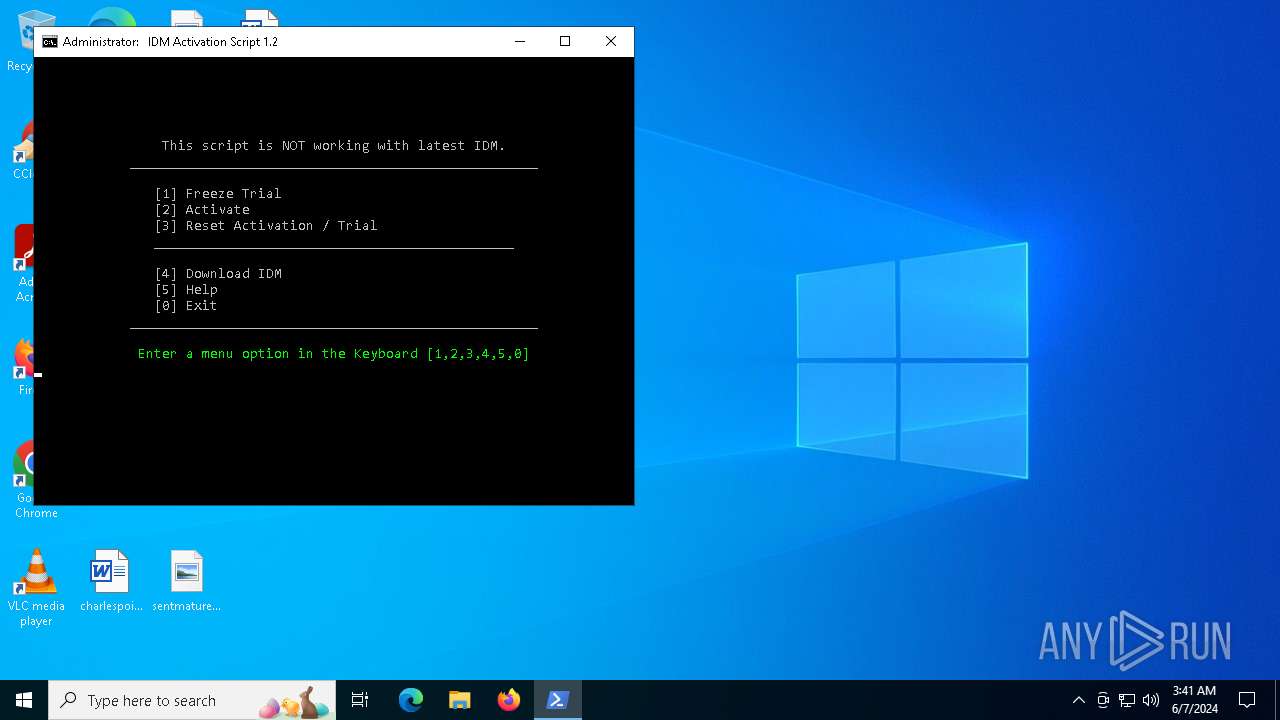
| File name: | IAS.cmd |
| Full analysis: | https://app.any.run/tasks/5b5a14ca-fb2a-4f06-ac96-9fe3dccb3de2 |
| Verdict: | Malicious activity |
| Analysis date: | June 07, 2024, 03:40:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (324), with CRLF line terminators |
| MD5: | E2E2B6FB84ED23B2950F26939C36FDF5 |
| SHA1: | 7988B5C71397DB6FC4A611A54F7D5622EEF73F40 |
| SHA256: | E06C490758709EFF468DF8F8AFDA86B8411758FD93EE16E14E6153DE5EE933E2 |
| SSDEEP: | 384:mNnhCo3piIUTUq5rrQmJbnl7+qK14TEJYab:mNn/ZiBAq5rrQmFl7G4gJYab |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 628)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 3040)
- cmd.exe (PID: 400)
- cmd.exe (PID: 2088)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 628)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 400)
Starts SC.EXE for service management
- cmd.exe (PID: 628)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 400)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3608)
- cmd.exe (PID: 628)
- powershell.exe (PID: 4380)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 3040)
- powershell.exe (PID: 2620)
- cmd.exe (PID: 400)
- cmd.exe (PID: 2088)
Executing commands from ".cmd" file
- cmd.exe (PID: 628)
- powershell.exe (PID: 4380)
- cmd.exe (PID: 3608)
- powershell.exe (PID: 2620)
- cmd.exe (PID: 400)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 628)
- cmd.exe (PID: 3608)
- conhost.exe (PID: 5924)
- cmd.exe (PID: 400)
- cmd.exe (PID: 6112)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 628)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 400)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 628)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 400)
Hides command output
- cmd.exe (PID: 6112)
- cmd.exe (PID: 5620)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 400)
- cmd.exe (PID: 5620)
INFO
Checks operating system version
- cmd.exe (PID: 628)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 400)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 400)
- powershell.exe (PID: 3044)
- powershell.exe (PID: 5064)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 400)
- powershell.exe (PID: 3044)
- powershell.exe (PID: 5064)
Checks supported languages
- mode.com (PID: 5420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
189
Monitored processes
73
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\WINDOWS\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | powershell.exe "$f=[io.file]::ReadAllText('C:\Users\admin\Desktop\IAS.cmd') -split ':PowerShellTest:\s*';iex ($f[1])" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | "C:\WINDOWS\System32\cmd.exe" /c ""C:\Users\admin\Desktop\IAS.cmd" -el -el -qedit" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | C:\WINDOWS\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\IAS.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 708 | reg query HKU\S-1-5-21-1693682860-607145093-2874071422-1001\Software | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | findstr /v "f7f81a39-5f63-5b42-9efd-1f13b5431005quot; "IAS.cmd" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
34 819
Read events
34 809
Write events
8
Delete events
2
Modification events
| (PID) Process: | (4380) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4380) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4380) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4380) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5108) reg.exe | Key: | HKEY_CURRENT_USER\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1616) reg.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\CLSID\IAS_TEST |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
1
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4380 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_usm4d2eq.o0x.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 400 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bkt0jrz4.1de.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3044 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_haywebkz.oku.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_racgsmrn.sld.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4380 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hjxtusys.ihn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3044 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rh22gftr.jgw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ofhhfdw3.2sg.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 400 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zbj4b20f.qdb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1280 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4uddo3fh.jqk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5064 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zzjb0auu.po1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2288 | RUXIMICS.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5228 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2288 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5228 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | POST | 200 | 13.69.239.73:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5228 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
2288 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2288 | RUXIMICS.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5228 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2288 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
5228 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
iasupdatecheck.massgrave.dev |
| unknown |
self.events.data.microsoft.com |
| whitelisted |