| File name: | TestVuln.zip |
| Full analysis: | https://app.any.run/tasks/b169a273-a982-44f2-be21-c8c2130c4473 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 08:47:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 556E5095609383B6996A7FB00EFE6087 |
| SHA1: | 7CB51C4B8D88B6A41B9552843C8A84F9EEE4A3A9 |
| SHA256: | E0E90CB6330D623B030ED2A03EF0EBC2BC2C7535BF67A858E9AFA832BA86597D |
| SSDEEP: | 6:5jHK4mgJPPBFxsRtKqNXmdKNklfT/VVcWBeaZmHK4Lghmt+lx5:5jqgJRQtKq0dgklL/RYaZJ1hmta7 |
MALICIOUS
CVE-2024-43451 has been detected
- explorer.exe (PID: 4772)
- WinRAR.exe (PID: 6536)
WebDav connection (SURICATA)
- explorer.exe (PID: 4772)
SUSPICIOUS
Creates file in the systems drive root
- WinRAR.exe (PID: 6536)
Potential Corporate Privacy Violation
- explorer.exe (PID: 4772)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6536)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
Creates files or folders in the user directory
- explorer.exe (PID: 4772)
Checks proxy server information
- explorer.exe (PID: 4772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:19 10:46:46 |
| ZipCRC: | 0x0b6de32d |
| ZipCompressedSize: | 136 |
| ZipUncompressedSize: | 153 |
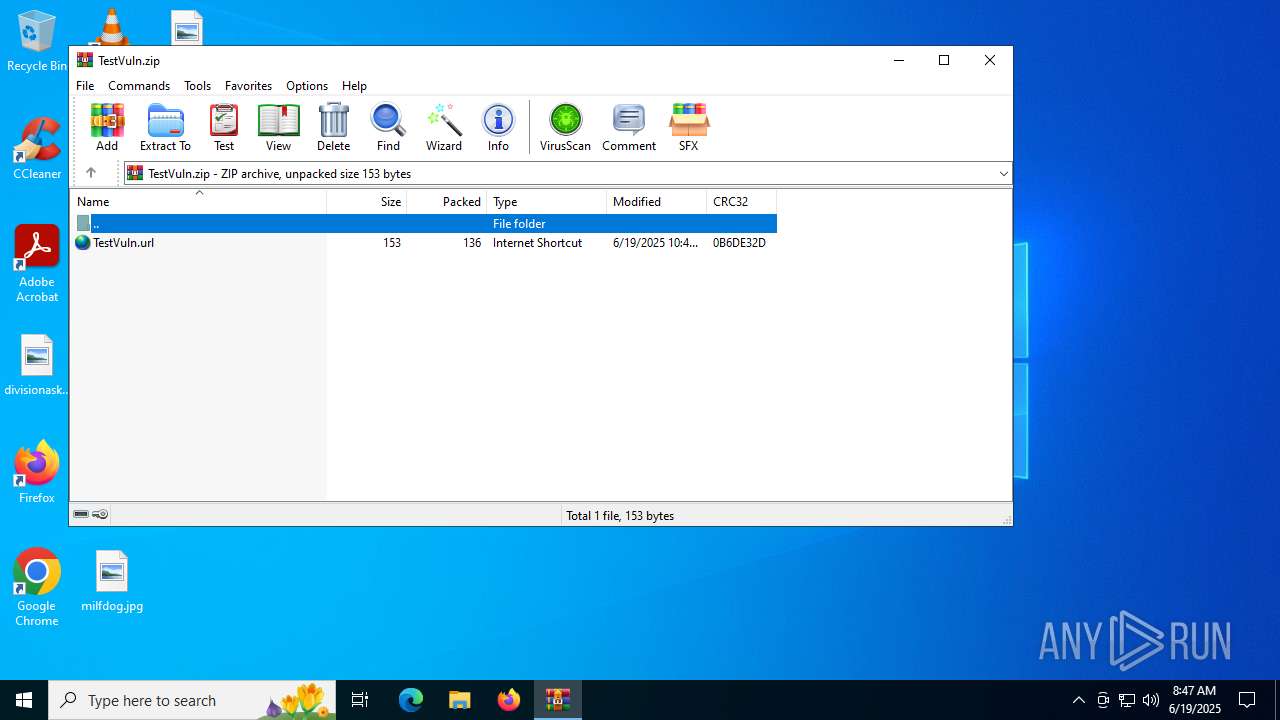
| ZipFileName: | TestVuln.url |
Total processes
135
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4772 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6536 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\TestVuln.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 865
Read events
2 840
Write events
25
Delete events
0
Modification events
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\TestVuln.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000004400000044000000 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010011000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C00000015000000000000006400690076006900730069006F006E00610073006B00650064002E006A00700067003E002000200000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C00000013000000000000006200720069007400690073006800610062006C0065002E007200740066003E002000200000001200000000000000630061006C006C007300650061007200630068002E006A00700067003E002000200000001A000000000000006D0061006E00750066006100630074007500720065007200670072006F007500700073002E007200740066003E002000200000000F000000000000006D0069006C00660064006F0067002E006A00700067003E00200020000000100000000000000070006D00720065007400610069006C002E006A00700067003E00200020000000110000000000000070006F0073007400650072006E006F0077002E006A00700067003E002000200000001400000000000000730074006100740065006D0065006E007400630075006D002E007200740066003E002000200000001100000000000000740069007000730063006F006D00650073002E007200740066003E0020002000000010000000000000005400650073007400560075006C006E002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001100000000000000000000000000000000000000803F0000004008000000803F000040400900000000000000404003000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F00000000000000803F01000000000000000040020000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000080401000 | |||
Executable files
0
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4772 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:88CECC3A0591E8F7440BCDE0BE2DFDA9 | SHA256:9B191BBEC8F248647FACEDDEE738E8D491949A0D046D0B9BC767E8A9E0CDB4E5 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6536.16455\TestVuln.url | binary | |
MD5:5867DE6A0584A3E892C5BC04E1BB4681 | SHA256:44AA81CC8E9F5C1AF0B6631E679FA97F9757DE3C179A3063C3F4905A5BCFF3AC | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 4772 | explorer.exe | C:\Users\admin\Desktop\TestVuln.url | binary | |
MD5:5867DE6A0584A3E892C5BC04E1BB4681 | SHA256:44AA81CC8E9F5C1AF0B6631E679FA97F9757DE3C179A3063C3F4905A5BCFF3AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
16
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1128 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1128 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4772 | explorer.exe | OPTIONS | 405 | 178.63.67.153:80 | http://webhook.site/ | unknown | — | — | whitelisted |
6900 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5348 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 178.63.67.153:445 | webhook.site | Hetzner Online GmbH | DE | whitelisted |
4 | System | 178.63.67.106:445 | webhook.site | Hetzner Online GmbH | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
webhook.site |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO DNS Query for Webhook/HTTP Request Inspection Service (webhook .site) |
2200 | svchost.exe | Misc activity | ET INFO DNS Query for Webhook/HTTP Request Inspection Service (webhook .site) |
4772 | explorer.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] WebDav activity has been detected |