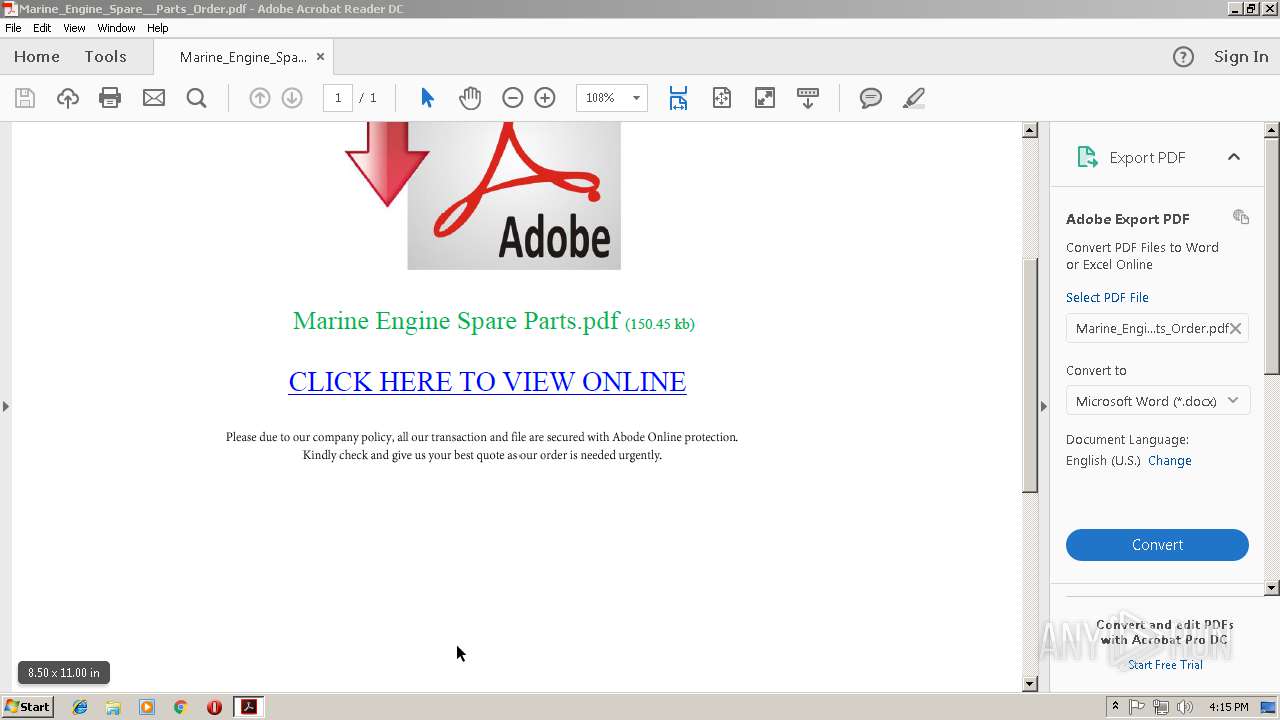
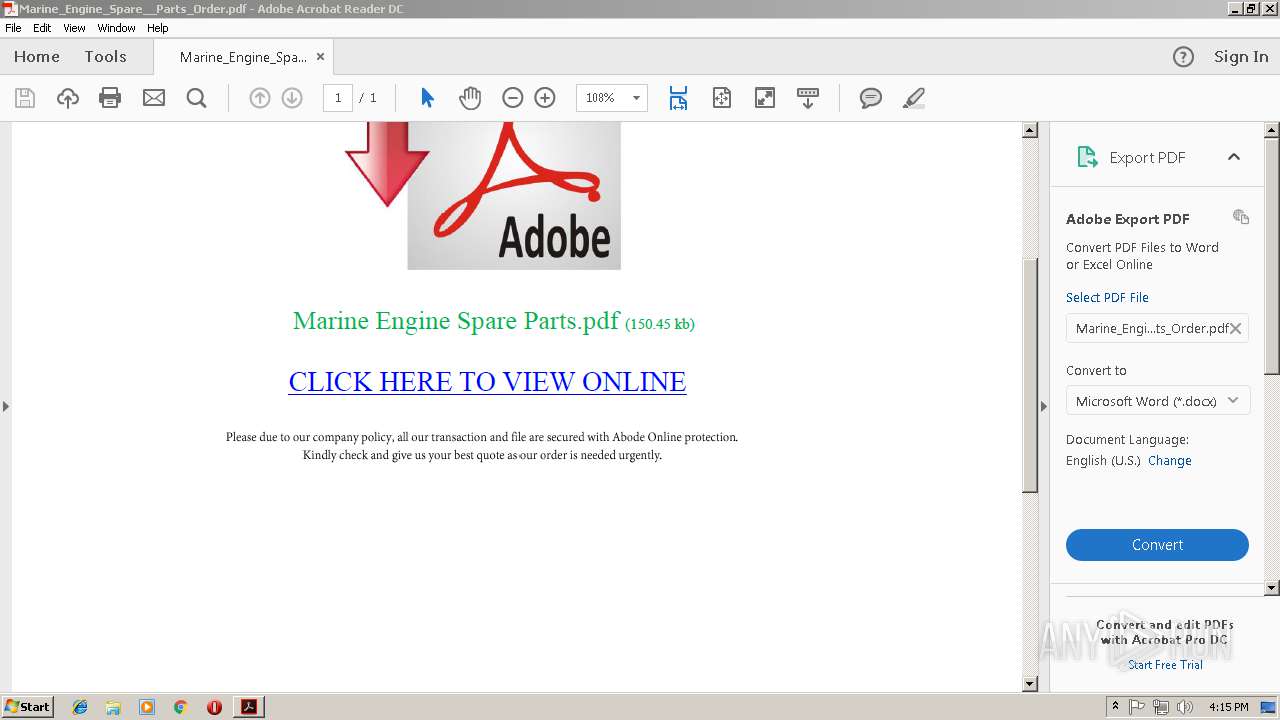
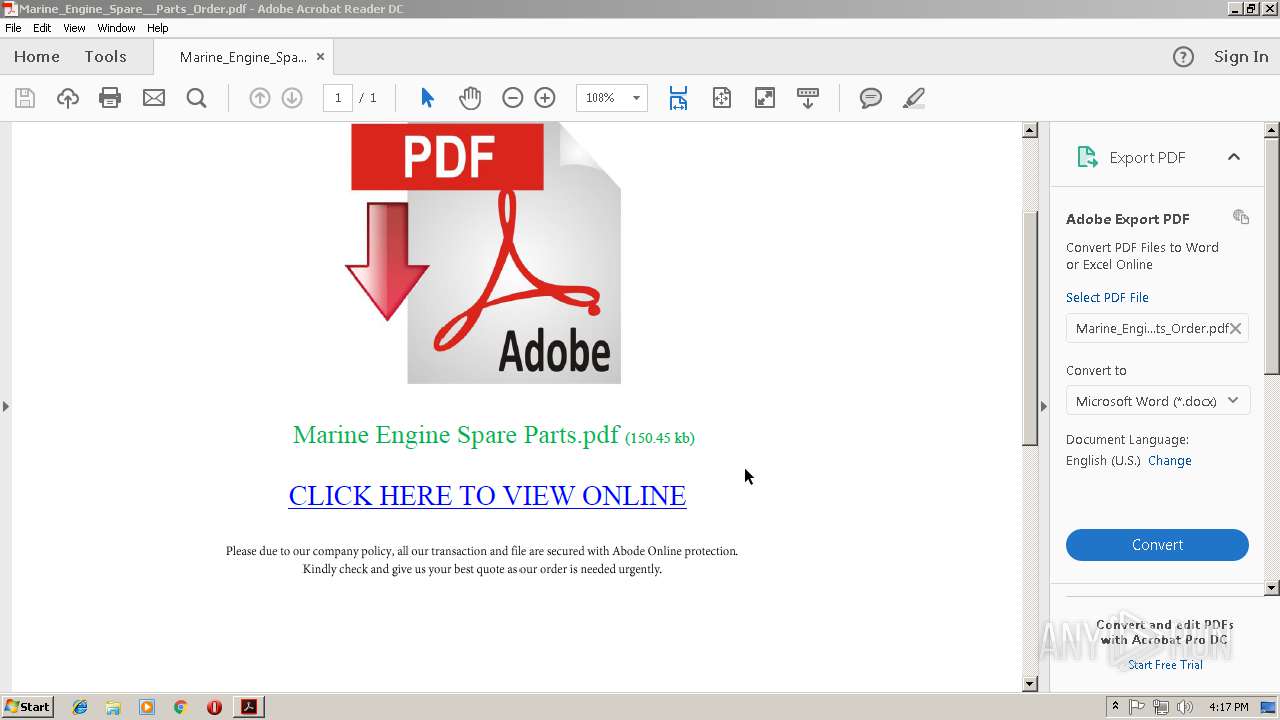
| File name: | Marine_Engine_Spare__Parts_Order.pdf |
| Full analysis: | https://app.any.run/tasks/8017bb5b-efdd-4e77-af0d-c160a5eaa8f6 |
| Verdict: | Malicious activity |
| Analysis date: | November 14, 2018, 16:15:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.5 |
| MD5: | 7C9576123A35749C1699F53A1206577E |
| SHA1: | 7B13CB86D74EE470C2F515F97A046FF26C7B8F56 |
| SHA256: | DFD97878C0BF2E8A43CF8A258D0A31DE0C2718F8564CB93B87D662CE2BD78569 |
| SSDEEP: | 1536:6gxEIegTxq8uK1tbLRTsB91AMW+U7AxRCpQ9X2:6pgFukoBKdAi |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the program directory
- AdobeARM.exe (PID: 2232)
INFO
Application launched itself
- RdrCEF.exe (PID: 2624)
- AcroRd32.exe (PID: 3836)
- chrome.exe (PID: 1352)
- chrome.exe (PID: 2960)
Modifies the open verb of a shell class
- chrome.exe (PID: 1352)
Creates files in the user directory
- AcroRd32.exe (PID: 3836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.5 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Language: | en-US |
| TaggedPDF: | Yes |
| Author: | Online2PDF.com |
| Creator: | Microsoft® Word 2013 |
| CreateDate: | 2018:08:20 01:37:24+01:00 |
| ModifyDate: | 2018:08:20 01:37:24+01:00 |
| Producer: | Microsoft® Word 2013 |
Total processes
53
Monitored processes
22
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2420 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2624.0.1560614162\1709459448" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=928,3827420015357015418,5248945691669305471,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=61BA64AA600BDDD37DE970EA0F65D5C0 --mojo-platform-channel-handle=3660 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=928,3827420015357015418,5248945691669305471,131072 --enable-features=PasswordImport --service-pipe-token=91AD41DF5E2663C87451E835F650BECE --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=91AD41DF5E2663C87451E835F650BECE --renderer-client-id=3 --mojo-platform-channel-handle=1540 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=928,3827420015357015418,5248945691669305471,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4DCD5104F95F93339021A640E033C355 --mojo-platform-channel-handle=520 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=928,3827420015357015418,5248945691669305471,131072 --enable-features=PasswordImport --service-pipe-token=AD53CB3A55D0B5792692155A2A47B5F1 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=AD53CB3A55D0B5792692155A2A47B5F1 --renderer-client-id=5 --mojo-platform-channel-handle=1892 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=928,3827420015357015418,5248945691669305471,131072 --enable-features=PasswordImport --service-pipe-token=B0CBB9CC2DFAF619238B578A655D2E2E --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=B0CBB9CC2DFAF619238B578A655D2E2E --renderer-client-id=4 --mojo-platform-channel-handle=1912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=844,10381581870951208324,11855132716883344306,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=78F2363765D2F0552E8EC7C92B007A95 --mojo-platform-channel-handle=896 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
Total events
880
Read events
682
Write events
191
Delete events
7
Modification events
| (PID) Process: | (2764) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (2764) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (2764) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (3836) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | aFS |
Value: DOS | |||
| (PID) Process: | (3836) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tDIText |
Value: /C/Users/admin/Desktop/Marine_Engine_Spare__Parts_Order.pdf | |||
| (PID) Process: | (3836) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileName |
Value: Marine_Engine_Spare__Parts_Order.pdf | |||
| (PID) Process: | (3836) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileSource |
Value: local | |||
| (PID) Process: | (3836) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sFileAncestors |
Value: 5B5D00 | |||
| (PID) Process: | (3836) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sDI |
Value: 2F432F55736572732F61646D696E2F4465736B746F702F4D6172696E655F456E67696E655F53706172655F5F50617274735F4F726465722E70646600 | |||
| (PID) Process: | (3836) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sDate |
Value: 443A32303138313131343136313532345A00 | |||
Executable files
0
Suspicious files
65
Text files
167
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2764 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1c3622e5-c654-42cc-97ca-6da80dc9b9cd.tmp | — | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\e6e06ecc-5bf2-435f-8659-e67d648bbf6b.tmp | — | |
MD5:— | SHA256:— | |||
| 2764 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
| 1352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF5dd339.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
32
DNS requests
24
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3836 | AcroRd32.exe | GET | 304 | 2.16.186.41:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
3836 | AcroRd32.exe | GET | 304 | 2.16.186.41:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
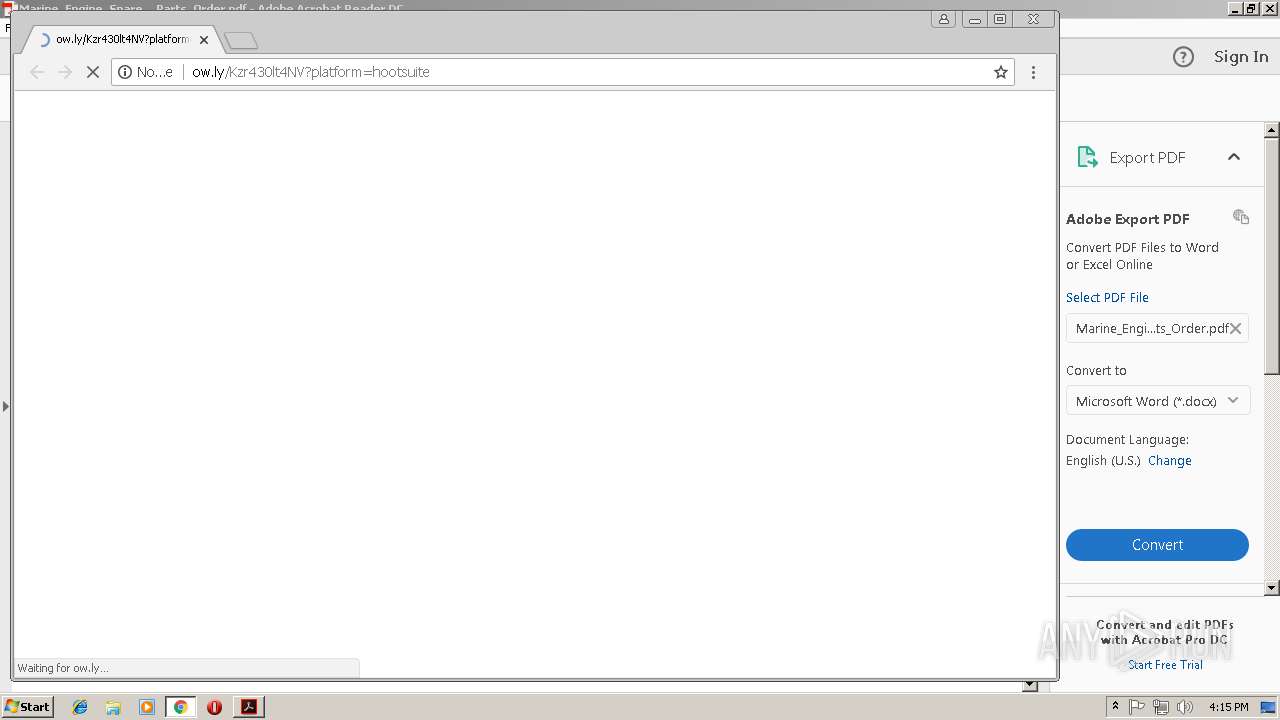
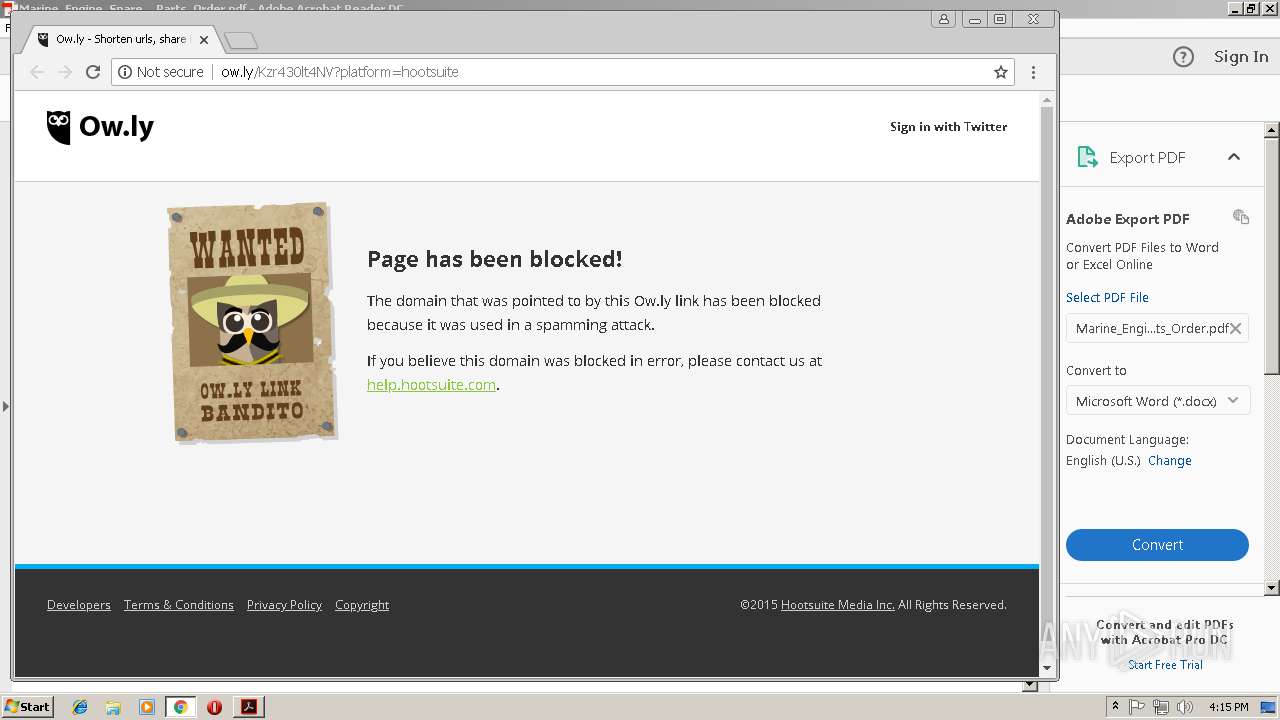
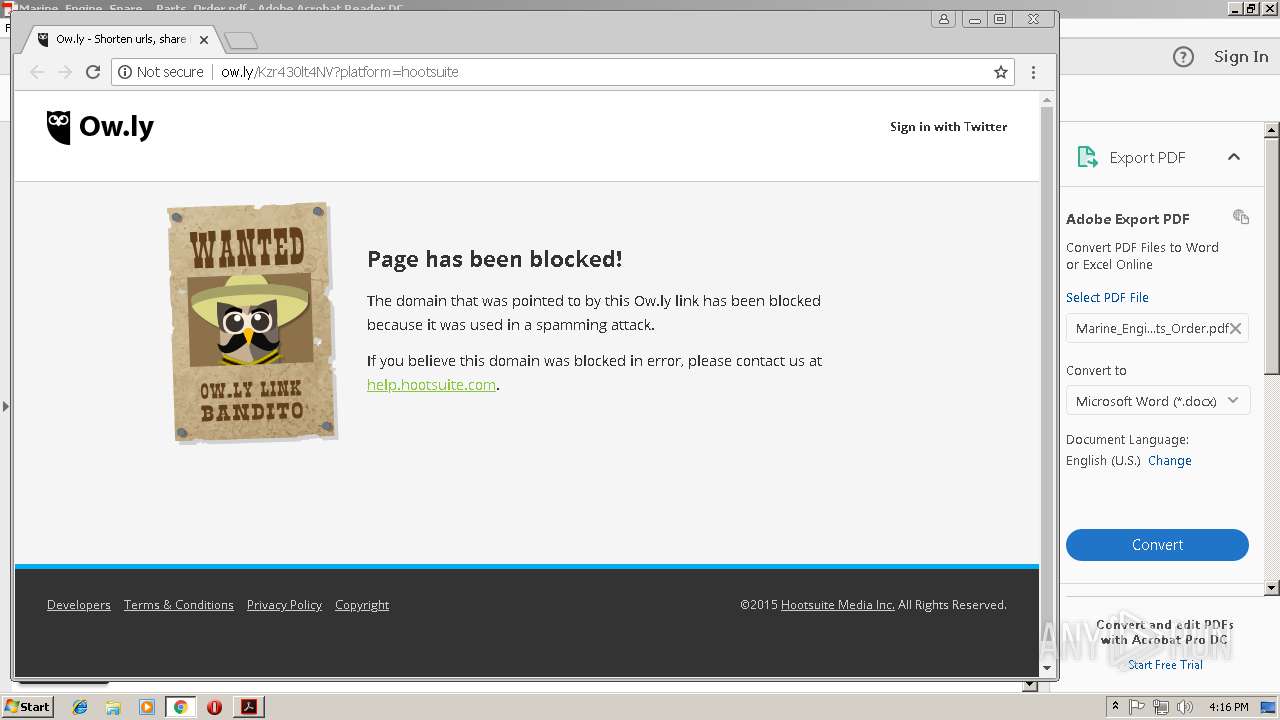
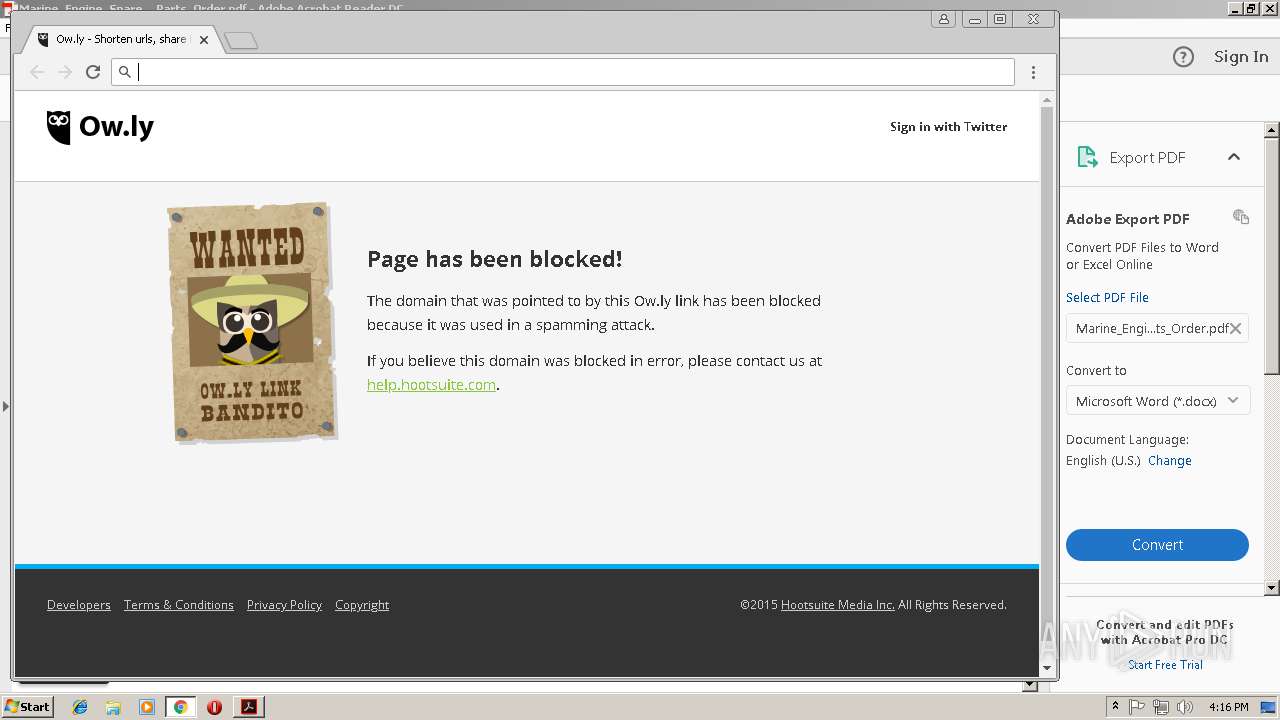
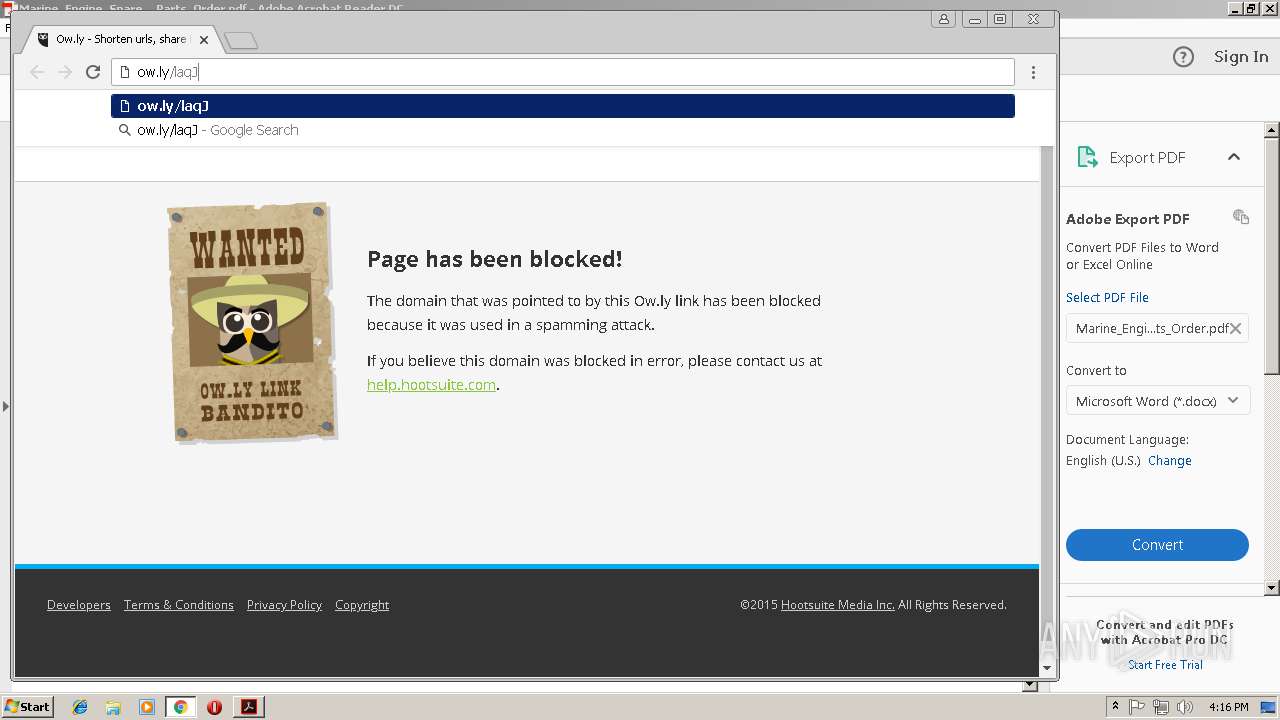
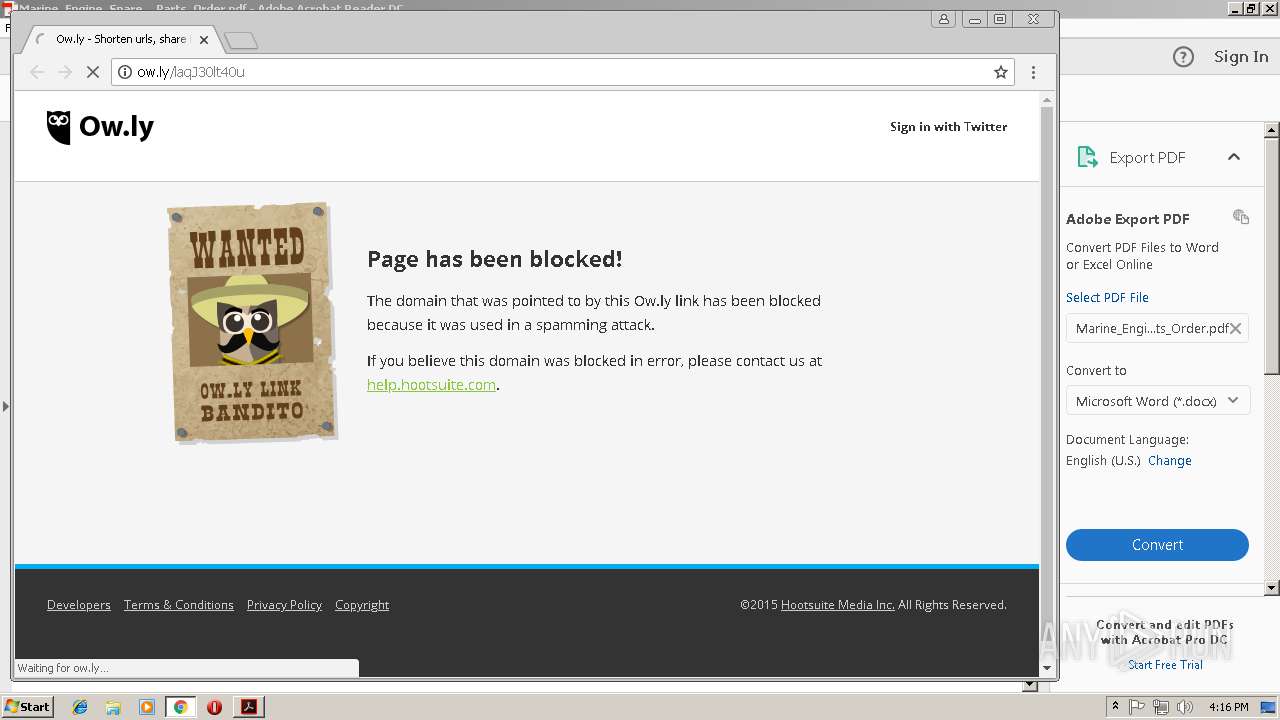
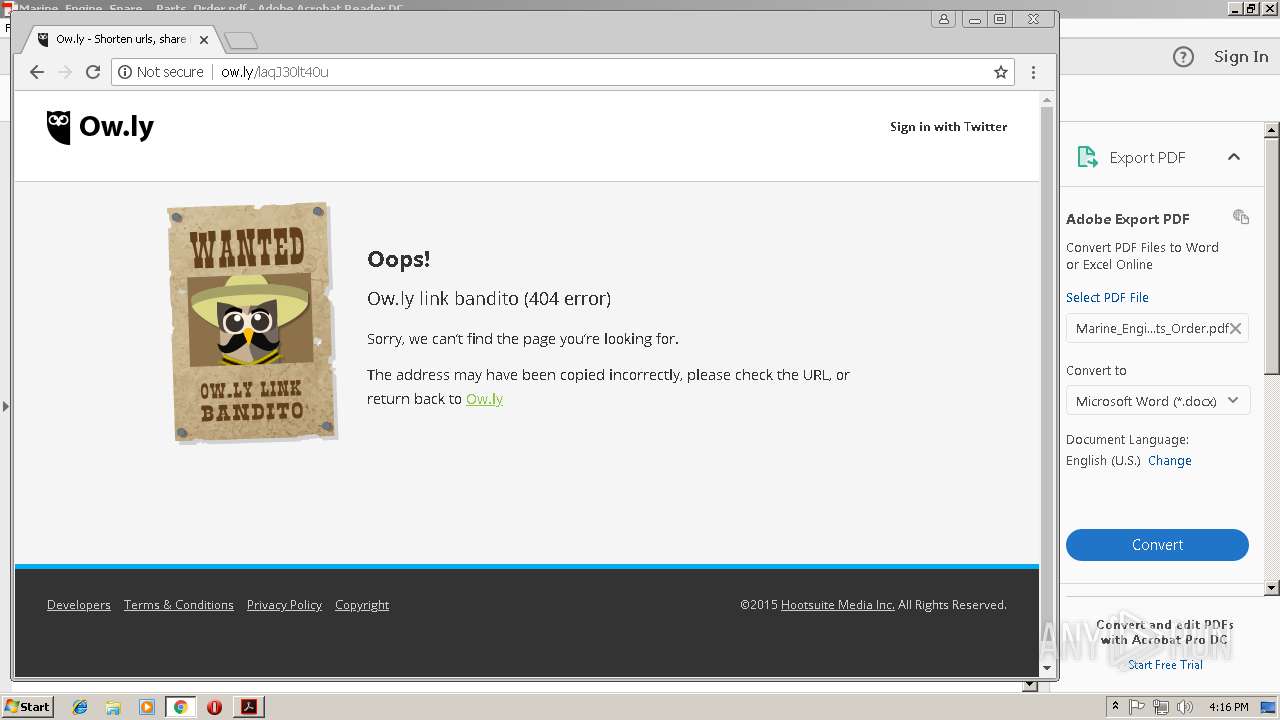
2960 | chrome.exe | GET | 404 | 54.183.130.144:80 | http://ow.ly/Kzr430lt4NV?platform=hootsuite | US | html | 2.38 Kb | shared |
2960 | chrome.exe | GET | 200 | 52.85.182.109:80 | http://static.ow.ly/v1/css/app.2fc2382996d502a2.gz.css | US | text | 9.05 Kb | shared |
2960 | chrome.exe | GET | 200 | 216.58.215.234:80 | http://fonts.googleapis.com/css?family=Open+Sans:400,700&subset=latin,latin-ext,cyrillic | US | text | 623 b | whitelisted |
2960 | chrome.exe | GET | 200 | 52.85.182.109:80 | http://static.ow.ly/v1/js/app.21d609cc16937ebb.gz.js | US | text | 41.8 Kb | shared |
2960 | chrome.exe | GET | 404 | 54.183.131.91:80 | http://ow.ly/laqJ30lt40u | US | html | 2.39 Kb | shared |
2960 | chrome.exe | GET | 200 | 52.85.182.109:80 | http://static.ow.ly/v1/images/bg_logo_header.fd2b7b6e6ba06c53.png | US | image | 1018 b | shared |
2960 | chrome.exe | GET | 200 | 52.85.182.109:80 | http://static.ow.ly/v1/images/favicon.9da2f5569b3e1489.ico | US | image | 1.12 Kb | shared |
2960 | chrome.exe | GET | 200 | 52.85.182.109:80 | http://static.ow.ly/v1/js/app.ebc7fcc65676567f.gz.js | US | text | 41.8 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1352 | chrome.exe | 172.217.168.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
1352 | chrome.exe | 216.58.215.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
3836 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
3836 | AcroRd32.exe | 2.16.186.11:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
1352 | chrome.exe | 216.58.215.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1352 | chrome.exe | 172.217.168.36:443 | www.google.com | Google Inc. | US | whitelisted |
1352 | chrome.exe | 172.217.168.3:443 | www.google.de | Google Inc. | US | whitelisted |
2960 | chrome.exe | 54.183.130.144:80 | ow.ly | Amazon.com, Inc. | US | suspicious |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
1352 | chrome.exe | 216.58.215.238:443 | apis.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.de |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |
2960 | chrome.exe | A Network Trojan was detected | SC BAD_UNKNOWN Possible threat - 'ow.ly' service used |