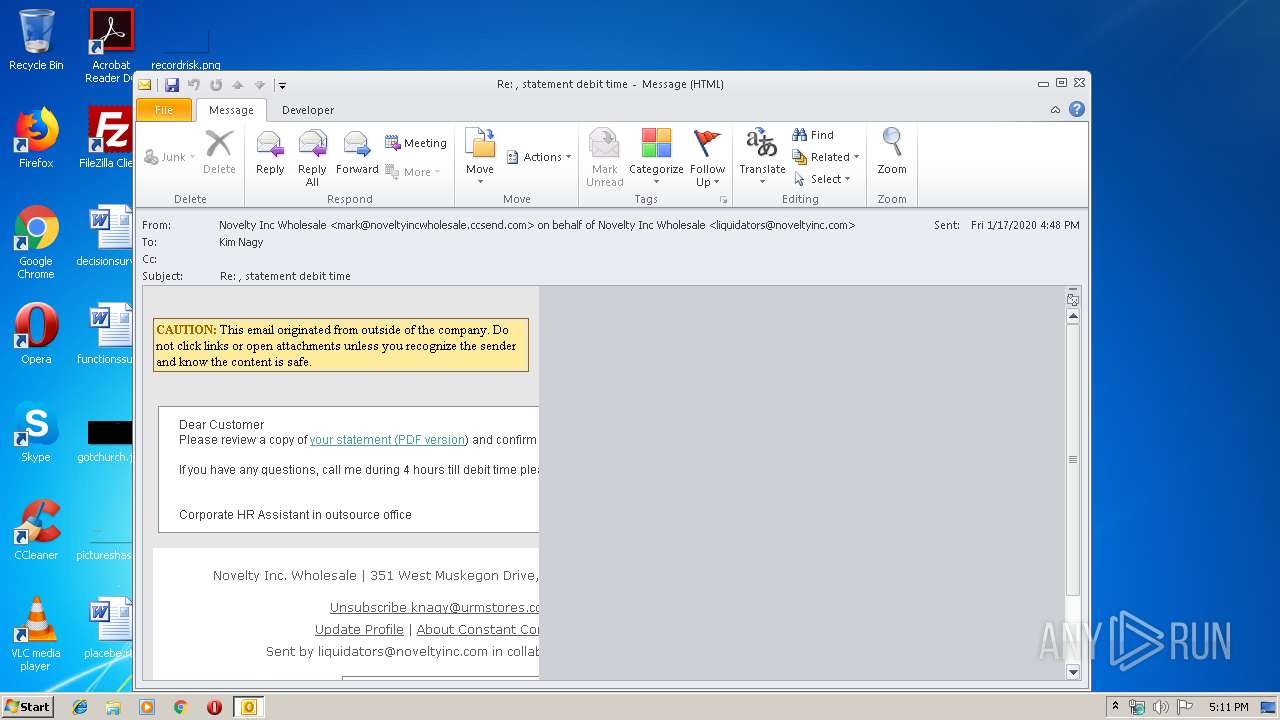
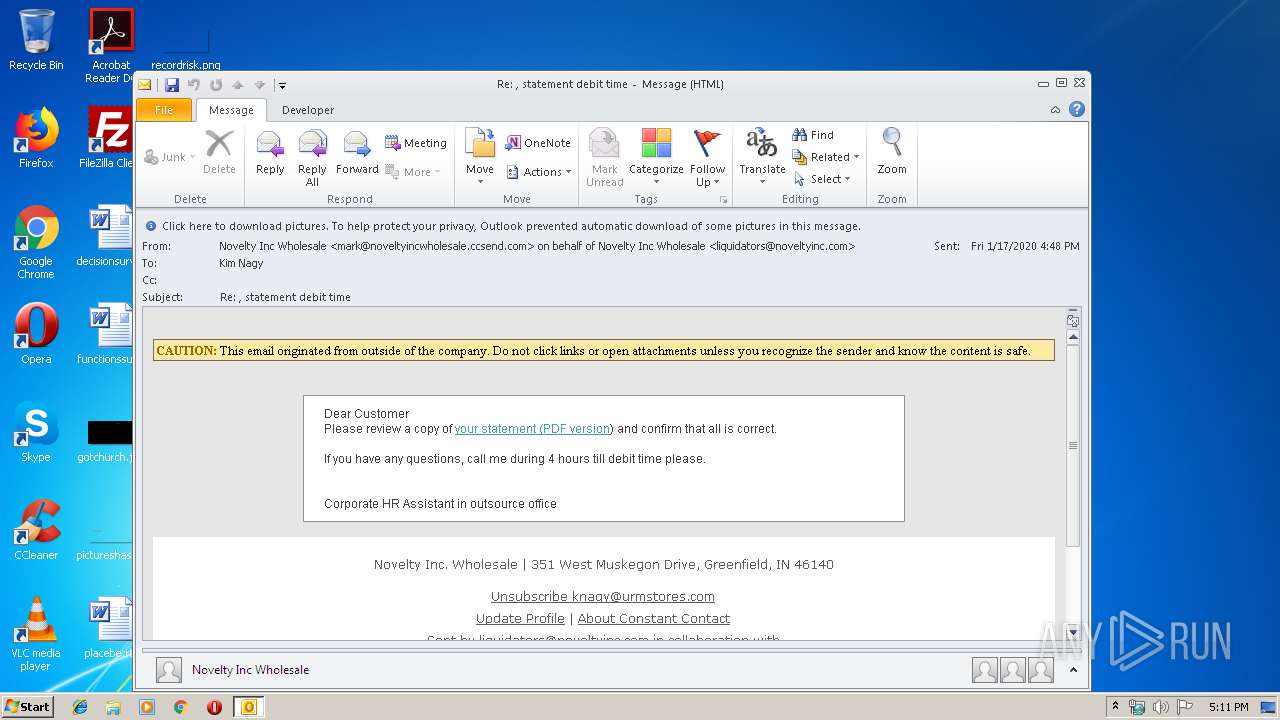
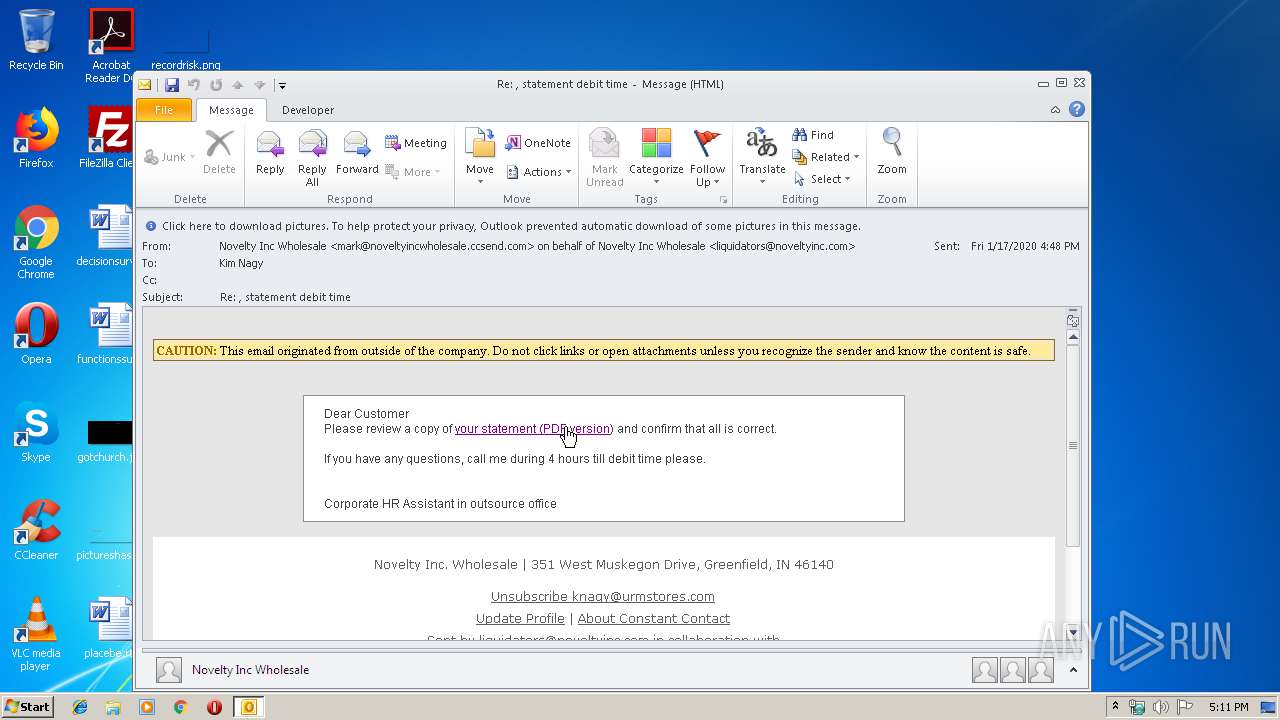
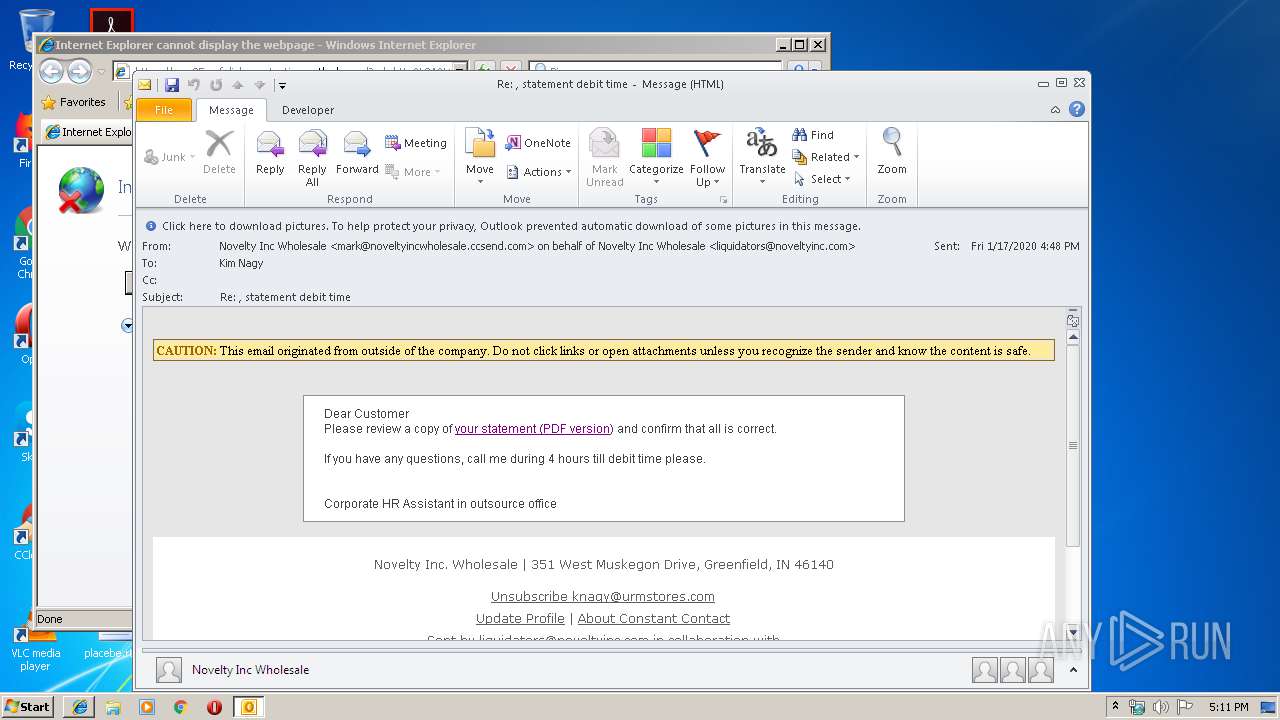
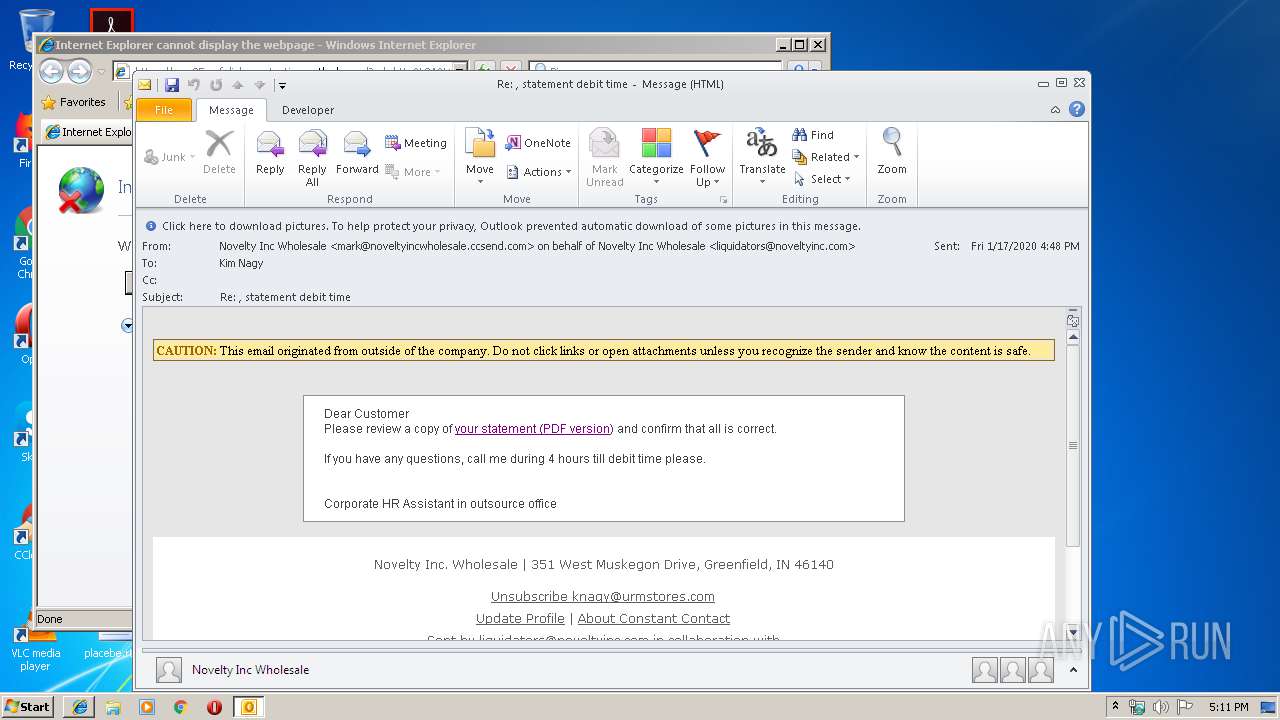
| File name: | Re statement debit time.msg |
| Full analysis: | https://app.any.run/tasks/83d68735-ac9b-466a-a382-8cfa6b0ff5e4 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 17:10:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 41656130AECD17B45B7AEBC74E4999D4 |
| SHA1: | A2F9FB372E36DAB22B6A6BA6897E31E6D58067ED |
| SHA256: | E062069BC5B5661F75CA8F69D13F10D6F1BDF040CEE06D47303424EAD64730AD |
| SSDEEP: | 3072:sATHZarceu7A5RnvWuceucZaUSRCoA5RnvTQou/Q2QtcKmVwAzORhR4m:XQ2QBAzORl |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2524)
SUSPICIOUS
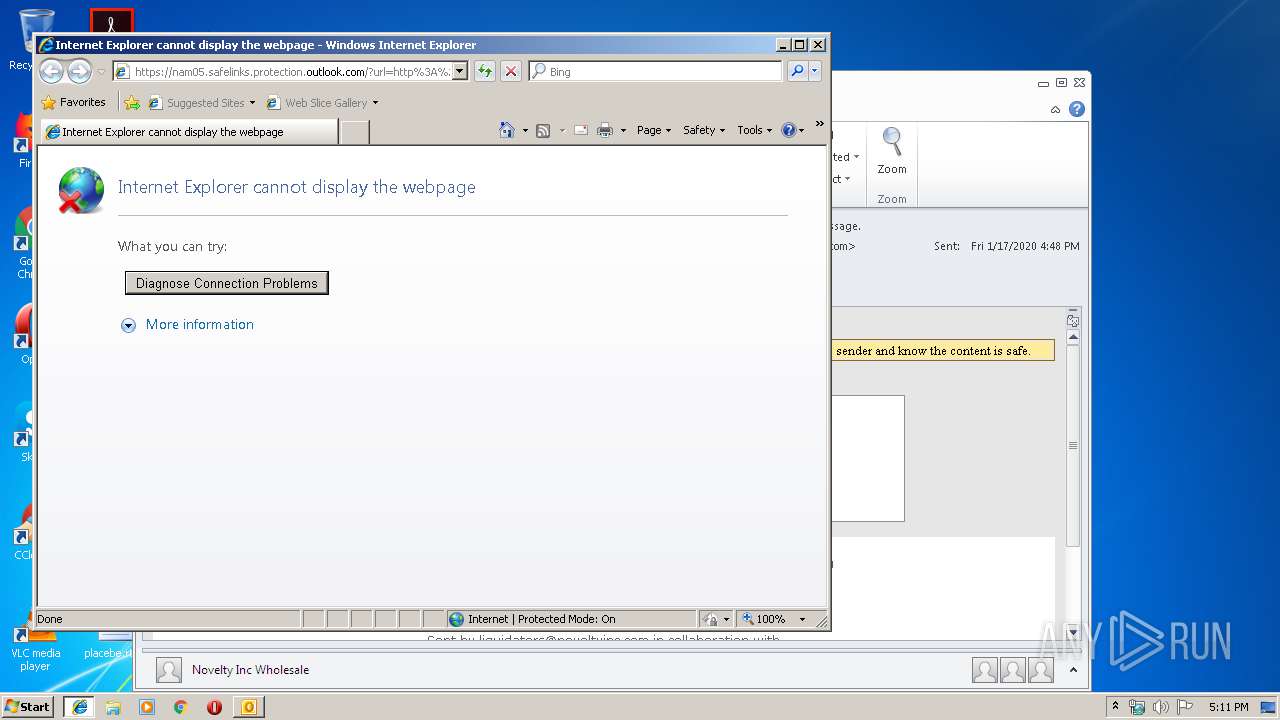
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2524)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2524)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2524)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3372)
Reads Internet Cache Settings
- iexplore.exe (PID: 2108)
Reads internet explorer settings
- iexplore.exe (PID: 2108)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (45.3) |
|---|---|---|
| .oft | | | Outlook Form Template (26.5) |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2108 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3372 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
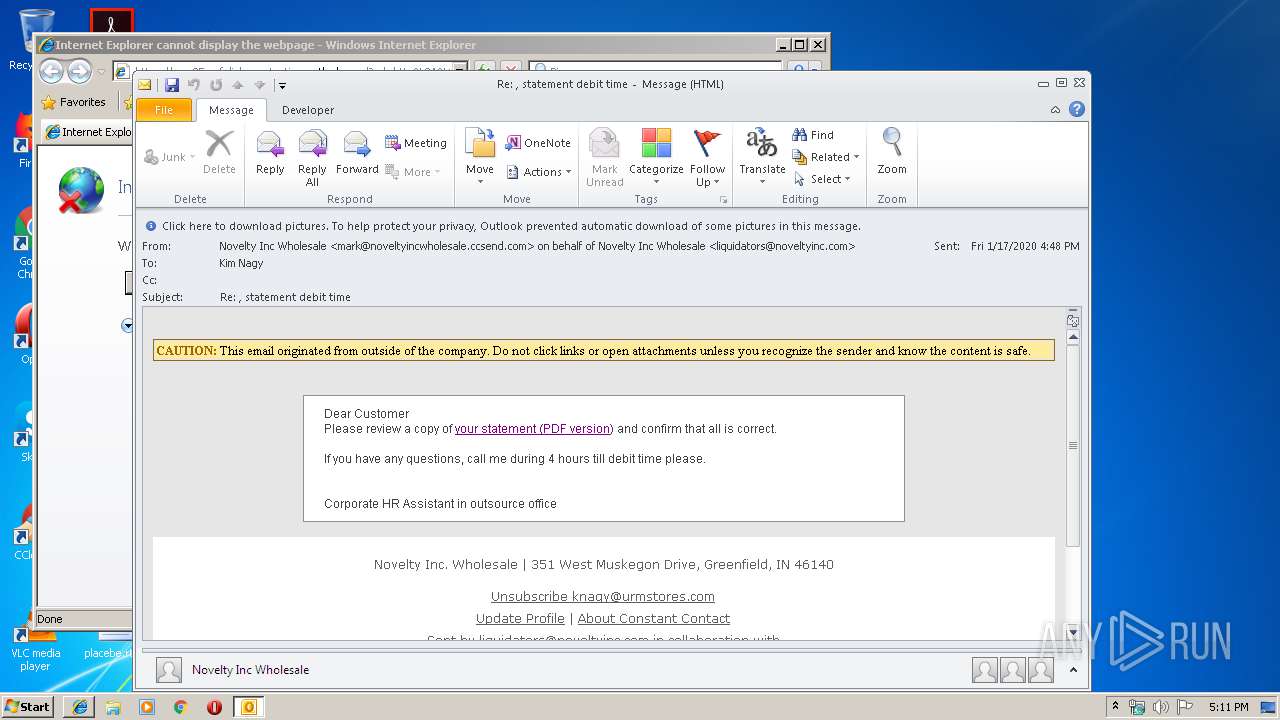
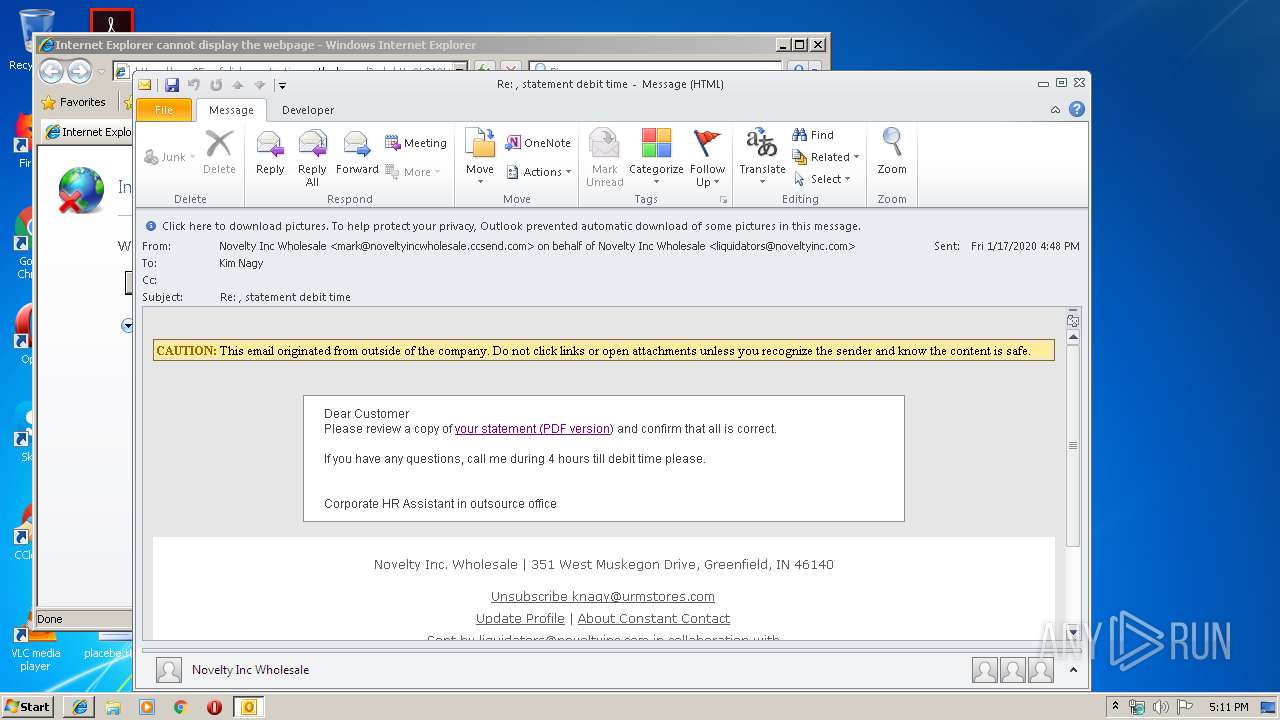
| 2524 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Re statement debit time.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
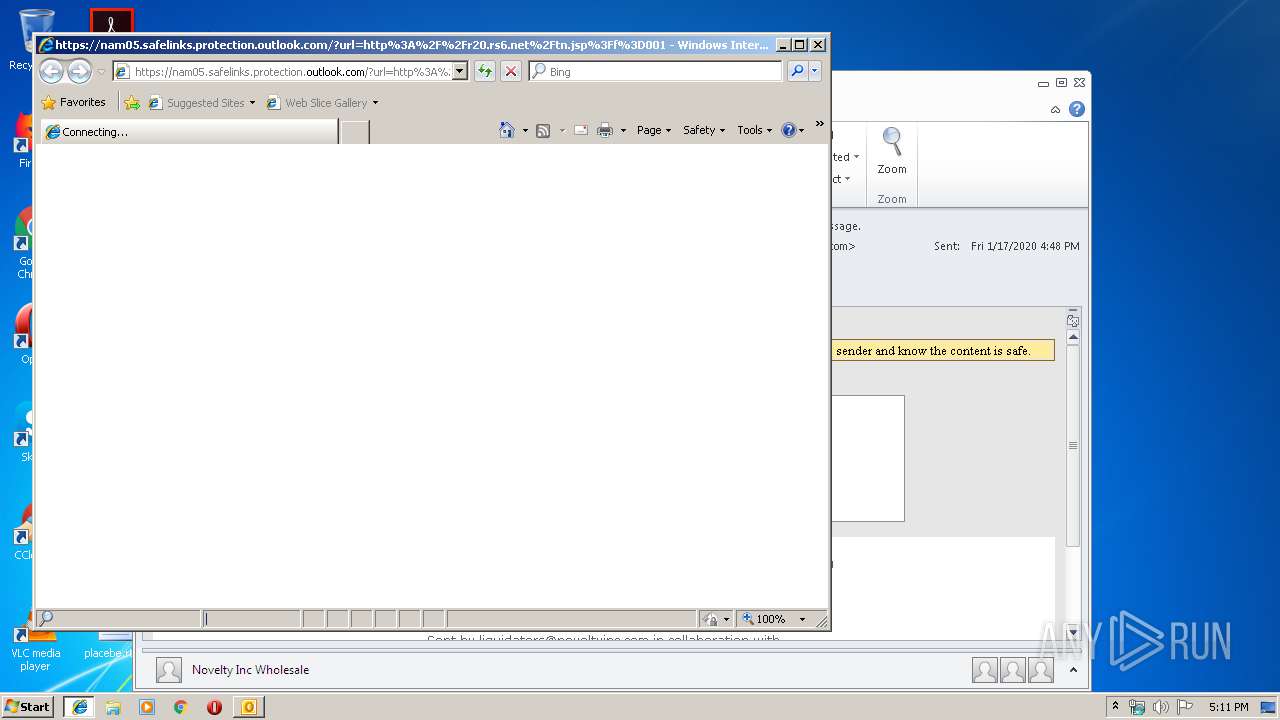
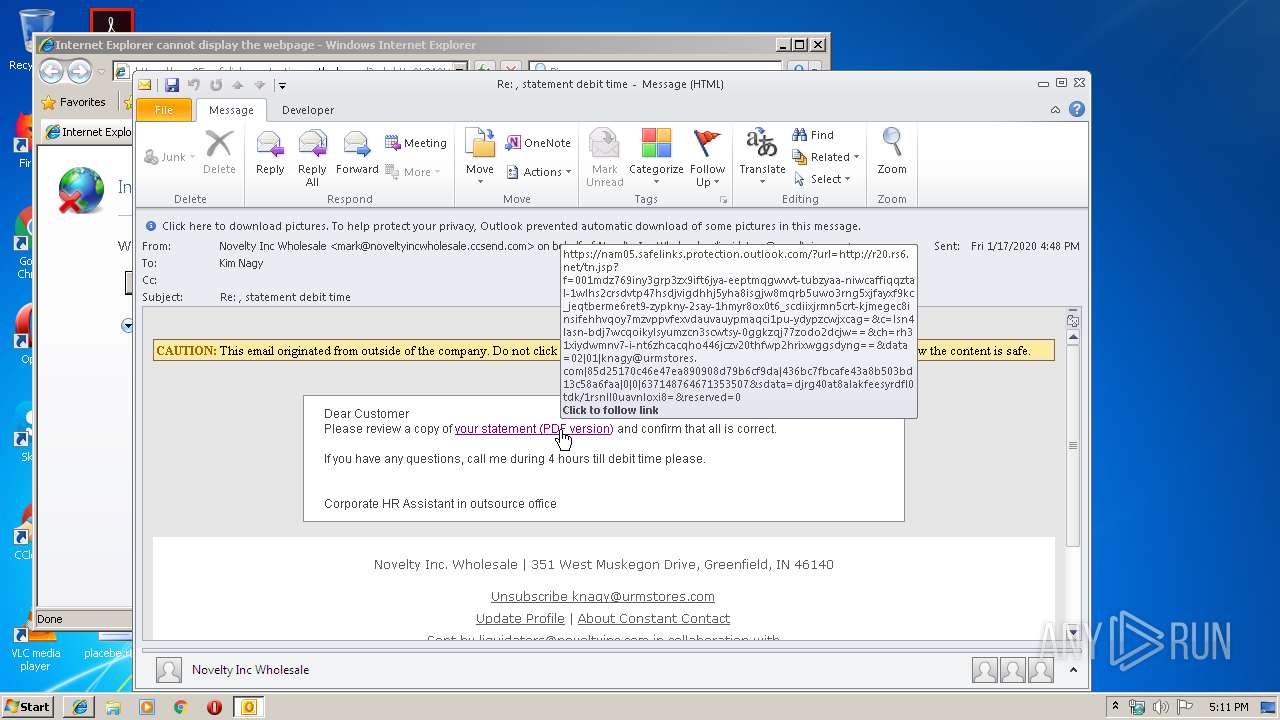
| 3372 | "C:\Program Files\Internet Explorer\iexplore.exe" https://nam05.safelinks.protection.outlook.com/?url=http%3A%2F%2Fr20.rs6.net%2Ftn.jsp%3Ff%3D001MDz769INy3GRp3zx9Ift6JYA-EePTmqgWvvT-TUbzYAa-NiWCaffIqqZtal-1wlhs2crSdVTp47hsdjVIgDhhJ5yha8iSGjw8mQrB5Uwo3RnG5XjFAyxf9kC_JeqTBerME6reT9-zyPkNy-2sAY-1hMYr8Ox0T6_scDiIxJRmN5crT-kjmEgeC8insiFEhHVQOY7MZvPpvFEXvDAUvaUYpMaqci1pU-YDYPZcWjXcag%3D%26c%3DLSN4laSn-BDj7WcQoIKylsYumzcn3sCWTsY-0gGkzqj77zoDO2dCJw%3D%3D%26ch%3Drh31xiydWMNv7-I-nt6zHcacQhO446jCZv20tHFWp2HrIXWGGSDYNg%3D%3D&data=02%7C01%7Cknagy%40urmstores.com%7C85d25170c46e47ea890908d79b6cf9da%7C436bc7fbcafe43a8b503bd13c58a6faa%7C0%7C0%7C637148764671353507&sdata=DJRG40at8ALakfEeSYRdFl0TDK%2F1RSnll0UAvnLOxi8%3D&reserved=0 | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 861
Read events
1 251
Write events
591
Delete events
19
Modification events
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1345388724 | |||
| (PID) Process: | (2524) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
0
Text files
40
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA89E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2524 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 2524 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_5C09F2CC5B437949912040B4AA43E88B.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 2108 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\V2PFGPYD\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2524 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2108 | iexplore.exe | 104.47.48.28:443 | nam05.safelinks.protection.outlook.com | Microsoft Corporation | US | whitelisted |
3372 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2108 | iexplore.exe | 23.43.115.188:443 | files.constantcontact.com | Akamai International B.V. | NL | unknown |
2108 | iexplore.exe | 208.75.122.11:80 | r20.rs6.net | Constant Contact, Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
nam05.safelinks.protection.outlook.com |
| whitelisted |
www.bing.com |
| whitelisted |
r20.rs6.net |
| whitelisted |
files.constantcontact.com |
| whitelisted |