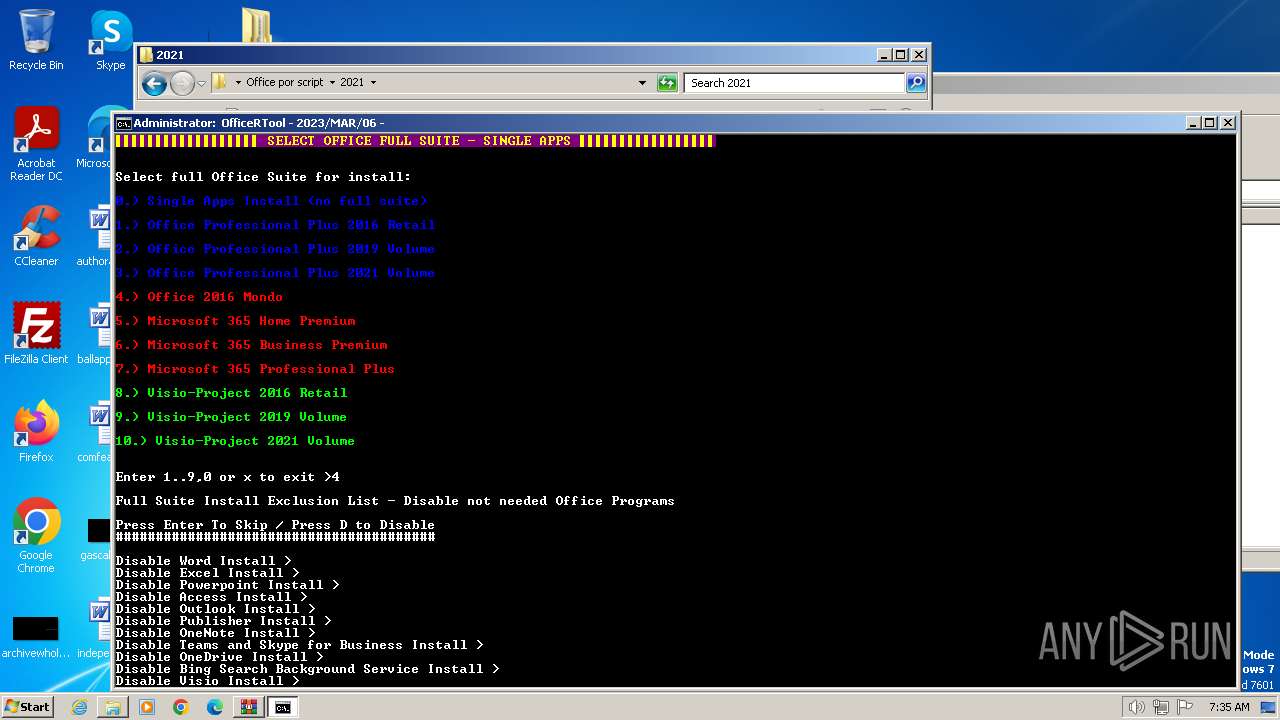
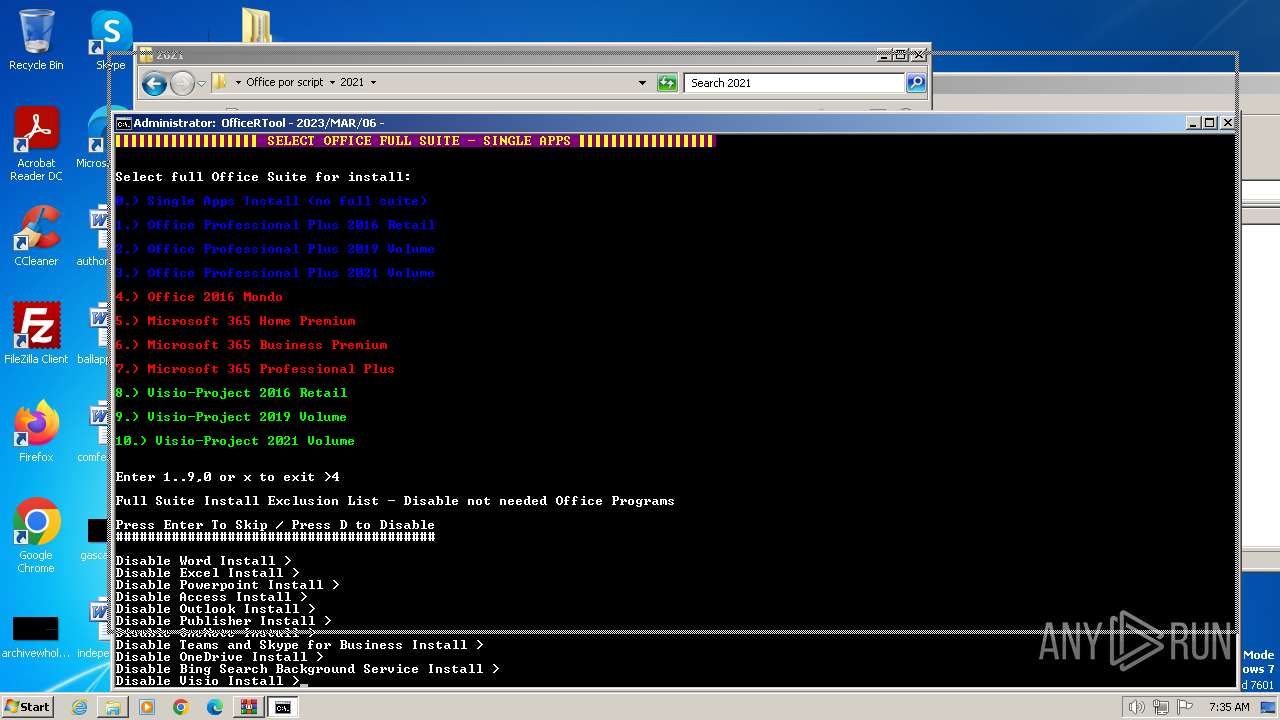
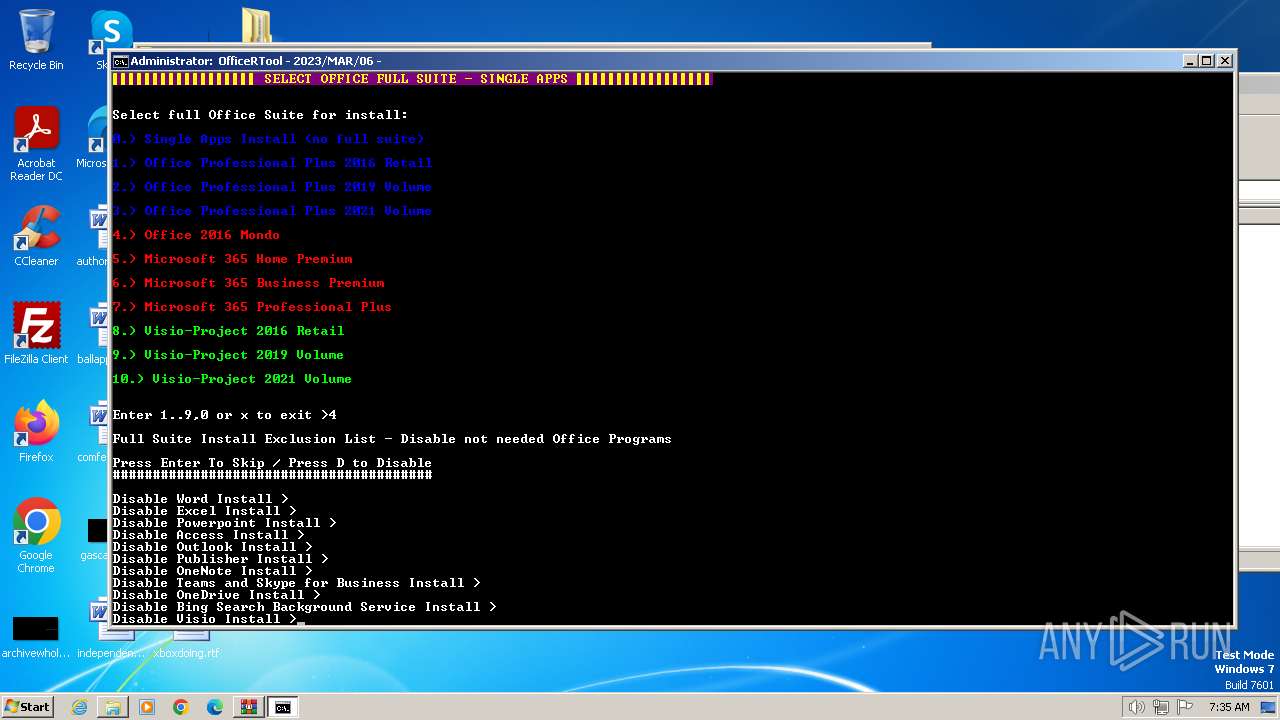
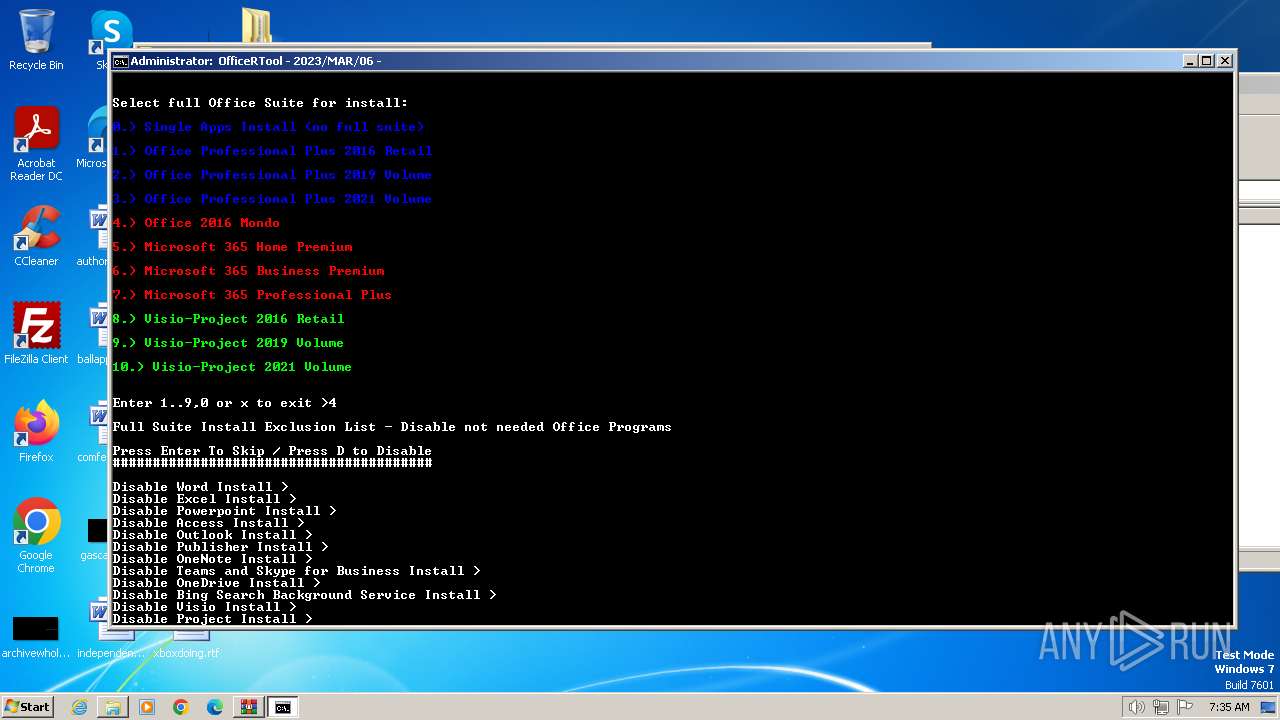
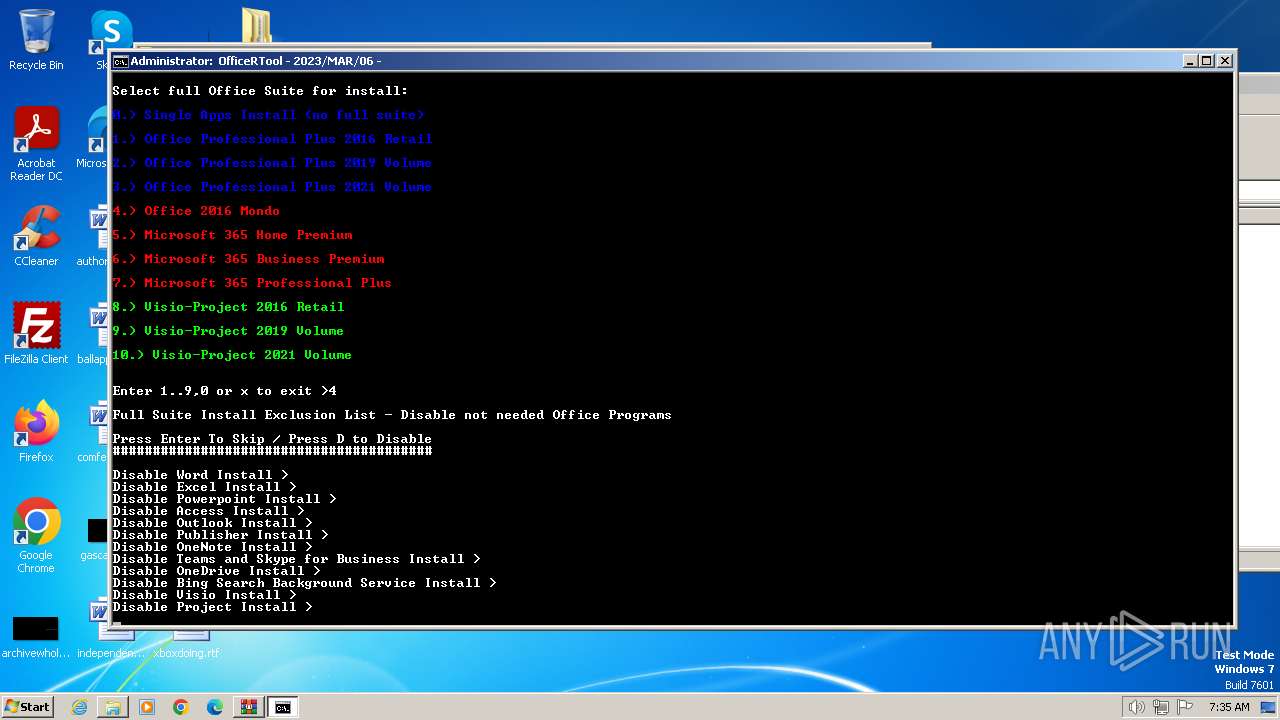
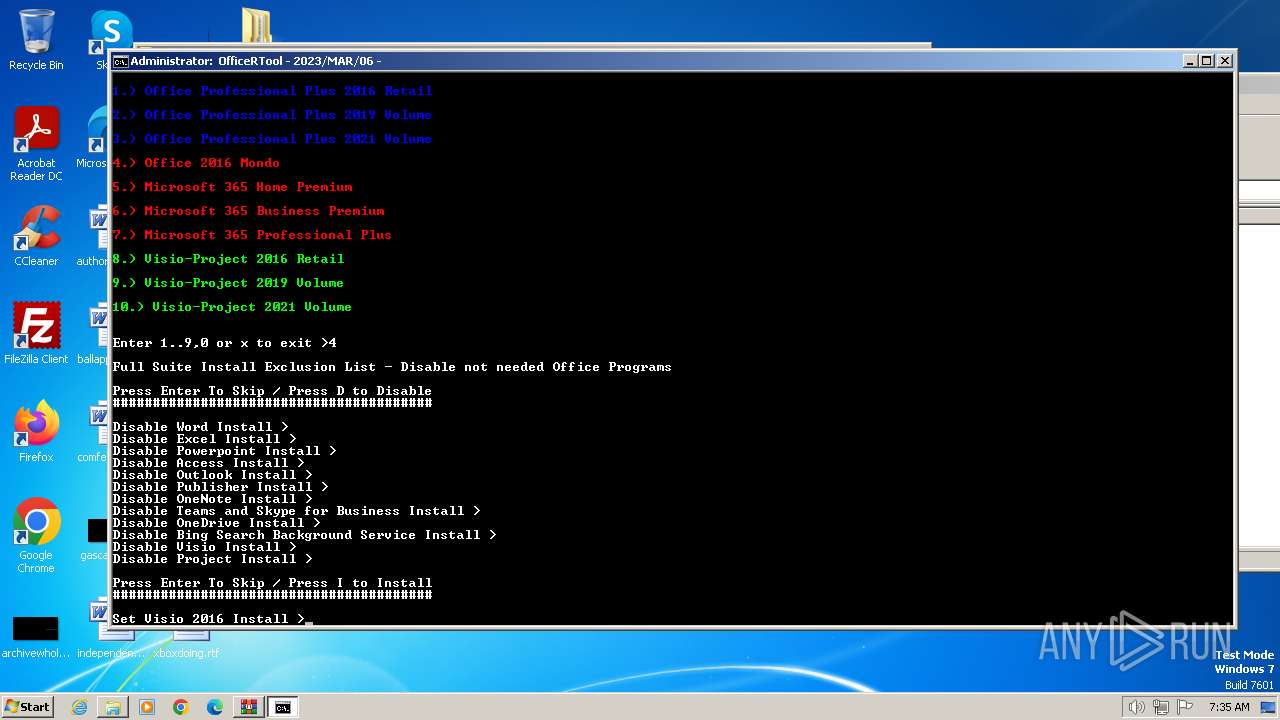
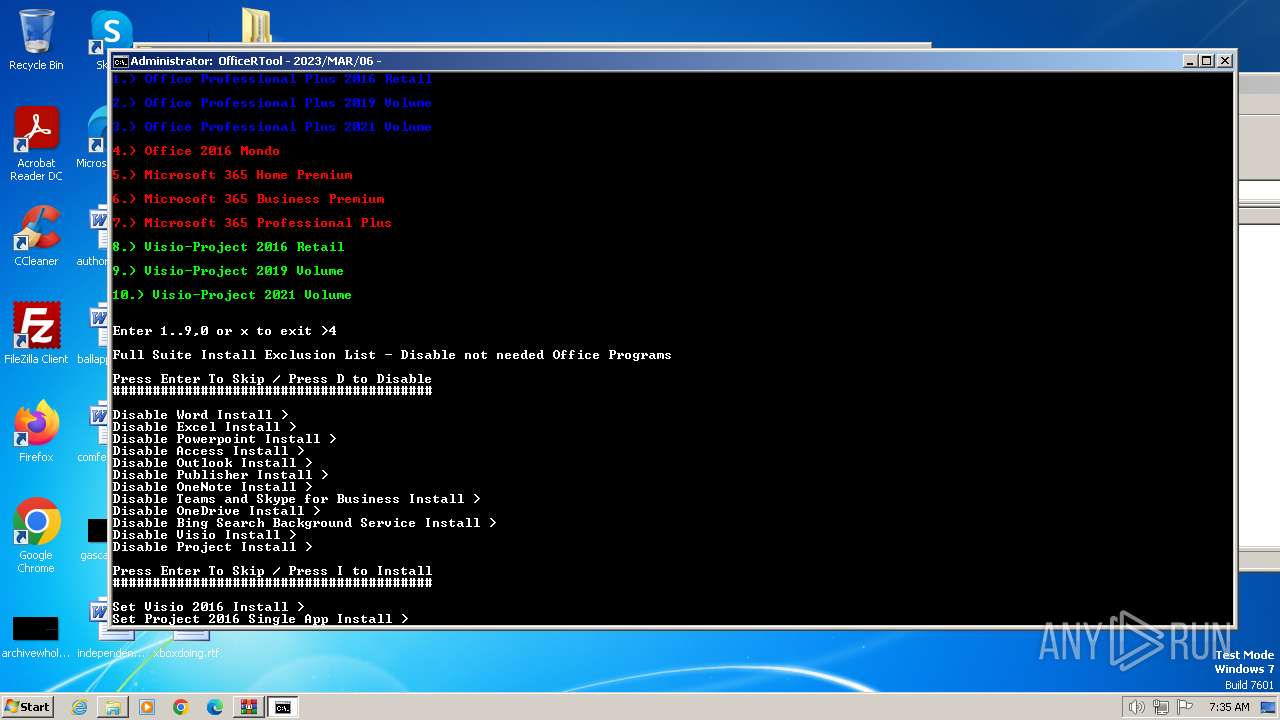
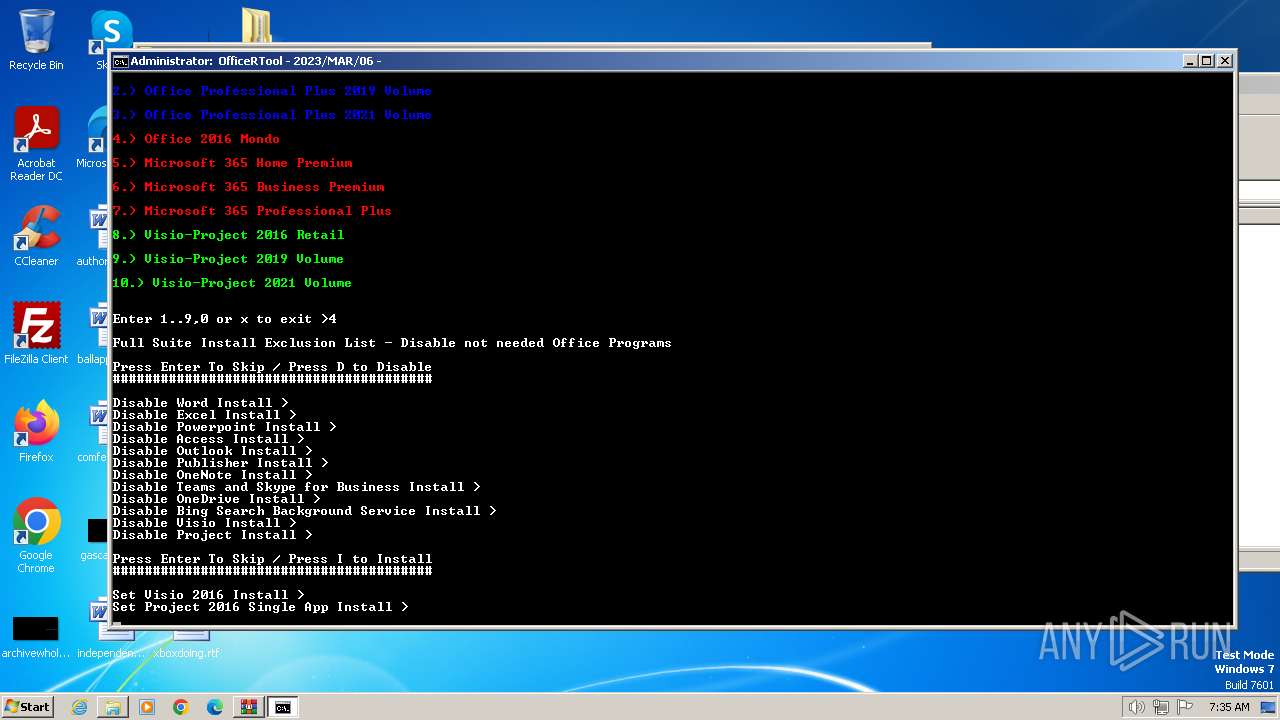
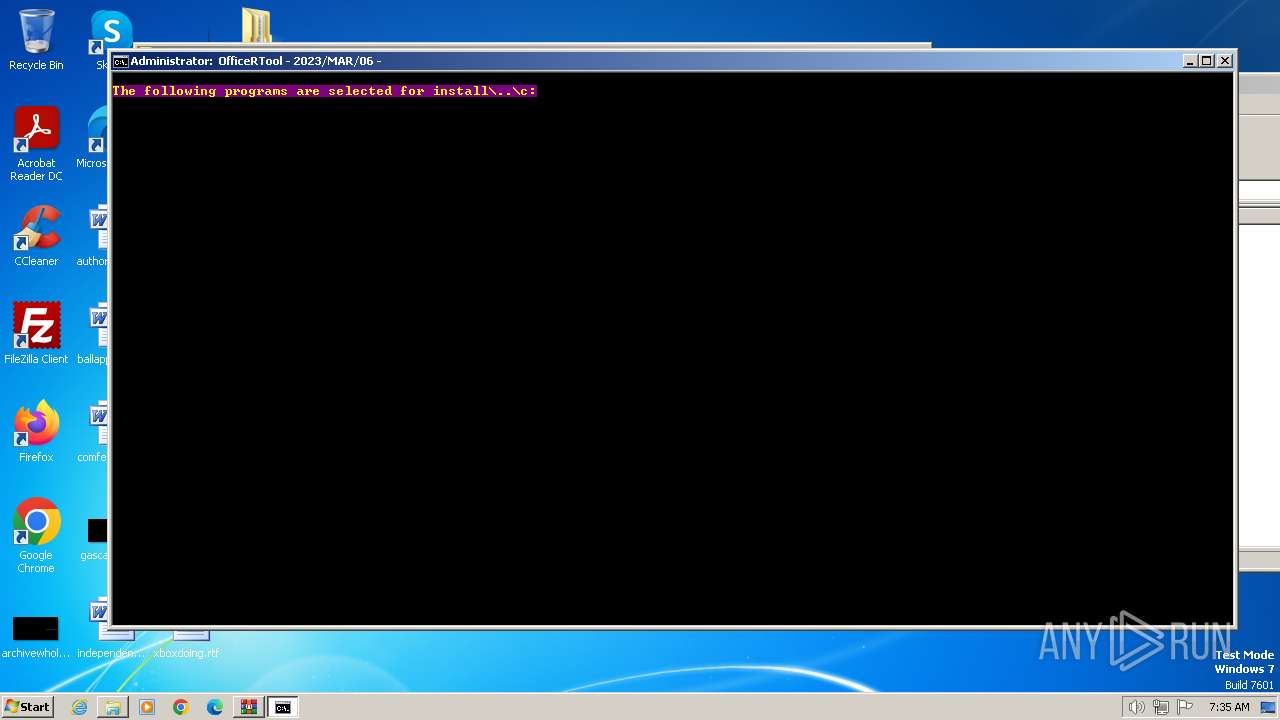
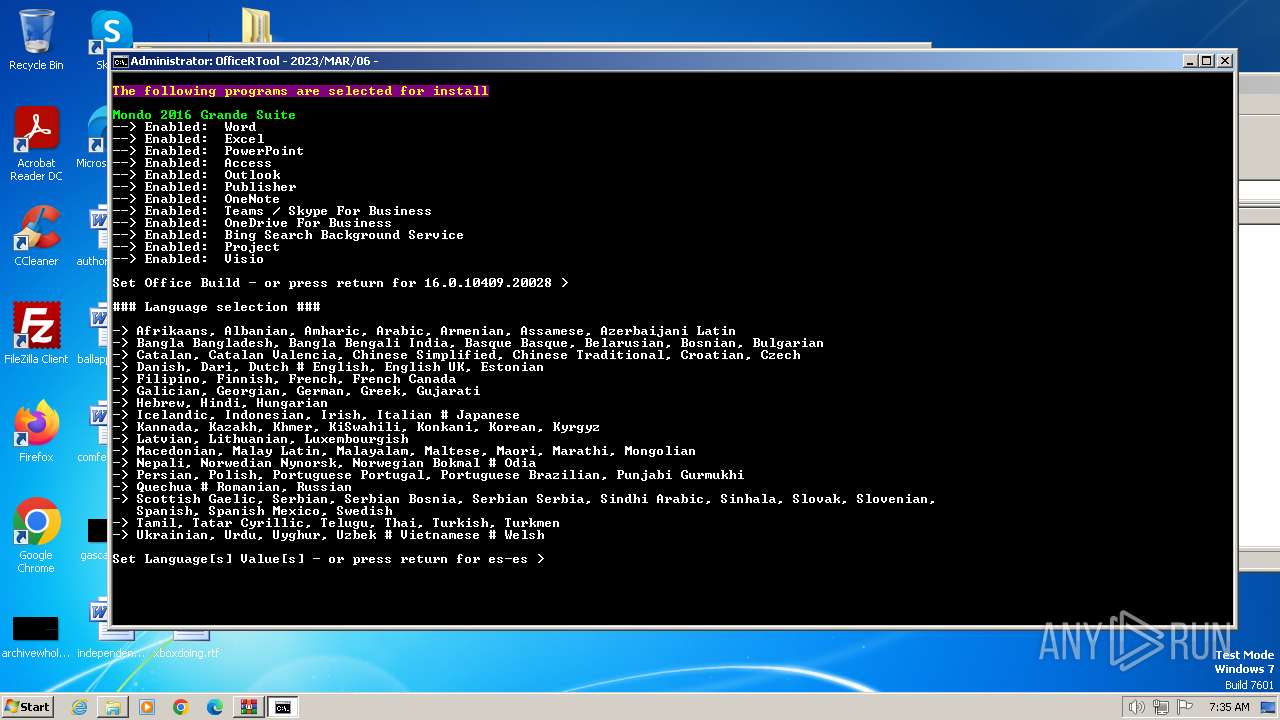
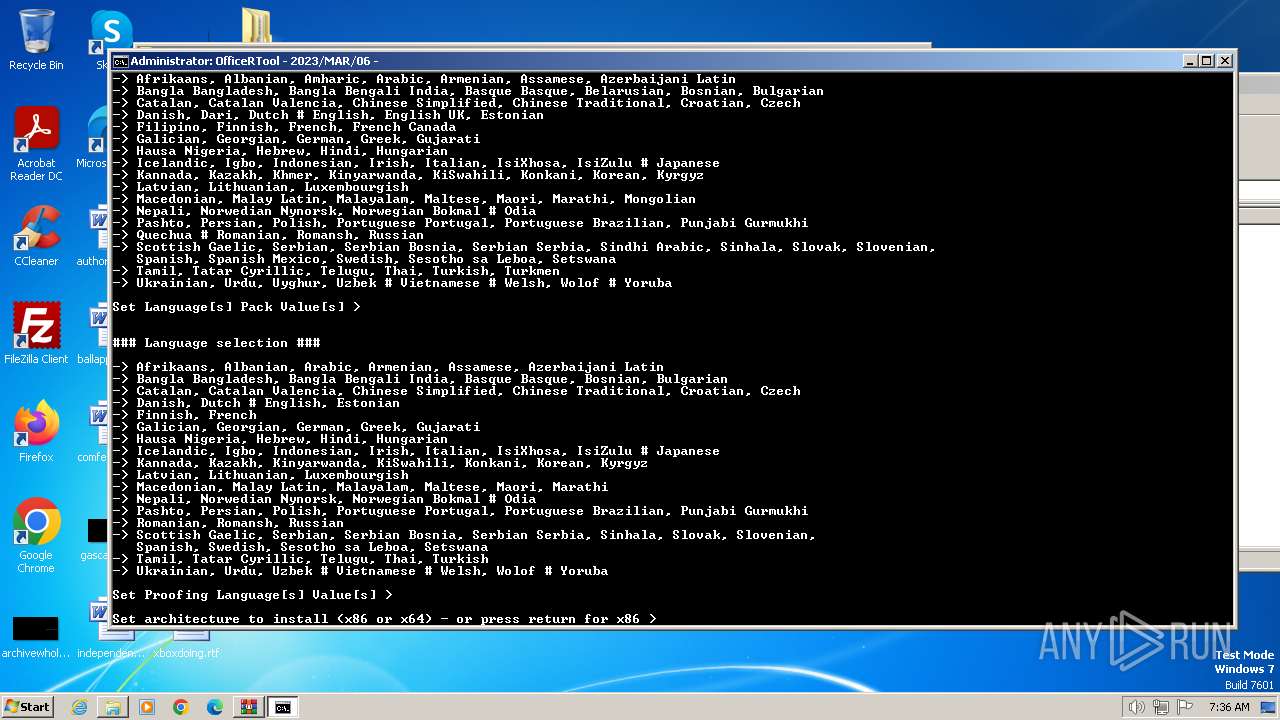
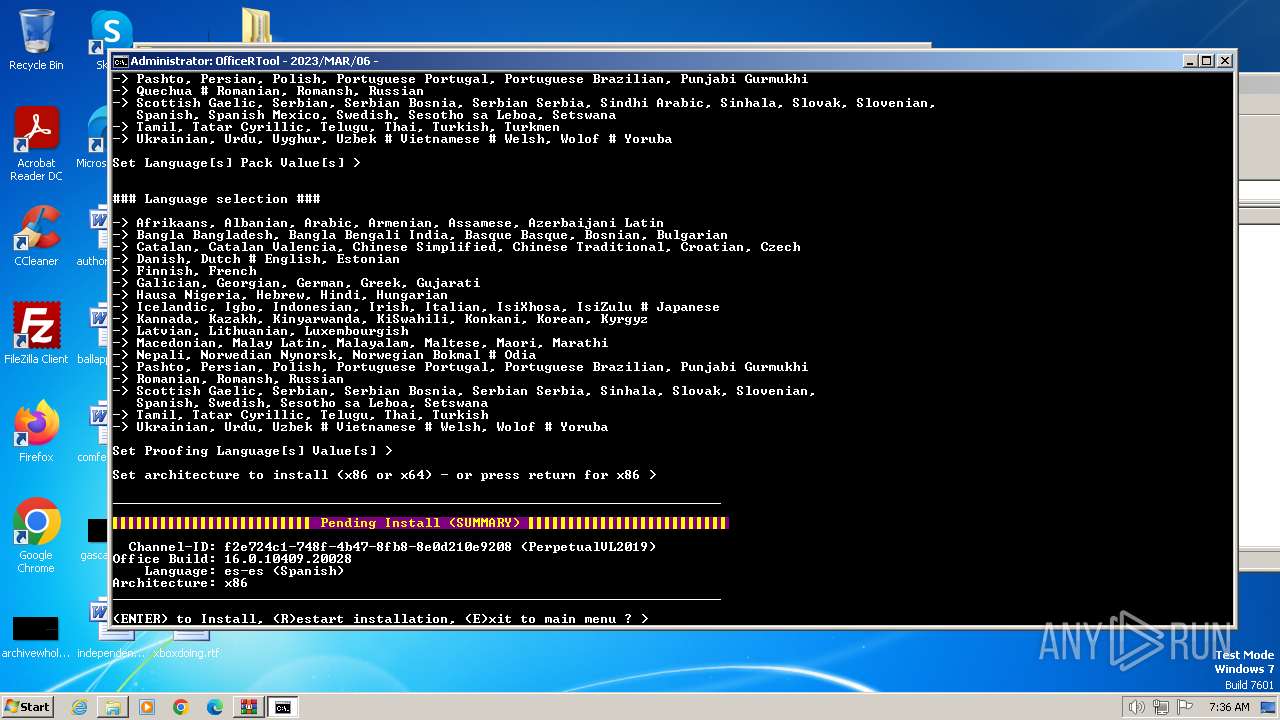
| File name: | Office por script.rar |
| Full analysis: | https://app.any.run/tasks/1b4462f2-7be8-4543-810a-5a212420778a |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2024, 06:33:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5E2D1BD62DF0BD5D7F86AEEB13C25FB0 |
| SHA1: | F715368B1722CB6EE5811C52F08944347BE74C98 |
| SHA256: | E0924BF8DAC1A147718E6AFA95BAB4E2CA2D91984CFA70DC0C703339597A2188 |
| SSDEEP: | 98304:OX9TcbvJKCP5xJzUxf2A83TY2CIegUVpRKnOzsv8gZV0SD9+9ANcZ+pq9RawWRqe:OTyUelQdNvkh44h4I9uO |
MALICIOUS
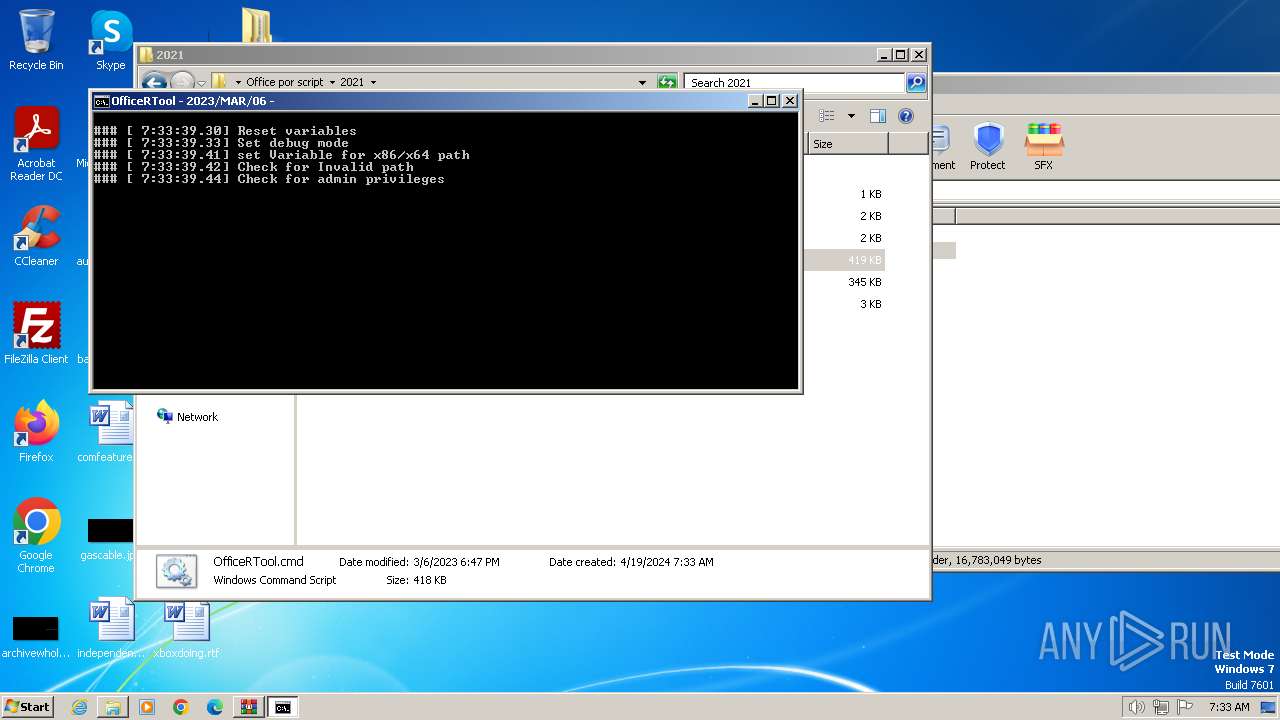
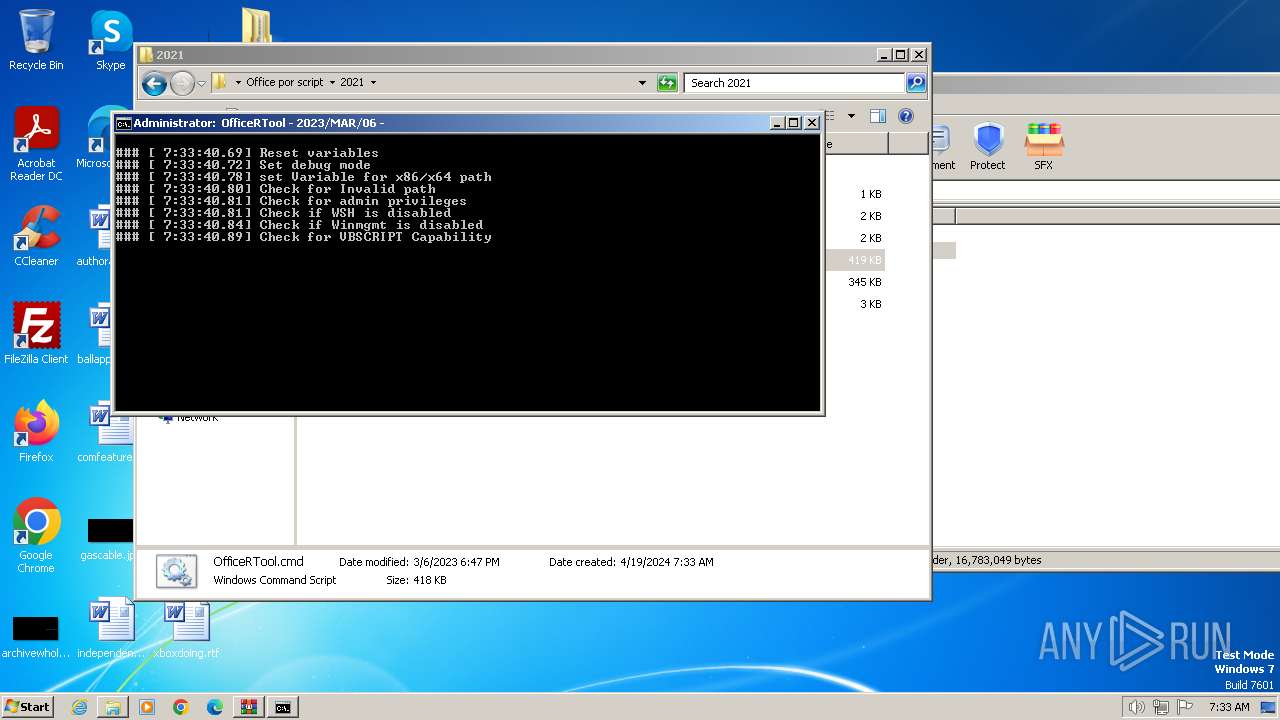
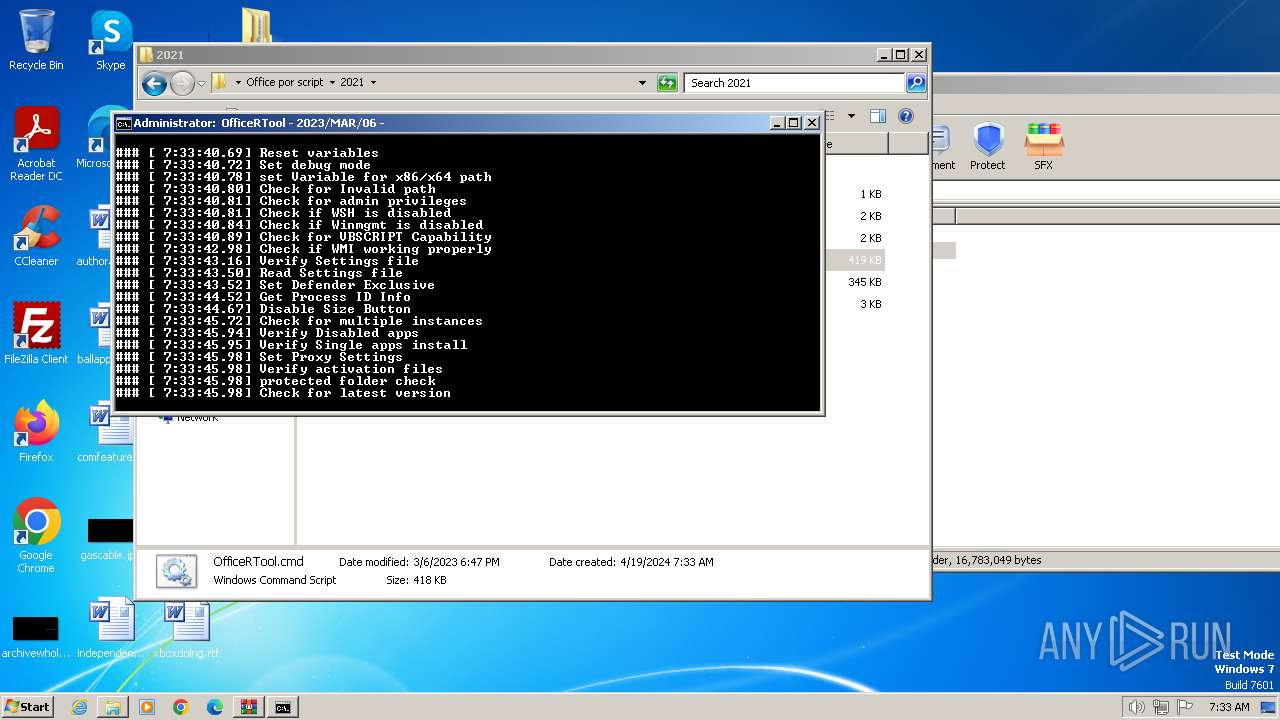
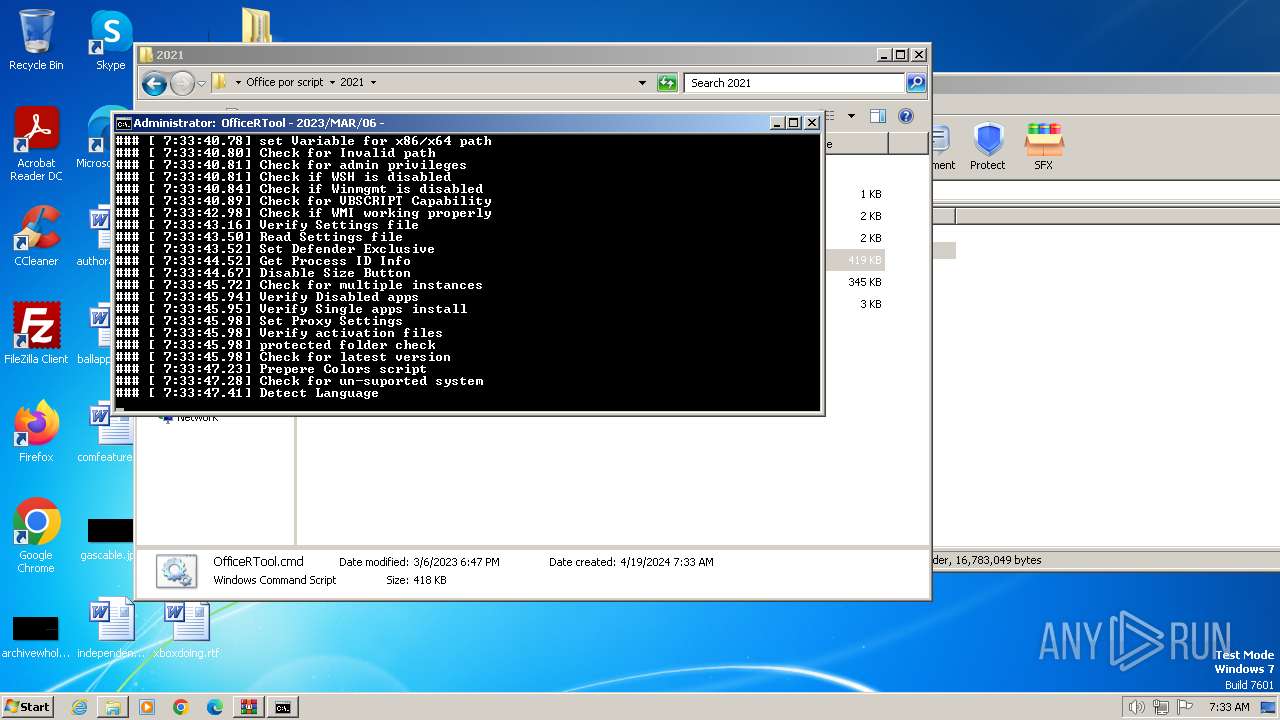
The DLL Hijacking
- DismHost.exe (PID: 3732)
- DismHost.exe (PID: 3748)
- DismHost.exe (PID: 3644)
Accesses Processor(Win32_Processor, may evade sandboxes) via WMI (SCRIPT)
- cscript.exe (PID: 1368)
- cscript.exe (PID: 2052)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3072)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3072)
Starts Visual C# compiler
- powershell.exe (PID: 3020)
Drops the executable file immediately after the start
- csc.exe (PID: 3844)
- cmd.exe (PID: 3072)
Bypass execution policy to execute commands
- powershell.exe (PID: 3020)
- powershell.exe (PID: 2124)
Run PowerShell with an invisible window
- powershell.exe (PID: 3972)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3768)
- Dism.exe (PID: 3104)
- Dism.exe (PID: 1924)
- Dism.exe (PID: 3696)
- cmd.exe (PID: 3072)
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 3768)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3592)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 924)
- powershell.exe (PID: 3612)
- cmd.exe (PID: 2920)
Application launched itself
- cmd.exe (PID: 3592)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 924)
- cmd.exe (PID: 2920)
Starts application with an unusual extension
- cmd.exe (PID: 3592)
- cmd.exe (PID: 3072)
Hides command output
- cmd.exe (PID: 572)
- cmd.exe (PID: 2156)
- cmd.exe (PID: 1336)
- cmd.exe (PID: 3916)
- cmd.exe (PID: 3288)
- cmd.exe (PID: 3900)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 3372)
- cmd.exe (PID: 2912)
- cmd.exe (PID: 2956)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 1928)
- cmd.exe (PID: 2956)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 572)
- cmd.exe (PID: 2156)
- cmd.exe (PID: 3592)
- cmd.exe (PID: 1336)
- cmd.exe (PID: 3916)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 956)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3592)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 3372)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 2956)
- setup.exe (PID: 376)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3592)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 3372)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 2956)
- setup.exe (PID: 376)
Reads the Internet Settings
- powershell.exe (PID: 3612)
- powershell.exe (PID: 3140)
- WMIC.exe (PID: 4076)
- WMIC.exe (PID: 3636)
- WMIC.exe (PID: 2148)
- powershell.exe (PID: 3420)
- powershell.exe (PID: 2124)
- cscript.exe (PID: 1876)
- powershell.exe (PID: 3972)
- setup.exe (PID: 376)
- powershell.exe (PID: 3820)
- powershell.exe (PID: 2880)
The process creates files with name similar to system file names
- Dism.exe (PID: 3104)
- Dism.exe (PID: 1924)
- Dism.exe (PID: 3696)
Executable content was dropped or overwritten
- Dism.exe (PID: 3104)
- Dism.exe (PID: 1924)
- csc.exe (PID: 3844)
- Dism.exe (PID: 3696)
- cmd.exe (PID: 3072)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 3732)
- DismHost.exe (PID: 3748)
- DismHost.exe (PID: 3644)
- setup.exe (PID: 376)
The process executes VB scripts
- cmd.exe (PID: 3072)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 1368)
- cscript.exe (PID: 2052)
- cscript.exe (PID: 1056)
- cscript.exe (PID: 3392)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 3072)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3140)
- powershell.exe (PID: 3420)
- powershell.exe (PID: 2124)
- powershell.exe (PID: 2880)
- powershell.exe (PID: 3820)
Uses WMIC.EXE
- cmd.exe (PID: 3072)
Get information on the list of running processes
- cmd.exe (PID: 3072)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 1368)
- cscript.exe (PID: 2052)
- cscript.exe (PID: 1056)
- cscript.exe (PID: 3392)
The process executes Powershell scripts
- cmd.exe (PID: 3072)
Uses .NET C# to load dll
- powershell.exe (PID: 3020)
Reads settings of System Certificates
- wget.exe (PID: 3404)
- setup.exe (PID: 376)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 3072)
Executing commands from ".cmd" file
- powershell.exe (PID: 3612)
- cmd.exe (PID: 3072)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3072)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3072)
Reads security settings of Internet Explorer
- setup.exe (PID: 376)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3768)
- Dism.exe (PID: 3104)
- Dism.exe (PID: 1924)
- Dism.exe (PID: 3696)
Checks supported languages
- chcp.com (PID: 3456)
- mode.com (PID: 3844)
- mode.com (PID: 1308)
- more.com (PID: 1544)
- chcp.com (PID: 2240)
- DismHost.exe (PID: 3732)
- DismHost.exe (PID: 3748)
- csc.exe (PID: 3844)
- cvtres.exe (PID: 3484)
- more.com (PID: 864)
- more.com (PID: 2360)
- mode.com (PID: 3576)
- chcp.com (PID: 2576)
- wget.exe (PID: 3404)
- chcp.com (PID: 2724)
- DismHost.exe (PID: 3644)
- wget.exe (PID: 2044)
- mode.com (PID: 3900)
- mode.com (PID: 3252)
- setup.exe (PID: 376)
Manual execution by a user
- cmd.exe (PID: 3592)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3768)
Create files in a temporary directory
- Dism.exe (PID: 3104)
- Dism.exe (PID: 1924)
- csc.exe (PID: 3844)
- cvtres.exe (PID: 3484)
- Dism.exe (PID: 3696)
- wget.exe (PID: 2044)
- expand.exe (PID: 2940)
- setup.exe (PID: 376)
Reads the machine GUID from the registry
- DismHost.exe (PID: 3732)
- DismHost.exe (PID: 3748)
- csc.exe (PID: 3844)
- cvtres.exe (PID: 3484)
- wget.exe (PID: 3404)
- DismHost.exe (PID: 3644)
- setup.exe (PID: 376)
Reads the computer name
- DismHost.exe (PID: 3732)
- DismHost.exe (PID: 3748)
- wget.exe (PID: 3404)
- DismHost.exe (PID: 3644)
- wget.exe (PID: 2044)
- setup.exe (PID: 376)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1368)
- cscript.exe (PID: 2052)
- cscript.exe (PID: 3392)
- cscript.exe (PID: 1056)
- cscript.exe (PID: 1876)
Checks operating system version
- cmd.exe (PID: 3072)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3140)
- powershell.exe (PID: 3420)
- powershell.exe (PID: 2880)
- powershell.exe (PID: 3820)
Checks Windows language
- DismHost.exe (PID: 3644)
Reads the time zone
- DismHost.exe (PID: 3644)
Reads Microsoft Office registry keys
- setup.exe (PID: 376)
Process checks computer location settings
- setup.exe (PID: 376)
Checks proxy server information
- setup.exe (PID: 376)
Creates files or folders in the user directory
- setup.exe (PID: 376)
Reads product name
- setup.exe (PID: 376)
Reads CPU info
- setup.exe (PID: 376)
Reads Environment values
- setup.exe (PID: 376)
Reads the software policy settings
- setup.exe (PID: 376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
351
Monitored processes
298
Malicious processes
15
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\system32\cmd.exe /S /D /c" type Settings.ini " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 120 | find /i "Force_Terminal=" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | C:\Windows\System32\reg.exe delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform" /f /v DisableKeyManagementServiceHostCaching | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | findstr /c:\ /a:0E "[A] SHOW ACTIVATION INFO"\..\c nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | C:\Windows\System32\reg.exe delete "HKEY_USERS\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /f /v KeyManagementServiceName | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
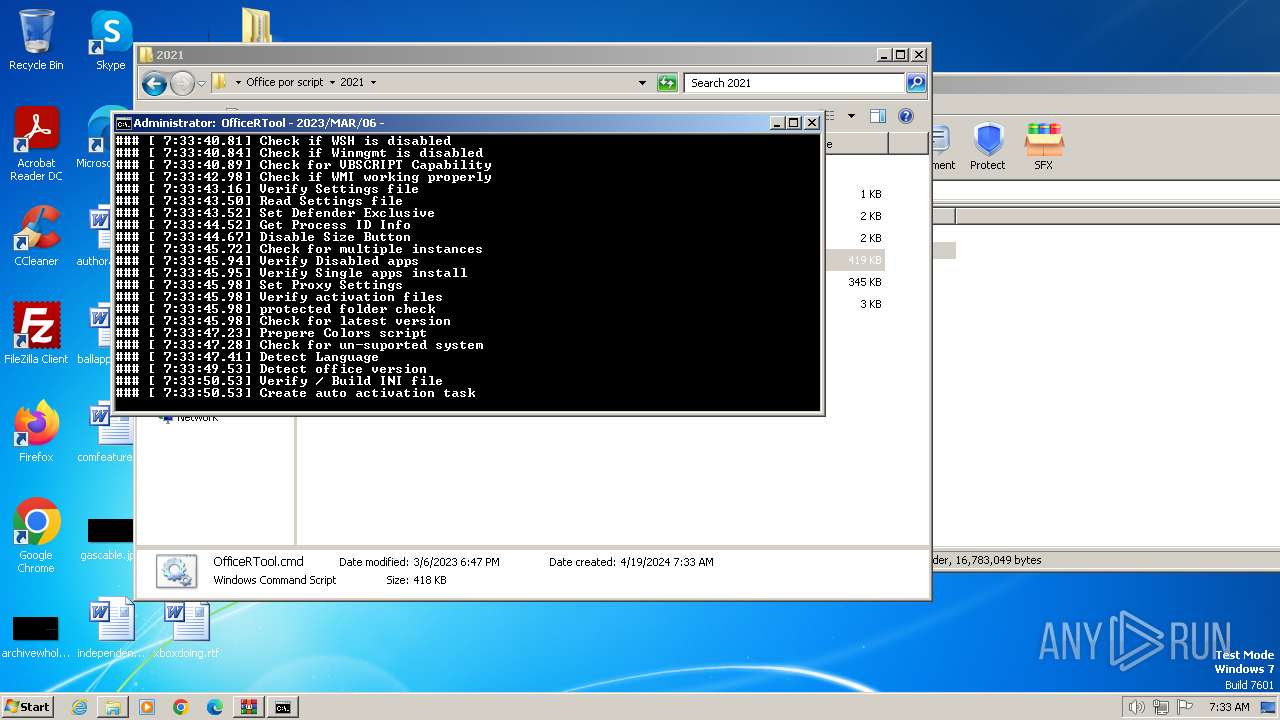
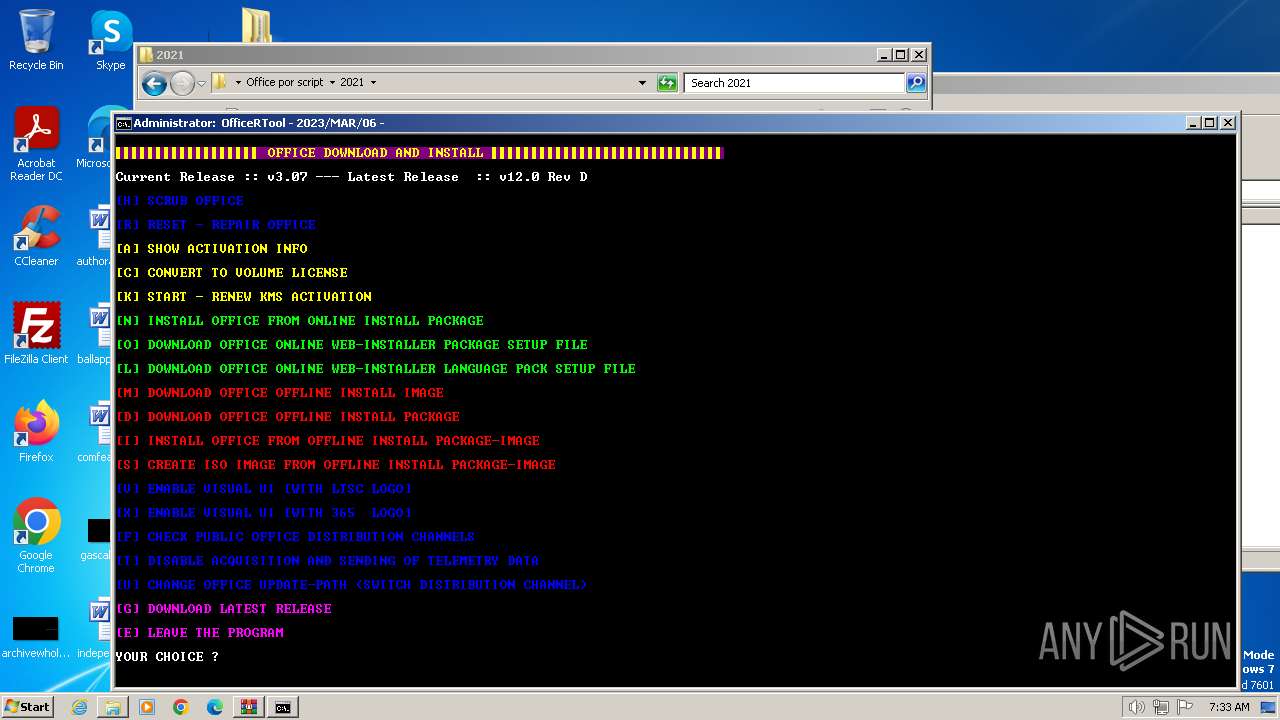
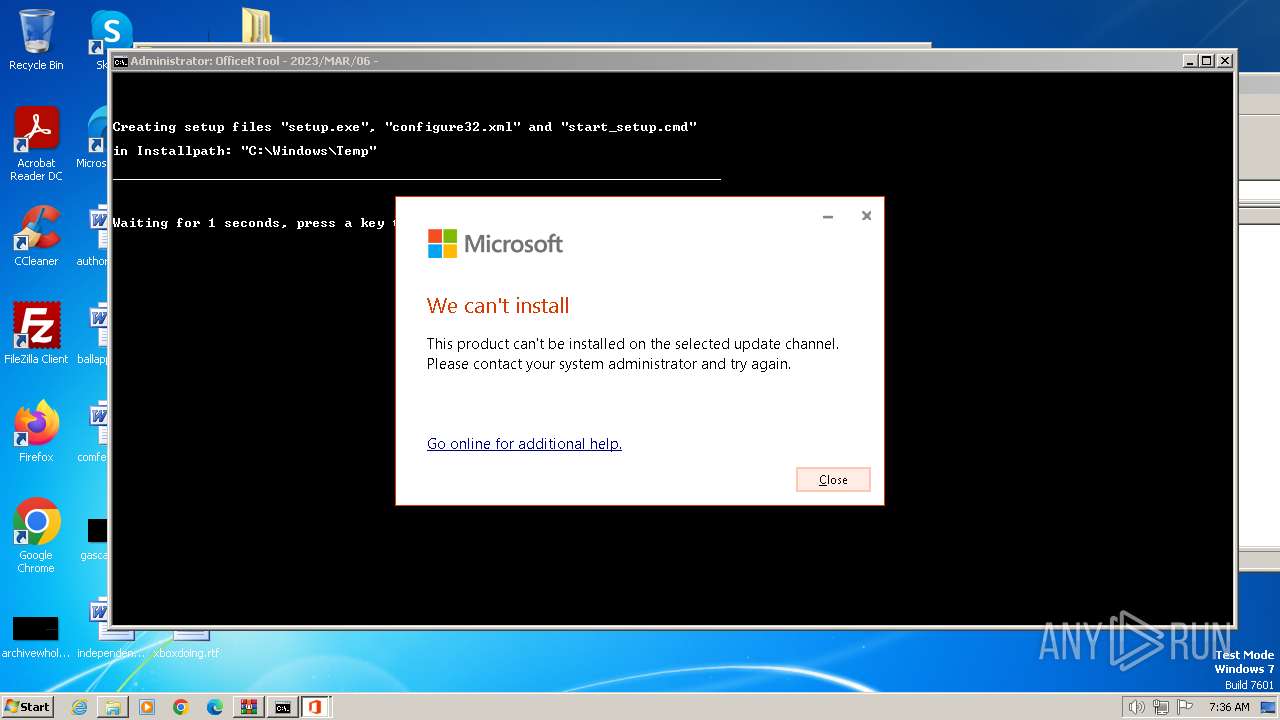
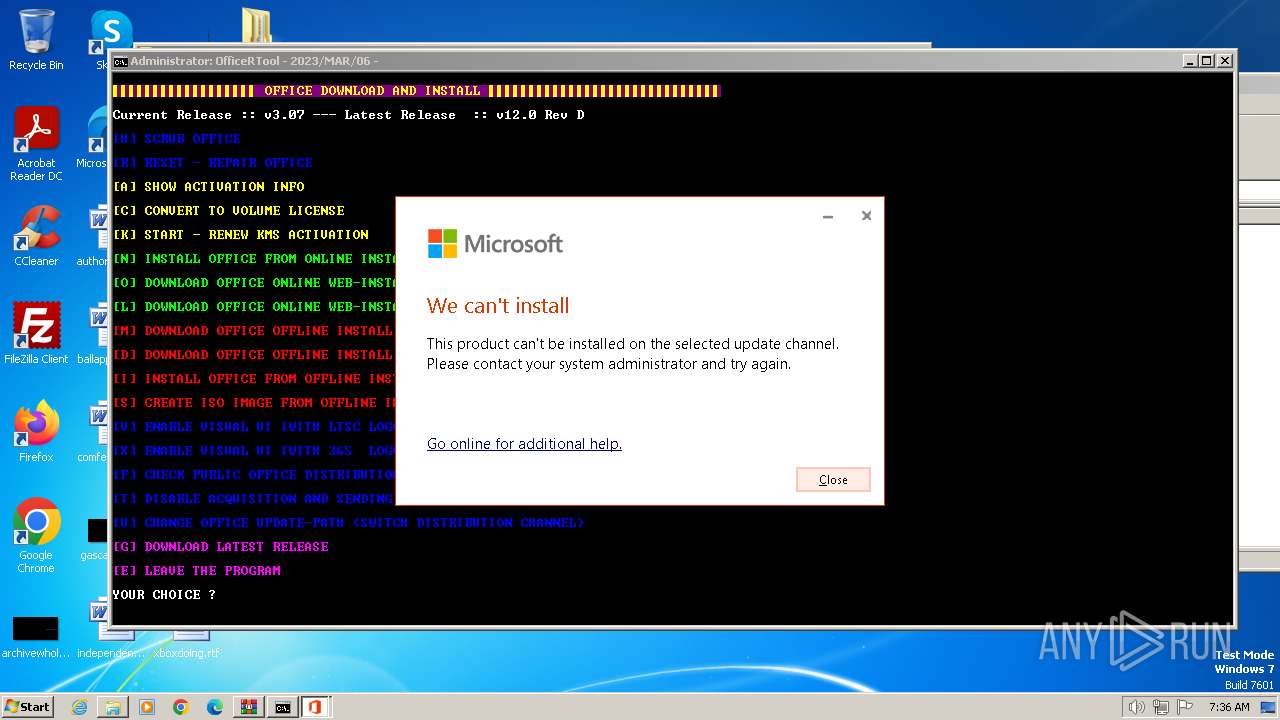
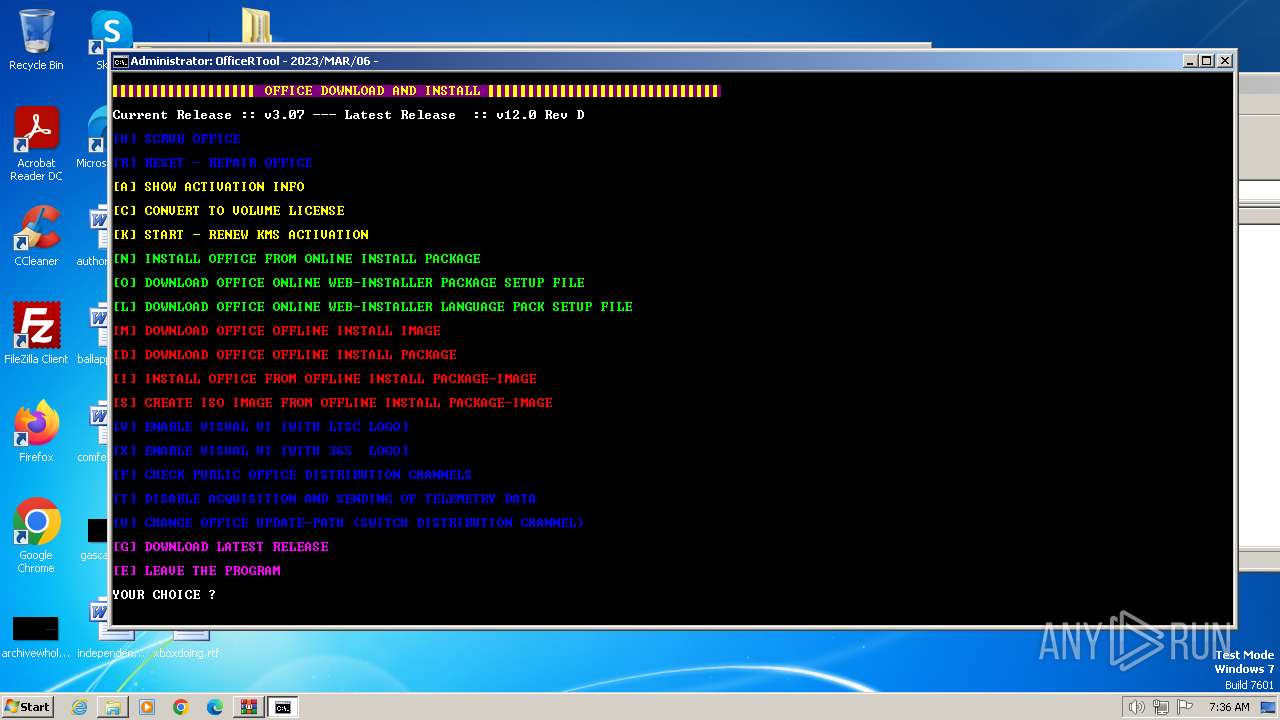
| 376 | "C:\Windows\Temp\setup.exe" /configure C:\Windows\Temp\configure32.xml | C:\Windows\Temp\setup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Exit code: 4294967295 Version: 16.0.14131.20278 Modules
| |||||||||||||||
| 492 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -noprofile -command "$Host.UI.RawUI.WindowTitle = 'Administrator: OfficeRTool - 2023/MAR/06 -'"; Write-Host "Mondo 2016 Grande Suite" -foreground "Green" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 548 | C:\Windows\system32\cmd.exe /c "type C:\Windows\temp\output" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 572 | C:\Windows\system32\cmd.exe /c "2>nul findstr "=" "C:\Users\admin\Desktop\Office por script\2021\Data\template.ini"" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 572 | C:\Windows\System32\reg.exe delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
44 673
Read events
43 972
Write events
644
Delete events
57
Modification events
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Office por script.rar | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3768) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
112
Suspicious files
6
Text files
235
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
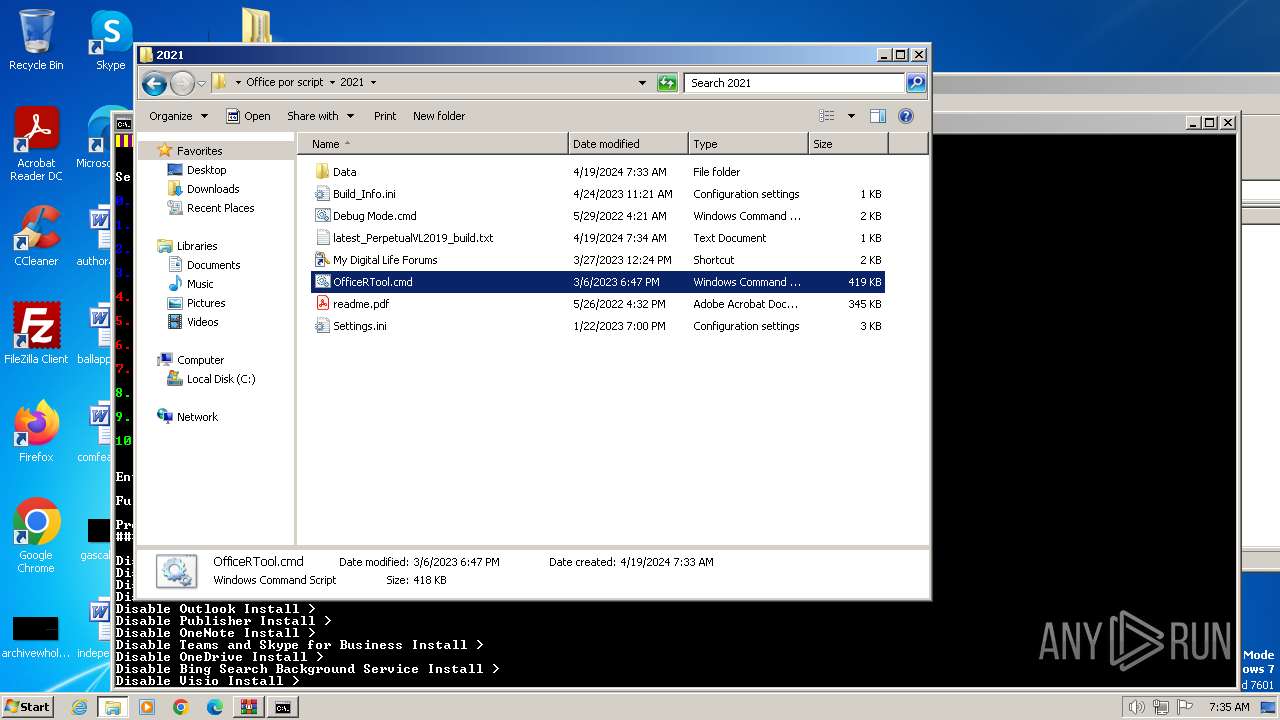
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Data\start_setup.cmd | text | |
MD5:FB5ABD106E9A939C47A0F372B462F781 | SHA256:F269AE680B699B52154B28DBA94131E086EA39FB48EE9A6558A4353325C4ACA3 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Debug Mode.cmd | text | |
MD5:2C4A1AE0FFE1298630974AF234A7ECC0 | SHA256:71B072BCF927ED85E377E420DDC37C26C4C7ED266FE9A27A1568C0A66E030311 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\readme.pdf | ||
MD5:FFC8DED7D71A200A1AE667C977AFB1E8 | SHA256:690E584517DC008A7FC80665CA89CABE2CC97C5072FC2F50C3544D56EEBFFD70 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Data\bin\7zxa.dll | executable | |
MD5:733ED533F9E63BBB0B959E1302BFE9EF | SHA256:73E0D2D7D98EF5D5C8080FC3F7630A8572746B40831DC8242F3EB62A6FED1D36 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Data\template.ini | text | |
MD5:64C2791461F9BBE090313729A494858A | SHA256:FE88D845750C459205494B1823F8B472DEA724A8B927B3A5C5250FB63C62534D | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Data\defaults.ini | text | |
MD5:72961BB637AAEE0294F724412E459781 | SHA256:CB46D0B25CF1AB335CD8B7537DAF19A915CC400D93EC6070103FF6AED45C1B87 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Data\bin\7z.exe | executable | |
MD5:54C3F15C02BC112C74C18FF770FBE7F8 | SHA256:060FD7CE8C54A257864FA036F59DE1413FDEB11CE2CD8D8C220EC04D30C6C1A3 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Data\bin\.wget-hsts | text | |
MD5:80B50459FFEB69350AFA5BB83D646C4B | SHA256:2294E74AC2CE04DF74659EAEEE51E4C34B5E748DE8A189F802F7E1E4D28CD5B6 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\My Digital Life Forums.lnk | lnk | |
MD5:A57B4BF486822F28940DFE2546D50433 | SHA256:90840A2FC69AC5ADDD68BF3850C804105F8CF5224A64612D9F871FB5F6A49DE0 | |||
| 3768 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3768.22140\Office por script\2021\Data\bin\cleanospp.exe | executable | |
MD5:CB600D36DE6A9D7A5D6E8DC06F665057 | SHA256:0CD5483DBD9292E08E1D28B3E8E1148DD9D411BCF3D222BCC6C8B2FD4F1A540C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
17
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | wget.exe | GET | 200 | 95.101.54.121:80 | http://officecdn.microsoft.com.edgesuite.net/pr/f2e724c1-748f-4b47-8fb8-8e0d210e9208/Office/Data/v32.cab | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3404 | wget.exe | 199.188.201.131:443 | officertool.org | NAMECHEAP-NET | US | unknown |
2044 | wget.exe | 95.101.54.121:80 | officecdn.microsoft.com.edgesuite.net | Akamai International B.V. | DE | unknown |
376 | setup.exe | 52.111.229.19:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
376 | setup.exe | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1360 | svchost.exe | 20.42.65.89:443 | vortex-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1360 | svchost.exe | 52.182.143.213:443 | vortex-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officertool.org |
| unknown |
officecdn.microsoft.com.edgesuite.net |
| unknown |
nexusrules.officeapps.live.com |
| whitelisted |
ecs.office.com |
| whitelisted |
vortex-win.data.microsoft.com |
| whitelisted |
nexus.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=3104 Failed to get an OSServices provider. Must be running in local store. Falling back to checking alongside the log provider for wdscore.dll. - CDISMLogger::FindWdsCore(hr:0x80004005) |
Dism.exe | PID=3104 The requested provider was not found in the Provider Store. - CDISMProviderStore::Internal_GetProvider(hr:0x80004005) |
Dism.exe | PID=3104 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3104 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3104 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3104 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3104 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=3104 Getting Provider OSServices - CDISMProviderStore::GetProvider |
Dism.exe | PID=3104 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=3732 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |