| URL: | https://hacker.com/ |
| Full analysis: | https://app.any.run/tasks/714be545-c909-48e3-82ff-13439343b1cd |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 16:04:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 30C4F07BBC1FD7CEF3B45392FD351199 |
| SHA1: | C3660E43FA83B2FCD5370F7FB631F3094E14EC71 |
| SHA256: | E02BD23C1728D21493207EEF17CFA544A3EC371DC08229DA84C2149DC8F54E5B |
| SSDEEP: | 3:N840:240 |
MALICIOUS
Changes the autorun value in the registry
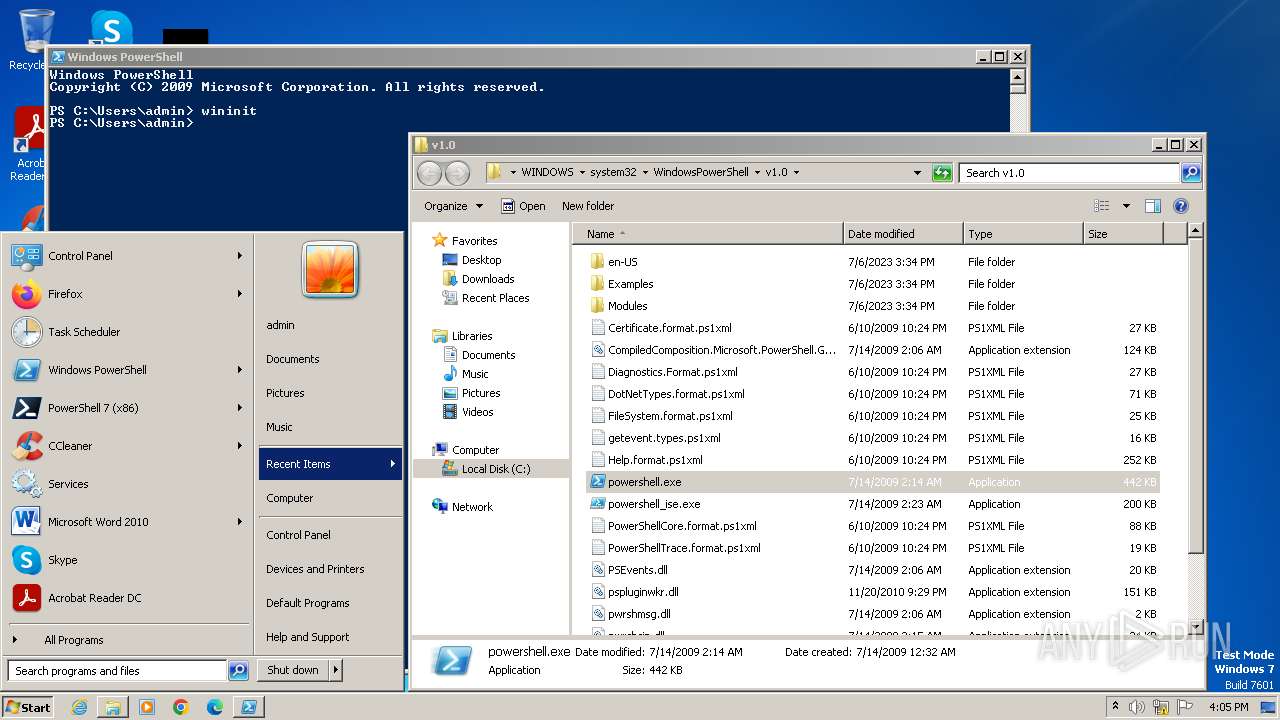
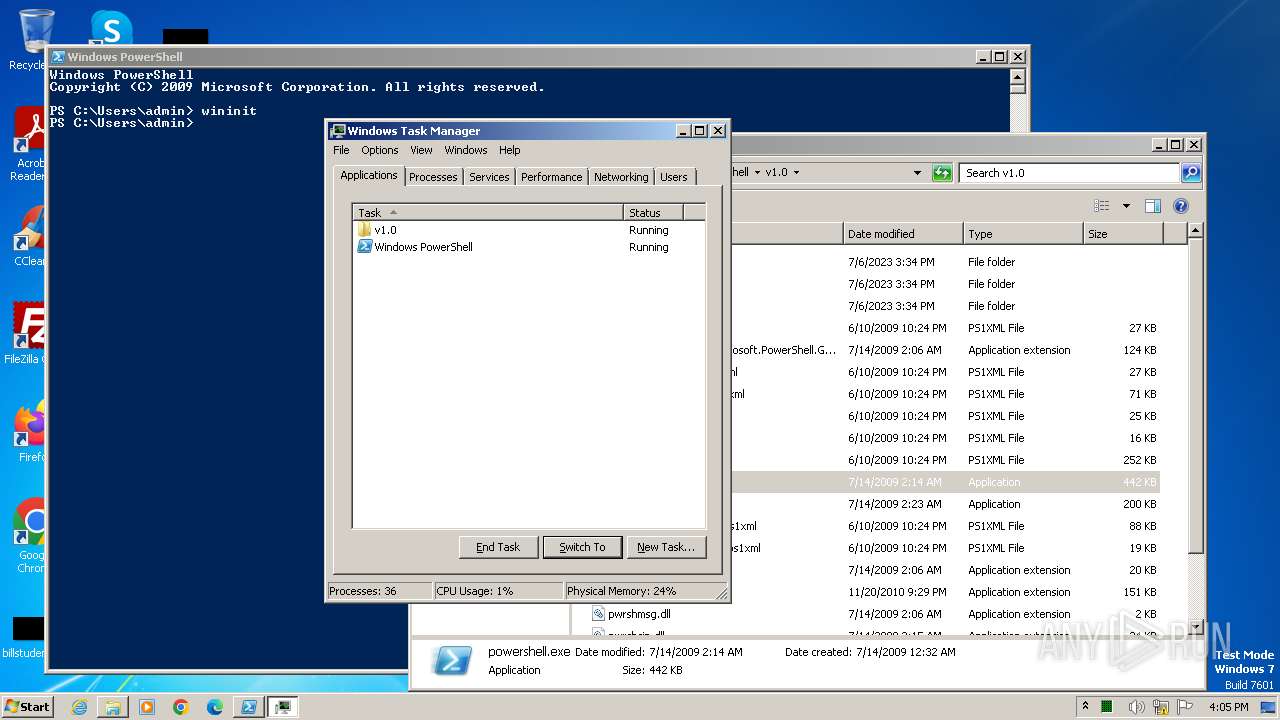
- taskmgr.exe (PID: 3684)
SUSPICIOUS
Powershell version downgrade attack
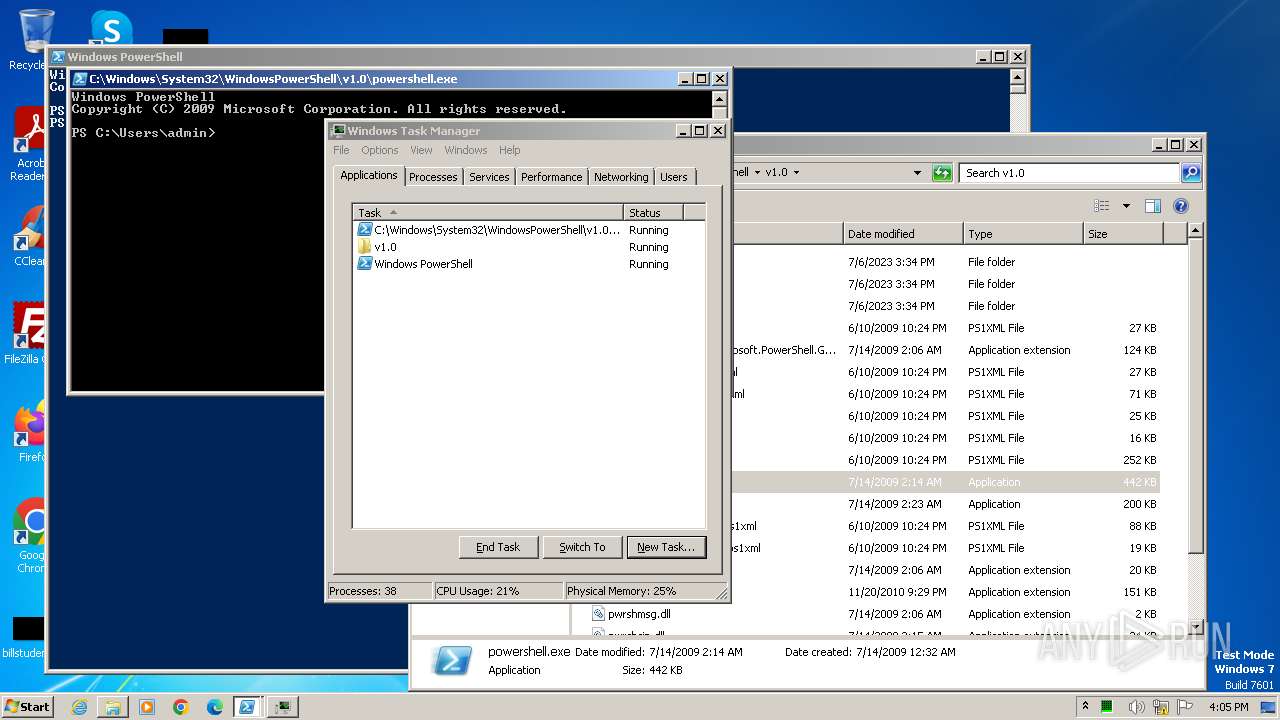
- powershell.exe (PID: 3856)
- powershell.exe (PID: 3588)
Starts POWERSHELL.EXE for commands execution
- taskmgr.exe (PID: 3684)
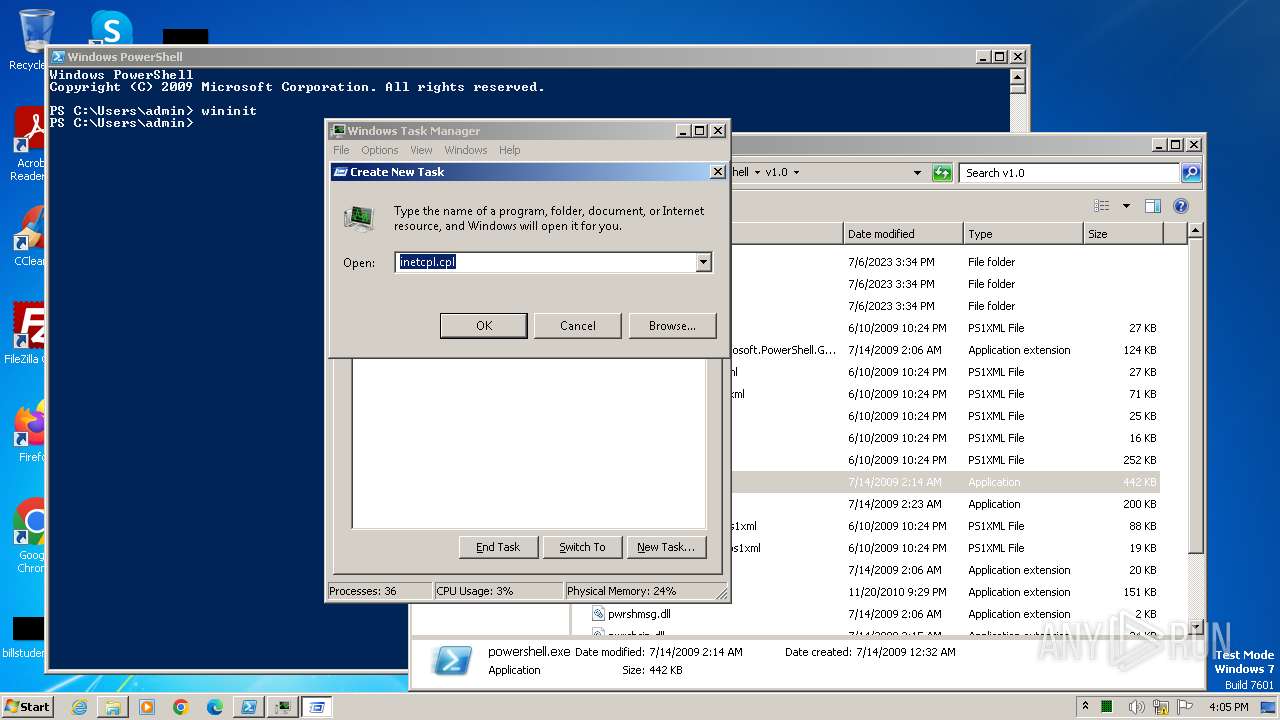
Reads the Internet Settings
- taskmgr.exe (PID: 3684)
INFO
Application launched itself
- iexplore.exe (PID: 2644)
Manual execution by a user
- powershell.exe (PID: 3856)
- taskmgr.exe (PID: 3684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1584 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2644 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://hacker.com/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3112 | "C:\Windows\system32\wininit.exe" | C:\Windows\System32\wininit.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Start-Up Application Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3588 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | taskmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3684 | "C:\Windows\system32\taskmgr.exe" | C:\Windows\System32\taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3856 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Windows\system32\wininit.exe" | C:\Windows\System32\wininit.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Start-Up Application Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 458
Read events
4 234
Write events
224
Delete events
0
Modification events
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
12
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\KOGAGZV9ER0YJHP4G4MY.temp | binary | |
MD5:3C9EA70BE0EB9C07AB7B929F19966EB2 | SHA256:9AD86CBABCCCD9B21DD789AA354DF25F0ECE29BAF284F5C81DE6A19A634E756F | |||
| 3856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:3C9EA70BE0EB9C07AB7B929F19966EB2 | SHA256:9AD86CBABCCCD9B21DD789AA354DF25F0ECE29BAF284F5C81DE6A19A634E756F | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{8859080E-912C-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:70D4612DF071C1248F9558E1FF8985E5 | SHA256:7E4C54CD9805A234F18B25055659553AD948A08F045755EA0B5BA077EFDE2167 | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA261BF4EDC6C2AB6.TMP | gmc | |
MD5:8D0629CCEA749F6E26F2C2373018A9A1 | SHA256:E9D579BCFB6416DDE864AF7274993A9E7B86EB2F38E0605C1966A6EF1F5687F7 | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF86A31AA4039EBF00.TMP | binary | |
MD5:3BF996D6B801BAA6783CA20A884EE86F | SHA256:0D31B0C4E0ACAD90AA335F293D9AECD8EC8827EC35B0164B93DA364C2710565A | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{8229EEA1-912C-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:D3F40BE6C55EF6904B4D1CB644DE84B5 | SHA256:C6DBB21F5447026B1B461B872FAA76A37334EADF9556C4EBA3E62ED177CF42B3 | |||
| 3588 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF216fff.TMP | binary | |
MD5:3C9EA70BE0EB9C07AB7B929F19966EB2 | SHA256:9AD86CBABCCCD9B21DD789AA354DF25F0ECE29BAF284F5C81DE6A19A634E756F | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCA381CCFE0F2BC2F.TMP | binary | |
MD5:27AFF9A6BB2A26FA49E991F79A414919 | SHA256:B333EA2FB3277DC16068E5C236F73A56EA683447853891DDCC3C02932F71D574 | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:8B51D45D69B9B02622D0CE6ADA561E50 | SHA256:6C35615ABDB6E79A9821A9BC8E8E6770DDB095993AAB710F9106A92000F4F17F | |||
| 3856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF20ae16.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
19
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2644 | iexplore.exe | 23.53.43.89:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2644 | iexplore.exe | 23.53.43.88:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2644 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
2644 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hacker.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
dns.msftncsi.com |
| shared |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |