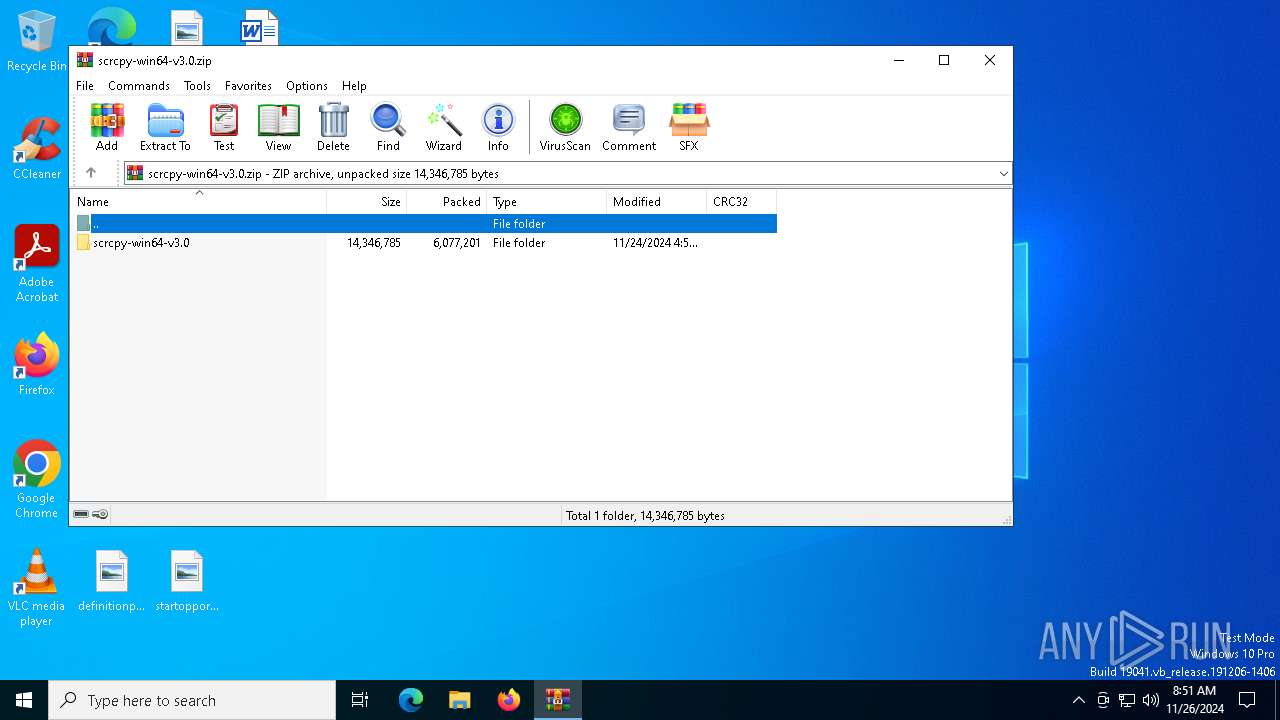
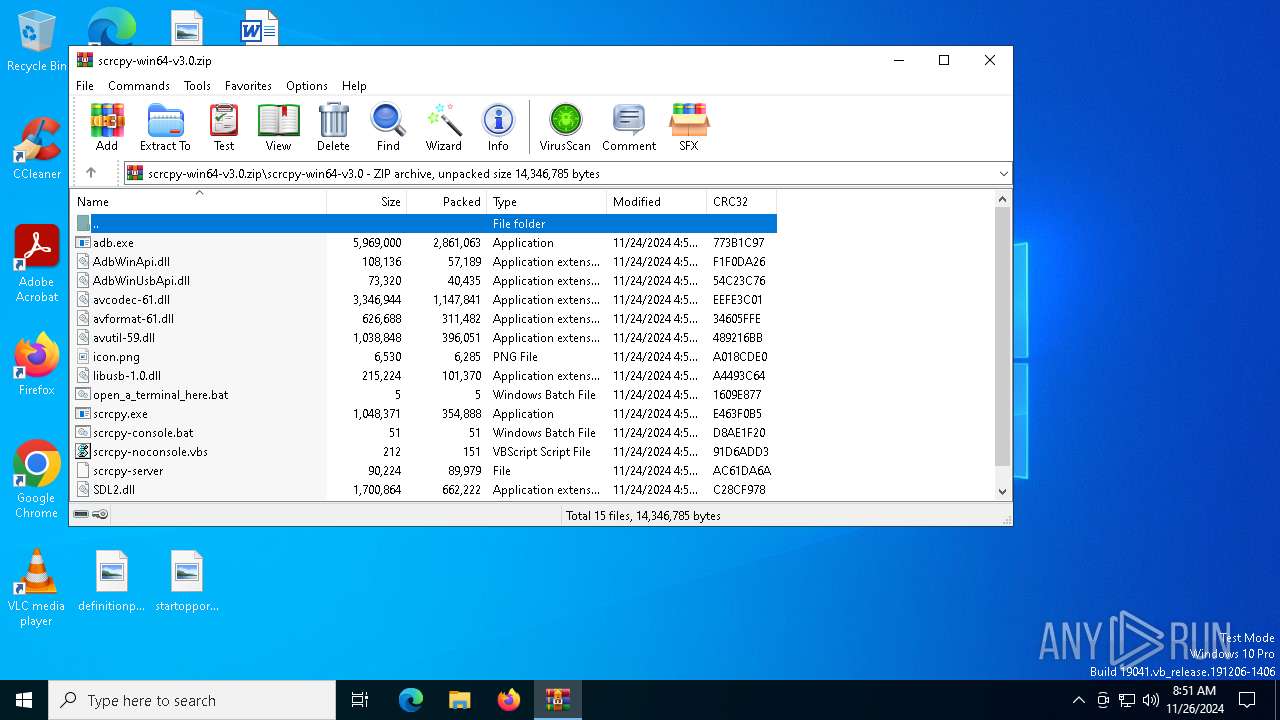
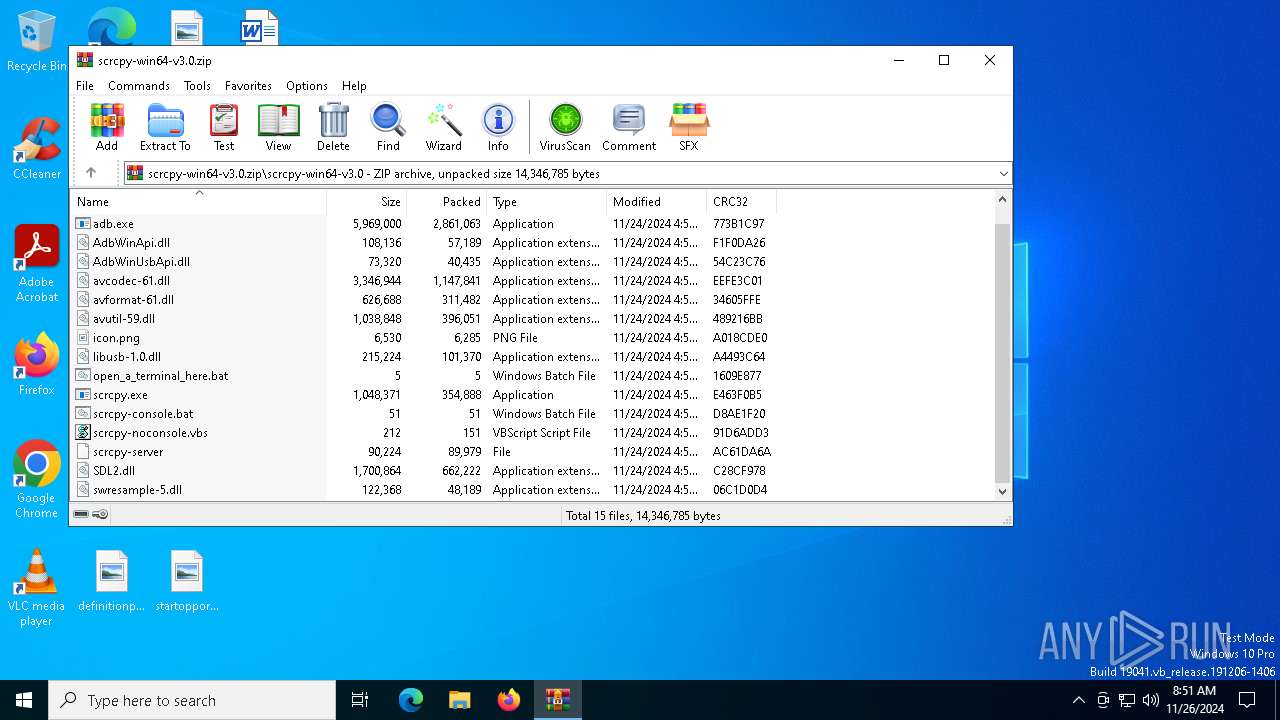
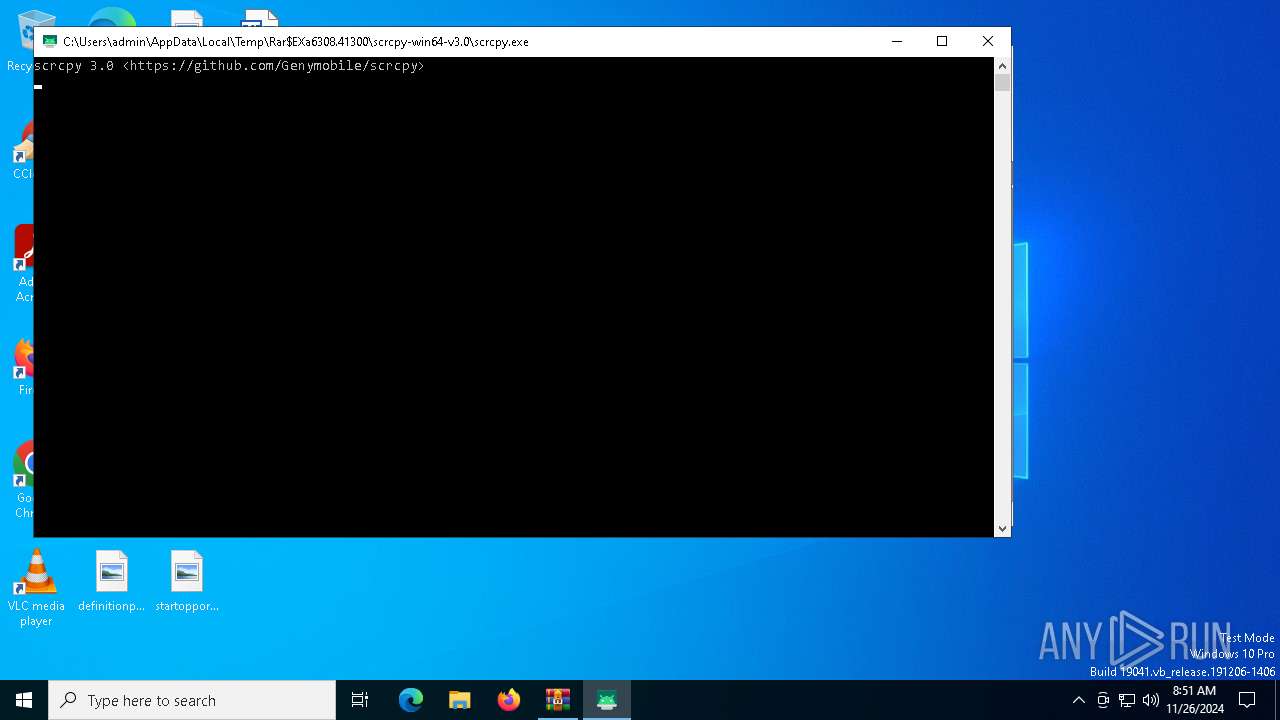
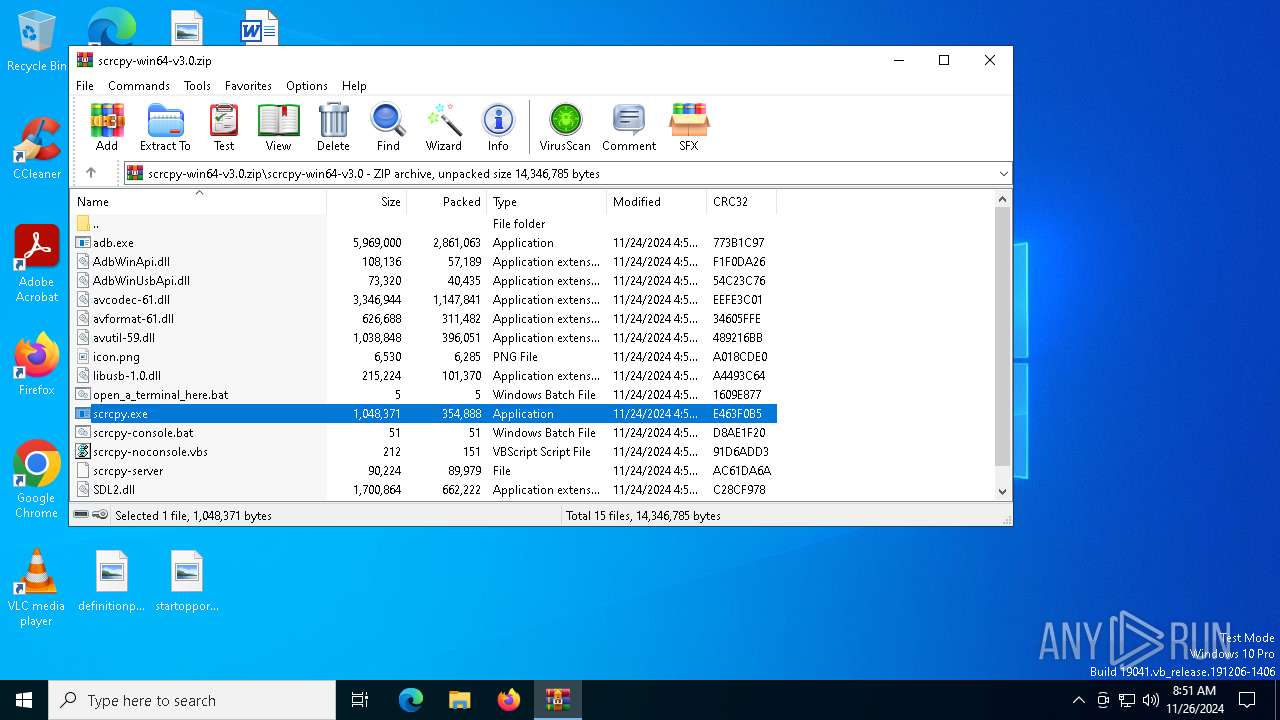
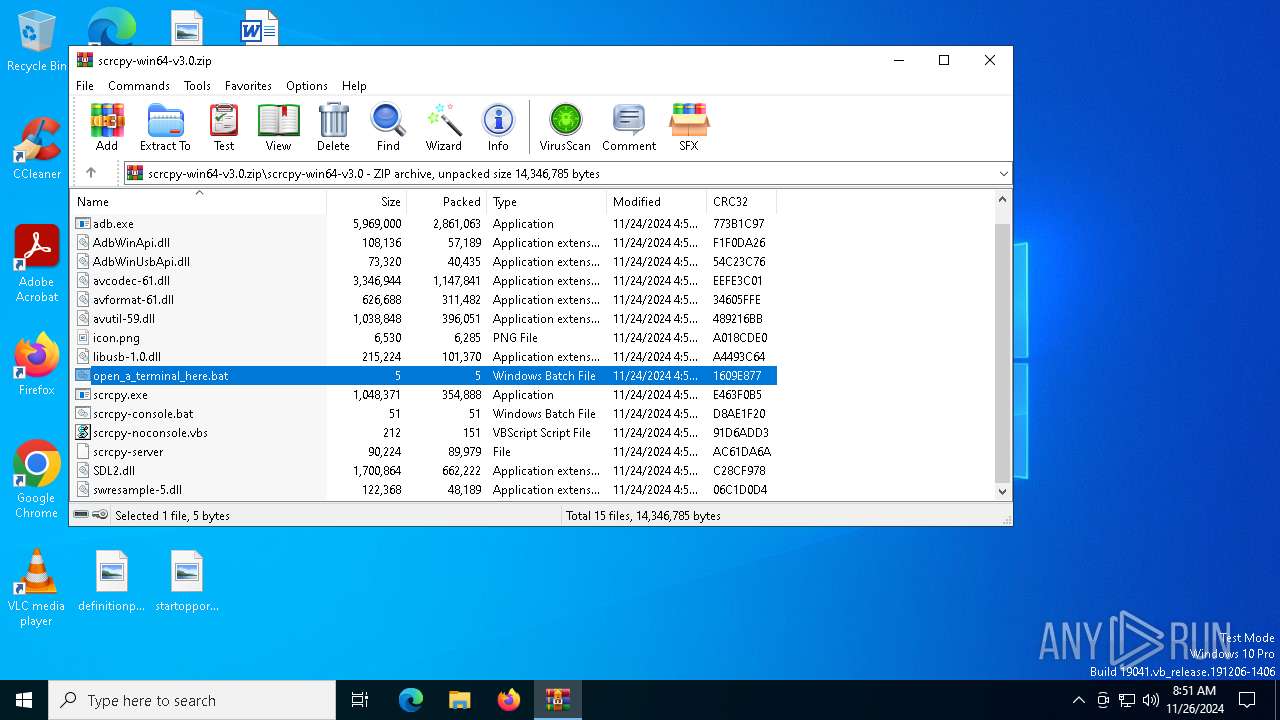
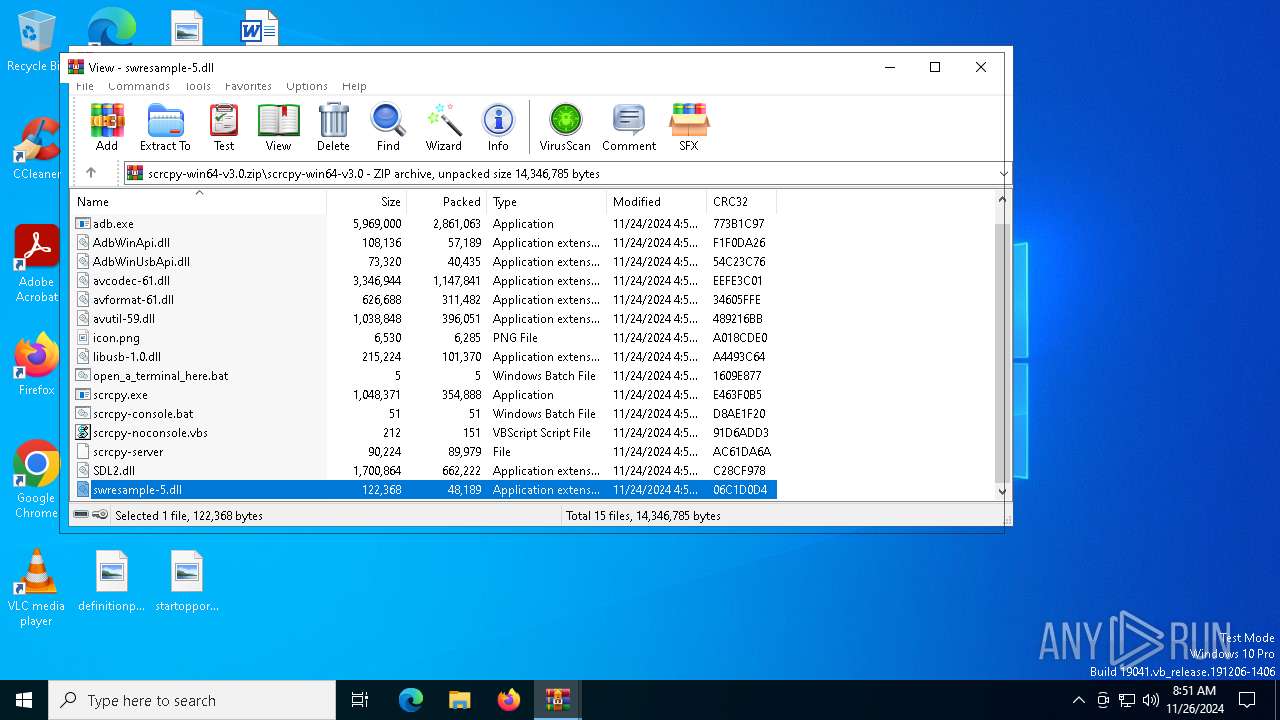
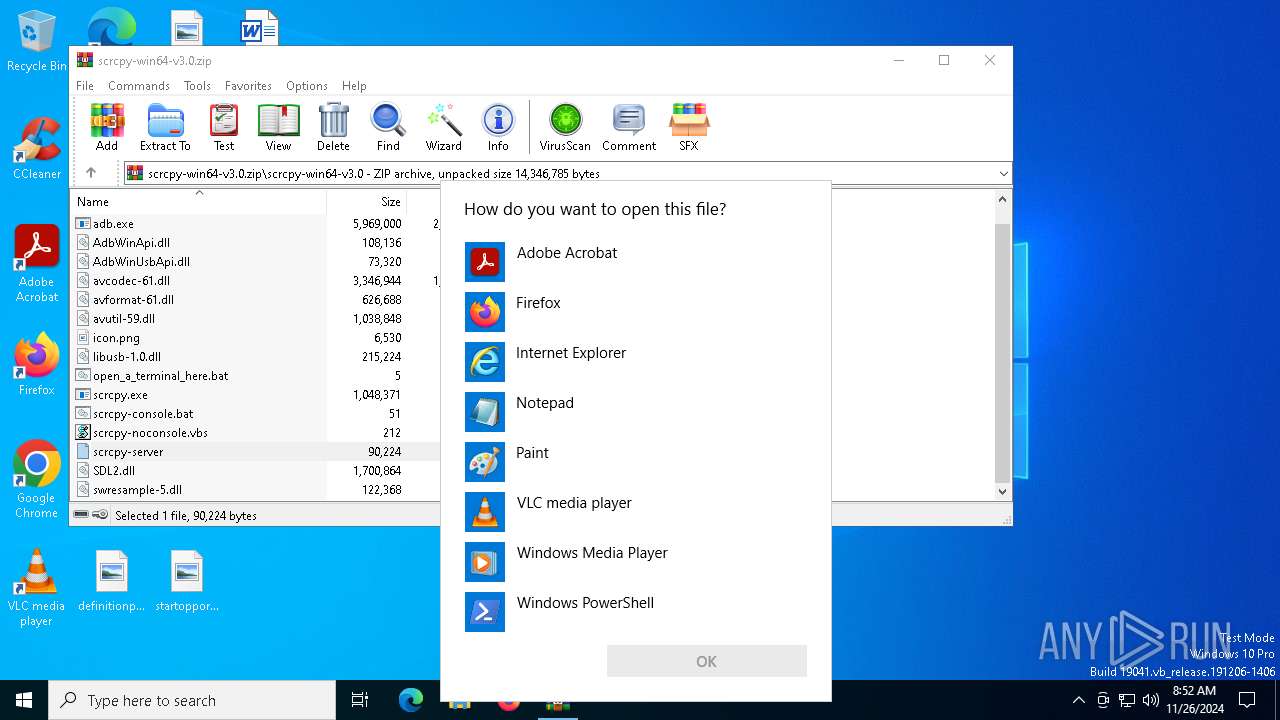
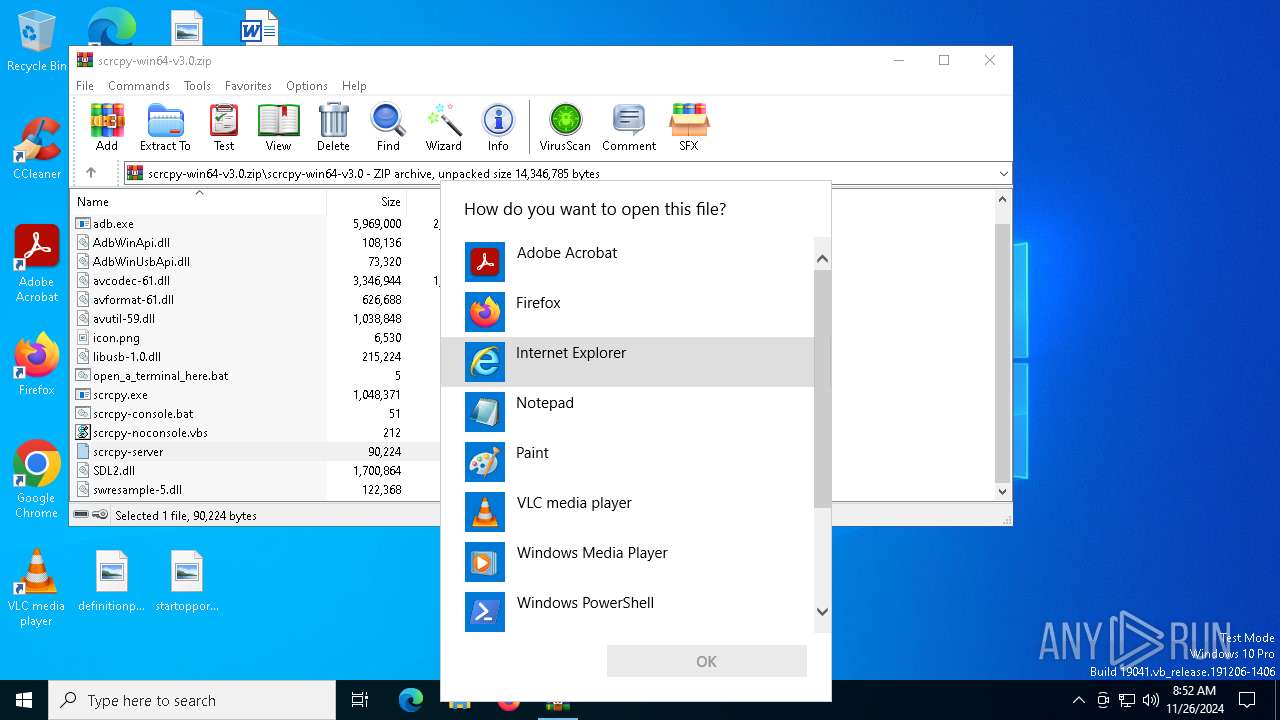
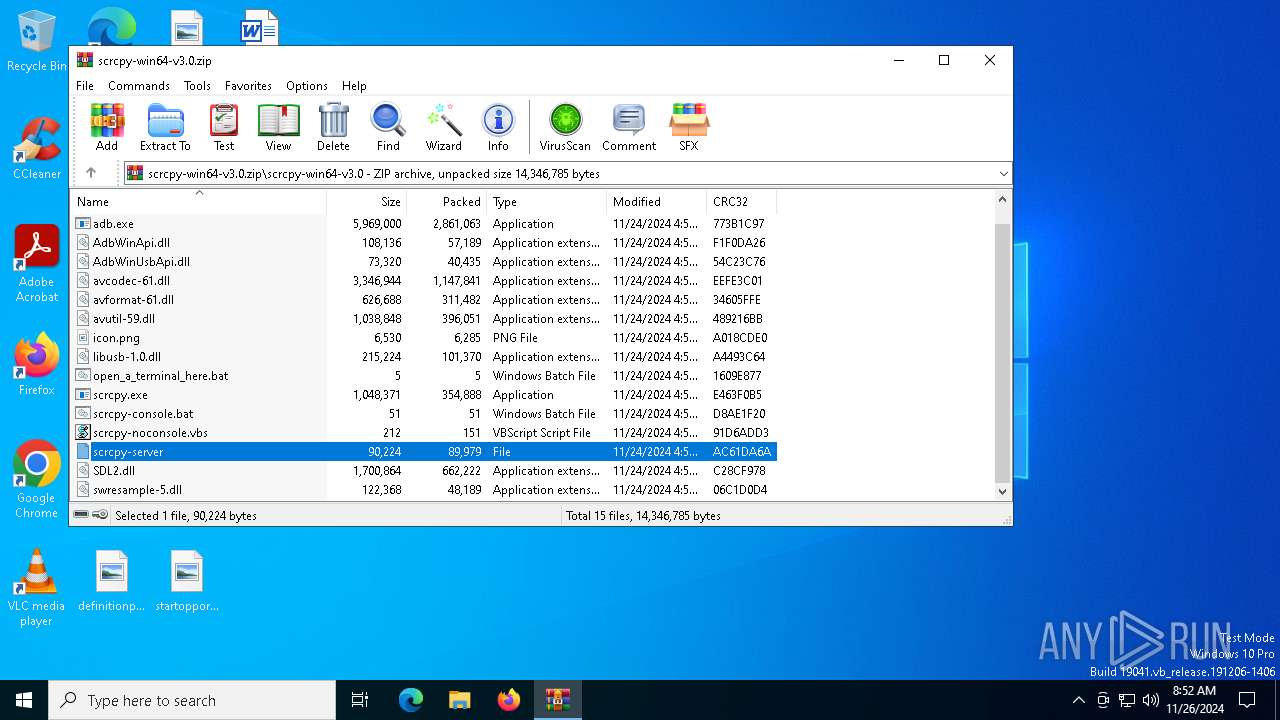
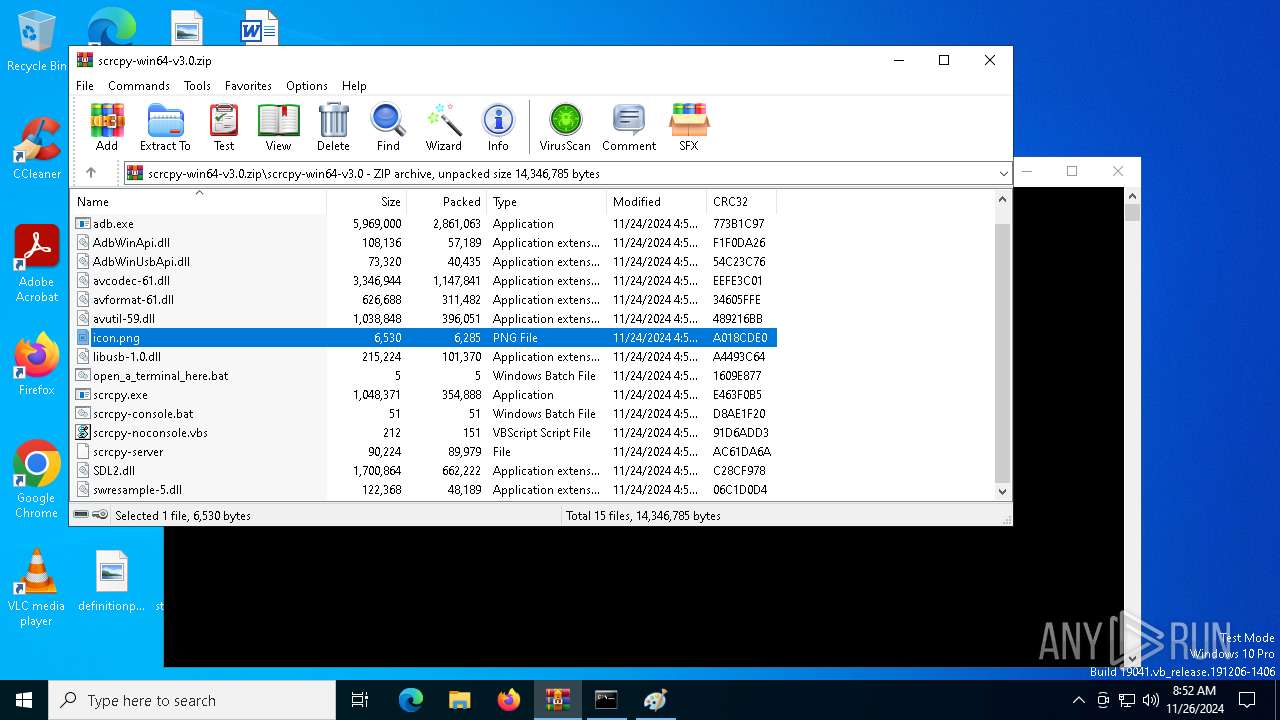
| File name: | scrcpy-win64-v3.0.zip |
| Full analysis: | https://app.any.run/tasks/49b4aa14-ac82-4ed7-b5b3-cb9b2c7f652a |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2024, 08:51:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1FBE088498166AB3D1A7272B4493C602 |
| SHA1: | 4650C9D4743DA8F479DE1B5465A70E61E686F61C |
| SHA256: | DFBE8A8FEF6535197ACC506936BFD59D0AA0427E9B44FB2E5C550EAE642F72BE |
| SSDEEP: | 98304:MFMPZQG/FyAB9uh7JJg/WJQ4cOWowpSY85iCvRDVrDceDQJpFl/om50iTNZzASiN:tM6L6hA0j |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6308)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6308)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7048)
- WinRAR.exe (PID: 6308)
- cmd.exe (PID: 6780)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7048)
The process executes VB scripts
- WinRAR.exe (PID: 6308)
Application launched itself
- adb.exe (PID: 5156)
- cmd.exe (PID: 6780)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6308)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6308)
The process uses the downloaded file
- WinRAR.exe (PID: 6308)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6308)
Checks supported languages
- adb.exe (PID: 6236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:24 16:57:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | scrcpy-win64-v3.0/ |
Total processes
147
Monitored processes
18
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3288 | adb -L tcp:5037 fork-server server --reply-fd 608 | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.41300\scrcpy-win64-v3.0\adb.exe | adb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4144 | adb devices -l | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.41300\scrcpy-win64-v3.0\adb.exe | — | scrcpy.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5156 | adb start-server | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.41300\scrcpy-win64-v3.0\adb.exe | — | scrcpy.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5576 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6168 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.41300\scrcpy-win64-v3.0\scrcpy.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.41300\scrcpy-win64-v3.0\scrcpy.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 6232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6236 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\adb.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\adb.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 6308 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\scrcpy-win64-v3.0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6500 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa6308.46505\icon.png" | C:\Windows\System32\mspaint.