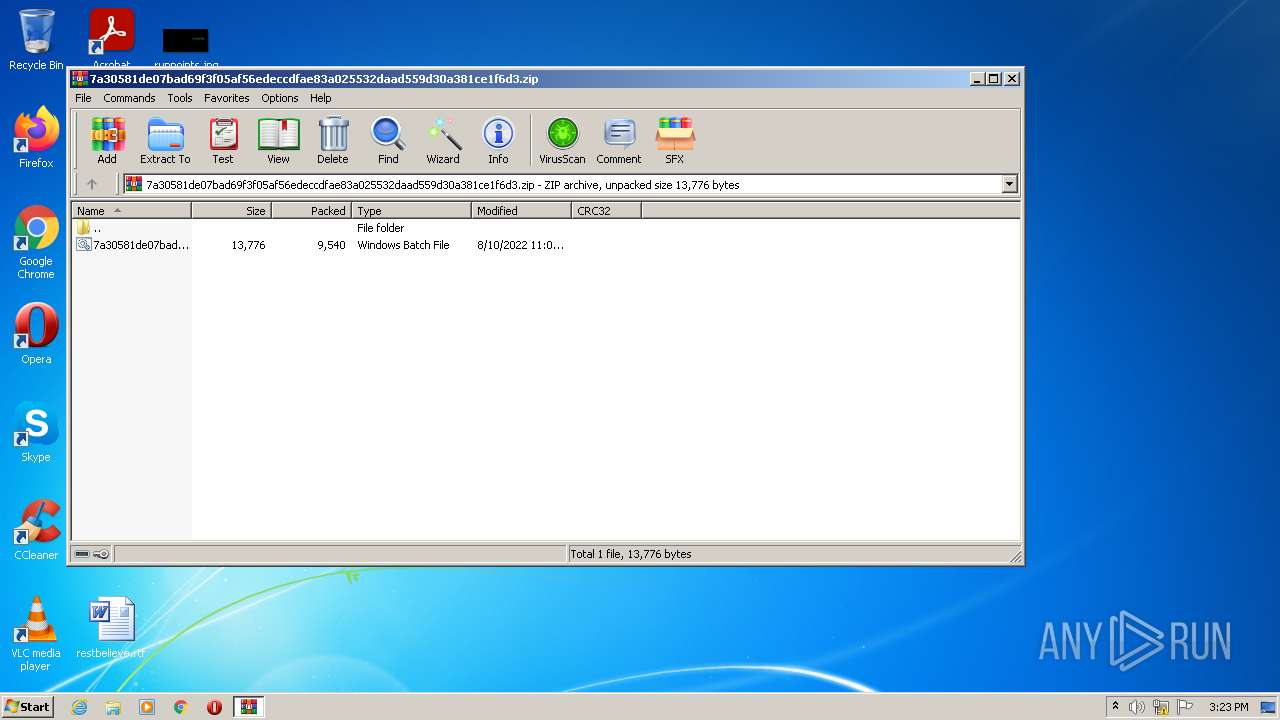
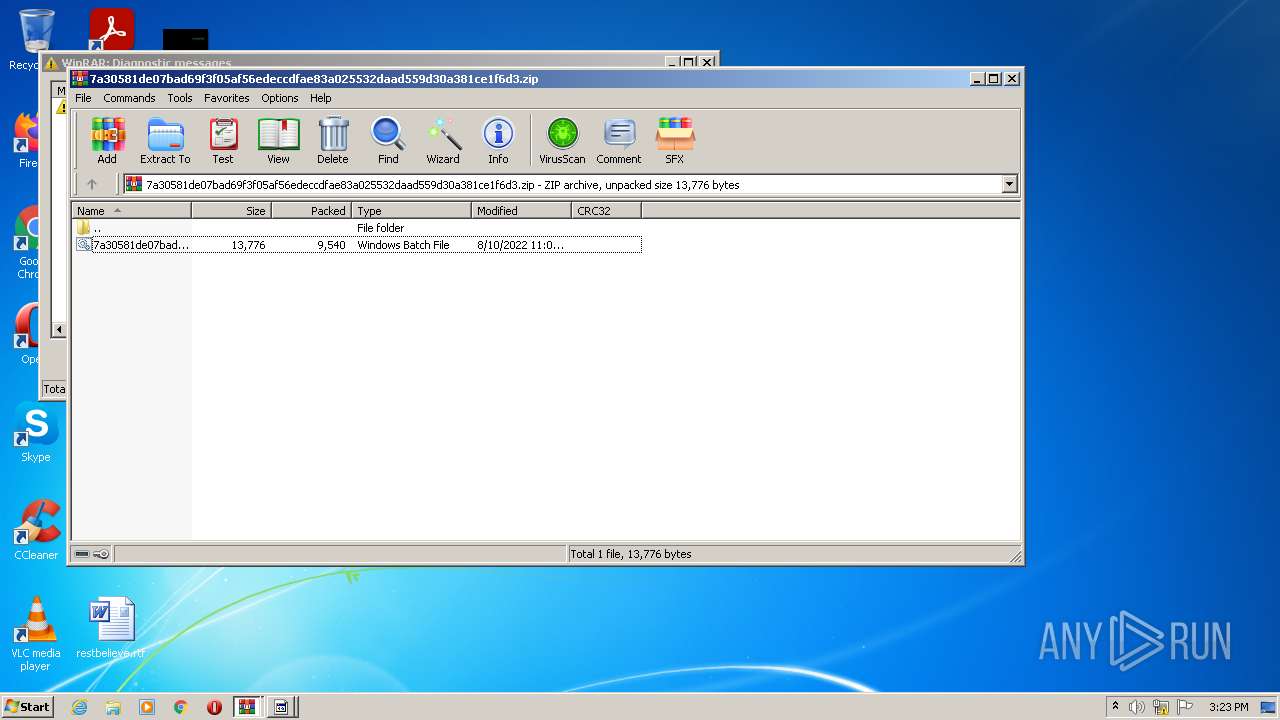
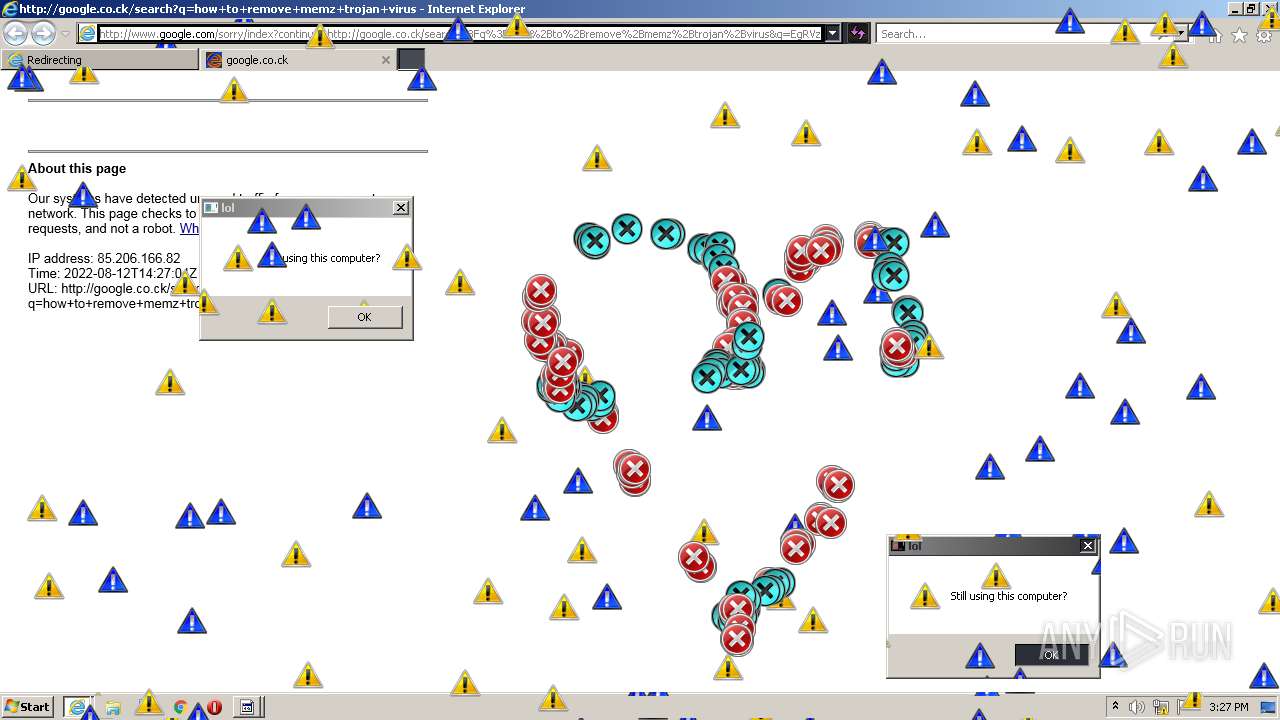
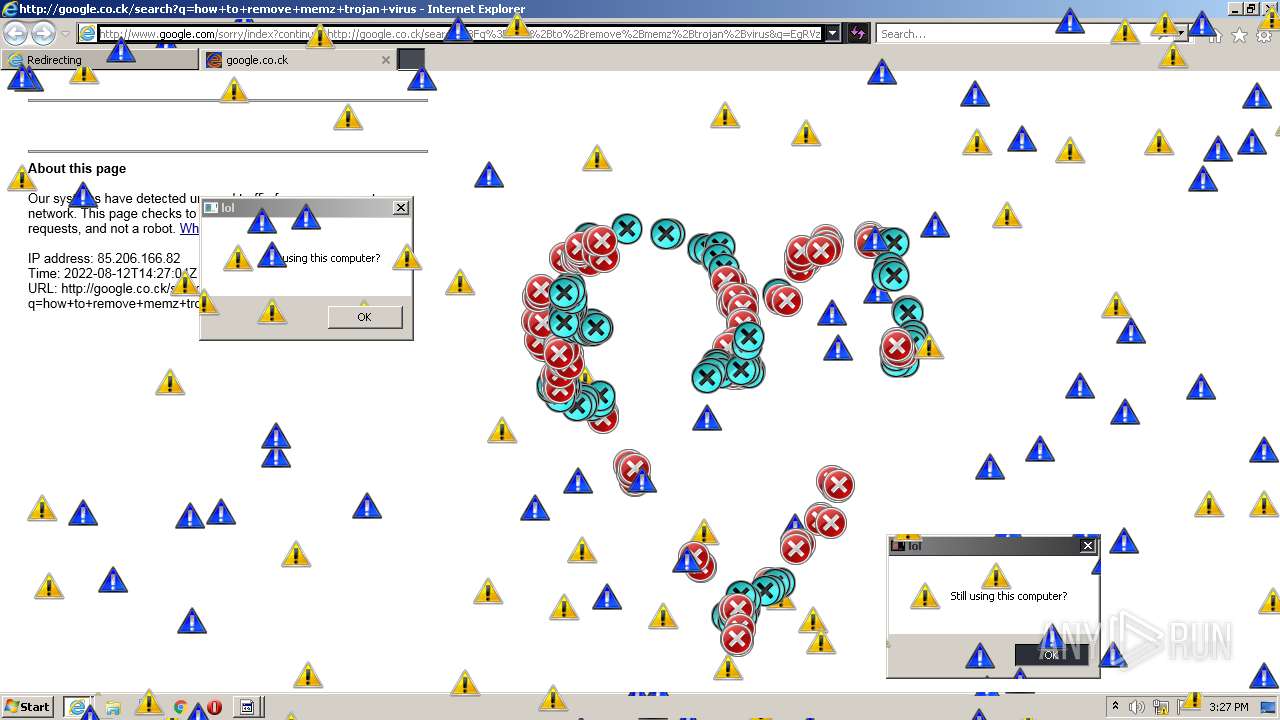
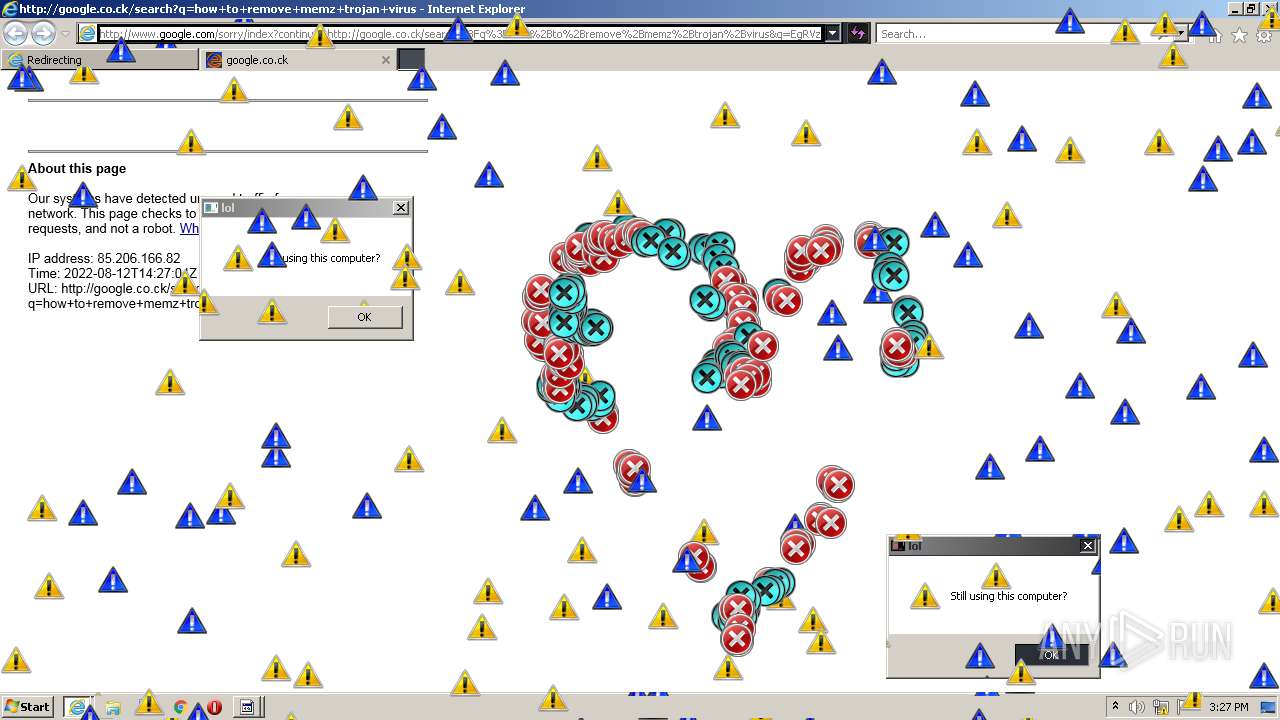
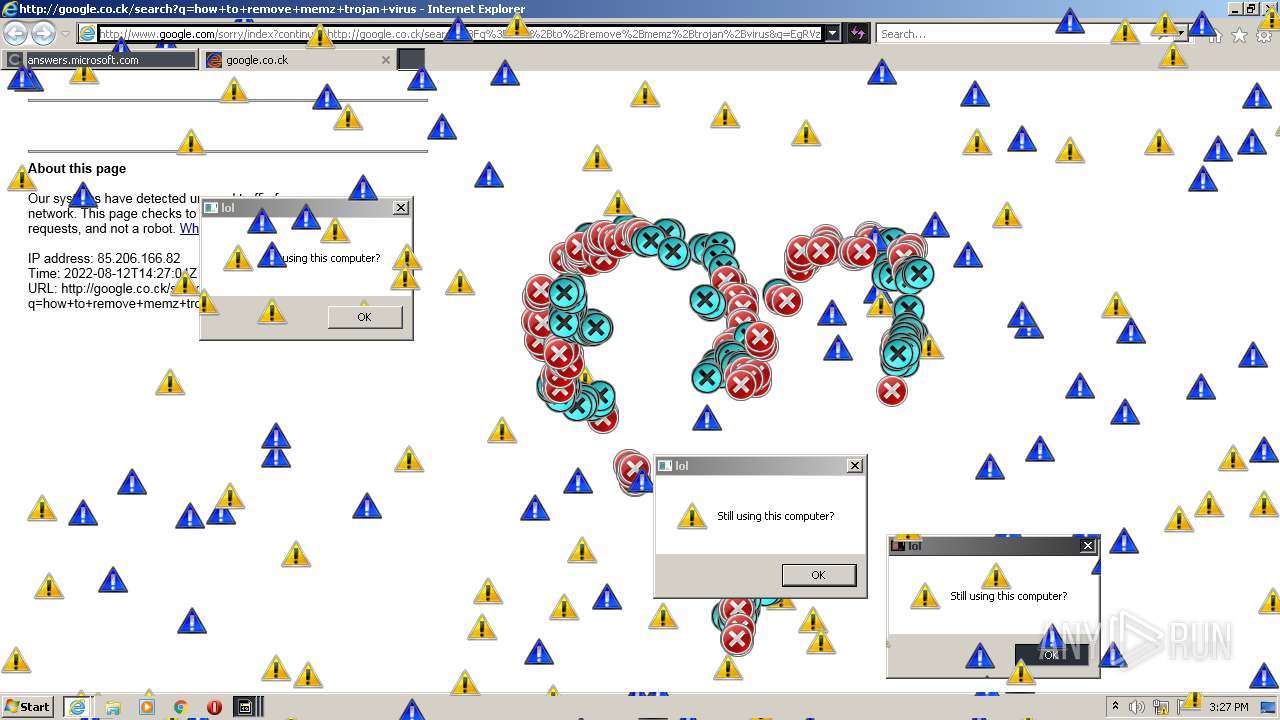
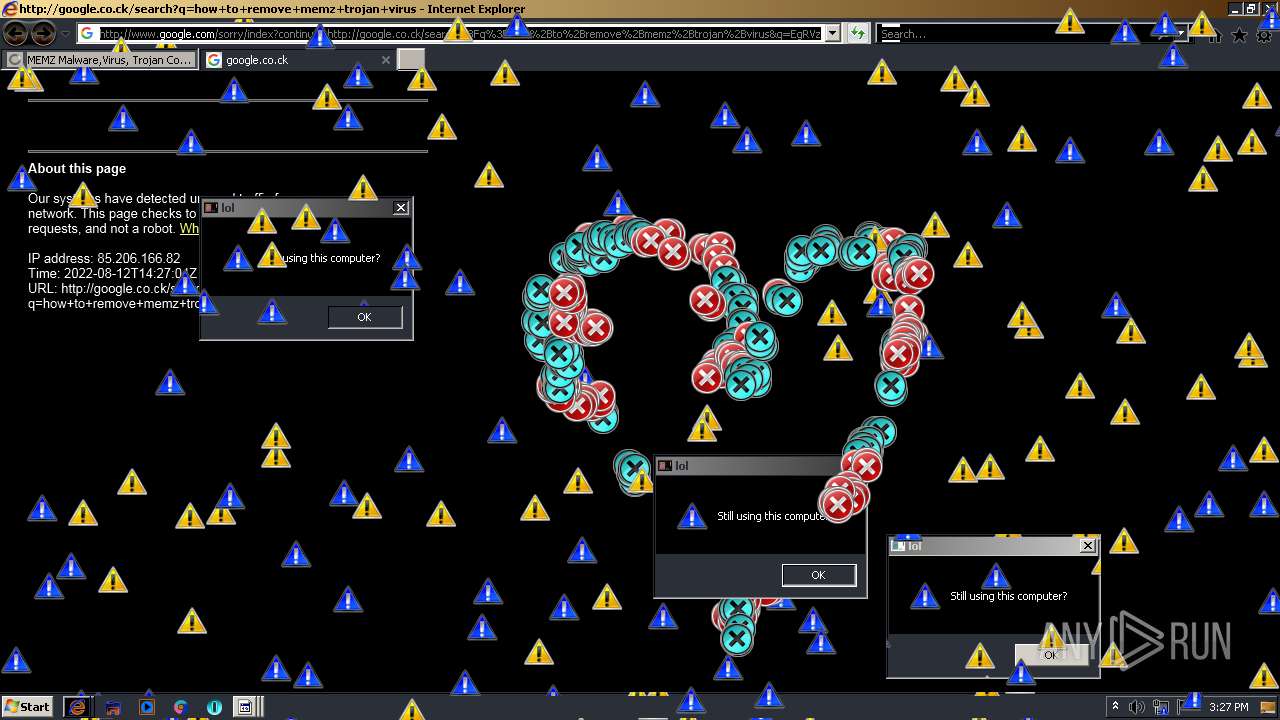
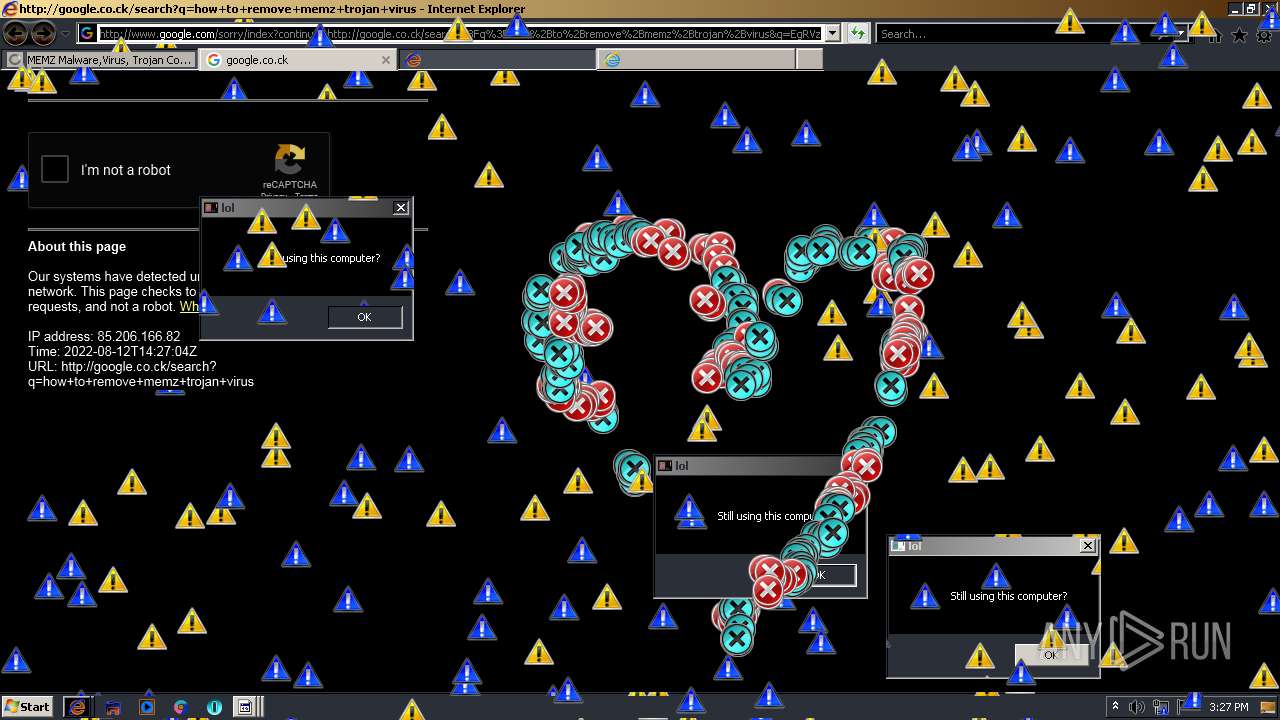
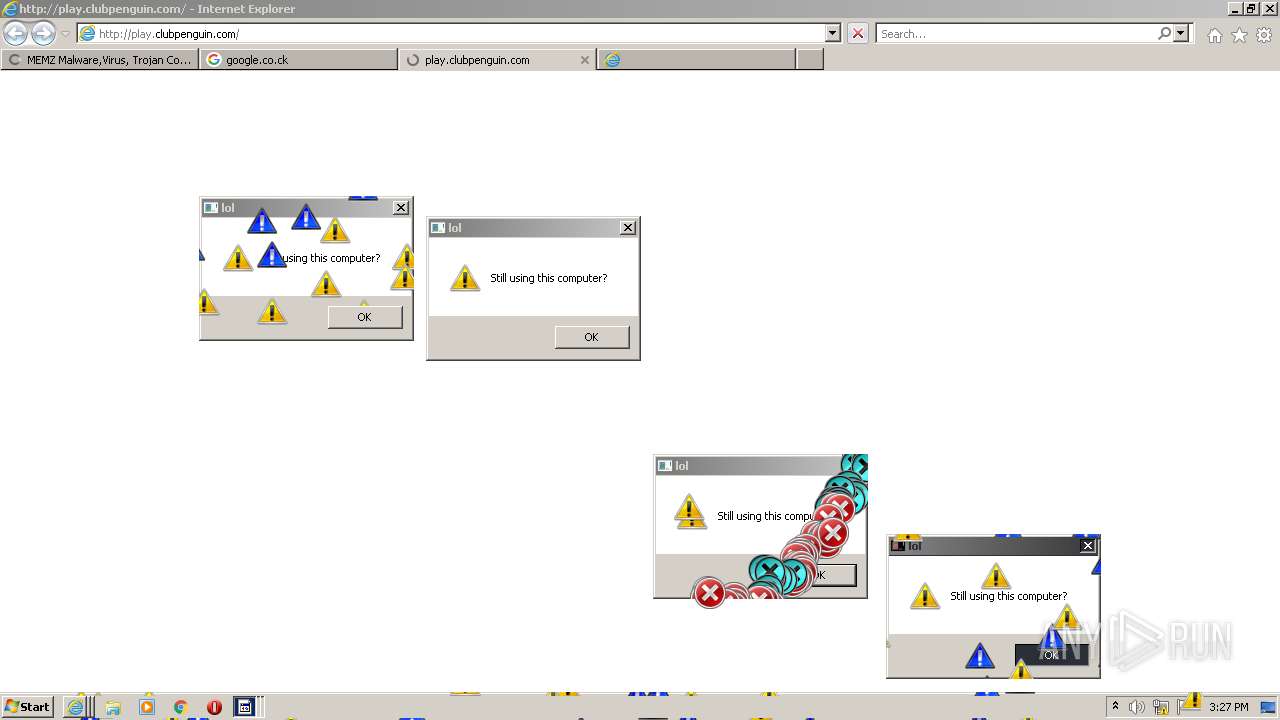
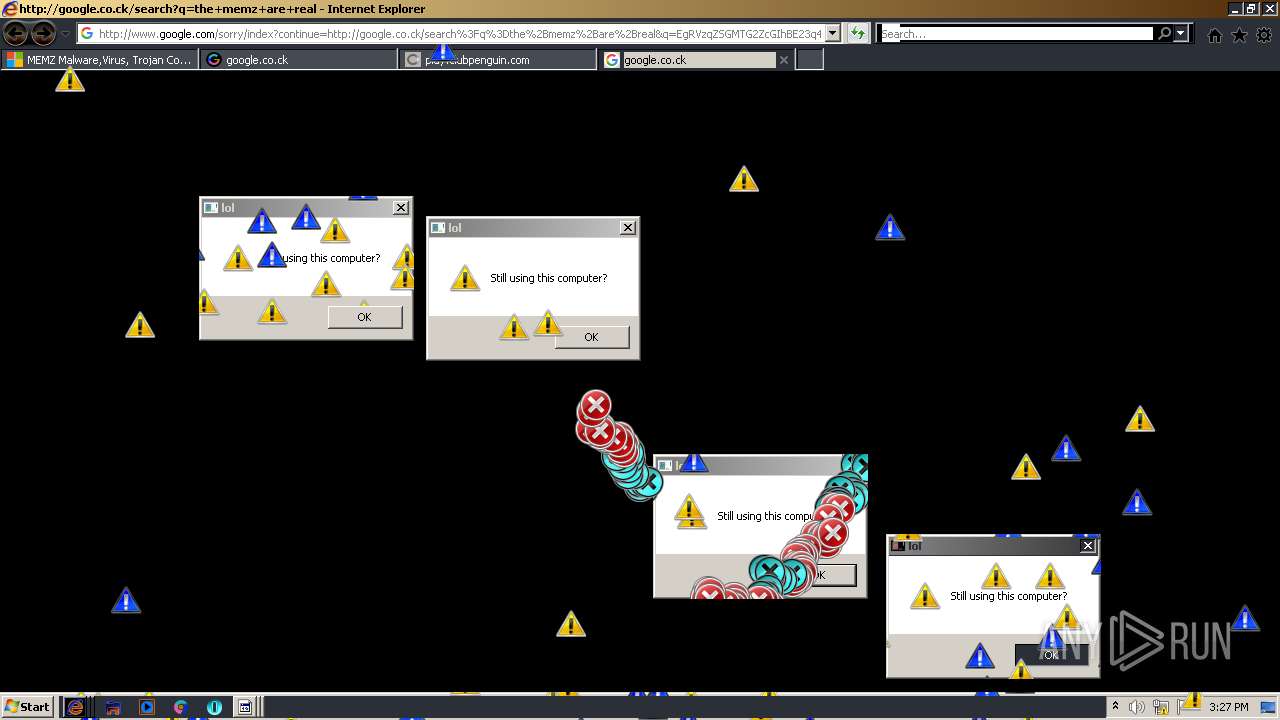
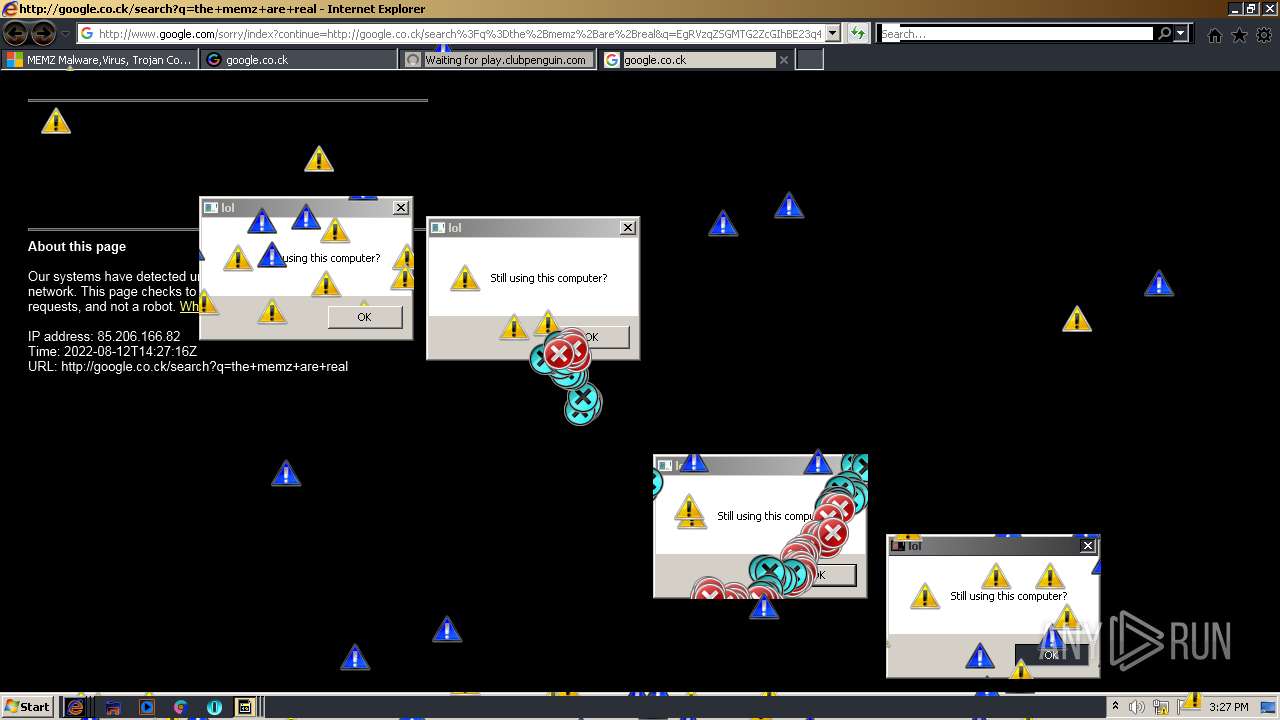
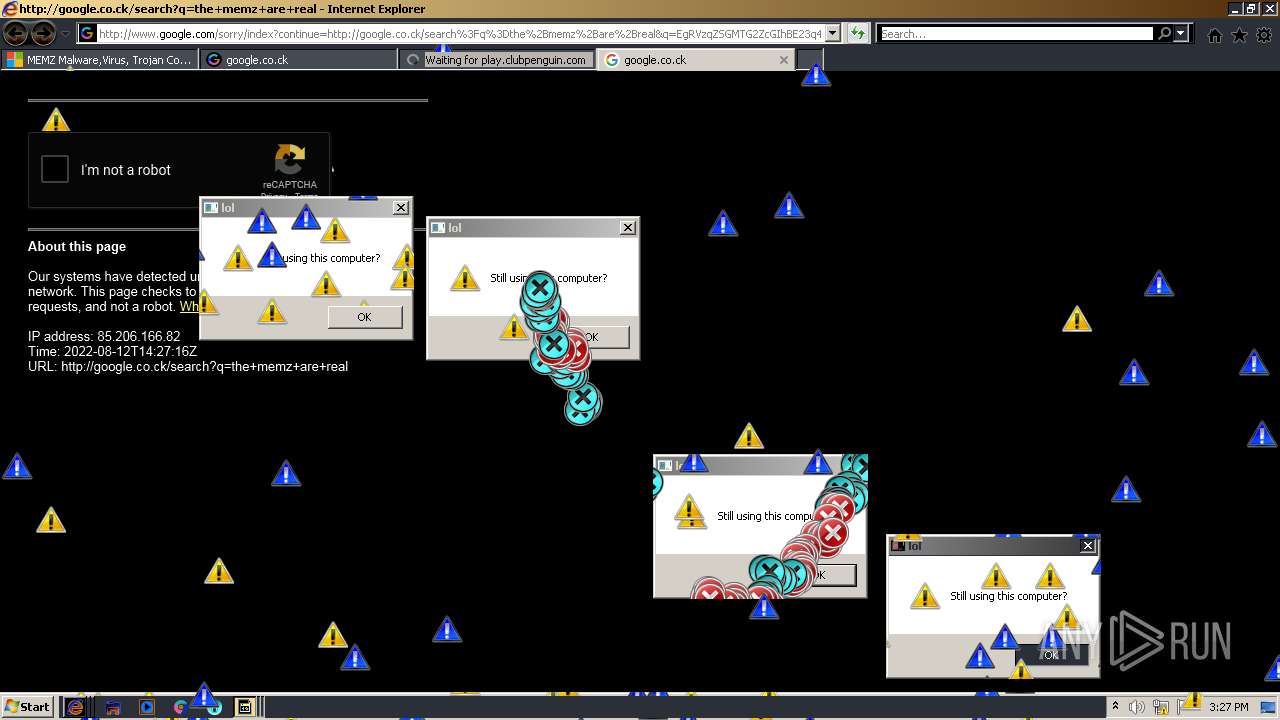
| File name: | 7a30581de07bad69f3f05af56edeccdfae83a025532daad559d30a381ce1f6d3.zip |
| Full analysis: | https://app.any.run/tasks/19087d1f-b9a3-4087-8167-e0d9b7aa57e9 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 14:23:00 |
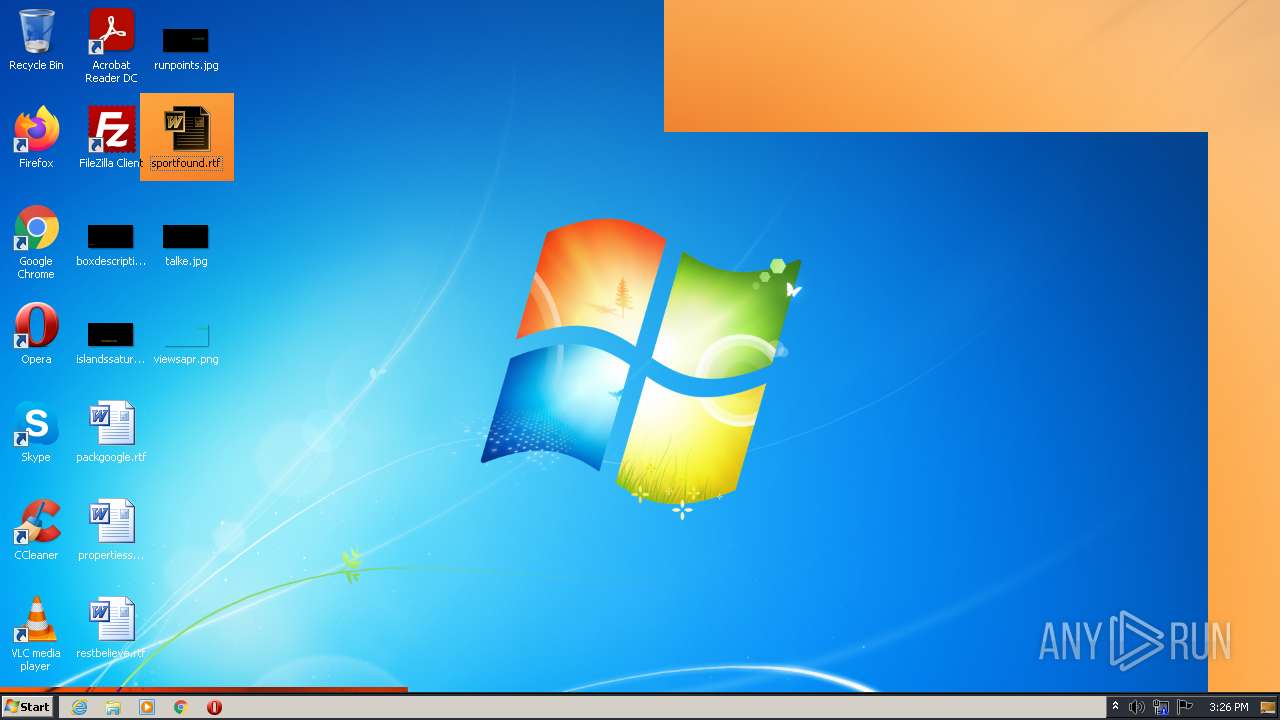
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 8F02100A55AEC031FE205E36F855018C |
| SHA1: | 34C2F17D0C0C5E864E4D1381349E365BD8F126A7 |
| SHA256: | DFB4D42E1EA6E7D616173A97624DE893ADD53F59E6B07F98F27667DECB88A7A5 |
| SSDEEP: | 192:PEpT2tENOCeUzPD7fju8iUsh5RiU0WBo9jaE/U1ak5JO8E4OV8V+VqDDJBkH:MhDsUrDrjd+iU04o9OE81HkV4OV8V+OK |
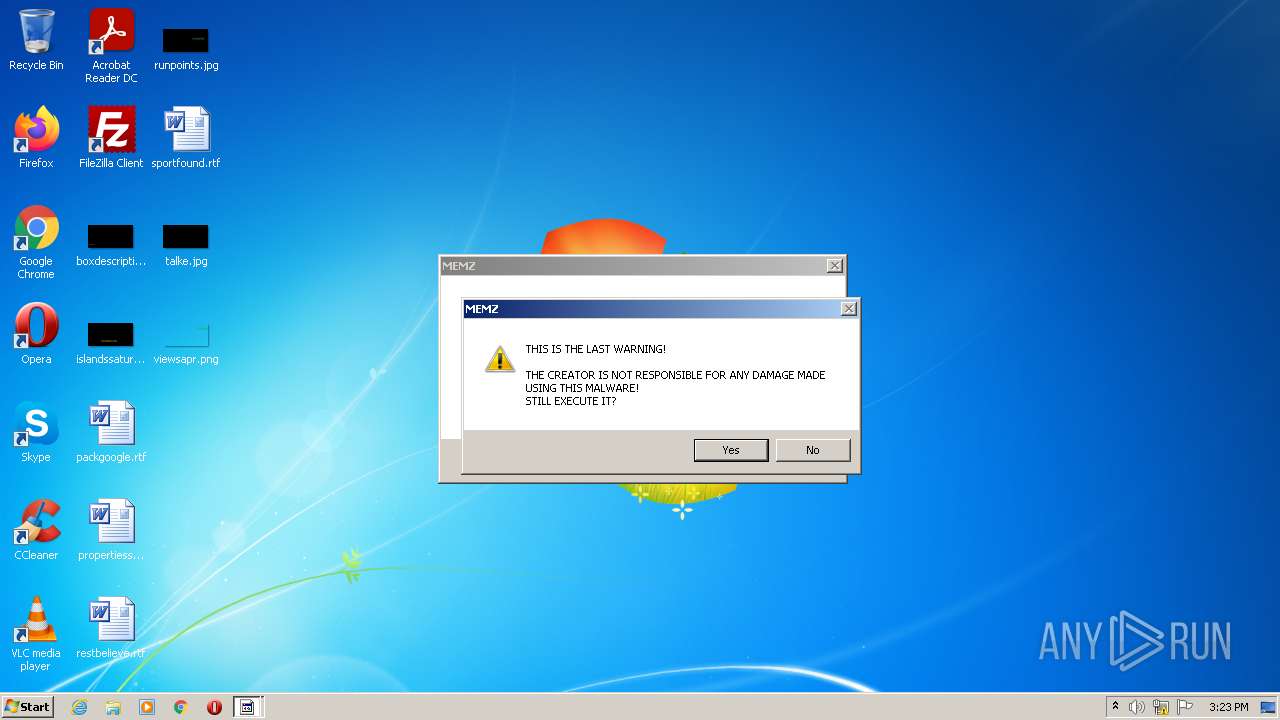
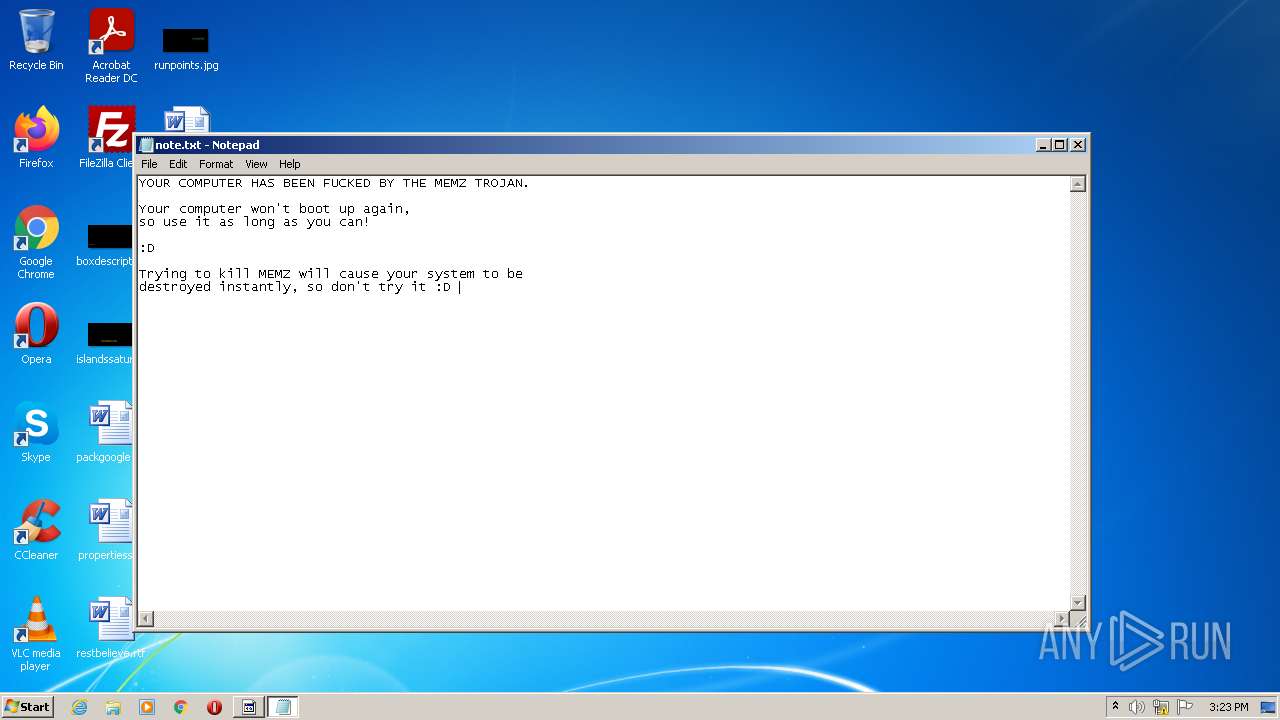
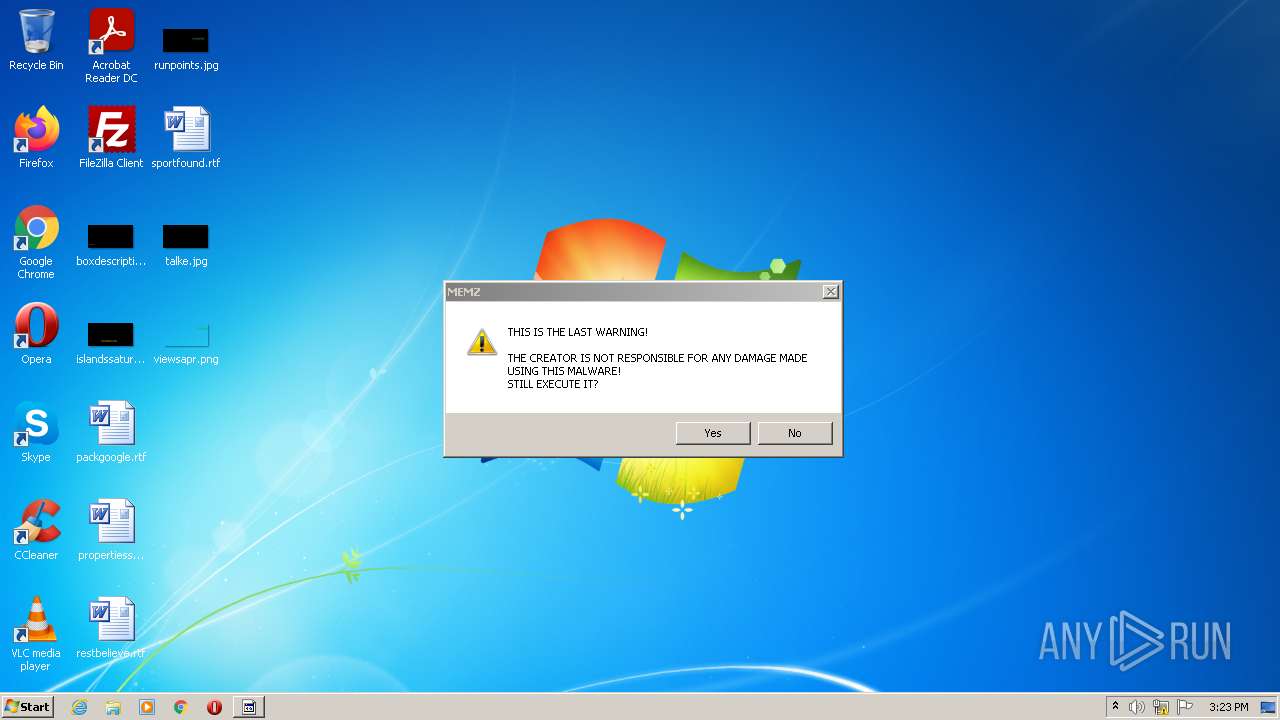
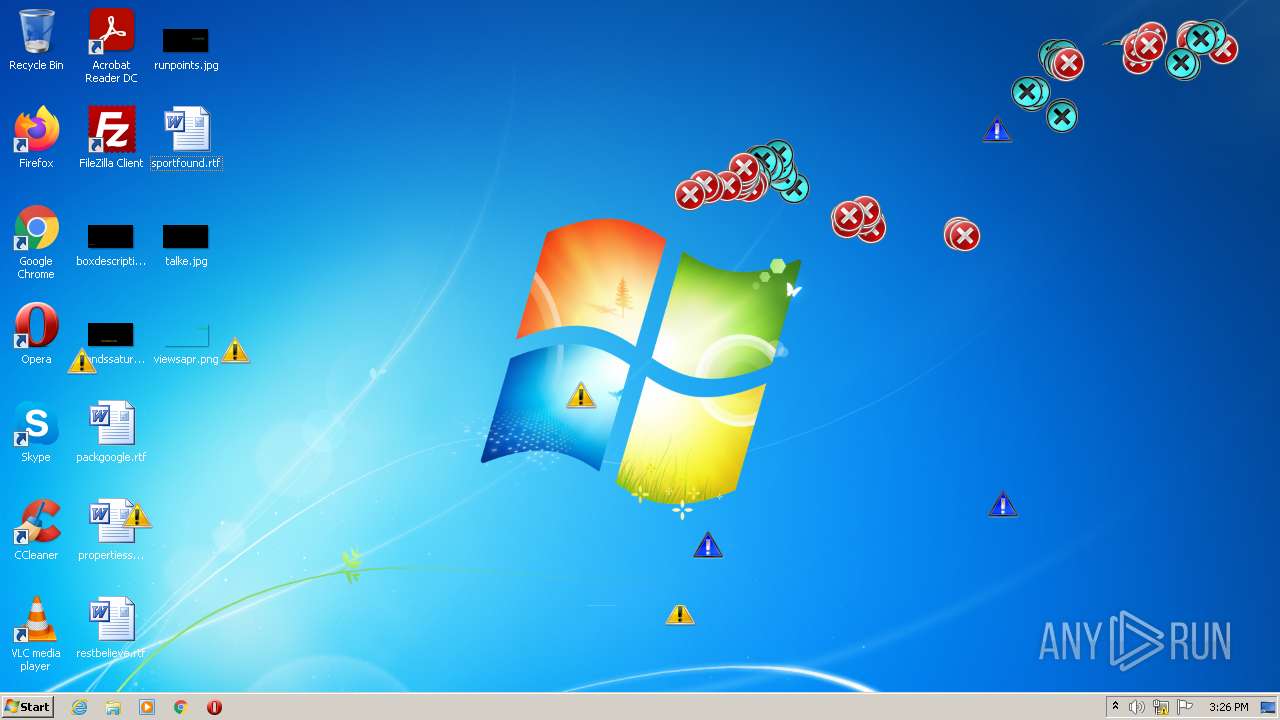
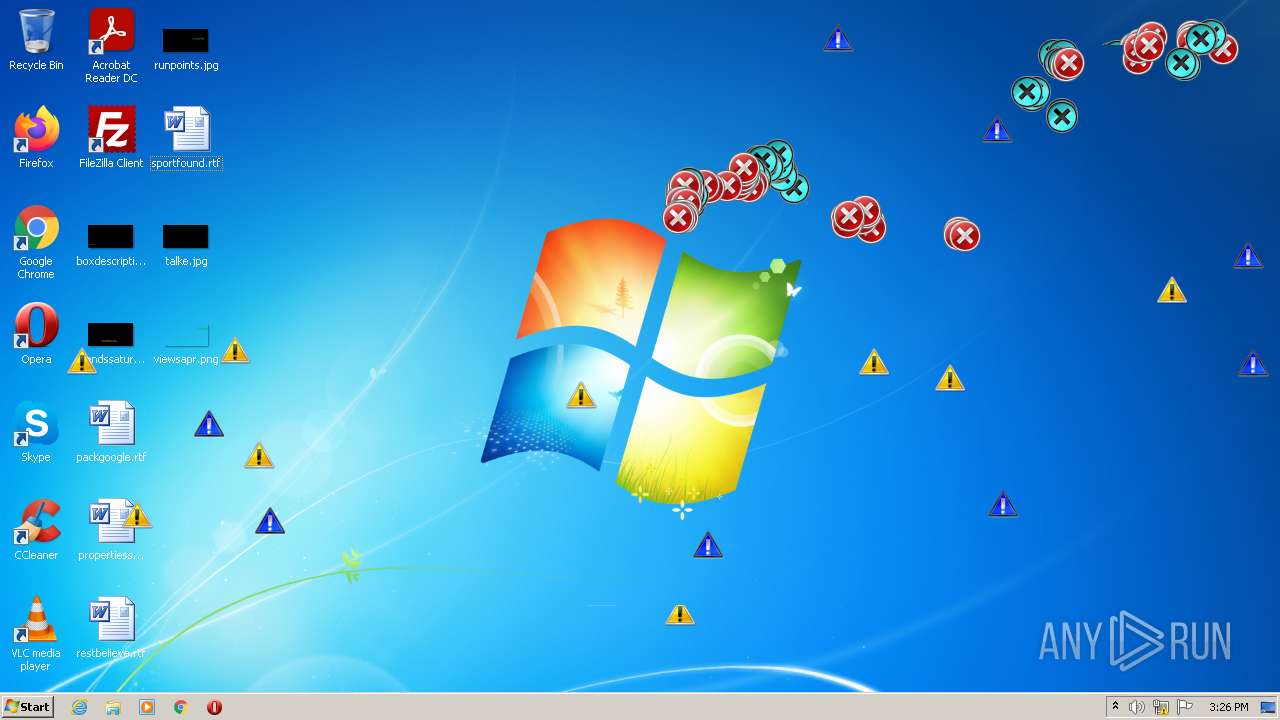
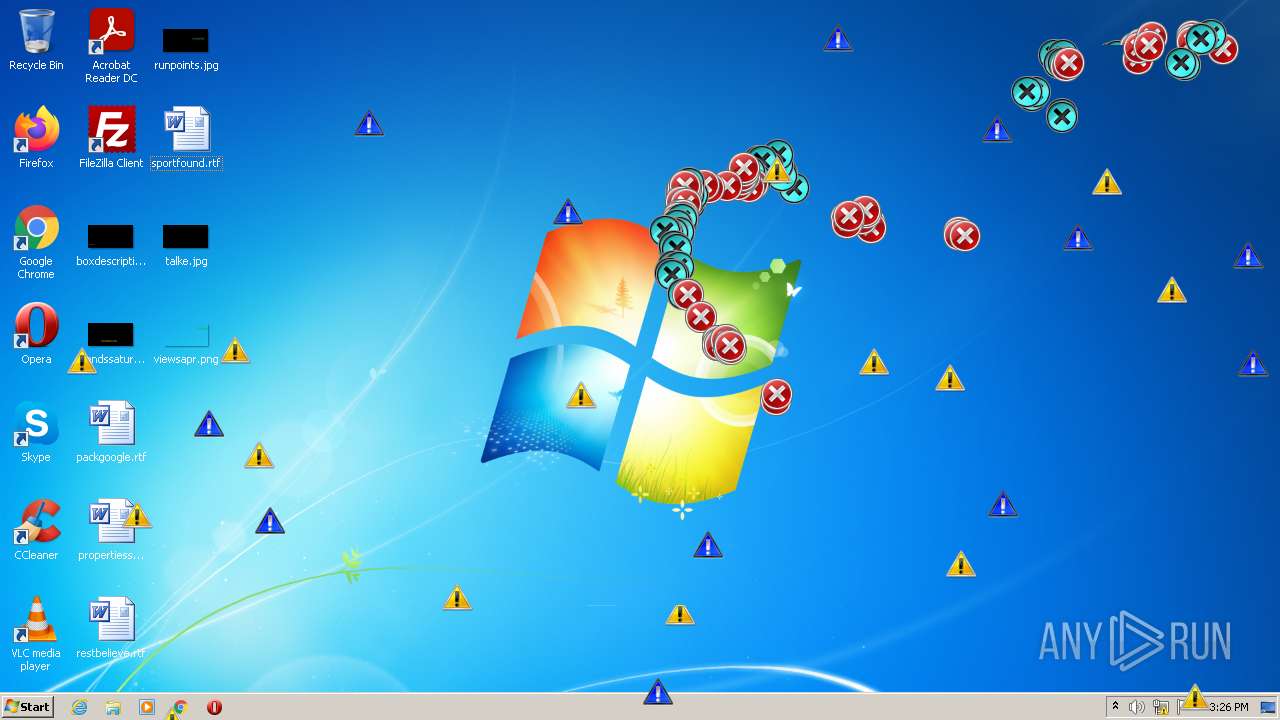
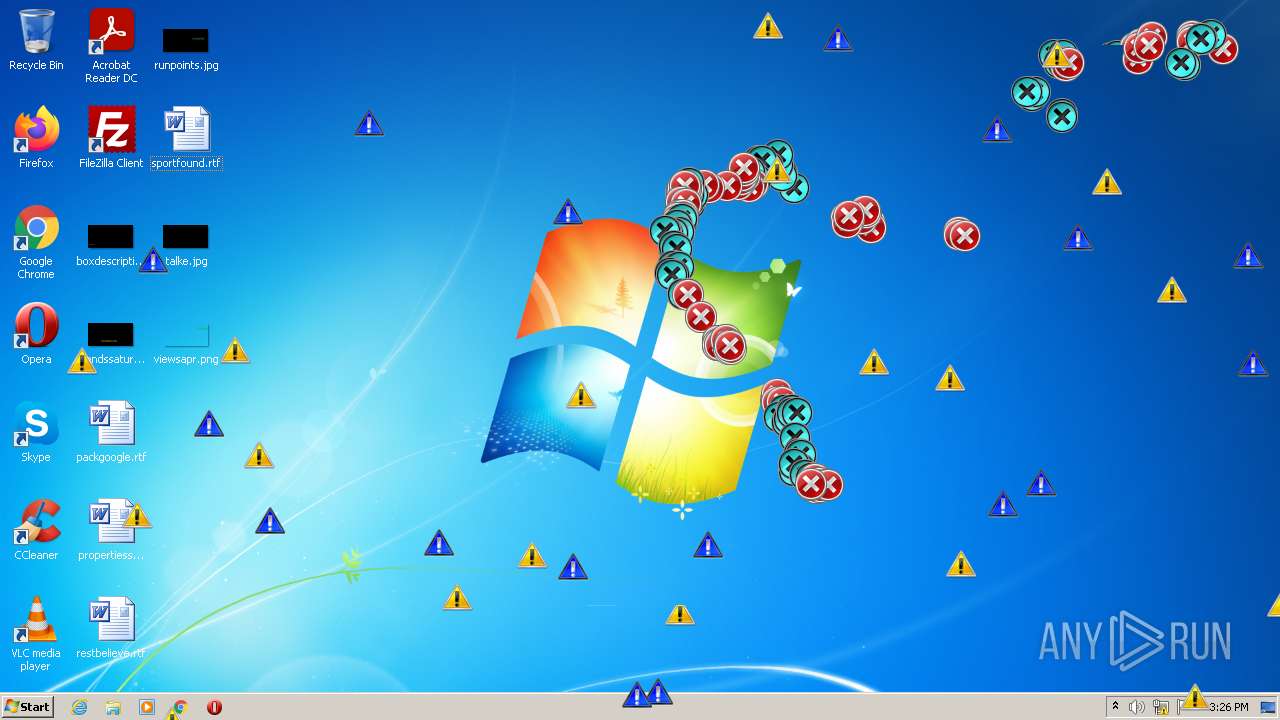
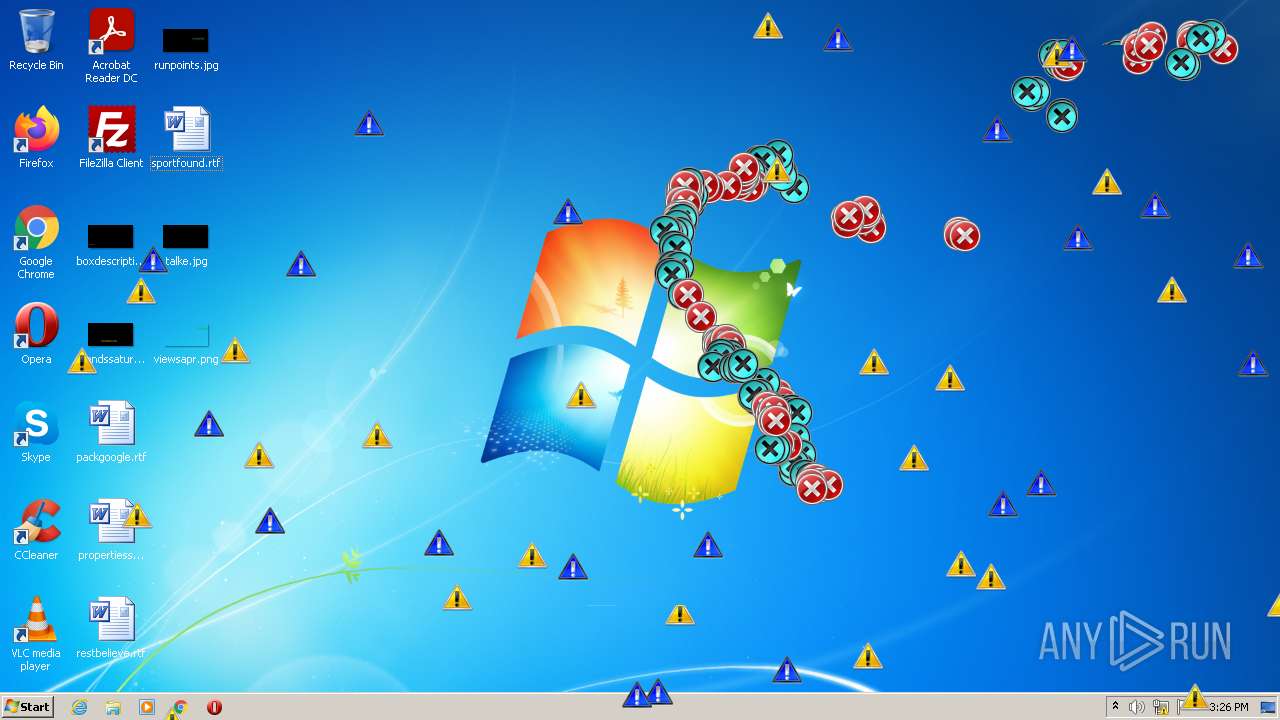
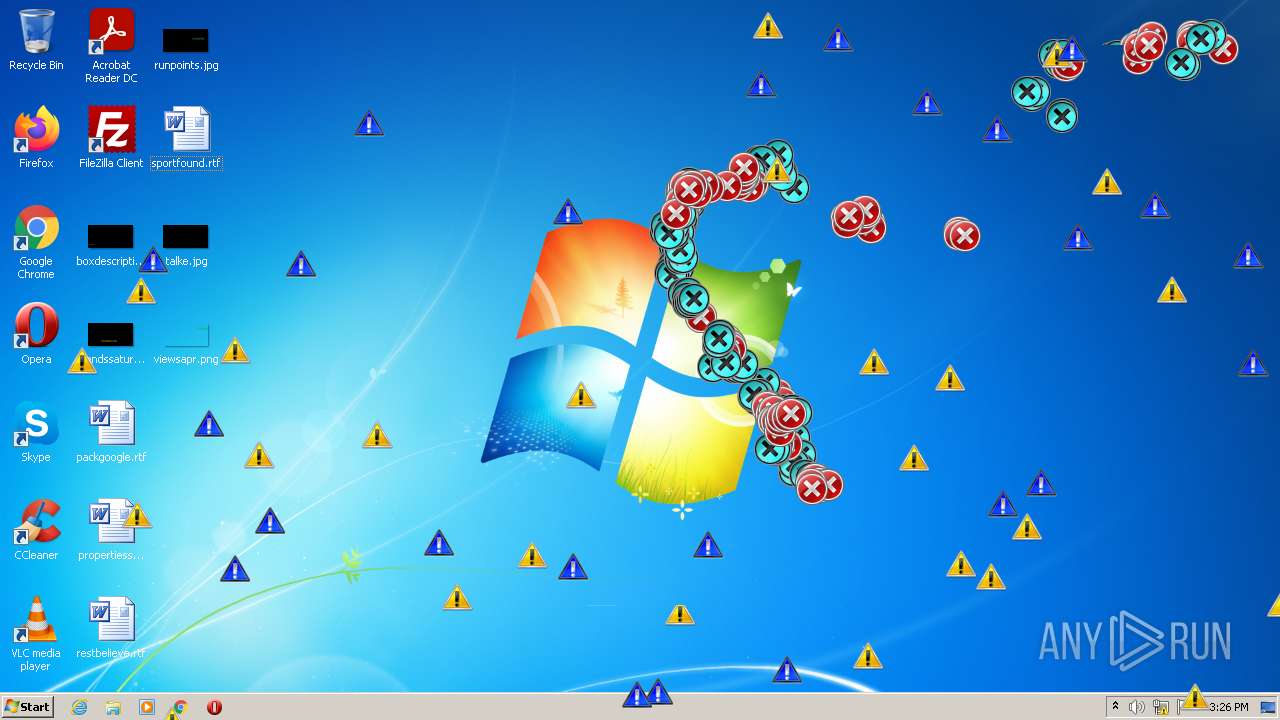
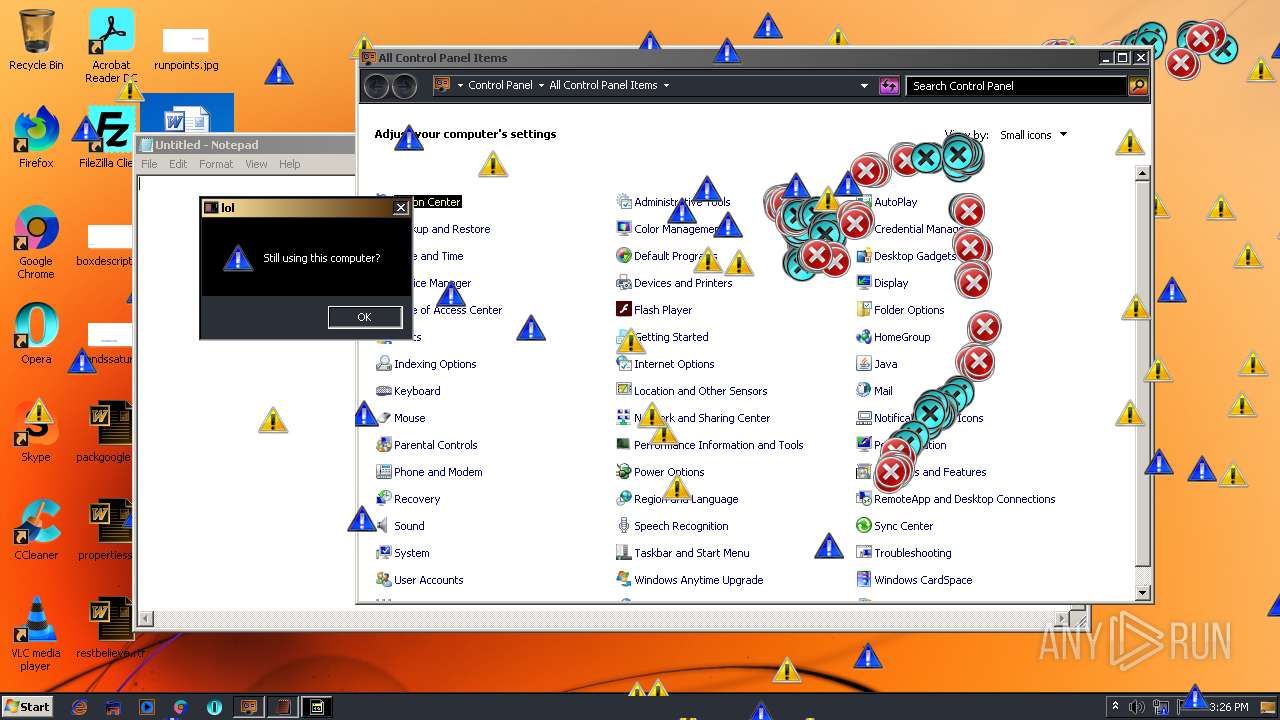
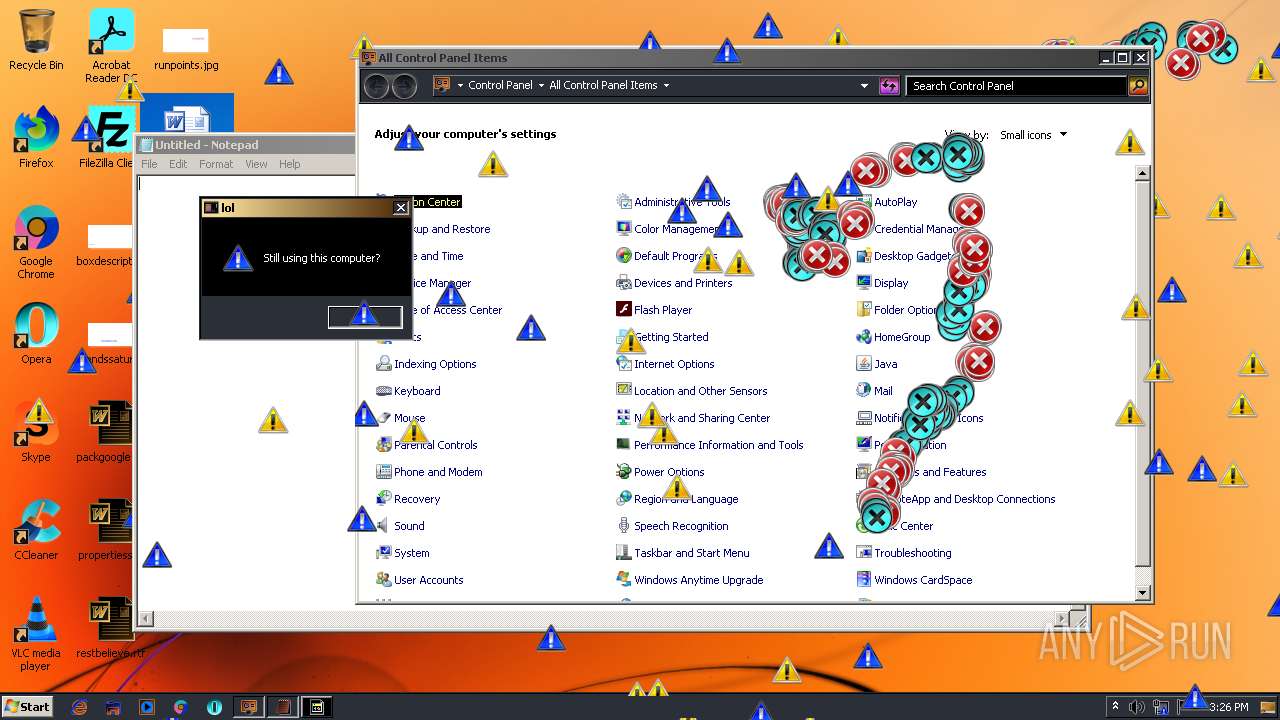
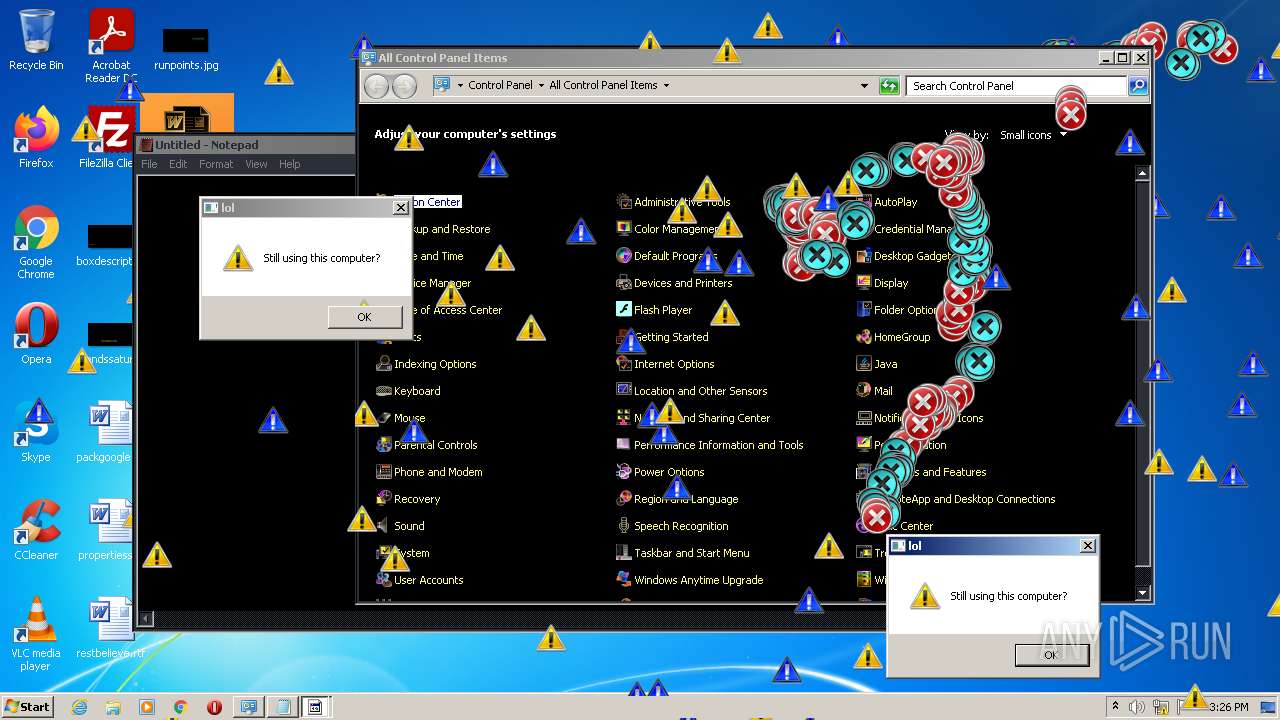
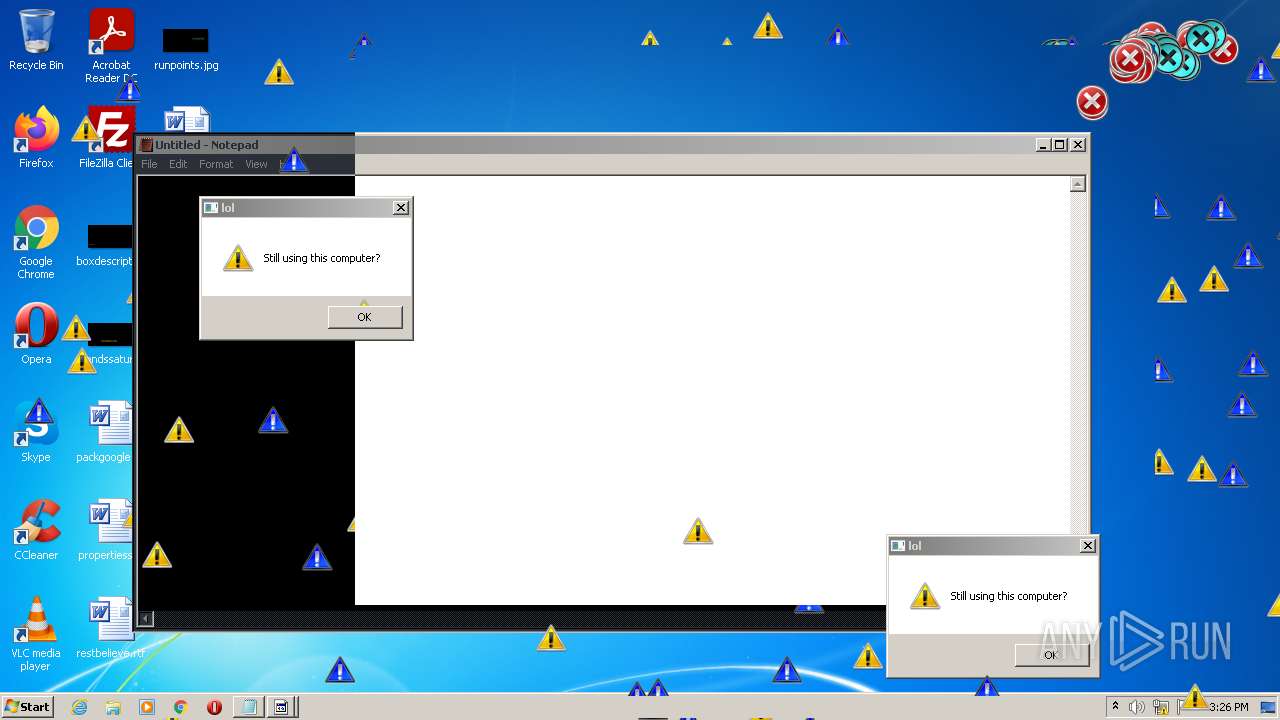
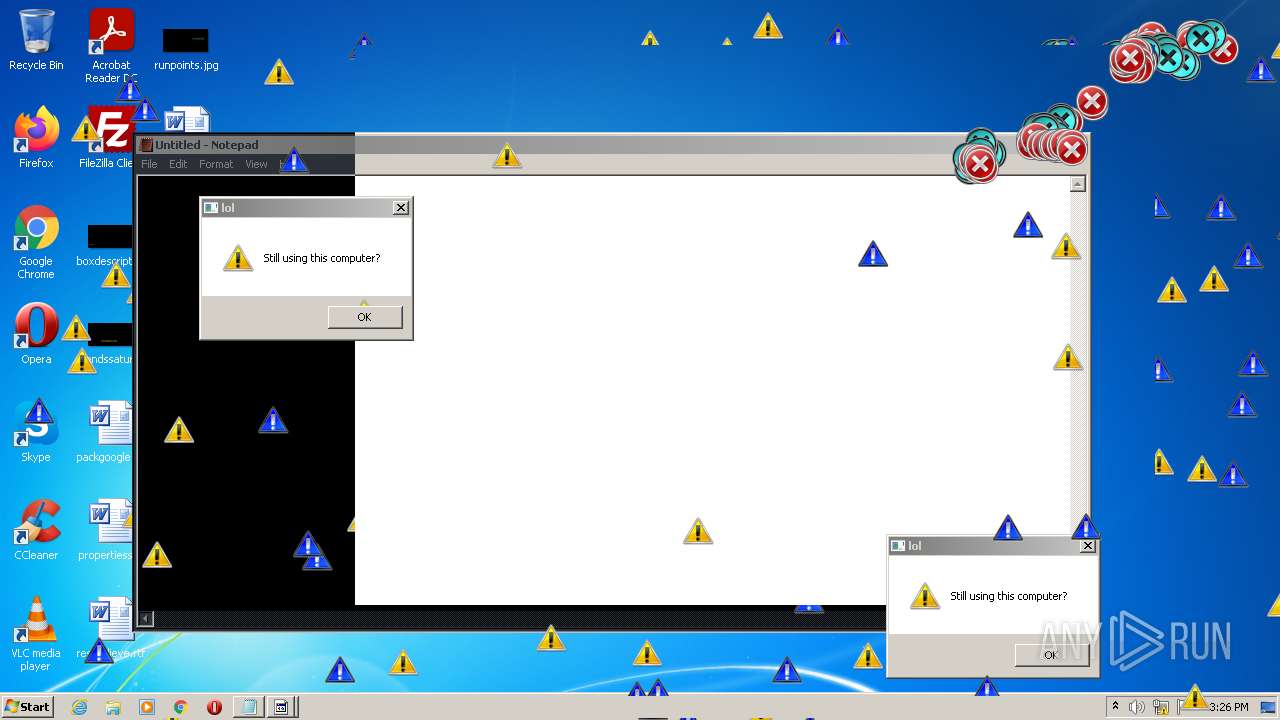
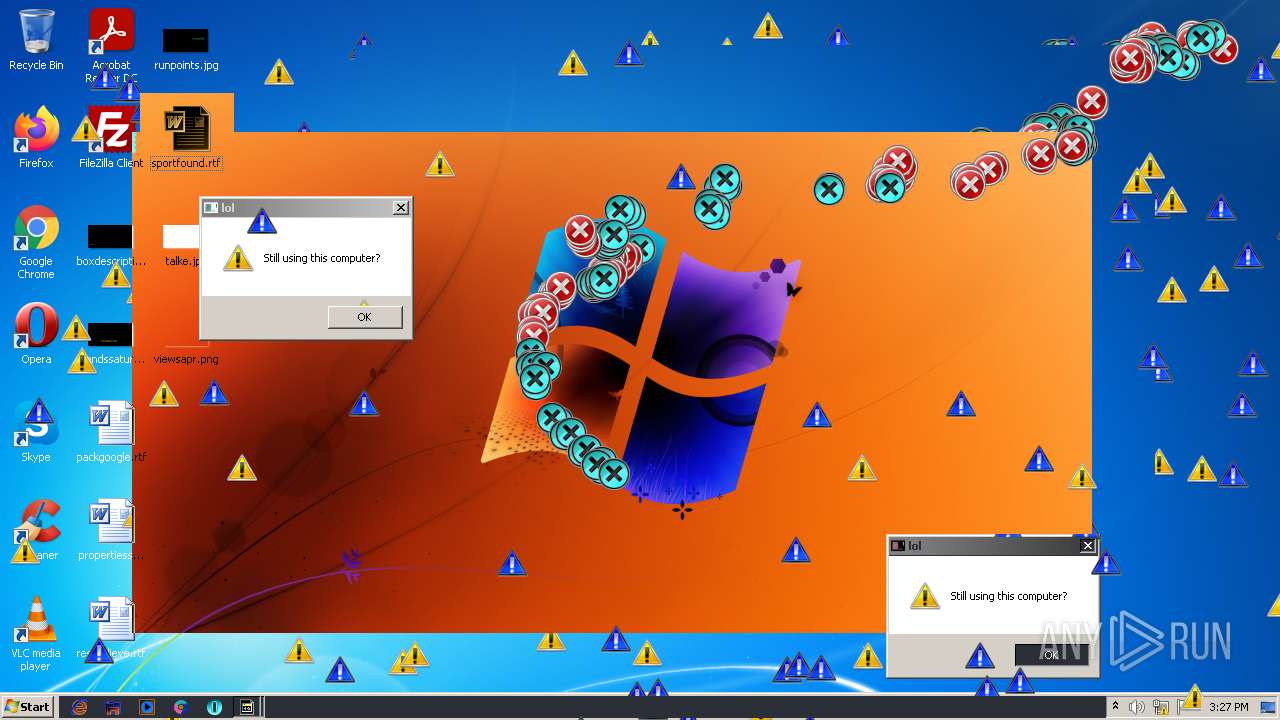
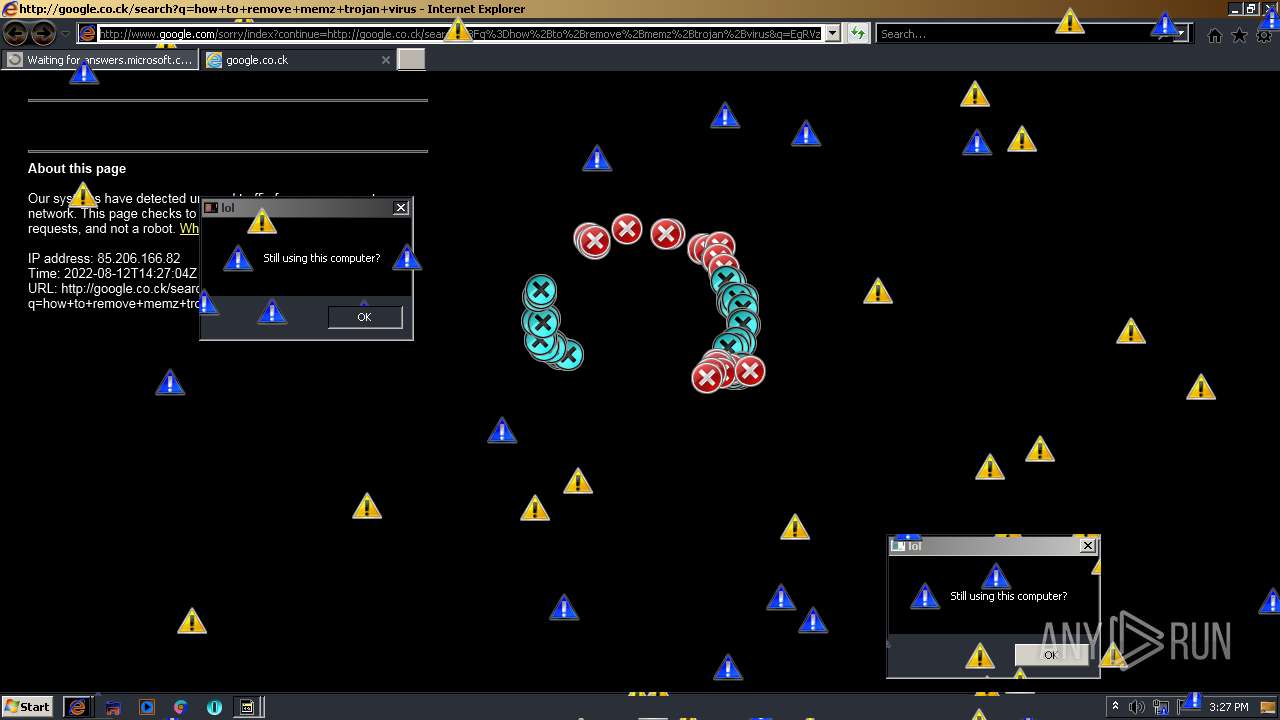
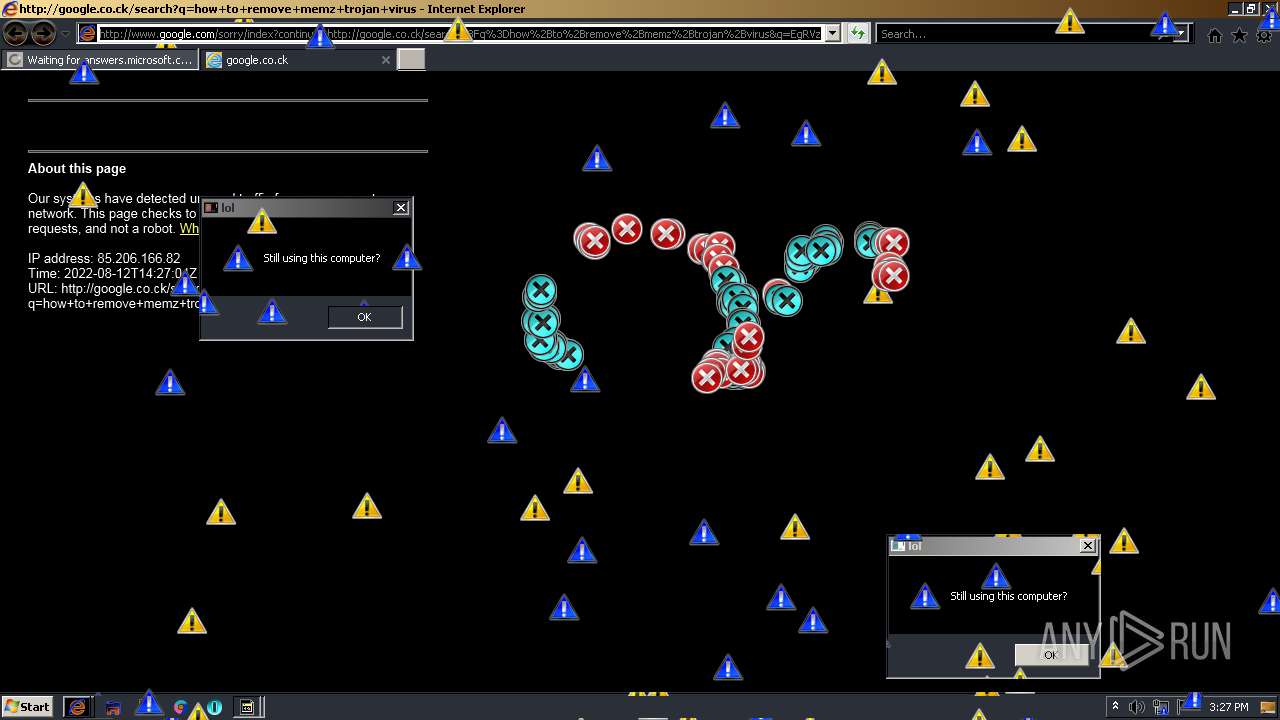
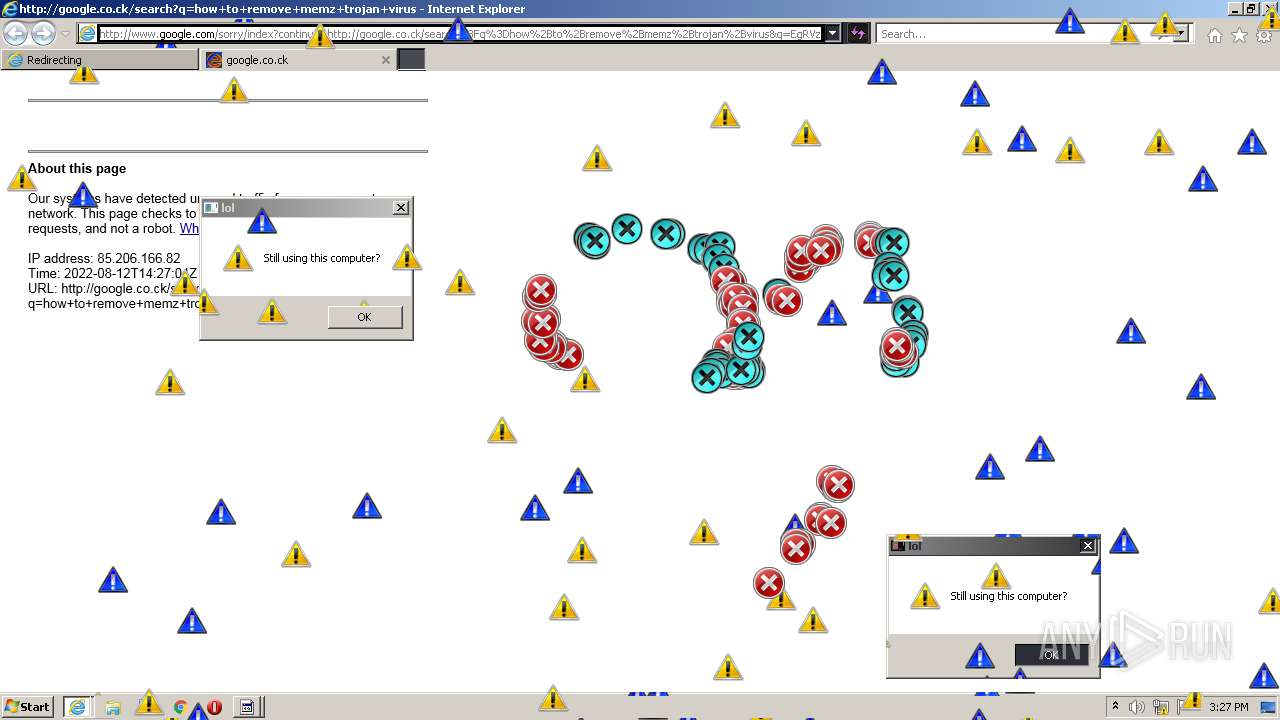
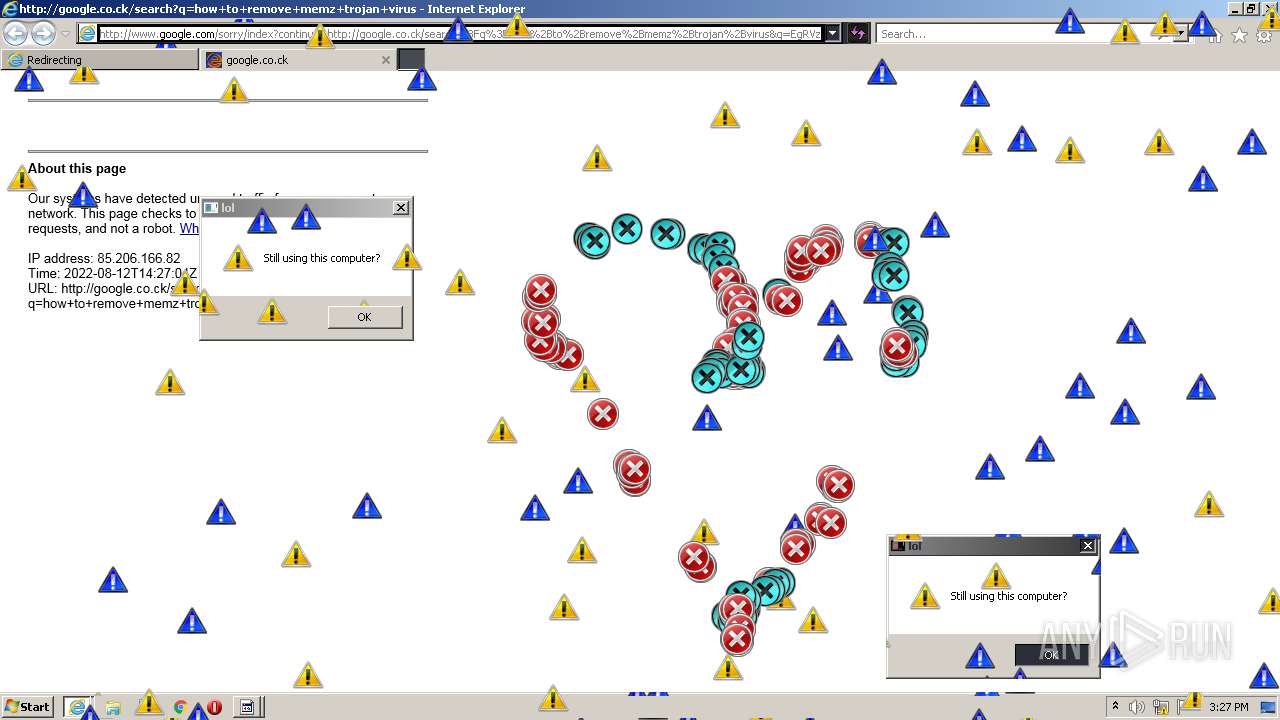
MALICIOUS
Application was dropped or rewritten from another process
- MEMZ.exe (PID: 3160)
- MEMZ.exe (PID: 1060)
- MEMZ.exe (PID: 2636)
- MEMZ.exe (PID: 596)
- MEMZ.exe (PID: 3000)
- MEMZ.exe (PID: 1044)
- MEMZ.exe (PID: 3260)
- MEMZ.exe (PID: 2880)
- MEMZ.exe (PID: 504)
- MEMZ.exe (PID: 1288)
- MEMZ.exe (PID: 2316)
- MEMZ.exe (PID: 3152)
- MEMZ.exe (PID: 4072)
- MEMZ.exe (PID: 2124)
- MEMZ.exe (PID: 1984)
- MEMZ.exe (PID: 3524)
- MEMZ.exe (PID: 2416)
- MEMZ.exe (PID: 2620)
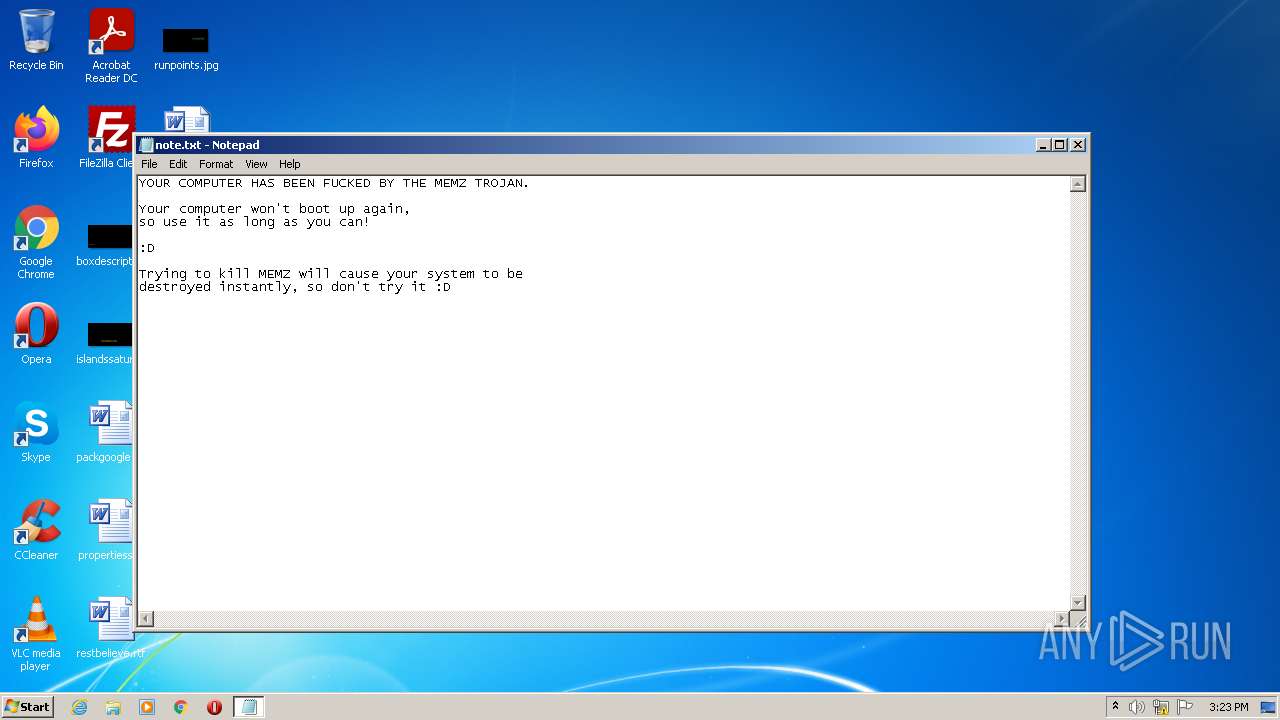
Drops executable file immediately after starts
- cscript.exe (PID: 2784)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3388)
- cmd.exe (PID: 508)
- MEMZ.exe (PID: 1060)
- cscript.exe (PID: 3048)
- cscript.exe (PID: 2784)
- cmd.exe (PID: 2432)
- MEMZ.exe (PID: 2880)
- MEMZ.exe (PID: 504)
- MEMZ.exe (PID: 2316)
- MEMZ.exe (PID: 3152)
- MEMZ.exe (PID: 1288)
- MEMZ.exe (PID: 1044)
- MEMZ.exe (PID: 3260)
- MEMZ.exe (PID: 4072)
- MEMZ.exe (PID: 2124)
- MEMZ.exe (PID: 2416)
- MEMZ.exe (PID: 3524)
- MEMZ.exe (PID: 1984)
- MEMZ.exe (PID: 2620)
- wordpad.exe (PID: 2052)
- cmd.exe (PID: 3940)
Reads the computer name
- WinRAR.exe (PID: 3388)
- cscript.exe (PID: 2784)
- cmd.exe (PID: 508)
- cscript.exe (PID: 3048)
- cmd.exe (PID: 2432)
- MEMZ.exe (PID: 2880)
- MEMZ.exe (PID: 3260)
- MEMZ.exe (PID: 1060)
- MEMZ.exe (PID: 2620)
- wordpad.exe (PID: 2052)
Drops a file with a compile date too recent
- cscript.exe (PID: 2784)
Executable content was dropped or overwritten
- cscript.exe (PID: 2784)
Application launched itself
- MEMZ.exe (PID: 2880)
- MEMZ.exe (PID: 1060)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 876)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 3240)
- iexplore.exe (PID: 2228)
- iexplore.exe (PID: 4016)
- iexplore.exe (PID: 3608)
- iexplore.exe (PID: 1376)
- iexplore.exe (PID: 3596)
- iexplore.exe (PID: 2956)
- iexplore.exe (PID: 476)
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 280)
- iexplore.exe (PID: 1440)
INFO
Checks Windows Trust Settings
- cscript.exe (PID: 2784)
- cscript.exe (PID: 3048)
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 3240)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 1376)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 280)
Checks supported languages
- notepad.exe (PID: 3420)
- notepad.exe (PID: 2896)
- notepad.exe (PID: 3316)
- iexplore.exe (PID: 3196)
- iexplore.exe (PID: 876)
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 3240)
- explorer.exe (PID: 3656)
- mmc.exe (PID: 2036)
- opera.exe (PID: 1176)
- iexplore.exe (PID: 1348)
- iexplore.exe (PID: 2228)
- iexplore.exe (PID: 4016)
- iexplore.exe (PID: 1376)
- iexplore.exe (PID: 508)
- control.exe (PID: 1504)
- iexplore.exe (PID: 3608)
- explorer.exe (PID: 1824)
- iexplore.exe (PID: 3064)
- iexplore.exe (PID: 3596)
- iexplore.exe (PID: 3528)
- iexplore.exe (PID: 476)
- control.exe (PID: 2056)
- iexplore.exe (PID: 2956)
- control.exe (PID: 2236)
- notepad.exe (PID: 3856)
- iexplore.exe (PID: 276)
- iexplore.exe (PID: 3692)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 280)
- iexplore.exe (PID: 1440)
Reads the computer name
- iexplore.exe (PID: 3196)
- iexplore.exe (PID: 876)
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 3240)
- mmc.exe (PID: 2036)
- opera.exe (PID: 1176)
- explorer.exe (PID: 3656)
- iexplore.exe (PID: 1348)
- iexplore.exe (PID: 2228)
- iexplore.exe (PID: 4016)
- iexplore.exe (PID: 3608)
- control.exe (PID: 1504)
- iexplore.exe (PID: 508)
- iexplore.exe (PID: 1376)
- explorer.exe (PID: 1824)
- iexplore.exe (PID: 3064)
- iexplore.exe (PID: 3596)
- iexplore.exe (PID: 3528)
- control.exe (PID: 2056)
- iexplore.exe (PID: 3692)
- iexplore.exe (PID: 2956)
- control.exe (PID: 2236)
- iexplore.exe (PID: 276)
- iexplore.exe (PID: 476)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 280)
- iexplore.exe (PID: 1440)
Changes internet zones settings
- iexplore.exe (PID: 3196)
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 1348)
- iexplore.exe (PID: 508)
- iexplore.exe (PID: 3064)
- iexplore.exe (PID: 3692)
- iexplore.exe (PID: 3528)
- iexplore.exe (PID: 276)
Application launched itself
- iexplore.exe (PID: 3196)
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 1348)
- iexplore.exe (PID: 508)
- iexplore.exe (PID: 3064)
- iexplore.exe (PID: 3528)
- iexplore.exe (PID: 3692)
- iexplore.exe (PID: 276)
Reads the date of Windows installation
- iexplore.exe (PID: 3196)
- iexplore.exe (PID: 3668)
- opera.exe (PID: 1176)
- iexplore.exe (PID: 1348)
- iexplore.exe (PID: 3064)
- iexplore.exe (PID: 508)
- iexplore.exe (PID: 3692)
- iexplore.exe (PID: 3528)
Reads settings of System Certificates
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 3240)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 1376)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 280)
Reads internet explorer settings
- iexplore.exe (PID: 3240)
- iexplore.exe (PID: 304)
- iexplore.exe (PID: 4016)
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 280)
Check for Java to be installed
- opera.exe (PID: 1176)
Manual execution by user
- opera.exe (PID: 1176)
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 1176)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 2204)
Changes settings of System certificates
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 2204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
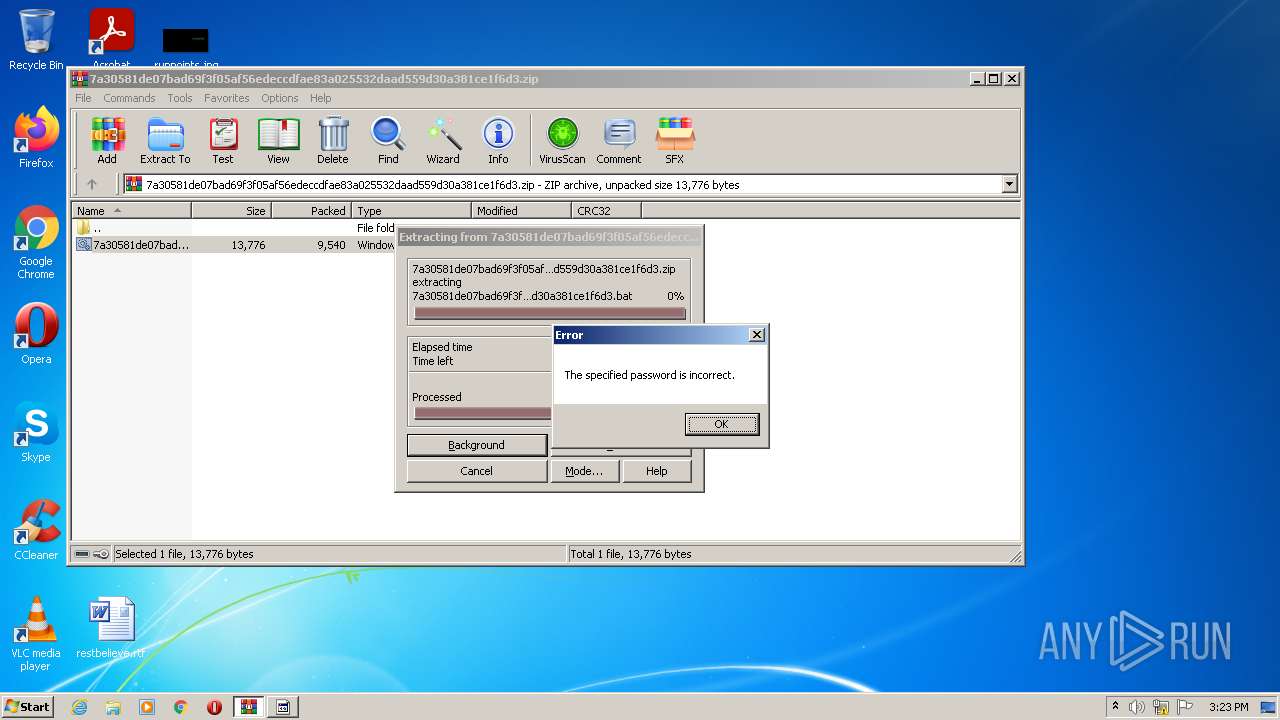
| ZipFileName: | 7a30581de07bad69f3f05af56edeccdfae83a025532daad559d30a381ce1f6d3.bat |
|---|---|
| ZipUncompressedSize: | 13776 |
| ZipCompressedSize: | 9540 |
| ZipCRC: | 0x030a8048 |
| ZipModifyDate: | 2022:08:10 11:04:07 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0003 |
| ZipRequiredVersion: | 51 |
Total processes
110
Monitored processes
58
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
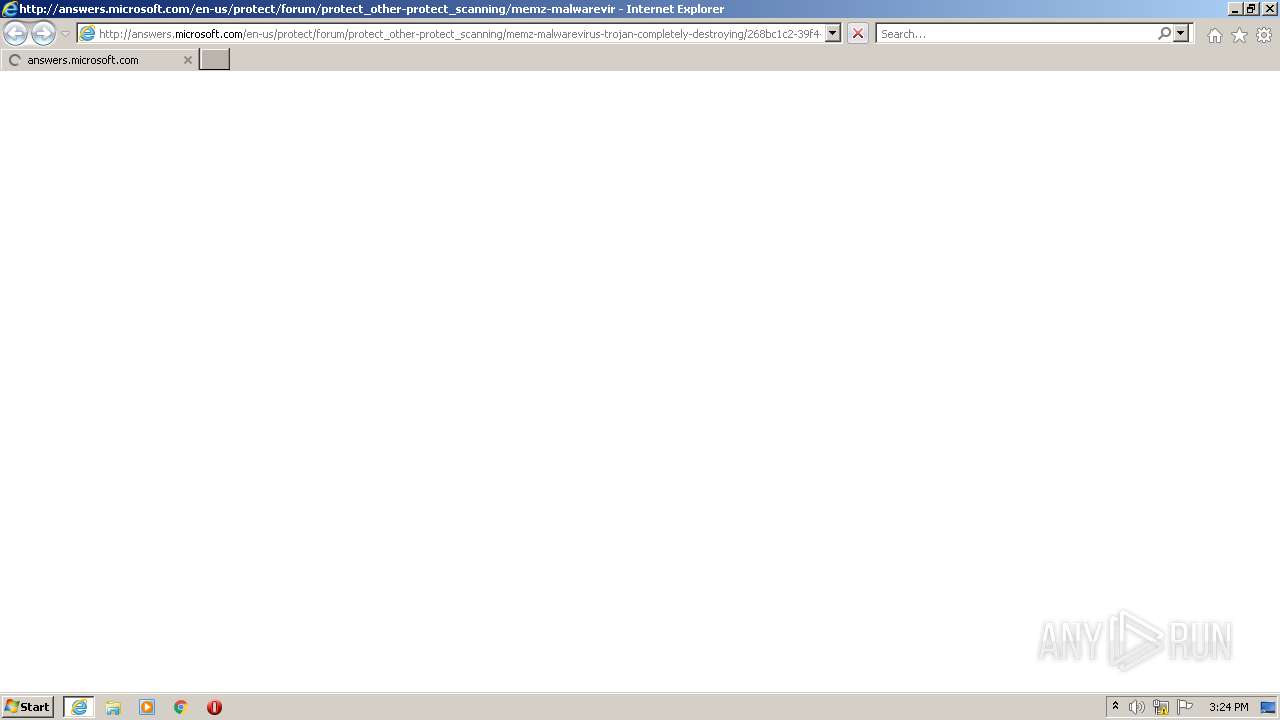
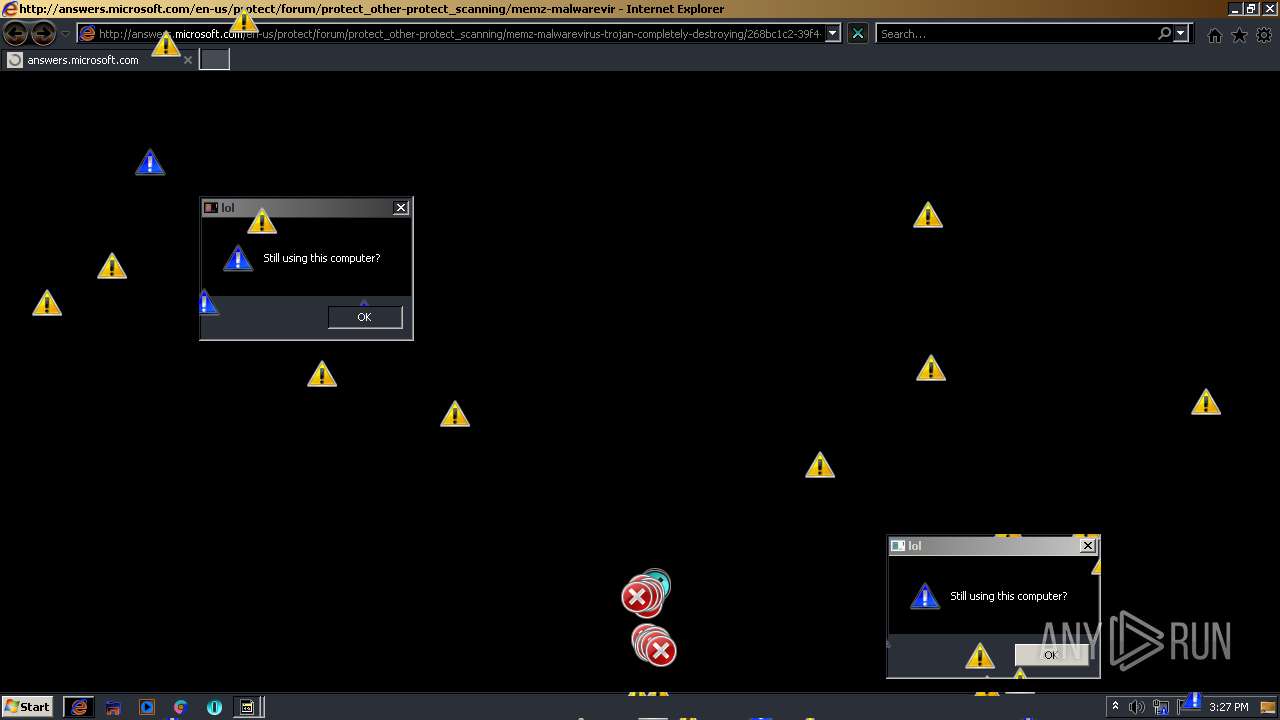
| 276 | "C:\Program Files\Internet Explorer\iexplore.exe" http://answers.microsoft.com/en-us/protect/forum/protect_other-protect_scanning/memz-malwarevirus-trojan-completely-destroying/268bc1c2-39f4-42f8-90c2-597a673b6b45 | C:\Program Files\Internet Explorer\iexplore.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 280 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:276 CREDAT:734217 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 304 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3668 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 476 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3528 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
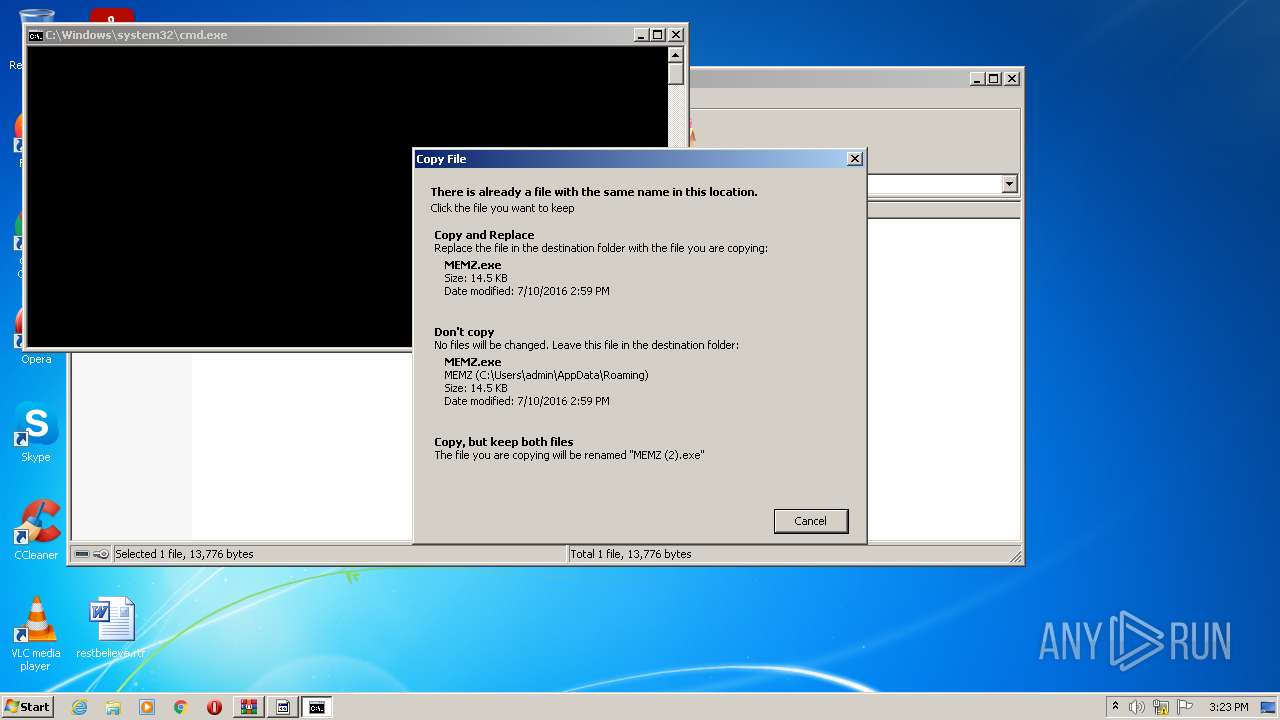
| 504 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 508 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIb3388.34410\7a30581de07bad69f3f05af56edeccdfae83a025532daad559d30a381ce1f6d3.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
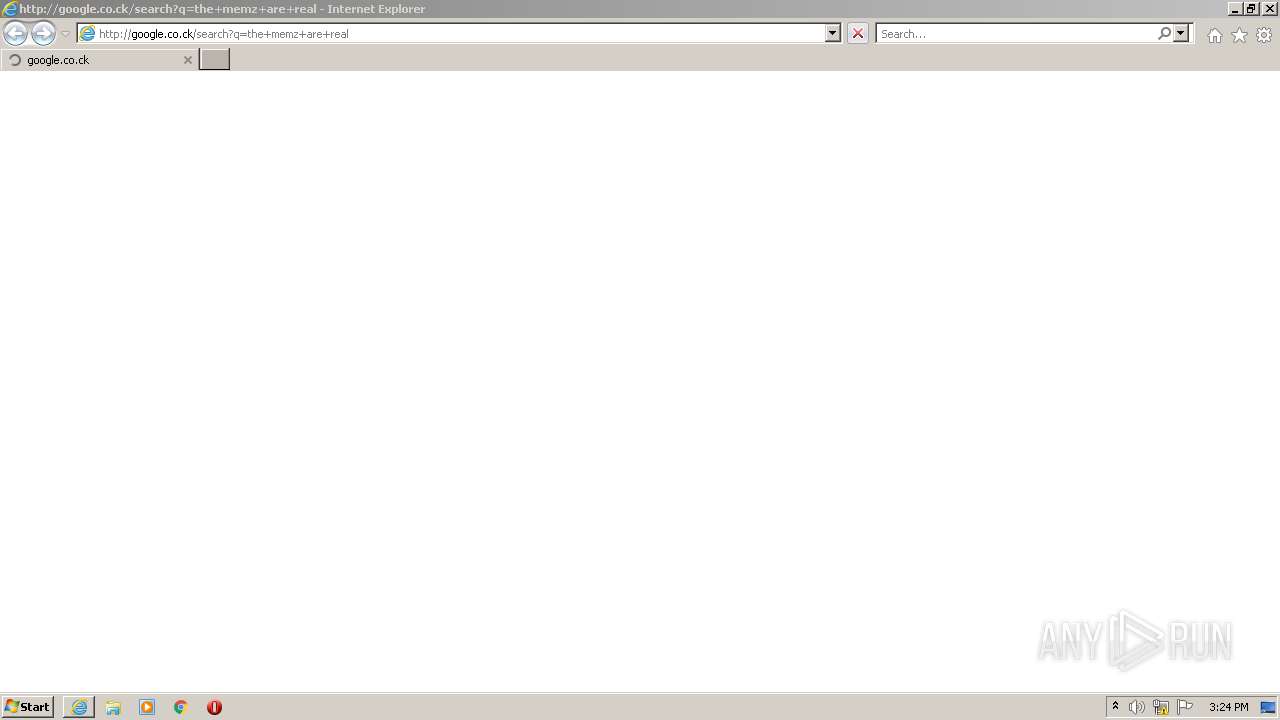
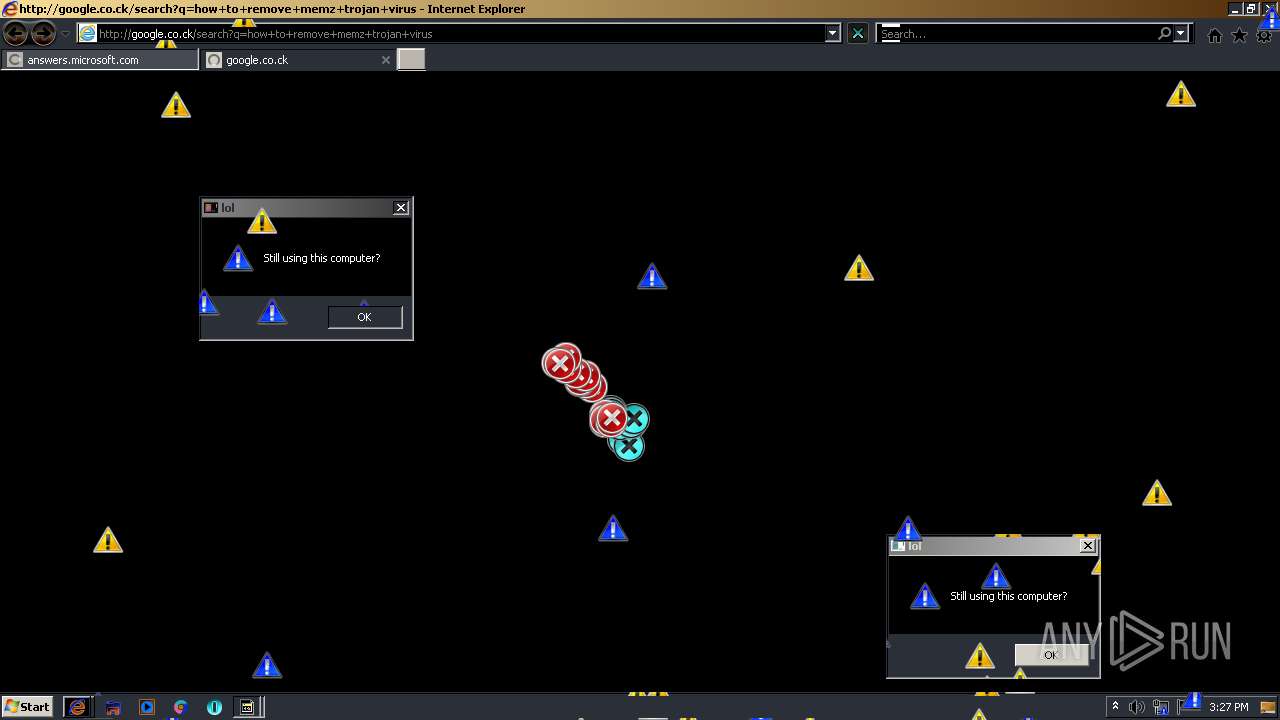
| 508 | "C:\Program Files\Internet Explorer\iexplore.exe" http://google.co.ck/search?q=batch+virus+download | C:\Program Files\Internet Explorer\iexplore.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 596 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3196 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
54 212
Read events
52 909
Write events
1 287
Delete events
16
Modification events
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\7a30581de07bad69f3f05af56edeccdfae83a025532daad559d30a381ce1f6d3.zip | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
62
Text files
35
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3388.34410\7a30581de07bad69f3f05af56edeccdfae83a025532daad559d30a381ce1f6d3.bat | text | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Last Active\{699C55D3-1A4A-11ED-8C90-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3388.34998\7a30581de07bad69f3f05af56edeccdfae83a025532daad559d30a381ce1f6d3.bat | text | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF3DC5AC72222B77E0.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF57DC09F0C1570848.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\{699C55D1-1A4A-11ED-8C90-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB3FAD90927889215.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Active\RecoveryStore.{699C55CF-1A4A-11ED-8C90-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3240 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\FWPH6XZC.txt | text | |
MD5:— | SHA256:— | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\High\Last Active\RecoveryStore.{699C55D2-1A4A-11ED-8C90-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
96
DNS requests
44
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
876 | iexplore.exe | GET | 301 | 104.111.216.166:80 | http://answers.microsoft.com/en-us/protect/forum/protect_other-protect_scanning/memz-malwarevirus-trojan-completely-destroying/268bc1c2-39f4-42f8-90c2-597a673b6b45 | NL | — | — | whitelisted |
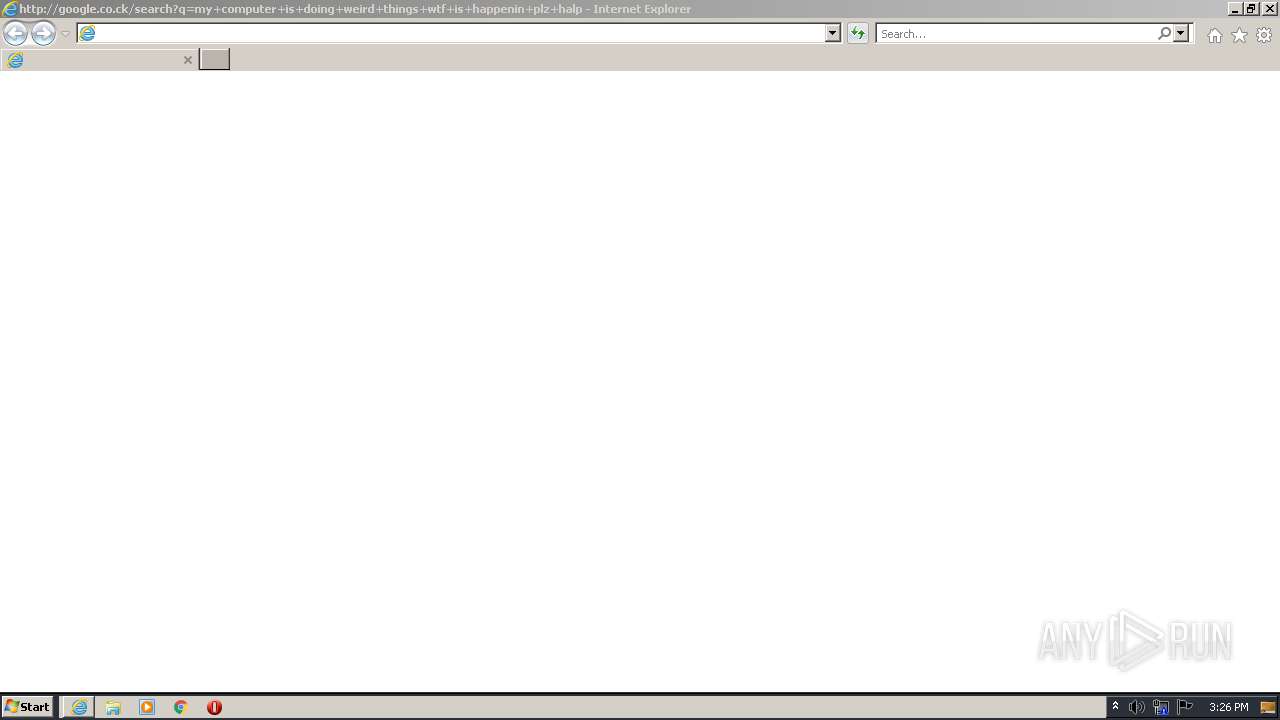
3596 | iexplore.exe | GET | — | 216.58.212.164:80 | http://google.co.ck/search?q=my+computer+is+doing+weird+things+wtf+is+happenin+plz+halp | US | — | — | whitelisted |
4016 | iexplore.exe | GET | — | 216.58.212.164:80 | http://google.co.ck/search?q=how+to+code+a+virus+in+visual+basic | US | — | — | whitelisted |
1176 | opera.exe | GET | — | 142.250.184.227:80 | http://www.google.com.ua/search?q=youtube&sourceid=opera&ie=utf-8&oe=utf-8&channel=suggest | US | — | — | whitelisted |
1376 | iexplore.exe | GET | 301 | 104.111.216.166:80 | http://answers.microsoft.com/en-us/protect/forum/protect_other-protect_scanning/memz-malwarevirus-trojan-completely-destroying/268bc1c2-39f4-42f8-90c2-597a673b6b45 | NL | — | — | whitelisted |
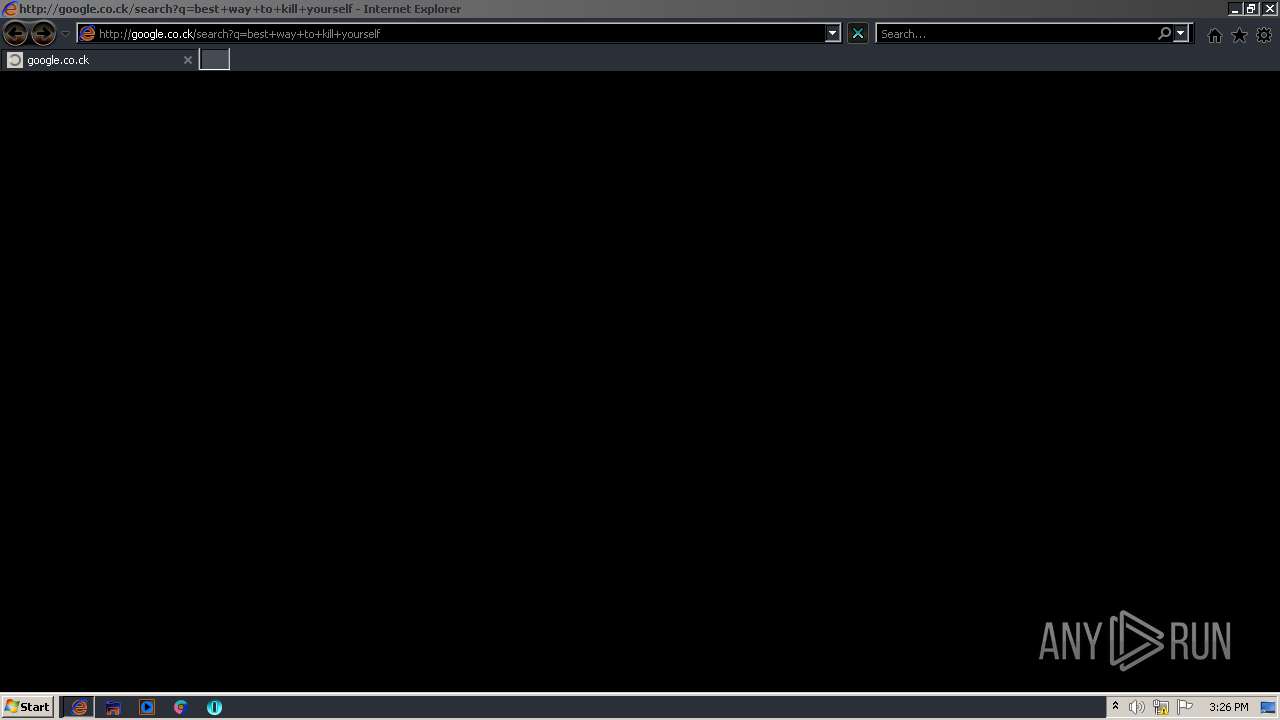
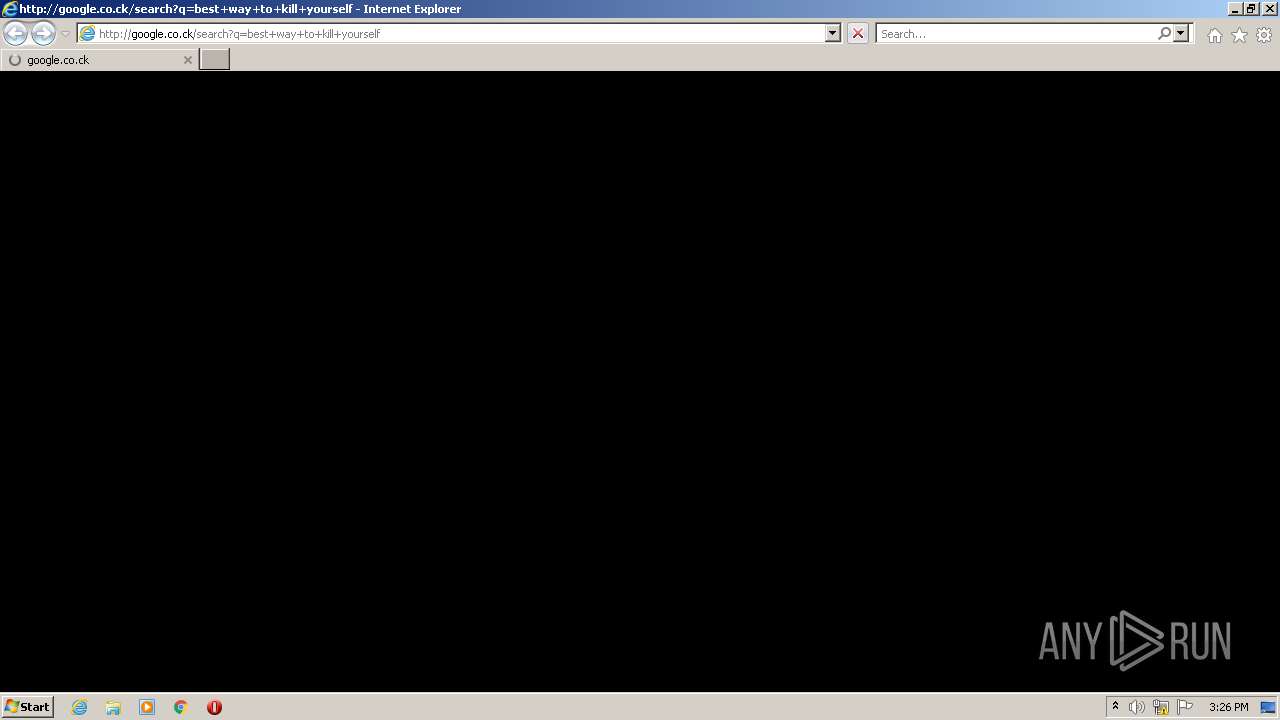
476 | iexplore.exe | GET | — | 216.58.212.164:80 | http://google.co.ck/search?q=best+way+to+kill+yourself | US | — | — | whitelisted |
2228 | iexplore.exe | GET | — | 216.58.212.164:80 | http://google.co.ck/search?q=minecraft+hax+download+no+virus | US | — | — | whitelisted |
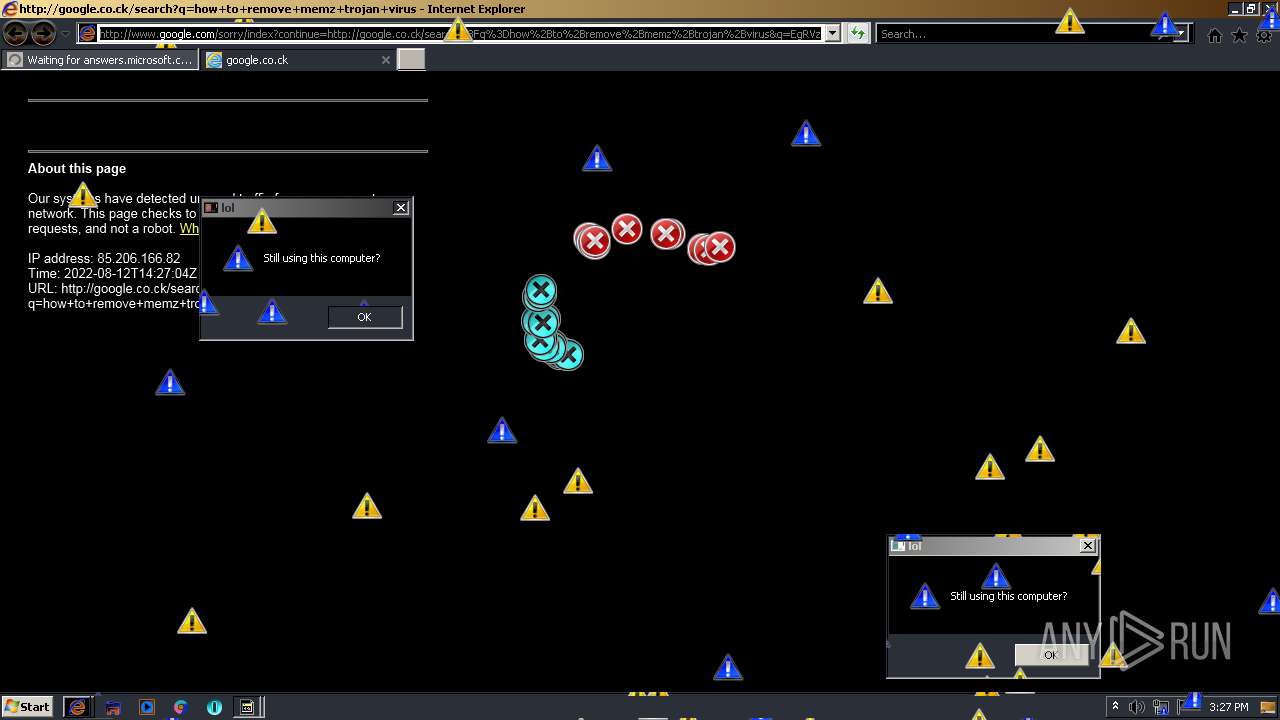
3608 | iexplore.exe | GET | — | 172.217.18.100:80 | http://www.google.com/sorry/index?continue=http://google.co.ck/search%3Fq%3Dbatch%2Bvirus%2Bdownload&q=EgRVzqZSGPLF2ZcGIhDxCBCo-pbOZjgqscHOO2JHMgFy | US | — | — | malicious |
3240 | iexplore.exe | GET | 302 | 216.58.212.164:80 | http://google.co.ck/search?q=mcafee+vs+norton | US | html | 344 b | whitelisted |
3668 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
876 | iexplore.exe | 104.111.216.166:80 | answers.microsoft.com | Akamai International B.V. | NL | unknown |
304 | iexplore.exe | 216.58.212.164:80 | google.co.ck | Google Inc. | US | whitelisted |
876 | iexplore.exe | 104.111.216.166:443 | answers.microsoft.com | Akamai International B.V. | NL | unknown |
3240 | iexplore.exe | 216.58.212.164:80 | google.co.ck | Google Inc. | US | whitelisted |
3668 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3240 | iexplore.exe | 172.217.18.100:80 | www.google.com | Google Inc. | US | whitelisted |
3240 | iexplore.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
3668 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
304 | iexplore.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
1176 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
answers.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |
google.co.ck |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
certs.opera.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report