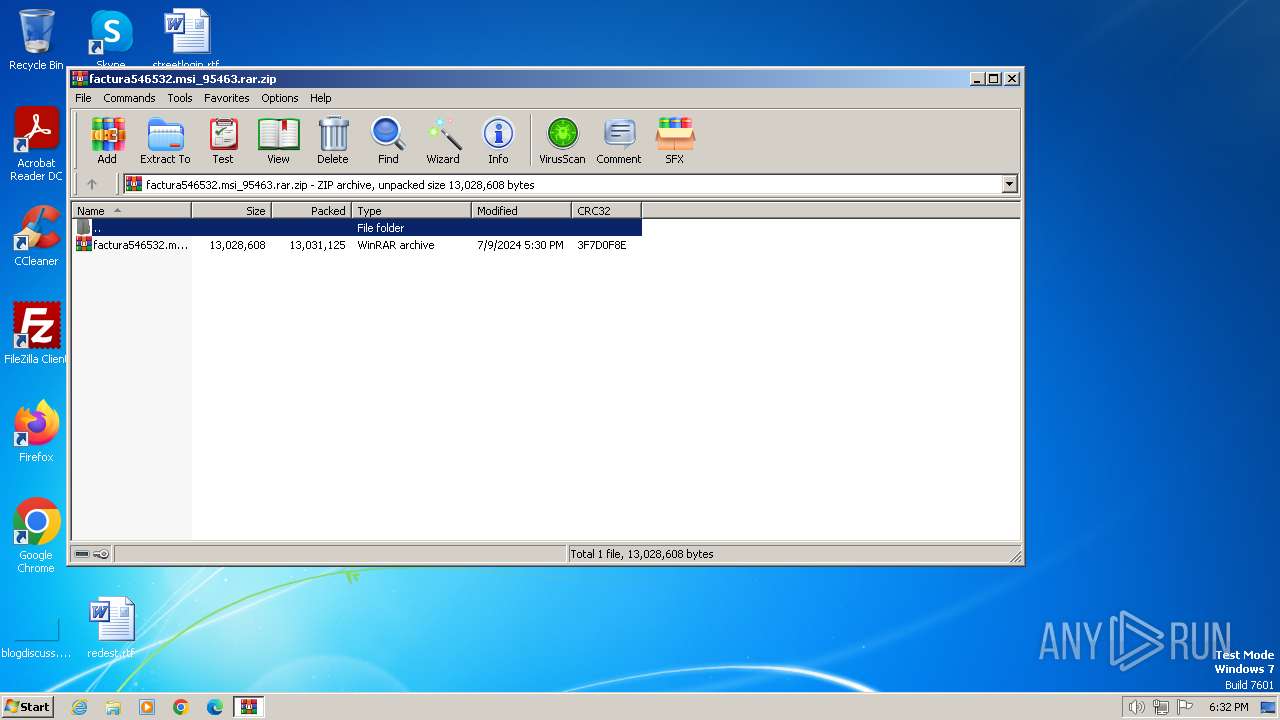
| File name: | factura546532.msi_95463.rar.zip |
| Full analysis: | https://app.any.run/tasks/8c2e589c-dac0-494c-96bd-f9e7dfdd490b |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2024, 17:32:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
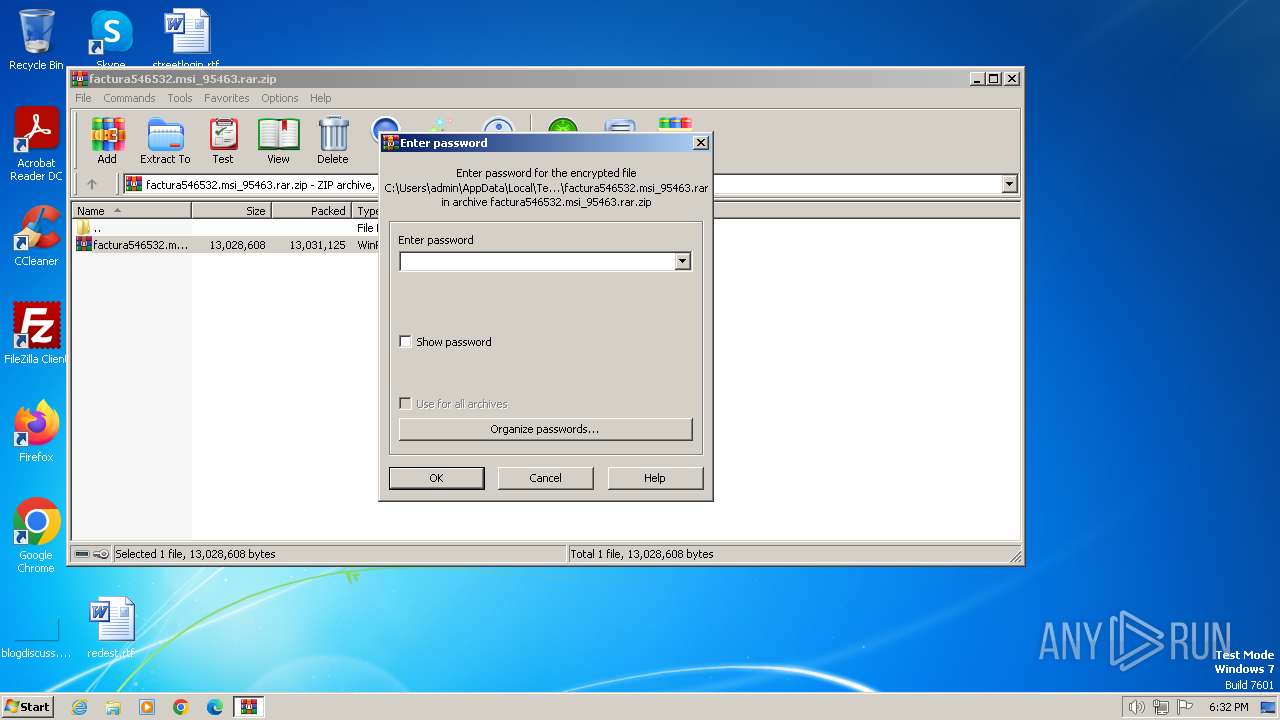
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 5F5B21F79EE6D11EAB1CFD3A0856D42D |
| SHA1: | 99431CA4FD05F6610753C381DD1872CAA8DA93A2 |
| SHA256: | E04D3E04DB783920DBBAF35772988EF0A156DE99DE6C98C2727BE4F6530B35F5 |
| SSDEEP: | 98304:kUeW1CirkLyrMtfq5eZ1y2aYlma/BBiBzbhNacUhEXaP46rWw4GLhT5kEPMEjUlm:iY33yH2gaLmZYTkxPBQavF/7oi |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3344)
- msiexec.exe (PID: 2748)
MEKOTIO has been detected (SURICATA)
- msiexec.exe (PID: 3144)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3344)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3532)
- WinRAR.exe (PID: 3344)
- msiexec.exe (PID: 3144)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2748)
Reads the Internet Settings
- msiexec.exe (PID: 3144)
Connects to unusual port
- msiexec.exe (PID: 3144)
Checks Windows Trust Settings
- msiexec.exe (PID: 3144)
Checks for external IP
- msiexec.exe (PID: 3144)
INFO
Reads the machine GUID from the registry
- msiexec.exe (PID: 2748)
- msiexec.exe (PID: 3144)
Reads the computer name
- msiexec.exe (PID: 3144)
- msiexec.exe (PID: 2748)
Checks supported languages
- msiexec.exe (PID: 3144)
- msiexec.exe (PID: 2748)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2748)
Application launched itself
- msiexec.exe (PID: 2748)
Checks proxy server information
- msiexec.exe (PID: 3144)
Reads the software policy settings
- msiexec.exe (PID: 3144)
Create files in a temporary directory
- msiexec.exe (PID: 2748)
- msiexec.exe (PID: 3144)
Reads Environment values
- msiexec.exe (PID: 3144)
Creates files or folders in the user directory
- msiexec.exe (PID: 3144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:07:09 17:30:02 |
| ZipCRC: | 0x3f7d0f8e |
| ZipCompressedSize: | 13031125 |
| ZipUncompressedSize: | 13028608 |
| ZipFileName: | factura546532.msi_95463.rar |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2748 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3144 | C:\Windows\system32\MsiExec.exe -Embedding D9D934A12412154E29A733DEA0A70585 | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
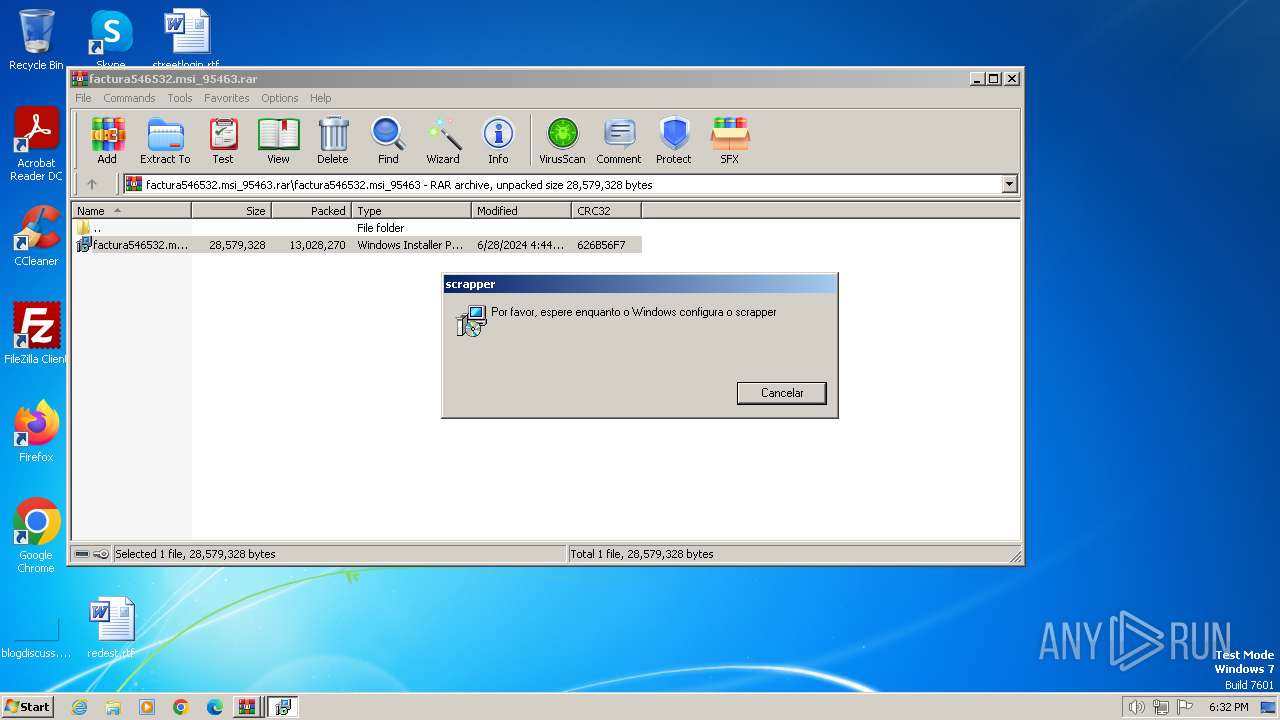
| 3208 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.18717\factura546532.msi_95463\factura546532.msi_factura546532.msi_95463.msi" | C:\Windows\System32\msiexec.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3344 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\factura546532.msi_95463.rar.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3532 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb3344.17704\factura546532.msi_95463.rar | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
14 404
Read events
14 284
Write events
108
Delete events
12
Modification events
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\factura546532.msi_95463.rar.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
11
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3344 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3344.17704\factura546532.msi_95463.rar | — | |
MD5:— | SHA256:— | |||
| 3532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3532.18717\factura546532.msi_95463\factura546532.msi_factura546532.msi_95463.msi | — | |
MD5:— | SHA256:— | |||
| 2748 | msiexec.exe | C:\Windows\Installer\52f54.msi | — | |
MD5:— | SHA256:— | |||
| 2748 | msiexec.exe | C:\Windows\Installer\MSI38FD.tmp | — | |
MD5:— | SHA256:— | |||
| 2748 | msiexec.exe | C:\Config.Msi\52f57.rbs | — | |
MD5:— | SHA256:— | |||
| 2748 | msiexec.exe | C:\ProgramData\ssleay32.dll | executable | |
MD5:931C97553B3319F21B9EF249AA3CD244 | SHA256:7E643C188A1EE3B0251B7DFCAB000B7C48FD840EFF35189E8A45901852E3910A | |||
| 2748 | msiexec.exe | C:\Windows\Installer\MSI3272.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 2748 | msiexec.exe | C:\Windows\Installer\MSI31F4.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 2748 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF60BD90F01016EA86.TMP | binary | |
MD5:4BC3AD9924CBD062994F8BE1E57806F9 | SHA256:192DDFB8CB5041E1F9496BC8B497FF7A789F1554E42E28049EEE57C6EE876A25 | |||
| 2748 | msiexec.exe | C:\ProgramData\libeay32.dll | executable | |
MD5:C2703965B8BA0ECF8C5D8A043976FACC | SHA256:E28E34FBDAFF077669586DCDB4E10F0BA2CA6C9973ED4D372A5C3EC3B8AD20E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
14
DNS requests
8
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | unknown |
3144 | msiexec.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3144 | msiexec.exe | GET | 200 | 184.24.77.57:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgN4GMmBeA8jMFX7CildM4dFVg%3D%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3144 | msiexec.exe | 34.117.186.192:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
3144 | msiexec.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
3144 | msiexec.exe | 184.24.77.57:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ipinfo.io |
| shared |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3144 | msiexec.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3144 | msiexec.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
1060 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
3144 | msiexec.exe | A Network Trojan was detected | BANKER [ANY.RUN] Mekotio Server Response |
3144 | msiexec.exe | A Network Trojan was detected | BANKER [ANY.RUN] Mekotio |
Process | Message |
|---|---|
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |