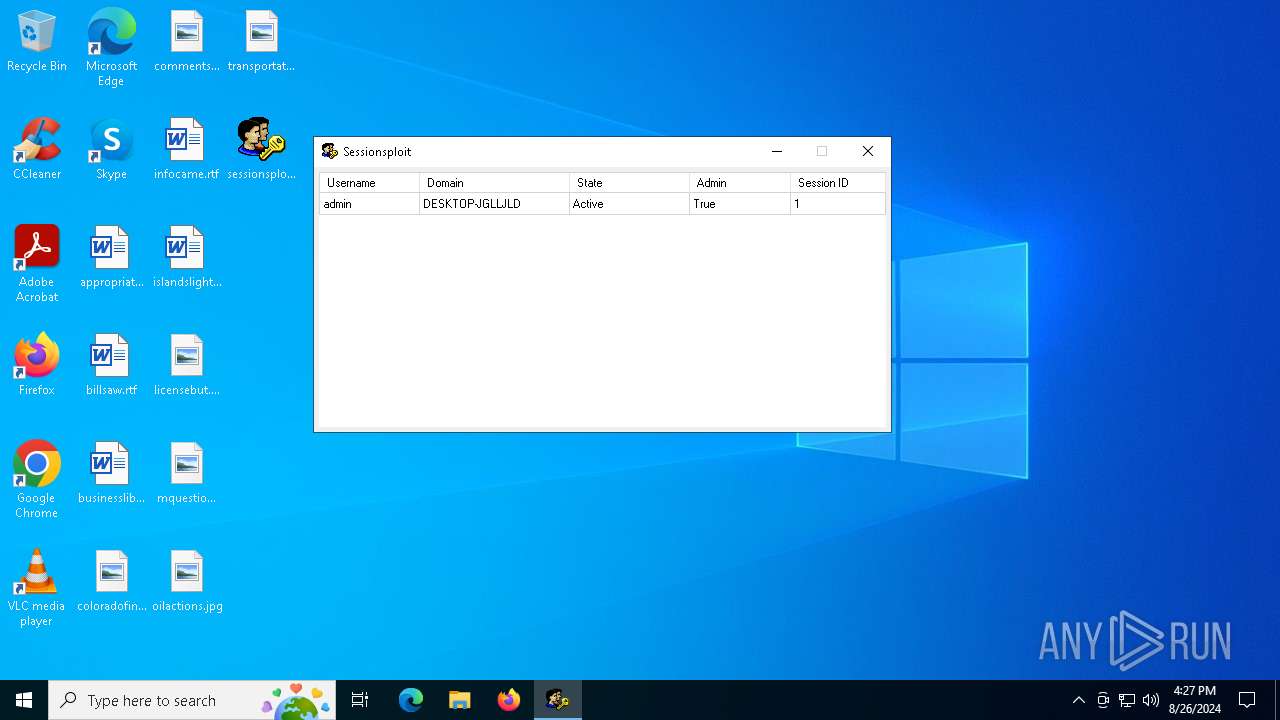
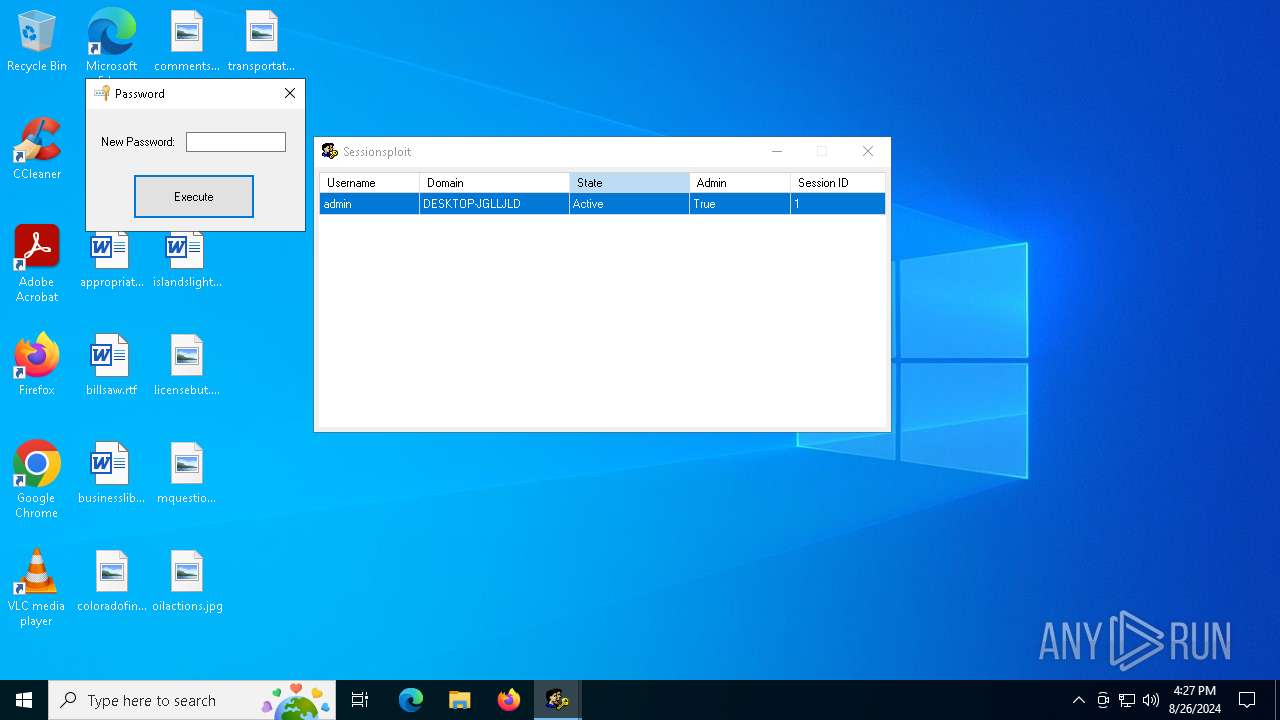
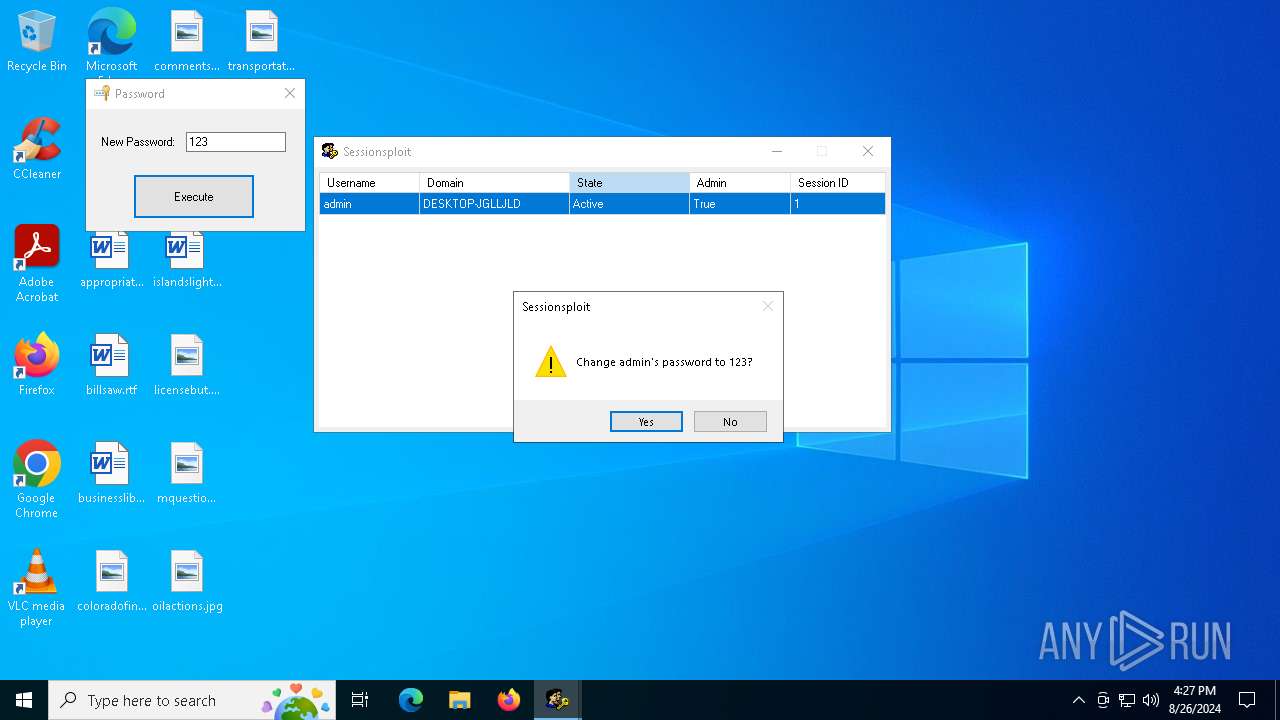
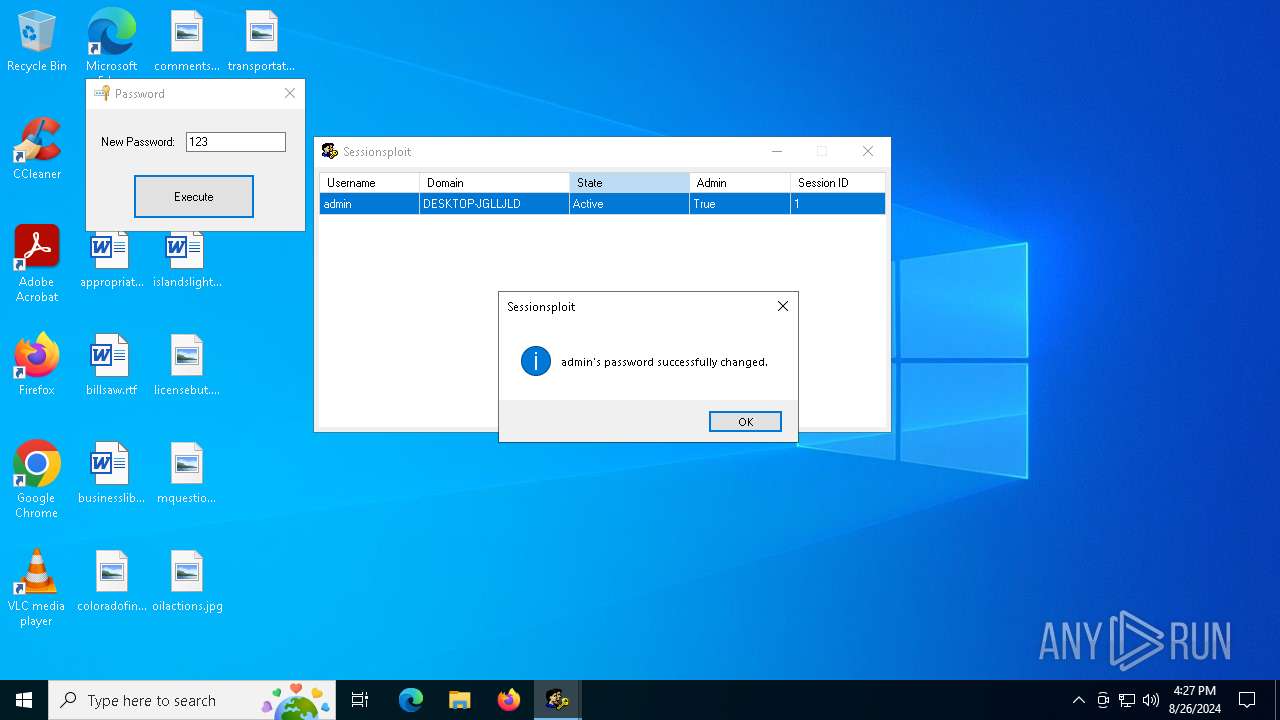
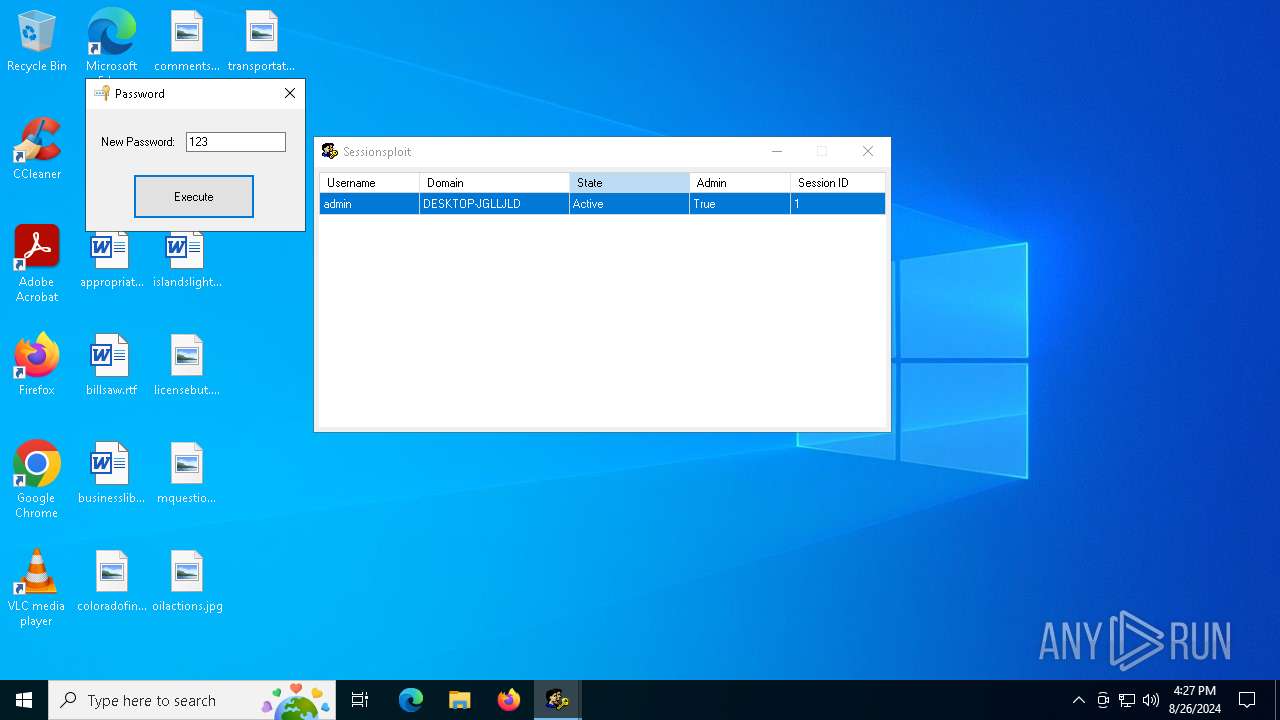
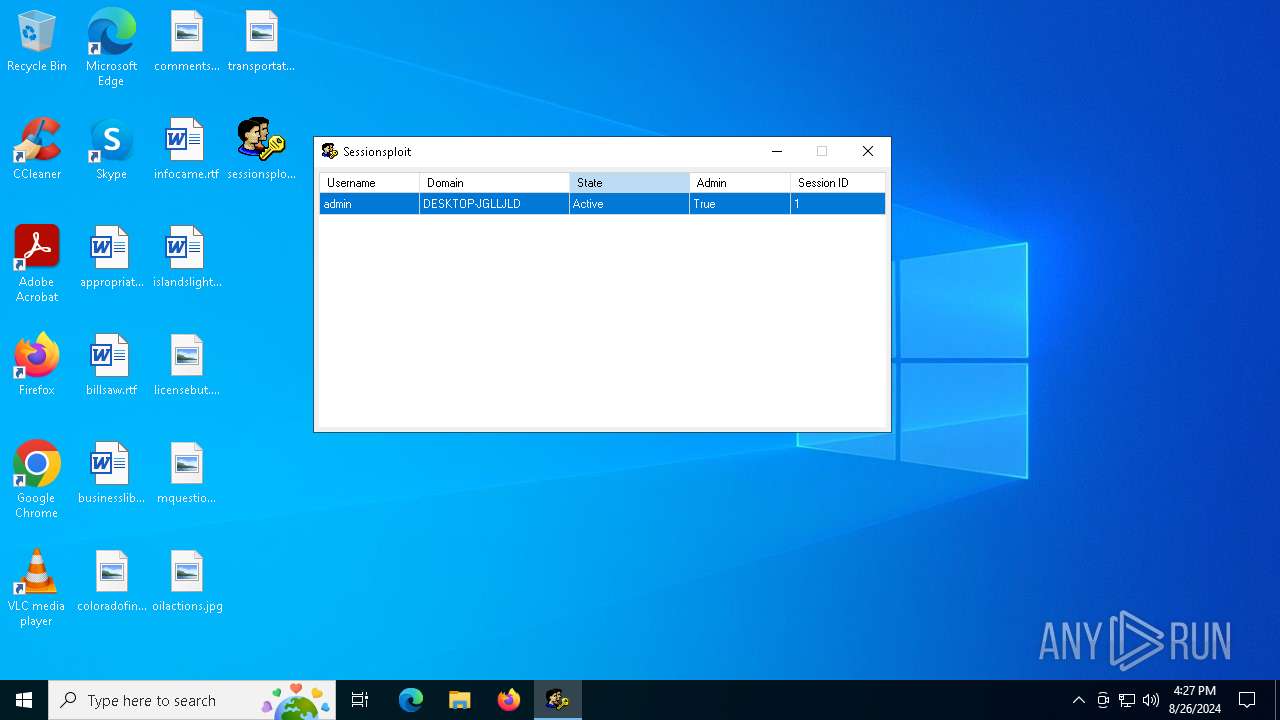
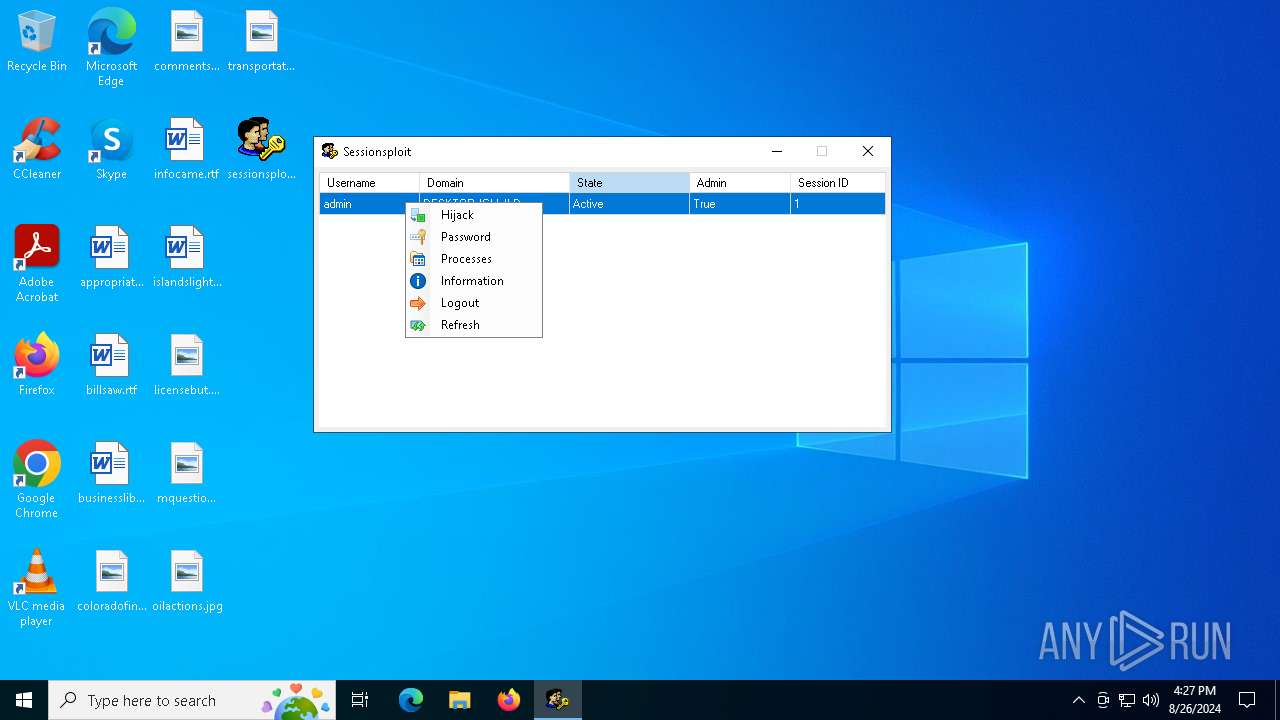
| download: | /MechEnjineerin4/sessionsploit-IS-TRASH/raw/main/sessionsploit.exe |
| Full analysis: | https://app.any.run/tasks/7ba5edbd-21a8-4f7e-9961-97154fbfaa3b |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 16:26:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | AB076C40C794F6FAE556EB095D14CFA8 |
| SHA1: | 4943F12B5549A40D069E97D00420B3D0AAB200BF |
| SHA256: | E04F83A60E6849F62E49E79AECD3644E5F7257A7E5E47C765CCA0C9B287B369C |
| SSDEEP: | 6144:SxIqVVVCVVVIVtVjVhhhhg8SZRmVVVhVVV:SxIqVVVCVVVIVtVjVhhhhkRmVVVhVVV |
MALICIOUS
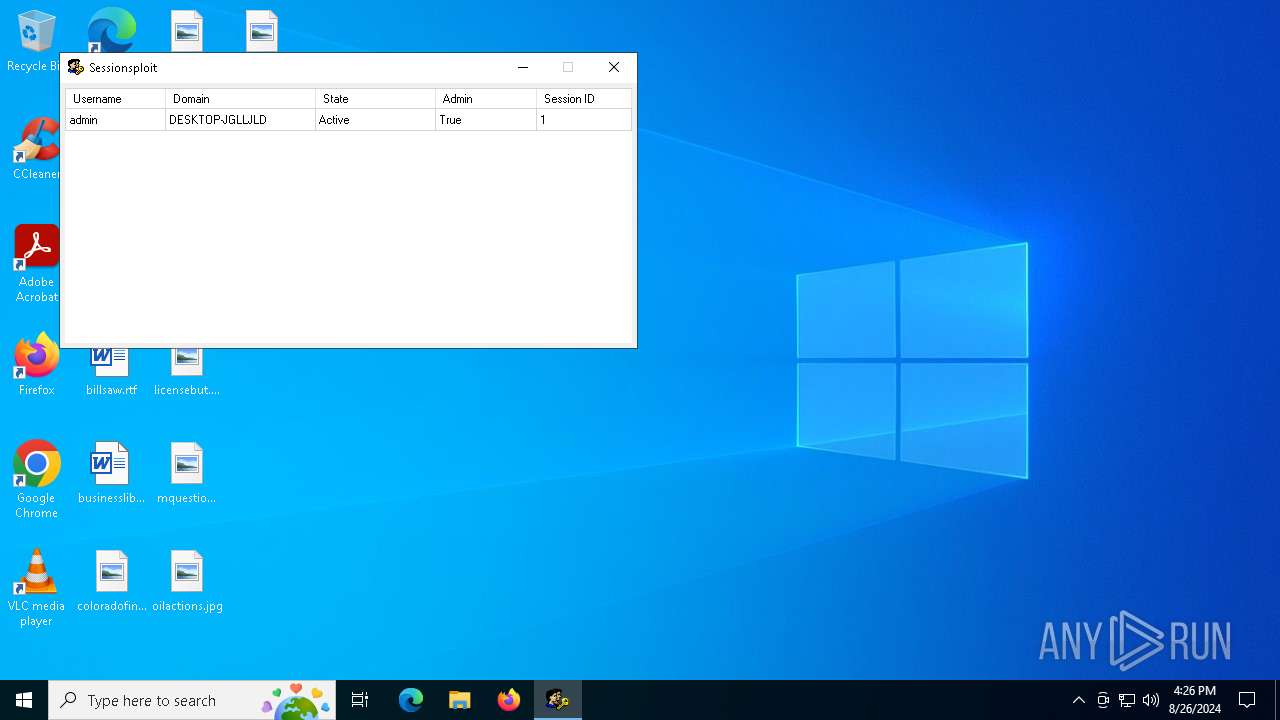
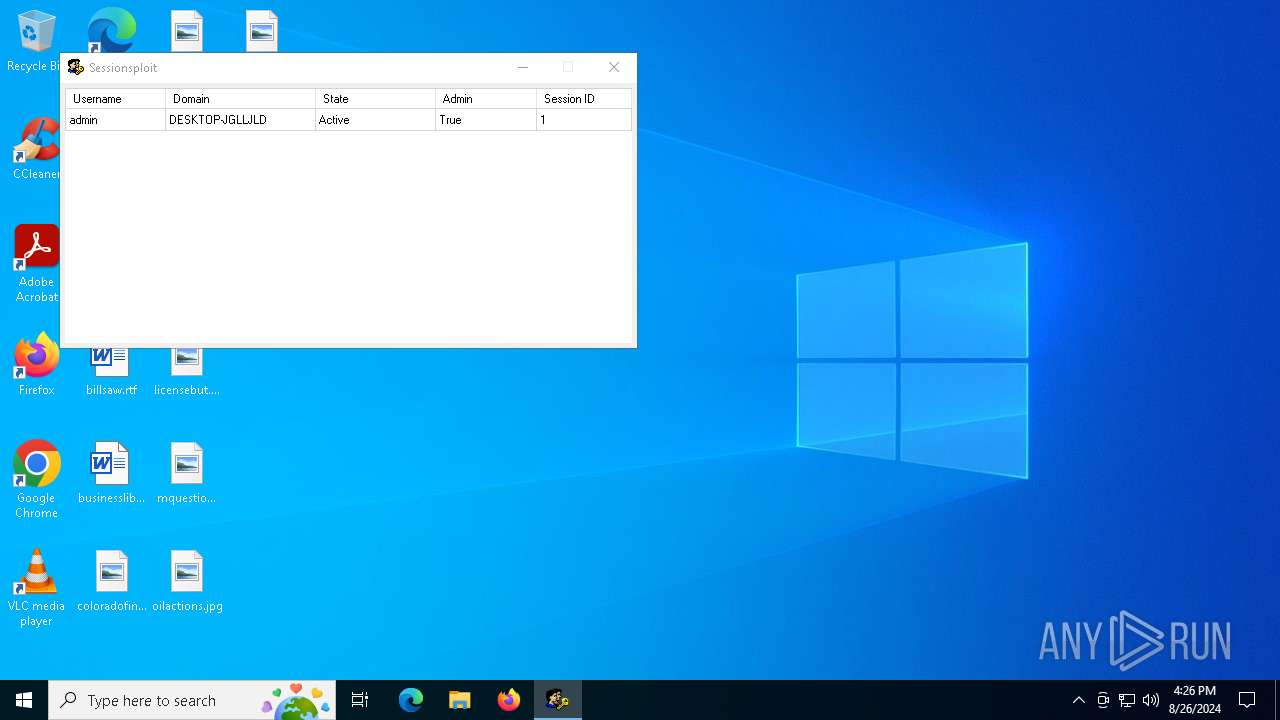
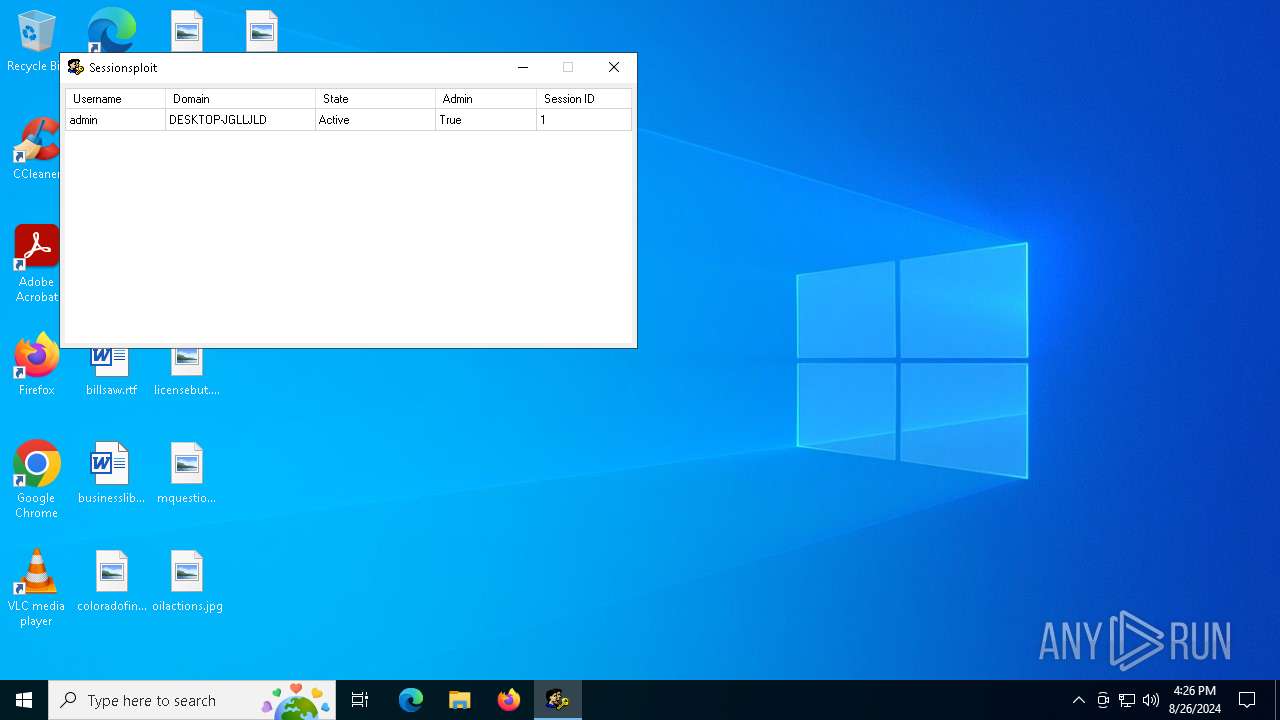
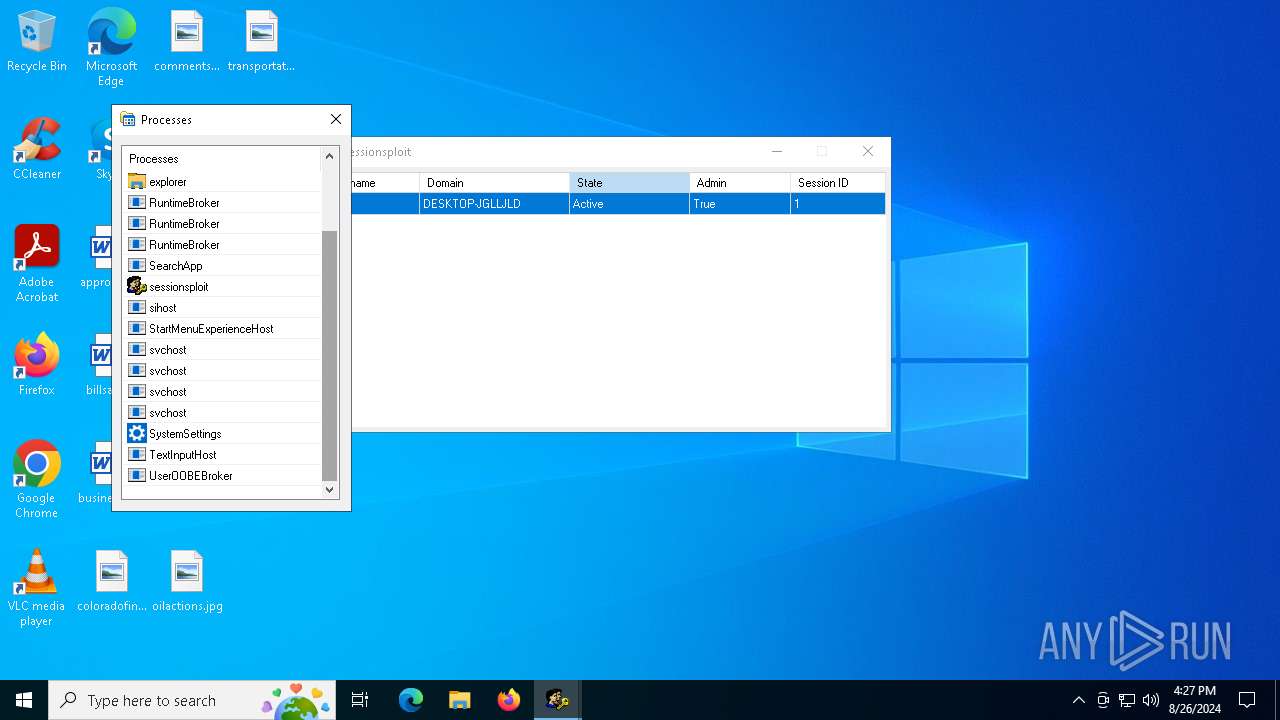
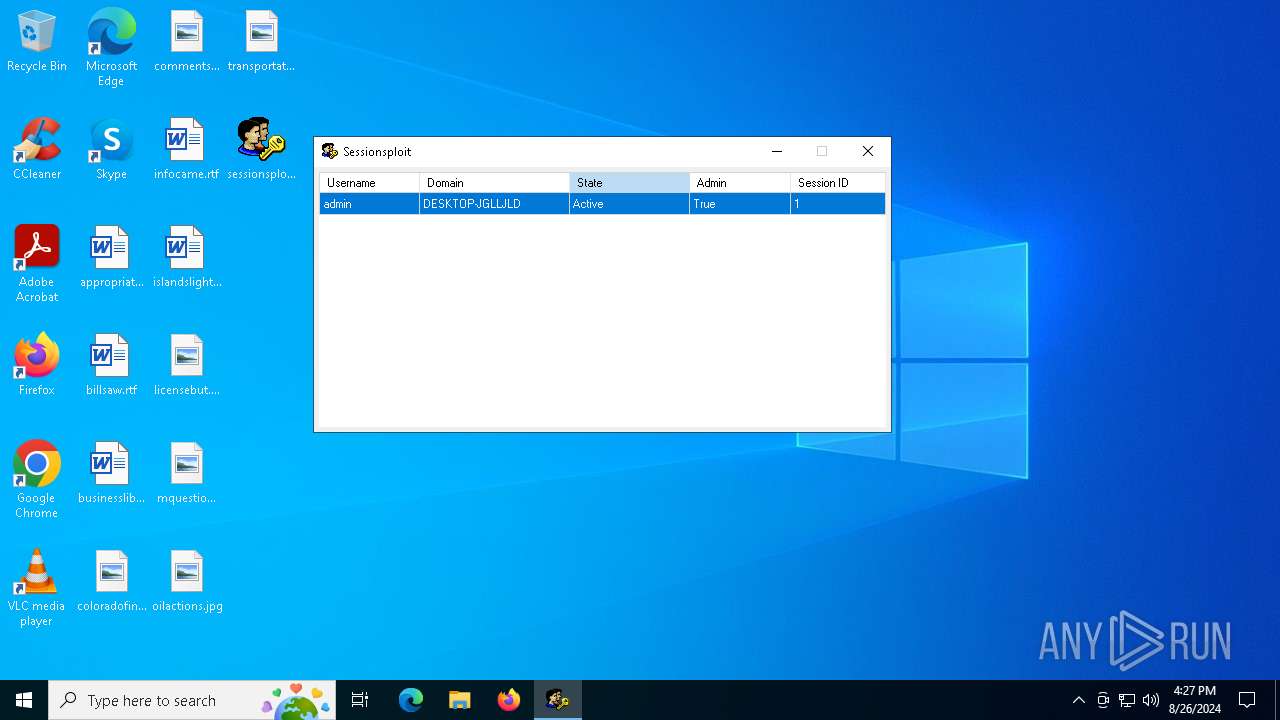
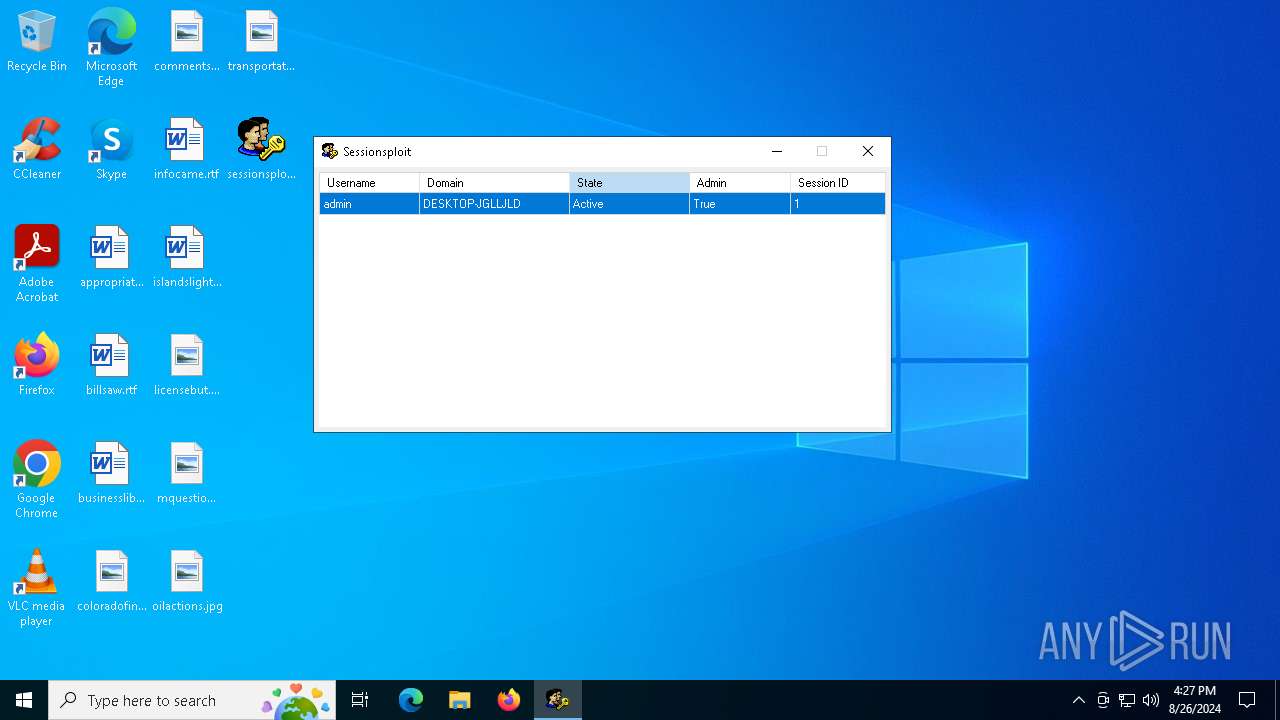
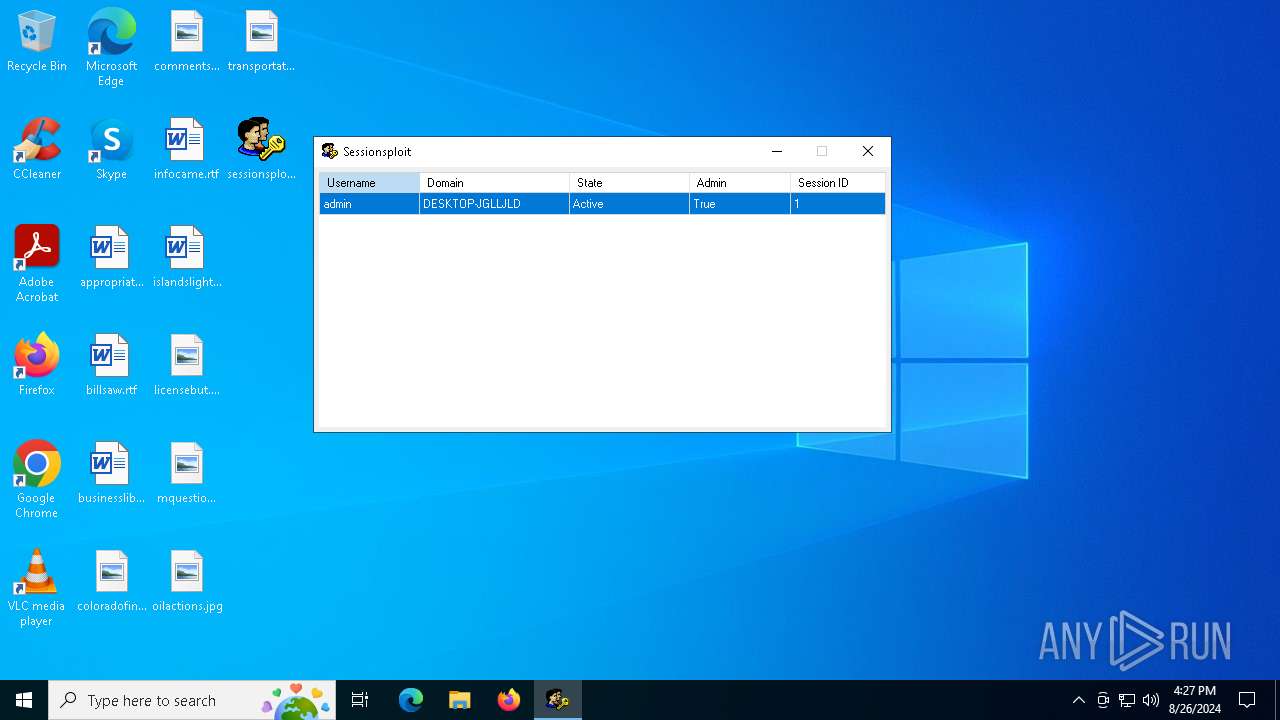
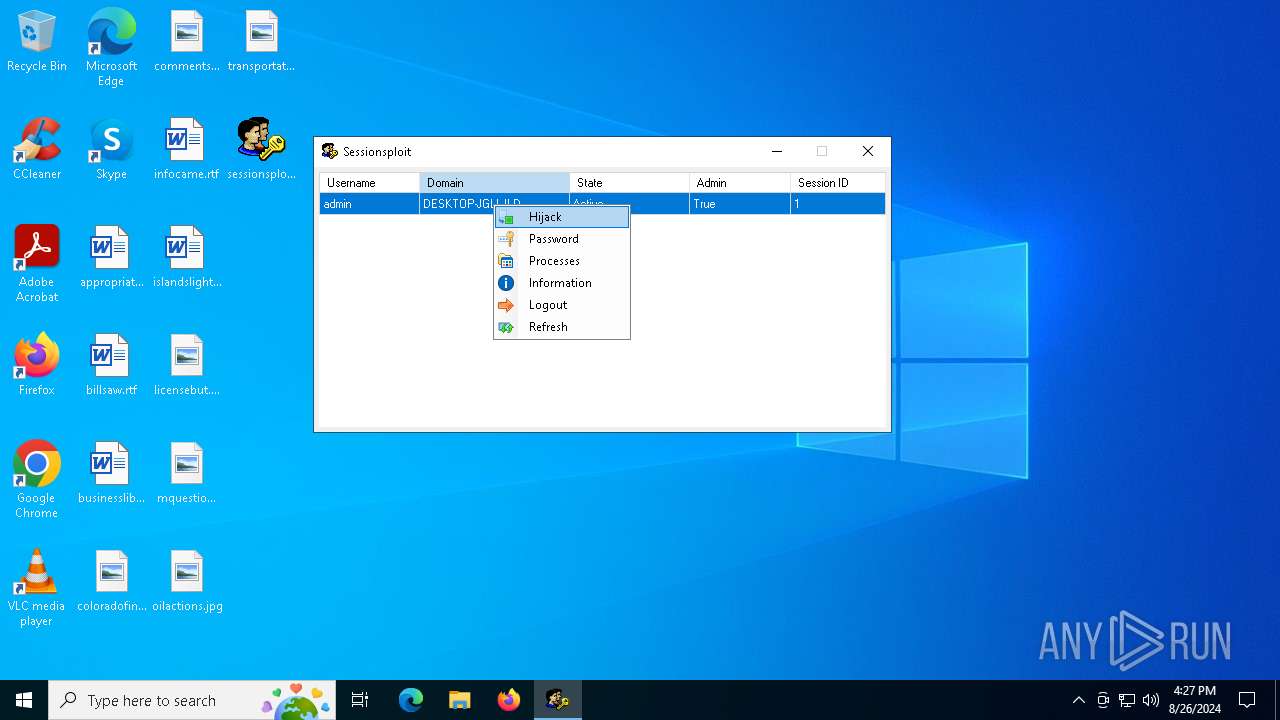
Starts NET.EXE to view/change users localgroup
- net.exe (PID: 6476)
- cmd.exe (PID: 6784)
- cmd.exe (PID: 4284)
- net.exe (PID: 6704)
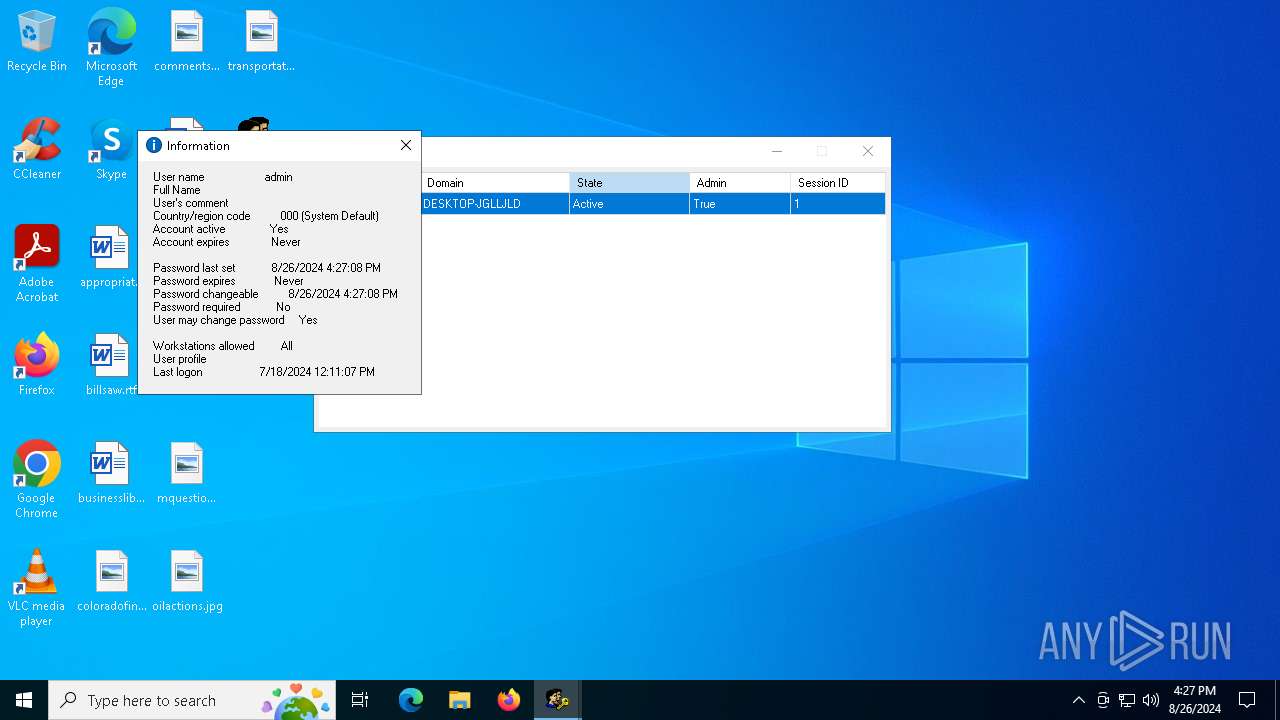
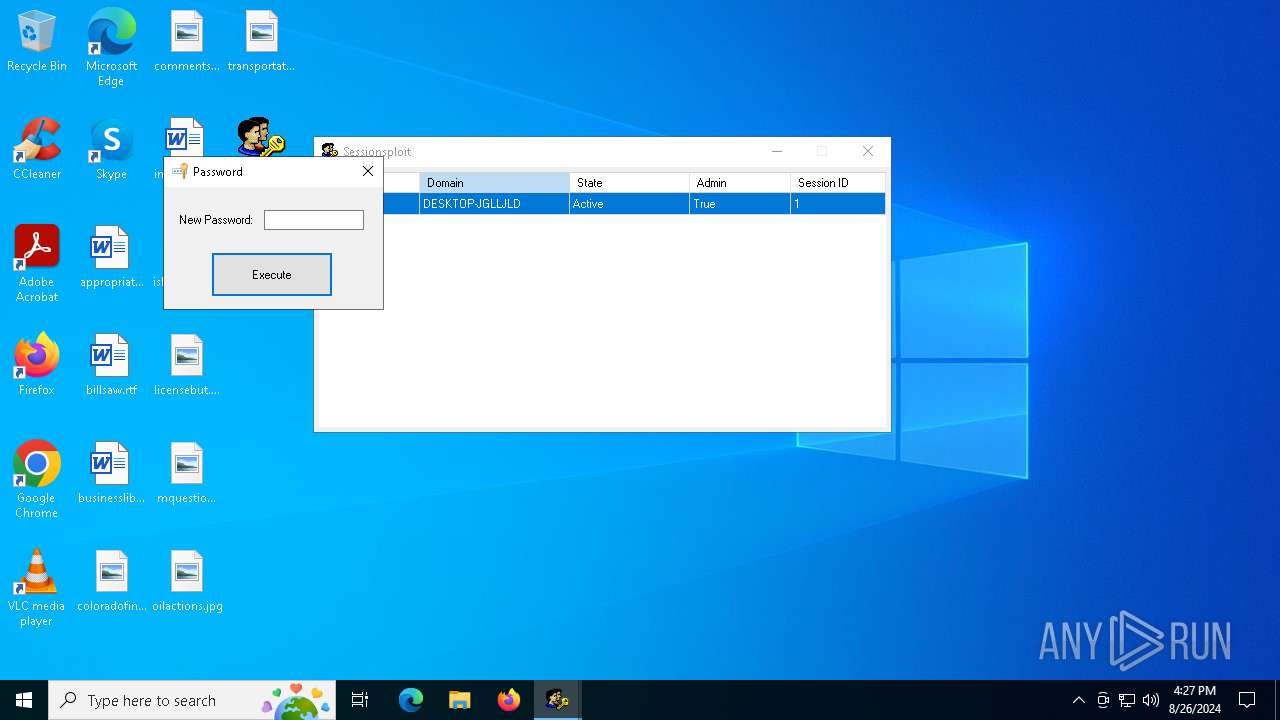
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 5264)
- net.exe (PID: 6840)
- cmd.exe (PID: 6964)
- net.exe (PID: 2820)
SUSPICIOUS
Application launched itself
- sessionsploit.exe (PID: 3964)
Drops the executable file immediately after the start
- sessionsploit.exe (PID: 3964)
- sessionsploit.exe (PID: 5124)
Reads security settings of Internet Explorer
- sessionsploit.exe (PID: 3964)
- sessionsploit.exe (PID: 5124)
- StartMenuExperienceHost.exe (PID: 5768)
Reads the date of Windows installation
- sessionsploit.exe (PID: 3964)
- StartMenuExperienceHost.exe (PID: 5768)
- SearchApp.exe (PID: 5340)
- SystemSettings.exe (PID: 4808)
Starts CMD.EXE for commands execution
- sessionsploit.exe (PID: 5124)
Executes application which crashes
- sessionsploit.exe (PID: 3964)
Get information on the list of running processes
- sessionsploit.exe (PID: 5124)
- cmd.exe (PID: 6600)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6600)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6600)
- cmd.exe (PID: 6964)
Starts a Microsoft application from unusual location
- tmpFC74.tmp (PID: 1448)
Executable content was dropped or overwritten
- sessionsploit.exe (PID: 5124)
Starts application with an unusual extension
- sessionsploit.exe (PID: 5124)
Process drops legitimate windows executable
- sessionsploit.exe (PID: 5124)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2960)
INFO
Reads the computer name
- sessionsploit.exe (PID: 3964)
- tmpFC74.tmp (PID: 1448)
- StartMenuExperienceHost.exe (PID: 5768)
- SearchApp.exe (PID: 5340)
- PLUGScheduler.exe (PID: 2960)
- SystemSettings.exe (PID: 4808)
- sessionsploit.exe (PID: 5124)
Checks supported languages
- sessionsploit.exe (PID: 3964)
- tmpFC74.tmp (PID: 1448)
- PLUGScheduler.exe (PID: 2960)
- StartMenuExperienceHost.exe (PID: 5768)
- SearchApp.exe (PID: 5340)
- SystemSettings.exe (PID: 4808)
- sessionsploit.exe (PID: 5124)
Process checks computer location settings
- sessionsploit.exe (PID: 3964)
- StartMenuExperienceHost.exe (PID: 5768)
- SearchApp.exe (PID: 5340)
Reads the machine GUID from the registry
- sessionsploit.exe (PID: 3964)
- sessionsploit.exe (PID: 5124)
- SearchApp.exe (PID: 5340)
Reads the software policy settings
- WerFault.exe (PID: 6800)
- SearchApp.exe (PID: 5340)
Creates files or folders in the user directory
- WerFault.exe (PID: 6800)
- dllhost.exe (PID: 5324)
Checks proxy server information
- WerFault.exe (PID: 6800)
- SearchApp.exe (PID: 5340)
Reads the time zone
- net1.exe (PID: 1920)
- net1.exe (PID: 7156)
Create files in a temporary directory
- sessionsploit.exe (PID: 5124)
Creates files in the program directory
- PLUGScheduler.exe (PID: 2960)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 5324)
- ApplicationFrameHost.exe (PID: 5548)
Process checks Internet Explorer phishing filters
- SearchApp.exe (PID: 5340)
Reads Environment values
- SearchApp.exe (PID: 5340)
Reads Microsoft Office registry keys
- SystemSettings.exe (PID: 4808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2096:03:24 14:53:09+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 201216 |
| InitializedDataSize: | 11776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | User Management Software |
| CompanyName: | Ebola Man |
| FileDescription: | Sessionsploit |
| FileVersion: | 1.0.0.0 |
| InternalName: | sessionsploit.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | Ebola Man |
| OriginalFileName: | sessionsploit.exe |
| ProductName: | Sessionsploit |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
206
Monitored processes
42
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | findstr /v "Home directory" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1404 | findstr /v "Logon script" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1440 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | "C:\Users\admin\AppData\Local\Temp\tmpFC74.tmp" 1 | C:\Users\admin\AppData\Local\Temp\tmpFC74.tmp | — | sessionsploit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Session Logoff Utility Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1828 | C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding | C:\Windows\System32\oobe\UserOOBEBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: User OOBE Broker Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1920 | C:\WINDOWS\system32\net1 user admin 123 | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | findstr /v "The command completed successfully" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2628 | powershell.exe "Get-Process -IncludeUserName | Select Processname,UserName" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2820 | net user admin | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 391
Read events
42 246
Write events
143
Delete events
2
Modification events
| (PID) Process: | (3964) sessionsploit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000044F8271D1F3A104485AC14651078412D11050000 | |||
| (PID) Process: | (3964) sessionsploit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3964) sessionsploit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3964) sessionsploit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3964) sessionsploit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6800) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Property |
| Operation: | write | Name: | 00180010F429971D |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB0100000042CB6C300049C042863C8A748EF9A2B200000000020000000000106600000001000020000000E6A90C0206E5E48DA3F8401E1F6773D94F5E2F41F83F72B0B7F4C40F50D2CA44000000000E8000000002000020000000A273A80162E9099B7CD43CC79DC02287C96F86282B34149293766E5F4A9E5245800000000EA07047374FE5F85A73EACC01B03A2C8B521AE7168113D41A706113D9453DB83B0E3E7AF1AD51756BD45E997B8089C03B421000E2B34906915D02A155D3DC8723ED15062280670FE7347C8D75B702446CB6E61AC81FEC730CCC11A6C5E8CE4BCCACF3489A764B2E82AC200C03E6135542864B8E9A99236F0B4A02B54A2FB7104000000007D599FD02763FCBBCF18CE152FF29913235DDE1B0597199E00B812506E8C6F8D451696ED4FA4CB5AF6F1FB0C4DC2658A3EF321FCEFD2B928AF1F1C27C0280A4 | |||
| (PID) Process: | (6800) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | DeviceTicket |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB0100000042CB6C300049C042863C8A748EF9A2B200000000020000000000106600000001000020000000C5498089C5EB121EBD7A7E5B9F00D9C82904A582EF66B1BFE67B5580E5674181000000000E80000000020000200000008234B8FC266BA6876D09F1A6D07BED408BB22B53CD14F91FD1C052147D7512FD200800009DF4E809D5F10F0A9D581E4EB47776458845F35F85892DB8FA67A6539C3C541FE20E74C9E8FA6C7E56E7909A7D1F1E2C70D6787BE76908F510CCB2411DF0B8E4B71E54928BB80E68DF35DB392E3D1C8A59C3E6CDE000C6BD2184133C6BC1E7E19A15C13D817584DBC36EE07DE73D139F68FDF8FE642A0885330B331E01D00FD1BE930664618D671CBB08D8F4CCA912738D524E26DE0A2CA06B1B9E3540A5FF9E63BD7F062226938433D191F3BFD80CAF0D728C2D53D237C48B35561AA5F38C0BB2F5168E39B020AEF25CE9A798D6EA4D89461460879954425A6410207E2889F1F15A93BD373EB5BDD18B17C39CBA123188EADE7D3DE587FDE499893D50DE6D193B2E56414918C868533E9F80F4260554CD0D2648409A317A42FFEF21AA64FDA1F9C36E2544C810DE50AA4D69B38733633C939799A7168115056C820E89576509AD18C7FADD3578F88A6A00644CA58A90A3AEAC298831461CBB6AD80895030B8BACB8BE4971B9C1381497628AD38BFFD92452D52188A3D56C3B1298ACD617313B59057CE112653BF11EF1690DE25A5D8F9B59B886B706A5BF914E0B07649A4F618851F299951F42E980D78546B2AF9644DA4C027AD86EC519836DA348BA502421C76B1AFF11D13E126D998715C1A823D823319448CBD78754E31B834AF675AEE81F0D683EECC615EA97B773B078AAA0C4B14C327FDCAC082CA28C4E824560403ED33A65B240CC9C31860A6513070D77C89F1B6FB4A92D9056989358E928E87DBF63458ACE7A3F98316452F4CD6F557436935F80676FCA0558C26C89FF64201F0422D9B6995E627E631B22D79213EDCEE2C03A22186B2E47D2F655B9EAD196027A2C0B746AA29110BA46D06F9F101662D6399D2A92C75F0A4DD95C512B19F40DE3AB63C9641494F6BD59186F489009A34E51F7A1AF2FCCF754B6C8F31DDC307523DE1A2E60EA42F8F3EC42D1C795EDD405B482BB39D99EE2E7A2EBA3348F5CD0FCC24B747F874E141B7E93326CE26A3E99E9011C1900ED000D82743FC5B9B5AA82C6B751604FC50363B8B4C96246922FCC43813E9A4A1F105DD573C94E8BF86AF2EA981A8B98BF7C62978A86587EFD5A050F480CC9DA53A9A1C7C5222B16D424B0CF5AB90676FD451780548B2F6D13D9425ABD8FF9C02D964AA4B6A7650034EAB9BC827E50F73113C0C8A0131FF8397AD4BB308350DCB923BB71A3F17E28CD8DE01F05615858461151ABD6402672EFD3EBCC42C9534A96C999D9F37092D81FC14488A4C21499076DF6975DE28DB3DDAE32F8E8DD8F3EA110D35433E19BA123D7A3533704AEE52EB35543AA80E5D52CCBF0A46DB762EB2CC12B70BE2277E27875E4CF4F9368901F8AB0F1B454ADC26D162AD7FA5222D94CC90290C1C46E874F3ED34DD75191003C741EA6C520F15648A8D144F21C80DFC703D394F7BC9DCC367BB77F3C89596C22A78F0E0533C1370F60E5ABBE7E8D100EEC649AD6C56E8D4F46667997625349466E0B8FA0C0ABF2233AB4E786CAD92A76B0F15FEFBED574816DBB1BD05BBFD93FB7C0FD02B1C1B7B8BEFE91E158BEF5AB3127E2FFC77224789F8196B732A6BE6C1B357A9D40F731622E86E0595FA1A9917CA20D792261364EEE9A323D2CDF3881EA7F5CCCF7AD4819C1A7C51EF0C9FF2CFEC95D29F620928AEC93EF29F0FA7273F691A9A906C9DAD695D916CDE5493D6347B99BC4779BCF21D7D3991DA0F176C989CDE04CBDFF2802900E978BBA534E23E80C43E7F21E31100E256884CF8971FADAB7F2FEDA70135F56C44744BC2249B30F8F28D6824A4BF26EE346FEE0D4D3C2468C0B65A547F437B3555EADF47A6599DCC2454B35A6497252CEEF8CE0EE6A02C56AA3A617348CF15946B2BACC0644722DA1DF11E82FC42E845DB93DCBBA1E017FE59970F91D95CF074595D2286775498E587892B8B7EAC1281B76D5253BE335FCD8289A8F4E7203E2AE6D160D1FBD0551AF7D95D966AB07F495D28E98F9F6C55BC5DE9AD2FA79AF3D2B5C1917EEEF22DC1FE0D5576F5D4C1370211D2FD5515E132270CBC28EAFB321BF5013A01102984706AC5EDA23D7EB4A0B9912C86ED793621728C4EC7A445A39AF4C7D45666F5F059E91835CA61219C8D06F51F4ED3612691A1EB7D146491D01F6033A89E9B3404F3E7746C630C6334FA86EC4F9CDADE69C84E4FCC0E732651BF9648C9E543616F8F80DF0E14ACD3A3152B4A5A602AE1D67A45D4A4564D0F3874728FCE763247A35B100345AA738ABB348650CD5C1E82215D220A5686AAAB5F300C93CAB4B4DB4BC2D4A32BA6ACD082ED1365C7241FDD9FF5C64A6B9F909F182AB8460D771AFA4643084EB2AED4368DF3B38896662F627C0D5D5B53E4F93D4C6E07E4FB952A91494057D2A24A07CCE86B417B81D61852D7CD3C3907720310F6ED26A6DB3A3BFD558758FB71C4620BFB1DAB1C3A42AF157FE0A04FD59AF2AD3B7E508DAE96C54075467408B592288ACFA10254BBF1852B052AEC66A96F60125E608600AF8DB220060A4CC7A399867B5BC517CC339A78C26BCAB7A6FD2D6B102544B78153EE04104A25F0042A2B5CC298DFA61DD3F72C47CD03CDD8A58C445AD66D10C4B4D57B90E154E4EAE11354C66D0E76832A00C2284C6AB14BB5882BF0CE97C93D07B138FFACE176713178B191613C7AEA03DB947F354E065F673A874229C4518EFD40636797846094E177A4F705EBCD3AD9BE8F91D1CA6BD55EDCEA24461DDA1D9C427612126D524E153C66EFA36749F589E300BA35CBF2BBA90AD273E6A676593AA04DABCE8EBE701B7ADD9FA613D28E290AA393AA9C9EF63CA6C1EA7D3215907E6572382B318A686870E3C04648FE0B8B40A7CC579C46E1777A7BBD763F95D1123C8634D94108EE5FBA85D8CD311B70784FF8DCC8E5BD7DBC71A666F54882ED9AA10E5AE624E41682DB50CC1C1D6400000009E43558DB8A506E6CEF9BFC82D3961617B1388A82D86A8DB2ECBE55DBA54BE643C4613A447707332044CBA6F0ED721BDFD1EEAE3E1D09E484C619DD99DB9ADAD | |||
| (PID) Process: | (6800) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | DeviceId |
Value: 00180010F429971D | |||
| (PID) Process: | (6800) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | ApplicationFlags |
Value: 1 | |||
| (PID) Process: | (5752) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SideBySide |
| Operation: | write | Name: | LastScavengingStarvationReport |
Value: 22E34DEBD4F7DA01 | |||
Executable files
3
Suspicious files
62
Text files
213
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_sessionsploit.ex_372d7b8a6e837be8f21ba5725b69532833af142_956c1ec5_8a4e61e8-0a5a-45bf-a760-970d3e6c13a2\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6800 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\sessionsploit.exe.3964.dmp | — | |
MD5:— | SHA256:— | |||
| 6800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERAE1C.tmp.xml | xml | |
MD5:E92CFBAFCA3DE3D95082328F7D26E1D7 | SHA256:0A595B24A82AF08D1A868C509E9F9F418CE8166429F1C2537BD27154E3B6EB46 | |||
| 6800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERABD8.tmp.dmp | dmp | |
MD5:767D1608BC52660220071F28EBB65A0B | SHA256:69CAFA645F9D4BA839987C91C3D2E34CBB464FB530D5183FD82BDB1100D8CA46 | |||
| 6800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERADFC.tmp.WERInternalMetadata.xml | xml | |
MD5:7497552B6AD6865BC2C24E28B310B46A | SHA256:089B7C21B1B6738C86589338E8D0C15997A36FEA77B87CB7D05E6EC8DBD7A651 | |||
| 2628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qz1onbbd.mth.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2960 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.024.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 5124 | sessionsploit.exe | C:\Users\admin\AppData\Local\Temp\tmpFC74.tmp | executable | |
MD5:DDB4F5DC12EC364DD325A2C63AB5F0DE | SHA256:4B5DF4CE25BCD9CF635CDED7333F5F53D23F57B2ADACA1DDF987C4B717F7FFB4 | |||
| 2628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rjvvx23v.eop.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2960 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | etl | |
MD5:079890A8EC8D5CB6523FCEC2209780AA | SHA256:0E12D2D76DD738CE196BED522E35F75E2CC91294F78CDDCBE8CE7787AAA70049 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
38
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2576 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2576 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2892 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5340 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4276 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6800 | WerFault.exe | 52.182.143.212:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |