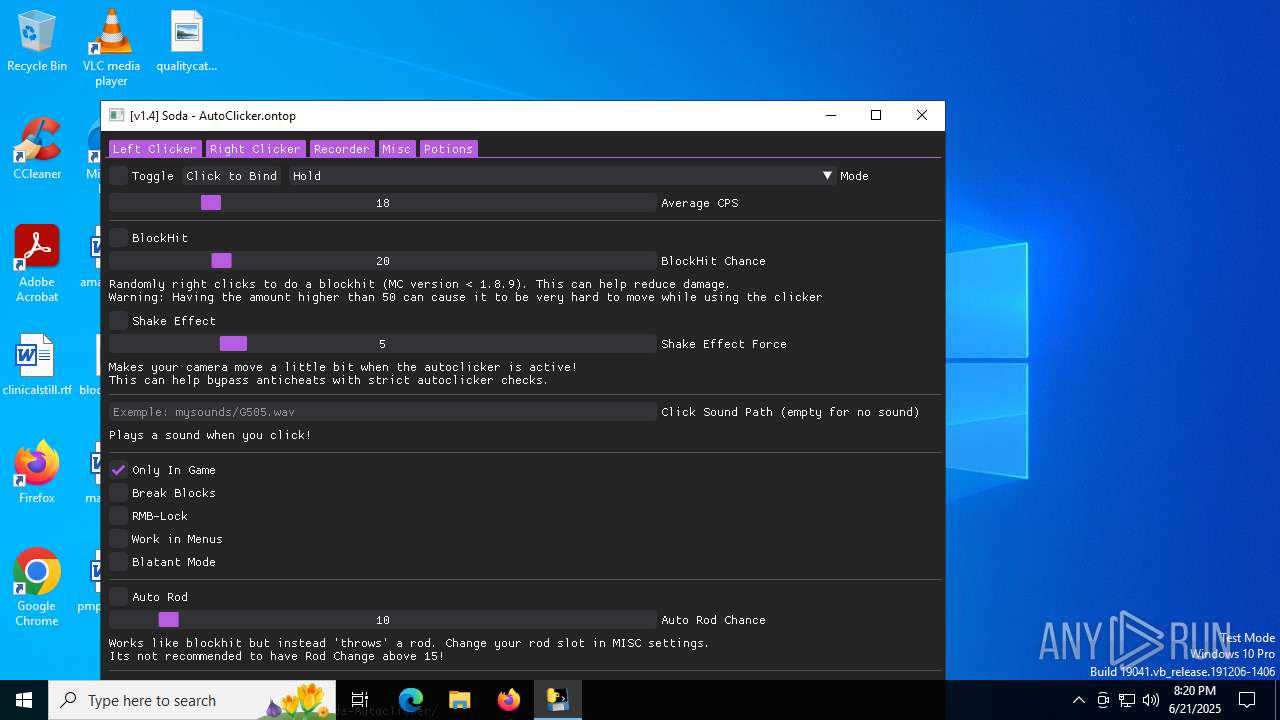
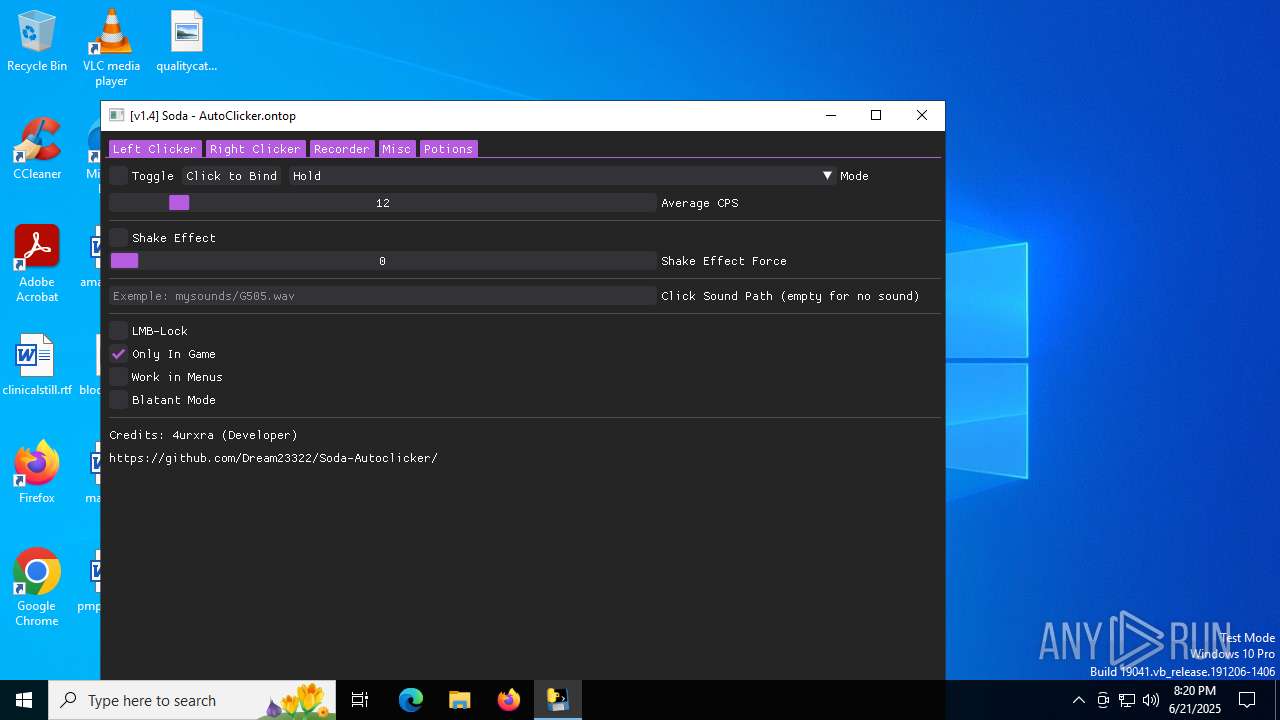
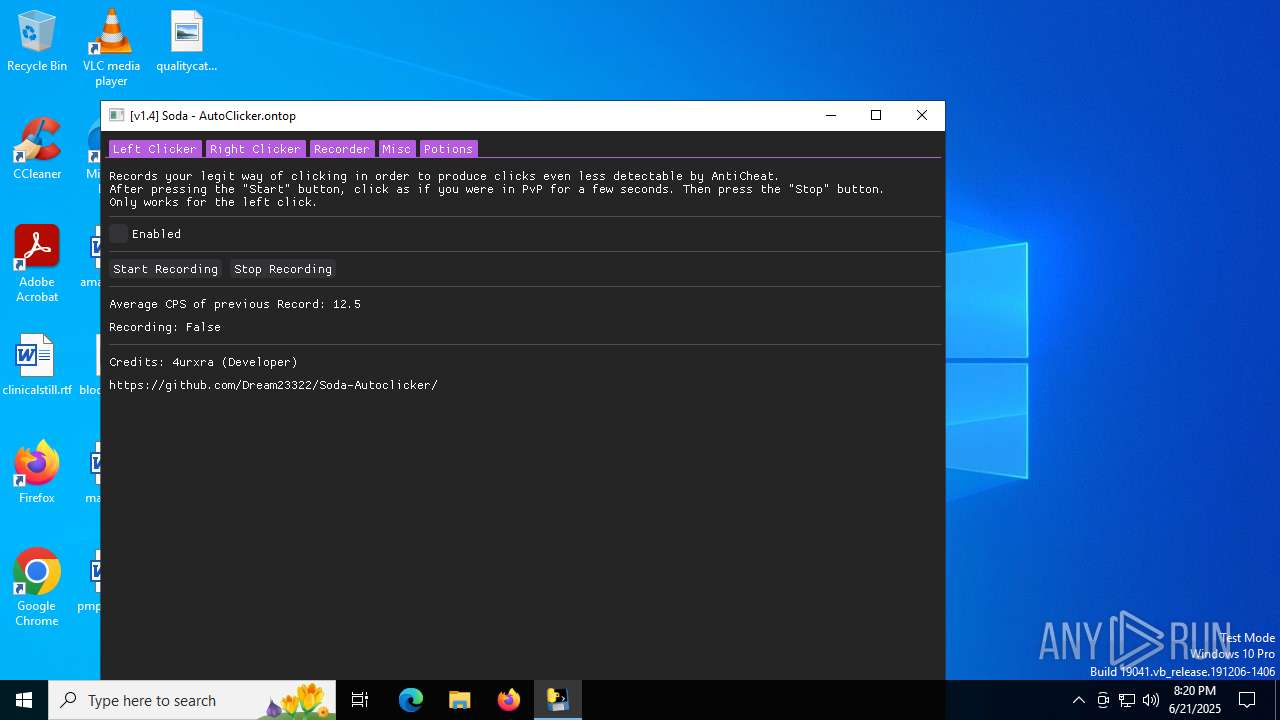
| File name: | Soda.v1.4.exe |
| Full analysis: | https://app.any.run/tasks/f7bae2bf-4728-435d-93ce-cf17c37db337 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 20:19:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 3EBA7AED5636CFFD9B8B8A3780870DB3 |
| SHA1: | E843680DB1ECCDE091CD8ED10C4E65F91472CA5E |
| SHA256: | E06623CC4BC2227BD3AEECED3758776051FEEE79102AD9F8CF79F1575F6D2E7E |
| SSDEEP: | 98304:UDZikAK/WfDcvDr0vg8OgxP1PXmRbS2zjI+GHELnu0XuYVpoSX6eC5qSc0IjlcLj:3qSTcsHuNBYNWbf2h |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Soda.v1.4.exe (PID: 1560)
Process drops legitimate windows executable
- Soda.v1.4.exe (PID: 1560)
The process drops C-runtime libraries
- Soda.v1.4.exe (PID: 1560)
Process drops python dynamic module
- Soda.v1.4.exe (PID: 1560)
Application launched itself
- Soda.v1.4.exe (PID: 1560)
Loads Python modules
- Soda.v1.4.exe (PID: 1068)
Starts CMD.EXE for commands execution
- Soda.v1.4.exe (PID: 1068)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 188)
INFO
Checks supported languages
- Soda.v1.4.exe (PID: 1560)
- Soda.v1.4.exe (PID: 1068)
Reads the computer name
- Soda.v1.4.exe (PID: 1560)
- Soda.v1.4.exe (PID: 1068)
Create files in a temporary directory
- Soda.v1.4.exe (PID: 1560)
Reads the machine GUID from the registry
- Soda.v1.4.exe (PID: 1068)
The sample compiled with english language support
- Soda.v1.4.exe (PID: 1560)
Checks operating system version
- Soda.v1.4.exe (PID: 1068)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 3580)
PyInstaller has been detected (YARA)
- Soda.v1.4.exe (PID: 1560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:17 22:25:45+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 173056 |
| InitializedDataSize: | 151040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb4d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
142
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\WINDOWS\system32\cmd.exe /c "wmic useraccount where name='%username%' get sid" | C:\Windows\System32\cmd.exe | — | Soda.v1.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\AppData\Local\Temp\Soda.v1.4.exe" | C:\Users\admin\AppData\Local\Temp\Soda.v1.4.exe | — | Soda.v1.4.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\AppData\Local\Temp\Soda.v1.4.exe" | C:\Users\admin\AppData\Local\Temp\Soda.v1.4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3580 | wmic useraccount where name='admin' get sid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3580 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3756 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Soda.v1.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4968 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | Soda.v1.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
664
Read events
664
Write events
0
Delete events
0
Modification events
Executable files
30
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\VCRUNTIME140.dll | executable | |
MD5:F12681A472B9DD04A812E16096514974 | SHA256:D66C3B47091CEB3F8D3CC165A43D285AE919211A0C0FCB74491EE574D8D464F8 | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\_bz2.pyd | executable | |
MD5:23DCE6CD4BE213F8374BF52E67A15C91 | SHA256:190ADE9F09BE287FCC5328A6A497921F164C5C67E6D4FCDCB8B8FD6853B06FE2 | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\_hashlib.pyd | executable | |
MD5:477DD76DBB15BAD8D77B978EA336F014 | SHA256:23063B56AA067C3D4A79A873D4DB113F6396F3E1FE0AF4B12D95D240C4CF9969 | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\_decimal.pyd | executable | |
MD5:B6ACB44C2F580991DF7B1358A0FC0B69 | SHA256:2BAB2833C24EB4E07FE082D291013EED000A5CFC22DF49311C729E7A57FE632E | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\_asyncio.pyd | executable | |
MD5:4AB3A456C59F6AED0D147C31FAB59604 | SHA256:97ED94F8D35445573177BA75E17DCF4C667E3C236C0B4D436FA97F8C862CC0BD | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\base_library.zip | compressed | |
MD5:B71C1E073B7A1BB2E4F87767EB17BF63 | SHA256:927B335F7088B8A9F8509F99E59E5A86435A4A691A85A889A5BC6833A3A3381E | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\libffi-7.dll | executable | |
MD5:EEF7981412BE8EA459064D3090F4B3AA | SHA256:F60DD9F2FCBD495674DFC1555EFFB710EB081FC7D4CAE5FA58C438AB50405081 | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\dearpygui\VCRUNTIME140_1.dll | executable | |
MD5:AB03551E4EF279ABED2D8C4B25F35BB8 | SHA256:F8BC270449CA6BB6345E88BE3632D465C0A7595197C7954357DC5066ED50AE44 | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\libcrypto-1_1.dll | executable | |
MD5:6F4B8EB45A965372156086201207C81F | SHA256:976CE72EFD0A8AEEB6E21AD441AA9138434314EA07F777432205947CDB149541 | |||
| 1560 | Soda.v1.4.exe | C:\Users\admin\AppData\Local\Temp\_MEI15602\dearpygui\_dearpygui.pyd | executable | |
MD5:243D02A18EC73ADB3B05E8E9CE1FD769 | SHA256:6247C5E0E4FC8509269CAC74F56BA0842C8756FEEE0031052CA2C0D3FC616C24 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.4:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7020 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1932 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1932 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5908 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.24.77.4:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1932 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |