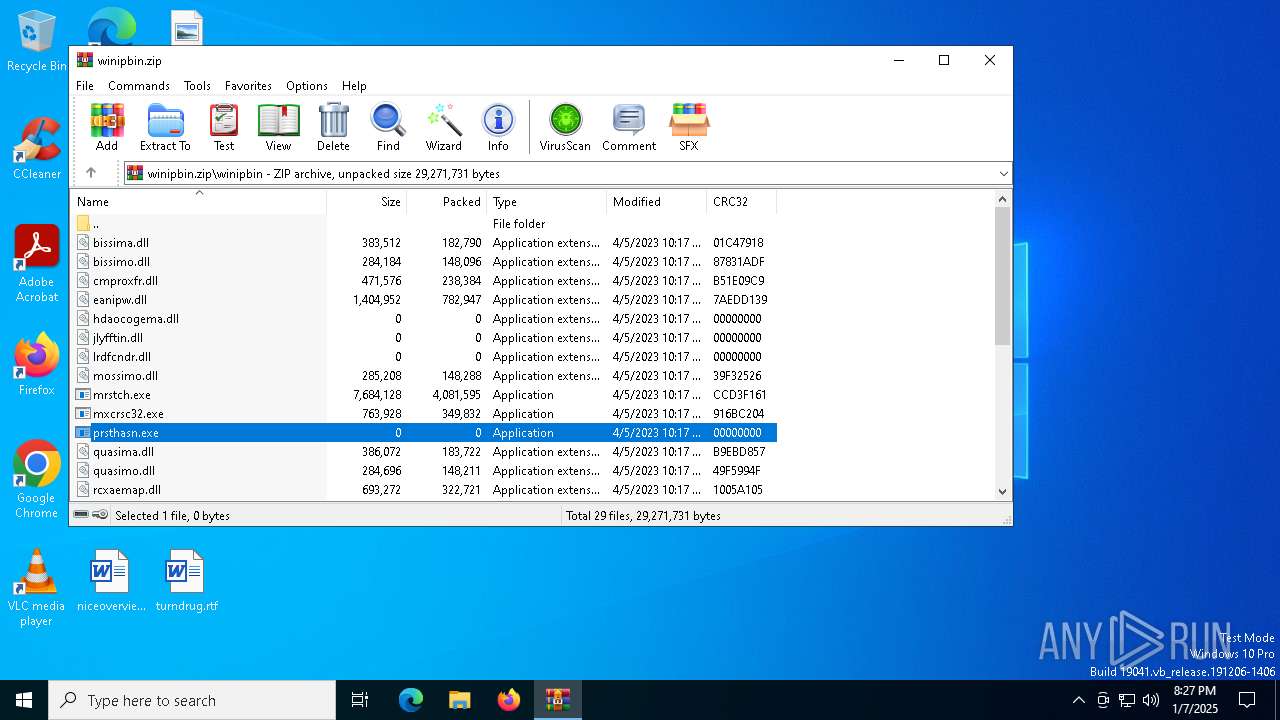
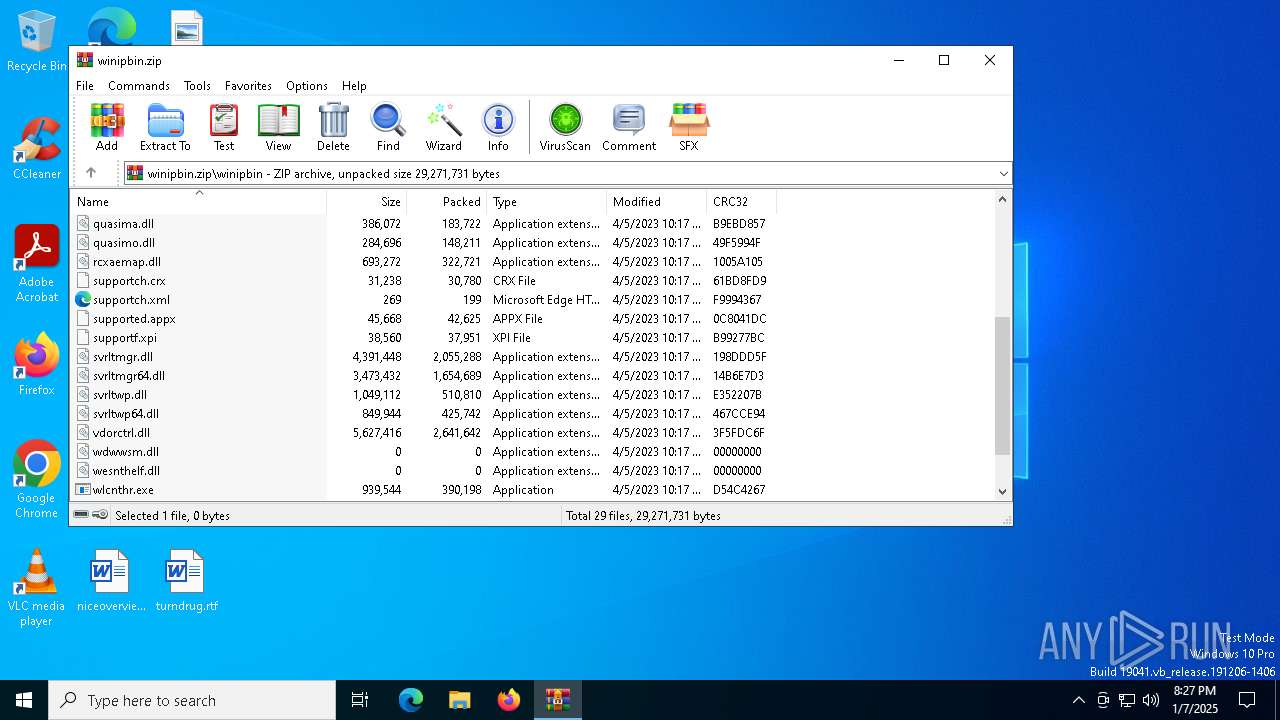
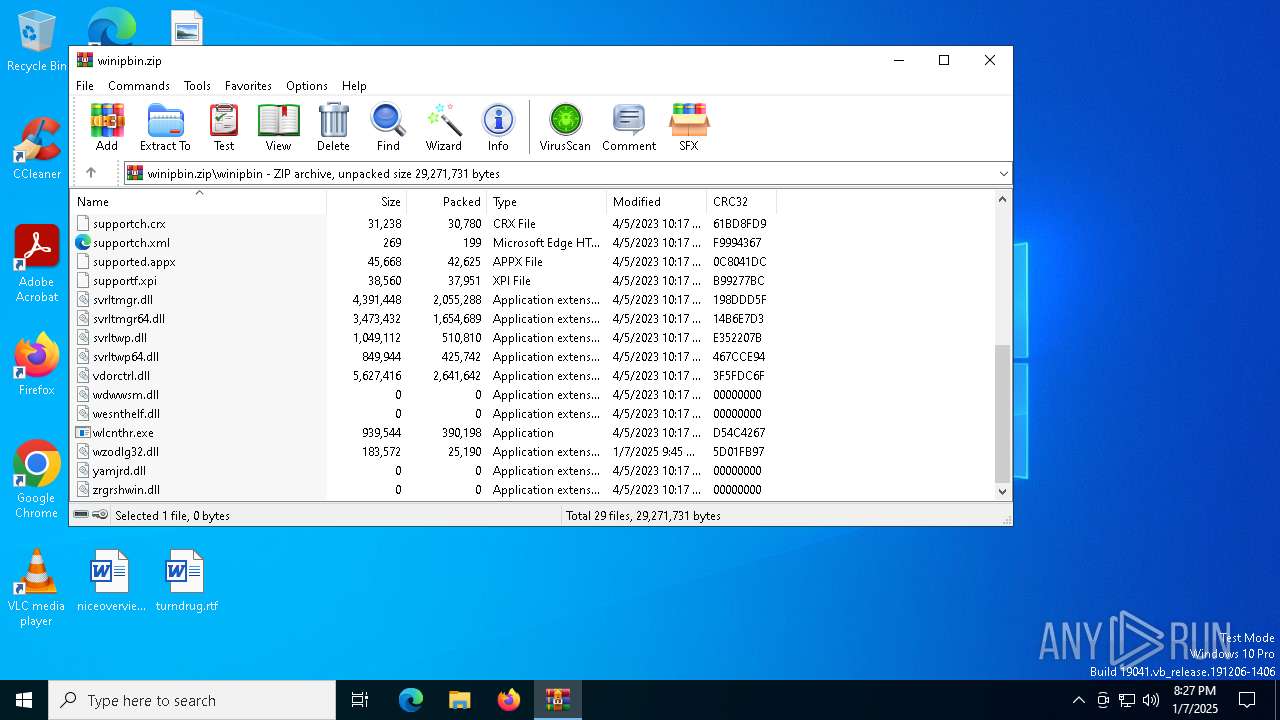
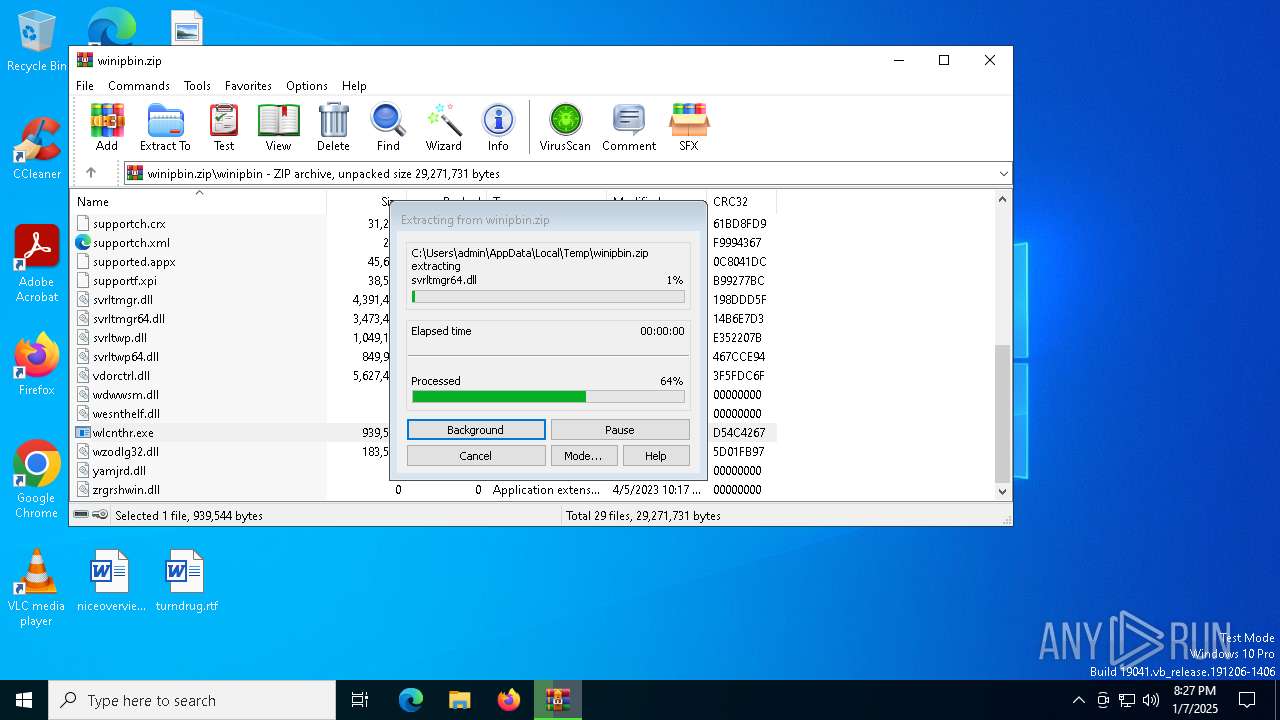
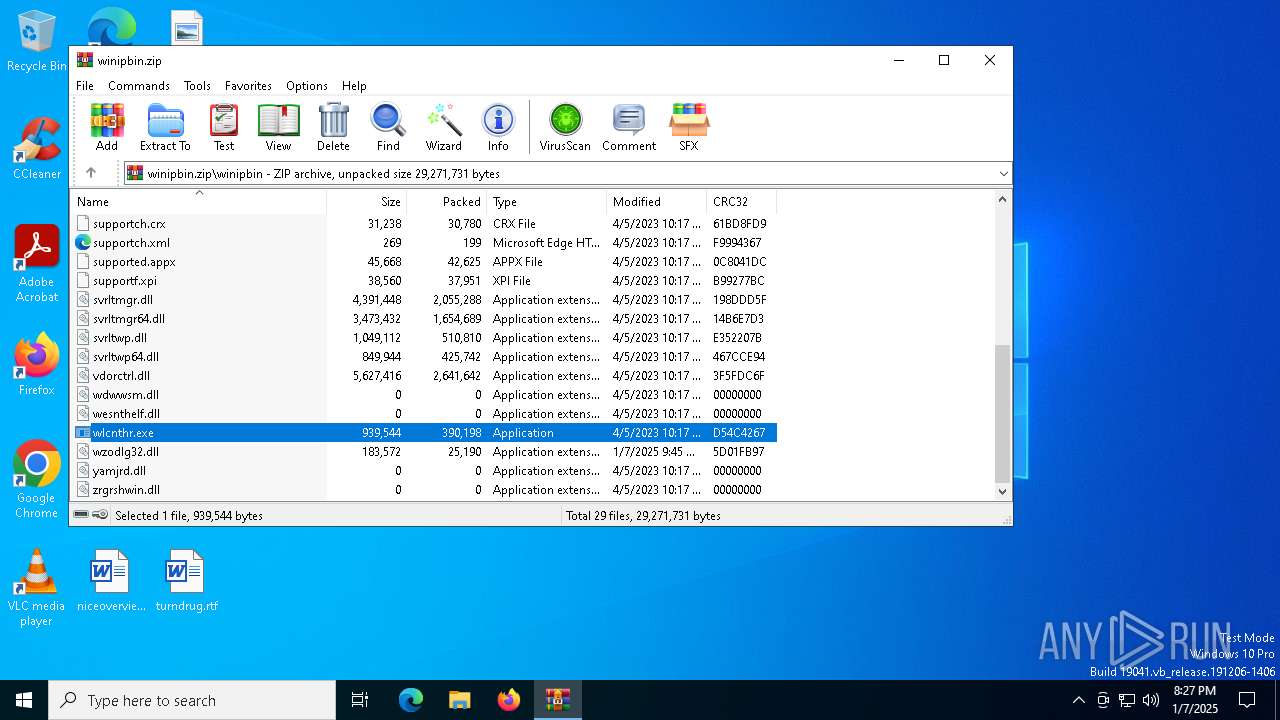
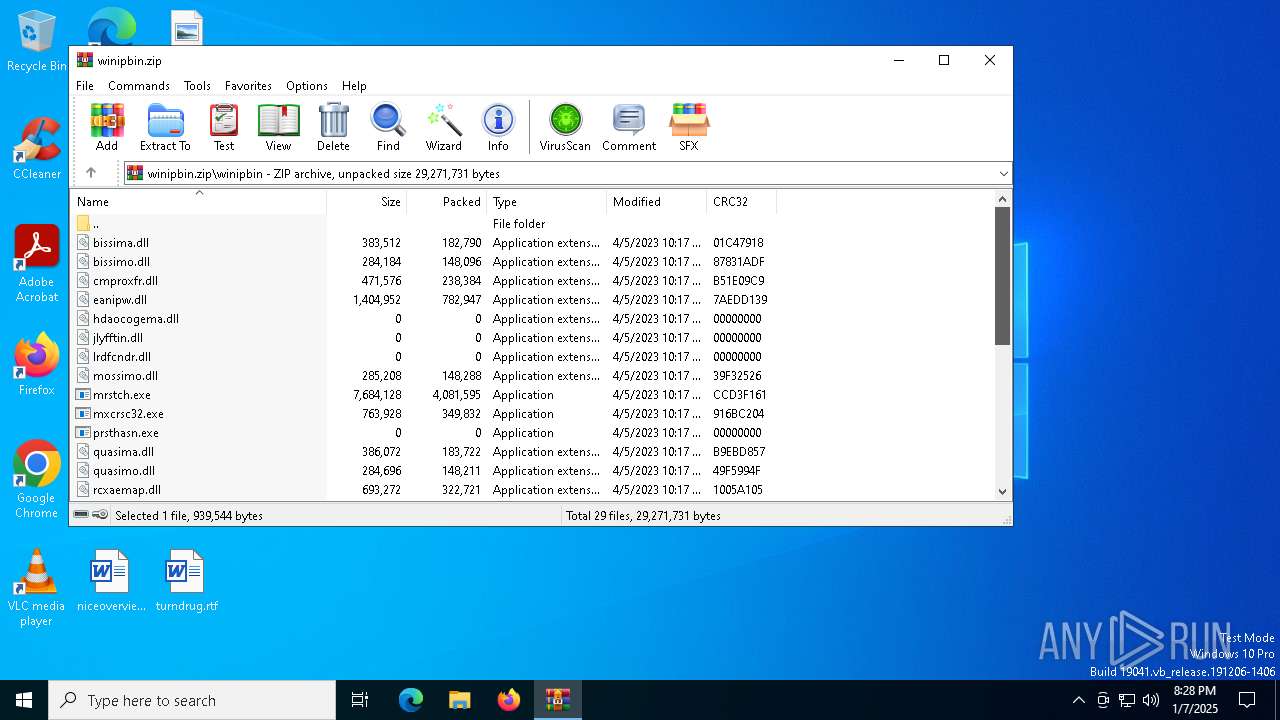
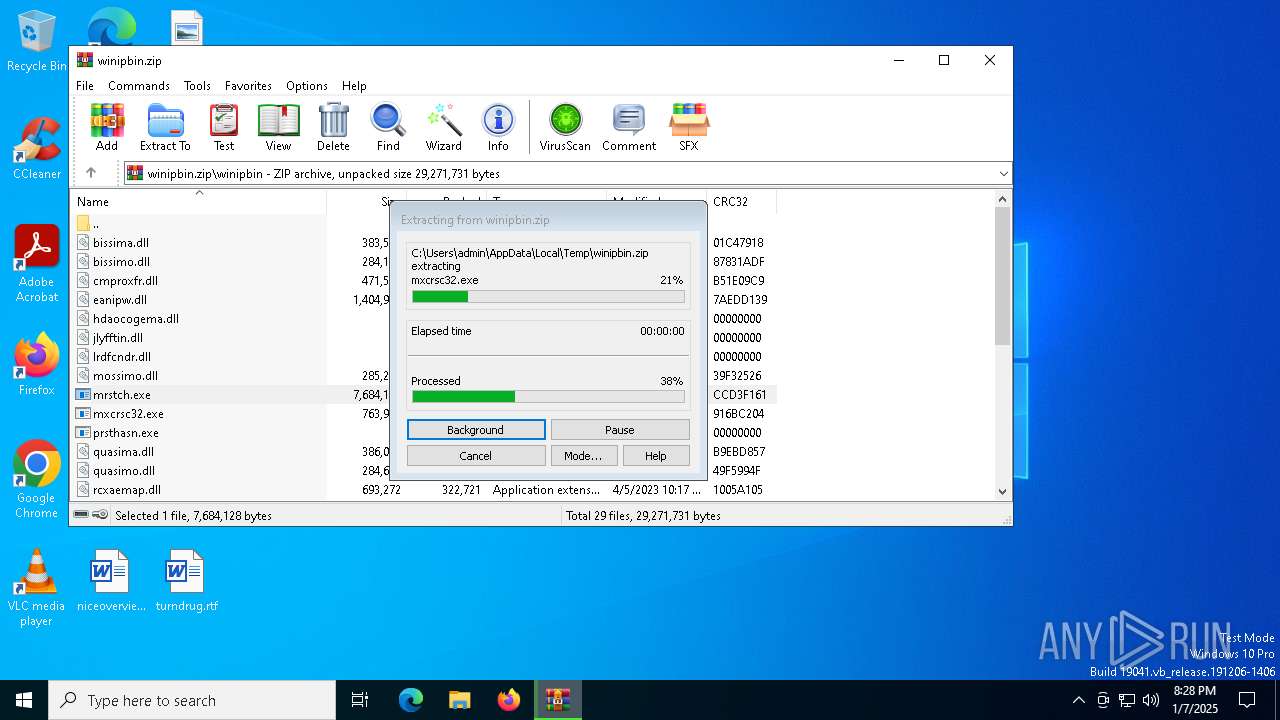
| File name: | winipbin.zip |
| Full analysis: | https://app.any.run/tasks/0461587f-a605-4d40-bbaa-557f8e7fdcc0 |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2025, 20:27:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1DC8A249C00987EC743627428CCAA3FD |
| SHA1: | 1CF0778476D2384F6194438AE7FAC665BFEAE2D7 |
| SHA256: | DFF4D3A86A123F1FE1947075B01E64E869D7618B6A2A90D0B4F3A851D69790F0 |
| SSDEEP: | 98304:gIf2KVm9DJNCaBzHP9rC66Rgp2VWGM0K+D88Jic0g9fLf7cyetbNZC0N8lrp+MJ/:qlvYOwXcPpLxhyK5Xqybsuvm |
MALICIOUS
Generic archive extractor
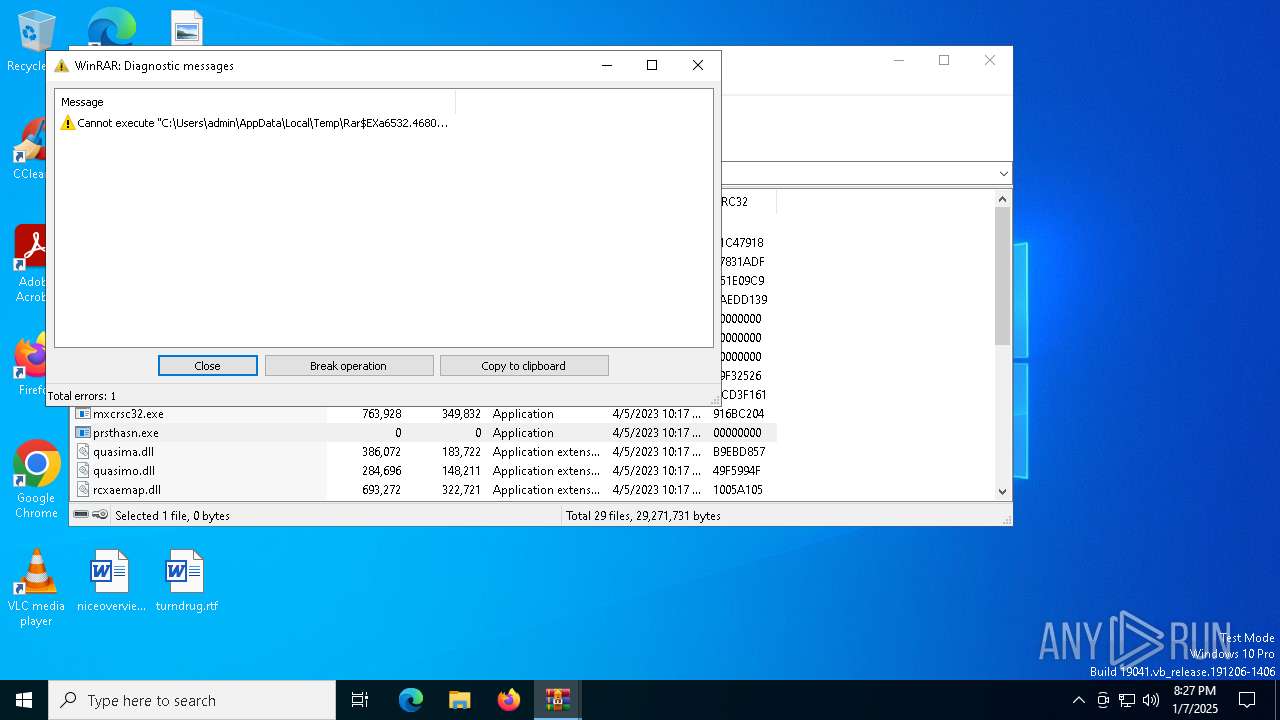
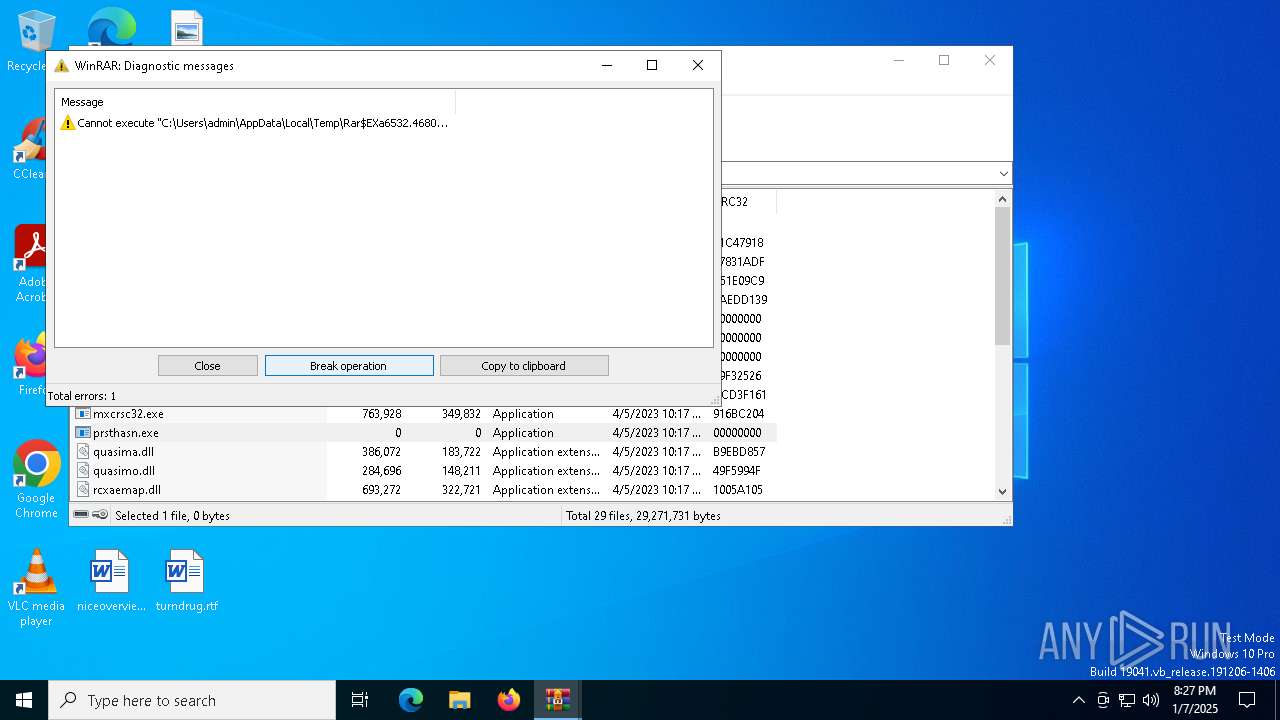
- WinRAR.exe (PID: 6532)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6532)
Executes application which crashes
- wlcnthr.exe (PID: 7064)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6532)
Checks proxy server information
- WerFault.exe (PID: 7148)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6532)
Checks supported languages
- wlcnthr.exe (PID: 7064)
The sample compiled with english language support
- WinRAR.exe (PID: 6532)
Reads the computer name
- mrstch.exe (PID: 3224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:04:05 10:17:32 |
| ZipCRC: | 0x01c47918 |
| ZipCompressedSize: | 182790 |
| ZipUncompressedSize: | 383512 |
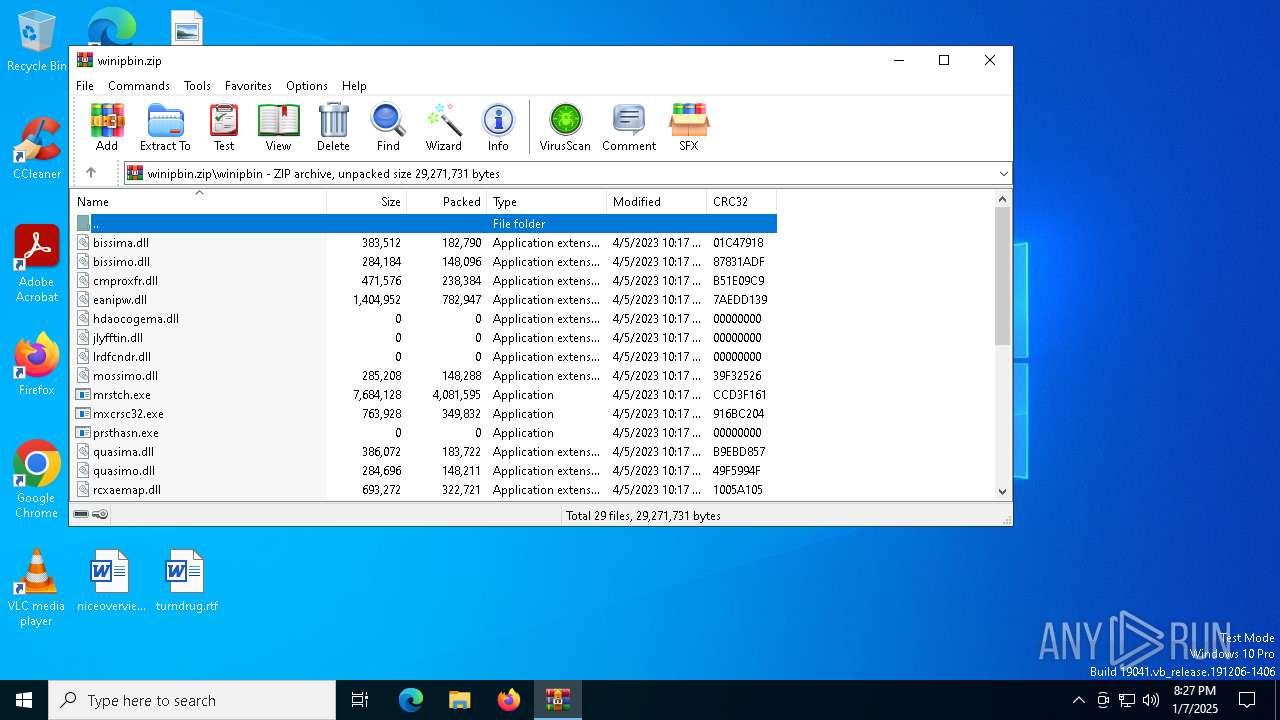
| ZipFileName: | winipbin\bissima.dll |
Total processes
128
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mrstch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.49895\winipbin\mrstch.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.49895\winipbin\mrstch.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 9.0.47350.18 Modules
| |||||||||||||||
| 6096 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.49895\winipbin\mrstch.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.49895\winipbin\mrstch.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 9.0.47350.18 Modules
| |||||||||||||||
| 6532 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\winipbin.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7064 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.48776\winipbin\wlcnthr.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.48776\winipbin\wlcnthr.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 7148 | C:\WINDOWS\system32\WerFault.exe -u -p 7064 -s 500 | C:\Windows\System32\WerFault.exe | wlcnthr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 730
Read events
5 722
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\winipbin.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
48
Suspicious files
9
Text files
8
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\bissimo.dll | executable | |
MD5:5F935191D567DB44F58DE09A3559359C | SHA256:E8E7F11F250C9DBF92AFA8AC699F34A45DA4C5FAEA0A01B1FCE35F56FC06102E | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\cmproxfr.dll | executable | |
MD5:2C56E306FF5D45933D5E1856ED76162C | SHA256:E4023597BB293484257B7A09C93B3FE74E72AFA7B2FB4620D25938764D5A6E07 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\eanipw.dll | executable | |
MD5:1C41FCD0A1723327A24553E48C7D3679 | SHA256:9CC1ABA05B13BC99439A08469F497AD8FC154E1B7A1F879454A57599AA6F373C | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\mrstch.exe | executable | |
MD5:AB2810F57F440BB4F00B26A1E7FFFA4C | SHA256:25E1D50B833BC38F38EDAA8BD8292472279F9A562B6996E623306BC60DF43FEA | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\bissima.dll | executable | |
MD5:3667532C417E81E72C18F97FEDC9C933 | SHA256:57CA746D955E65241340054E5AC0FD92FB971E5A79AC179358C3A4A00BD04173 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\supportch.xml | text | |
MD5:79F507DDED6E083686C5154BB0852E8E | SHA256:BBF25CAA2DBAA401CFD81338939F0C98CAA13773E893298FE890583C2551A282 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\supportf.xpi | compressed | |
MD5:470B443CA89AA8A36D4CE5B651A7E07A | SHA256:5FFEEA42C6B6B723B430C8B690CC8BB563EFF3D1FE371B9D2FA0EAB27FCC5FB1 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\svrltmgr.dll | executable | |
MD5:2CA6C5E723938B6017A46BEBEA76CE8B | SHA256:BC83EA7395C955C7CFEE883E39782CEE3599B1601A9D8C260334A15FCE0715F1 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\supported.appx | compressed | |
MD5:F008BC32FC6BC8A22447D25B701BF27B | SHA256:2F209301BB2DB49A84BD8C22CA101FE9207C9E8E53BF8DCE3987BF1549148F41 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6532.46806\winipbin\svrltwp.dll | executable | |
MD5:BE0FA47190543AE42A448B804D4C9CD3 | SHA256:0E2704FCF02EC561C00AFE1D7DD50675A86CEC89D3E435D58F7203BCE75474A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7148 | WerFault.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6936 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7148 | WerFault.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6936 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1380 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1076 | svchost.exe | 23.56.254.14:443 | go.microsoft.com | Mobile Telecommunications Company | KW | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1380 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |