| File name: | F0EB0_P4rr0tCr4sh3r.bat |
| Full analysis: | https://app.any.run/tasks/f7bd4ff6-b63c-4b4b-9605-5dba756788e4 |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2025, 22:34:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 2E5DBFF716D281FD7A15F39B4F30F819 |
| SHA1: | A7437F71B2C11D83147850052F5785CC938400F2 |
| SHA256: | E015AD4A3D72193DE437CA7A296E58BC6B317A858AE0B7628DA8EE4C8F389F09 |
| SSDEEP: | 12:wbYVJbOfOOOByTWtUdOoPTViypiOCaKU0F5tRWyOWk/Ws9WW7B6/Wf4od9sEXUuB:wqSOByTWWbGHnNKPL9WC8EIEXUuB |
MALICIOUS
No malicious indicators.SUSPICIOUS
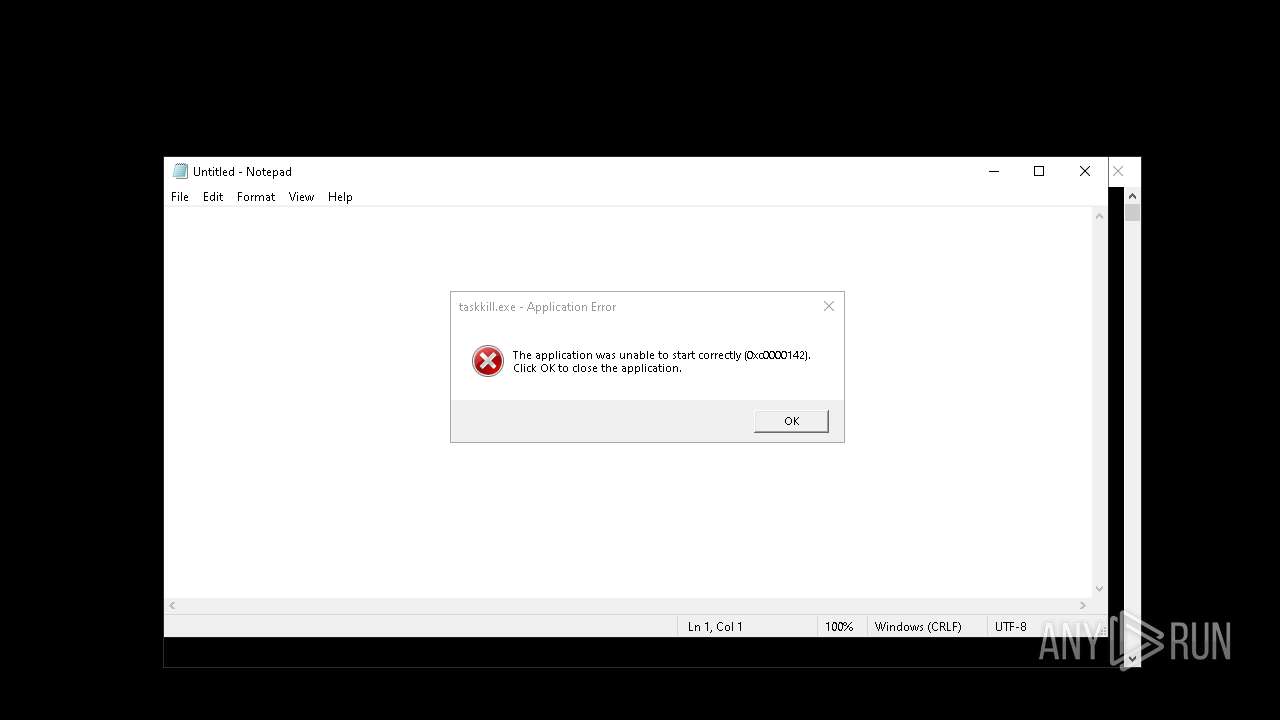
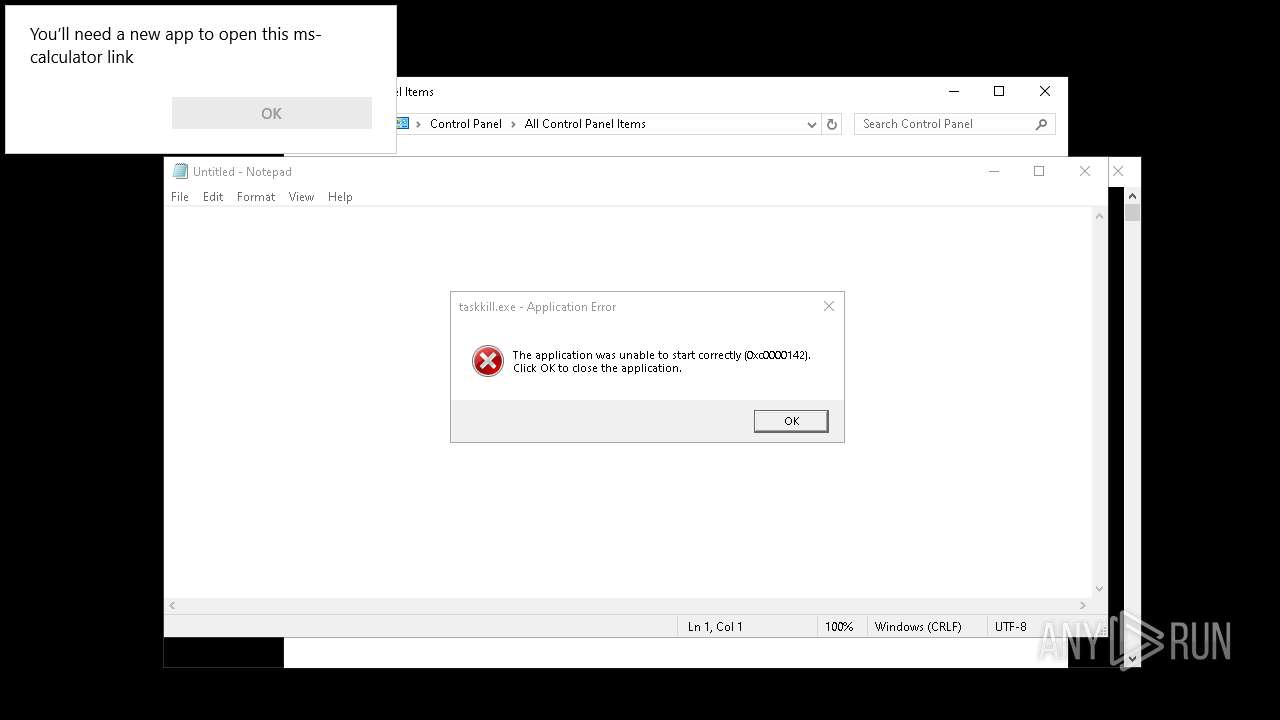
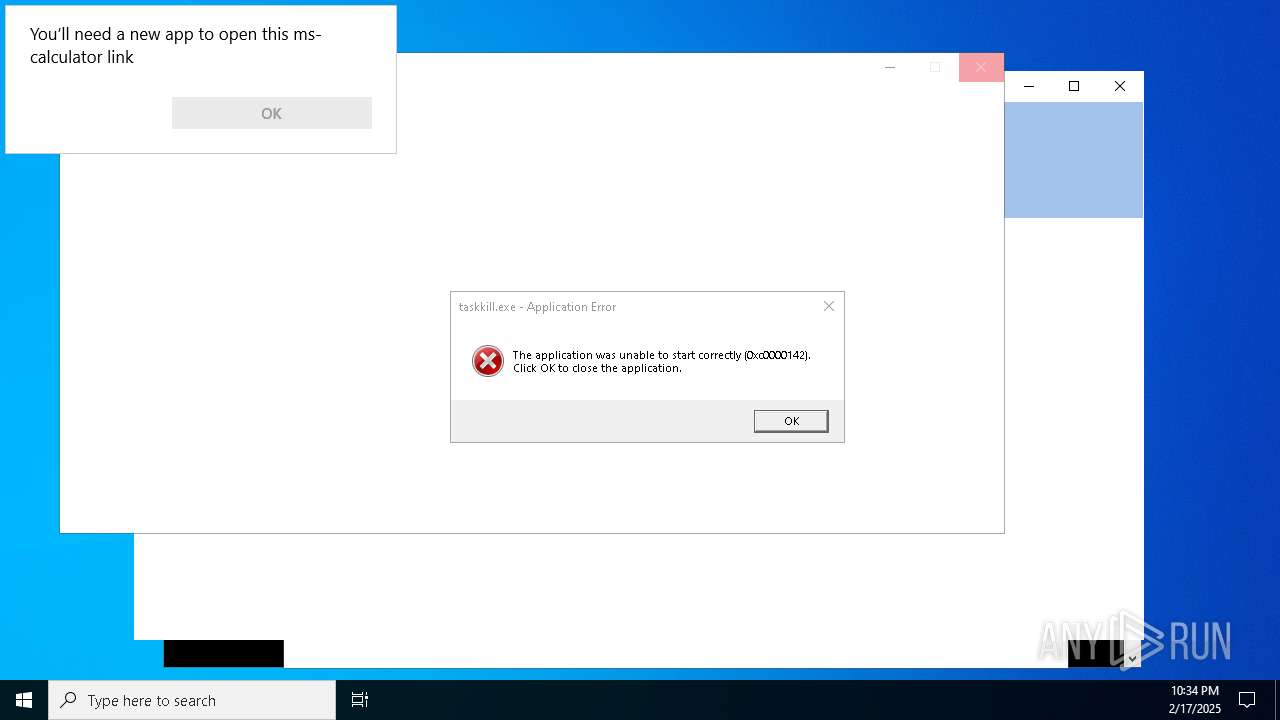
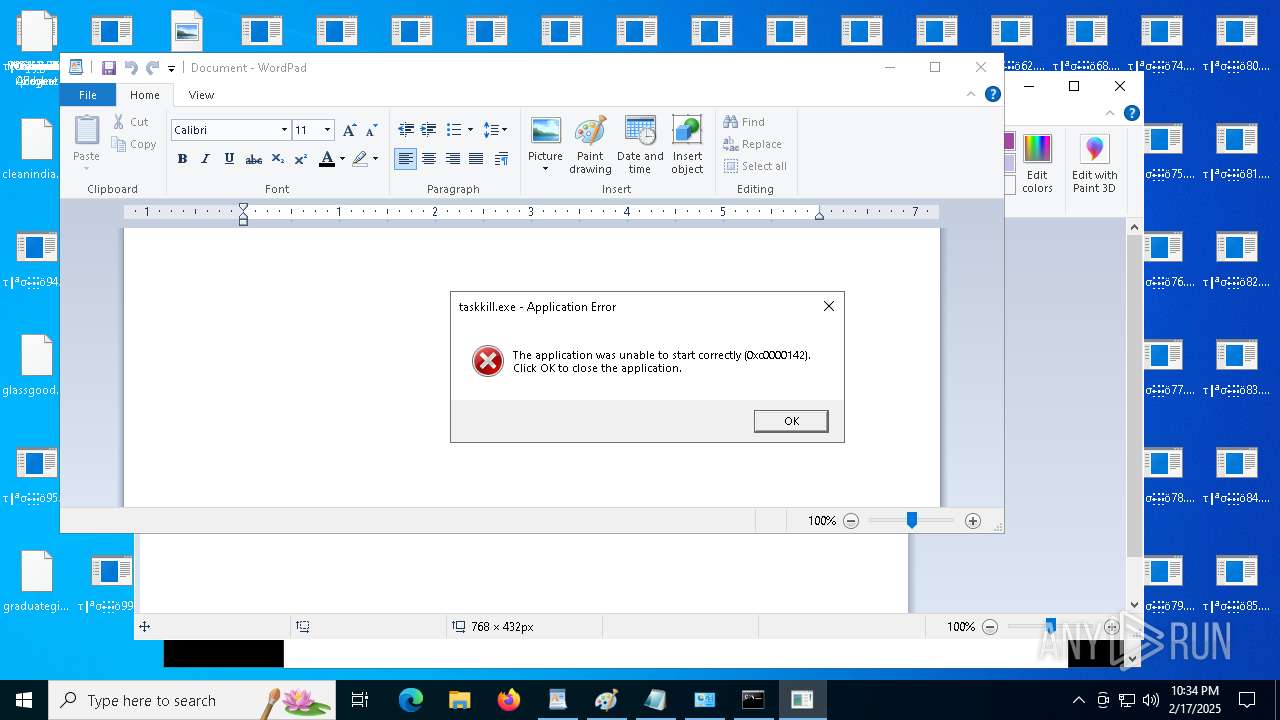
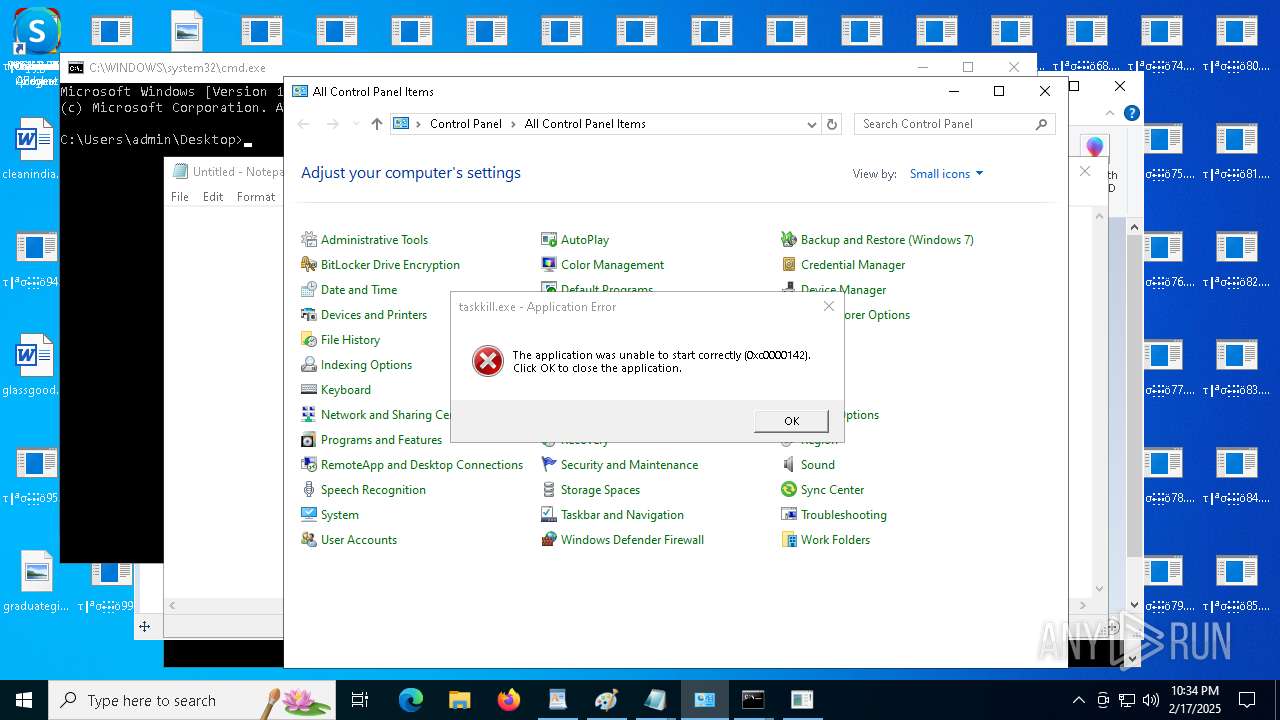
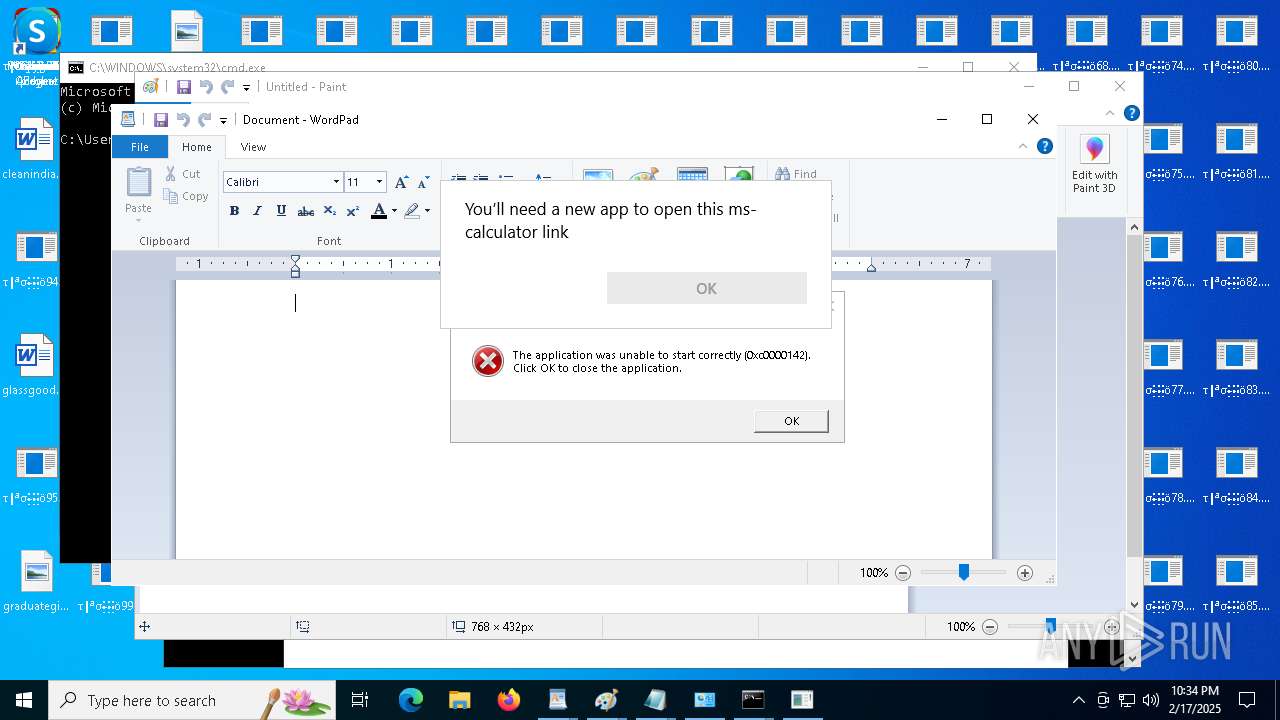
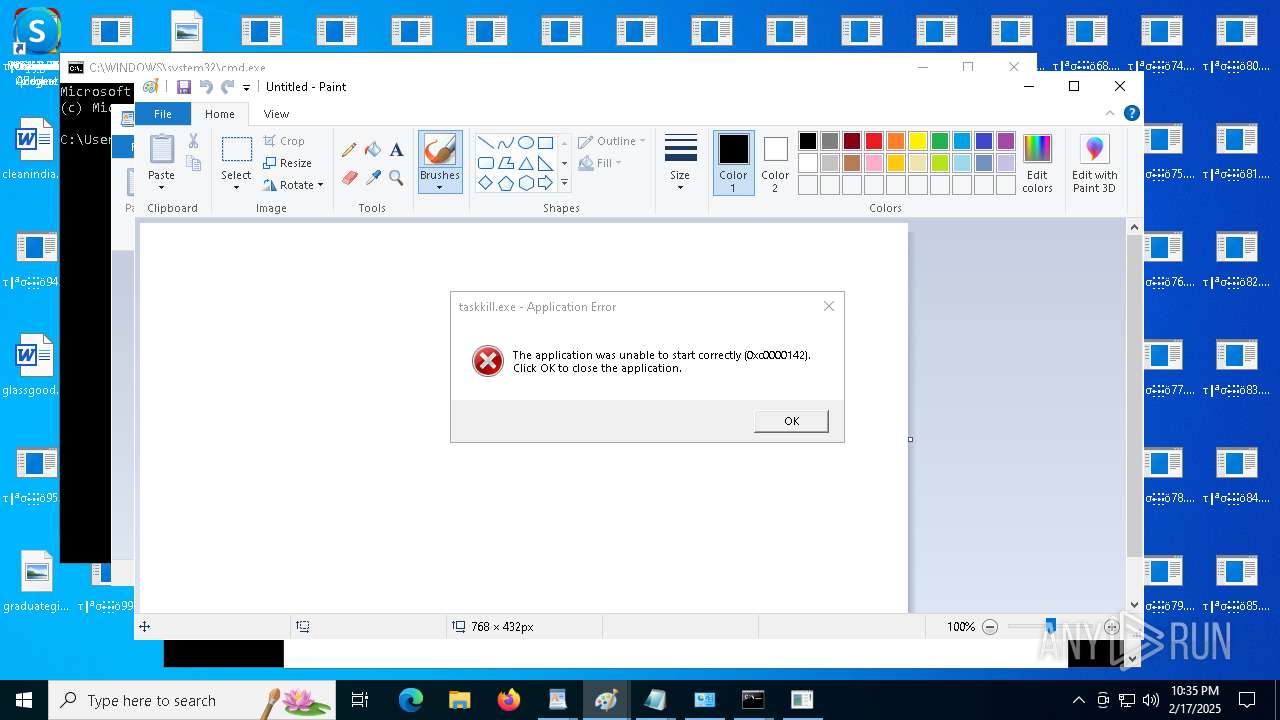
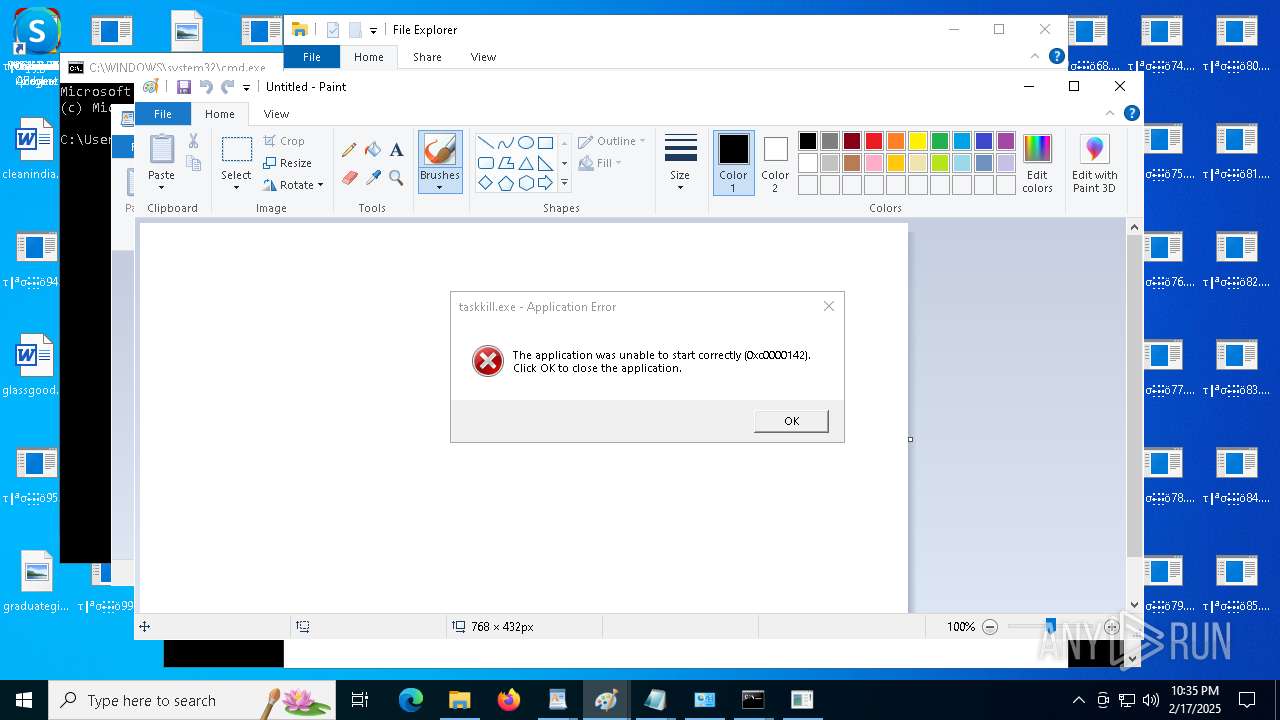
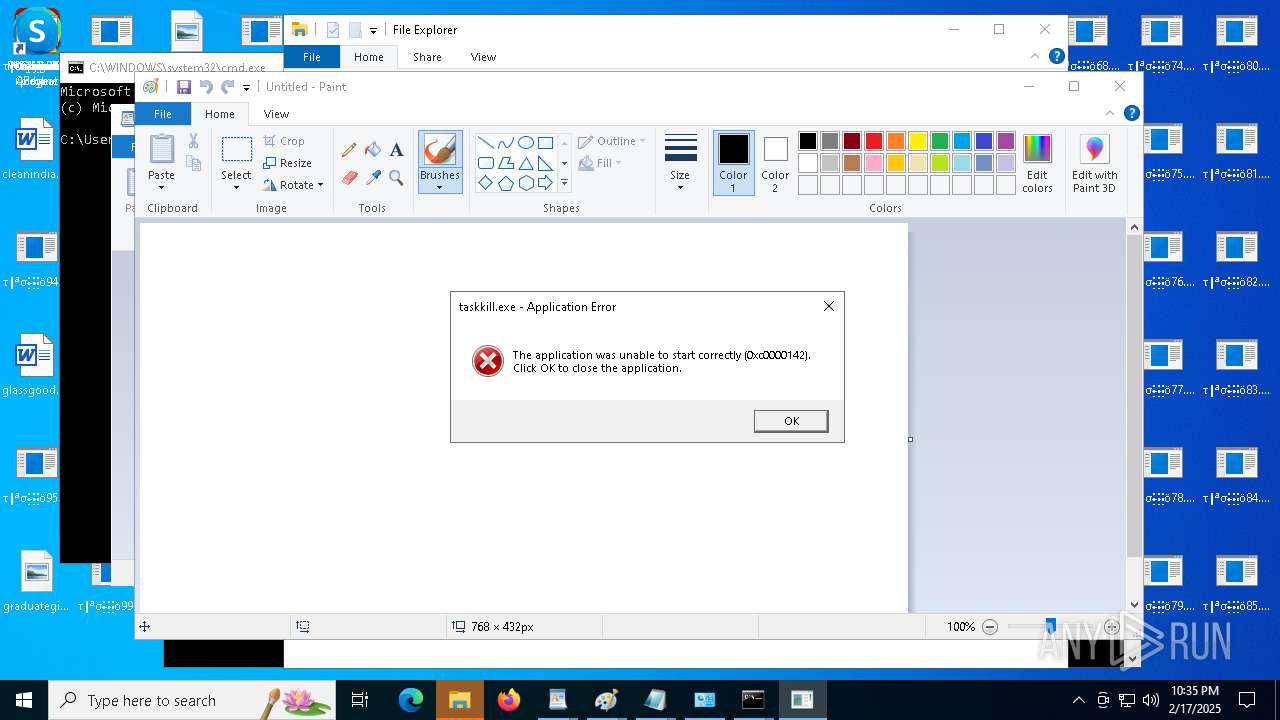
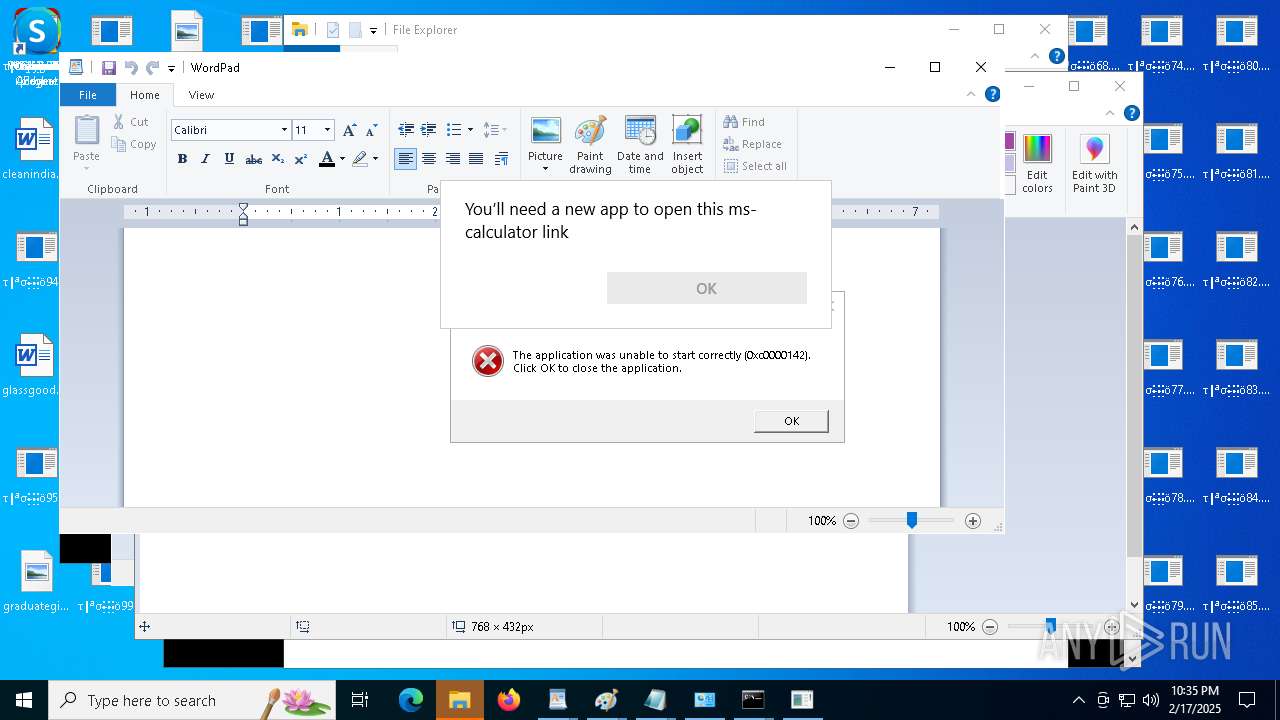
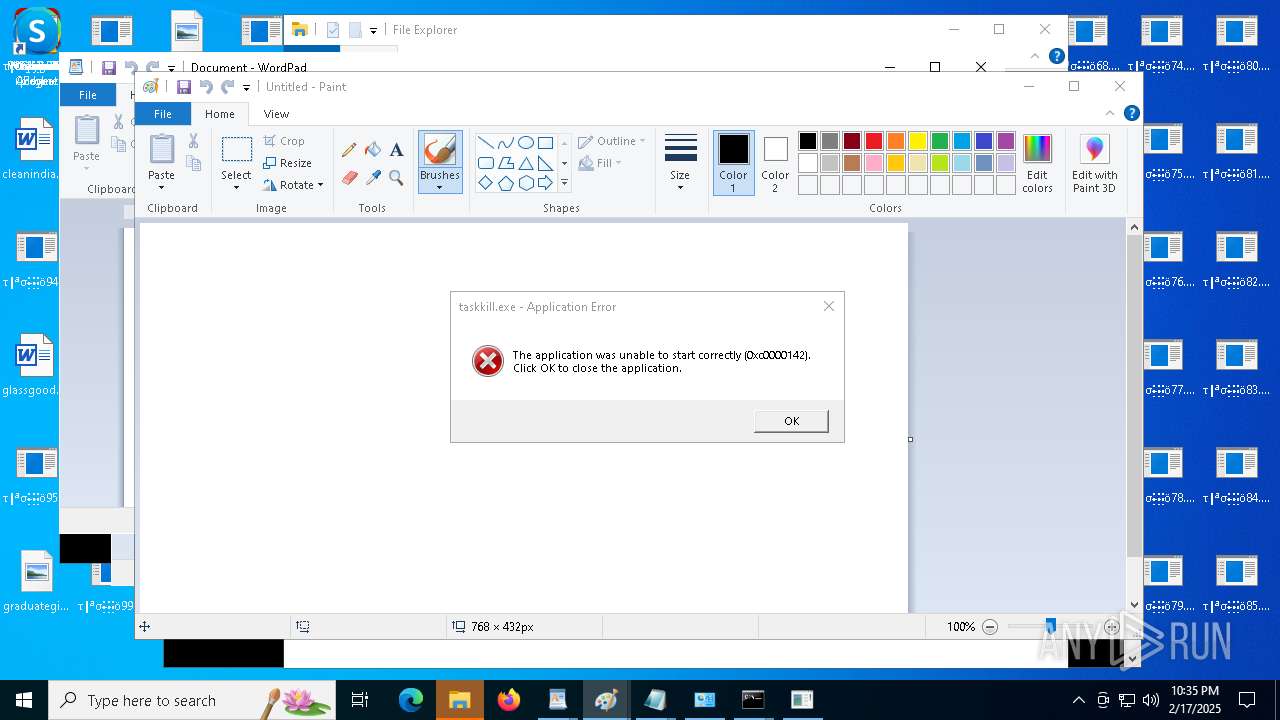
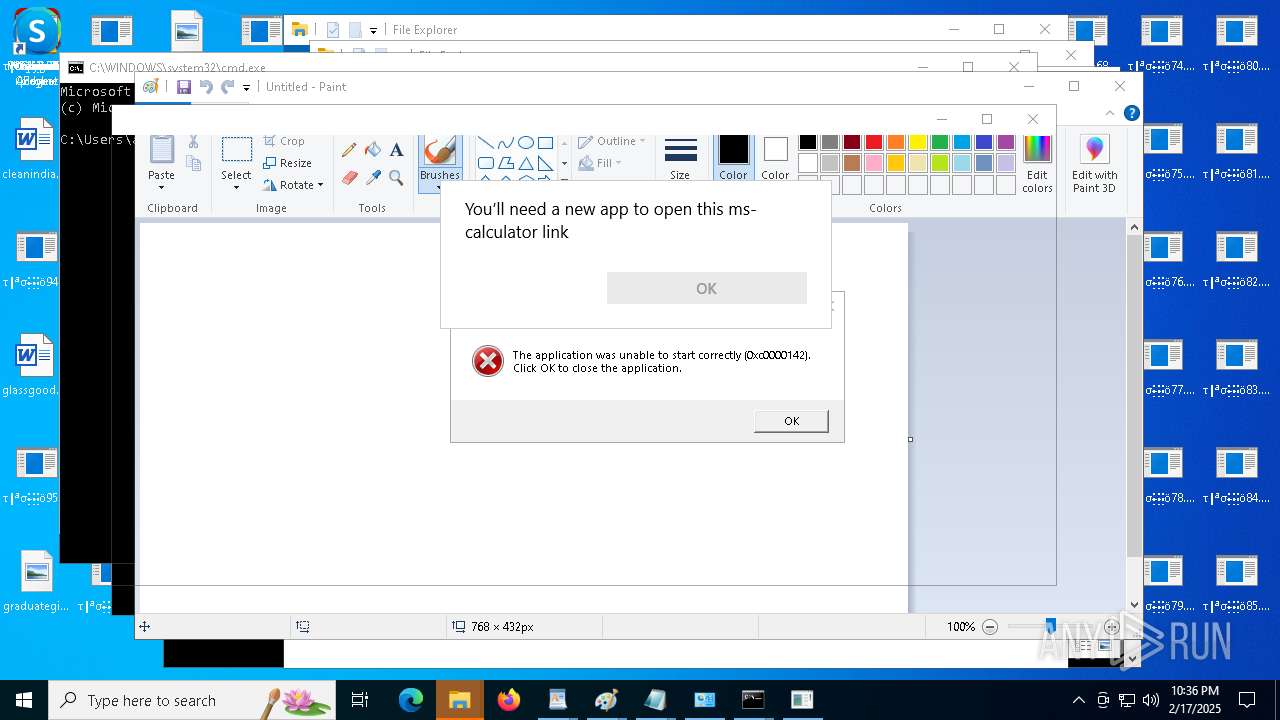
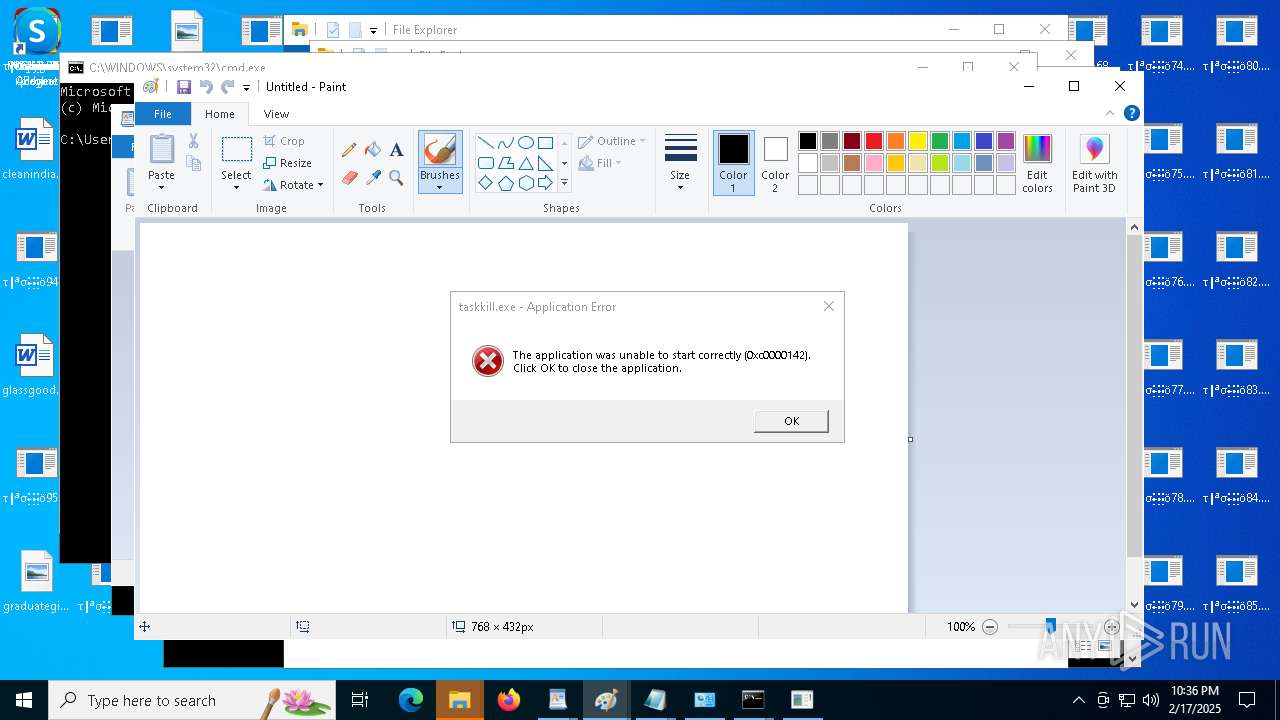
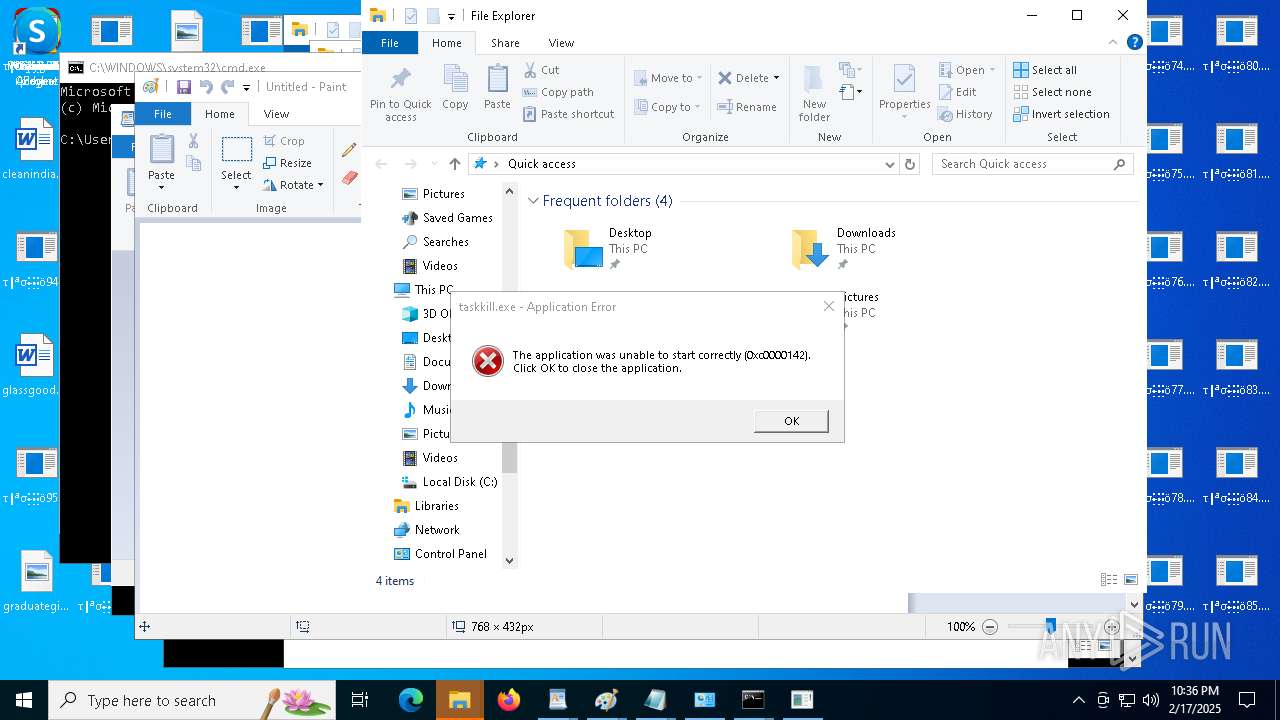
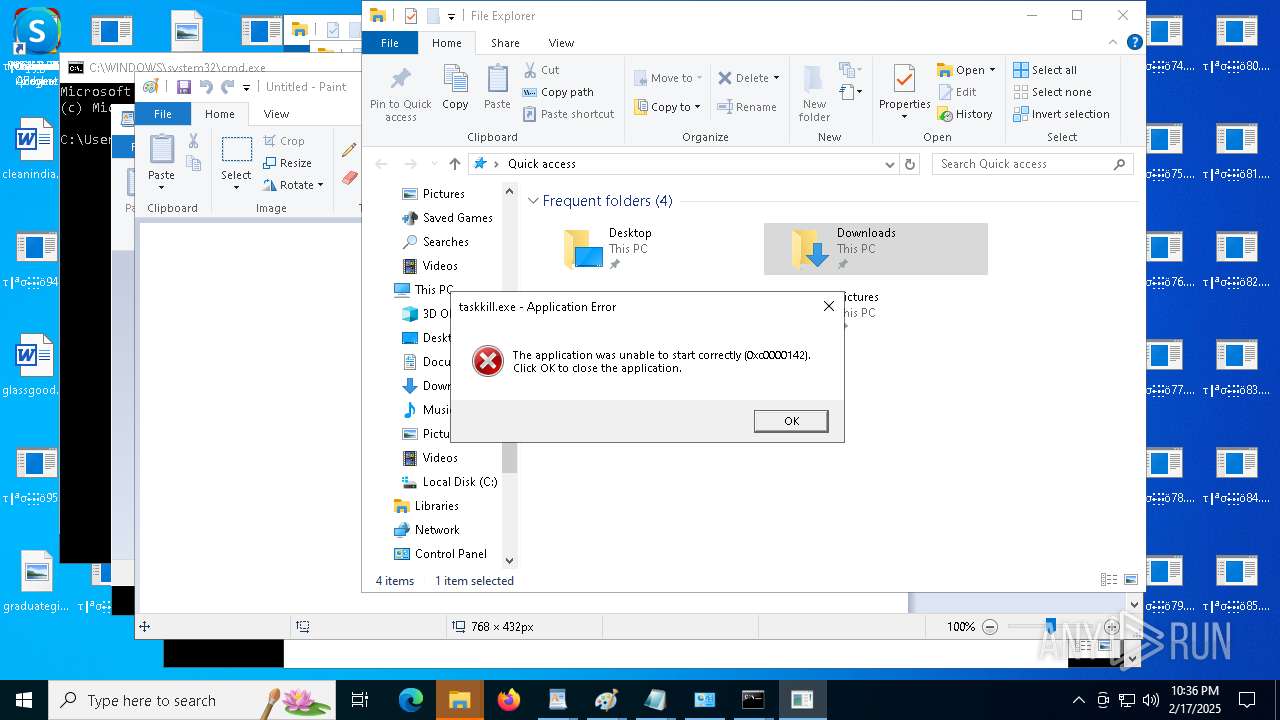
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6600)
Reads security settings of Internet Explorer
- wordpad.exe (PID: 5720)
- StartMenuExperienceHost.exe (PID: 6560)
- wordpad.exe (PID: 1596)
- wordpad.exe (PID: 1820)
- wordpad.exe (PID: 5864)
- wordpad.exe (PID: 364)
Application launched itself
- cmd.exe (PID: 6600)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6600)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 6560)
- SearchApp.exe (PID: 4588)
Sets XML DOM element text (SCRIPT)
- wordpad.exe (PID: 5720)
- wordpad.exe (PID: 1596)
- wordpad.exe (PID: 1820)
- wordpad.exe (PID: 364)
- wordpad.exe (PID: 5864)
INFO
Reads security settings of Internet Explorer
- write.exe (PID: 6188)
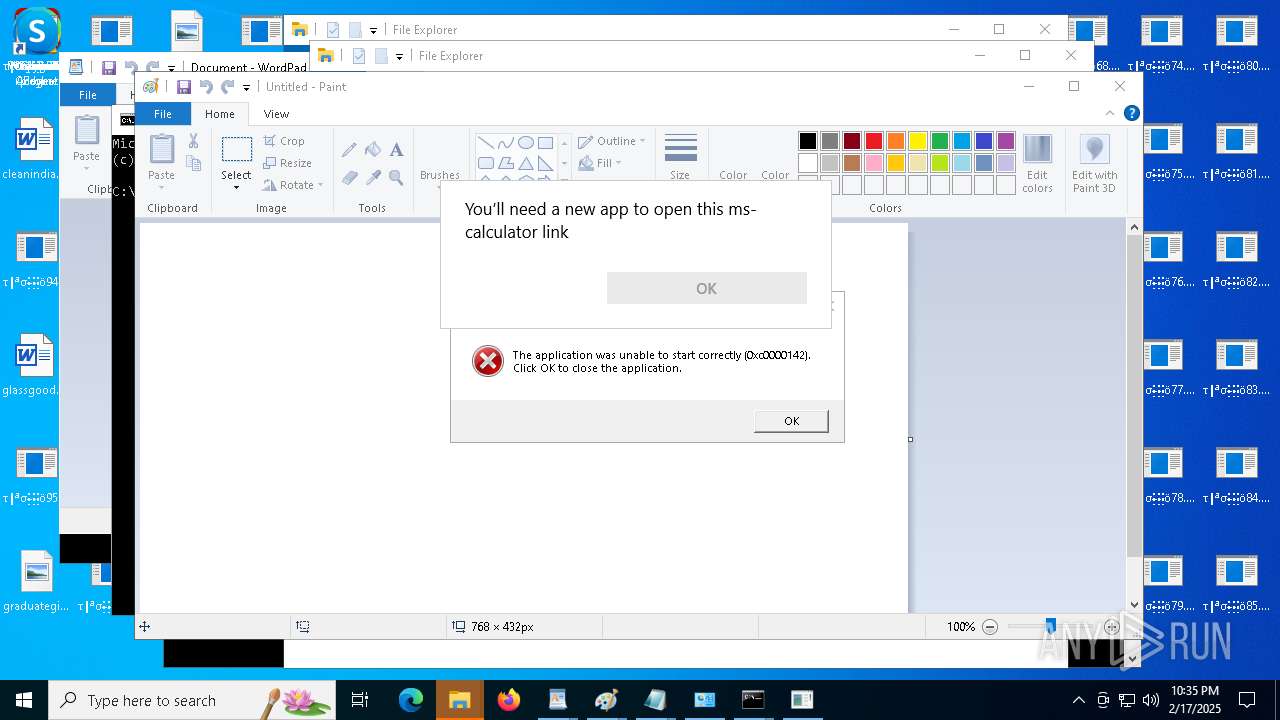
- calc.exe (PID: 7140)
- OpenWith.exe (PID: 6404)
- write.exe (PID: 5244)
- explorer.exe (PID: 2356)
- OpenWith.exe (PID: 6720)
- explorer.exe (PID: 2076)
- calc.exe (PID: 5600)
- OpenWith.exe (PID: 5240)
- OpenWith.exe (PID: 5216)
- calc.exe (PID: 936)
- write.exe (PID: 5348)
- write.exe (PID: 2736)
- calc.exe (PID: 4076)
- OpenWith.exe (PID: 4708)
- calc.exe (PID: 3176)
- write.exe (PID: 5084)
Reads Environment values
- wordpad.exe (PID: 5720)
- SearchApp.exe (PID: 4588)
- wordpad.exe (PID: 1596)
- wordpad.exe (PID: 1820)
- wordpad.exe (PID: 5864)
- wordpad.exe (PID: 364)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 6560)
- SearchApp.exe (PID: 4588)
Reads the computer name
- SearchApp.exe (PID: 4588)
- wordpad.exe (PID: 5720)
- StartMenuExperienceHost.exe (PID: 6560)
- wordpad.exe (PID: 1596)
- wordpad.exe (PID: 364)
- wordpad.exe (PID: 5864)
- wordpad.exe (PID: 1820)
Checks supported languages
- SearchApp.exe (PID: 4588)
- StartMenuExperienceHost.exe (PID: 6560)
- wordpad.exe (PID: 1596)
- wordpad.exe (PID: 1820)
- wordpad.exe (PID: 5720)
- wordpad.exe (PID: 364)
- wordpad.exe (PID: 5864)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 4588)
Checks proxy server information
- SearchApp.exe (PID: 4588)
- explorer.exe (PID: 2076)
Creates files or folders in the user directory
- explorer.exe (PID: 2076)
Reads the software policy settings
- SearchApp.exe (PID: 4588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
205
Monitored processes
88
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Program Files\Windows NT\Accessories\wordpad.exe" | C:\Program Files\Windows NT\Accessories\wordpad.exe | — | write.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Wordpad Application Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | explorer | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 908 | mspaint | C:\Windows\System32\mspaint.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | calc | C:\Windows\System32\calc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | taskkill /f /im conhost.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 3221225794 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | control | C:\Windows\System32\control.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | mspaint | C:\Windows\System32\mspaint.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | explorer | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Windows NT\Accessories\wordpad.exe" | C:\Program Files\Windows NT\Accessories\wordpad.exe | — | write.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Wordpad Application Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1808 | taskkill /f /im dllhost.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 3221225794 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 425
Read events
67 046
Write events
337
Delete events
42
Modification events
| (PID) Process: | (7164) control.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309DF1040000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6404) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6404) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6404) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5208) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5208) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 00000000040000000E00000003000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5208) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (2076) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | TraySearchBoxVisible |
Value: 0 | |||
| (PID) Process: | (2076) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | TraySearchBoxVisibleOnAnyMonitor |
Value: 0 | |||
| (PID) Process: | (2076) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | TraySearchBoxVisible |
Value: 1 | |||
Executable files
4
Suspicious files
35
Text files
298
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔1.exe | text | |
MD5:4647B911ED41412EAC7B52057E66F6B0 | SHA256:EBF81FB7A1C18EF2AE8E7B5805F0F89153793C93F9FBD289181FC9EBF25ACDCD | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔8.exe | text | |
MD5:71FF5ACA95779907300C2FA33098CA43 | SHA256:ADE3BDDA02650306B6AD86BAB1DDCFEEC5DE5E2DAB45A5474D8FDED812B357C5 | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔7.exe | text | |
MD5:558140ED623E3BC0BBEB72B0106ADBB4 | SHA256:0ACF742A6EF5BA9ADA80B0673C3ABD62B6ED176364A15E57D415469E93CA7596 | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔18.exe | text | |
MD5:74A7253CA91E3F64CF4805649E9C10F6 | SHA256:96177C1675A91EAA8C735F354F44A2C531CC2E7A3AF36EDF462FE44E80020D5E | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔17.exe | text | |
MD5:313010E2BEA51C1A8A9DD330635D53C3 | SHA256:9E76BC5E7EF96E3136397FE9488C358F383CB59887FD9DE90868CF87D049DB80 | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔11.exe | text | |
MD5:BD5EEB425A04F09EDE815415DF7E71BF | SHA256:BD1F3EDB5C347D1715DAAFDD003F96CB1262E24C0986BEA3D7EB600EF8019A6A | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔5.exe | text | |
MD5:458C23E77F658D35A2AB50F261EFF309 | SHA256:E2355C8CD8CDD2E374EC6F32B91A6798EF379C6649A5242A7930F789CFE8E809 | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔19.exe | text | |
MD5:8852A2BCB49577A6DF57FCEAACDEDADD | SHA256:182A30AC2C029744144BC0CA048046DC53198204B8EC1C41ABA6F98F1A824D42 | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔16.exe | text | |
MD5:247D39CBCD5B44696072C33E3A4B0ECE | SHA256:8E1C0A8BD039D2307D7EB61BF83687A8D180E6A6101001841312D849A5A37280 | |||
| 6600 | cmd.exe | C:\Users\admin\Desktop\约尔12.exe | text | |
MD5:9EF19663574A05A2E5759515A4F64132 | SHA256:FD515D8E5313E0FB758A3AC7EC231A6472443158978102A1F61A686550D394C5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
19
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.126.37.128:443 | https://www.bing.com/rb/16/jnc,nj/0SrfjVbd4BJYe5wzcCR3l-BPV6c.js?bu=Dis0e4gBjwGSAYUBfoIBxwHKATS-Ac0B&or=w | unknown | binary | 21.5 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.154:443 | https://www.bing.com/rb/19/cir3,ortl,cc,nc/FgBbpIj0thGWZOh_xFnM9i4O7ek.css?bu=C9oJ6wPsBLYKmwmFCY0HbW1tbQ&or=w | unknown | text | 19.8 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.123:443 | https://www.bing.com/rb/6k/cir3,ortl,cc,nc/2u1i5bXJCKdk4jOb70d5CjAHxg4.css?bu=M8cKwQrNCsEKsQvBCrcLwQrBCsEKwgvBCskLwQrPC8EK1QvBCtsLwQrfCsEK5QrBCtkKwQrBCqgLwQr0CsEK-grBCu4KwQqAC4oLjQvBCsEKpQuTC8EKmQucC8EKhwzBCuELwQrADA&or=w | unknown | text | 444 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.128:443 | https://www.bing.com/rb/6k/ortl,cc,nc/fvNdnrKxhhxDQUEi09cCaSWpzzE.css?bu=Ca0MwQqyDMEKtgzBCsEKwQrBCg&or=w | unknown | text | 428 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.123:443 | https://www.bing.com/rb/3D/ortl,cc,nc/VbCw90KbfciOAAXUwrx6Ers36VI.css?bu=A4gCjAKPAg&or=w | unknown | text | 15.5 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.144:443 | https://www.bing.com/rp/1giEXriiR3EOVRN7C9sblV6Vn-s.br.js | unknown | binary | 300 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.123:443 | https://www.bing.com/rb/6k/ortl,cc,nc/QNBBNqWD9F_Blep-UqQSqnMp-FI.css?bu=AcEK&or=w | unknown | text | 6 b | whitelisted |
— | — | GET | 200 | 104.126.37.176:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Init | unknown | html | 125 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.145:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4588 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |