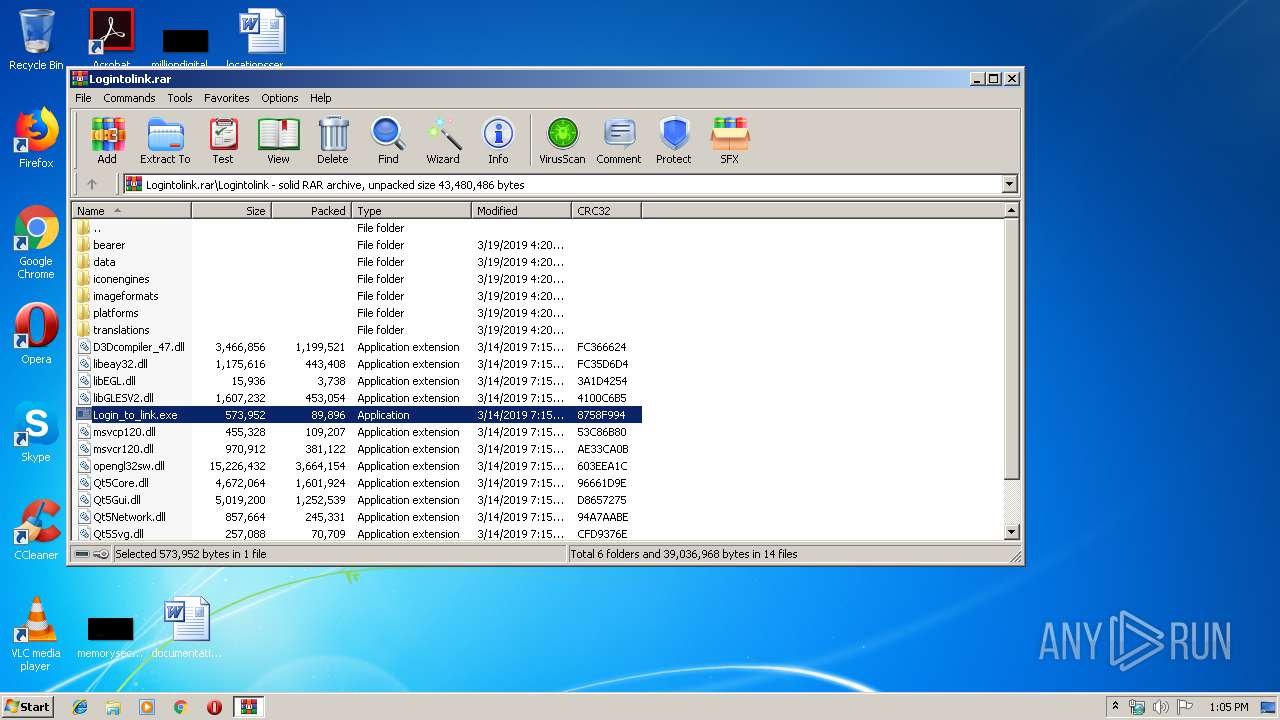
| File name: | Logintolink.rar |
| Full analysis: | https://app.any.run/tasks/056e48ed-7ff9-4419-8f83-f29b81a84381 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2019, 13:04:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 821026DB7D7F2C106CA209619B063397 |
| SHA1: | 12AF65F7ACE4CA1547115C131B7A46434E4DD0C9 |
| SHA256: | E08AF5B5B0AFB54805632027E0078F3E19F3F5D60B31152BF58ECAEF5419294D |
| SSDEEP: | 196608:Qm4V16GUw7YVbLzdn3pfiQKMWTIIPWMG3rDnJnSylXRQ9+UdM++ZMZFLHvn:r+17UwwnzdnZKQjqfmrDnJndQVdM++Zc |
MALICIOUS
Application was dropped or rewritten from another process
- Login_to_link.exe (PID: 3932)
- Login_to_link.exe (PID: 1376)
Loads dropped or rewritten executable
- Login_to_link.exe (PID: 1376)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2728)
Executes PowerShell scripts
- Login_to_link.exe (PID: 1376)
Creates files in the user directory
- powershell.exe (PID: 2624)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1376 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\Login_to_link.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\Login_to_link.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2624 | powershell.exe -inputformat none -ExecutionPolicy RemoteSigned -File C:/Users/admin/AppData/Local/Temp/Rar$EXa2728.42420/Logintolink/AddAVExclusion.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Login_to_link.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2728 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Logintolink.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3932 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\Login_to_link.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\Login_to_link.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
622
Read events
551
Write events
71
Delete events
0
Modification events
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Logintolink.rar | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2728) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
28
Suspicious files
2
Text files
11
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\data\project.xml | xml | |
MD5:— | SHA256:— | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\Login_to_link.exe | executable | |
MD5:— | SHA256:— | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\imageformats\qjpeg.dll | executable | |
MD5:4FF942230C2F69EBB469F3CA33139ADD | SHA256:D2F2CC52D5074154A2C9B9DA4797FC70D3755C73F63CBD82244D4F61C10415D0 | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\libGLESV2.dll | executable | |
MD5:DE6E94179D9202DB0CEE6414CBA63C4F | SHA256:AEEB1979302195AC1780BAB15326419E1BEF7B8D1E051ADD22D2AD21F061BD73 | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\imageformats\qdds.dll | executable | |
MD5:9DF6BE9517F318652B8F19017CF616A0 | SHA256:33270F72E06C4F469913D3531FC786D09F420B6C3CDA13F7060AB7DDC2995637 | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\bearer\qgenericbearer.dll | executable | |
MD5:80C5ED3F8D3F58A1C0D380BF46BE59F8 | SHA256:107404ECCBD0BDB938D9C0EF52C43719E9955B801322F11508C3F387BB528288 | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\imageformats\qgif.dll | executable | |
MD5:171B091335615A78AF8D0F2999FBD6AF | SHA256:3910A85ACB8848F225623E058DD60872BD41A8E60DCED605686BD6289808DEC0 | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\msvcr120.dll | executable | |
MD5:034CCADC1C073E4216E9466B720F9849 | SHA256:86E39B5995AF0E042FCDAA85FE2AEFD7C9DDC7AD65E6327BD5E7058BC3AB615F | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\imageformats\qico.dll | executable | |
MD5:D966EC500E29A924465D976EA9EF9880 | SHA256:D9389AF174ECB78C79CC4973595B363BDDB9032F44EA64AED99FB0F346FEEA7D | |||
| 2728 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2728.42420\Logintolink\bearer\qnativewifibearer.dll | executable | |
MD5:F38FA04E28151218DD13D73F8992D6A3 | SHA256:B8B643083F5E643D5C60F19B41084CF07AE2C96014BD565BDD91907725DE49C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1376 | Login_to_link.exe | 146.185.145.186:443 | bablosoft.com | Digital Ocean, Inc. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bablosoft.com |
| whitelisted |