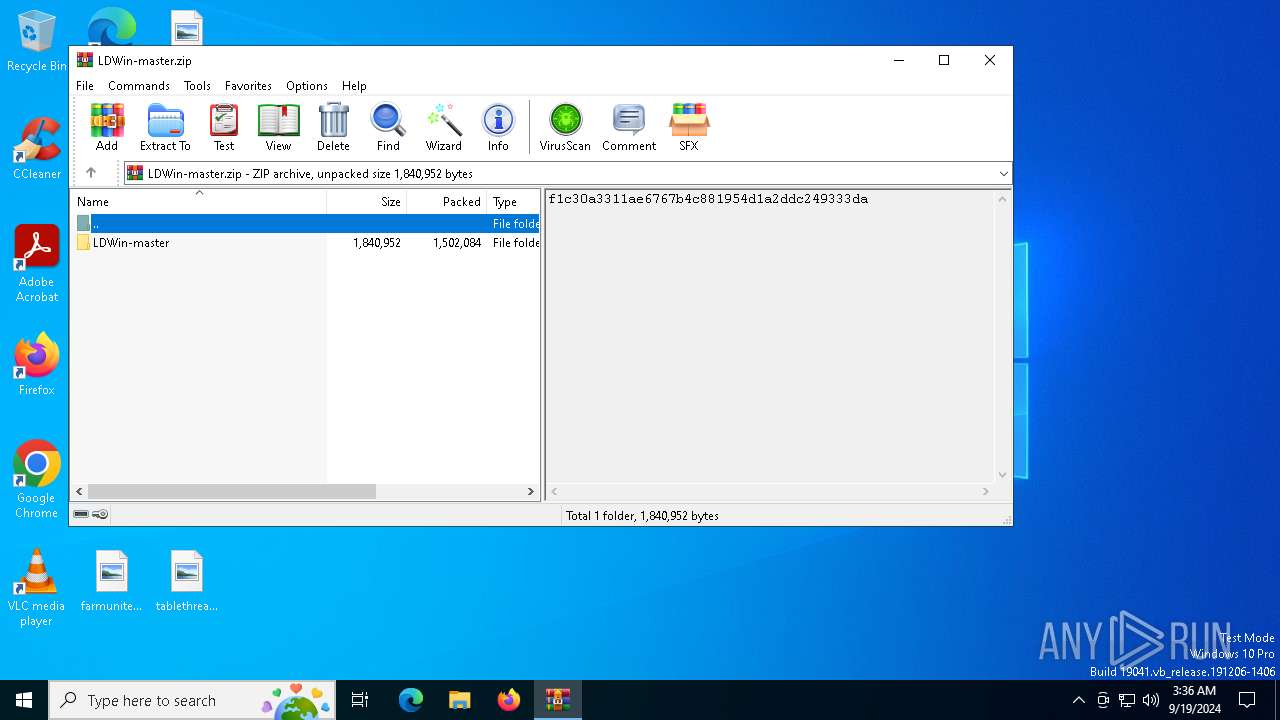
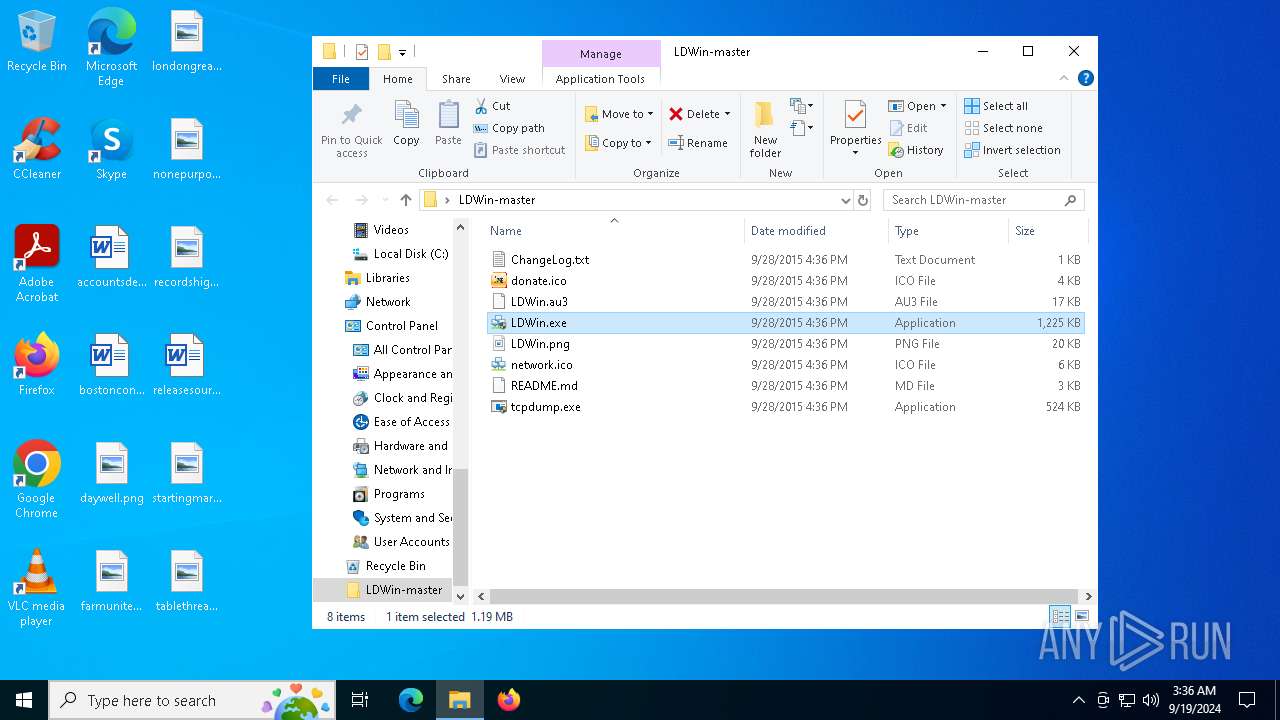
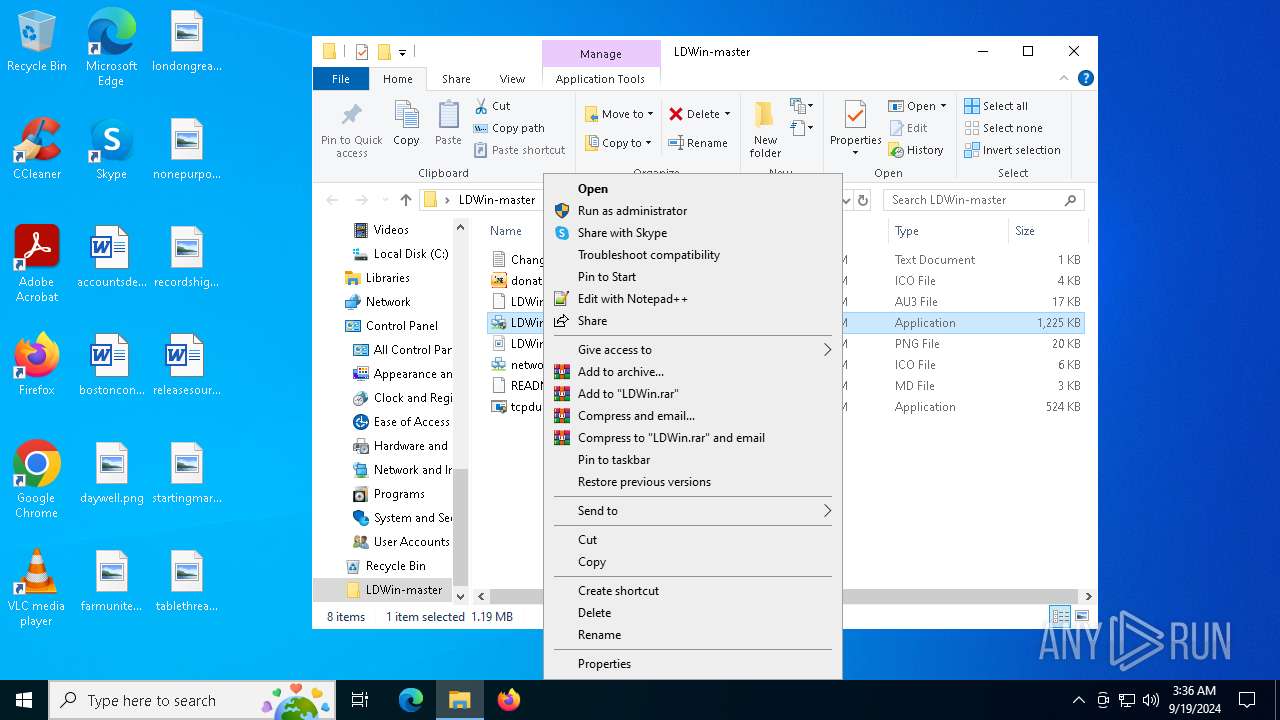
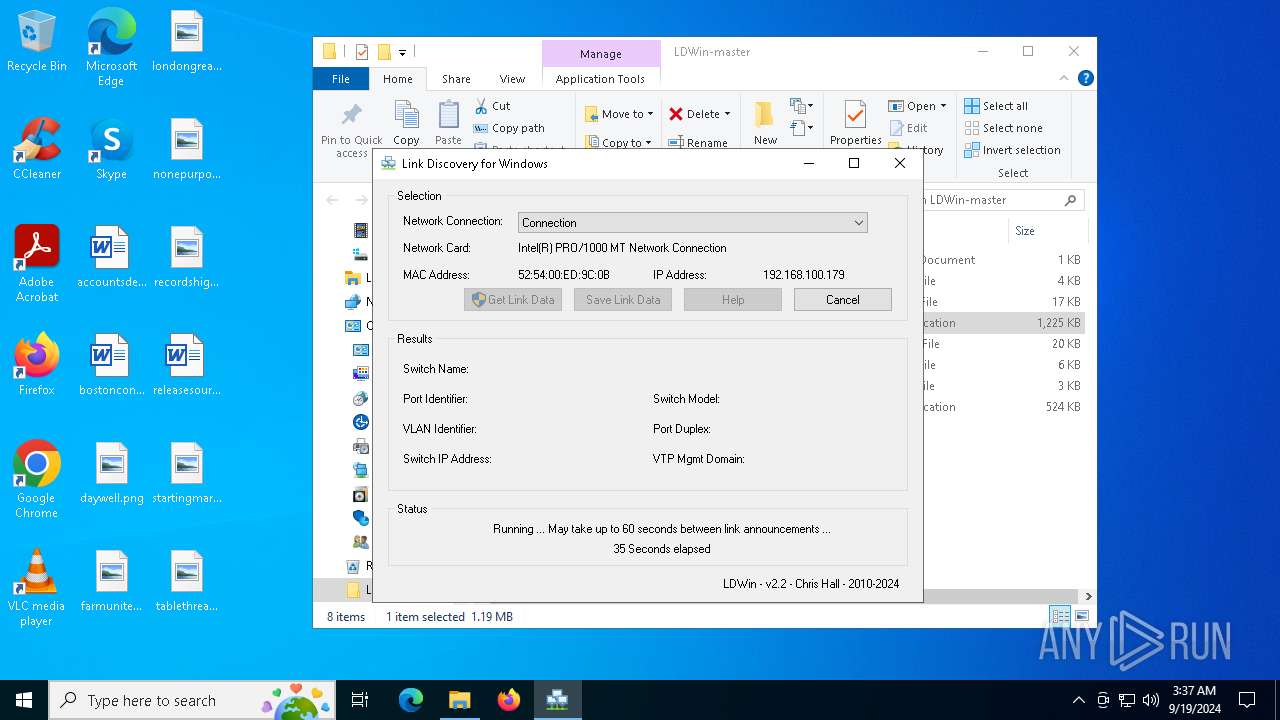
| File name: | LDWin-master.zip |
| Full analysis: | https://app.any.run/tasks/e2f65762-2039-4640-97a0-78bb161b38f9 |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2024, 03:36:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 06450E72DB376D2F2346934B11C98D5E |
| SHA1: | ACF61959F4364BD3A782ED9E0D8B48FB7FE86E67 |
| SHA256: | DFFFC44D57A41E761C59990ABD784244065266CB14E6C61379CB17A176C0F550 |
| SSDEEP: | 49152:V+AKapfAkTO1RDLssFZTfsOBmy5vtoszVwf3AduYhOSvpQuIZ5bAQYL0qeZrc56A:VMYO1BRZTfslcvLzKPALvpQuw5lnRc8A |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- LDWin.exe (PID: 4680)
- LDWin.exe (PID: 6628)
- tcpdump.exe (PID: 6428)
Drops a system driver (possible attempt to evade defenses)
- tcpdump.exe (PID: 6428)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5060)
The process uses AutoIt
- LDWin.exe (PID: 4680)
UPX packer has been detected
- tcpdump.exe (PID: 6428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2015:09:28 09:36:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | LDWin-master/ |
Total processes
142
Monitored processes
11
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3936 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\tcpdump.exe -i \Device\{D950CA8D-448E-4CA2-89DE-A65A1AC2B2A6} -nn -v -s 1500 -c 1 (ether[12:2]==0x88cc or ether[20:2]==0x2000) >%temp%\Data_Out.txt | C:\Windows\SysWOW64\cmd.exe | — | LDWin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
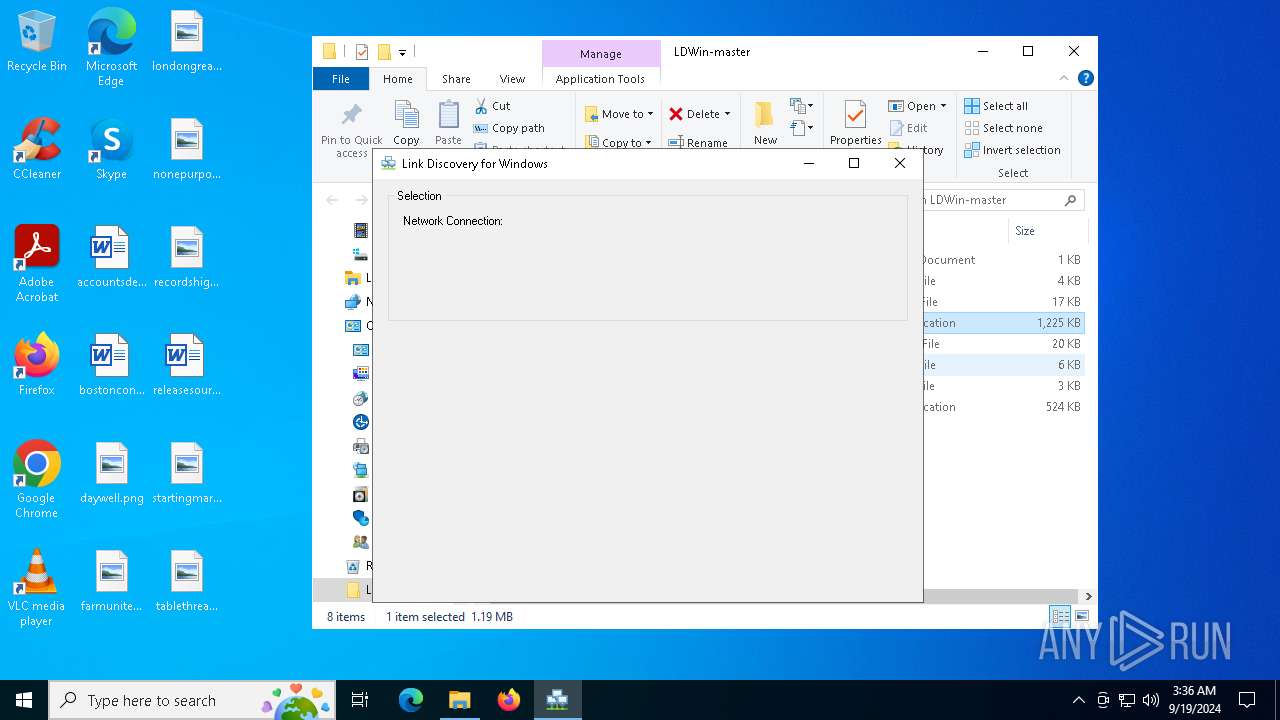
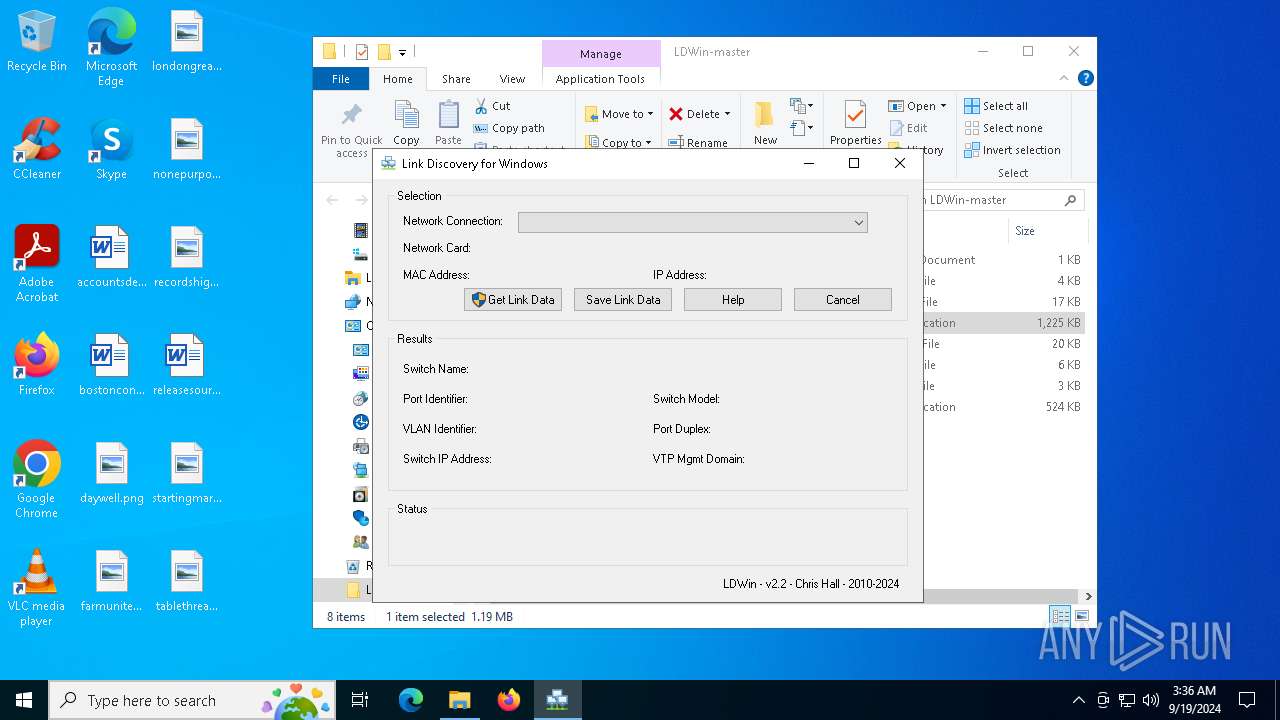
| 4680 | "C:\Users\admin\Desktop\LDWin-master\LDWin.exe" | C:\Users\admin\Desktop\LDWin-master\LDWin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Link Discovery for Windows Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
| 4824 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5060 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\LDWin-master.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6312 | "C:\Users\admin\Desktop\LDWin-master\LDWin.exe" | C:\Users\admin\Desktop\LDWin-master\LDWin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Link Discovery for Windows Exit code: 3221226540 Version: 2.2.0.0 Modules
| |||||||||||||||
| 6428 | C:\Users\admin\AppData\Local\Temp\tcpdump.exe -i \Device\{D950CA8D-448E-4CA2-89DE-A65A1AC2B2A6} -nn -v -s 1500 -c 1 (ether[12:2]==0x88cc or ether[20:2]==0x2000) | C:\Users\admin\AppData\Local\Temp\tcpdump.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6600 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6612 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 221
Read events
3 204
Write events
17
Delete events
0
Modification events
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\LDWin-master.zip | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5060) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
8
Suspicious files
2
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5060.28222\LDWin-master\LDWin.au3 | text | |
MD5:BED7FFCB63CE53C7786A98771EA88DD7 | SHA256:28C7BF335706BD7B73586732240BBD9657B834B5762D8DB9A38700DA8996D266 | |||
| 6628 | LDWin.exe | C:\Users\admin\AppData\Local\Temp\autF65F.tmp | executable | |
MD5:4AF745D8FB1CE63BC97CD7874EEDB613 | SHA256:99CFEFAF942BA679D08A17C07ABDBAFE99F8C156E5DB93A2F52F5E277830BB94 | |||
| 6628 | LDWin.exe | C:\Users\admin\AppData\Local\Temp\tcpdump.exe | executable | |
MD5:4AF745D8FB1CE63BC97CD7874EEDB613 | SHA256:99CFEFAF942BA679D08A17C07ABDBAFE99F8C156E5DB93A2F52F5E277830BB94 | |||
| 6628 | LDWin.exe | C:\Users\admin\AppData\Local\Temp\LinkData.txt | text | |
MD5:4C940878A60396E052552885FB4646E1 | SHA256:59E72A7215B8516348D75BD9EA5DEE4B21D08AA68E1964B18490C4350BAC17E4 | |||
| 4680 | LDWin.exe | C:\Users\admin\AppData\Local\Temp\aut137C.tmp | executable | |
MD5:4AF745D8FB1CE63BC97CD7874EEDB613 | SHA256:99CFEFAF942BA679D08A17C07ABDBAFE99F8C156E5DB93A2F52F5E277830BB94 | |||
| 5060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5060.28222\LDWin-master\LDWin.png | image | |
MD5:9EDD2A08C9848AD0DFA63B99FEE2CE5A | SHA256:601D25432936C8F5A79B05FE562506CF45292EBD09FFCBA063284CB4A2891592 | |||
| 4680 | LDWin.exe | C:\Users\admin\AppData\Local\Temp\tcpdump.exe | executable | |
MD5:4AF745D8FB1CE63BC97CD7874EEDB613 | SHA256:99CFEFAF942BA679D08A17C07ABDBAFE99F8C156E5DB93A2F52F5E277830BB94 | |||
| 5060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5060.28222\LDWin-master\ChangeLog.txt | text | |
MD5:532FB151F65150359D261A4CD1F3167B | SHA256:710A735876617942A5999F7B3A5901D0A4036D9EAB5B9AF61A96BA9CFC658FA0 | |||
| 6628 | LDWin.exe | C:\Users\admin\AppData\Local\Temp\donate.ico | image | |
MD5:56D21E02150175332CB6D343ABADA53E | SHA256:23438154D279704EA70E335861E16B8D1EC930252221383EE70FEADEFAD896DA | |||
| 5060 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5060.28222\LDWin-master\network.ico | image | |
MD5:DE1F2193F035FE51F0586D2C8CEF0664 | SHA256:C8F0A398D3D446532EFD176198D4F12788BBCEEAD9EBEB7A859076549E3320D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2424 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5172 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2424 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
892 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5172 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5744 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.189.173.11:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5172 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5172 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |