| URL: | https://www.teamspeak.de/en/download/teamspeak-3-32-Bit-client-windows/ |
| Full analysis: | https://app.any.run/tasks/e77277d0-3e61-4628-9cb4-e64186ec6aa9 |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 18:38:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | EFB553ECAEC23F10C961A9685984D822 |
| SHA1: | 336F4E9F4EAF077A27048C664B6D19CF7EAF4802 |
| SHA256: | E066FDF95423993B3CD110CA2FCE0568150BE69D1684BC8977EBCA5523D327F5 |
| SSDEEP: | 3:N8DSLfVAEo9CkzEWrYEBvM1JN:2OLfqRrrUIM1JN |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
Reads the Internet Settings
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
- ts3client_win32.exe (PID: 1608)
- ts3client_win32.exe (PID: 2520)
Searches for installed software
- vcredist_x86.exe (PID: 3432)
Reads settings of System Certificates
- ts3client_win32.exe (PID: 1608)
Detected use of alternative data streams (AltDS)
- ts3client_win32.exe (PID: 2520)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 296)
- chrome.exe (PID: 2960)
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
- vcredist_x86.exe (PID: 3432)
- package_inst.exe (PID: 2996)
- package_inst.exe (PID: 3972)
- package_inst.exe (PID: 3572)
Application launched itself
- iexplore.exe (PID: 128)
- chrome.exe (PID: 2448)
- chrome.exe (PID: 2960)
- vcredist_x86.exe (PID: 3840)
Manual execution by a user
- chrome.exe (PID: 2448)
- chrome.exe (PID: 2960)
- ts3client_win32.exe (PID: 3772)
- ts3client_win32.exe (PID: 2520)
- ts3client_win32.exe (PID: 3048)
- ts3client_win32.exe (PID: 3360)
- ts3client_win32.exe (PID: 2776)
- ts3client_win32.exe (PID: 2784)
The process uses the downloaded file
- chrome.exe (PID: 2960)
- chrome.exe (PID: 1232)
Reads the computer name
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
- vcredist_x86.exe (PID: 3840)
- vcredist_x86.exe (PID: 3432)
- ts3client_win32.exe (PID: 1608)
- ts3client_win32.exe (PID: 2520)
- ts3client_win32.exe (PID: 2776)
- ts3client_win32.exe (PID: 2784)
Create files in a temporary directory
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
- vcredist_x86.exe (PID: 3432)
- ts3client_win32.exe (PID: 1608)
- package_inst.exe (PID: 2996)
- package_inst.exe (PID: 3972)
- package_inst.exe (PID: 3572)
Malware-specific behavior (creating "System.dll" in Temp)
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
Checks supported languages
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
- vcredist_x86.exe (PID: 3840)
- vcredist_x86.exe (PID: 3432)
- ts3client_win32.exe (PID: 1608)
- package_inst.exe (PID: 2996)
- package_inst.exe (PID: 3972)
- ts3client_win32.exe (PID: 2520)
- ts3client_win32.exe (PID: 2784)
- ts3client_win32.exe (PID: 2776)
- QtWebEngineProcess.exe (PID: 1936)
- package_inst.exe (PID: 3572)
Checks proxy server information
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
Process drops legitimate windows executable
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
- vcredist_x86.exe (PID: 3432)
- package_inst.exe (PID: 3972)
Reads the machine GUID from the registry
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
- ts3client_win32.exe (PID: 1608)
- package_inst.exe (PID: 2996)
- package_inst.exe (PID: 3972)
- ts3client_win32.exe (PID: 2520)
- ts3client_win32.exe (PID: 2776)
- ts3client_win32.exe (PID: 2784)
- package_inst.exe (PID: 3572)
Creates files in the program directory
- TeamSpeak3-Client-win32-3.5.6.exe (PID: 3264)
Creates files or folders in the user directory
- ts3client_win32.exe (PID: 1608)
- package_inst.exe (PID: 2996)
- package_inst.exe (PID: 3572)
- ts3client_win32.exe (PID: 2520)
- package_inst.exe (PID: 3972)
Reads Windows Product ID
- ts3client_win32.exe (PID: 1608)
- ts3client_win32.exe (PID: 2520)
Connects to unusual port
- ts3client_win32.exe (PID: 2520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
108
Monitored processes
59
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.teamspeak.de/en/download/teamspeak-3-32-Bit-client-windows/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=656 --field-trial-handle=1156,i,16174114260867774134,13704040035235581733,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:128 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1372 --field-trial-handle=1140,i,17937383433306036249,14462899855473955045,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1752 --field-trial-handle=1156,i,16174114260867774134,13704040035235581733,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=4012 --field-trial-handle=1156,i,16174114260867774134,13704040035235581733,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3768 --field-trial-handle=1156,i,16174114260867774134,13704040035235581733,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2156 --field-trial-handle=1156,i,16174114260867774134,13704040035235581733,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3796 --field-trial-handle=1156,i,16174114260867774134,13704040035235581733,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2152 --field-trial-handle=1140,i,17937383433306036249,14462899855473955045,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
27 415
Read events
27 159
Write events
251
Delete events
5
Modification events
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
71
Suspicious files
803
Text files
446
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:B6E9A32DB2F500A4E448B0C312FFAE9D | SHA256:229A3A482E9E89265600D0BAD0366B5BD529FC1D54B1A4E56B72A97AD17239AD | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:52AD4C4B4C7CAECB6EA86B73046A694D | SHA256:6222DC5F9ED95A43C8A0C83FF14F14C119FEDE6E3141B931D3B083A674782840 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1851B118FC888B79D80FC2D44CBA9AC7 | binary | |
MD5:561882D645149E1641EDD15ADDC85B3C | SHA256:B9AE3B868C5883AF34B46922A2FF486FC69E51831F842565286F470FB5DBFB2D | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabFDD9.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:D666AE4CDBBF182C0DC6957FBC3C08E1 | SHA256:AAD992A94278B4B1FBB9F8405D2D498600990D187446A984B6084F67C9B74BFA | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarFDDA.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1851B118FC888B79D80FC2D44CBA9AC7 | binary | |
MD5:695B38AC2FB45C88D8951D6E6BBDD849 | SHA256:5721BFE21D2B7482F4F7183476A93C41720B61EDB8AE1BD5D0E9A6A3CBE00845 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\scrollable[1].css | text | |
MD5:6A9836085E78C5C8C0DDAD6556FB28C5 | SHA256:3059A8D316AA87711533DC321F448163E88BB8178AB3BA02F519B40F19FB439C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
136
DNS requests
118
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
296 | iexplore.exe | GET | 200 | 184.24.77.188:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?712397d87c9bba6b | unknown | compressed | 4.66 Kb | unknown |
296 | iexplore.exe | GET | 200 | 184.24.77.188:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2f131cf452408714 | unknown | compressed | 65.2 Kb | unknown |
296 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
296 | iexplore.exe | GET | 200 | 184.24.77.76:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMW%2FV8QC%2BkpXgrtzYFZTD96%2Bg%3D%3D | unknown | binary | 503 b | unknown |
296 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEA1uFYrLabZxEtE2U5X5DGM%3D | unknown | binary | 471 b | unknown |
296 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
296 | iexplore.exe | GET | 200 | 184.24.77.76:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPg5%2F3M7hj3%2B41bu5Kd8fDQ9w%3D%3D | unknown | binary | 503 b | unknown |
296 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCZXmpIP%2Bo%2BHhJmodADfw%2Fc | unknown | binary | 472 b | unknown |
128 | iexplore.exe | GET | 304 | 184.24.77.188:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?759f26dac4e392bf | unknown | — | — | unknown |
128 | iexplore.exe | GET | 304 | 184.24.77.188:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?85105a2067e5fff2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
296 | iexplore.exe | 89.49.127.20:443 | www.teamspeak.de | freenet Datenkommunikations GmbH | DE | unknown |
296 | iexplore.exe | 184.24.77.188:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
296 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
296 | iexplore.exe | 184.24.77.76:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
296 | iexplore.exe | 104.126.37.153:443 | consent.cookiebot.com | Akamai International B.V. | DE | unknown |
296 | iexplore.exe | 142.250.185.106:443 | ajax.googleapis.com | GOOGLE | US | whitelisted |
296 | iexplore.exe | 194.97.52.162:443 | static.4players.de | freenet Datenkommunikations GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.teamspeak.de |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
ajax.googleapis.com |
| whitelisted |
consent.cookiebot.com |
| whitelisted |
static.4players.de |
| unknown |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
subpixel.4players.de |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3264 | TeamSpeak3-Client-win32-3.5.6.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
Process | Message |
|---|---|
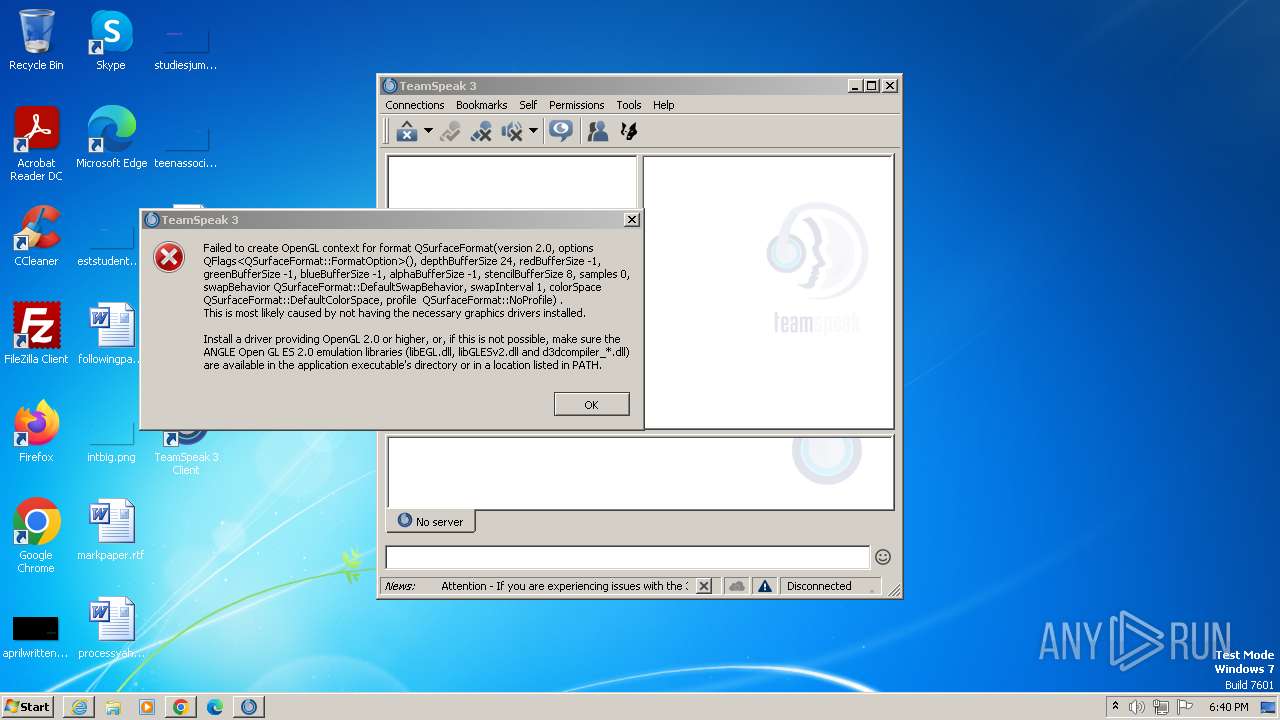
ts3client_win32.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|
ts3client_win32.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
ts3client_win32.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|
ts3client_win32.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
ts3client_win32.exe | QWindowsEGLStaticContext::create: When using ANGLE, check if d3dcompiler_4x.dll is available
|
ts3client_win32.exe | WebEngineContext used before QtWebEngine::initialize() or OpenGL context creation failed.
|
ts3client_win32.exe | QWindowsEGLStaticContext::create: Could not initialize EGL display: error 0x3001
|
ts3client_win32.exe | Qt WebEngine ICU data not found at C:/Qt/Qt5.12.3/5.12.3/msvc2017/resources. Trying parent directory...
|
ts3client_win32.exe | Installed Qt WebEngine locales directory not found at location C:/Qt/Qt5.12.3/5.12.3/msvc2017/translations\qtwebengine_locales. Trying application directory...
|
ts3client_win32.exe | Qt WebEngine resources not found at C:/Qt/Qt5.12.3/5.12.3/msvc2017/resources. Trying parent directory...
|