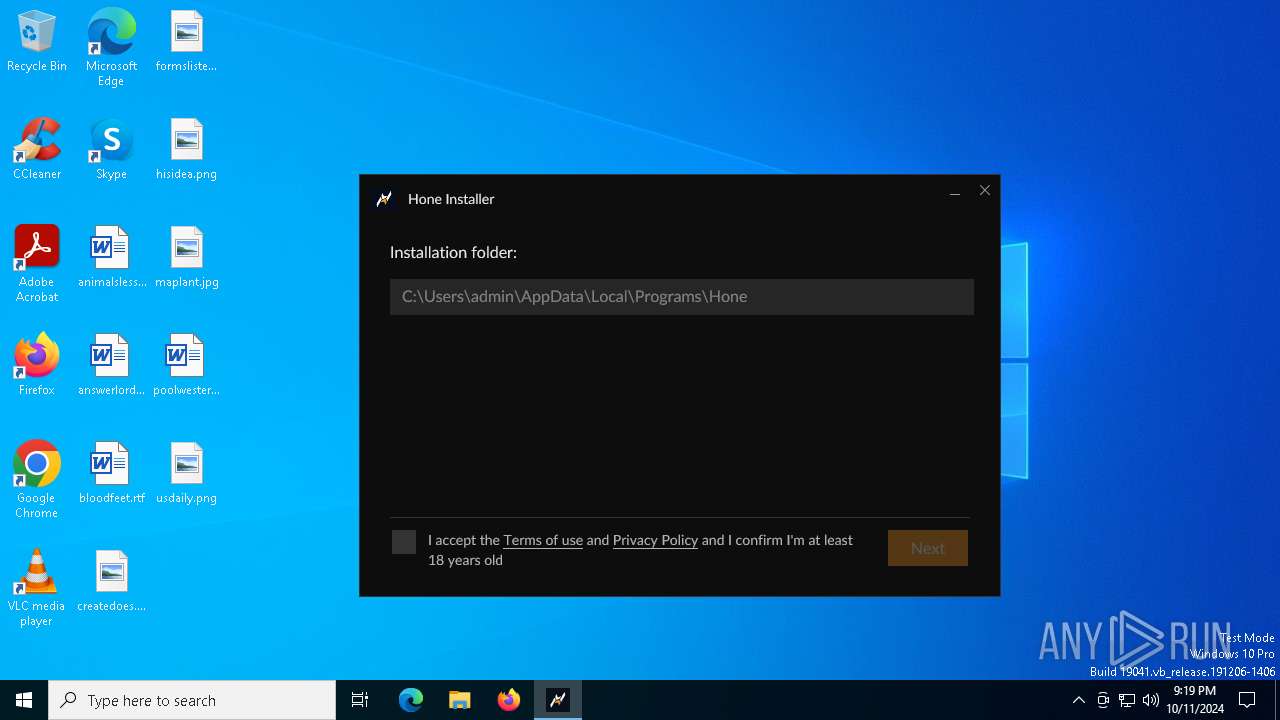
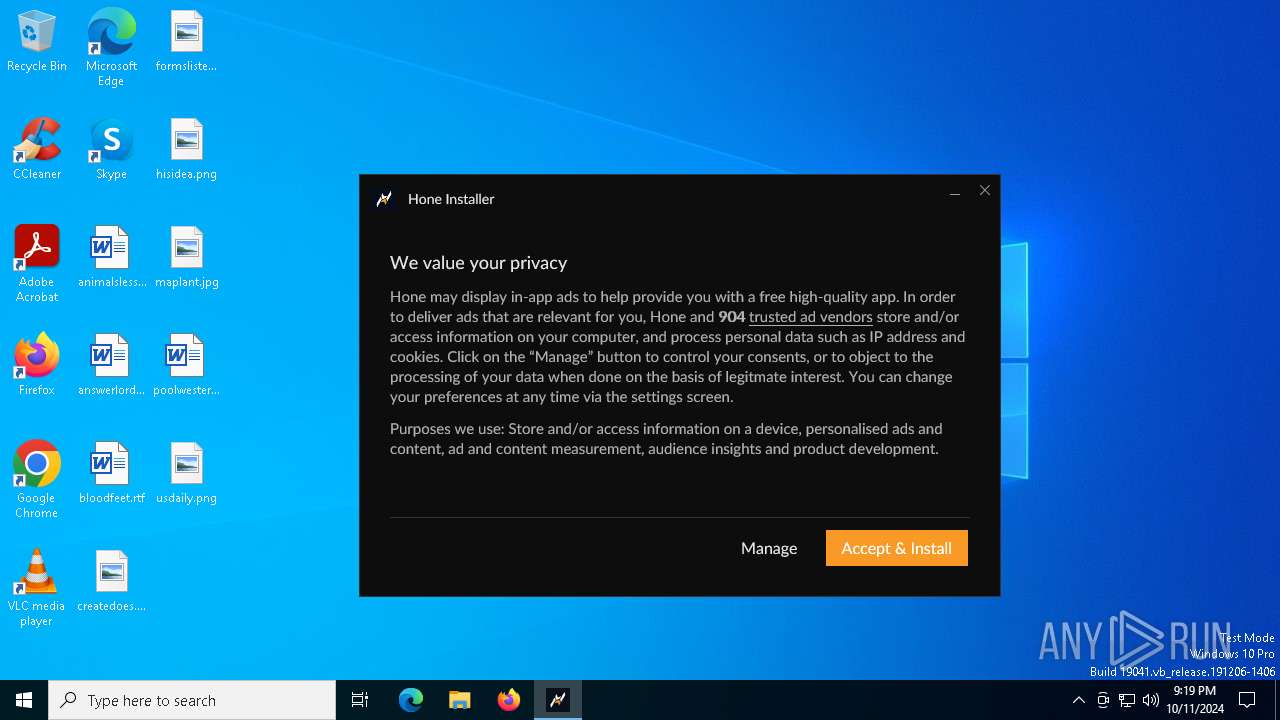
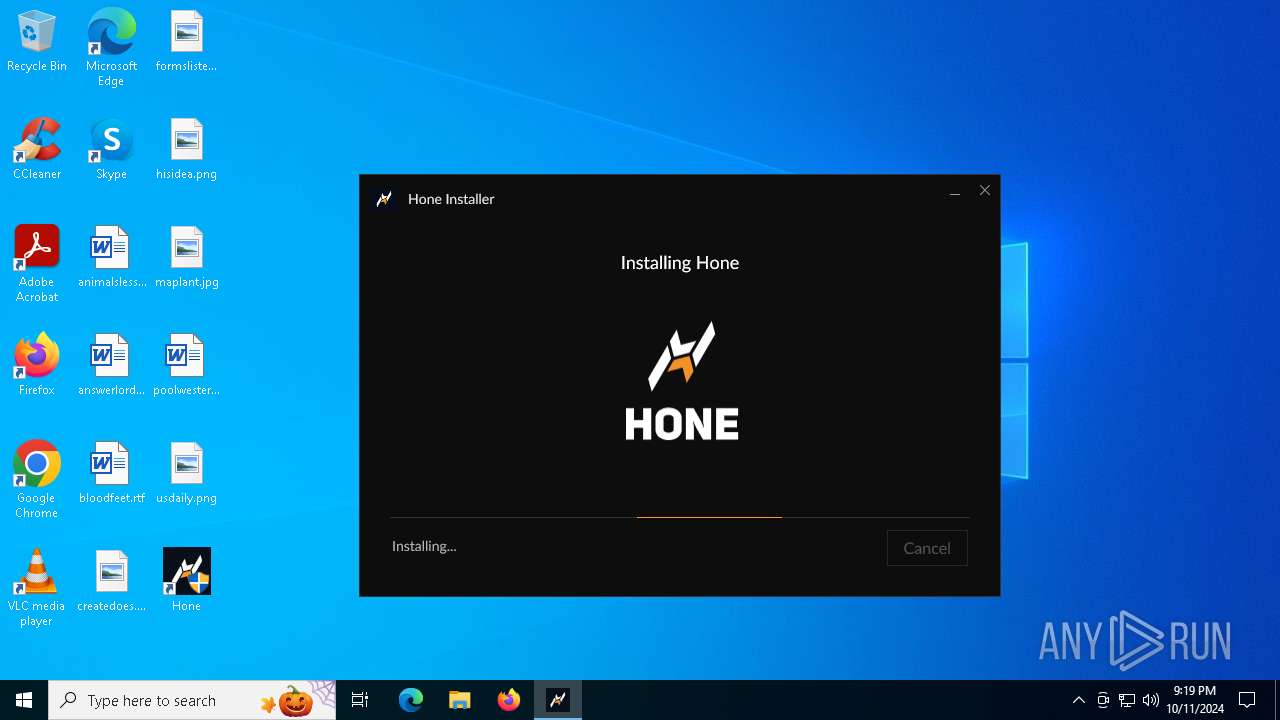
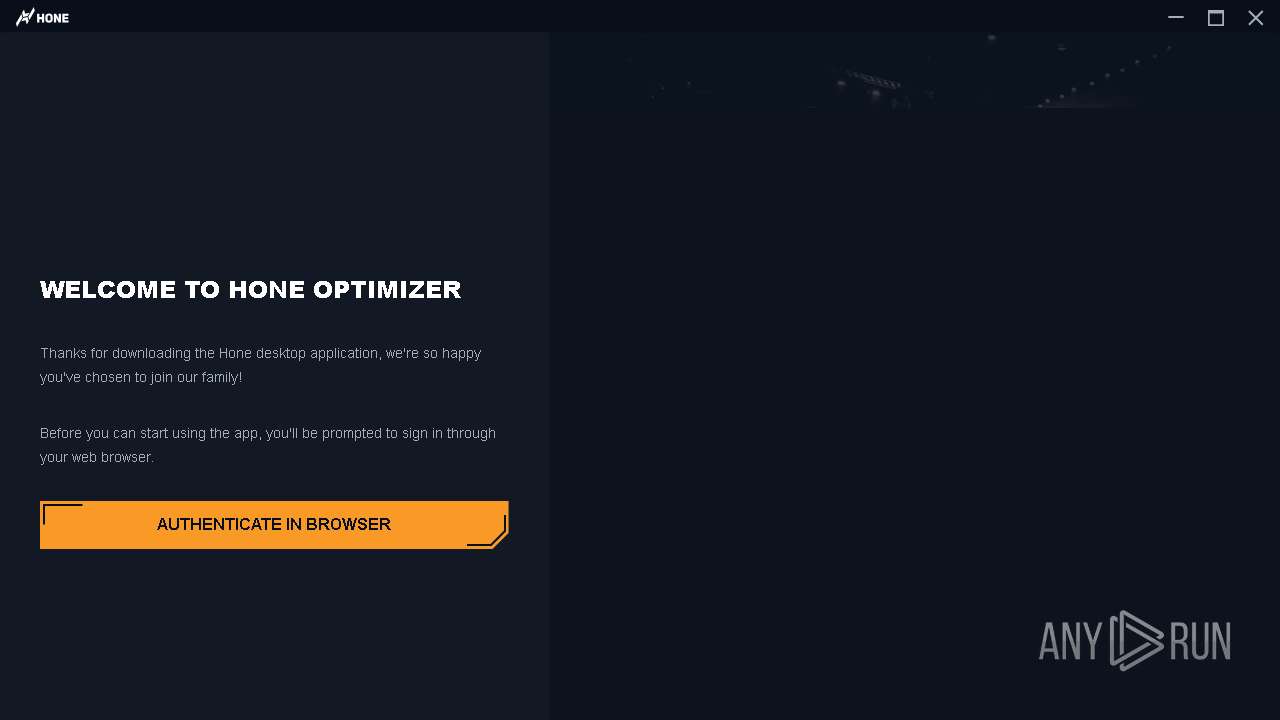
| File name: | Hone - Installer.exe |
| Full analysis: | https://app.any.run/tasks/b17a18e9-046b-4c19-aae6-53770190e35a |
| Verdict: | Malicious activity |
| Analysis date: | October 11, 2024, 21:18:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 01011FFA7010AA0EBE066B12E246DD8D |
| SHA1: | D84213457340D775FAA40DAD74FC5941380BC28F |
| SHA256: | E0E18234E3B35290E6ACFDE525A55376A45B59683A70EF5129F626455EAA446F |
| SSDEEP: | 98304:a/HapPJ/A9nGcRa1xXcVsy3RxeLLCIJgap176MVhjE5fWHkVv8d1BfOwiVs/vZah:qai |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- Hone.exe (PID: 3432)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 7852)
Bypass execution policy to execute commands
- powershell.exe (PID: 8144)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 7764)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Hone - Installer.exe (PID: 6024)
- Hone - Installer.exe (PID: 5932)
- ow-electron-setup.exe (PID: 4308)
Drops 7-zip archiver for unpacking
- Hone - Installer.exe (PID: 6024)
- Hone - Installer.exe (PID: 5932)
- ow-electron-setup.exe (PID: 4308)
Executable content was dropped or overwritten
- Hone - Installer.exe (PID: 6024)
- Hone - Installer.exe (PID: 5932)
- ow-electron-setup.exe (PID: 4308)
- Hone.exe (PID: 7452)
The process creates files with name similar to system file names
- Hone - Installer.exe (PID: 6024)
Application launched itself
- Hone - Installer.exe (PID: 6024)
- Hone.exe (PID: 3432)
Reads security settings of Internet Explorer
- Hone - Installer.exe (PID: 6024)
The process drops C-runtime libraries
- ow-electron-setup.exe (PID: 4308)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5068)
- cmd.exe (PID: 7120)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 6896)
Starts CMD.EXE for commands execution
- Hone.exe (PID: 3432)
- ow-electron-setup.exe (PID: 4308)
The process bypasses the loading of PowerShell profile settings
- Hone.exe (PID: 3432)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 7852)
The process hides Powershell's copyright startup banner
- Hone.exe (PID: 3432)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 7852)
Starts POWERSHELL.EXE for commands execution
- Hone.exe (PID: 3432)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 5920)
- cmd.exe (PID: 7852)
Drops a system driver (possible attempt to evade defenses)
- ow-electron-setup.exe (PID: 4308)
The process executes Powershell scripts
- cmd.exe (PID: 7524)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 5920)
- cmd.exe (PID: 7852)
The process hide an interactive prompt from the user
- cmd.exe (PID: 8060)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 7852)
Get information on the list of running processes
- cmd.exe (PID: 1372)
- ow-electron-setup.exe (PID: 4308)
Process drops legitimate windows executable
- ow-electron-setup.exe (PID: 4308)
INFO
Checks supported languages
- Hone - Installer.exe (PID: 6024)
Create files in a temporary directory
- Hone - Installer.exe (PID: 6024)
Process checks computer location settings
- Hone - Installer.exe (PID: 6024)
Reads the computer name
- Hone - Installer.exe (PID: 6024)
Manual execution by a user
- Hone.exe (PID: 7036)
- Hone.exe (PID: 3432)
- msedge.exe (PID: 7332)
Application launched itself
- msedge.exe (PID: 8040)
- msedge.exe (PID: 7332)
- msedge.exe (PID: 7588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.261.0.3 |
| ProductVersionNumber: | 2.261.0.3 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Overwolf Ltd. |
| FileDescription: | Hone |
| FileVersion: | 2.261.0.3 |
| LegalCopyright: | Copyright (C) 2021 Overwolf Ltd. All Rights Reserved. |
| LegalTrademarks: | - |
| ProductName: | Hone |
| ProductVersion: | 2.261.0.3 |
Total processes
240
Monitored processes
104
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5180 --field-trial-handle=2296,i,7020212362868817,3901175683731996294,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 784 | reg add "hklm\Software\Classes\hone" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1172 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2648 --field-trial-handle=2296,i,7020212362868817,3901175683731996294,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1176 