binary | |
MD5:8F53FC52AD45A1893E74613827DE0052 | SHA256:3674C90C63B00076DEB5318DB20EB927C9FB24F00B2C31171784DD0F9B2A9800 | |||
| 740 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tsgctmte.ahr.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 740 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF57fd6.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 740 | powershell.exe | C:\Users\admin\AppData\Local\Temp\htkucjtn.pq3.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 740 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:8F53FC52AD45A1893E74613827DE0052 | SHA256:3674C90C63B00076DEB5318DB20EB927C9FB24F00B2C31171784DD0F9B2A9800 | |||
| 1788 | install-interception.exe | C:\Windows\system32\drivers\keyboard.sys | executable | |
MD5:08D1211820889F97D8A8796584D38EB9 | SHA256:979F790B75860FC713C159740F00ED4A11E7BC785E417B3442F765FFEC4DDC36 | |||
| 1788 | install-interception.exe | C:\Windows\system32\drivers\mouse.sys | executable | |
MD5:63CD86F720B000CF7CC75BB78CECBDC3 | SHA256:548C86A06FDACC093E7A3B9A5484FFAE6F66D9676A05B7B7E8D666DA52DEFDC6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?60bcd71e49d094b3 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1060 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |