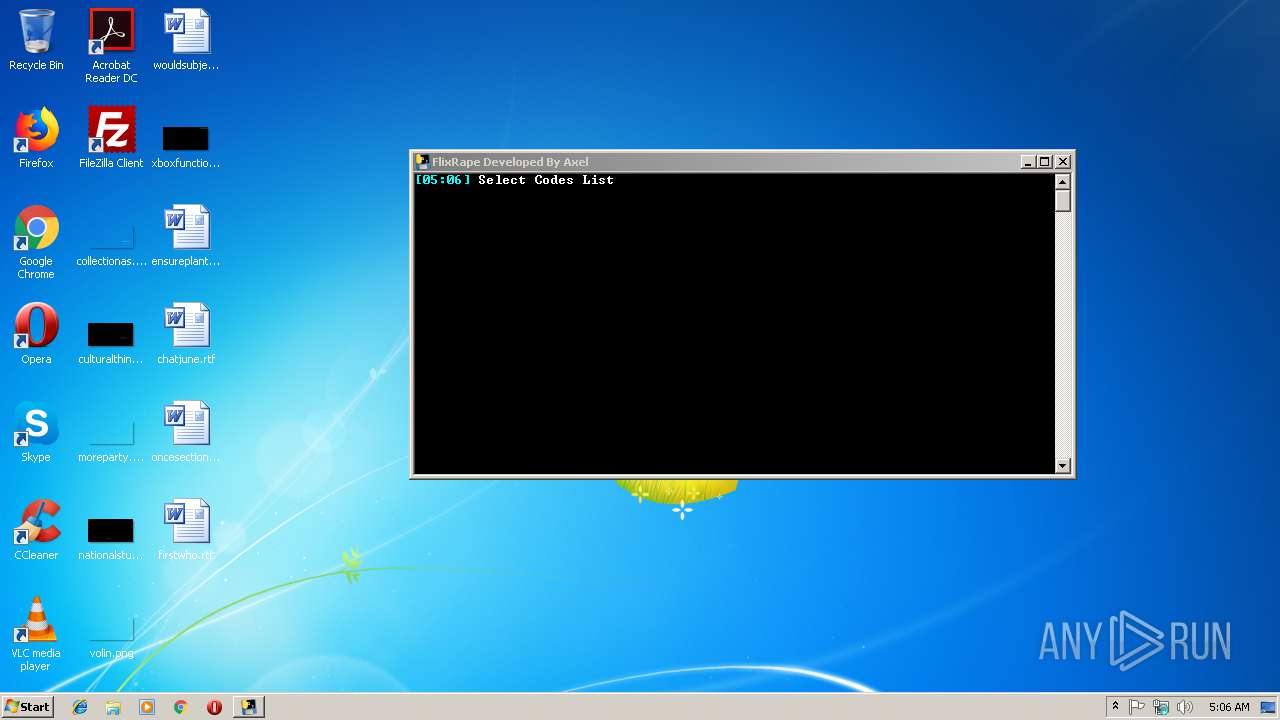
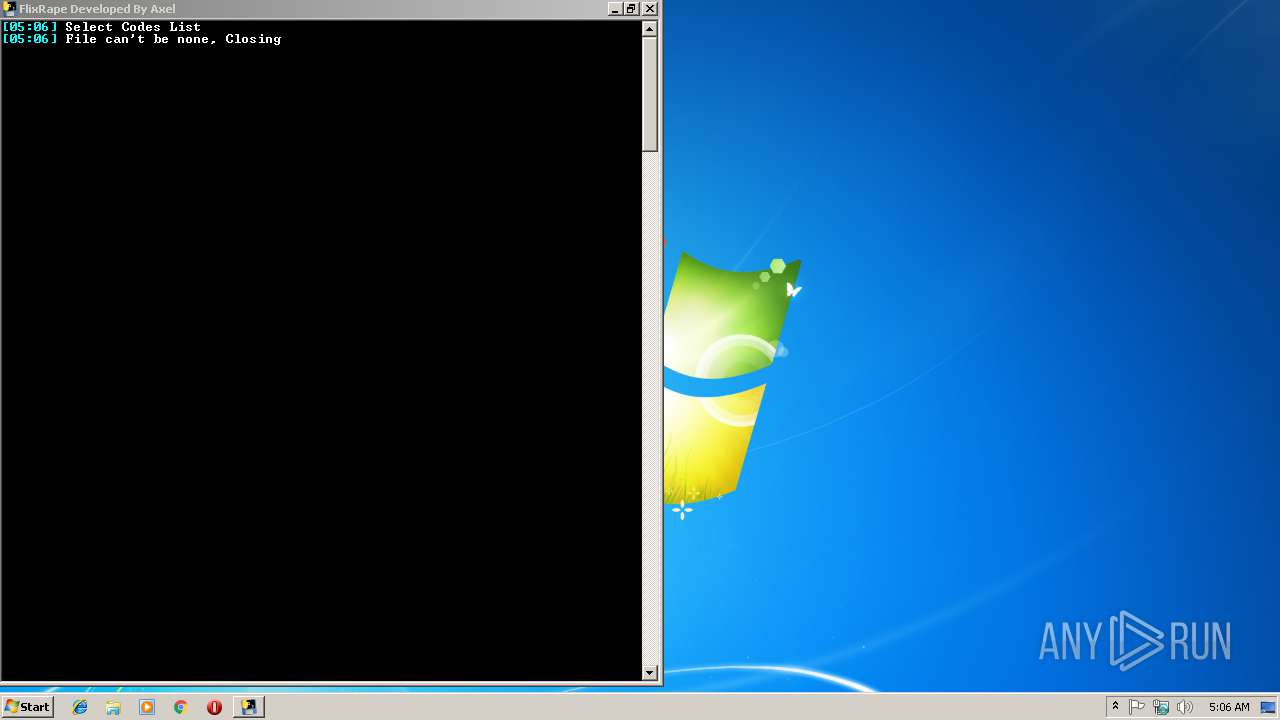
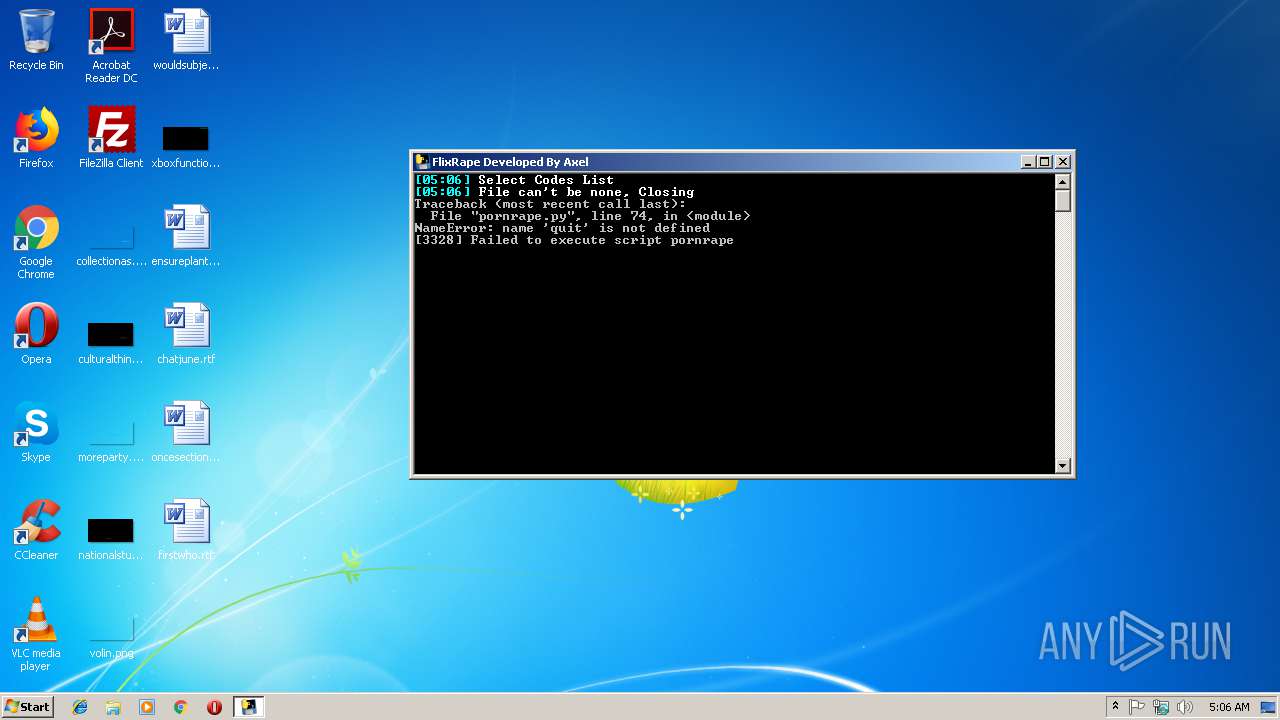
| File name: | FlixRape.exe |
| Full analysis: | https://app.any.run/tasks/13551c95-417a-43f1-befb-52195834e2f0 |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 05:05:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 6607B4D4BEE1C76CE2D62EF99A135289 |
| SHA1: | 7DB46B3873D9AF6550458077CFACDD253289F2E9 |
| SHA256: | E0D03EEC01589CED0B2872638650E5B1A1E83DEA526A9AB304DDF9D8BCE9CD31 |
| SSDEEP: | 196608:aGMMewaX5sBwaIaw48KwFqAZnaWTXS6SxndnZabT6jYSpW56X9j63KDe8HvK5eG1:QMhaX5sBwKwGAZ9Zsn7iI5rjM5eFVY5 |
MALICIOUS
Loads dropped or rewritten executable
- FlixRape.exe (PID: 3328)
SUSPICIOUS
Executable content was dropped or overwritten
- FlixRape.exe (PID: 3232)
Application launched itself
- FlixRape.exe (PID: 3232)
Starts CMD.EXE for commands execution
- FlixRape.exe (PID: 3328)
Loads Python modules
- FlixRape.exe (PID: 3328)
INFO
Dropped object may contain Bitcoin addresses
- FlixRape.exe (PID: 3232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:12:11 16:09:08+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 127488 |
| InitializedDataSize: | 172032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x769a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 11-Dec-2017 15:09:08 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 11-Dec-2017 15:09:08 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001F144 | 0x0001F200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.66103 |
.rdata | 0x00021000 | 0x0000B06C | 0x0000B200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.0856 |
.data | 0x0002D000 | 0x0000E678 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.93451 |
.gfids | 0x0003C000 | 0x000000B8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.85613 |
.rsrc | 0x0003D000 | 0x0000EA38 | 0x0000EC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.29706 |
.reloc | 0x0004C000 | 0x000017B8 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.6361 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.58652 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
2 | 6.05629 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 5.5741 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 7.95079 | 37019 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 5.29119 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 5.43869 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 5.89356 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
101 | 2.71858 | 104 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
KERNEL32.dll |
WS2_32.dll |
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2408 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\system32\cmd.exe | — | FlixRape.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3232 | "C:\Users\admin\AppData\Local\Temp\FlixRape.exe" | C:\Users\admin\AppData\Local\Temp\FlixRape.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 3328 | "C:\Users\admin\AppData\Local\Temp\FlixRape.exe" | C:\Users\admin\AppData\Local\Temp\FlixRape.exe | — | FlixRape.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
569
Read events
527
Write events
41
Delete events
1
Modification events
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0700000000000000010000000200000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\0 |
| Operation: | write | Name: | 1 |
Value: 4A003100000000004B4ECF28102054656D700000360008000400EFBE454B814A4B4ECF282A00000090010000000002000000000000000000000000000000540065006D007000000014000000 | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000FFFFFFFF | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\0\1 |
| Operation: | write | Name: | NodeSlot |
Value: 95 | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\0\1 |
| Operation: | write | Name: | MRUListEx |
Value: FFFFFFFF | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\95\Shell |
| Operation: | write | Name: | KnownFolderDerivedFolderType |
Value: {57807898-8C4F-4462-BB63-71042380B109} | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\95\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (3328) FlixRape.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
22
Suspicious files
1
Text files
913
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\_tkinter.pyd | executable | |
MD5:— | SHA256:— | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\bcrypt._bcrypt.pyd | executable | |
MD5:— | SHA256:— | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\cryptography.hazmat.bindings._constant_time.pyd | executable | |
MD5:— | SHA256:— | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\cryptography.hazmat.bindings._openssl.pyd | executable | |
MD5:— | SHA256:— | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\lxml._elementpath.pyd | executable | |
MD5:— | SHA256:— | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\VCRUNTIME140.dll | executable | |
MD5:A2523EA6950E248CBDF18C9EA1A844F6 | SHA256:6823B98C3E922490A2F97F54862D32193900077E49F0360522B19E06E6DA24B4 | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\_lzma.pyd | executable | |
MD5:7C97599E2CA514B2787C3E5BCA56A7B8 | SHA256:B4271370F7A93B767B1E57ED3889B84D088CD2606B7715B68EE06A6A280E1BCC | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\_cffi_backend.pyd | executable | |
MD5:7BFFCF7C75E45FFABB1599D6B13B4882 | SHA256:3FAF98FAFBB7EE72C2F7357AFFF62848FBE3570150B93387F00D7137505D4003 | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\_decimal.pyd | executable | |
MD5:378DFBBDFD14E72AD8776318137B3684 | SHA256:04A7BBE7054C35332A43C354D55185380ABC26F2E3511F5A02FF5F155C549E73 | |||
| 3232 | FlixRape.exe | C:\Users\admin\AppData\Local\Temp\_MEI32322\_socket.pyd | executable | |
MD5:17B184F3427547207FE93C8B5A5450F3 | SHA256:FDBAA83954B6C165EF7D2588D3B3AB2EB6C0A12AABBBB7477CE8C19BFD01D537 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report