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6532 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa6308.44724\scrcpy-console.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 981
Read events
6 968
Write events
13
Delete events
0
Modification events
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\scrcpy-win64-v3.0.zip | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Viewer |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3400000034000000F40300001D020000 | |||
Executable files
28
Suspicious files
3
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6308.40542\scrcpy-noconsole.vbs | text | |
MD5:A6ADB14566ED94E5D80107AEB0FA5291 | SHA256:3CCDA94C161F18CEF07C50D4D3C4913EB883D4B0FE3B939C35FAE52784FB1D2B | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\swresample-5.dll | executable | |
MD5:DEF6342B3579177A74C71E30BD6F8480 | SHA256:73A89738AF442C3120CB5130CB8B830F43BB9D3B3AED77B3ED754C3080DB4149 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\AdbWinUsbApi.dll | executable | |
MD5:93A6075B7AE7D0DF52EC55017A2F8214 | SHA256:3BA13420D47C60D958E0D5B333440F9895704879BB7C983B55F195717F621A3E | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\icon.png | image | |
MD5:9E1FFBD6D2630C3B89BE2B9C19C29E8F | SHA256:8E8CA237898FAA16014CDD118396AF53405B423F3DB0508C50CC3EDCE08EB313 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\scrcpy-console.bat | text | |
MD5:7B8D3B0D87DD886730D4993AF807FAE1 | SHA256:B49A3EB642898269E7E690E80F3DE17898F966F69E75F11ABEB31EB7023B0EE5 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\libusb-1.0.dll | executable | |
MD5:E2F778A6C4F2388434C2AAF255319080 | SHA256:34C63BE7C812443F7659EE7B7F3350EAB038DF6A1AEB9C14D377F61E23A1B294 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\scrcpy-server | compressed | |
MD5:FE1737478E471DB5A6C5B937123CCBAF | SHA256:800044C62A94D5FC16F5AB9C86D45B1050EAE3EB436514D1B0D2FE2646B894EA | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\SDL2.dll | executable | |
MD5:C8E989CB961AB95BE94EEA98188A434E | SHA256:DB0EEF2E80AD06E158BAC2DFE3C3731BF1BAB857C17B695B6FBB7E3141D083E3 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\scrcpy.exe | executable | |
MD5:AD1FDD71339D46ACDDE9FEB3DA5095EC | SHA256:B5D73A7B764C0AB073C6DB9412082CF7E8E9BB1B8CA97B59C1DED02DAF93F473 | |||
| 6308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6308.40982\scrcpy-win64-v3.0\AdbWinApi.dll | executable | |
MD5:D2C034449BE65653AEC2459D9AB83AE5 | SHA256:DB92F418F6C384FAEEBCCADBC592FB339AF3D51ECFEC3EC04BD3572080247BAE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1380 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4944 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4944 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6580 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1380 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1476 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1380 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1380 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 23.212.110.187:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |