| File name: | .PrintExp.exe |
| Full analysis: | https://app.any.run/tasks/173b3855-9dac-4905-87af-6ba781b67c59 |
| Verdict: | Malicious activity |
| Analysis date: | October 18, 2024, 00:49:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1770A8EA718BC965B6911996C8BE59CB |
| SHA1: | 82DA28A9E5F894EBB5E6BE802242930FCAF1EE64 |
| SHA256: | DFB0EEF5D149FF5BCF42205277C1ADAEDD56EA799E1C65385ECD489F55C8AC8D |
| SSDEEP: | 98304:7r7ayGJ6kHOSP59WX882XHD2D+S+6YqVM1gFZ/jYSg67PCmMpH7D+POLb4b62BoI:Tf |
MALICIOUS
Changes the autorun value in the registry
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Connects to the CnC server
- Synaptics.exe (PID: 6228)
SUSPICIOUS
Reads security settings of Internet Explorer
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Executable content was dropped or overwritten
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Contacting a server suspected of hosting an CnC
- Synaptics.exe (PID: 6228)
There is functionality for taking screenshot (YARA)
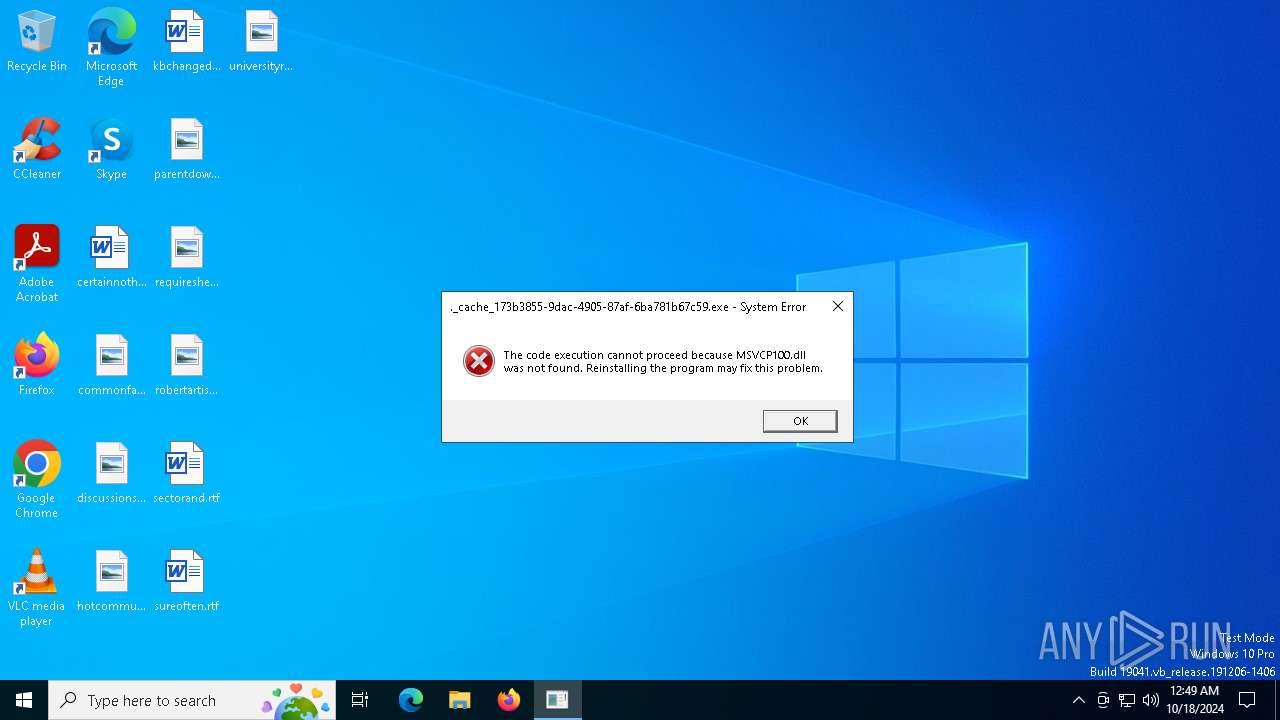
- ._cache_173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6844)
- Synaptics.exe (PID: 6228)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 6228)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 6228)
INFO
Reads the computer name
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Create files in a temporary directory
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Checks supported languages
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Process checks computer location settings
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
The process uses the downloaded file
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Creates files in the program directory
- 173b3855-9dac-4905-87af-6ba781b67c59.exe (PID: 6628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (96.4) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.3) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 1702400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Turkish |
| CharacterSet: | Windows, Turkish |
| CompanyName: | Synaptics |
| FileDescription: | Synaptics Pointing Device Driver |
| FileVersion: | 1.0.0.4 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Synaptics Pointing Device Driver |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
139
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4868 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6228 | "C:\ProgramData\Synaptics\Synaptics.exe" InjUpdate | C:\ProgramData\Synaptics\Synaptics.exe | 173b3855-9dac-4905-87af-6ba781b67c59.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: HIGH Description: Synaptics Pointing Device Driver Version: 1.0.0.4 Modules
| |||||||||||||||
| 6628 | "C:\Users\admin\AppData\Local\Temp\173b3855-9dac-4905-87af-6ba781b67c59.exe" | C:\Users\admin\AppData\Local\Temp\173b3855-9dac-4905-87af-6ba781b67c59.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 6648 | "C:\Users\admin\AppData\Local\Temp\._cache_173b3855-9dac-4905-87af-6ba781b67c59.exe" | C:\Users\admin\AppData\Local\Temp\._cache_173b3855-9dac-4905-87af-6ba781b67c59.exe | — | 173b3855-9dac-4905-87af-6ba781b67c59.exe | |||||||||||
User: admin Company: Shenzhen HosonSoft Co., Ltd. Integrity Level: MEDIUM Description: Hosonsoft-PrintExp Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
| 6844 | "C:\Users\admin\AppData\Local\Temp\._cache_173b3855-9dac-4905-87af-6ba781b67c59.exe" | C:\Users\admin\AppData\Local\Temp\._cache_173b3855-9dac-4905-87af-6ba781b67c59.exe | 173b3855-9dac-4905-87af-6ba781b67c59.exe | ||||||||||||
User: admin Company: Shenzhen HosonSoft Co., Ltd. Integrity Level: HIGH Description: Hosonsoft-PrintExp Version: 1.0.0.1 Modules
| |||||||||||||||
| 6888 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 608
Read events
1 604
Write events
4
Delete events
0
Modification events
| (PID) Process: | (6628) 173b3855-9dac-4905-87af-6ba781b67c59.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6628) 173b3855-9dac-4905-87af-6ba781b67c59.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Synaptics Pointing Device Driver |
Value: C:\ProgramData\Synaptics\Synaptics.exe | |||
| (PID) Process: | (6628) 173b3855-9dac-4905-87af-6ba781b67c59.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A7803901000060B81DB4E48ED2119906E49FADC173CA7D000000 | |||
| (PID) Process: | (6628) 173b3855-9dac-4905-87af-6ba781b67c59.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 84B0116700000000 | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6628 | 173b3855-9dac-4905-87af-6ba781b67c59.exe | C:\Users\admin\AppData\Local\Temp\._cache_173b3855-9dac-4905-87af-6ba781b67c59.exe | executable | |
MD5:AAA73B11438CBEB9CB1F5DFDA3C3664B | SHA256:21F013C7D44F5E18CB8C6A8819E483FC75C3A1D5F78E77BD7F33A940B73227A8 | |||
| 6628 | 173b3855-9dac-4905-87af-6ba781b67c59.exe | C:\ProgramData\Synaptics\RCXBA11.tmp | executable | |
MD5:FDDC9378895CD6C8B475FF7F34DB7B7F | SHA256:8D0EB55F72C6A318D6A4A9C9D50AB6FE6C6F34E8842B979CF99A90CD830CA4D4 | |||
| 6628 | 173b3855-9dac-4905-87af-6ba781b67c59.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:1770A8EA718BC965B6911996C8BE59CB | SHA256:DFB0EEF5D149FF5BCF42205277C1ADAEDD56EA799E1C65385ECD489F55C8AC8D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
69
DNS requests
21
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6228 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3028 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3028 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1768 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5640 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.16.110.121:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2172 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2172 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
6228 | Synaptics.exe | 69.42.215.252:80 | freedns.afraid.org | AWKNET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
xred.mooo.com |
| whitelisted |
freedns.afraid.org |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
3 ETPRO signatures available at the full report