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | C:\WINDOWS\system32\cmd.exe /d /s /c "reg add "hklm\Software\Classes\hone" /v "URL Protocol" /t REG_SZ /d "" /f" | C:\Windows\System32\cmd.exe | — | Hone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2292 --field-trial-handle=2296,i,7020212362868817,3901175683731996294,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1372 | "C:\WINDOWS\system32\cmd.exe" /c tasklist /FI "USERNAME eq %USERNAME%" /FI "IMAGENAME eq Hone.exe" /FO csv | "C:\WINDOWS\system32\find.exe" "Hone.exe" | C:\Windows\SysWOW64\cmd.exe | — | ow-electron-setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2056 | C:\WINDOWS\system32\cmd.exe /d /s /c "reg query "hklm\Software\Classes\hone" 2> nul" | C:\Windows\System32\cmd.exe | — | Hone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
48 782
Read events
48 692
Write events
70
Delete events
20
Modification events
| (PID) Process: | (5932) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5932) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5932) Hone - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6660) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Overwolf |
| Operation: | write | Name: | MUID |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (6660) OWInstaller.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\OverwolfElectron |
| Operation: | write | Name: | MUID |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (6660) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6660) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6660) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6660) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6660) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
126
Suspicious files
290
Text files
240
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\websocket-sharp.dll | executable | |
MD5:28838B57A9F9E05C63C0EF96E3635D2A | SHA256:92C58929510D037E77D8DD10F7ECB0CB3E588525A6B3AE1A6FBC449A896D16B9 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\nsProcess.dll | executable | |
MD5:10E47E822B85D2A12FA4727001612182 | SHA256:D530589A90918334B8E08D7355630892DD62F41333D948A860735D5BECFCB391 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\UserInfo.dll | executable | |
MD5:1DD4CA0F4A94155F8D46EC95A20ADA4A | SHA256:A27DC3069793535CB64123C27DCA8748983D133C8FA5AADDEE8CDBC83F16986D | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\uac.dll | executable | |
MD5:861F7E800BB28F68927E65719869409C | SHA256:10A0E8CF46038AB3B2C3CF5DCE407B9A043A631CBDE9A5C8BCF0A54B2566C010 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\Newtonsoft.Json.dll | executable | |
MD5:98CBB64F074DC600B23A2EE1A0F46448 | SHA256:7B44639CBFBC8DDAC8C7A3DE8FFA97A7460BEBB0D54E9FF2E1CCDC3A742C2B13 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\log4net.dll | executable | |
MD5:F15C8A9E2876568B3910189B2D493706 | SHA256:AE9C8073C3357C490F5D1C64101362918357C568F6B9380A60B09A4A4C1FF309 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\OverWolf.Client.CommonUtils.dll | executable | |
MD5:7D584940A66AAB5447EFE1E902E22404 | SHA256:4F90E211C47C3C8849AF671DCF13524F58839AC63CF4AB7CA3C4BB6F77BED246 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\Microsoft.Win32.TaskScheduler.dll | executable | |
MD5:4AFA0E645D87DB538A8998A9AA7E4571 | SHA256:81ED9A92B6122DAD85A1550273D663D3E8B56094FB14E07C04BFFED81BBDF453 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\OWInstaller.exe.config | xml | |
MD5:82D22E4E19E27E306317513B9BFA70FF | SHA256:272E4C5364193E73633CAA3793E07509A349B79314EA01808B24FDB12C51B827 | |||
| 6024 | Hone - Installer.exe | C:\Users\admin\AppData\Local\Temp\nslBD5E.tmp\CommandLine.dll | executable | |
MD5:84DCF802B8813A746374AB7C4CD1E37B | SHA256:65C2F0B197252A03B4CB3BA1242FEBA8A05AFF2C684A29D8FB820D5CE57998DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
136
DNS requests
98
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5932 | Hone - Installer.exe | GET | 200 | 18.244.18.46:80 | http://analyticsnew.overwolf.com/analytics/Counter?Name=installer_uac_action&Value=1&&Extra=%5b%7b%22Name%22%3a%22installer_version%22%2c%22Value%22%3a%222.261.0.3%22%7d%5d | unknown | — | — | whitelisted |
6660 | OWInstaller.exe | GET | 200 | 216.58.206.78:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=895875288&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=406267333&utmr=/&utmp=/&utmac=UA-80584726-1&utmcc=__utma%3D0.2091849097.1728681536.1728681536.1728681536.2%3B%2B__utmz%3D0.1728681536.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6660 | OWInstaller.exe | GET | 200 | 216.58.206.78:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=502203835&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=760921731&utmr=/&utmp=/&utmac=UA-18298709-8&utmcc=__utma%3D0.2091849097.1728681536.1728681536.1728681536.2%3B%2B__utmz%3D0.1728681536.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
6660 | OWInstaller.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca3.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRkNawYMzz%2BjKSfYbTyFR0AXuhs6QQUq7bb1waeN6wwhgeRcMecxBmxeMACEwdzEm3iwvr9LEetiLFWbgGCBG0%3D | unknown | — | — | unknown |
6660 | OWInstaller.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
6660 | OWInstaller.exe | GET | 200 | 142.250.186.99:80 | http://o.pki.goog/wr2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEQCMIoSniFj39BAtXGMIdqpm | unknown | — | — | whitelisted |
6660 | OWInstaller.exe | GET | 200 | 142.250.186.99:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACECX6MgWg0QhIEt9Tgf8DZ5Y%3D | unknown | — | — | whitelisted |
6660 | OWInstaller.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7060 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5932 | Hone - Installer.exe | 18.244.18.46:80 | analyticsnew.overwolf.com | — | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6660 | OWInstaller.exe | 216.58.206.78:80 | google.com | GOOGLE | US | whitelisted |
6660 | OWInstaller.exe | 18.244.18.46:443 | analyticsnew.overwolf.com | — | US | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
analyticsnew.overwolf.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
content.overwolf.com |
| whitelisted |
ocsp.rootca3.amazontrust.com |
| unknown |
th.bing.com |
| whitelisted |
storeapi.overwolf.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5932 | Hone - Installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2 ETPRO signatures available at the full report