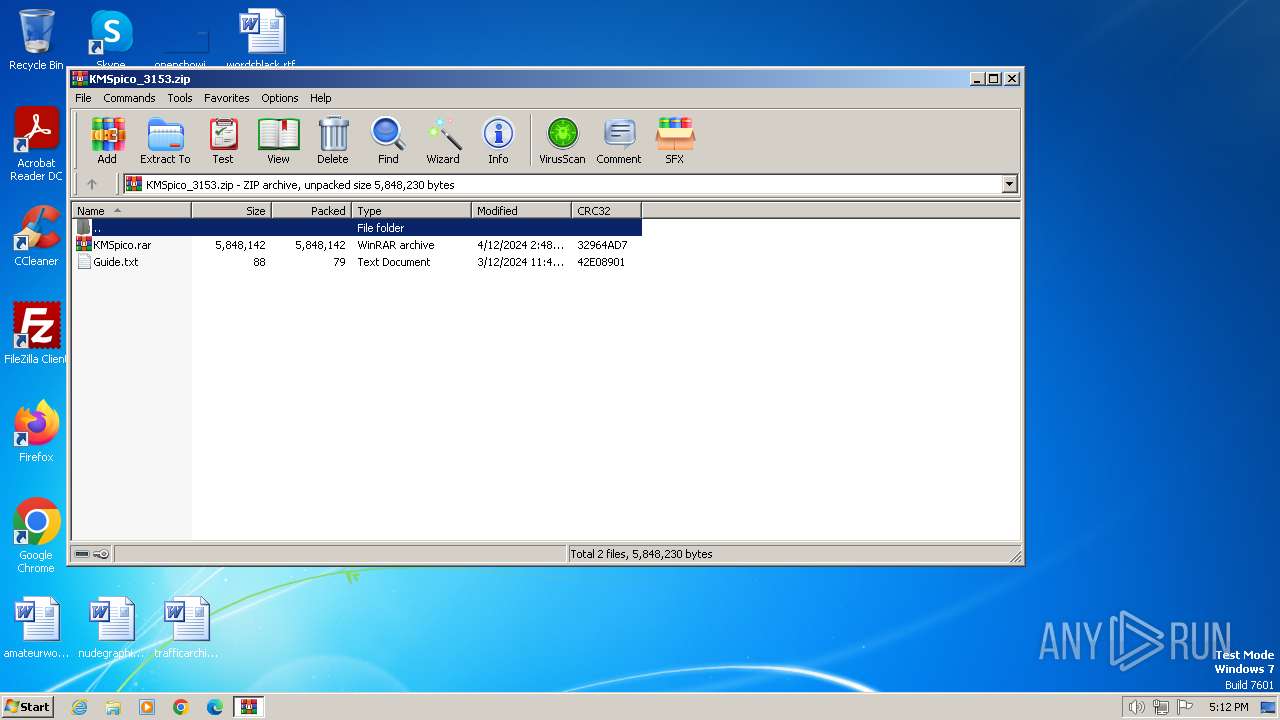
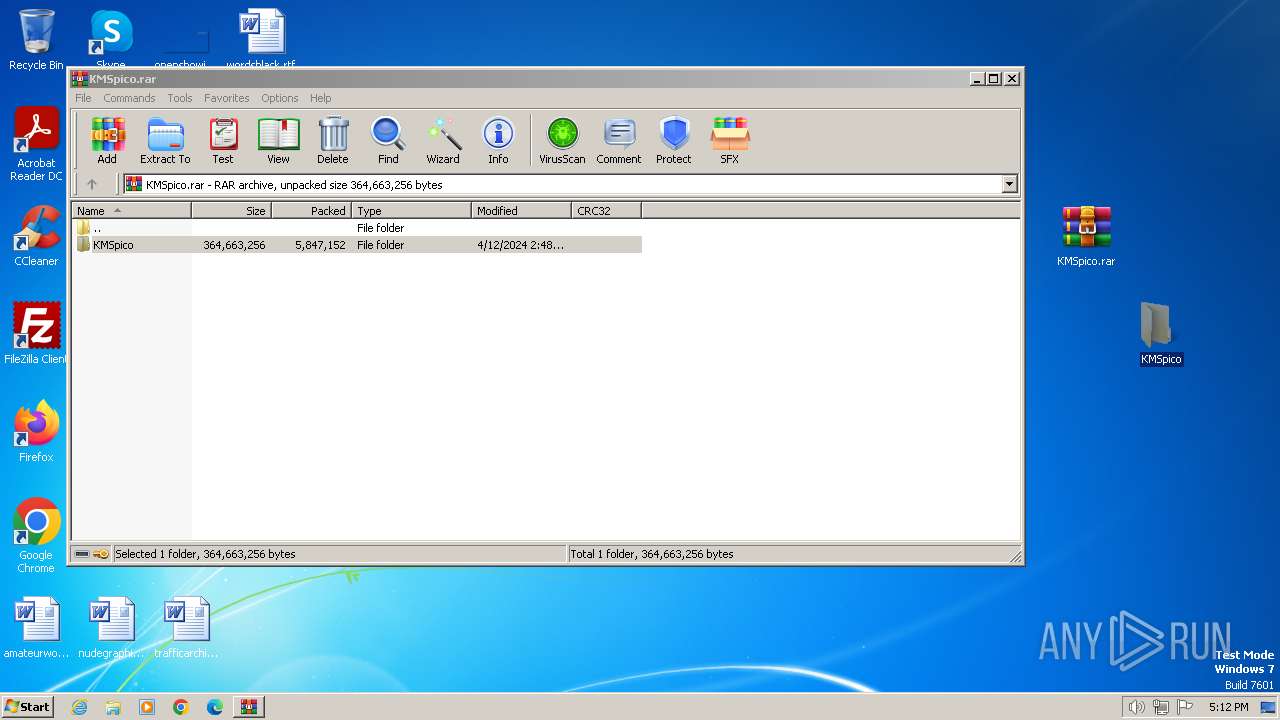
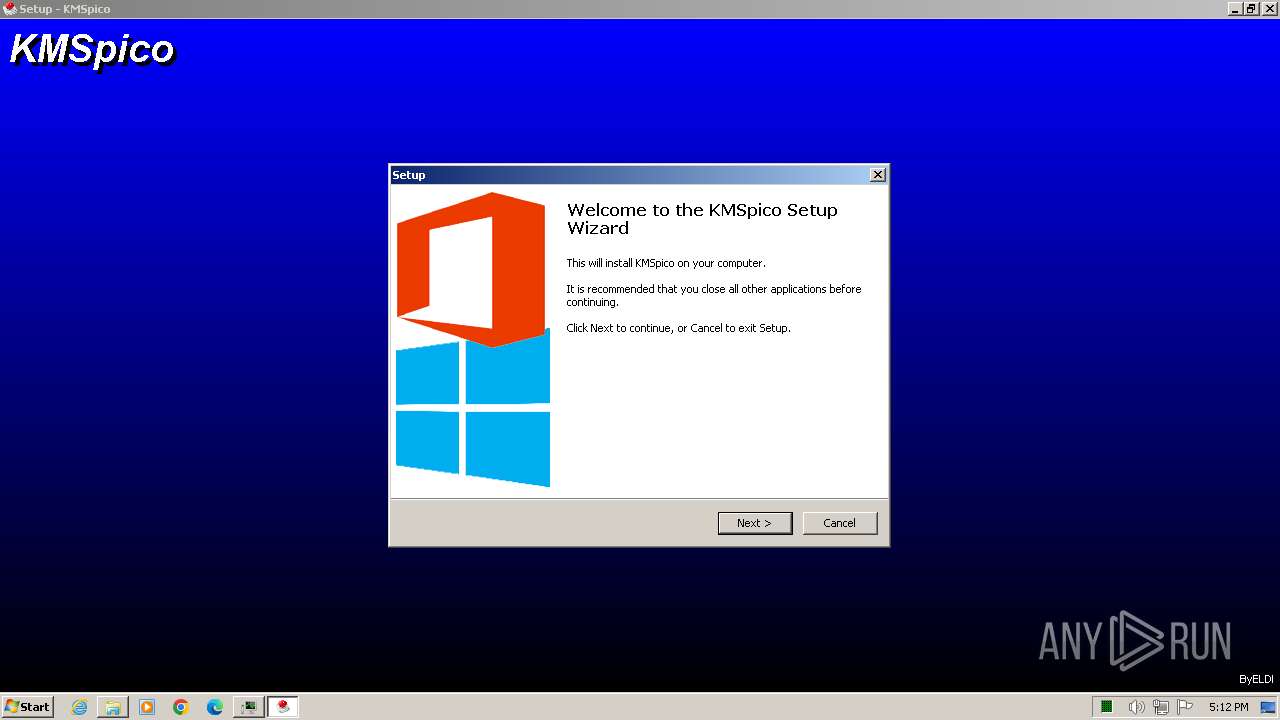
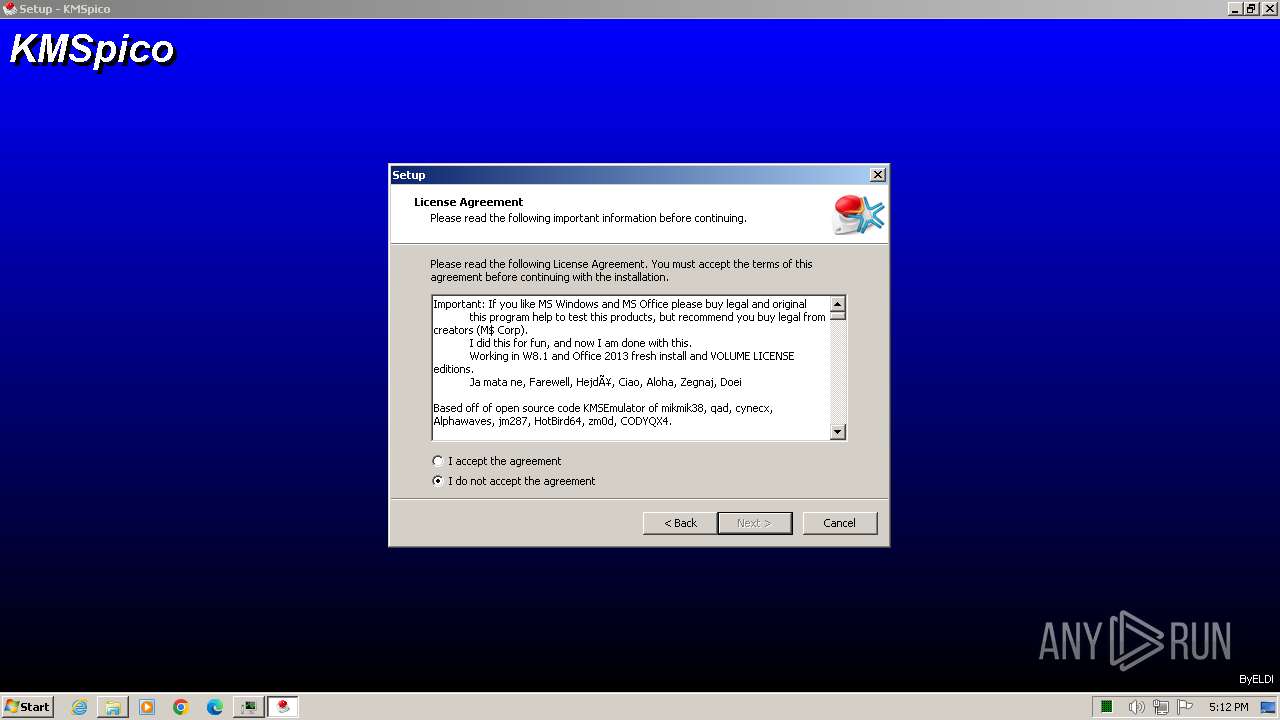
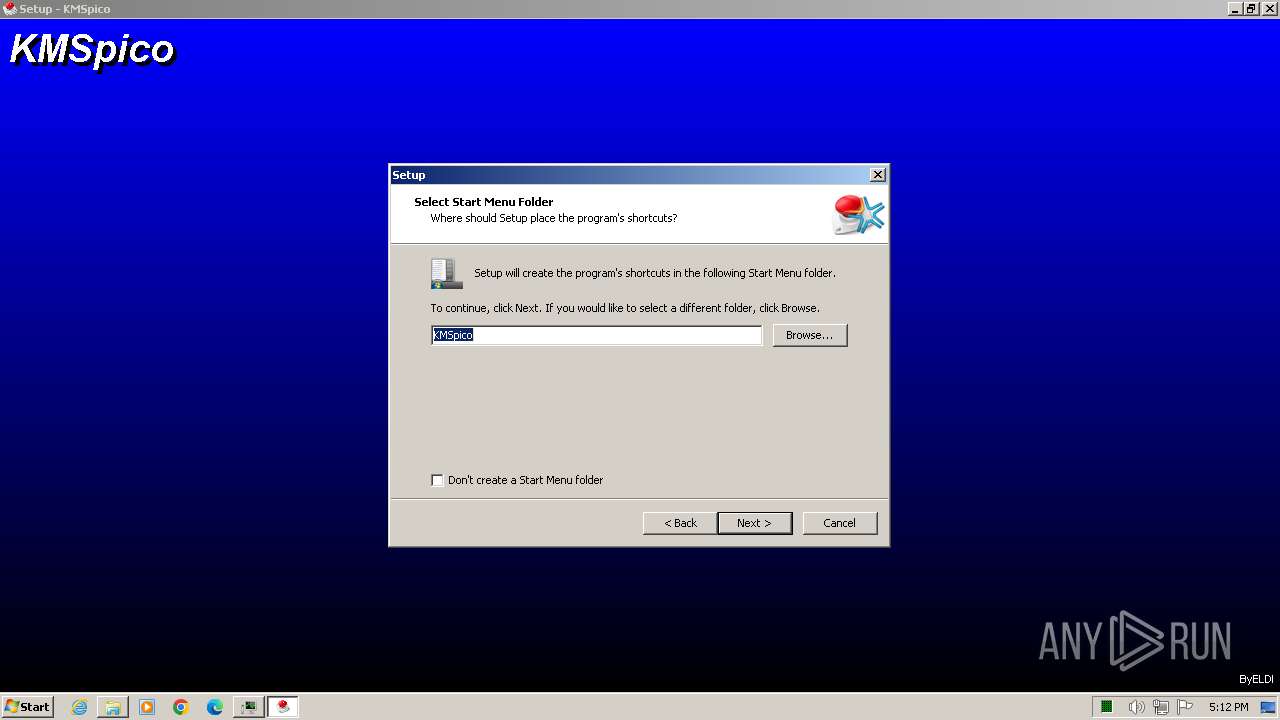
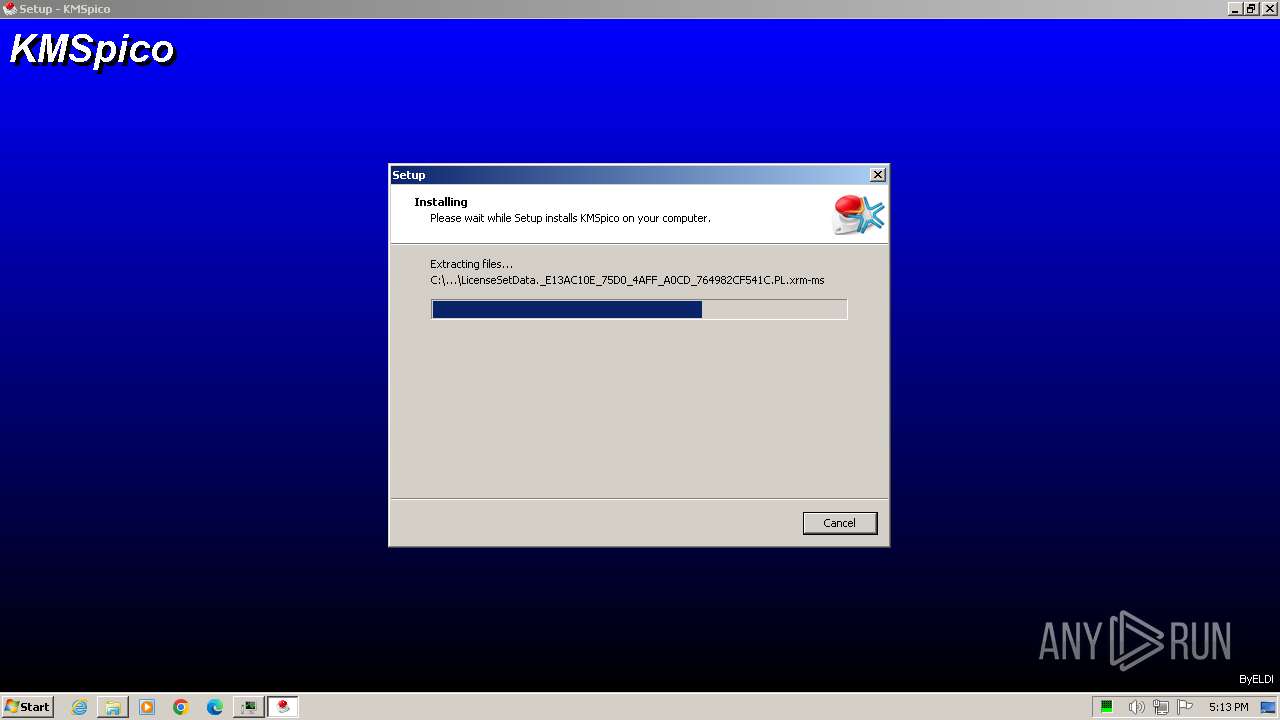
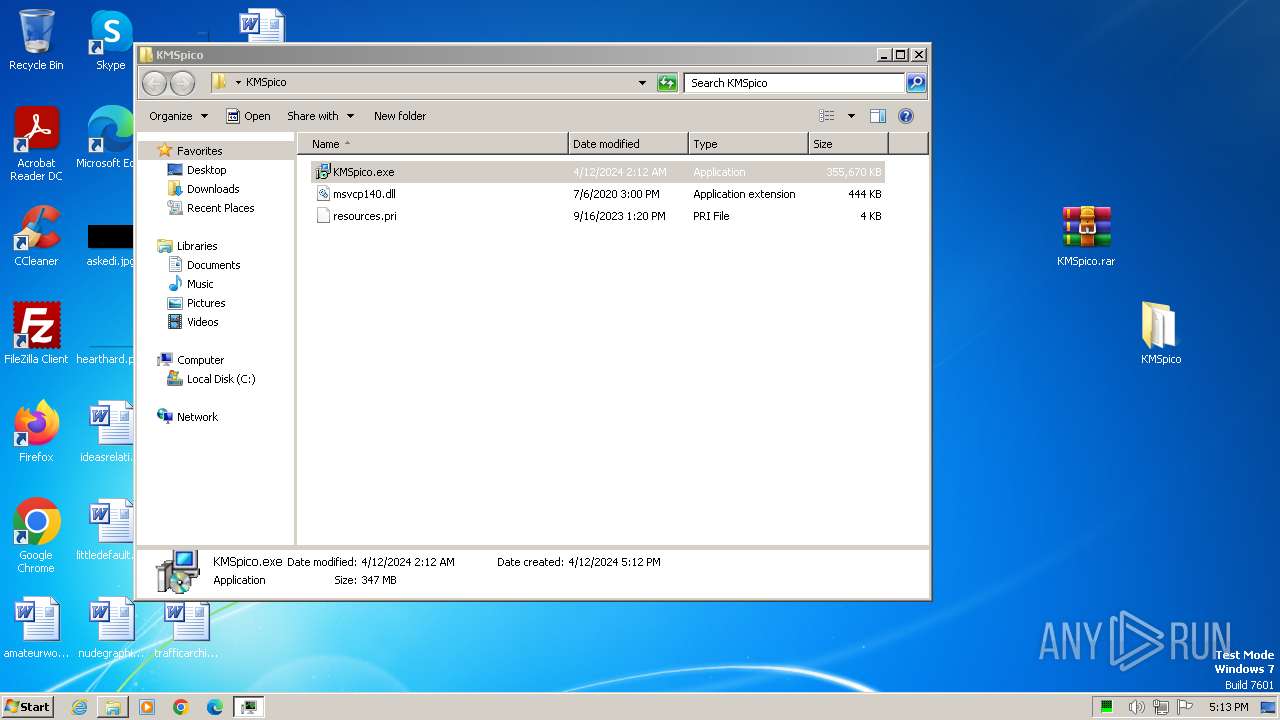
| File name: | КМSpicо_3153.zip |
| Full analysis: | https://app.any.run/tasks/d4820cdf-d87e-4b68-9d7c-6adc2b1b259b |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2024, 16:11:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | CC39EA6DF2A1BBFDEBF1D166D0D30B27 |
| SHA1: | F4A4D8A1D086F407F2455E62FE4BC7A96DA4CA17 |
| SHA256: | E0305E3F96F2A6FAB97D62A9200A4BF5C01D7D66ABFCAD12857039D56DA2562B |
| SSDEEP: | 98304:ibCs+Wa1Oe06P395RI8j8SIrjClTpUQ/sERhwQPs43Ej3rd+riPFX3u0sVIfuX6v:5nkEk1nEebR/ |
MALICIOUS
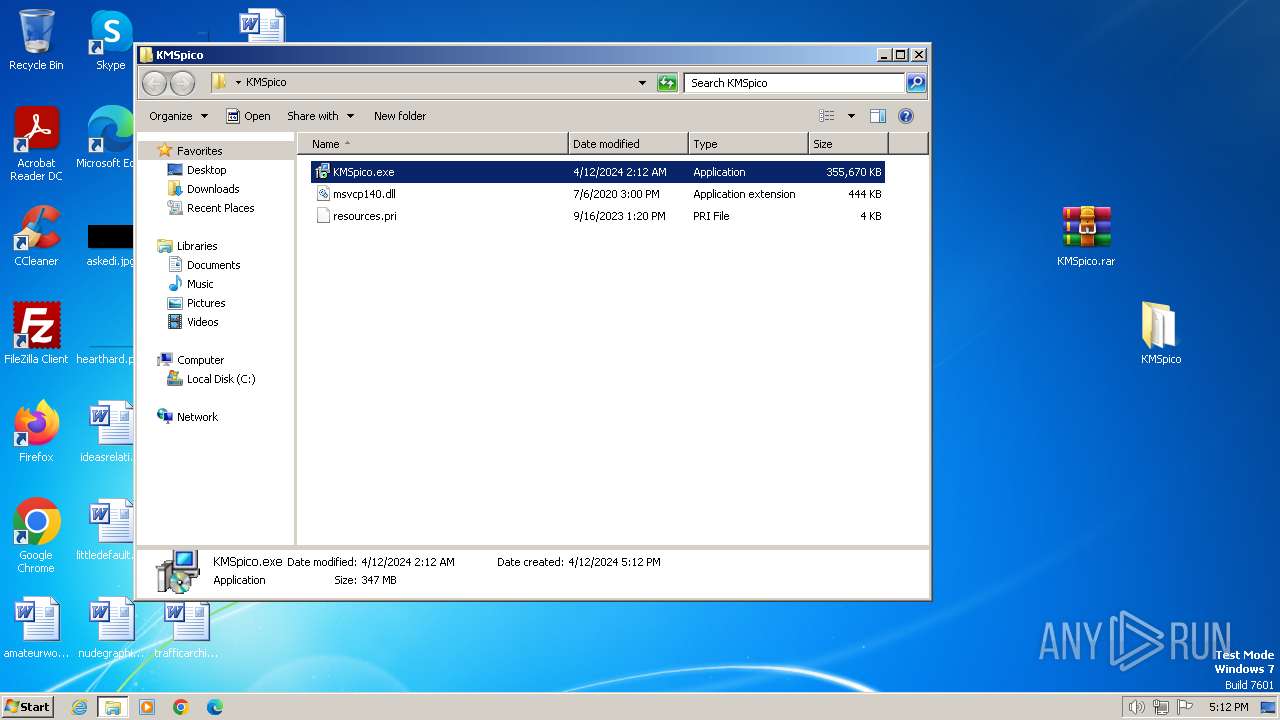
Drops the executable file immediately after the start
- KMSpico.exe (PID: 1236)
- Setup.exe (PID: 980)
- Setup.tmp (PID: 2240)
Actions looks like stealing of personal data
- KMSpico.exe (PID: 1236)
Creates a writable file in the system directory
- Setup.tmp (PID: 2240)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3180)
- Setup.tmp (PID: 2240)
Executable content was dropped or overwritten
- KMSpico.exe (PID: 1236)
- Setup.exe (PID: 980)
- Setup.tmp (PID: 2240)
- expand.exe (PID: 3540)
Reads the Internet Settings
- KMSpico.exe (PID: 1236)
Reads security settings of Internet Explorer
- KMSpico.exe (PID: 1236)
Reads the Windows owner or organization settings
- Setup.tmp (PID: 2240)
Searches for installed software
- KMSpico.exe (PID: 1236)
Reads browser cookies
- KMSpico.exe (PID: 1236)
Starts CMD.EXE for commands execution
- KMSpico.exe (PID: 1236)
- Setup.tmp (PID: 2240)
Modifies the phishing filter of IE
- Setup.tmp (PID: 2240)
Executing commands from ".cmd" file
- Setup.tmp (PID: 2240)
Starts SC.EXE for service management
- cmd.exe (PID: 1892)
Creates or modifies Windows services
- KMSELDI.exe (PID: 1784)
Non-standard symbols in registry
- Setup.tmp (PID: 2240)
The process executes via Task Scheduler
- Davonevur.exe (PID: 1316)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3180)
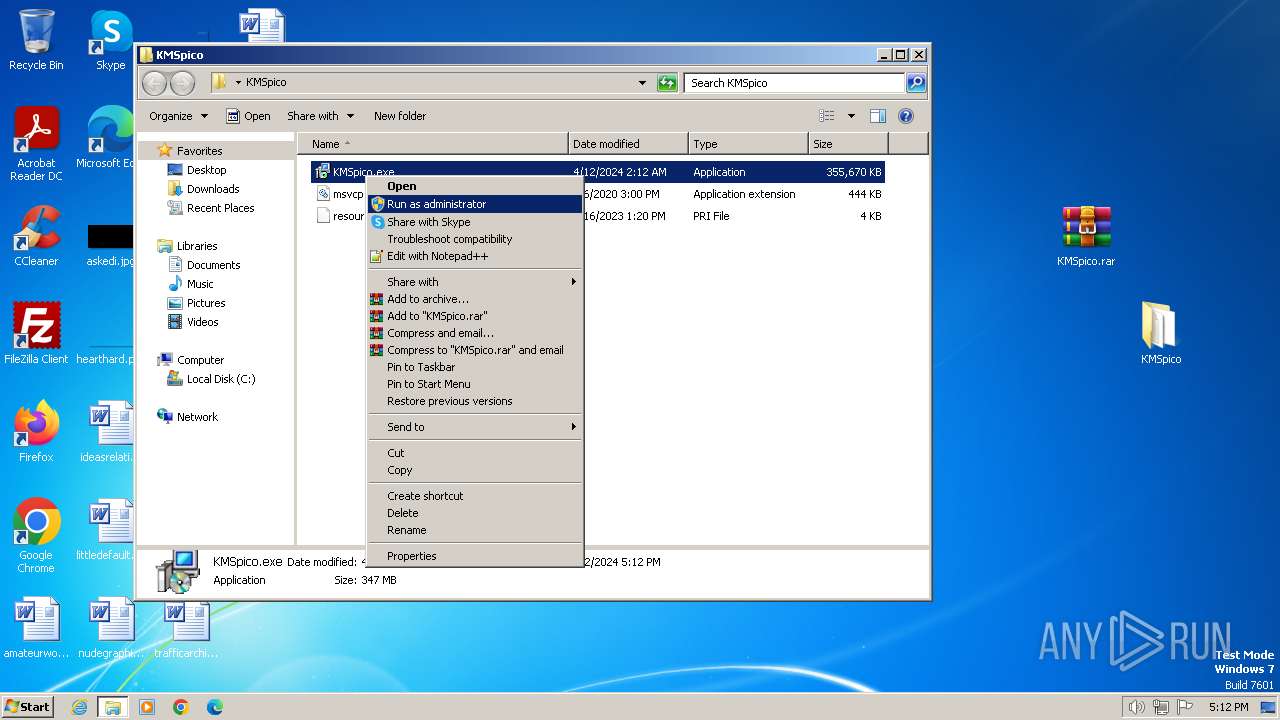
Manual execution by a user
- WinRAR.exe (PID: 3180)
- KMSpico.exe (PID: 1236)
- taskmgr.exe (PID: 2724)
- KMSELDI.exe (PID: 3588)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 2900)
- KMSELDI.exe (PID: 3852)
Checks supported languages
- KMSpico.exe (PID: 1236)
- Setup.exe (PID: 980)
- Setup.tmp (PID: 2240)
- UninsHs.exe (PID: 3088)
- KMSELDI.exe (PID: 1784)
- AutoPico.exe (PID: 3492)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 3852)
- Davonevur.exe (PID: 1316)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3180)
- expand.exe (PID: 3540)
Create files in a temporary directory
- KMSpico.exe (PID: 1236)
- Setup.exe (PID: 980)
- Setup.tmp (PID: 2240)
Reads the computer name
- KMSpico.exe (PID: 1236)
- Setup.tmp (PID: 2240)
- KMSELDI.exe (PID: 1784)
- AutoPico.exe (PID: 3492)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 3852)
Reads CPU info
- KMSpico.exe (PID: 1236)
Creates files in the program directory
- Setup.tmp (PID: 2240)
- KMSELDI.exe (PID: 1784)
- AutoPico.exe (PID: 3492)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 3852)
Creates files or folders in the user directory
- KMSpico.exe (PID: 1236)
- expand.exe (PID: 3540)
Creates a software uninstall entry
- Setup.tmp (PID: 2240)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 1784)
- AutoPico.exe (PID: 3492)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 3852)
Reads Environment values
- KMSELDI.exe (PID: 1784)
- AutoPico.exe (PID: 3492)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 3852)
Reads product name
- KMSELDI.exe (PID: 1784)
- AutoPico.exe (PID: 3492)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 3852)
Reads Microsoft Office registry keys
- KMSELDI.exe (PID: 1784)
- AutoPico.exe (PID: 3492)
- KMSELDI.exe (PID: 3832)
- KMSELDI.exe (PID: 3852)
Reads mouse settings
- Davonevur.exe (PID: 1316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:12 04:48:44 |
| ZipCRC: | 0x32964ad7 |
| ZipCompressedSize: | 5848142 |
| ZipUncompressedSize: | 5848142 |
| ZipFileName: | ??Spic?.rar |
Total processes
77
Monitored processes
22
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 980 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | KMSpico.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: KMSpico Setup Exit code: 0 Version: 10.2.0 Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\Desktop\КМSpicо\KMSpico.exe" | C:\Users\admin\Desktop\КМSpicо\KMSpico.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1316 | C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.exe "C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.jpg" | C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.exe | — | taskeng.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Version: 3, 3, 16, 1 Modules
| |||||||||||||||
| 1540 | sc create "Service KMSELDI" binPath= "C:\Program Files\KMSpico\Service_KMS.exe" type= own error= normal start= auto DisplayName= "Service KMSELDI" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1624 | "C:\Windows\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\Install_Task.cmd"" | C:\Windows\System32\cmd.exe | — | Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1728 | SCHTASKS /Create /TN "AutoPico Daily Restart" /TR "'C:\Program Files\KMSpico\AutoPico.exe' /silent" /SC DAILY /ST 23:59:59 /RU "NT AUTHORITY\SYSTEM" /RL Highest /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
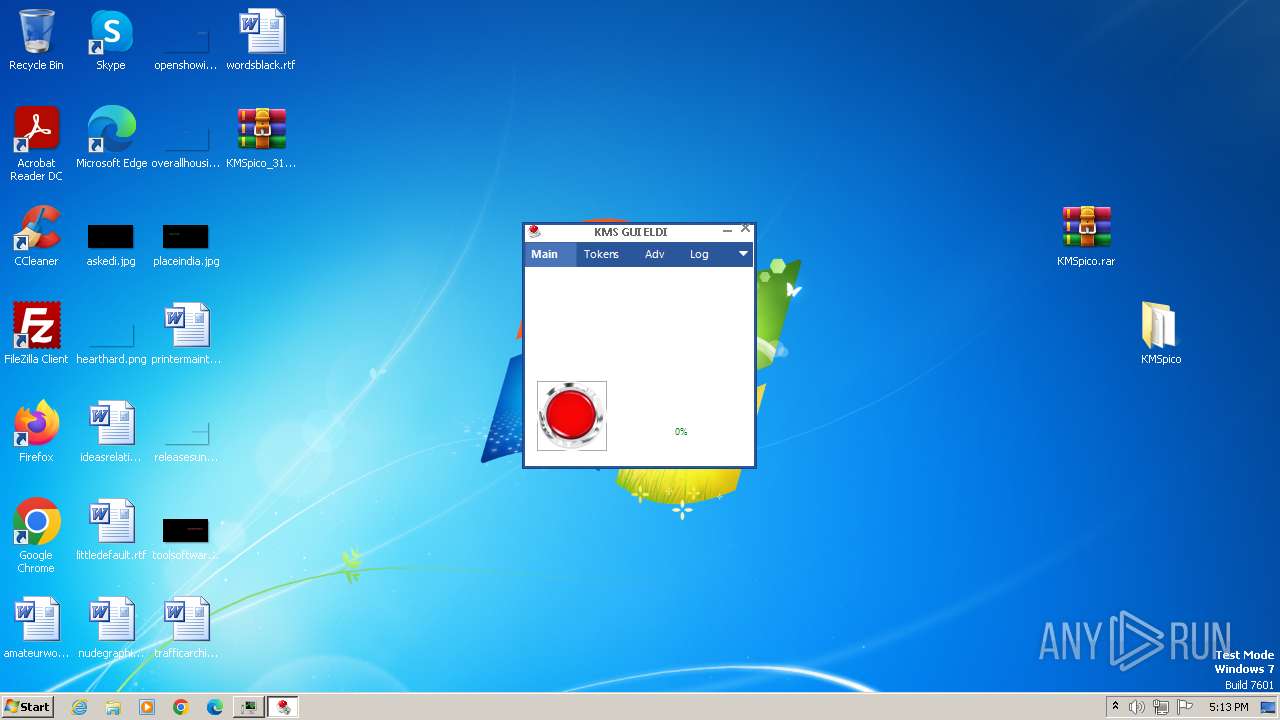
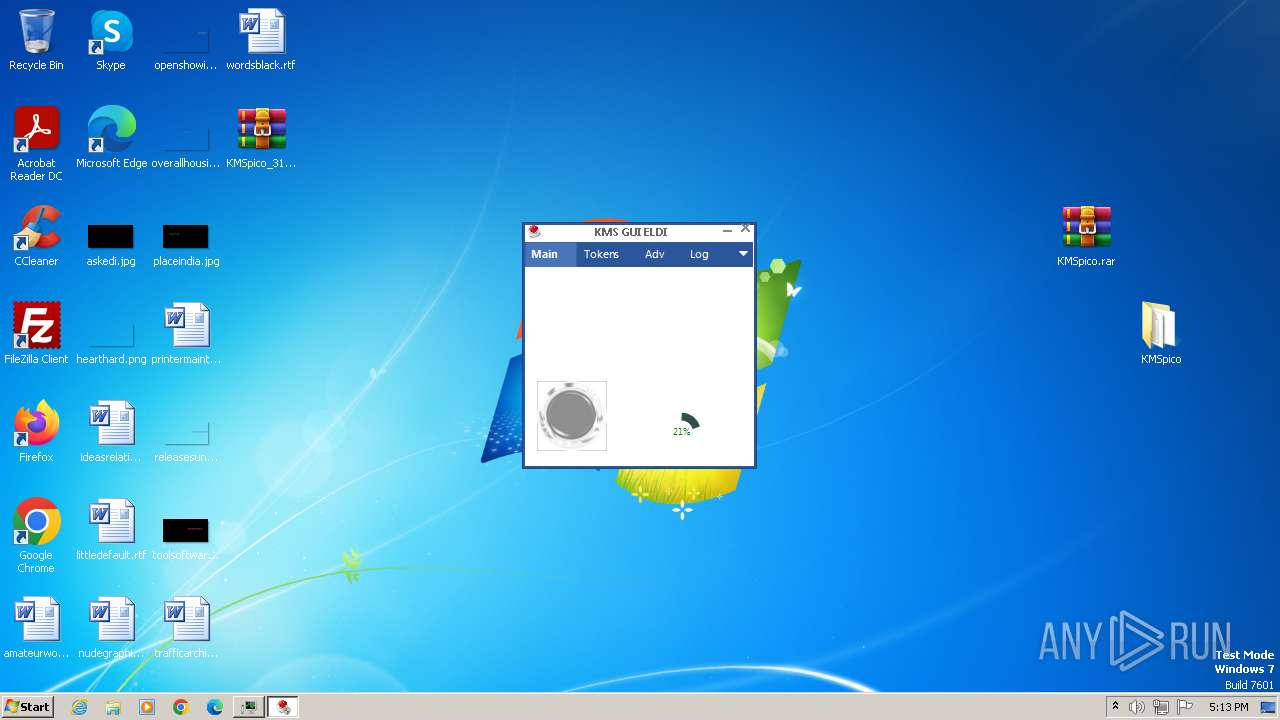
| 1784 | "C:\Program Files\KMSpico\KMSELDI.exe" /silent /backup | C:\Program Files\KMSpico\KMSELDI.exe | Setup.tmp | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 4294967295 Version: 37.1.0.0 Modules
| |||||||||||||||
| 1864 | schtasks /create /tn \Service\Data /tr """"C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.exe""" """C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.jpg"""" /st 00:01 /du 9800:59 /sc once /ri 1 /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | "C:\Windows\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\Install_Service.cmd"" | C:\Windows\System32\cmd.exe | — | Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\AppData\Local\Temp\is-4OUOV.tmp\Setup.tmp" /SL5="$601F0,2952592,69120,C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-4OUOV.tmp\Setup.tmp | Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
22 307
Read events
22 115
Write events
182
Delete events
10
Modification events
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\КМSpicо_3153.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
24
Suspicious files
34
Text files
720
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3936.14415\КМSpicо.rar | — | |
MD5:— | SHA256:— | |||
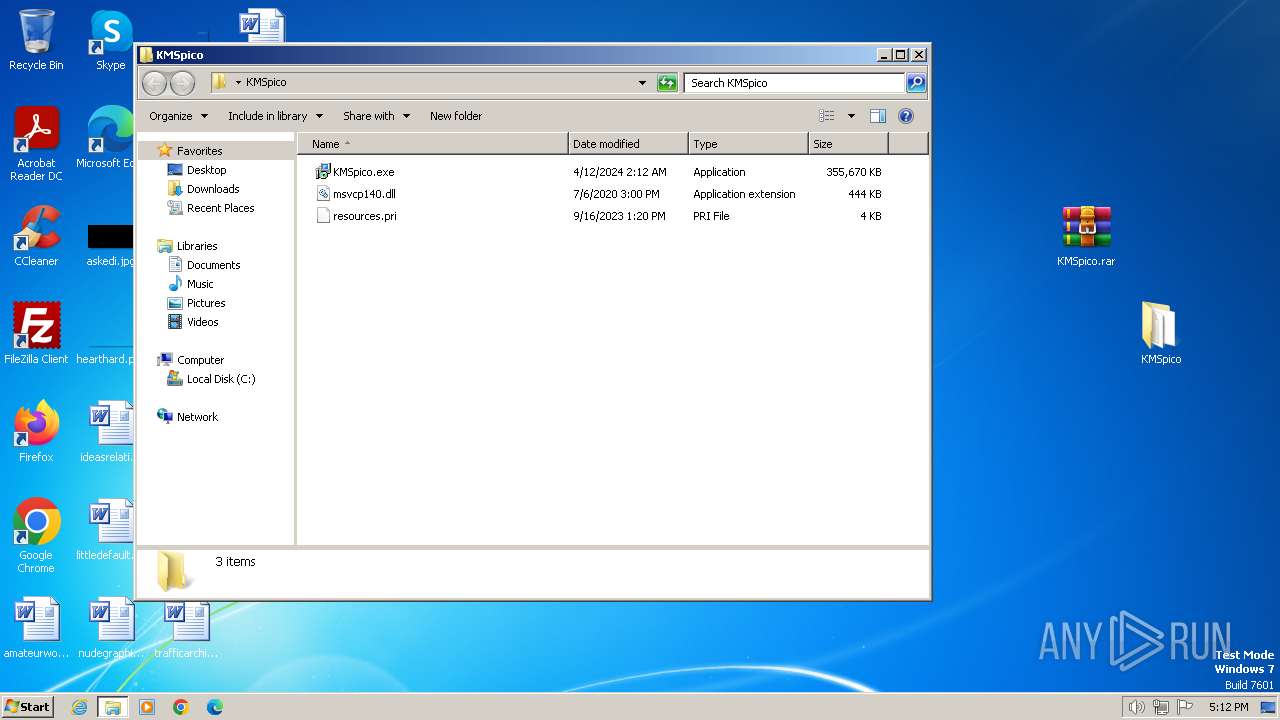
| 3180 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3180.15042\КМSpicо\KMSpico.exe | — | |
MD5:— | SHA256:— | |||
| 3180 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3180.15042\КМSpicо\msvcp140.dll | executable | |
MD5:— | SHA256:— | |||
| 3180 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3180.15042\КМSpicо\resources.pri | pri | |
MD5:— | SHA256:— | |||
| 1236 | KMSpico.exe | C:\Users\admin\AppData\Local\Temp\Setup.exe | executable | |
MD5:— | SHA256:— | |||
| 980 | Setup.exe | C:\Users\admin\AppData\Local\Temp\is-4OUOV.tmp\Setup.tmp | executable | |
MD5:— | SHA256:— | |||
| 2240 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-J7J4K.tmp\_isetup\_shfoldr.dll | executable | |
MD5:— | SHA256:— | |||
| 2240 | Setup.tmp | C:\Program Files\KMSpico\is-0HMMP.tmp | executable | |
MD5:— | SHA256:— | |||
| 2240 | Setup.tmp | C:\Program Files\KMSpico\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 2240 | Setup.tmp | C:\Program Files\KMSpico\is-OB0OQ.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
6
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1236 | KMSpico.exe | POST | 200 | 193.222.62.12:80 | http://glfor4pt.top/upload.php | unknown | — | — | unknown |
1236 | KMSpico.exe | POST | 200 | 193.222.62.12:80 | http://glfor4pt.top/upload.php | unknown | — | — | unknown |
1236 | KMSpico.exe | POST | 200 | 193.222.62.12:80 | http://glfor4pt.top/upload.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1236 | KMSpico.exe | 193.222.62.12:80 | glfor4pt.top | Sprinthost.ru LLC | RU | unknown |
1784 | KMSELDI.exe | 144.76.76.107:123 | 1.pool.ntp.org | — | — | unknown |
3492 | AutoPico.exe | 85.220.190.246:123 | 2.pool.ntp.org | — | — | unknown |
3832 | KMSELDI.exe | 85.220.190.246:123 | 2.pool.ntp.org | — | — | unknown |
3852 | KMSELDI.exe | 212.112.228.242:123 | 0.pool.ntp.org | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
glfor4pt.top |
| unknown |
1.pool.ntp.org |
| whitelisted |
www.google.com |
| whitelisted |
2.pool.ntp.org |
| whitelisted |
0.pool.ntp.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1236 | KMSpico.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3 ETPRO signatures available at the full report