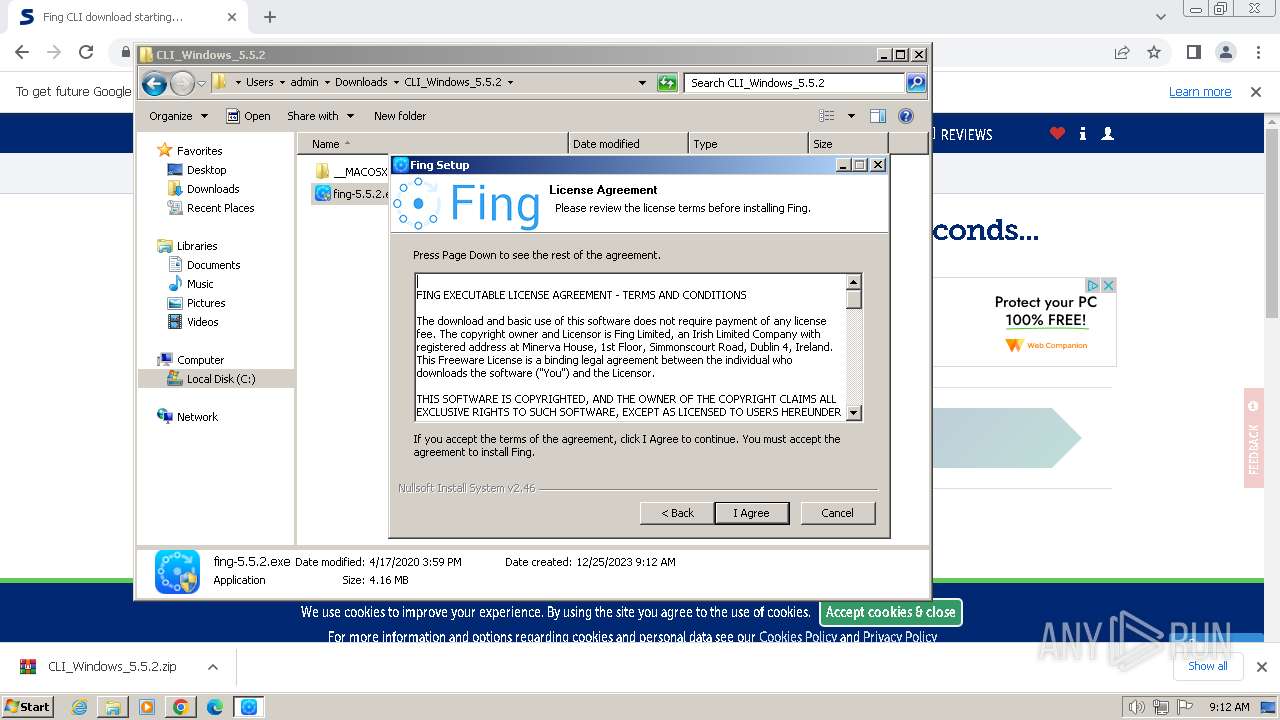
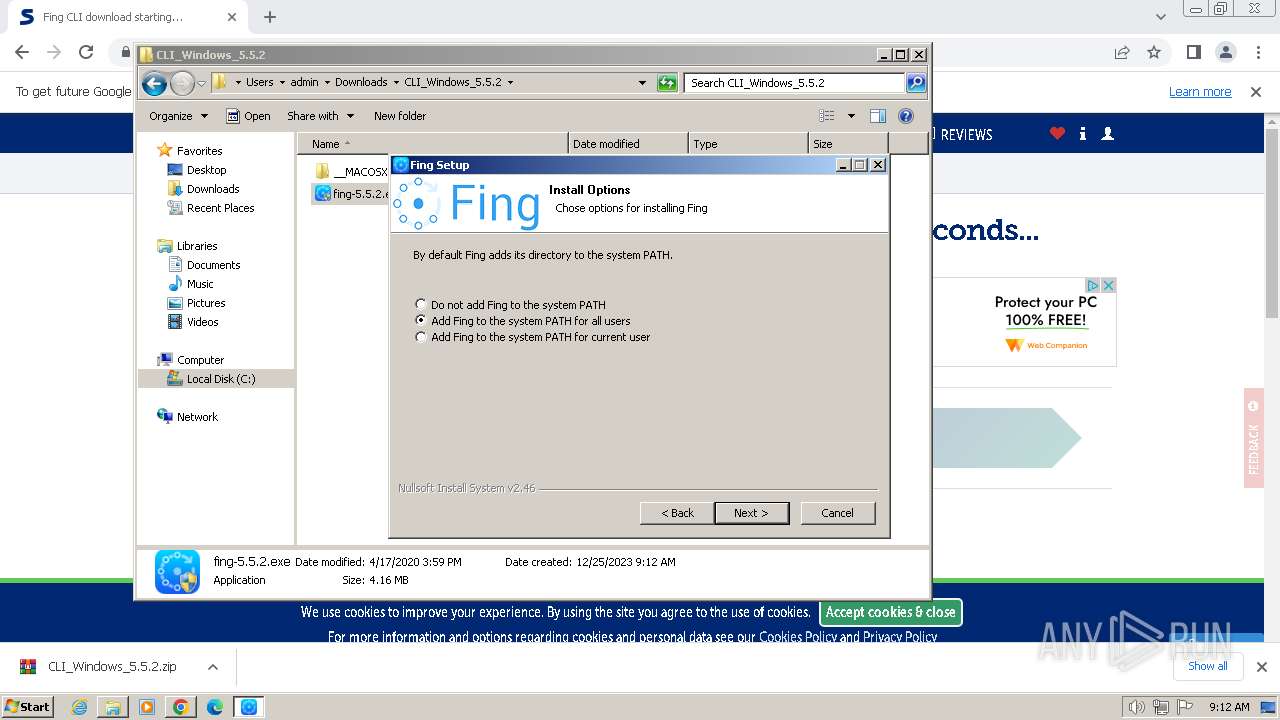
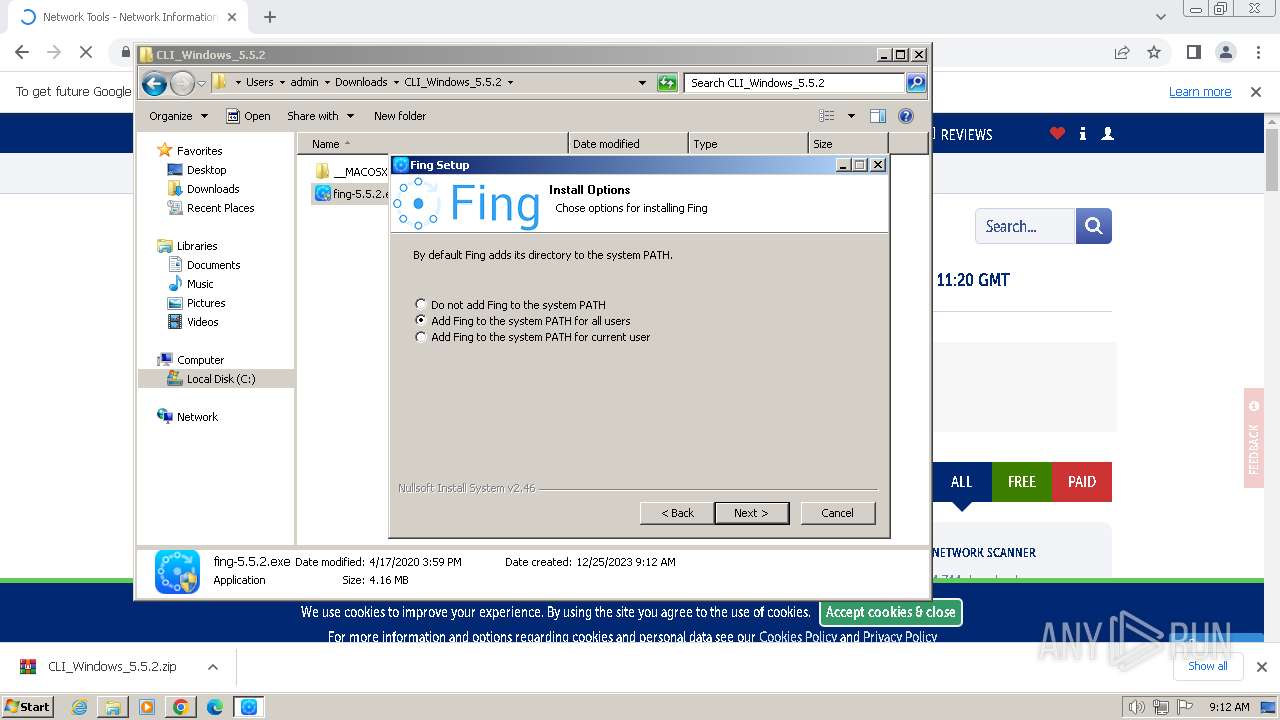
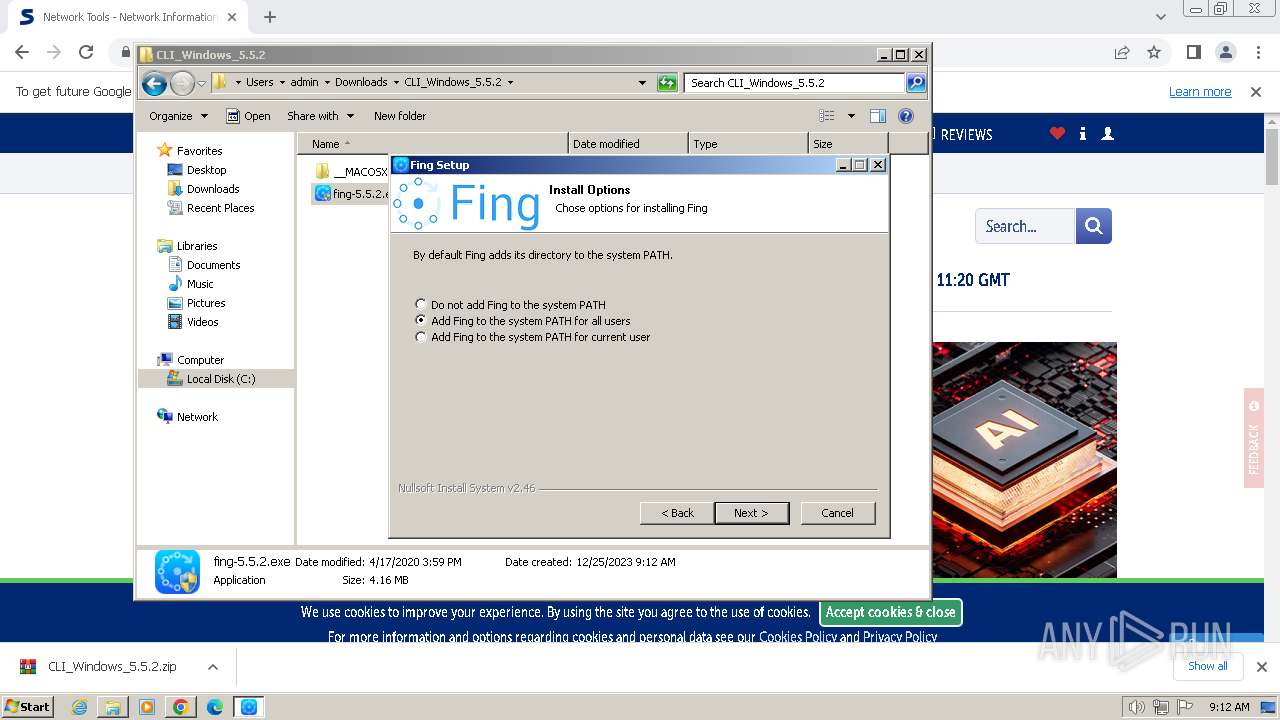
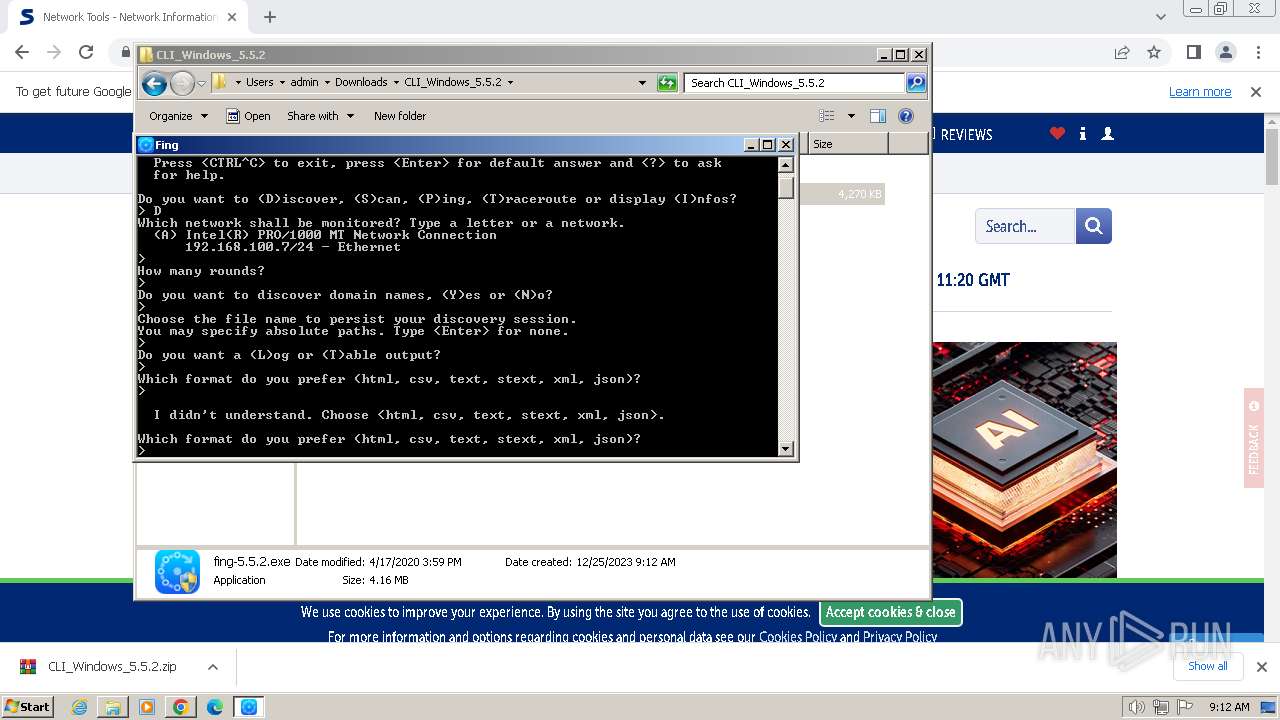
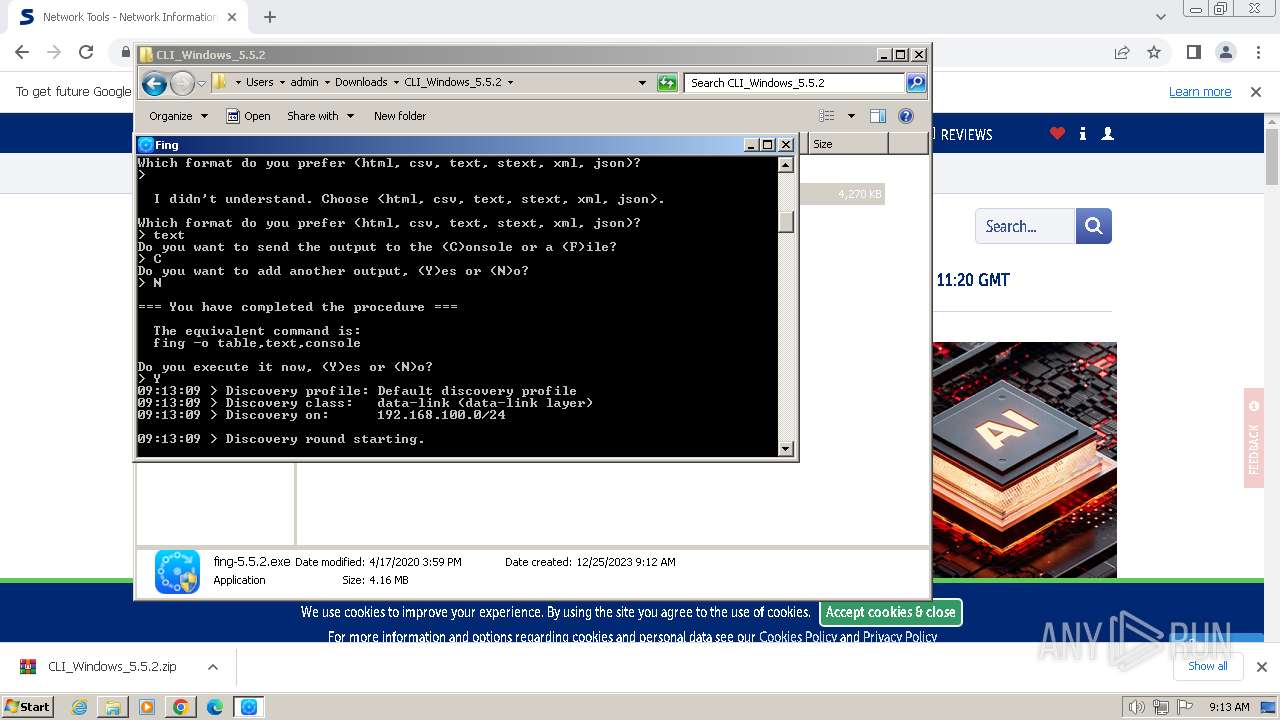
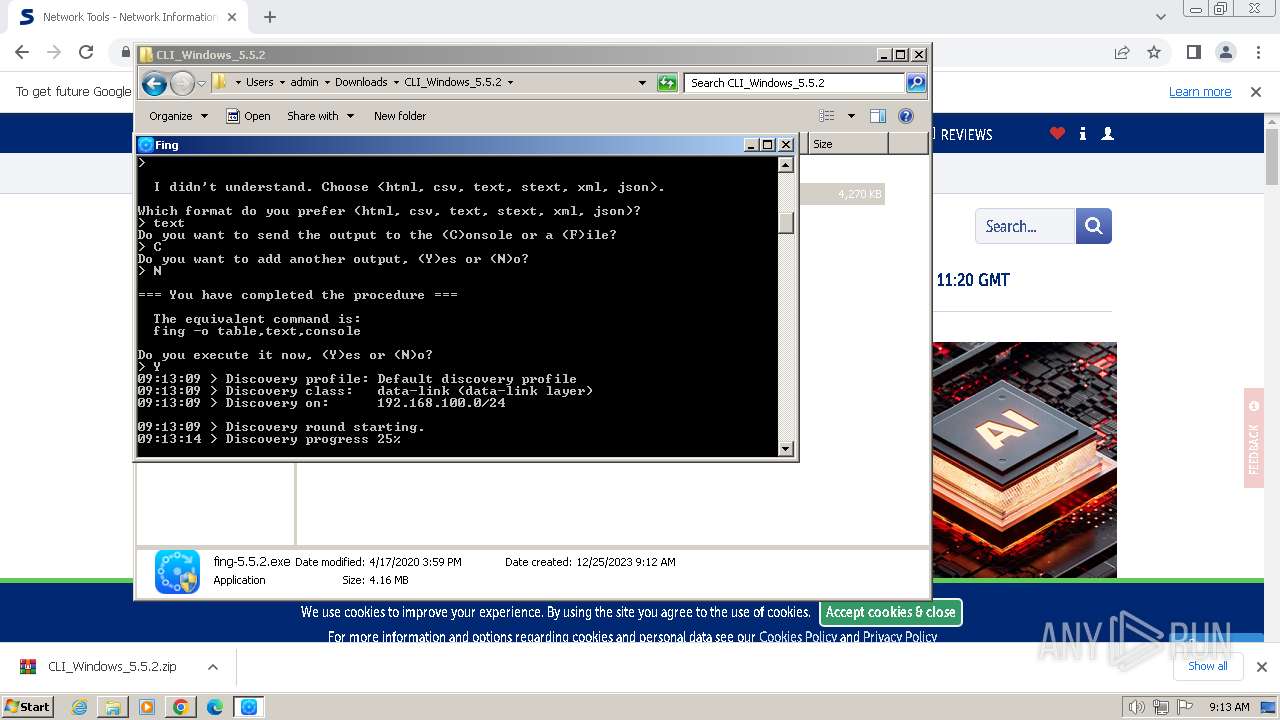
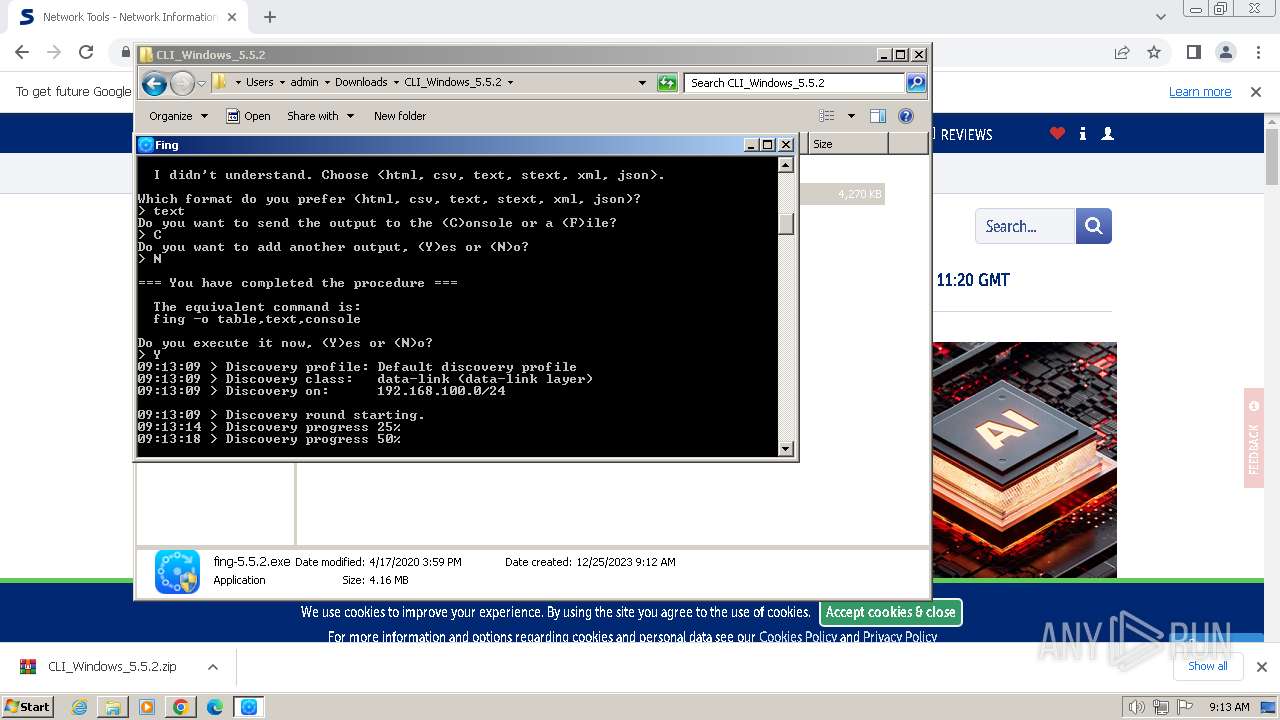
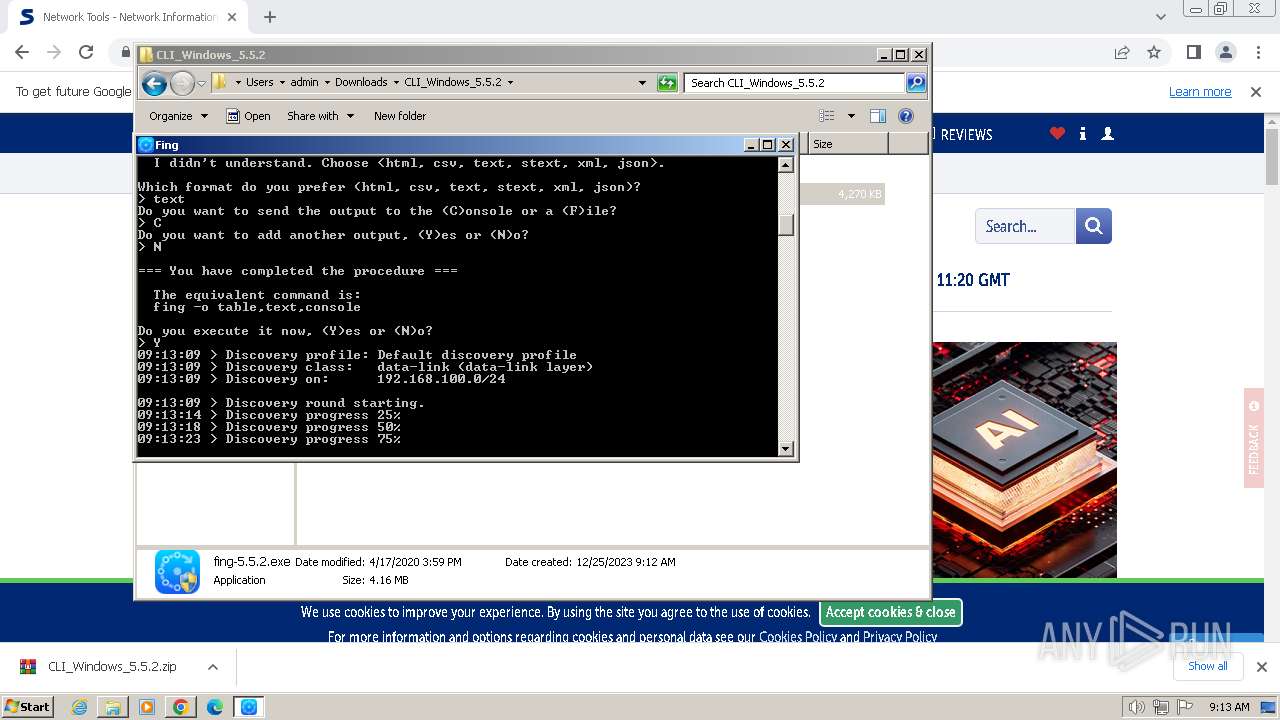
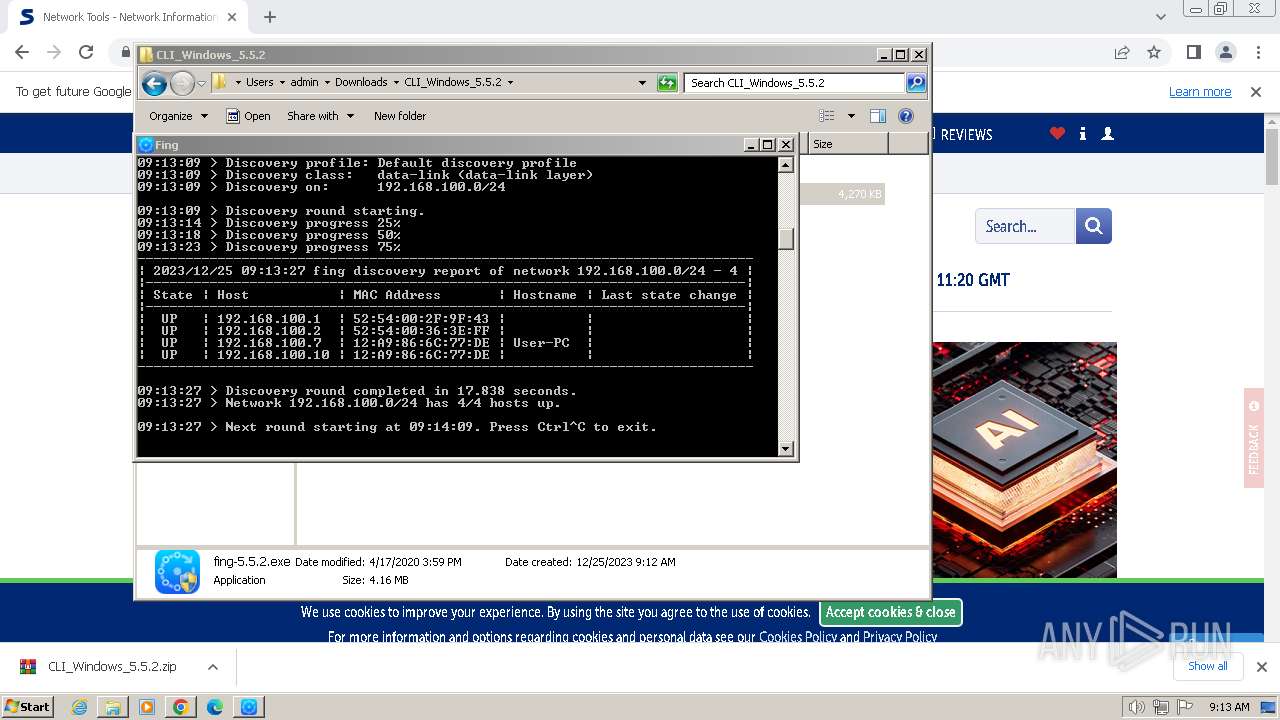
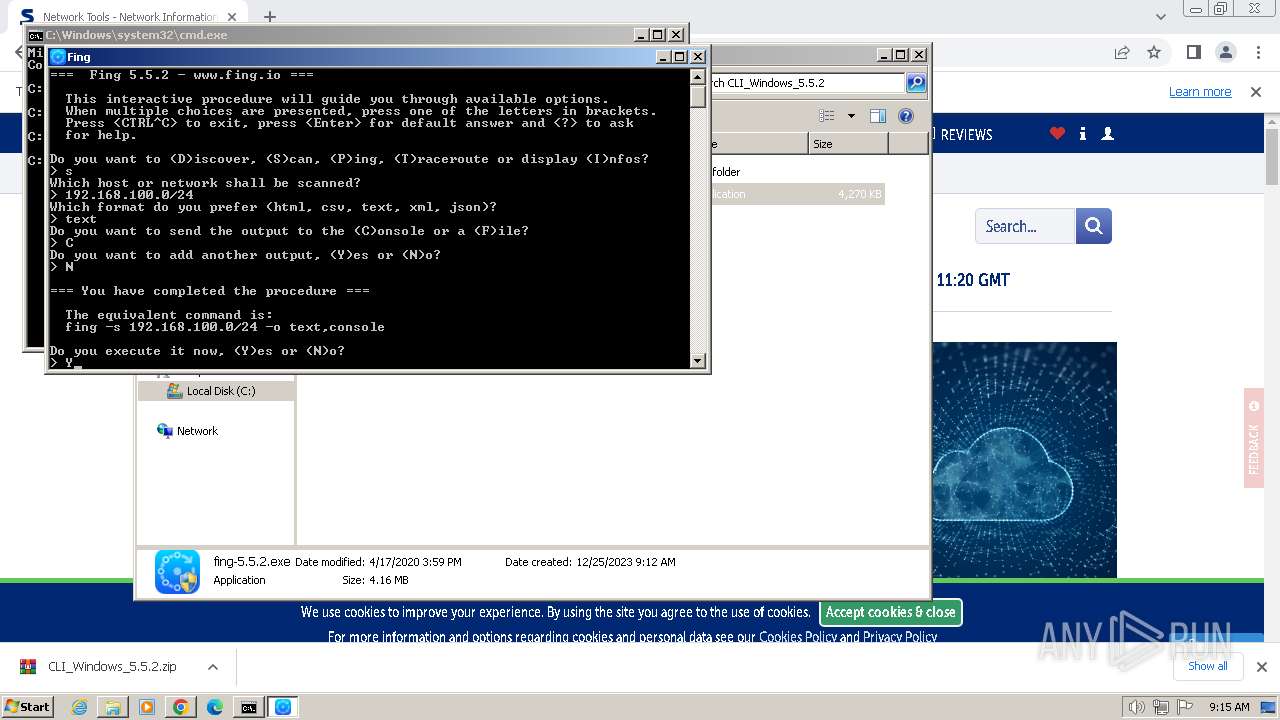
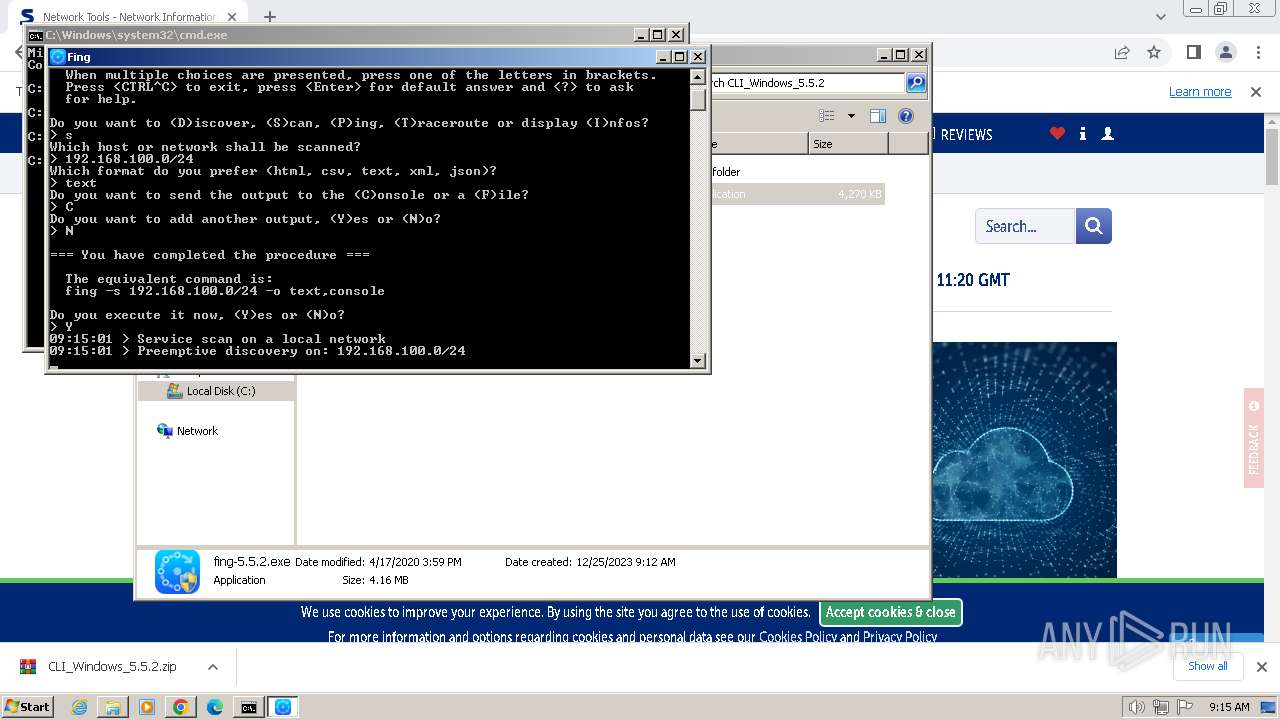
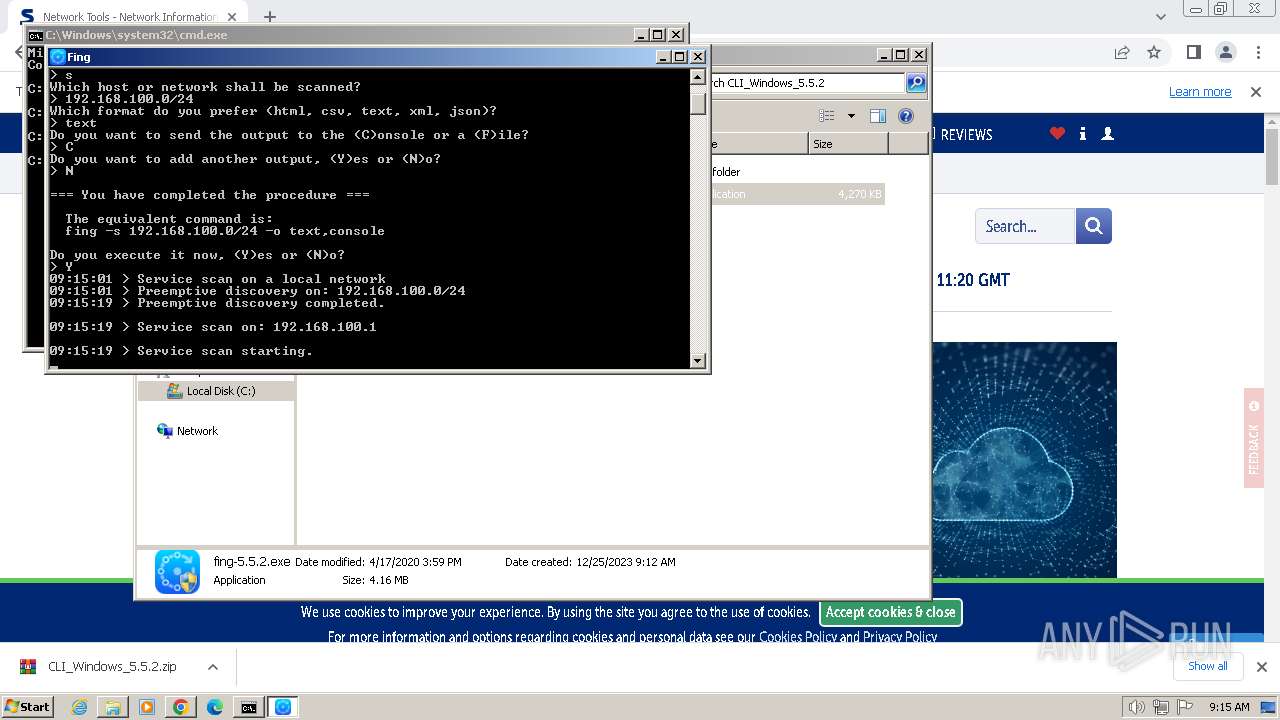
| URL: | https://www.softpedia.com/get/Network-Tools/Network-Information/Fing.shtml |
| Full analysis: | https://app.any.run/tasks/f5e6826a-ce8a-4517-87c2-f9f561310183 |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2023, 09:11:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E3312C1503286F469ED6E1D39041B449 |
| SHA1: | 9CC5048F0BA448986A16C5971669F648E0761F3B |
| SHA256: | E05CE29D4A98D4155E8F83B683F56503A49F3B35EECC67C645C7FB7AE2770883 |
| SSDEEP: | 3:N8DSLav1RwrKex10PAMKLK+CLKGn:2OLUbwrPx1KAMK++CLKGn |
MALICIOUS
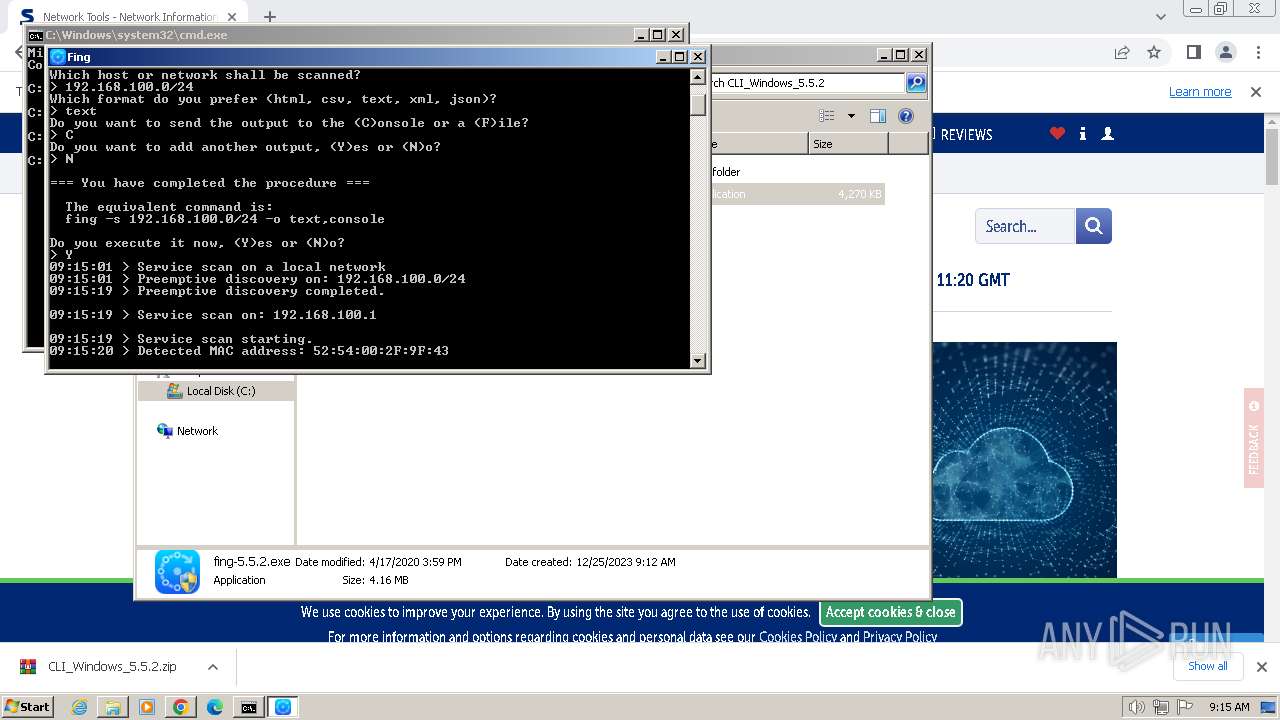
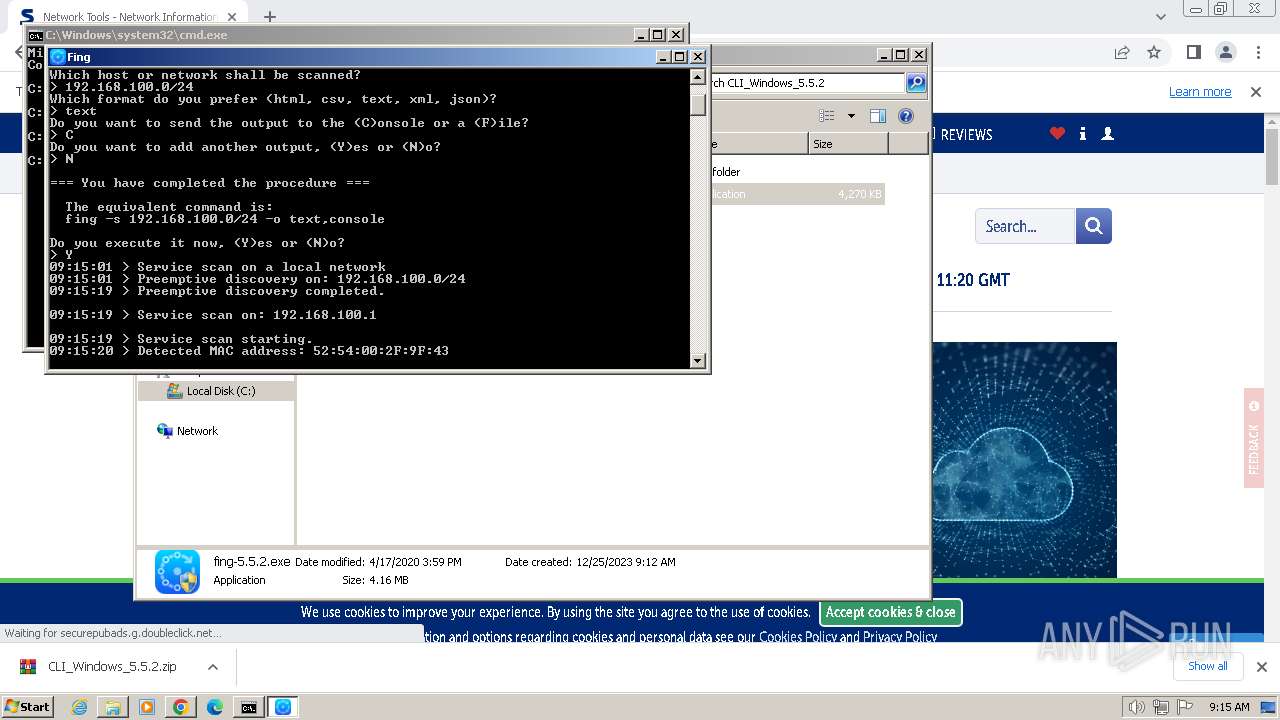
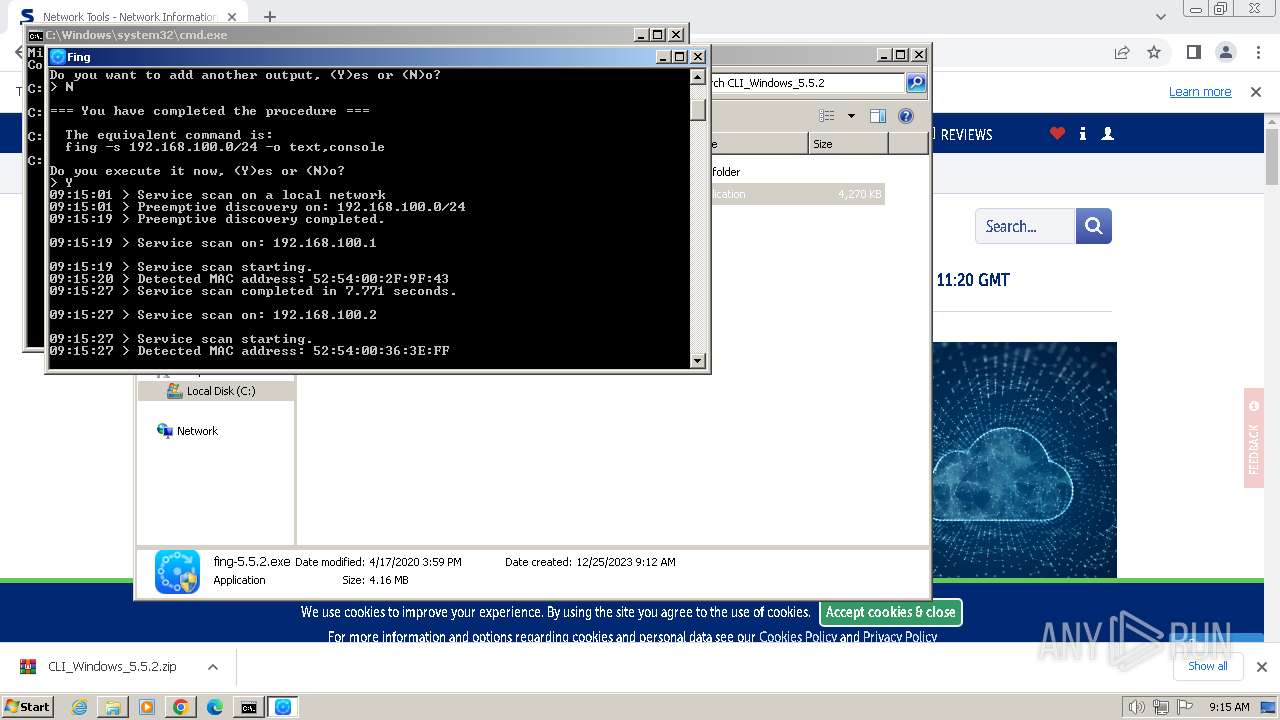
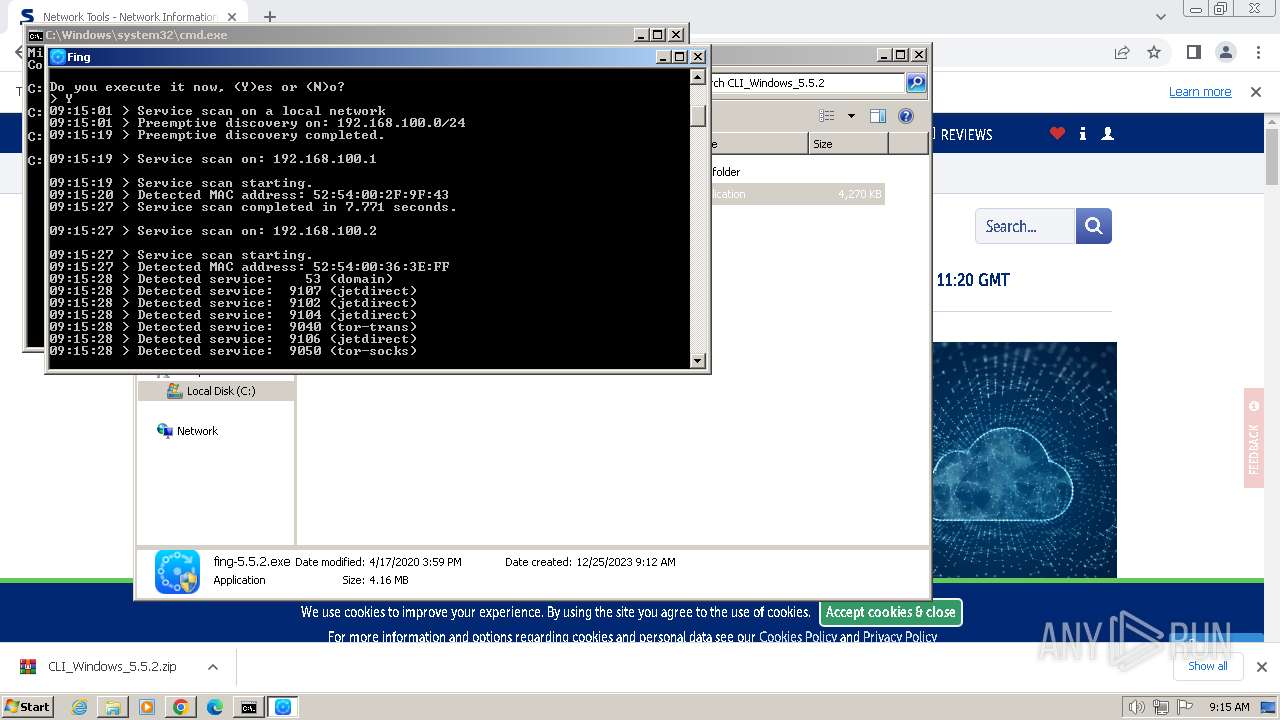
Starts NET.EXE for service management
- nsEDE9.tmp (PID: 2660)
- nsEED5.tmp (PID: 3040)
- net.exe (PID: 2896)
- nsEE57.tmp (PID: 1020)
- net.exe (PID: 2972)
- net.exe (PID: 924)
- nsFD3E.tmp (PID: 664)
- net.exe (PID: 3696)
Creates a writable file in the system directory
- winpcap-fing-4.1.3.exe (PID: 292)
SUSPICIOUS
The process creates files with name similar to system file names
- winpcap-fing-4.1.3.exe (PID: 292)
Starts application with an unusual extension
- winpcap-fing-4.1.3.exe (PID: 292)
Creates files in the driver directory
- winpcap-fing-4.1.3.exe (PID: 292)
Drops a system driver (possible attempt to evade defenses)
- winpcap-fing-4.1.3.exe (PID: 292)
Creates or modifies Windows services
- winpcap-fing-4.1.3.exe (PID: 292)
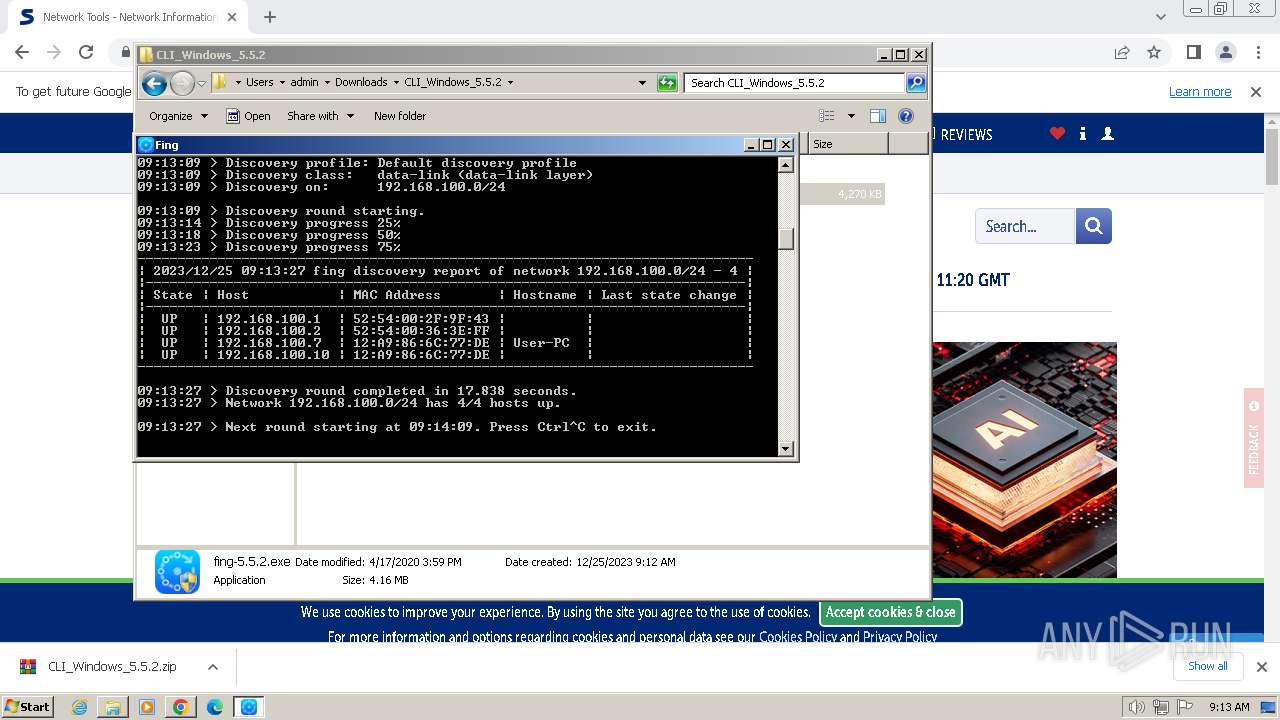
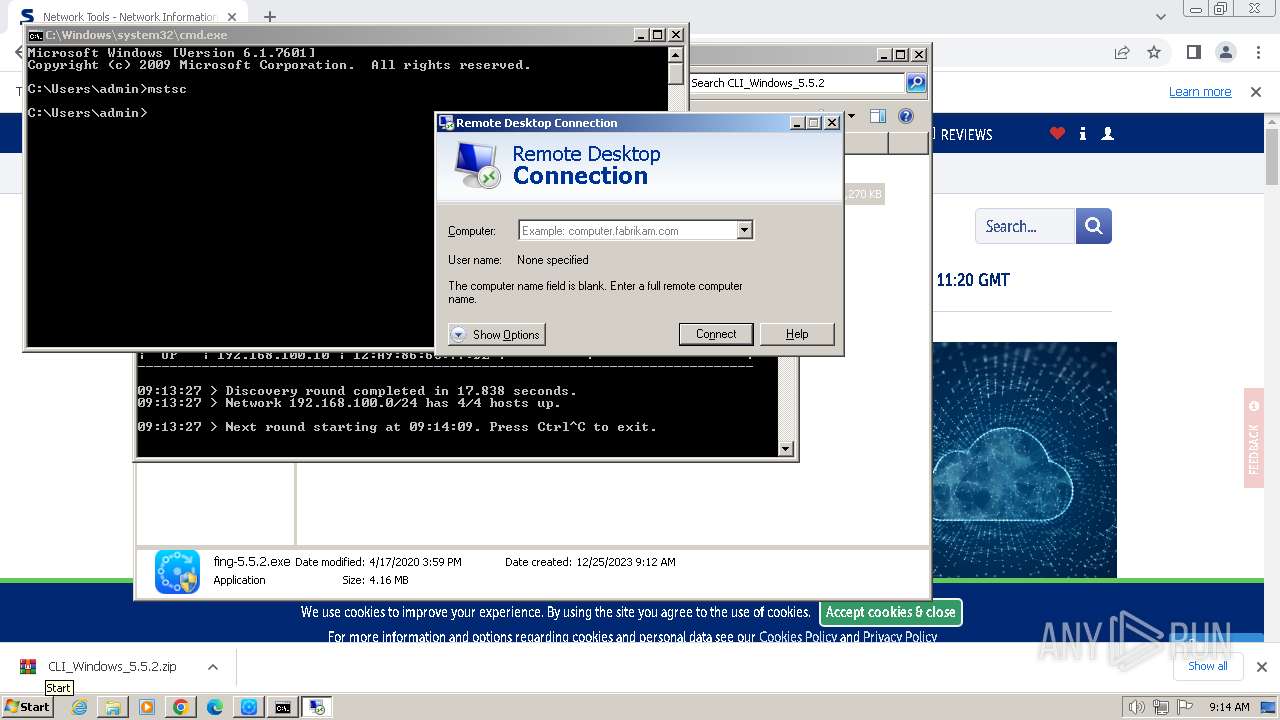
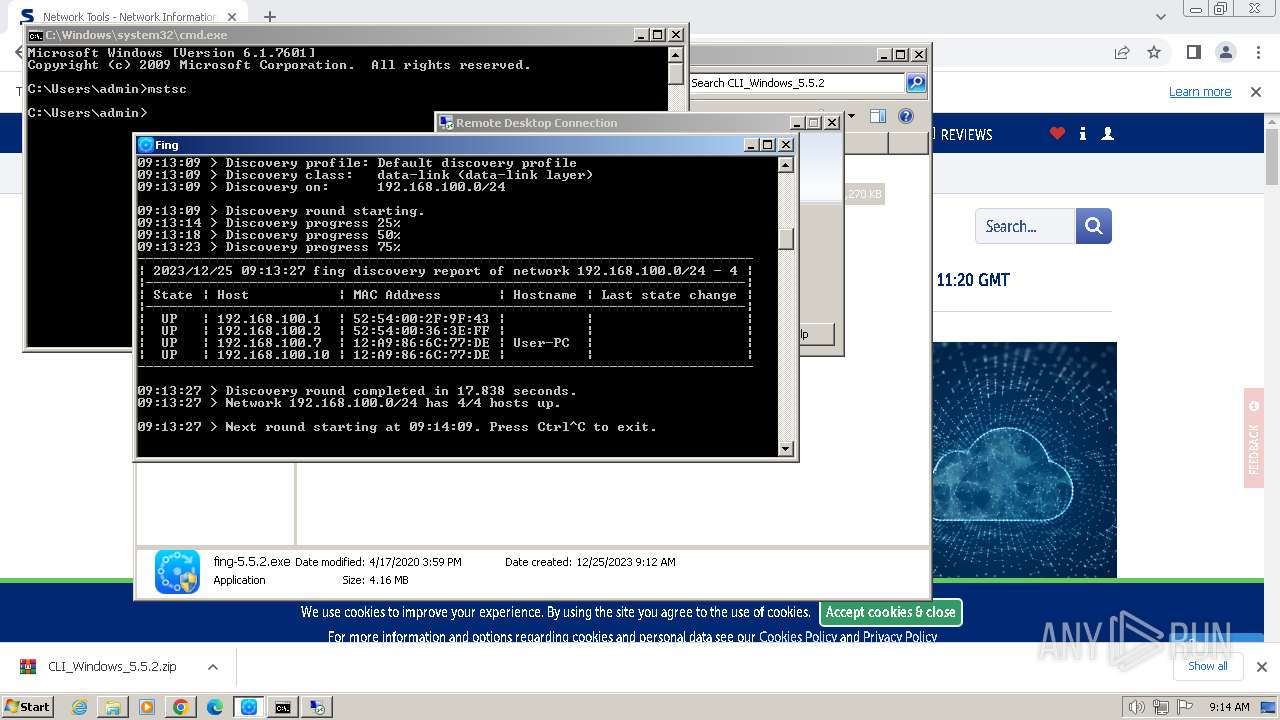
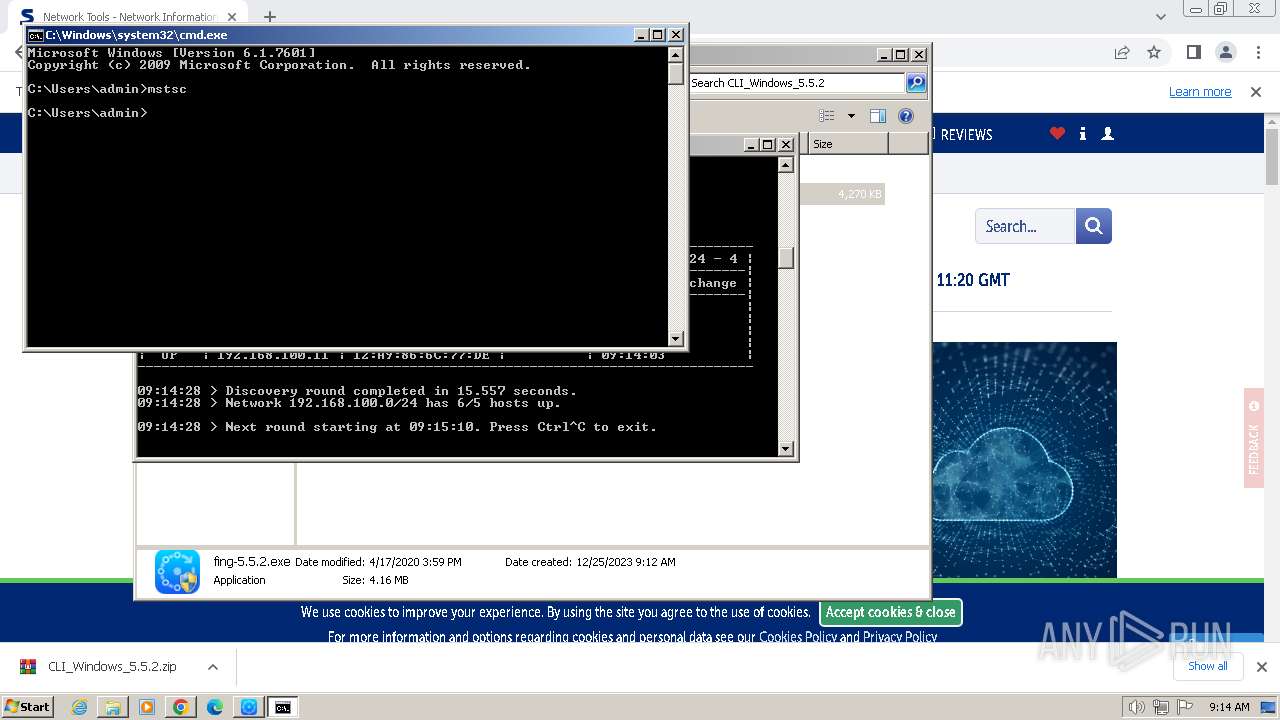
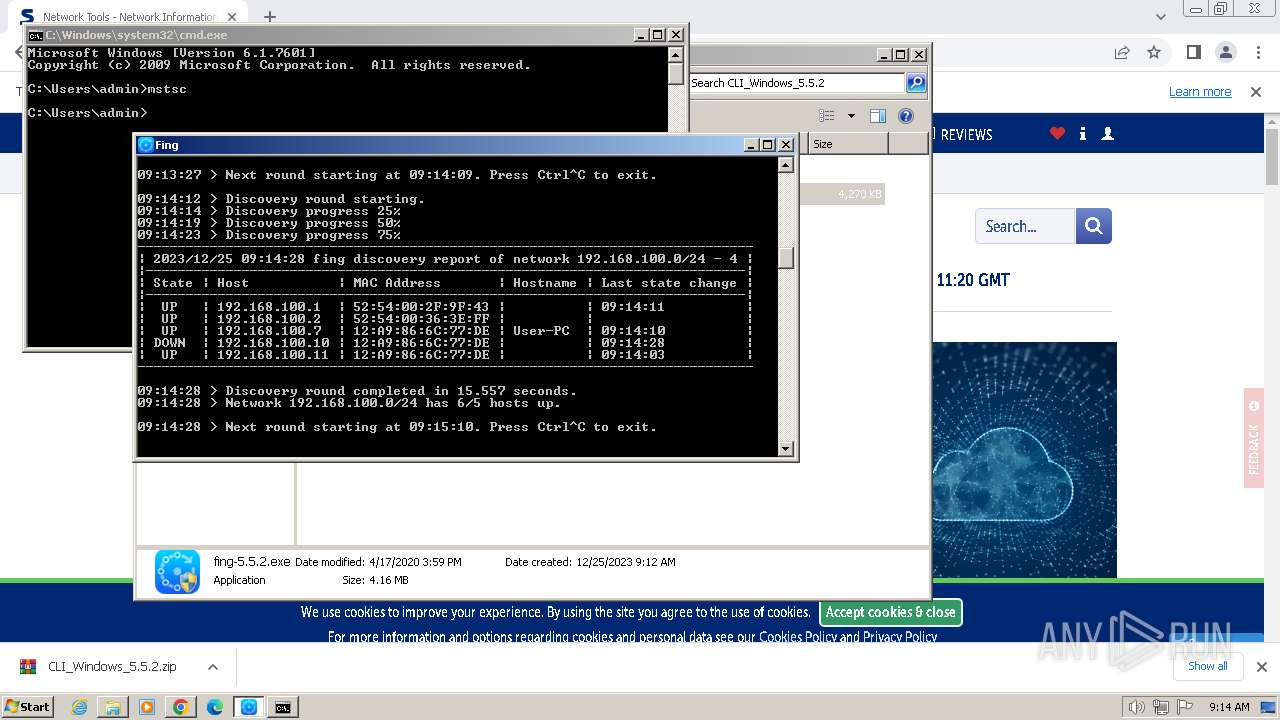
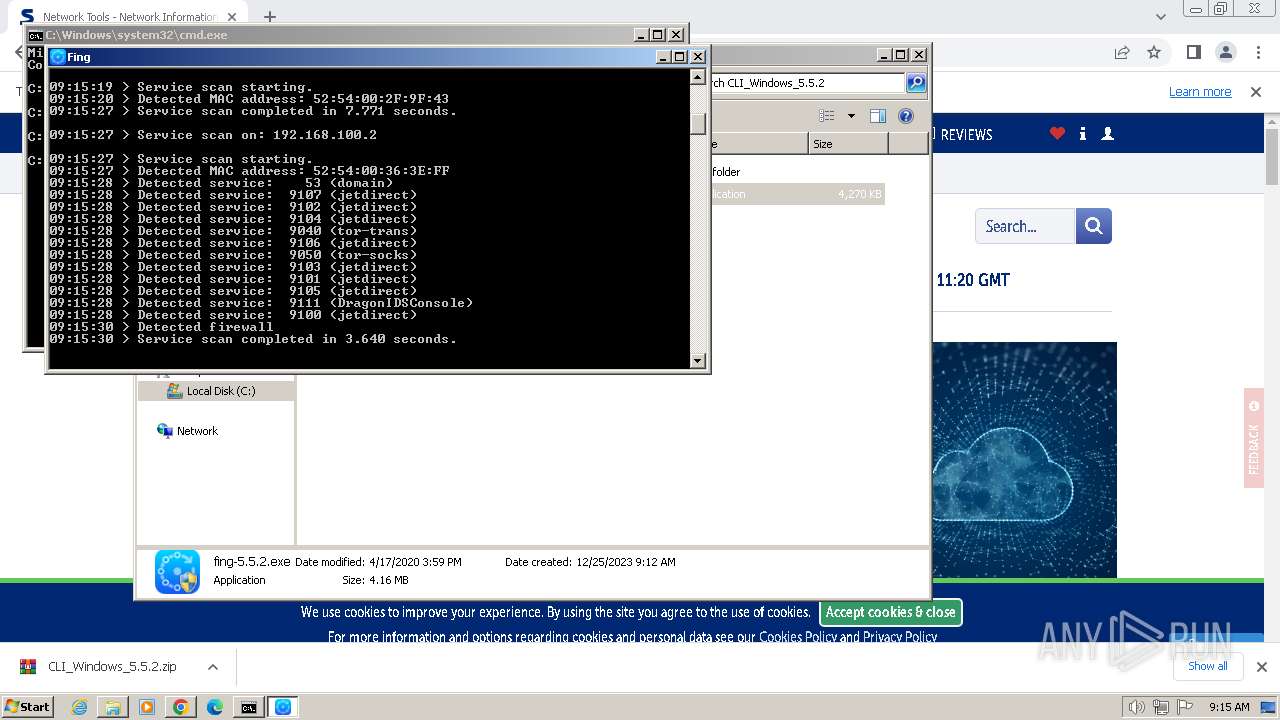
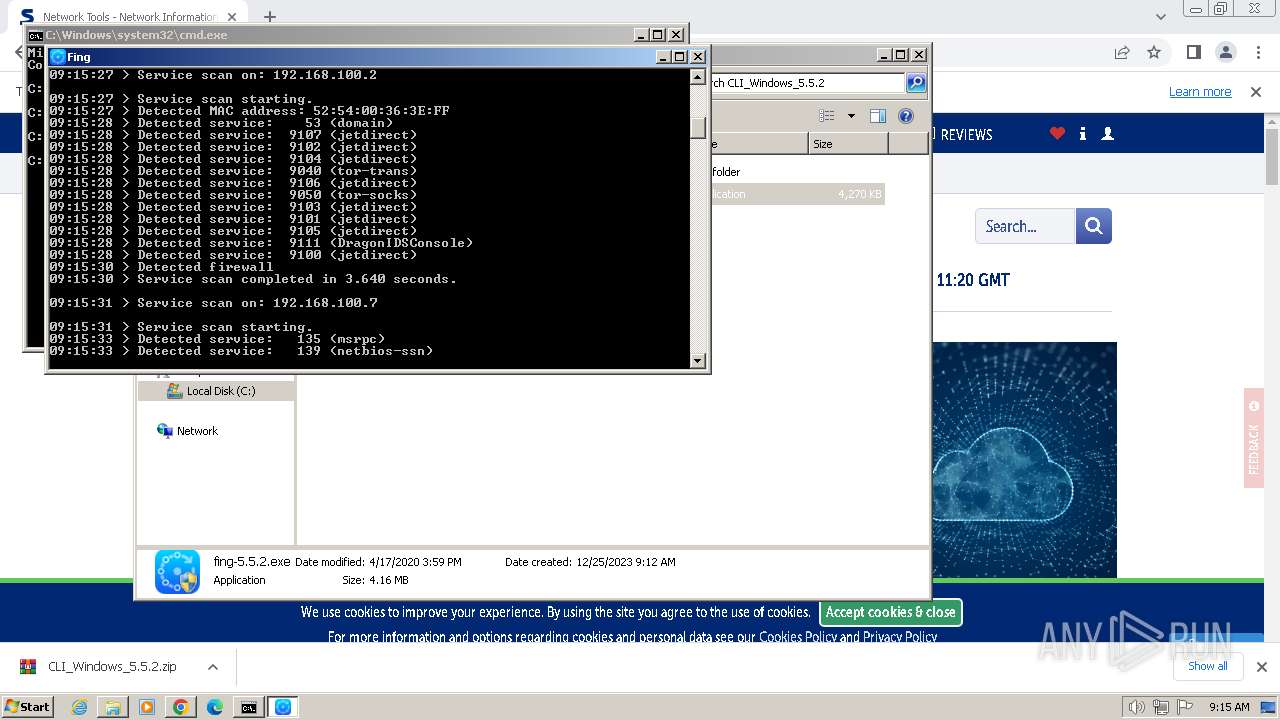
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 2440)
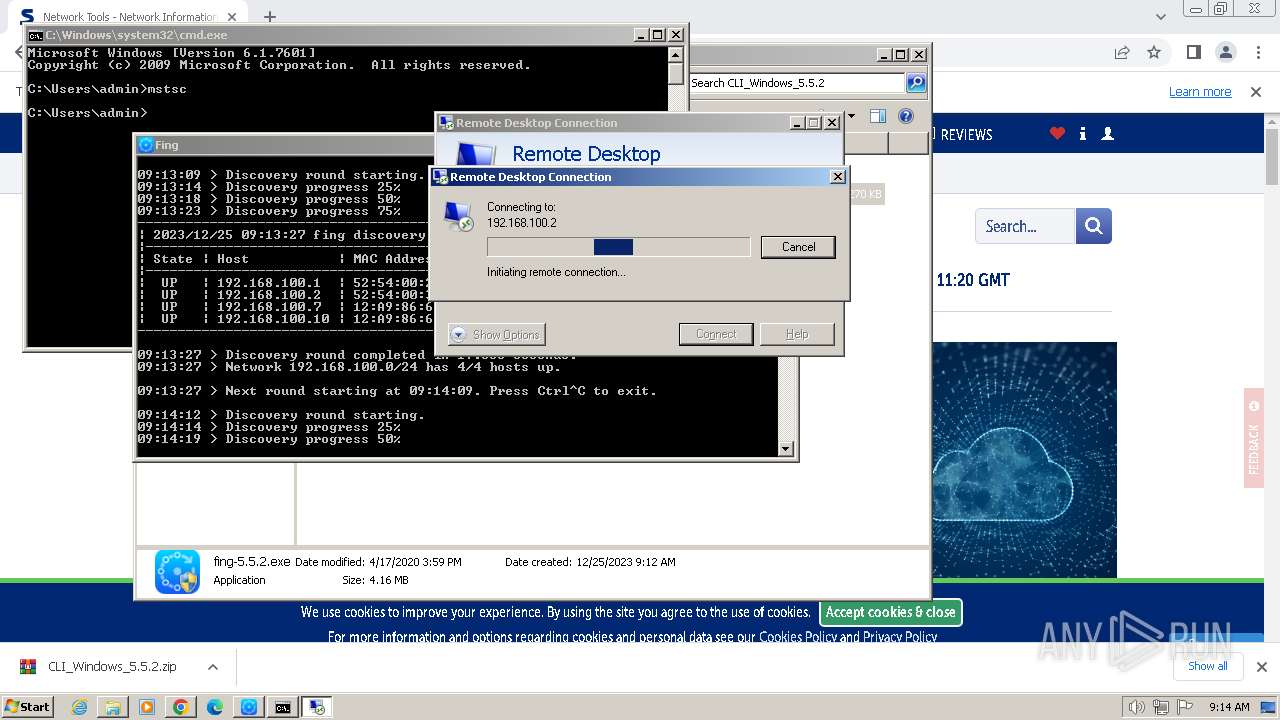
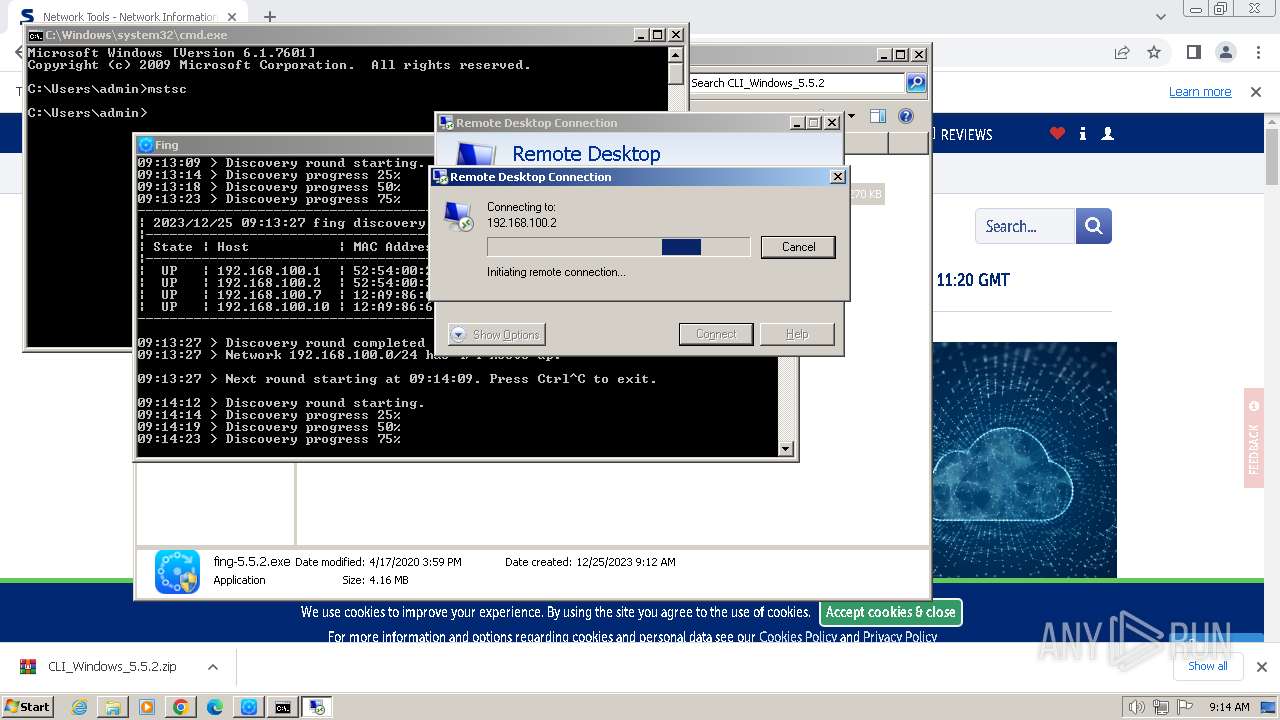
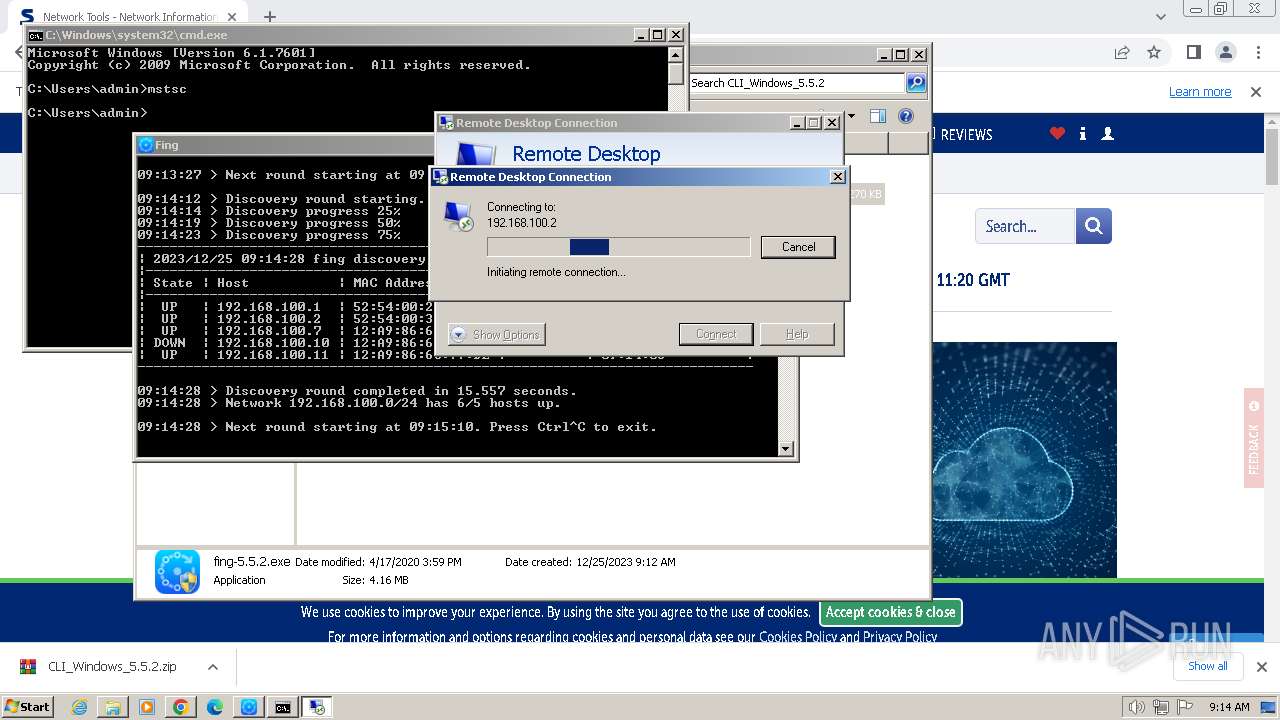
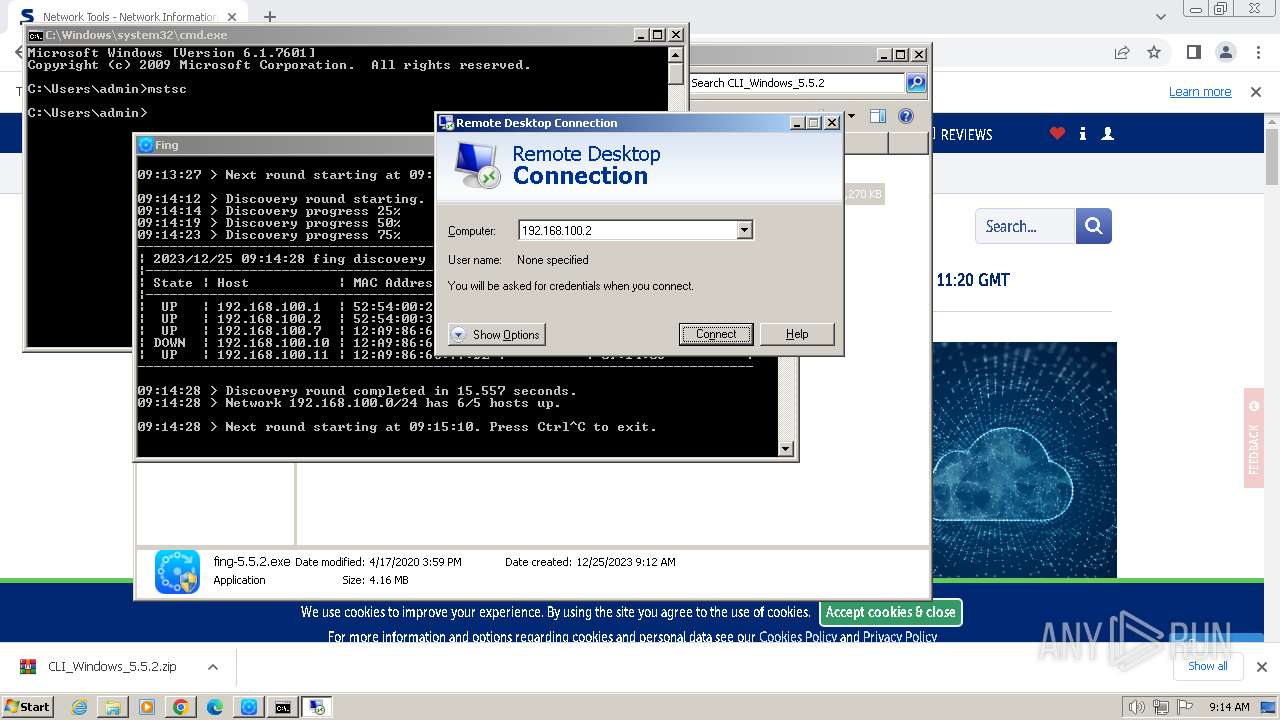
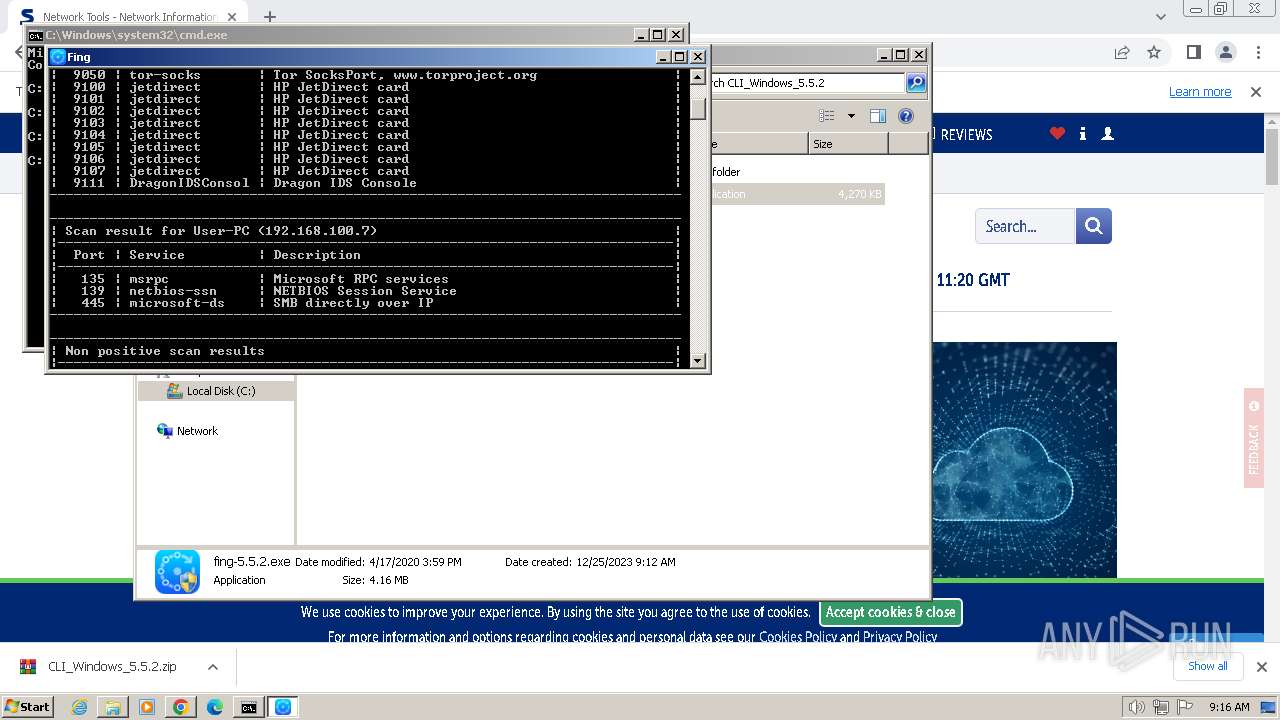
Connects to unusual port
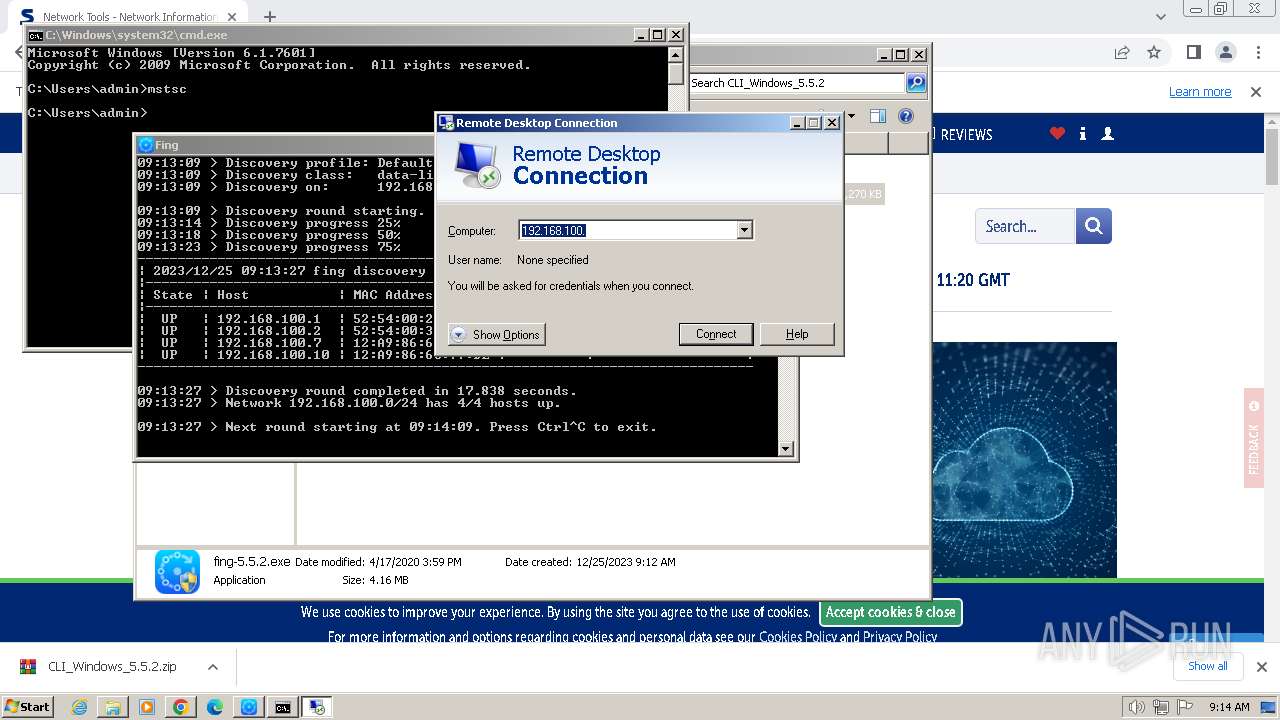
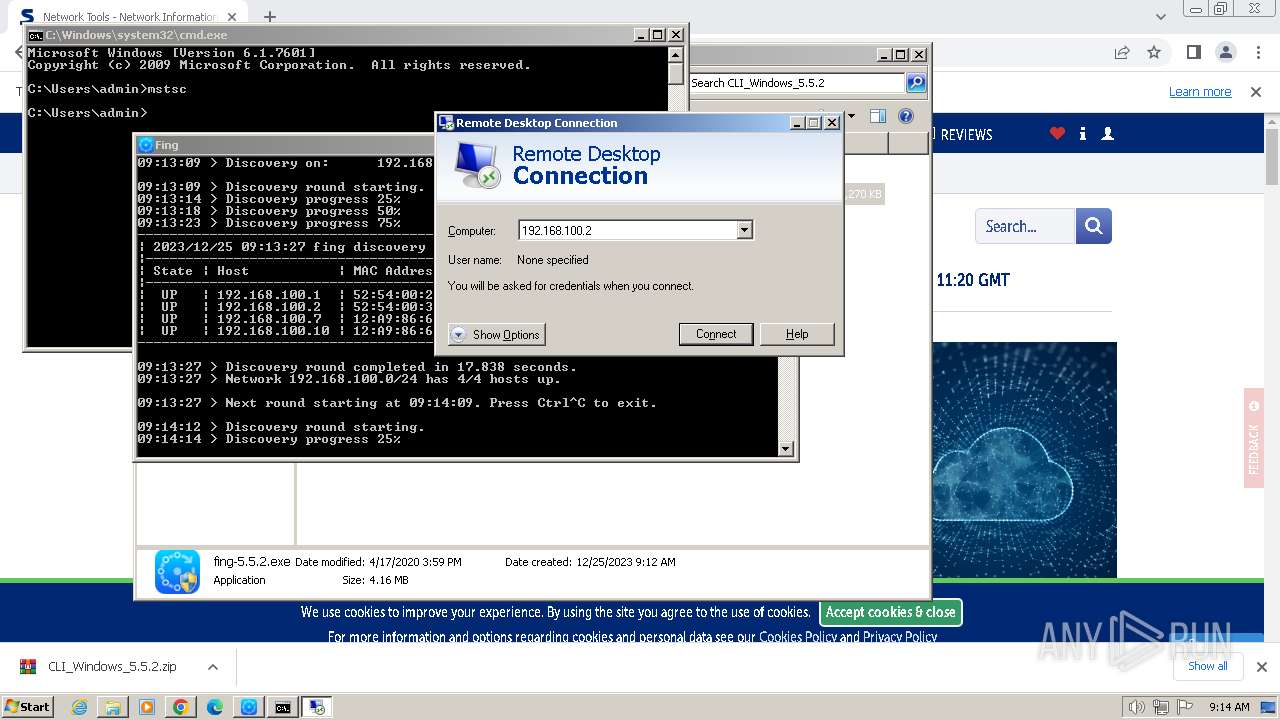
- mstsc.exe (PID: 2932)
INFO
The process uses the downloaded file
- chrome.exe (PID: 4036)
- WinRAR.exe (PID: 2868)
Application launched itself
- chrome.exe (PID: 116)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2868)
- fing-5.5.2.exe (PID: 3308)
- winpcap-fing-4.1.3.exe (PID: 292)
- chrome.exe (PID: 560)
Manual execution by a user
- fing-5.5.2.exe (PID: 3508)
- WinRAR.exe (PID: 2868)
- fing-5.5.2.exe (PID: 3308)
- cmd.exe (PID: 2440)
- cmd.exe (PID: 3256)
- fing.exe (PID: 3704)
- fing.exe (PID: 3660)
Checks supported languages
- fing-5.5.2.exe (PID: 3308)
- winpcap-fing-4.1.3.exe (PID: 292)
- nsEDE9.tmp (PID: 2660)
- nsEE57.tmp (PID: 1020)
- nsEED5.tmp (PID: 3040)
- nsFD3E.tmp (PID: 664)
- fing.exe (PID: 3704)
- fing.exe (PID: 3660)
Reads the computer name
- fing-5.5.2.exe (PID: 3308)
- winpcap-fing-4.1.3.exe (PID: 292)
- fing.exe (PID: 3660)
- fing.exe (PID: 3704)
Create files in a temporary directory
- fing-5.5.2.exe (PID: 3308)
- winpcap-fing-4.1.3.exe (PID: 292)
Creates files in the program directory
- fing-5.5.2.exe (PID: 3308)
- winpcap-fing-4.1.3.exe (PID: 292)
Process drops legitimate windows executable
- fing-5.5.2.exe (PID: 3308)
The process drops C-runtime libraries
- fing-5.5.2.exe (PID: 3308)
Reads the machine GUID from the registry
- fing-5.5.2.exe (PID: 3308)
Malware-specific behavior (creating "System.dll" in Temp)
- winpcap-fing-4.1.3.exe (PID: 292)
Reads Environment values
- winpcap-fing-4.1.3.exe (PID: 292)
- fing-5.5.2.exe (PID: 3308)
Creates files or folders in the user directory
- fing.exe (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
114
Monitored processes
65
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://www.softpedia.com/get/Network-Tools/Network-Information/Fing.shtml" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1064 --field-trial-handle=1108,i,1780658768134748717,16099976385604303851,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1984 --field-trial-handle=1108,i,1780658768134748717,16099976385604303851,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 292 | "C:\Program Files\Fing\bin\winpcap-fing-4.1.3.exe" | C:\Program Files\Fing\bin\winpcap-fing-4.1.3.exe | — | fing-5.5.2.exe | |||||||||||
User: admin Integrity Level: HIGH Description: WinPcap 4.1.3 for Fing installer Exit code: 0 Version: 4.1.0.2980 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1268 --field-trial-handle=1108,i,1780658768134748717,16099976385604303851,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=4200 --field-trial-handle=1108,i,1780658768134748717,16099976385604303851,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2964 --field-trial-handle=1108,i,1780658768134748717,16099976385604303851,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 604 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --mojo-platform-channel-handle=4956 --field-trial-handle=1108,i,1780658768134748717,16099976385604303851,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Local\Temp\nsxE731.tmp\nsFD3E.tmp" net start npf | C:\Users\admin\AppData\Local\Temp\nsxE731.tmp\nsFD3E.tmp | — | winpcap-fing-4.1.3.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3380 --field-trial-handle=1108,i,1780658768134748717,16099976385604303851,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
9 378
Read events
9 254
Write events
123
Delete events
1
Modification events
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (116) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
49
Suspicious files
403
Text files
82
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFdfb0a.TMP | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFdfb29.TMP | text | |
MD5:ADB669AB4CD1C63883C64FB0DBA2C7DA | SHA256:18BFF89047EC5B122573D089B3DC7A7DD14A5A7A515B2D8141584B41E723253F | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFdfb1a.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe01e0.TMP | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old~RFe1c6d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
2 274
DNS requests
279
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 6.05 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 10.0 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 8.26 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 9.90 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 17.7 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 42.8 Kb | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 8.26 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 73.0 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 161 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
116 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
316 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | unknown |
316 | chrome.exe | 104.22.12.228:443 | www.softpedia.com | CLOUDFLARENET | — | unknown |
316 | chrome.exe | 142.250.185.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
316 | chrome.exe | 142.250.184.194:443 | securepubads.g.doubleclick.net | GOOGLE | US | unknown |
316 | chrome.exe | 104.22.13.228:443 | www.softpedia.com | CLOUDFLARENET | — | unknown |
316 | chrome.exe | 18.245.86.24:443 | cmp.quantcast.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
www.softpedia.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
cdnssl.softpedia.com |
| unknown |
cmp.quantcast.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
windows-cdn.softpedia.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
cmp.inmobi.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
316 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
316 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |